CAS-003 Exam Prep Free – 50 Practice Questions to Get You Ready for Exam Day
Getting ready for the CAS-003 certification? Our CAS-003 Exam Prep Free resource includes 50 exam-style questions designed to help you practice effectively and feel confident on test day
Effective CAS-003 exam prep free is the key to success. With our free practice questions, you can:
- Get familiar with exam format and question style
- Identify which topics you’ve mastered—and which need more review
- Boost your confidence and reduce exam anxiety
Below, you will find 50 realistic CAS-003 Exam Prep Free questions that cover key exam topics. These questions are designed to reflect the structure and challenge level of the actual exam, making them perfect for your study routine.
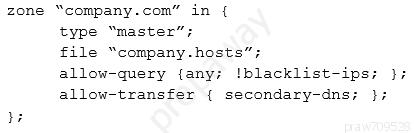
A security engineer is assisting a developer with input validation, and they are studying the following code block:The security engineer wants to ensure strong input validation is in place for customer-provided account identifiers. These identifiers are ten-digit numbers. The developer wants to ensure input validation is fast because a large number of people use the system. Which of the following would be the BEST advice for the security engineer to give to the developer?
A. Replace code with Java-based type checks
B. Parse input into an array
C. Use regular expressions
D. Canonicalize input into string objects before validation
A security incident responder discovers an attacker has gained access to a network and has overwritten key system files with backdoor software. The server was reimaged and patched offline. Which of the following tools should be implemented to detect similar attacks?
A. Vulnerability scanner
B. TPM
C. Host-based firewall
D. File integrity monitor
E. NIPS
A security engineer is embedded with a development team to ensure security is built into products being developed. The security engineer wants to ensure developers are not blocked by a large number of security requirements applied at specific schedule points. Which of the following solutions BEST meets the engineer's goal?
A. Schedule weekly reviews of al unit test results with the entire development team and follow up between meetings with surprise code inspections.
B. Develop and implement a set of automated security tests to be installed on each development team leader’s workstation.
C. Enforce code quality and reuse standards into the requirements definition phase of the waterfall development process.
D. Deploy an integrated software tool that builds and tests each portion of code committed by developers and provides feedback.
The security administrator of a small firm wants to stay current on the latest security vulnerabilities and attack vectors being used by crime syndicates and nation- states. The information must be actionable and reliable. Which of the following would BEST meet the needs of the security administrator?
A. Software vendor threat reports
B. White papers
C. Security blogs
D. Threat data subscription
A Chief Information Security Officer (CISO) recently changed jobs into a new industry. The CISO's first task is to write a new, relevant risk assessment for the organization. Which of the following would BEST help the CISO find relevant risks to the organization? (Choose two.)
A. Perform a penetration test.
B. Conduct a regulatory audit.
C. Hire a third-party consultant.
D. Define the threat model.
E. Review the existing BIA.
F. Perform an attack path analysis.
An organization is reviewing endpoint security solutions. In evaluating products, the organization has the following requirements: 1. Support server, laptop, and desktop infrastructure 2. Due to limited security resources, implement active protection capabilities 3. Provide users with the ability to self-service classify information and apply policies 4. Protect data-at-rest and data-in-use Which of the following endpoint capabilities would BEST meet the above requirements? (Choose two.)
A. Data loss prevention
B. Application whitelisting
C. Endpoint detect and respond
D. Rights management
E. Log monitoring
F. Antivirus
A project manager is working with a team that is tasked to develop software applications in a structured environment and host them in a vendor's cloud-based infrastructure. The organization will maintain responsibility for the software but will not manage the underlying server applications. Which of the following does the organization plan to leverage?
A. SaaS
B. PaaS
C. IaaS
D. Hybrid cloud
E. Network virtualization
A software company is releasing a new mobile application to a broad set of external customers. Because the software company is rapidly releasing new features, it has built in an over-the-air software update process that can automatically update the application at launch time. Which of the following security controls should be recommended by the company's security architect to protect the integrity of the update process? (Choose two.)
A. Validate cryptographic signatures applied to software updates
B. Perform certificate pinning of the associated code signing key
C. Require HTTPS connections for downloads of software updates
D. Ensure there are multiple download mirrors for availability
E. Enforce a click-through process with user opt-in for new features
Given the following output from a security tool in Kali:
A. Log reduction
B. Network enumerator
C. Fuzzer
D. SCAP scanner
An organization is currently working with a client to migrate data between a legacy ERP system and a cloud-based ERP tool using a global PaaS provider. As part of the engagement, the organization is performing data deduplication and sanitization of client data to ensure compliance with regulatory requirements. Which of the following is the MOST likely reason for the need to sanitize the client data?
A. Data aggregation
B. Data sovereignty
C. Data isolation
D. Data volume
E. Data analytics
As part of incident response, a technician is taking an image of a compromised system and copying the image to a remote image server (192.168.45.82). The system drive is very large but does not contain the sensitive data. The technician has limited time to complete this task. Which of the following is the BEST command for the technician to run?
A. tar cvf – / | ssh 192.168.45.82 ג€cat – > /images/image.tarג€
B. dd if=/dev/mem | scp – 192.168.45.82:/images/image.dd
C. memdump /dev/sda1 | nc 192.168.45.82 3000
D. dd if=/dev/sda | nc 192.168.45.82 3000
The government is concerned with remote military missions being negatively impacted by the use of technology that may fail to protect operational security. To remediate this concern, a number of solutions have been implemented, including the following: ✑ End-to-end encryption of all inbound and outbound communication, including personal email and chat sessions that allow soldiers to securely communicate with families. ✑ Layer 7 inspection and TCP/UDP port restriction, including firewall rules to only allow TCP port 80 and 443 and approved applications ✑ A host-based whitelist of approved websites and applications that only allow mission-related tools and sites ✑ The use of satellite communication to include multiple proxy servers to scramble the source IP address Which of the following is of MOST concern in this scenario?
A. The unsecure port 80 being used for general web traffic
B. Family members posting geotagged images on social media that were received via email from soldiers
C. The effect of communication latency that may negatively impact real-time communication with mission control
D. The use of centrally managed military network and computers by soldiers when communicating with external parties
Following a recent outage, a systems administrator is conducting a study to determine a suitable bench stock on server hard drives. Which of the following metrics is MOST valuable to the administrator in determining how many hard drives to keep-on hand?
A. TTR
B. ALE
C. MTBF
D. SLE
E. RPO
A company contracts a security consultant to perform a remote white-box penetration test. The company wants the consultant to focus on Internet-facing services without negatively impacting production services. Which of the following is the consultant MOST likely to use to identify the company's attack surface? (Choose two.)
A. Web crawler
B. WHOIS registry
C. DNS records
D. Company’s firewall ACL
E. Internal routing tables
F. Directory service queries
An organization's network engineering team recently deployed a new software encryption solution to ensure the confidentiality of data at rest, which was found to add 300ms of latency to data read-write requests in storage, impacting business operations. Which of the following alternative approaches would BEST address performance requirements while meeting the intended security objective?
A. Employ hardware FDE or SED solutions.
B. Utilize a more efficient cryptographic hash function.
C. Replace HDDs with SSD arrays.
D. Use a FIFO pipe a multithreaded software solution.
A security tester is performing a black-box assessment of an RFID access control system. The tester has a handful of RFID tags and is able to access the reader. However, the tester cannot disassemble the reader because it is in use by the company. Which of the following shows the steps the tester should take to assess the RFID access control system in the correct order?
A. 1. Attempt to eavesdrop and replay RFID communications. 2. Determine the protocols being used between the tag and the reader. 3. Retrieve the RFID tag identifier and manufacturer details. 4. Take apart an RFID tag and analyze the chip.
B. 1. Determine the protocols being used between the tag and the reader. 2. Take apart an RFID tag and analyze the chip. 3. Retrieve the RFID tag identifier and manufacturer details. 4. Attempt to eavesdrop and replay RFID communications.
C. 1. Retrieve the RFID tag identifier and manufacturer details. 2. Determine the protocols is being used between the tag and the reader. 3. Attempt to eavesdrop and replay RFID communications. 4. Take apart an RFID tag and analyze the chip.
D. 1. Take apart an RFID tag and analyze the chip. 2. Retrieve the RFID tag identifier and manufacturer details. 3. Determine the protocols being used between the tag and the reader. 4. Attempt to eavesdrop and replay RFID communications.
The Chief Information Security Officer (CISO) suspects that a database administrator has been tampering with financial data to the administrator's advantage. Which of the following would allow a third-party consultant to conduct an on-site review of the administrator's activity?
A. Separation of duties
B. Job rotation
C. Continuous monitoring
D. Mandatory vacation
A penetration test is being scoped for a set of web services with API endpoints. The APIs will be hosted on existing web application servers. Some of the new APIs will be available to unauthenticated users, but some will only be available to authenticated users. Which of the following tools or activities would the penetration tester MOST likely use or do during the engagement? (Choose two.)
A. Static code analyzer
B. Intercepting proxy
C. Port scanner
D. Reverse engineering
E. Reconnaissance gathering
F. User acceptance testing
A security manager needed to protect a high-security data center, so the manager installed a mantrap that can detect an employee's heartbeat, weight, and badge. Which of the following did the security manager implement?
A. A physical control
B. A corrective control
C. A compensating control
D. A managerial control
A security engineer is deploying an IdP to broker authentication between applications. These applications all utilize SAML 2.0 for authentication. Users log into the IdP with their credentials and are given a list of applications they may access. One of the application's authentications is not functional when a user initiates an authentication attempt from the IdP. The engineer modifies the configuration so users browse to the application first, which corrects the issue. Which of the following BEST describes the root cause?
A. The application only supports SP-initiated authentication.
B. The IdP only supports SAML 1.0
C. There is an SSL certificate mismatch between the IdP and the SaaS application.
D. The user is not provisioned correctly on the IdP.
A network service on a production system keeps crashing at random times. The systems administrator suspects a bug in the listener is causing the service to crash, resulting in a DoS. When the service crashes, a core dump is left in the /tmp directory. Which of the following tools can the systems administrator use to reproduce these symptoms?
A. Fuzzer
B. Vulnerability scanner
C. Core dump analyzer
D. Debugger
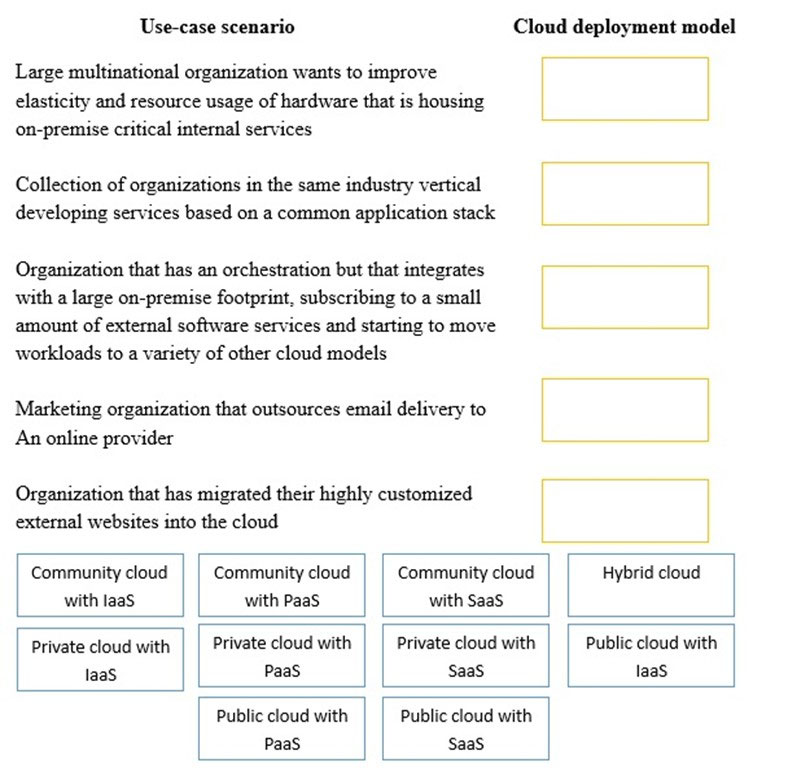
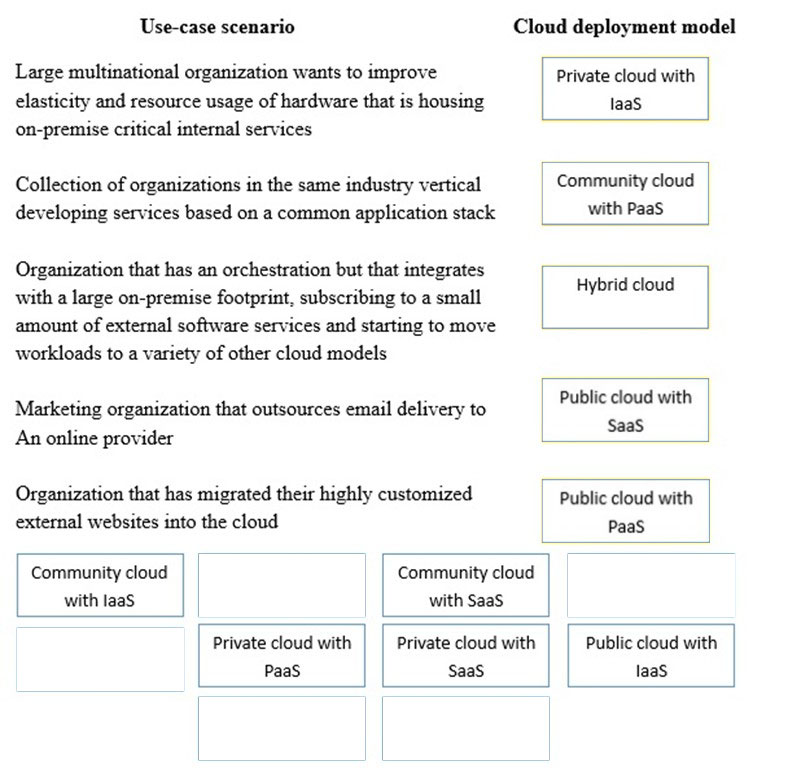
DRAG DROP - Drag and drop the cloud deployment model to the associated use-case scenario. Options may be used only once or not at all. Select and Place:
A security administrator is troubleshooting RADIUS authentication issues from a newly implemented controller-based wireless deployment. The RADIUS server contains the following information in its logs:Based on this information, the administrator reconfigures the RADIUS server, which results in the following log data:
To correct this error message, the administrator makes an additional change to the RADIUS server. Which of the following did the administrator reconfigure on the RADIUS server? (Choose two.)
A. Added the controller address as an authorized client
B. Registered the RADIUS server to the wireless controller
C. Corrected a mismatched shared secret
D. Renewed the expired client certificate
E. Reassigned the RADIUS policy to the controller
F. Modified the client authentication method
A manufacturing company recently recovered from an attack on its ICS devices. It has since reduced the attack surface by isolating the affected components. The company now wants to implement detection capabilities. It is considering a system that is based on machine learning. Which of the following features would BEST describe the driver to adopt such nascent technology over mainstream commercial IDSs?
A. Trains on normal behavior and identifies deviations therefrom
B. Identifies and triggers upon known bad signatures and behaviors
C. Classifies traffic based on logical protocols and messaging formats
D. Automatically reconfigures ICS devices based on observed behavior
A forensic analyst suspects that a buffer overflow exists in a kernel module. The analyst executes the following command:However, the analyst is unable to find any evidence of the running shell. Which of the following of the MOST likely reason the analyst cannot find a process ID for the shell?
A. The NX bit is enabled
B. The system uses ASLR
C. The shell is obfuscated
D. The code uses dynamic libraries
A company's Chief Operating Officer (COO) is concerned about the potential for competitors to infer proprietary information gathered from employees' social media accounts. Which of the following methods should the company use to gauge its own social media threat level without targeting individual employees?
A. Utilize insider threat consultants to provide expertise.
B. Require that employees divulge social media accounts.
C. Leverage Big Data analytical algorithms.
D. Perform social engineering tests to evaluate employee awareness.
A systems security engineer is assisting an organization's market survey team in reviewing requirements for an upcoming acquisition of mobile devices. The engineer expresses concerns to the survey team about a particular class of devices that uses a separate SoC for baseband radio I/O. For which of the following reasons is the engineer concerned?
A. These devices can communicate over networks older than HSPA+ and LTE standards, exposing device communications to poor encryptions routines
B. The organization will be unable to restrict the use of NFC, electromagnetic induction, and Bluetooth technologies
C. The associated firmware is more likely to remain out of date and potentially vulnerable
D. The manufacturers of the baseband radios are unable to enforce mandatory access controls within their driver set
An information security officer reviews a report and notices a steady increase in outbound network traffic over the past ten months. There is no clear explanation for the increase. The security officer interviews several business units and discovers an unsanctioned cloud storage provider was used to share marketing materials with potential customers. Which of the following services would be BEST for the security officer to recommend to the company?
A. NIDS
B. HIPS
C. CASB
D. SFTP
A penetration tester has been contracted to conduct a physical assessment of a site. Which of the following is the MOST plausible method of social engineering to be conducted during this engagement?
A. Randomly calling customer employees and posing as a help desk technician requiring user password to resolve issues
B. Posing as a copier service technician and indicating the equipment had ג€phoned homeג€ to alert the technician for a service call
C. Simulating an illness while at a client location for a sales call and then recovering once listening devices are installed
D. Obtaining fake government credentials and impersonating law enforcement to gain access to a company facility
An internal penetration tester was assessing a recruiting page for potential issues before it was pushed to the production website. The penetration tester discovers an issue that must be corrected before the page goes live. The web host administrator collects the log files below and gives them to the development team so improvements can be made to the security design of the website.Which of the following types of attack vectors did the penetration tester use?
A. SQL injection
B. CSRF
C. Brute force
D. XSS
E. TOC/TOU
A legacy web application, which is being used by a hospital, cannot be upgraded for 12 months. A new vulnerability is found in the legacy application, and the networking team is tasked with mitigation. Middleware for mitigation will cost $100,000 per year. Which of the following must be calculated to determine ROI? (Choose two.)
A. ALE
B. RTO
C. MTBF
D. ARO
E. RPO
A security engineer is investigating a compromise that occurred between two internal computers. The engineer has determined during the investigation that one computer infected another. While reviewing the IDS logs, the engineer can view the outbound callback traffic, but sees no traffic between the two computers. Which of the following would BEST address the IDS visibility gap?
A. Install network taps at the edge of the network.
B. Send syslog from the IDS into the SIEM.
C. Install HIDS on each computer.
D. SPAN traffic form the network core into the IDS.
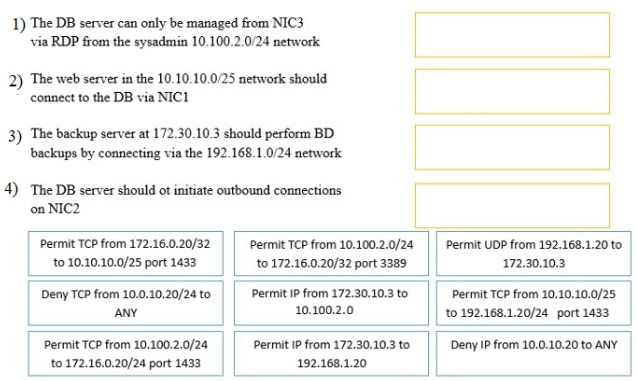
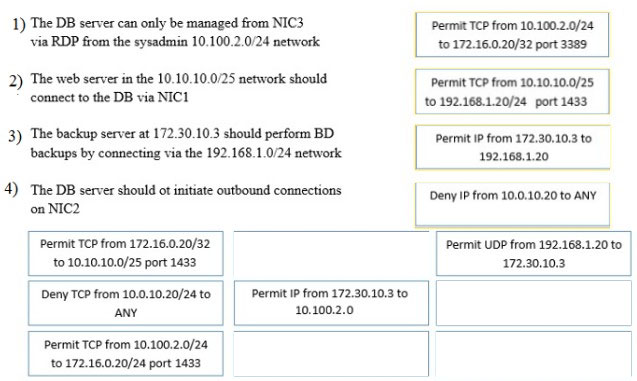
DRAG DROP - A security administrator must configure the database server shown below to comply with the four requirements listed. Drag and drop the appropriate ACL that should be configured on the database server to its corresponding requirement. Answer options may be used once or not at all.Select and Place:
A company has gone through a round of phishing attacks. More than 200 users have had their workstation infected because they clicked on a link in an email. An incident analysis has determined an executable ran and compromised the administrator account on each workstation. Management is demanding the information security team prevent this from happening again. Which of the following would BEST prevent this from happening again?
A. Antivirus
B. Patch management
C. Log monitoring
D. Application whitelisting
E. Awareness training
A systems analyst is concerned that the current authentication system may not provide the appropriate level of security. The company has integrated WAYF within its federation system and implemented a mandatory two-step authentication system. Some accounts are still becoming compromised via phishing attacks that redirect users to a fake portal, which is automatically collecting and replaying the stolen credentials. Which of the following is a technical solution that would BEST reduce the risk of similar compromises?
A. Security awareness training
B. Push-based authentication
C. Software-based TOTP
D. OAuth tokens
E. Shibboleth
An engineer maintains a corporate-owned mobility infrastructure, and the organization requires that all web browsing using corporate-owned resources be monitored. Which of the following would allow the organization to meet its requirement? (Choose two.)
A. Exempt mobile devices from the requirement, as this will lead to privacy violations
B. Configure the devices to use an always-on IPSec VPN
C. Configure all management traffic to be tunneled into the enterprise via TLS
D. Implement a VDI solution and deploy supporting client apps to devices
E. Restrict application permissions to establish only HTTPS connections outside of the enterprise boundary
A security consultant was hired to audit a company's password are account policy. The company implements the following controls: ✑ Minimum password length: 16 ✑ Maximum password age: 0 ✑ Minimum password age: 0 ✑ Password complexity: disabled ✑ Store passwords in plain text: disabled ✑ Failed attempts lockout: 3 ✑ Lockout timeout: 1 hour The password database uses salted hashes and PBKDF2. Which of the following is MOST likely to yield the greatest number of plain text passwords in the shortest amount of time?
A. Offline hybrid dictionary attack
B. Offline brute-force attack
C. Online hybrid dictionary password spraying attack
D. Rainbow table attack
E. Online brute-force attack
F. Pass-the-hash attack
A security engineer is assessing the controls that are in place to secure the corporate-Internet-facing DNS server. The engineer notices that security ACLs exist but are not being used properly. The DNS server should respond to any source but only provide information about domains it has authority over. Additionally, the DNS administrator have identified some problematic IP addresses that should not be able to make DNS requests. Given the ACLs below:Which of the following should the security administrator configure to meet the DNS security needs? A.
B.
C.
D.
A threat advisory alert was just emailed to the IT security staff. The alert references specific types of host operating systems that can allow an unauthorized person to access files on a system remotely. A fix was recently published, but it requires a recent endpoint protection engine to be installed prior to running the fix. Which of the following MOST likely need to be configured to ensure the system are mitigated accordingly? (Choose two.)
A. Antivirus
B. HIPS
C. Application whitelisting
D. Patch management
E. Group policy implementation
F. Firmware updates
An engineer is reviewing the security architecture for an enterprise network. During the review, the engineer notices an undocumented node on the network. Which of the following approaches can be utilized to determine how this node operates? (Choose two.)
A. Use reverse engineering and techniques
B. Assess the node within a continuous integration environment
C. Employ a static code analyzer
D. Review network and traffic logs
E. Use a penetration testing framework to analyze the node
F. Analyze the output of a ping sweep
A company has made it a spending priority to implement security architectures that will be resilient during an attack. Recent incidents have involved attackers leveraging latent vulnerabilities in cryptographic implementations and VPN concentrators to be able to compromise sensitive information. Patches have been slowly released for these emergent vulnerabilities, leaving weeks to months of exposed and vulnerable attack surface. Which of the following approaches would be BEST to increase enterprise resilience during similar future attacks?
A. Implement appliances and software from diverse manufacturers
B. Segment remote VPN users logically from the production LAN
C. Maximize open-source software to benefit from swifter patch releases
D. Upgrade the cryptographic ciphers used on the VPN concentrators
A company relies on an ICS to perform equipment monitoring functions that are federally mandated for operation of the facility. Fines for non-compliance could be costly. The ICS has known vulnerabilities and can no longer be patched or updated. Cyber-liability insurance cannot be obtained because insurance companies will not insure this equipment. Which of the following would be the BEST option to manage this risk to the company's production environment?
A. Avoid the risk by removing the ICS from production
B. Transfer the risk associated with the ICS vulnerabilities
C. Mitigate the risk by restricting access to the ICS
D. Accept the risk and upgrade the ICS when possible
An engineer is evaluating the control profile to assign to a system containing PII, financial, and proprietary data.Based on the data classification table above, which of the following BEST describes the overall classification?
A. High confidentiality, high availability
B. High confidentiality, medium availability
C. Low availability, low confidentiality
D. High integrity, low availability
A company that has been breached multiple times is looking to protect cardholder data. The previous undetected attacks all mimicked normal administrative-type behavior. The company must deploy a host solution to meet the following requirements: ✑ Detect administrative actions ✑ Block unwanted MD5 hashes ✑ Provide alerts ✑ Stop exfiltration of cardholder data Which of the following solutions would BEST meet these requirements? (Choose two.)
A. AV
B. EDR
C. HIDS
D. DLP
E. HIPS
F. EFS
An incident responder wants to capture volatile memory comprehensively from a running machine for forensic purposes. The machine is running a very recent release of the Linux OS. Which of the following technical approaches would be the MOST feasible way to accomplish this capture?
A. Run the memdump utility with the -k flag.
B. Use a loadable kernel module capture utility, such as LiME.
C. Run dd on/dev/mem.
D. Employ a stand-alone utility, such as FTK Imager.
An attacker has been compromising banking institution targets across a regional area. The Chief Information Security Officer (CISO) at a local bank wants to detect and prevent an attack before the bank becomes a victim. Which of the following actions should the CISO take?
A. Utilize cloud-based threat analytics to identify anomalous behavior in the company’s B2B and vendor traffic
B. Purchase a CASB solution to identify and control access to cloud-based applications and services and integrate them with on-premises legacy security monitoring
C. Instruct a security engineer to configure the IDS to consume threat intelligence feeds from an information-sharing association in the banking sector
D. Attend and present at the regional banking association lobbying group meetings each month and facilitate a discussion on the topic
Ann, a user, brings her laptop to an analyst after noticing it has been operating very slowly. The security analyst examines the laptop and obtains the following output:Which of the following will the analyst most likely use NEXT?
A. Process explorer
B. Vulnerability scanner
C. Antivirus
D. Network enumerator
While investigating suspicious activity on a server, a security administrator runs the following report:In addition, the administrator notices changes to the /etc/shadow file that were not listed in the report. Which of the following BEST describe this scenario? (Choose two.)
A. An attacker compromised the server and may have used a collision hash in the MD5 algorithm to hide the changes to the /etc/shadow file
B. An attacker compromised the server and may have also compromised the file integrity database to hide the changes to the /etc/shadow file
C. An attacker compromised the server and may have installed a rootkit to always generate valid MD5 hashes to hide the changes to the /etc/shadow file
D. An attacker compromised the server and may have used MD5 collision hashes to generate valid passwords, allowing further access to administrator accounts on the server
E. An attacker compromised the server and may have used SELinux mandatory access controls to hide the changes to the /etc/shadow file
A security engineer must establish a method to assess compliance with company security policies as they apply to the unique configuration of individual endpoints, as well as to the shared configuration policies of common devices.Which of the following tools is the security engineer using to produce the above output?
A. Vulnerability scanner
B. SIEM
C. Port scanner
D. SCAP scanner
A SaaS provider decides to offer data storage as a service. For simplicity, the company wants to make the service available over industry standard APIs, routable over the public Internet. Which of the following controls offers the MOST protection to the company and its customer's information?
A. Detailed application logging
B. Use of non-standard ports
C. Web application firewall
D. Multifactor authentication
Access Full CAS-003 Exam Prep Free
Want to go beyond these 50 questions? Click here to unlock a full set of CAS-003 exam prep free questions covering every domain tested on the exam.
We continuously update our content to ensure you have the most current and effective prep materials.
Good luck with your CAS-003 certification journey!