CAS-003 Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your CAS-003 certification exam? Start your preparation the smart way with our CAS-003 Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for CAS-003 exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our CAS-003 Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
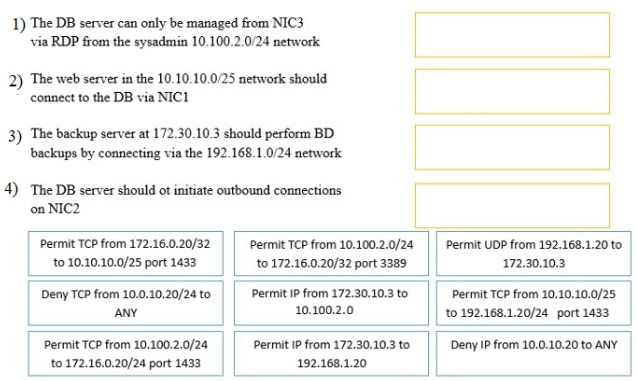
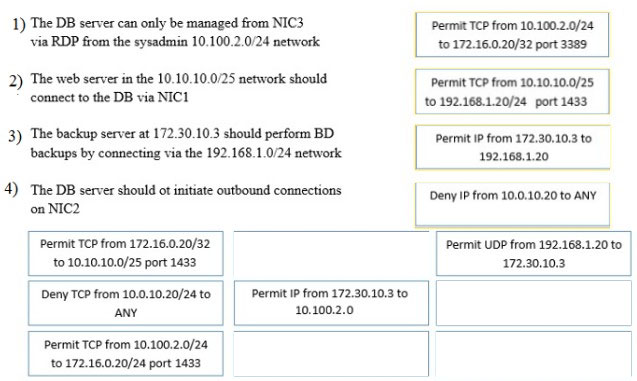
DRAG DROP - A security administrator must configure the database server shown below to comply with the four requirements listed. Drag and drop the appropriate ACL that should be configured on the database server to its corresponding requirement. Answer options may be used once or not at all.Select and Place:
A systems administrator receives an advisory email that a recently discovered exploit is being used in another country and the financial institutions have ceased operations while they find a way to respond to the attack. Which of the following BEST describes where the administrator should look to find information on the attack to determine if a response must be prepared for the systems? (Choose two.)
A. Bug bounty websites
B. Hacker forums
C. Antivirus vendor websites
D. Trade industry association websites
E. CVE database
F. Company’s legal department
The board of a financial services company has requested that the senior security analyst acts as a cybersecurity advisor in order to comply with recent federal legislation. The analyst is required to give a report on current cybersecurity and threat trends in the financial services industry at the next board meeting. Which of the following would be the BEST methods to prepare this report? (Choose two.)
A. Review the CVE database for critical exploits over the past year
B. Use social media to contact industry analysts
C. Use intelligence gathered from the Internet relay chat channels
D. Request information from security vendors and government agencies
E. Perform a penetration test of the competitor’s network and share the results with the board
A Chief Information Security Officer (CISO) is reviewing technical documentation from various regional offices and notices some key differences between these groups. The CISO has not discovered any governance documentation. The CISO creates the following chart to visualize the differences among the networking used:Which of the following would be the CISO's MOST immediate concern?
A. There are open standards in use on the network.
B. Network engineers have ignored defacto standards.
C. Network engineers are not following SOPs.
D. The network has competing standards in use.
Ann, a corporate executive, has been the recent target of increasing attempts to obtain corporate secrets by competitors through advanced, well-funded means. Ann frequently leaves her laptop unattended and physically unsecure in hotel rooms during travel. A security engineer must find a practical solution for Ann that minimizes the need for user training. Which of the following is the BEST solution in this scenario?
A. Full disk encryption
B. Biometric authentication
C. An eFuse-based solution
D. Two-factor authentication
The government is concerned with remote military missions being negatively impacted by the use of technology that may fail to protect operational security. To remediate this concern, a number of solutions have been implemented, including the following: ✑ End-to-end encryption of all inbound and outbound communication, including personal email and chat sessions that allow soldiers to securely communicate with families. ✑ Layer 7 inspection and TCP/UDP port restriction, including firewall rules to only allow TCP port 80 and 443 and approved applications ✑ A host-based whitelist of approved websites and applications that only allow mission-related tools and sites ✑ The use of satellite communication to include multiple proxy servers to scramble the source IP address Which of the following is of MOST concern in this scenario?
A. The unsecure port 80 being used for general web traffic
B. Family members posting geotagged images on social media that were received via email from soldiers
C. The effect of communication latency that may negatively impact real-time communication with mission control
D. The use of centrally managed military network and computers by soldiers when communicating with external parties
Following a recent network intrusion, a company wants to determine the current security awareness of all of its employees. Which of the following is the BEST way to test awareness?
A. Conduct a series of security training events with comprehensive tests at the end
B. Hire an external company to provide an independent audit of the network security posture
C. Review the social media of all employees to see how much proprietary information is shared
D. Send an email from a corporate account, requesting users to log onto a website with their enterprise account
The legal department has required that all traffic to and from a company's cloud-based word processing and email system is logged. To meet this requirement, the Chief Information Security Officer (CISO) has implemented a next-generation firewall to perform inspection of the secure traffic and has decided to use a cloud- based log aggregation solution for all traffic that is logged. Which of the following presents a long-term risk to user privacy in this scenario?
A. Confidential or sensitive documents are inspected by the firewall before being logged.
B. Latency when viewing videos and other online content may increase.
C. Reports generated from the firewall will take longer to produce due to more information from inspected traffic.
D. Stored logs may contain non-encrypted usernames and passwords for personal websites.
A Chief Information Security Officer (CISO is reviewing and revising system configuration and hardening guides that were developed internally and have been used several years to secure the organization's systems. The CISO knows improvements can be made to the guides. Which of the following would be the BEST source of reference during the revision process?
A. CVE database
B. Internal security assessment reports
C. Industry-accepted standards
D. External vulnerability scan reports
E. Vendor-specific implementation guides
An external red team member conducts a penetration test, attempting to gain physical access to a large organization's server room in a branch office. During reconnaissance, the red team member sees a clearly marked door to the server room, located next to the lobby, with a tumbler lock. Which of the following is BEST for the red team member to bring on site to open the locked door as quickly as possible without causing significant damage?
A. Screwdriver set
B. Bump key
C. RFID duplicator
D. Rake picking
SIMULATION - An administrator wants to install a patch to an application. INSTRUCTIONS - Given the scenario, download, verify, and install the patch in the most secure manner. The last install that is completed will be the final submission. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
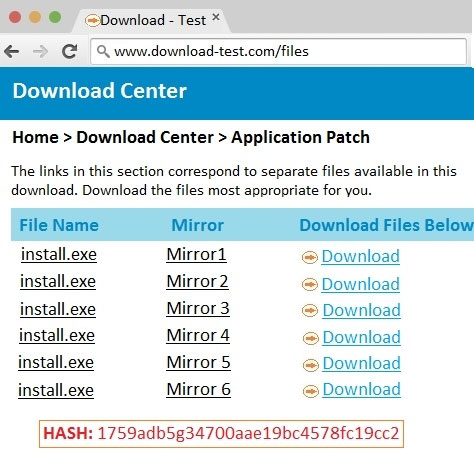
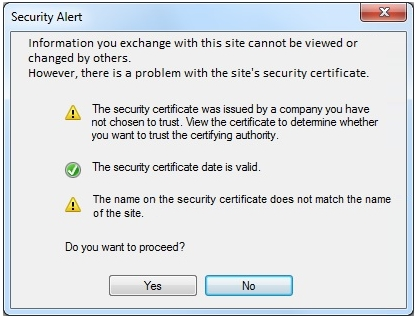
A school contracts with a vendor to devise a solution that will enable the school library to lend out tablet computers to students while on site. The tablets must adhere to string security and privacy practices. The school's key requirements are to: ✑ Maintain privacy of students in case of loss ✑ Have a theft detection control in place ✑ Be compliant with defined disability requirements Have a four-hour minimum battery lifeWhich of the following should be configured to BEST meet the requirements? (Choose two.)
A. Remote wiping
B. Geofencing
C. Antivirus software
D. TPM
E. FDE
F. Tokenization
A Chief Information Security Officer (CISO) is developing a new BIA for the organization. The CISO wants to gather requirements to determine the appropriate RTO and RPO for the organization's ERP. Which of the following should the CISO interview as MOST qualified to provide RTO/RPO metrics?
A. Data custodian
B. Data owner
C. Security analyst
D. Business unit director
E. Chief Executive Officer (CEO)
Several recent ransomware outbreaks at a company have cost a significant amount of lost revenue. The security team needs to find a technical control mechanism that will meet the following requirements and aid in preventing these outbreaks: ✑ Stop malicious software that does not match a signature ✑ Report on instances of suspicious behavior ✑ Protect from previously unknown threats Augment existing security capabilitiesWhich of the following tools would BEST meet these requirements?
A. Host-based firewall
B. EDR
C. HIPS
D. Patch management
To meet an SLA, which of the following document should be drafted, defining the company's internal interdependent unit responsibilities and delivery timelines.
A. BPA
B. OLA
C. MSA
D. MOU
A security analyst is validating the MAC policy on a set of Android devices. The policy was written to ensure non-critical applications are unable to access certain resources. When reviewing dmesg, the analyst notes many entries, such as:Despite the deny message, this action was still permitted. Which of the following is the MOST likely fix for this issue?
A. Add the objects of concern to the default context.
B. Set the devices to enforcing mode.
C. Create separate domain and context files for irc.
D. Rebuild the sepolicy, reinstall, and test.
A request has been approved for a vendor to access a new internal server using only HTTPS and SSH to manage the back-end system for the portal. Internal users just need HTTP and HTTPS access to all internal web servers. All other external access to the new server and its subnet is not allowed. The security manager must ensure proper access is configured.Below is a snippet from the firewall related to that server (access is provided in a top-down model):
Which of the following lines should be configured to allow the proper access? (Choose two.)
A. Move line 3 below line 4 and change port 80 to 443 on line 4.
B. Move line 3 below line 4 and add port 443 to line.
C. Move line 4 below line 5 and add port 80 to 8080 on line 2.
D. Add port 22 to line 2.
E. Add port 22 to line 5.
F. Add port 443 to line 2.
G. Add port 443 to line 5.
A server was compromised recently, and two unauthorized daemons were set up to listen for incoming connections. In addition, CPU cycles were being used by an additional unauthorized cron job. Which of the following would have prevented the breach if it was properly configured?
A. Set up log forwarding and utilize a SIEM for centralized management and alerting.
B. Use a patch management system to close the vulnerabilities in a shorter time frame.
C. Implement a NIDS/NIPS.
D. Deploy SELinux using the system baseline as the starting point.
E. Configure the host firewall to block unauthorized inbound connections.
After multiple service interruptions caused by an older datacenter design, a company decided to migrate away from its datacenter. The company has successfully completed the migration of all datacenter servers and services to a cloud provider. The migration project includes the following phases: ✑ Selection of a cloud provider ✑ Architectural design ✑ Microservice segmentation ✑ Virtual private cloud ✑ Geographic service redundancy ✑ Service migration The Chief Information Security Officer (CISO) is still concerned with the availability requirements of critical company applications. Which of the following should the company implement NEXT?
A. Multicloud solution
B. Single-tenancy private cloud
C. Hybrid cloud solution
D. Cloud access security broker
A security analyst is trying to identify the source of a recent data loss incident. The analyst has reviewed all the logs for the time surrounding the incident and identified all the assets on the network at the time of the data loss. The analyst suspects the key to finding the source was obfuscated in an application. Which of the following tools should the analyst use NEXT?
A. Software decompiler
B. Network enumerator
C. Log reduction and analysis tool
D. Static code analysis
An organization enables BYOD but wants to allow users to access the corporate email, calendar, and contacts from their devices. The data associated with the user's accounts is sensitive, and therefore, the organization wants to comply with the following requirements: ✑ Active full-device encryption ✑ Enabled remote-device wipe ✑ Blocking unsigned applications ✑ Containerization of email, calendar, and contacts Which of the following technical controls would BEST protect the data from attack or loss and meet the above requirements?
A. Require frequent password changes and disable NFC.
B. Enforce device encryption and activate MAM.
C. Install a mobile antivirus application.
D. Configure and monitor devices with an MDM.
Security policies that are in place at an organization prohibit USB drives from being utilized across the entire enterprise, with adequate technical controls in place to block them. As a way to still be able to work from various locations on different computing resources, several sales staff members have signed up for a web- based storage solution without the consent of the IT department. However, the operations department is required to use the same service to transmit certain business partner documents. Which of the following would BEST allow the IT department to monitor and control this behavior?
A. Enabling AAA
B. Deploying a CASB
C. Configuring an NGFW
D. Installing a WAF
E. Utilizing a vTPM
A project manager is working with a team that is tasked to develop software applications in a structured environment and host them in a vendor's cloud-based infrastructure. The organization will maintain responsibility for the software but will not manage the underlying server applications. Which of the following does the organization plan to leverage?
A. SaaS
B. PaaS
C. IaaS
D. Hybrid cloud
E. Network virtualization
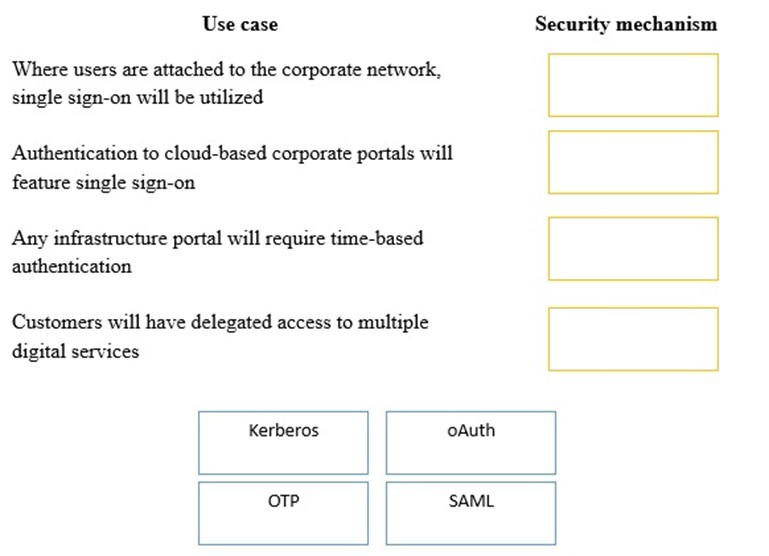
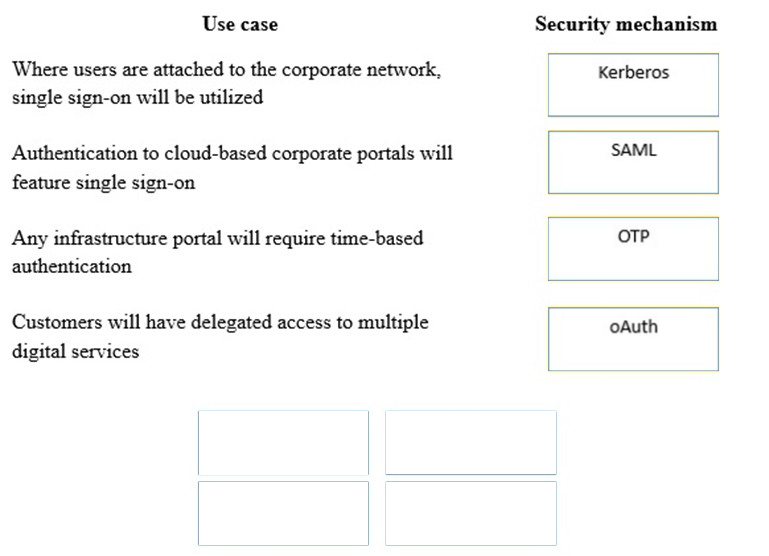
DRAG DROP - A security consultant is considering authentication options for a financial institution. The following authentication options are available. Drag and drop the security mechanism to the appropriate use case. Options may be used once. Select and Place:
The Chief Information Officer (CISO) is concerned that certain systems administrators will privileged access may be reading other users' emails. Review of a tool's output shows the administrators have used web mail to log into other users' inboxes. Which of the following tools would show this type of output?
A. Log analysis tool
B. Password cracker
C. Command-line tool
D. File integrity monitoring tool
A developer has executed code for a website that allows users to search for employees' phone numbers by last name. The query string sent by the browser is as follows: http://www.companywebsite.com/search.php?q=SMITH The developer has implemented a well-known JavaScript sanitization library and stored procedures, but a penetration test shows the website is vulnerable to XSS. Which of the following should the developer implement NEXT to prevent XSS? (Choose two.)
A. Sanitization library
B. Secure cookies
C. TLS encryption
D. Input serialization
E. Output encoding
F. PUT form submission
A security architect is determining the best solution for a new project. The project is developing a new intranet with advanced authentication capabilities, SSO for users, and automated provisioning to streamline Day 1 access to systems. The security architect has identified the following requirements: 1. Information should be sourced from the trusted master data source. 2. There must be future requirements for identity proofing of devices and users. 3. A generic identity connector that can be reused must be developed. 4. The current project scope is for internally hosted applications only. Which of the following solution building blocks should the security architect use to BEST meet the requirements?
A. LDAP, multifactor authentication, OAuth, XACML
B. AD, certificate-based authentication, Kerberos, SPML
C. SAML, context-aware authentication, OAuth, WAYF
D. NAC, radius, 802.1x, centralized active directory
A Chief Information Security Officer (CISO) of a large financial institution undergoing an IT transformation program wants to embed security across the business rapidly and across as many layers of the business as possible to achieve quick wins and reduce risk to the organization. Which of the following business areas should the CISO target FIRST to best meet the objective?
A. Programmers and developers should be targeted to ensure secure coding practices, including automated code reviews with remediation processes, are implemented immediately.
B. Human resources should be targeted to ensure all new employees undertake security awareness and compliance training to reduce the impact of phishing and ransomware attacks.
C. The project management office should be targeted to ensure security is managed and included at all levels of the project management cycle for new and in- flight projects.
D. Risk assurance teams should be targeted to help identify key business unit security risks that can be aggregated across the organization to produce a risk posture dashboard for executive management.
A security administrator is updating corporate policies to respond to an incident involving collusion between two systems administrators that went undetected for more than six months. Which of the following policies would have MOST likely uncovered the collusion sooner? (Choose two.)
A. Mandatory vacation
B. Separation of duties
C. Continuous monitoring
D. Incident response
E. Time-of-day restrictions
F. Job rotation
A software company is releasing a new mobile application to a broad set of external customers. Because the software company is rapidly releasing new features, it has built in an over-the-air software update process that can automatically update the application at launch time. Which of the following security controls should be recommended by the company's security architect to protect the integrity of the update process? (Choose two.)
A. Validate cryptographic signatures applied to software updates
B. Perform certificate pinning of the associated code signing key
C. Require HTTPS connections for downloads of software updates
D. Ensure there are multiple download mirrors for availability
E. Enforce a click-through process with user opt-in for new features
During a sprint, developers are responsible for ensuring the expected outcome of a change is thoroughly evaluated for any security impacts. Any impacts must be reported to the team lead. Before changes are made to the source code, which of the following MUST be performed to provide the required information to the team lead?
A. Risk assessment
B. Regression testing
C. User story development
D. Data abstraction
E. Business impact assessment
The Chief Information Security Officer (CISO) of an e-retailer, which has an established security department, identifies a customer who has been using a fraudulent credit card. The CISO calls the local authorities, and when they arrive on-site, the authorities ask a security engineer to create a point-in-time copy of the running database in their presence. This is an example of:
A. creating a forensic image
B. deploying fraud monitoring
C. following a chain of custody
D. analyzing the order of volatility
A security manager wants to implement a policy that will provide management with the ability to monitor employee's activities with minimum impact to productivity. Which of the following policies is BEST suited for this scenario?
A. Separation of duties
B. Mandatory vacations
C. Least privilege
D. Incident response
A user asks a security practitioner for recommendations on securing a home network. The user recently purchased a connected home assistant and multiple IoT devices in an effort to automate the home. Some of the IoT devices are wearables, and other are installed in the user's automobiles. The current home network is configured as a single flat network behind an ISP-supplied router. The router has a single IP address, and the router performs NAT on incoming traffic to route it to individual devices. Which of the following security controls would address the user's privacy concerns and provide the BEST level of security for the home network?
A. Ensure all IoT devices are configured in a geofencing mode so the devices do not work when removed from the home network. Disable the home assistant unless actively using it, and segment the network so each IoT device has its own segment.
B. Install a firewall capable of cryptographically separating network traffic, require strong authentication to access all IoT devices, and restrict network access for the home assistant based on time-of-day restrictions.
C. Segment the home network to separate network traffic from users and the IoT devices, ensure security settings on the home assistant support no or limited recording capability, and install firewall rules on the router to restrict traffic to the home assistant as much as possible.
D. Change all default passwords on the IoT devices, disable Internet access for the IoT devices and the home assistant, obtain routable IP addresses for all devices, and implement IPv6 and IPSec protections on all network traffic.
Company.org has requested a black-box security assessment be performed on key cyber terrain. One area of concern is the company's SMTP services. The security assessor wants to run reconnaissance before taking any additional action and wishes to determine which SMTP server is Internet-facing. Which of the following commands should the assessor use to determine this information?
A. dnsrecon ג€”d company.org ג€”t SOA
B. dig company.org mx
C. nc ג€”v company.org
D. whois company.org
A company has decided to replace all the T-1 uplinks at each regional office and move away from using the existing MPLS network. All regional sites will use high- speed connections and VPNs to connect back to the main campus. Which of the following devices would MOST likely be added at each location?
A. SIEM
B. IDS/IPS
C. Proxy server
D. Firewall
E. Router
A security administrator wants to implement controls to harden company-owned mobile devices. Company policy specifies the following requirements: ✑ Mandatory access control must be enforced by the OS. ✑ Devices must only use the mobile carrier data transport. Which of the following controls should the security administrator implement? (Choose three.)
A. Enable DLP
B. Enable SEAndroid
C. Enable EDR
D. Enable secure boot
E. Enable remote wipe
F. Disable Bluetooth
G. Disable 802.11
H. Disable geotagging
An analyst is investigating anomalous behavior on a corporate-owned, corporate-managed mobile device with application whitelisting enabled, based on a name string. The employee to whom the device is assigned reports the approved email client is displaying warning messages that can launch browser windows and is adding unrecognized email addresses to the `compose` window. Which of the following would provide the analyst the BEST chance of understanding and characterizing the malicious behavior?
A. Reverse engineer the application binary.
B. Perform static code analysis on the source code.
C. Analyze the device firmware via the JTAG interface.
D. Change to a whitelist that uses cryptographic hashing.
E. Penetration test the mobile application.
A development team releases updates to an application regularly. The application is compiled with several standard, open-source security products that require a minimum version for compatibility. During the security review portion of the development cycle, which of the following should be done to minimize possible application vulnerabilities?
A. The developers should require an exact version of the open-source security products, preventing the introduction of new vulnerabilities.
B. The application development team should move to an Agile development approach to identify security concerns faster.
C. The change logs for the third-party libraries should be reviewed for security patches, which may need to be included in the release
D. The application should eliminate the use of open-source libraries and products to prevent known vulnerabilities from being included
A security analyst has requested network engineers integrate sFlow into the SOC's overall monitoring picture. For this to be a useful addition to the monitoring capabilities, which of the following must be considered by the engineering team?
A. Effective deployment of network taps
B. Overall bandwidth available at Internet PoP
C. Optimal placement of log aggregators
D. Availability of application layer visualizers
An incident responder wants to capture volatile memory comprehensively from a running machine for forensic purposes. The machine is running a very recent release of the Linux OS. Which of the following technical approaches would be the MOST feasible way to accomplish this capture?
A. Run the memdump utility with the -k flag.
B. Use a loadable kernel module capture utility, such as LiME.
C. Run dd on/dev/mem.
D. Employ a stand-alone utility, such as FTK Imager.
A company is developing requirements for a customized OS build that will be used in an embedded environment. The company procured hardware that is capable of reducing the likelihood of successful buffer overruns while executables are processing. Which of the following capabilities must be included for the OS to take advantage of this critical hardware-based countermeasure?
A. Application whitelisting
B. NX/XN bit
C. ASLR
D. TrustZone
E. SCP
An organization is improving its web services to enable better customer engagement and self-service. The organization has a native mobile application and a rewards portal provided by a third party. The business wants to provide customers with the ability to log in once and have SSO between each of the applications. The integrity of the identity is important so it can be propagated through to back-end systems to maintain a consistent audit trail. Which of the following authentication and authorization types BEST meet the requirements? (Choose two.)
A. SAML
B. Social login
C. OpenID connect
D. XACML
E. SPML
F. OAuth
An organization is evaluating options related to moving organizational assets to a cloud-based environment using an IaaS provider. One engineer has suggested connecting a second cloud environment within the organization's existing facilities to capitalize on available datacenter space and resources. Other project team members are concerned about such a commitment of organizational assets, and ask the Chief Security Officer (CSO) for input. The CSO explains that the project team should work with the engineer to evaluate the risks associated with using the datacenter to implement:
A. a hybrid cloud.
B. an on-premises private cloud.
C. a hosted hybrid cloud.
D. a private cloud.
After a large organization has completed the acquisition of a smaller company, the smaller company must implement new host-based security controls to connect its employees' devices to the network. Given that the network requires 802.1X EAP-PEAP to identify and authenticate devices, which of the following should the security administrator do to integrate the new employees' devices into the network securely?
A. Distribute a NAC client and use the client to push the company’s private key to all the new devices.
B. Distribute the device connection policy and a unique public/private key pair to each new employee’s device.
C. Install a self-signed SSL certificate on the company’s RADIUS server and distribute the certificate’s public key to all new client devices.
D. Install an 802.1X supplicant on all new devices and let each device generate a self-signed certificate to use for network access.
A company is acquiring incident response and forensic assistance from a managed security service provider in the event of a data breach. The company has selected a partner and must now provide required documents to be reviewed and evaluated. Which of the following documents would BEST protect the company and ensure timely assistance? (Choose two.)
A. RA
B. BIA
C. NDA
D. RFI
E. RFQ
F. MSA
While conducting a BIA for a proposed acquisition, the IT integration team found that both companies outsource CRM services to competing and incompatible third-party cloud services. The decision has been made to bring the CRM service in-house, and the IT team has chosen a future solution. With which of the following should the Chief Information Security Officer (CISO) be MOST concerned? (Choose two.)
A. Data remnants
B. Sovereignty
C. Compatible services
D. Storage encryption
E. Data migration
F. Chain of custody
A security technician is incorporating the following requirements in an RFP for a new SIEM: ✑ New security notifications must be dynamically implemented by the SIEM engine ✑ The SIEM must be able to identify traffic baseline anomalies ✑ Anonymous attack data from all customers must augment attack detection and risk scoring Based on the above requirements, which of the following should the SIEM support? (Choose two.)
A. Autoscaling search capability
B. Machine learning
C. Multisensor deployment
D. Big Data analytics
E. Cloud-based management
F. Centralized log aggregation
A company contracts a security consultant to perform a remote white-box penetration test. The company wants the consultant to focus on Internet-facing services without negatively impacting production services. Which of the following is the consultant MOST likely to use to identify the company's attack surface? (Choose two.)
A. Web crawler
B. WHOIS registry
C. DNS records
D. Company’s firewall ACL
E. Internal routing tables
F. Directory service queries
Given the following output from a security tool in Kali:
A. Log reduction
B. Network enumerator
C. Fuzzer
D. SCAP scanner
Access Full CAS-003 Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete CAS-003 Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our CAS-003 mock test free today—and take a major step toward exam success!