AZ-500 Practice Test Free – 50 Real Exam Questions to Boost Your Confidence
Preparing for the AZ-500 exam? Start with our AZ-500 Practice Test Free – a set of 50 high-quality, exam-style questions crafted to help you assess your knowledge and improve your chances of passing on the first try.
Taking a AZ-500 practice test free is one of the smartest ways to:
- Get familiar with the real exam format and question types
- Evaluate your strengths and spot knowledge gaps
- Gain the confidence you need to succeed on exam day
Below, you will find 50 free AZ-500 practice questions to help you prepare for the exam. These questions are designed to reflect the real exam structure and difficulty level. You can click on each Question to explore the details.
You have an Azure subscription that contains a user named Admin1 and a virtual machine named VM1. VM1 runs Windows Server 2019 and was deployed by using an Azure Resource Manager template. VM1 is the member of a backend pool of a public Azure Basic Load Balancer. Admin1 reports that VM1 is listed as Unsupported on the Just in time VM access blade of Azure Security Center. You need to ensure that Admin1 can enable just in time (JIT) VM access for VM1. What should you do?
A. Create and configure a network security group (NSG).
B. Create and configure an additional public IP address for VM1.
C. Replace the Basic Load Balancer with an Azure Standard Load Balancer.
D. Assign an Azure Active Directory Premium Plan 1 license to Admin1.
Your company makes use of Azure Active Directory (Azure AD) in a hybrid configuration. All users are making use of hybrid Azure AD joined Windows 10 computers. You manage an Azure SQL database that allows for Azure AD authentication. You need to make sure that database developers are able to connect to the SQL database via Microsoft SQL Server Management Studio (SSMS). You also need to make sure the developers use their on-premises Active Directory account for authentication. Your strategy should allow for authentication prompts to be kept to a minimum. Which of the following is the authentication method the developers should use?
A. Azure AD token.
B. Azure Multi-Factor authentication.
C. Active Directory integrated authentication.
SIMULATION - You need to prevent HTTP connections to the rg1lod28681041n1 Azure Storage account. To complete this task, sign in to the Azure portal.
You have an Azure subscription named Sub1 that has Security defaults disabled. The subscription contains the following users: • Five users that have owner permissions for Sub1. • Ten users that have owner permissions for Azure resources. None of the users have multi-factor authentication (MFA) enabled. Sub1 has the secure score as shown in the Secure Score exhibit. (Click the Secure Score tab.)You plan to enable MFA for the following users: • Five users that have owner permission for Sub1. • Five users that have owner permissions for Azure resources. By how many points will the secure score increase after you perform the planned changes?
A. 0
B. 5
C. 7.5
D. 10
E. 14
You have an Azure subscription that contains a user named User1. You need to ensure that User1 can perform the following tasks: • Create groups. • Create access reviews for role-assignable groups. • Assign Azure AD roles to groups. The solution must use the principle of least privilege. Which role should you assign to User1?
A. Groups administrator
B. Authentication administrator
C. Identity Governance Administrator
D. Privileged role administrator
You are testing an Azure Kubernetes Service (AKS) cluster. The cluster is configured as shown in the exhibit. (Click the Exhibit tab.)You plan to deploy the cluster to production. You disable HTTP application routing. You need to implement application routing that will provide reverse proxy and TLS termination for AKS services by using a single IP address. What should you do?
A. Create an AKS Ingress controller.
B. Install the container network interface (CNI) plug-in.
C. Create an Azure Standard Load Balancer.
D. Create an Azure Basic Load Balancer.
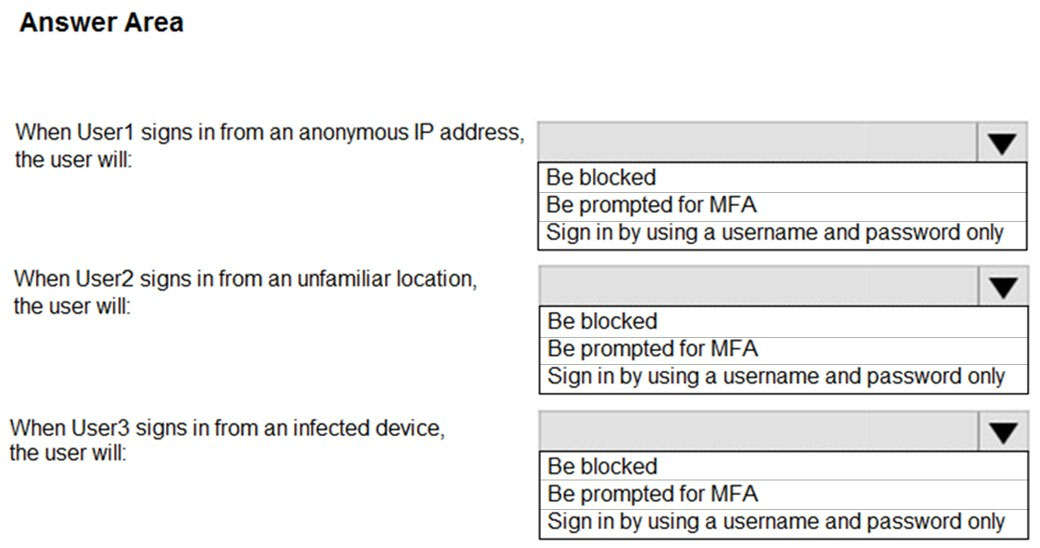
You need to meet the technical requirements for the finance department users. Which CAPolicy1 settings should you modify?
A. Cloud apps or actions
B. Conditions
C. Grant
D. Session
You have an Azure subscription that contains virtual machines. You enable just in time (JIT) VM access to all the virtual machines. You need to connect to a virtual machine by using Remote Desktop. What should you do first?
A. From Azure Directory (Azure AD) Privileged Identity Management (PIM), activate the Security administrator user role.
B. From Azure Active Directory (Azure AD) Privileged Identity Management (PIM), activate the Owner role for the virtual machine.
C. From the Azure portal, select the virtual machine, select Connect, and then select Request access.
D. From the Azure portal, select the virtual machine and add the Network Watcher Agent virtual machine extension.
Your company's Azure subscription includes an Azure Log Analytics workspace. Your company has a hundred on-premises servers that run either Windows Server 2012 R2 or Windows Server 2016, and is linked to the Azure Log Analytics workspace. The Azure Log Analytics workspace is set up to gather performance counters associated with security from these linked servers. You have been tasked with configuring alerts according to the information gathered by the Azure Log Analytics workspace. You have to make sure that alert rules allow for dimensions, and that alert creation time should be kept to a minimum. Furthermore, a single alert notification must be created when the alert is created and when the alert is sorted out. You need to make use of the necessary signal type when creating the alert rules. Which of the following is the option you should use?
A. You should make use of the Activity log signal type.
B. You should make use of the Application Log signal type.
C. You should make use of the Metric signal type.
D. You should make use of the Audit Log signal type.
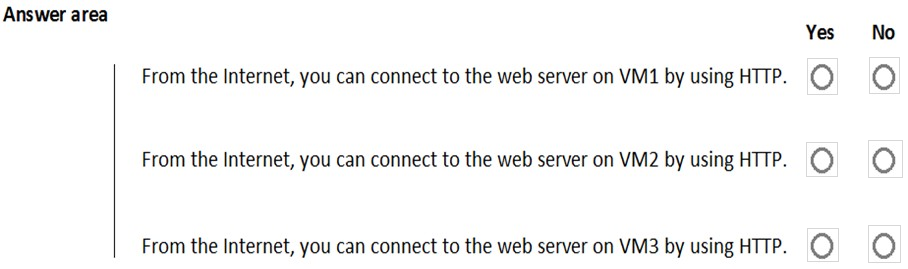
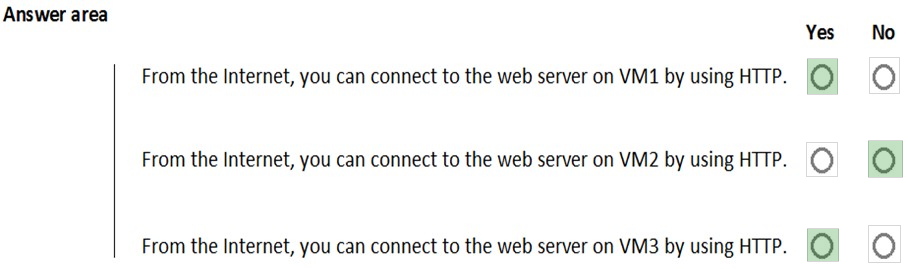
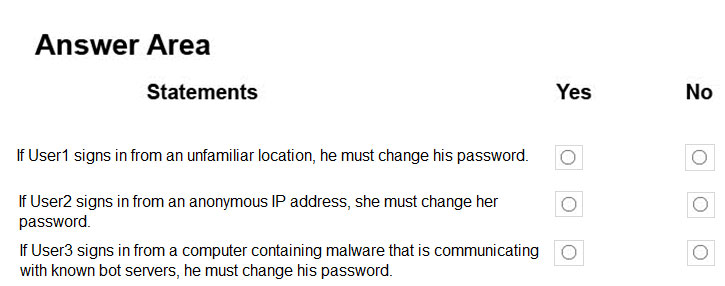
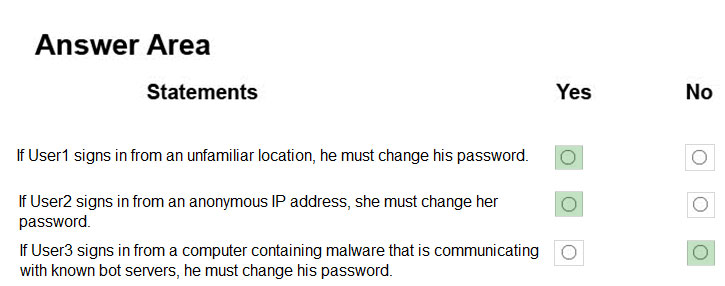
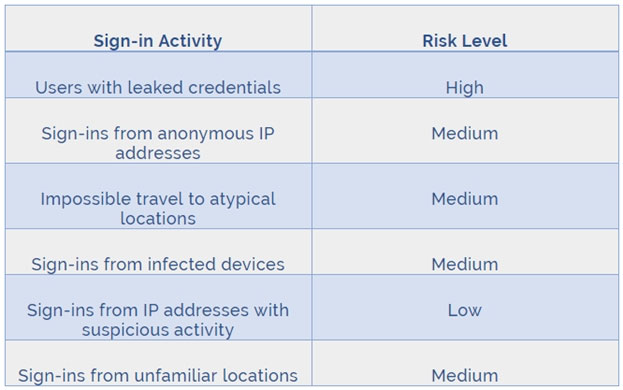
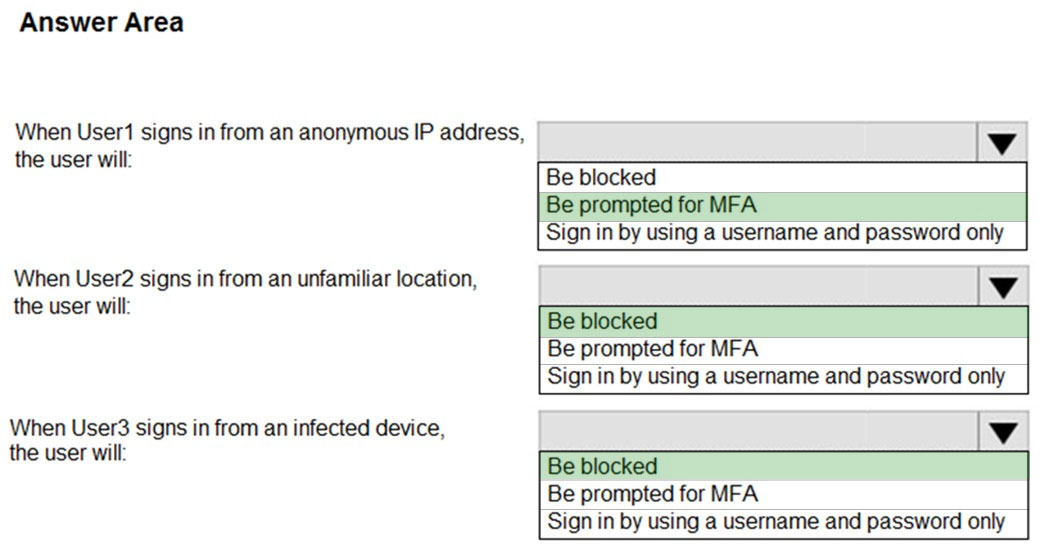
HOTSPOT - You are evaluating the security of VM1, VM2, and VM3 in Sub2. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
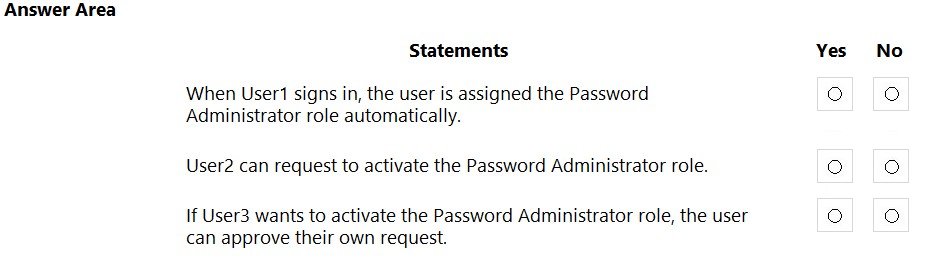
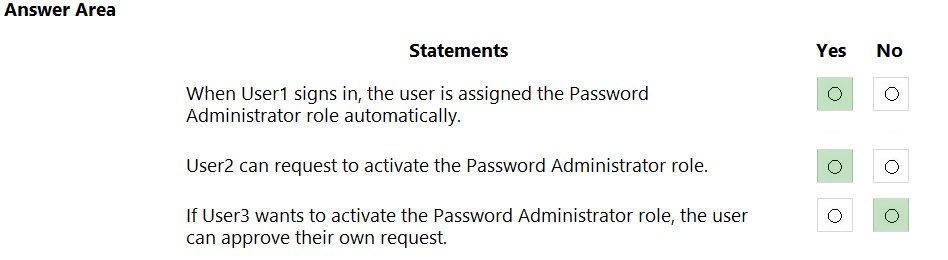
HOTSPOT - You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table.Azure AD Privileged Identity Management (PIM) is used in contoso.com. In PIM, the Password Administrator role has the following settings: ✑ Maximum activation duration (hours): 2 ✑ Send email notifying admins of activation: Disable ✑ Require incident/request ticket number during activation: Disable ✑ Require Azure Multi-Factor Authentication for activation: Enable ✑ Require approval to activate this role: Enable ✑ Selected approver: Group1 You assign users the Password Administrator role as shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
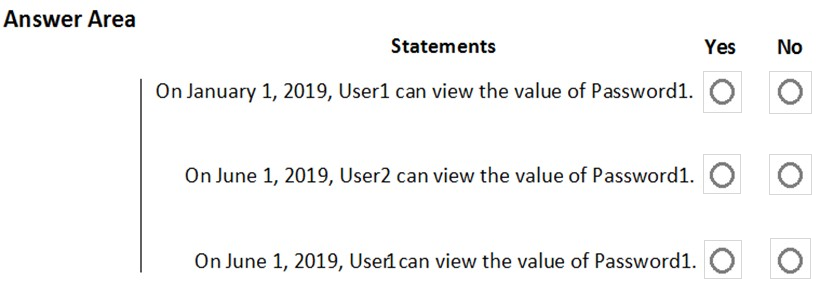
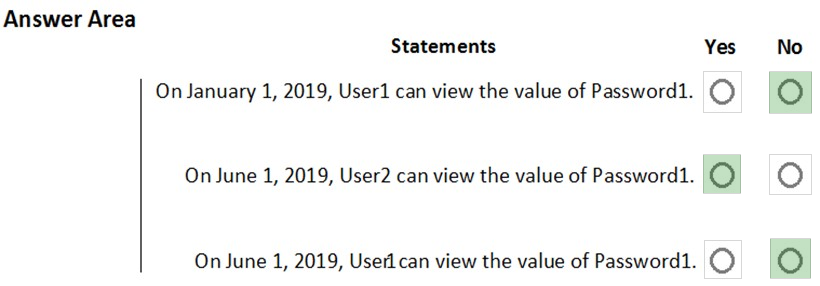
HOTSPOT - You have an Azure subscription that contains the resources shown in the following table.User1 is a member of Group1. Group1 and User2 are assigned the Key Vault Contributor role for Vault1. On January 1, 2019, you create a secret in Vault1. The secret is configured as shown in the exhibit. The date format YYYY-MM-DD is used on the exhibit. (Click the Exhibit tab.)
User2 is assigned an access policy to Vault1. The policy has the following configurations: ✑ Key Management Operations: Get, List, and Restore ✑ Cryptographic Operations: Decrypt and Unwrap Key ✑ Secret Management Operations: Get, List, and Restore Group1 is assigned an access policy to Vault1. The policy has the following configurations: ✑ Key Management Operations: Get and Recover ✑ Secret Management Operations: List, Backup, and Recover For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
You have an Azure subscription. You create a new virtual network named VNet1. You plan to deploy an Azure web app named App1 that will use VNet1 and will be reachable by using private IP addresses. The solution must support inbound and outbound network traffic. What should you do?
A. Create an Azure App Service Hybrid Connection.
B. Create an Azure application gateway.
C. Create an App Service Environment.
D. Configure regional virtual network integration.
You have an Azure AD tenant that contains a user named User1. You purchase an app named App1. User1 needs to publish App1 by using Azure AD Application Proxy. Which role should you assign to User1?
A. Cloud application administrator
B. Application administrator
C. Hybrid identity administrator
D. Cloud App Security Administrator
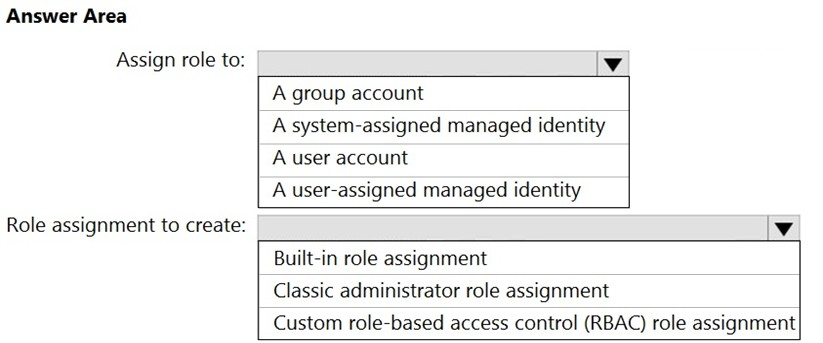
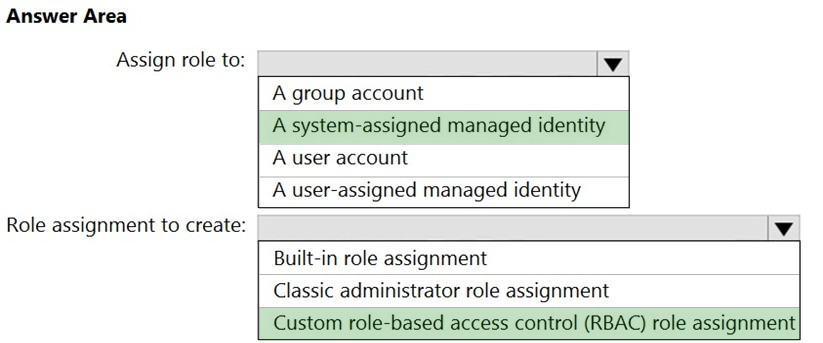
HOTSPOT - You plan to implement an Azure function named Function1 that will create new storage accounts for containerized application instances. You need to grant Function1 the minimum required privileges to create the storage accounts. The solution must minimize administrative effort. What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have an Azure AD tenant. The tenant contains users that are assigned Azure AD Premium P2 licenses. You have a partner company that has a domain named fabrikam.com. The fabrikam.com domain contains a user named User1. User1 has an email address of user1@fabrikam.com You need to provide User1 with access to the resources in the tenant. The solution must meet the following requirements: • User1 must be able to sign in by using the user1@fabrikam.com credentials. • You must be able to grant User1 access to the resources in the tenant. • Administrative effort must be minimized. What should you do?
A. Create a user account for User1.
B. To the tenant, add fabrikam.com as a custom domain.
C. Create an invite for User1.
D. Set Enable guest self-service sign up via user flows to Yes for the tenant.
SIMULATION - You need to configure network connectivity between a virtual network named VNET1 and a virtual network named VNET2. The solution must ensure that virtual machines connected to VNET1 can communicate with virtual machines connected to VNET2. To complete this task, sign in to the Azure portal and modify the Azure resources.
You have Azure Resource Manager templates that you use to deploy Azure virtual machines. You need to disable unused Windows features automatically as instances of the virtual machines are provisioned. What should you use?
A. device configuration policies in Microsoft Intune
B. Azure Automation State Configuration
C. security policies in Azure Security Center
D. device compliance policies in Microsoft Intune
You have been tasked with making sure that you are able to modify the operating system security configurations via Azure Security Center. To achieve your goal, you need to have the correct pricing tier for Azure Security Center in place. Which of the following is the pricing tier required?
A. Advanced
B. Premium
C. Standard
D. Free
You have an Azure subscription that contains the resources shown in the following table.You need to ensure that ServerAdmins can perform the following tasks: ✑ Create virtual machines in RG1 only. ✑ Connect the virtual machines to the existing virtual networks in RG2 only. The solution must use the principle of least privilege. Which two role-based access control (RBAC) roles should you assign to ServerAdmins? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. a custom RBAC role for RG2
B. the Network Contributor role for RG2
C. the Contributor role for the subscription
D. a custom RBAC role for the subscription
E. the Network Contributor role for RG1
F. the Virtual Machine Contributor role for RG1
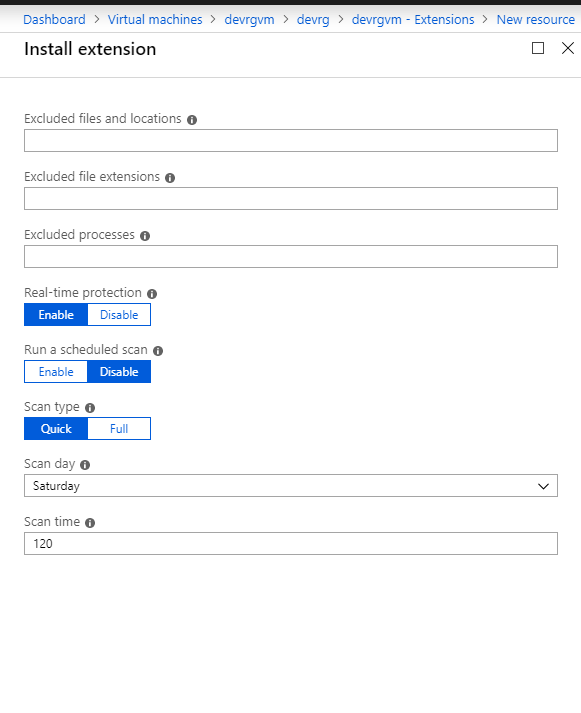
SIMULATION - You need to perform a full malware scan every Sunday at 02:00 on a virtual machine named VM1 by using Microsoft Antimalware for Virtual Machines. To complete this task, sign in to the Azure portal.
You have a sneaking suspicion that there are users trying to sign in to resources which are inaccessible to them. You decide to create an Azure Log Analytics query to confirm your suspicions. The query will detect unsuccessful user sign-in attempts from the last few days. You want to make sure that the results only show users who had failed to sign-in more than five times. Which of the following should be included in your query?
A. The EventID and CountIf() parameters.
B. The ActivityID and CountIf() parameters.
C. The EventID and Count() parameters.
D. The ActivityID and Count() parameters.
You are troubleshooting a security issue for an Azure Storage account. You enable Azure Storage Analytics logs and archive it to a storage account. What should you use to retrieve the diagnostics logs?
A. Azure Cosmos DB explorer
B. Azure Monitor
C. Microsoft Defender for Cloud
D. Azure Storage Explorer
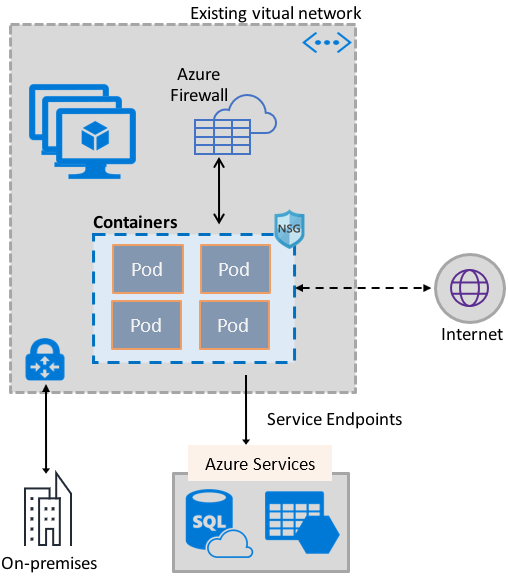
Your Company's Azure subscription includes a virtual network that has a single subnet configured. You have created a service endpoint for the subnet, which includes an Azure virtual machine that has Ubuntu Server 18.04 installed. You are preparing to deploy Docker containers to the virtual machine. You need to make sure that the containers can access Azure Storage resources and Azure SQL databases via the service endpoint. You need to perform a task on the virtual machine prior to deploying containers. Solution: You install the container network interface (CNI) plug-in. Does the solution meet the goal?
A. Yes
B. No
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution. After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a hybrid configuration of Azure Active Directory (Azure AD). You have an Azure HDInsight cluster on a virtual network. You plan to allow users to authenticate to the cluster by using their on-premises Active Directory credentials. You need to configure the environment to support the planned authentication. Solution: You deploy an Azure AD Application Proxy. Does this meet the goal?
A. Yes
B. No
You are troubleshooting a security issue for an Azure Storage account. You enable Azure Storage Analytics logs and archive it to a storage account. What should you use to retrieve the diagnostics logs?
A. Azure Cosmos DB explorer
B. SQL query editor in Azure
C. AzCopy
D. the Security admin center
You have an Azure subscription that contains a user named User1 and an Azure Container Registry named ContReg1. You enable content trust for ContReg1. You need to ensure that User1 can create trusted images in ContReg1. The solution must use the principle of least privilege. Which two roles should you assign to User1? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. AcrQuarantineReader
B. Contributor
C. AcrPush
D. AcrImageSigner
E. AcrQuarantineWriter
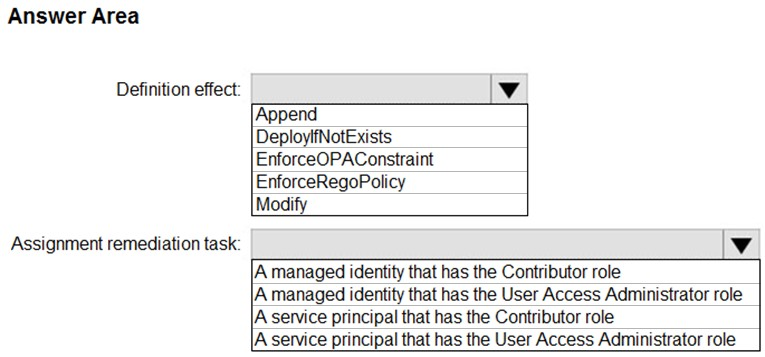
HOTSPOT - You have an Azure subscription. You need to create and deploy an Azure policy that meets the following requirements: ✑ When a new virtual machine is deployed, automatically install a custom security extension. ✑ Trigger an autogenerated remediation task for non-compliant virtual machines to install the extension. What should you include in the policy? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table.You create and enforce an Azure AD Identity Protection user risk policy that has the following settings: ✑ Assignment: Include Group1, Exclude Group2 ✑ Conditions: Sign-in risk of Medium and above ✑ Access: Allow access, Require password change For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
You have an Azure subscription and the computers shown in the following table.You need to perform a vulnerability scan of the computers by using Microsoft Defender for Cloud. Which computers can you scan?
A. VM1 only
B. VM1 and VM2 only
C. Server1 and VMSS1_0 only
D. VM1, VM2, and Server1 only
E. VM1, VM2, Server 1, and VMSS1_0
You have an Azure subscription. You create an Azure web app named Contoso1812 that uses an S1 App Service plan. You plan to - create a CNAME DNS record for www.contoso.com that points to Contoso1812. You need to ensure that users can access Contoso1812 by using the https://www.contoso.com URL. Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Turn on the system-assigned managed identity for Contoso1812.
B. Add a hostname to Contoso1812.
C. Scale out the App Service plan of Contoso1812.
D. Add a deployment slot to Contoso1812.
E. Scale up the App Service plan of Contoso1812.
F. Upload a PFX file to Contoso1812.
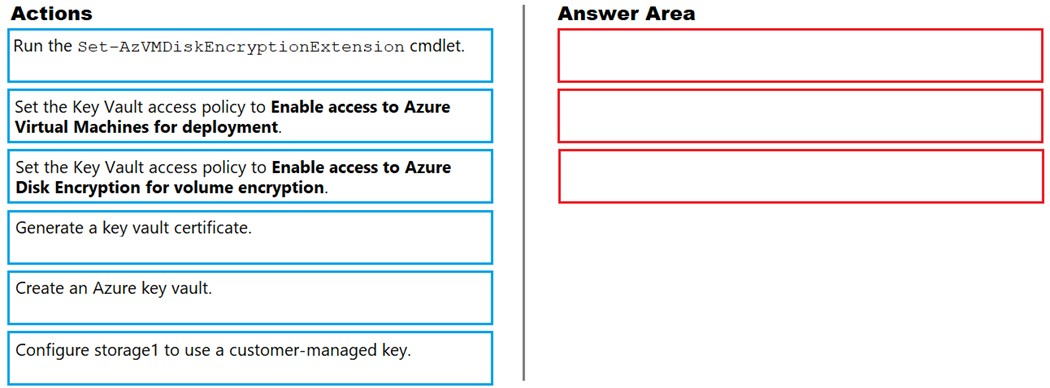
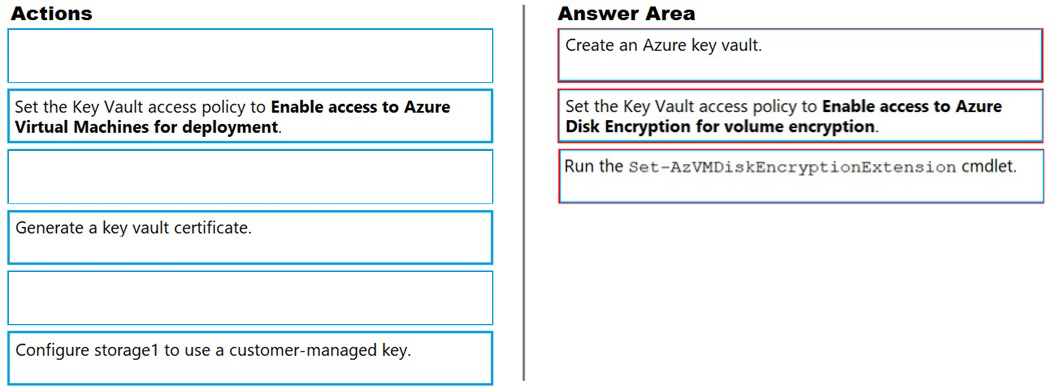
DRAG DROP - You have an Azure Storage account named storage1 and an Azure virtual machine named VM1. VM1 has a premium SSD managed disk. You need to enable Azure Disk Encryption for VM1. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange then in the correct order. Select and Place:
HOTSPOT - You have an Azure subscription that contains a user named User1 and a storage account named storage1. The storage1 account contains the resources shown in the following table.User1 is assigned the following roles for storage1: • Storage Blob Data Reader • Storage Table Data Contributor • Storage File Data SMB Share Reader In storage1, you create a shared access signature (SAS) named SAS1 as shown in the following exhibit.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
You have an Azure virtual machine that runs Ubuntu 16.04-DAILY-LTS. You plan to deploy and configure an Azure Key vault, and enable Azure Disk Encryption for the virtual machine. Which of the following is TRUE with regards to Azure Disk Encryption for a Linux VM?
A. It is NOT supported for basic tier VMs.
B. It is NOT supported for standard tier VMs.
C. OS drive encryption for Linux virtual machine scale sets is supported.
D. Custom image encryption is supported.
Your company recently created an Azure subscription. You have, subsequently, been tasked with making sure that you are able to secure Azure AD roles by making use of Azure Active Directory (Azure AD) Privileged Identity Management (PIM). Which of the following actions should you take FIRST?
A. You should sign up Azure Active Directory (Azure AD) Privileged Identity Management (PIM) for Azure AD roles.
B. You should consent to Azure Active Directory (Azure AD) Privileged Identity Management (PIM).
C. You should discover privileged roles.
D. You should discover resources.
You have an Azure subscription linked to an Azure AD tenant named contoso.com. Contoso.com contains a user named User1 and an Azure web app named App1. You plan to enable User1 to perform the following tasks: • Configure contoso.com to use Microsoft Entra Verified ID. • Register App1 in contoso.com. You need to identify which roles to assign to User1. The solution must use the principle of least privilege. Which two roles should you identify? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Authentication Policy Administrator
B. Authentication Administrator
C. Cloud App Security Administrator
D. Application Administrator
E. User Administrator
SIMULATION - You need to configure a virtual network named VNET2 to meet the following requirements: ✑ Administrators must be prevented from deleting VNET2 accidentally. ✑ Administrators must be able to add subnets to VNET2 regularly. To complete this task, sign in to the Azure portal and modify the Azure resources.
SIMULATION - You need to configure a Microsoft SQL server named Web1234578 only to accept connections from the Subnet0 subnet on the VNET01 virtual network. To complete this task, sign in to the Azure portal.
HOTSPOT - You have an Azure Active Directory (Azure AD) tenant that contains the users shown in the following table.You create and enforce an Azure AD Identity Protection sign-in risk policy that has the following settings: ✑ Assignments: Include Group1, exclude Group2 ✑ Conditions: Sign-in risk level: Medium and above ✑ Access: Allow access, Require multi-factor authentication You need to identify what occurs when the users sign in to Azure AD. What should you identify for each user? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - You have an Azure subscription that contains the virtual networks shown in the following table.The subscription contains the virtual machines shown in the following table.
You have a storage account named contoso2024 that contains the following resources: • A container named Container1 that contains a file named File1 • A file share named Share1 that contains a file named File2 You create a private endpoint for contoso2024 as shown in the following exhibit.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
SIMULATION - You need to ensure that the rg1lod28681041n1 Azure Storage account is encrypted by using a key stored in the KeyVault28681041 Azure key vault. To complete this task, sign in to the Azure portal.
You have an Azure subscription named Subscription1. You deploy a Linux virtual machine named VM1 to Subscription1. You need to monitor the metrics and the logs of VM1. What should you use?
A. the AzurePerformanceDiagnostics extension
B. Azure HDInsight
C. Linux Diagnostic Extension (LAD) 3.0
D. Azure Analysis Services
You have an Azure subscription that uses Microsoft Defender for Cloud. The subscription contains the Azure Policy definitions shown in the following table.Which definitions can be assigned as a security policy in Defender for Cloud?
A. Policy1 and Policy2 only
B. Initiative1 and Initiative2 only
C. Policy1 and Initiative1 only
D. Policy2 and Initiative2 only
E. Policy1, Policy2, Initiative1, and Initiative2
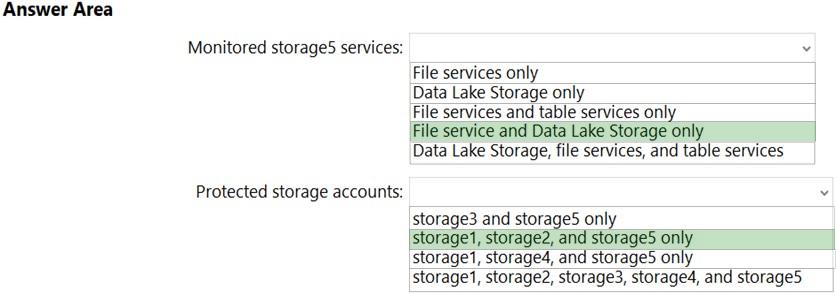
HOTSPOT - You have an Azure subscription that contains the storage accounts shown in the following table.You enable Azure Defender for Storage. Which storage services of storage5 are monitored by Azure Defender for Storage, and which storage accounts are protected by Azure Defender for Storage? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
SIMULATION - You need to ensure that web1234578 is protected from malware by using Microsoft Antimalware for Virtual Machines and is scanned every Friday at 01:00. To complete this task, sign in to the Azure portal.
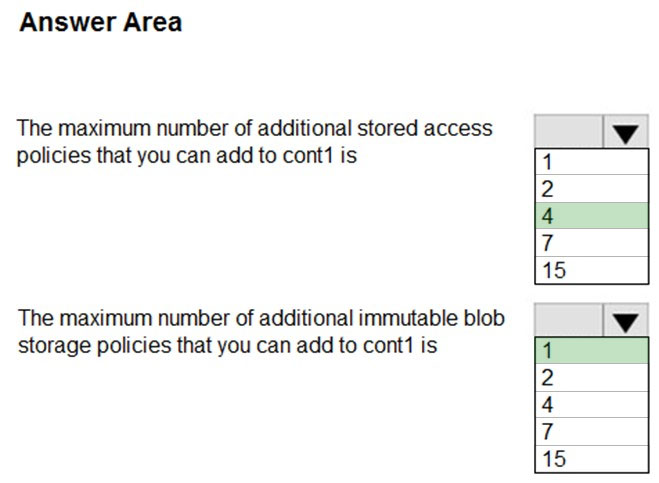
HOTSPOT - You have an Azure subscription that contains a blob container named cont1. Cont1 has the access policies shown in the following exhibit.Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point. Hot Area:
SIMULATION - You need to configure a weekly backup of an Azure SQL database named Homepage. The backup must be retained for eight weeks. To complete this task, sign in to the Azure portal.
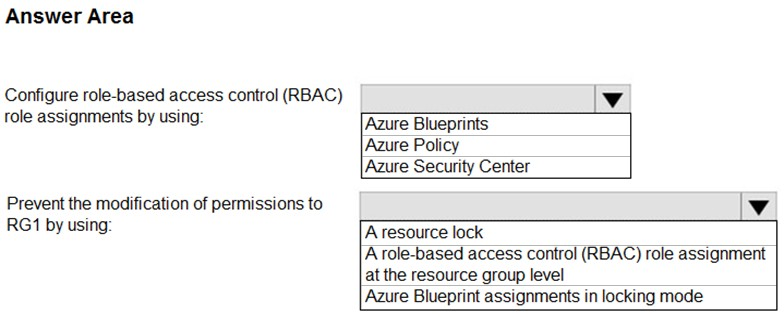
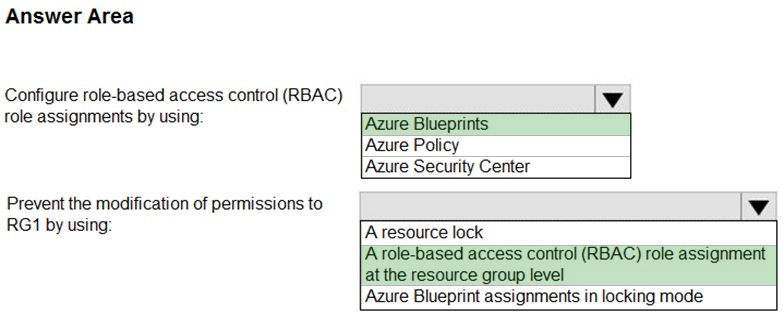
HOTSPOT - You have 20 Azure subscriptions and a security group named Group1. The subscriptions are children of the root management group. Each subscription contains a resource group named RG1. You need to ensure that for each subscription RG1 meets the following requirements: ✑ The members of Group1 are assigned the Owner role. ✑ The modification of permissions to RG1 is prevented. What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You want to gather logs from a large number of Windows Server 2016 computers using Azure Log Analytics. You are configuring an Azure Resource Manager template to deploy the Microsoft Monitoring Agent to all the servers automatically. Which of the following should be included in the template? (Choose all that apply.)
A. WorkspaceID
B. AzureADApplicationID
C. WorkspaceKey
D. StorageAccountKey
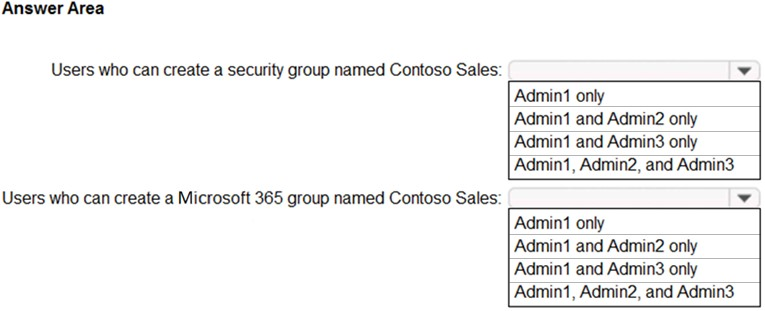
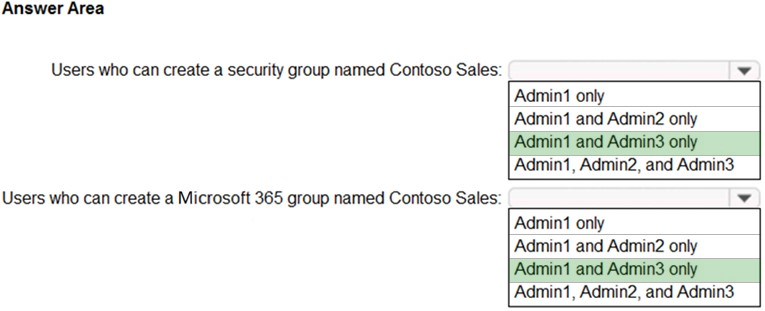
HOTSPOT - You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table.Contoso.com contains a group naming policy. The policy has a custom blocked word list rule that includes the word Contoso. Which users can create a group named Contoso Sales in contoso.com? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
Free Access Full AZ-500 Practice Test Free Questions
If you’re looking for more AZ-500 practice test free questions, click here to access the full AZ-500 practice test.
We regularly update this page with new practice questions, so be sure to check back frequently.
Good luck with your AZ-500 certification journey!