CAS-003 Dump Free – 50 Practice Questions to Sharpen Your Exam Readiness.
Looking for a reliable way to prepare for your CAS-003 certification? Our CAS-003 Dump Free includes 50 exam-style practice questions designed to reflect real test scenarios—helping you study smarter and pass with confidence.
Using an CAS-003 dump free set of questions can give you an edge in your exam prep by helping you:
- Understand the format and types of questions you’ll face
- Pinpoint weak areas and focus your study efforts
- Boost your confidence with realistic question practice
Below, you will find 50 free questions from our CAS-003 Dump Free collection. These cover key topics and are structured to simulate the difficulty level of the real exam, making them a valuable tool for review or final prep.
A security analyst is trying to identify the source of a recent data loss incident. The analyst has reviewed all the logs for the time surrounding the incident and identified all the assets on the network at the time of the data loss. The analyst suspects the key to finding the source was obfuscated in an application. Which of the following tools should the analyst use NEXT?
A. Software decompiler
B. Network enumerator
C. Log reduction and analysis tool
D. Static code analysis
The SOC is reviewing processes and procedures after a recent incident. The review indicates it took more than 30 minutes to determine that quarantining an infected host was the best course of action. This allowed the malware to spread to additional hosts before it was contained. Which of the following would BEST to improve the incident response process?
A. Updating the playbook with better decision points
B. Dividing the network into trusted and untrusted zones
C. Providing additional end-user training on acceptable use
D. Implementing manual quarantining of infected hosts
A networking administrator was recently promoted to security administrator in an organization that handles highly sensitive data. The Chief Information Security Officer (CISO) has just asked for all IT security personnel to review a zero-day vulnerability and exploit for specific application servers to help mitigate the organization's exposure to that risk. Which of the following should the new security administrator review to gain more information? (Choose three.)
A. CVE database
B. Recent security industry conferences
C. Security vendor pages
D. Known vendor threat models
E. Secure routing metrics
F. Server’s vendor documentation
G. Verified security forums
H. NetFlow analytics
Following a recent data breach, a company has hired a new Chief Information Security Officer (CISO). The CISO is very concerned about the response time to the previous breach and wishes to know how the security team expects to react to a future attack. Which of the following is the BEST method to achieve this goal while minimizing disruption?
A. Perform a black box assessment
B. Hire an external red team audit
C. Conduct a tabletop exercise.
D. Recreate the previous breach.
E. Conduct an external vulnerability assessment.
After analyzing code, two developers at a company bring these samples to the security operations manager:Which of the following would BEST solve these coding problems?
A. Use a privileged access management system
B. Prompt the administrator for the password
C. Use salted hashes with PBKDF2
D. Increase the complexity and length of the password
A manufacturing company recently recovered from an attack on its ICS devices. It has since reduced the attack surface by isolating the affected components. The company now wants to implement detection capabilities. It is considering a system that is based on machine learning. Which of the following features would BEST describe the driver to adopt such nascent technology over mainstream commercial IDSs?
A. Trains on normal behavior and identifies deviations therefrom
B. Identifies and triggers upon known bad signatures and behaviors
C. Classifies traffic based on logical protocols and messaging formats
D. Automatically reconfigures ICS devices based on observed behavior
A request has been approved for a vendor to access a new internal server using only HTTPS and SSH to manage the back-end system for the portal. Internal users just need HTTP and HTTPS access to all internal web servers. All other external access to the new server and its subnet is not allowed. The security manager must ensure proper access is configured.Below is a snippet from the firewall related to that server (access is provided in a top-down model):
Which of the following lines should be configured to allow the proper access? (Choose two.)
A. Move line 3 below line 4 and change port 80 to 443 on line 4.
B. Move line 3 below line 4 and add port 443 to line.
C. Move line 4 below line 5 and add port 80 to 8080 on line 2.
D. Add port 22 to line 2.
E. Add port 22 to line 5.
F. Add port 443 to line 2.
G. Add port 443 to line 5.
The email administrator must reduce the number of phishing emails by utilizing more appropriate security controls. The following configurations already are in place: ✑ Keyword blocking based on word lists ✑ URL rewriting and protection ✑ Stripping executable files from messages Which of the following is the BEST configuration change for the administrator to make?
A. Configure more robust word lists for blocking suspicious emails.
B. Configure appropriate regular expression rules per suspicious email received.
C. Configure Bayesian filtering to block suspicious inbound email.
D. Configure the mail gateway to strip any attachments.
The results of an external penetration test for a software development company show a small number of applications account for the largest number of findings. While analyzing the content and purpose of the applications, the following matrix is created:The findings are then categorized according to the following chart:
Which of the following would BEST reduce the amount of immediate risk incurred by the organization from a compliance and legal standpoint? (Choose two.)
A. Place a WAF in line with Application 2
B. Move Application 3 to a secure VLAN and require employees to use a jump server for access
C. Apply the missing OS and software patches to the server hosting Application 4
D. Use network segmentation and ACLs to control access to Application 5
E. Implement an IDS/IPS on the same network segment as Application 3
F. Install a FIM on the server hosting Application 4
G. Enforce Group Policy password complexity rules on the server hosting Application 1
An organization is currently working with a client to migrate data between a legacy ERP system and a cloud-based ERP tool using a global PaaS provider. As part of the engagement, the organization is performing data deduplication and sanitization of client data to ensure compliance with regulatory requirements. Which of the following is the MOST likely reason for the need to sanitize the client data? (Choose two.)
A. Data aggregation
B. Data sovereignty
C. Data isolation
D. Data volume
E. Data analytics
F. Data precision
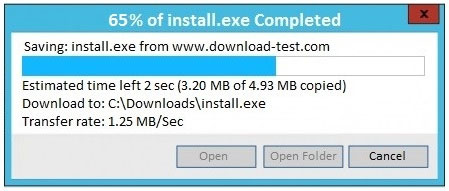
SIMULATION - An administrator wants to install a patch to an application. INSTRUCTIONS - Given the scenario, download, verify, and install the patch in the most secure manner. The last install that is completed will be the final submission. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
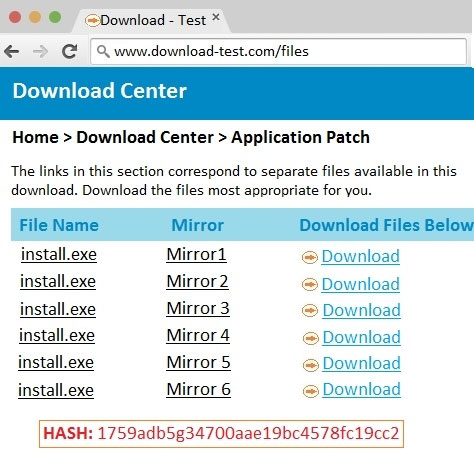
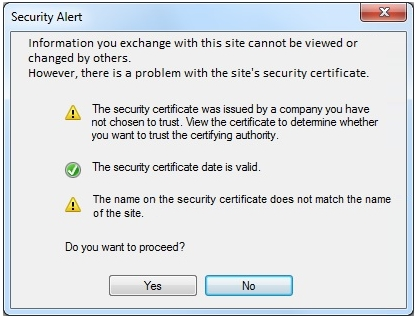
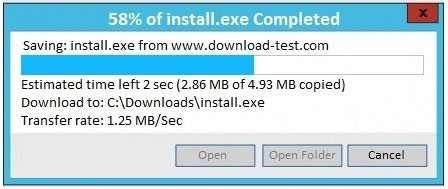
A security analyst is reviewing the following packet capture of communication between a host and a company's router:Which of the following actions should the security analyst take to remove this vulnerability?
A. Update the router code
B. Implement a router ACL
C. Disconnect the host from the network
D. Install the latest antivirus definitions
E. Deploy a network-based IPS
An infrastructure team is at the end of a procurement process and has selected a vendor. As part of the final negotiation, there are a number of outstanding issues, including: 1. Indemnity clauses have identified the maximum liability. 2. The data will be hosted and managed outside of the company's geographical location. The number of users accessing the system will be small, and no sensitive data will be hosted in the solution. As the security consultant of the project, which of the following should the project's security consultant recommend as the NEXT step?
A. Develop a security exemption, as it does not meet the security policies.
B. Require the solution owner to accept the identified risks and consequences.
C. Mitigate the risk by asking the vendor to accept the in-country privacy principles.
D. Review the procurement process to determine the lessons learned.
A company's user community is being adversely affected by various types of emails whose authenticity cannot be trusted. The Chief Information Security Officer (CISO) must address the problem. Which of the following solutions would BEST support trustworthy communication solutions?
A. Enabling spam filtering and DMARC.
B. Using MFA when logging into email clients and the domain.
C. Enforcing HTTPS everywhere so web traffic, including email, is secure.
D. Enabling SPF and DKIM on company servers.
E. Enforcing data classification labels before an email is sent to an outside party.
A security engineer is deploying an IdP to broker authentication between applications. These applications all utilize SAML 2.0 for authentication. Users log into the IdP with their credentials and are given a list of applications they may access. One of the application's authentications is not functional when a user initiates an authentication attempt from the IdP. The engineer modifies the configuration so users browse to the application first, which corrects the issue. Which of the following BEST describes the root cause?
A. The application only supports SP-initiated authentication.
B. The IdP only supports SAML 1.0
C. There is an SSL certificate mismatch between the IdP and the SaaS application.
D. The user is not provisioned correctly on the IdP.
After multiple service interruptions caused by an older datacenter design, a company decided to migrate away from its datacenter. The company has successfully completed the migration of all datacenter servers and services to a cloud provider. The migration project includes the following phases: ✑ Selection of a cloud provider ✑ Architectural design ✑ Microservice segmentation ✑ Virtual private cloud ✑ Geographic service redundancy ✑ Service migration The Chief Information Security Officer (CISO) is still concerned with the availability requirements of critical company applications. Which of the following should the company implement NEXT?
A. Multicloud solution
B. Single-tenancy private cloud
C. Hybrid cloud solution
D. Cloud access security broker
Following a merger, the number of remote sites for a company has doubled to 52. The company has decided to secure each remote site with an NGFW to provide web filtering, NIDS/NIPS, and network antivirus. The Chief Information Officer (CIO) has requested that the security engineer provide recommendations on sizing for the firewall with the requirements that it be easy to manage and provide capacity for growth. The tables below provide information on a subset of remote sites and the firewall options: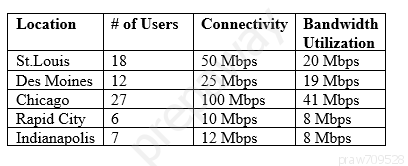
Which of the following would be the BEST option to recommend to the CIO?
A. Vendor C for small remote sites, and Vendor B for large sites.
B. Vendor B for all remote sites
C. Vendor C for all remote sites
D. Vendor A for all remote sites
E. Vendor D for all remote sites
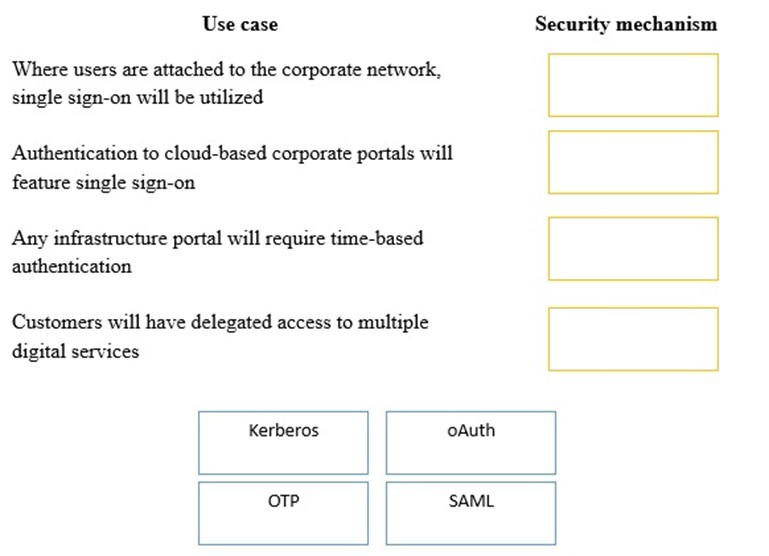
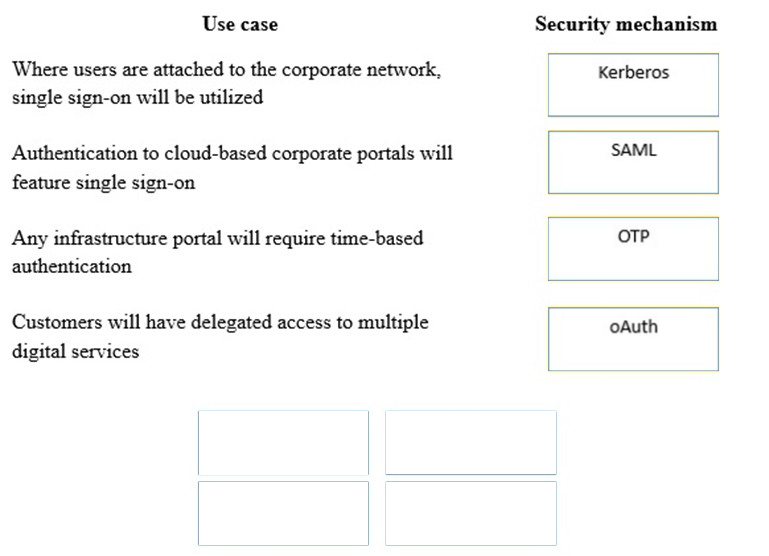
DRAG DROP - A security consultant is considering authentication options for a financial institution. The following authentication options are available. Drag and drop the security mechanism to the appropriate use case. Options may be used once. Select and Place:
A financial consulting firm recently recovered from some damaging incidents that were associated with malware installed via rootkit. Post-incident analysis is ongoing, and the incident responders and systems administrators are working to determine a strategy to reduce the risk of recurrence. The firm's systems are running modern operating systems and feature UEFI and TPMs. Which of the following technical options would provide the MOST preventive value?
A. Update and deploy GPOs
B. Configure and use measured boot
C. Strengthen the password complexity requirements
D. Update the antivirus software and definitions
Users have been reporting unusual automated phone calls, including names and phone numbers, that appear to come from devices internal to the company. Which of the following should the systems administrator do to BEST address this problem?
A. Add an ACL to the firewall to block VoIP.
B. Change the settings on the phone system to use SIP-TLS.
C. Have the phones download new configurations over TFTP.
D. Enable QoS configuration on the phone VLAN.
The Chief Information Security Officer (CISO) for an organization wants to develop custom IDS rulesets faster, prior to new rules being released by IDS vendors. Which of the following BEST meets this objective?
A. Identify a third-party source for IDS rules and change the configuration on the applicable IDSs to pull in the new rulesets
B. Encourage cybersecurity analysts to review open-source intelligence products and threat database to generate new IDS rules based on those sources
C. Leverage the latest TCP- and UDP-related RFCs to arm sensors and IDSs with appropriate heuristics for anomaly detection
D. Use annual hacking conventions to document the latest attacks and threats, and then develop IDS rules to counter those threats
The Chief Executive Officer (CEO) of a company has considered implementing a cost-saving measure that might result in new risk to the company. When deciding whether to implement this measure, which of the following would be the BEST course of action to manage the organization's risk?
A. Present the detailed risk resulting from the change to the company’s board of directors
B. Pilot new mitigations that cost less than the total amount saved by the change
C. Modify policies and standards to discourage future changes that increase risk
D. Capture the risk in a prioritized register that is shared routinely with the CEO
An employee decides to log into an authorized system. The system does not prompt the employee for authentication prior to granting access to the console, and it cannot authenticate the network resources. Which of the following attack types can this lead to if it is not mitigated?
A. Memory leak
B. Race condition
C. Smurf
D. Deadlock
A security assessor is working with an organization to review the policies and procedures associated with managing the organization's virtual infrastructure. During a review of the virtual environment, the assessor determines the organization is using servers to provide more than one primary function, which violates a regulatory requirement. The assessor reviews hardening guides and determines policy allows for this configuration. It would be MOST appropriate for the assessor to advise the organization to:
A. segment dual-purpose systems on a hardened network segment with no external access
B. assess the risks associated with accepting non-compliance with regulatory requirements
C. update system implementation procedures to comply with regulations
D. review regulatory requirements and implement new policies on any newly provisioned servers
An organization is currently performing a market scan for managed security services and EDR capability. Which of the following business documents should be released to the prospective vendors in the first step of the process? (Choose two.)
A. MSA
B. RFP
C. NDA
D. RFI
E. MOU
F. RFQ
A company that has been breached multiple times is looking to protect cardholder data. The previous undetected attacks all mimicked normal administrative-type behavior. The company must deploy a host solution to meet the following requirements: ✑ Detect administrative actions ✑ Block unwanted MD5 hashes ✑ Provide alerts ✑ Stop exfiltration of cardholder data Which of the following solutions would BEST meet these requirements? (Choose two.)
A. AV
B. EDR
C. HIDS
D. DLP
E. HIPS
F. EFS
A healthcare company wants to increase the value of the data it collects on its patients by making the data available to third-party researchers for a fee. Which of the following BEST mitigates the risk to the company?
A. Log all access to the data and correlate with the researcher.
B. Anonymize identifiable information using keyed strings.
C. Ensure all data is encrypted in transit to the researcher.
D. Ensure all researchers sign and abide by non-disclosure agreements.
E. Sanitize date and time stamp information in the records.
Ann, a security administrator, is conducting an assessment on a new firewall, which was placed at the perimeter of a network containing PII. Ann runs the following commands on a server (10.0.1.19) behind the firewall:From her own workstation (192.168.2.45) outside the firewall, Ann then runs a port scan against the server and records the following packet capture of the port scan:
Connectivity to the server from outside the firewall worked as expected prior to executing these commands. Which of the following can be said about the new firewall?
A. It is correctly dropping all packets destined for the server.
B. It is not blocking or filtering any traffic to the server.
C. Iptables needs to be restarted.
D. The IDS functionality of the firewall is currently disabled.
The Chief Information Security Officer (CISO) of an e-retailer, which has an established security department, identifies a customer who has been using a fraudulent credit card. The CISO calls the local authorities, and when they arrive on-site, the authorities ask a security engineer to create a point-in-time copy of the running database in their presence. This is an example of:
A. creating a forensic image
B. deploying fraud monitoring
C. following a chain of custody
D. analyzing the order of volatility
Users have reported that an internally developed web application is acting erratically, and the response output is inconsistent. The issue began after a web application dependency patch was applied to improve security. Which of the following would be the MOST appropriate tool to help identify the issue?
A. Fuzzer
B. SCAP scanner
C. Vulnerability scanner
D. HTTP interceptor
A penetration tester is conducting an assessment on Comptia.org and runs the following command from a coffee shop while connected to the public Internet:Which of the following should the penetration tester conclude about the command output?
A. The public/private views on the Comptia.org DNS servers are misconfigured
B. Comptia.org is running an older mail server, which may be vulnerable to exploits
C. The DNS SPF records have not been updated for Comptia.org
D. 192.168.102.67 is a backup mail server that may be more vulnerable to attack
A bank is initiating the process of acquiring another smaller bank. Before negotiations happen between the organizations, which of the following business documents would be used as the FIRST step in the process?
A. MOU
B. OLA
C. BPA
D. NDA
A security consultant is conducting a penetration test against a customer enterprise that comprises local hosts and cloud-based servers. The hosting service employs a multitenancy model with elastic provisioning to meet customer demand. The customer runs multiple virtualized servers on each provisioned cloud host. The security consultant is able to obtain multiple sets of administrator credentials without penetrating the customer network. Which of the following is the MOST likely risk the tester exploited?
A. Data-at-rest encryption misconfiguration and repeated key usage
B. Offline attacks against the cloud security broker service
C. The ability to scrape data remnants in a multitenancy environment
D. VM escape attacks against the customer network hypervisors
A breach was caused by an insider threat in which customer PII was compromised. Following the breach, a lead security analyst is asked to determine which vulnerabilities the attacker used to access company resources. Which of the following should the analyst use to remediate the vulnerabilities?
A. Protocol analyzer
B. Root cause analysis
C. Behavioral analytics
D. Data leak prevention
An engineer is evaluating the control profile to assign to a system containing PII, financial, and proprietary data.Based on the data classification table above, which of the following BEST describes the overall classification?
A. High confidentiality, high availability
B. High confidentiality, medium availability
C. Low availability, low confidentiality
D. High integrity, low availability
A security analyst sees some suspicious entries in a log file from a web server website, which has a form that allows customers to leave feedback on the company's products. The analyst believes a malicious actor is scanning the web form. To know which security controls to put in place, the analyst first needs to determine the type of activity occurring to design a control. Given the log below:Which of the following is the MOST likely type of activity occurring?
A. SQL injection
B. XSS scanning
C. Fuzzing
D. Brute forcing
Which of the following may indicate a configuration item has reached end-of-life?
A. The device will no longer turn on and indicated an error.
B. The vendor has not published security patches recently.
C. The object has been removed from the Active Directory.
D. Logs show a performance degradation of the component.
Following a security assessment, the Chief Information Security Officer (CISO) is reviewing the results of the assessment and evaluating potential risk treatment strategies. As part of the CISO's evaluation, a judgment of potential impact based on the identified risk is performed. To prioritize response actions, the CISO uses past experience to take into account the exposure factor as well as the external accessibility of the weakness identified. Which of the following is the CISO performing?
A. Documentation of lessons learned
B. Quantitative risk assessment
C. Qualitative assessment of risk
D. Business impact scoring
E. Threat modeling
A project manager is working with a team that is tasked to develop software applications in a structured environment and host them in a vendor's cloud-based infrastructure. The organization will maintain responsibility for the software but will not manage the underlying server applications. Which of the following does the organization plan to leverage?
A. SaaS
B. PaaS
C. IaaS
D. Hybrid cloud
E. Network virtualization
SIMULATION - As a security administrator, you are asked to harden a server running Red Hat Enterprise Server 5.5 64-bit. This server is being used as a DNS and time server. It is not used as a database, web server, or print server. There are no wireless connections to the server, and it does not need to print. The command window will be provided along with root access. You are connected via a secure shell with root access. You may query help for a list of commands. Instructions: You need to disable and turn off unrelated services and processes. It is possible to simulate a crash of your server session. The simulation can be reset, but the server cannot be rebooted. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
An information security officer reviews a report and notices a steady increase in outbound network traffic over the past ten months. There is no clear explanation for the increase. The security officer interviews several business units and discovers an unsanctioned cloud storage provider was used to share marketing materials with potential customers. Which of the following services would be BEST for the security officer to recommend to the company?
A. NIDS
B. HIPS
C. CASB
D. SFTP
A security administrator is hardening a TrustedSolaris server that processes sensitive data. The data owner has established the following security requirements: ✑ The data is for internal consumption only and shall not be distributed to outside individuals ✑ The systems administrator should not have access to the data processed by the server ✑ The integrity of the kernel image is maintainedWhich of the following host-based security controls BEST enforce the data owner's requirements? (Choose three.)
A. SELinux
B. DLP
C. HIDS
D. Host-based firewall
E. Measured boot
F. Data encryption
G. Watermarking
The Chief Information Officer (CIO) wants to increase security and accessibility among the organization's cloud SaaS applications. The applications are configured to use passwords, and two-factor authentication is not provided natively. Which of the following would BEST address the CIO's concerns?
A. Procure a password manager for the employees to use with the cloud applications.
B. Create a VPN tunnel between the on-premises environment and the cloud providers.
C. Deploy applications internally and migrate away from SaaS applications.
D. Implement an IdP that supports SAML and time-based, one-time passwords.
A security engineer is investigating a compromise that occurred between two internal computers. The engineer has determined during the investigation that one computer infected another. While reviewing the IDS logs, the engineer can view the outbound callback traffic, but sees no traffic between the two computers. Which of the following would BEST address the IDS visibility gap?
A. Install network taps at the edge of the network.
B. Send syslog from the IDS into the SIEM.
C. Install HIDS on each computer.
D. SPAN traffic form the network core into the IDS.
An advanced threat emulation engineer is conducting testing against a client's network. The engineer conducts the testing in as realistic a manner as possible. Consequently, the engineer has been gradually ramping up the volume of attacks over a long period of time. Which of the following combinations of techniques would the engineer MOST likely use in this testing? (Choose three.)
A. Black box testing
B. Gray box testing
C. Code review
D. Social engineering
E. Vulnerability assessment
F. Pivoting
G. Self-assessment
H. White teaming
A security analyst works for a defense contractor that produces classified research on drones. The contractor faces nearly constant attacks from sophisticated nation-state actors and other APIs. Which of the following would help protect the confidentiality of the research data?
A. Use diverse components in layers throughout the architecture
B. Implement non-heterogeneous components at the network perimeter
C. Purge all data remnants from client devices’ volatile memory at regularly scheduled intervals
D. Use only in-house developed applications that adhere to strict SDLC security requirements
A secure facility has a server room that currently is controlled by a simple lock and key, and several administrators have copies of the key. To maintain regulatory compliance, a second lock, which is controlled by an application on the administrators' smartphones, is purchased and installed. The application has various authentication methods that can be used. The criteria for choosing the most appropriate method are: ✑ It cannot be invasive to the end user. ✑ It must be utilized as a second factor. ✑ Information sharing must be avoided. ✑ It must have a low false acceptance rate. Which of the following BEST meets the criteria?
A. Facial recognition
B. Swipe pattern
C. Fingerprint scanning
D. Complex passcode
E. Token card
A security administrator is reviewing the following output from an offline password audit:Which of the following should the systems administrator implement to BEST address this audit finding? (Choose two.)
A. Cryptoprocessor
B. Bcrypt
C. SHA-256
D. PBKDF2
E. Message authentication
A hospital is deploying new imaging software that requires a web server for access to images for both local and remote users. The web server allows user authentication via secure LDAP. The information security officer wants to ensure the server does not allow unencrypted access to the imaging server by using Nmap to gather additional information. Given the following: ✑ The imaging server IP is 192.168.101.24. ✑ The domain controller IP is 192.168.100.1. ✑ The client machine IP is 192.168.200.37. Which of the following should be used to confirm this is the only open port on the web server?
A. nmap -p 80,443 192.168.101.24
B. nmap -p 80, 443,389,636 192.168.100.1
C. nmap ג€”p 80,389 192.168.200.37
D. nmap -p- 192.168.101.24
A company is deploying a DLP solution and scanning workstations and network drives for documents that contain potential PII and payment card data. The results of the first scan are as follows:The security team is unable to identify the data owners for the specific files in a timely manner and does not suspect malicious activity with any of the detected files. Which of the following would address the inherent risk until the data owners can be formally identified?
A. Move the files from the marketing share to a secured drive
B. Search the metadata for each file to locate the file’s creator and transfer the files to the personal drive of the listed creator
C. Configure the DLP tool to delete the files on the shared drives
D. Remove the access for the internal audit group from the accounts payable and payroll shares
Access Full CAS-003 Dump Free
Looking for even more practice questions? Click here to access the complete CAS-003 Dump Free collection, offering hundreds of questions across all exam objectives.
We regularly update our content to ensure accuracy and relevance—so be sure to check back for new material.
Begin your certification journey today with our CAS-003 dump free questions — and get one step closer to exam success!