AZ-500 Practice Exam Free – 50 Questions to Simulate the Real Exam
Are you getting ready for the AZ-500 certification? Take your preparation to the next level with our AZ-500 Practice Exam Free – a carefully designed set of 50 realistic exam-style questions to help you evaluate your knowledge and boost your confidence.
Using a AZ-500 practice exam free is one of the best ways to:
- Experience the format and difficulty of the real exam
- Identify your strengths and focus on weak areas
- Improve your test-taking speed and accuracy
Below, you will find 50 realistic AZ-500 practice exam free questions covering key exam topics. Each question reflects the structure and challenge of the actual exam.
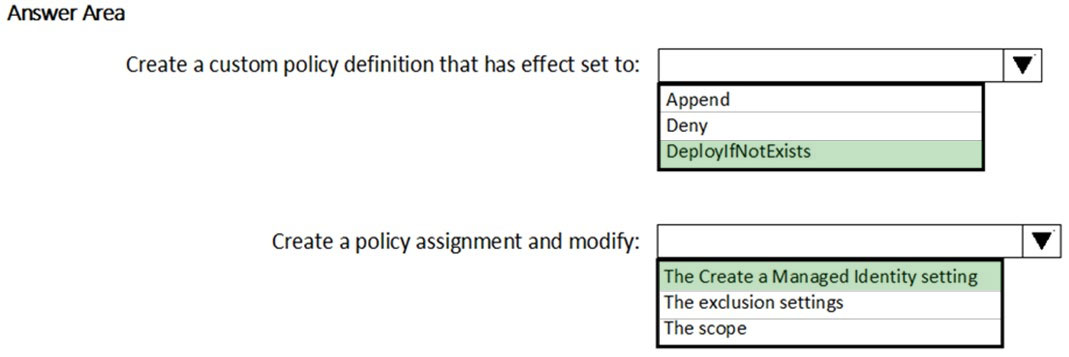
You have an Azure subscription that contains a resource group named RG1 and the network security groups (NSGs) shown in the following table.You create the Azure policy shown in the following exhibit.
You assign the policy to RG1. What will occur if you assign the policy to NSG1 and NSG2?
A. Flow logs will be enabled for NSG2 only.
B. Flow logs will be disabled for NSG1 and NSG2.
C. Flow logs will be enabled for NSG1 and NSG2.
D. Flow logs will be enabled for NSG1 only.
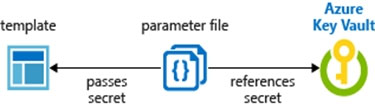
You plan to use Azure Resource Manager templates to perform multiple deployments of identically configured Azure virtual machines. The password for the administrator account of each deployment is stored as a secret in different Azure key vaults. You need to identify a method to dynamically construct a resource ID that will designate the key vault containing the appropriate secret during each deployment. The name of the key vault and the name of the secret will be provided as inline parameters. What should you use to construct the resource ID?
A. a key vault access policy
B. a linked template
C. a parameters file
D. an automation account
HOTSPOT - You have an Azure subscription that contains an Azure key vault named ContosoKey1. You create users and assign them roles as shown in the following table.You need to identify which users can perform the following actions: ✑ Delegate permissions for ContosoKey1. ✑ Configure network access to ContosoKey1. Which users should you identify? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have Azure Resource Manager templates that you use to deploy Azure virtual machines. You need to disable unused Windows features automatically as instances of the virtual machines are provisioned. What should you use?
A. device configuration policies in Microsoft Intune
B. an Azure Desired State Configuration (DSC) virtual machine extension
C. security policies in Azure Security Center
D. Azure Logic Apps
SIMULATION - You need to configure a weekly backup of an Azure SQL database named Homepage. The backup must be retained for eight weeks. To complete this task, sign in to the Azure portal.
HOTSPOT - You have an Azure SQL database named DB1 that contains a table named Tablet. You need to configure DB1 to meet the following requirements: • Sensitive data in Table1 must be identified automatically. • Only the first character and last character of the sensitive data must be displayed in query results. Which two features should you configure? To answer, select the features in the answer area. NOTE: Each correct selection is worth one point.
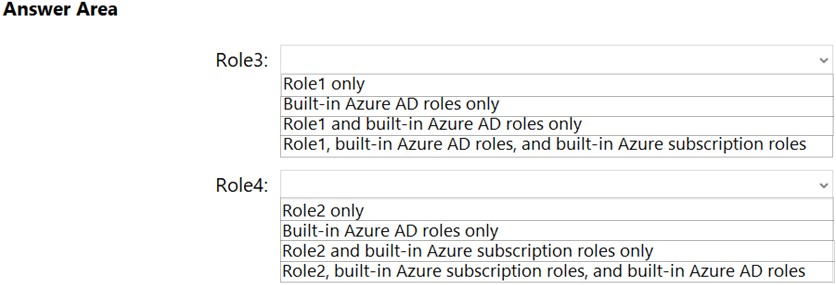
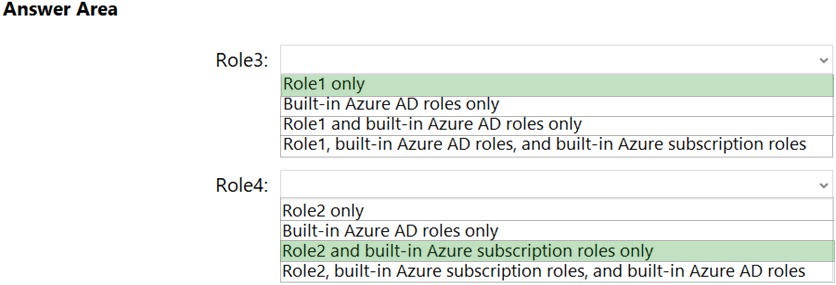
DRAG DROP - You have an Azure subscription. You plan to create two custom roles named Role1 and Role2. The custom roles will be used to perform the following tasks: • Members of Role1 will manage application security groups. • Members of Role2 will manage Azure Bastion. You need to add permissions to the custom roles. Which resource provider should you use for each role? To answer, drag the appropriate resource providers to the correct roles. Each resource provider may be used, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
You have an Azure SQL Database server named SQL1. For SQL1, you turn on Azure Defender for SQL to detect all threat detection types. Which action will Azure Defender for SQL detect as a threat?
A. A user updates more than 50 percent of the records in a table.
B. A user attempts to sign in as SELECT * FROM table1.
C. A user is added to the db_owner database role.
D. A user deletes more than 100 records from the same table.
Your company has an Active Directory forest with a single domain, named weylandindustries.com. They also have an Azure Active Directory (Azure AD) tenant with the same name. After syncing all on-premises identities to Azure AD, you are informed that users with a givenName attribute starting with LAB should not be allowed to sync to Azure AD. Which of the following actions should you take?
A. You should make use of the Synchronization Rules Editor to create an attribute-based filtering rule.
B. You should configure a DNAT rule on the Firewall.
C. You should configure a network traffic filtering rule on the Firewall.
D. You should make use of Active Directory Users and Computers to create an attribute-based filtering rule.
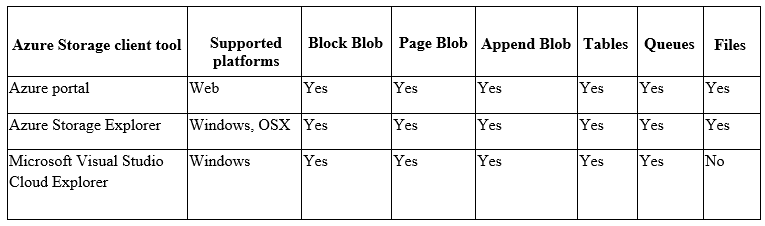
You are troubleshooting a security issue for an Azure Storage account. You enable the diagnostic logs for the storage account. What should you use to retrieve the diagnostics logs?
A. Azure Storage Explorer
B. SQL query editor in Azure
C. File Explorer in Windows
D. Azure Security Center
Your company has Azure subscription linked to their Azure Active Directory (Azure AD) tenant. As a Global administrator for the tenant, part of your responsibilities involves managing Azure Security Center settings. You are currently preparing to create a custom sensitivity label. Solution: You start by creating a custom sensitive information type. Does the solution meet the goal?
A. Yes
B. No
SIMULATION - You need to deploy an Azure firewall to a virtual network named VNET3. To complete this task, sign in to the Azure portal and modify the Azure resources. This task might take several minutes to complete. You can perform other tasks while the task completes.
You have an Azure Active Directory (Azure AD) tenant named Contoso.com and an Azure Kubernetes Service (AKS) cluster AKS1. You discover that AKS1 cannot be accessed by using accounts from Contoso.com. You need to ensure AKS1 can be accessed by using accounts from Contoso.com. The solution must minimize administrative effort. What should you do first?
A. From Azure, recreate AKS1.
B. From AKS1, upgrade the version of Kubernetes.
C. From Azure AD, implement Azure AD Premium P2
D. From Azure AD, configure the User settings.
You need to ensure that you can meet the security operations requirements. What should you do first?
A. Turn on Auto Provisioning in Security Center.
B. Integrate Security Center and Microsoft Cloud App Security.
C. Upgrade the pricing tier of Security Center to Standard.
D. Modify the Security Center workspace configuration.
You have an Azure resource group that contains 100 virtual machines. You have an initiative named Initiative1 that contains multiple policy definitions. Initiative1 is assigned to the resource group. You need to identify which resources do NOT match the policy definitions. What should you do?
A. From Azure Security Center, view the Regulatory compliance assessment.
B. From the Policy blade of the Azure Active Directory admin center, select Compliance.
C. From Azure Security Center, view the Secure Score.
D. From the Policy blade of the Azure Active Directory admin center, select Assignments.
You have an Azure subscription that contains the Azure Log Analytics workspaces shown in the following table.You create the virtual machines shown in the following table.
You plan to use Azure Sentinel to monitor Windows Defender Firewall on the virtual machines. Which virtual machines you can connect to Azure Sentinel?
A. VM1 only
B. VM1 and VM3 only
C. VM1, VM2, VM3, and VM4
D. VM1 and VM2 only
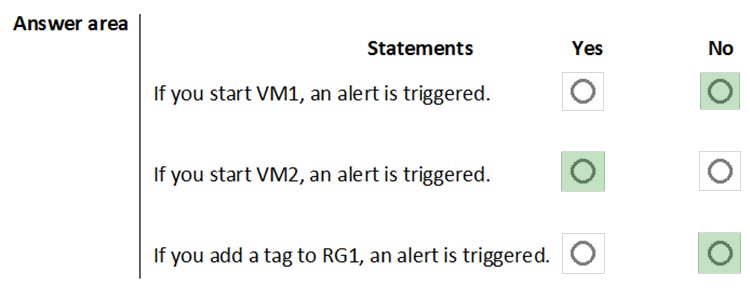
HOTSPOT - You have an Azure subscription that contains the resources shown in the following table.VM1 and VM2 are stopped. You create an alert rule that has the following settings: ✑ Resource: RG1 ✑ Condition: All Administrative operations ✑ Actions: Action groups configured for this alert rule: ActionGroup1 ✑ Alert rule name: Alert1 You create an action rule that has the following settings: ✑ Scope: VM1 ✑ Filter criteria: Resource Type = "Virtual Machines" ✑ Define on this scope: Suppression ✑ Suppression config: From now (always) ✑ Name: ActionRule1 For each of the following statements, select Yes if the statement is true. Otherwise, select No. Note: Each correct selection is worth one point. Hot Area:
You have an Azure subscription that contains a web app named App1. Users must be able to select between a Google identity or a Microsoft identity when authenticating to App1. You need to add Google as an identity provider in Azure AD. Which two pieces of information should you configure? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. a client ID
B. a tenant name
C. the endpoint URL of an application
D. a tenant ID
E. a client secret
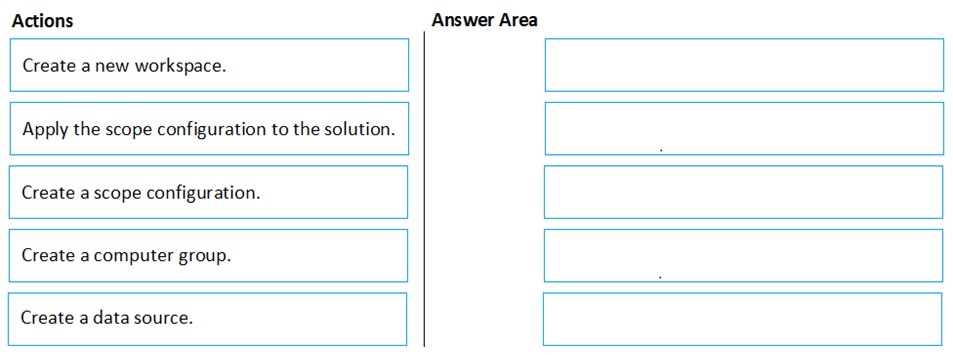
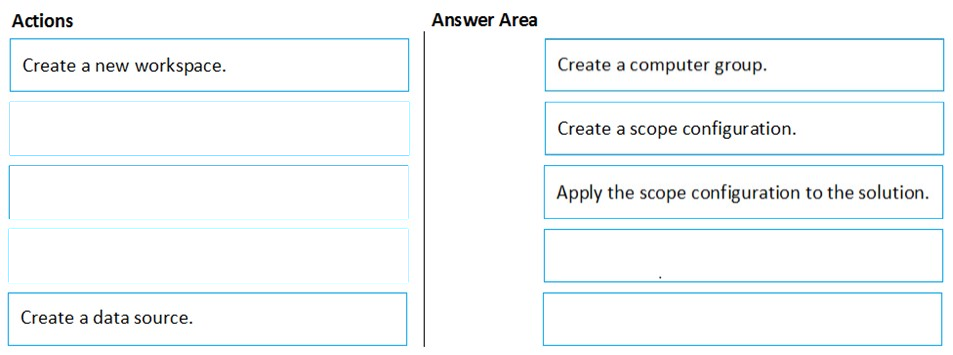
DRAG DROP - You have an Azure subscription named Sub1 that contains an Azure Log Analytics workspace named LAW1. You have 500 Azure virtual machines that run Windows Server 2016 and are enrolled in LAW1. You plan to add the System Update Assessment solution to LAW1. You need to ensure that System Update Assessment-related logs are uploaded to LAW1 from 100 of the virtual machines only. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. Select and Place:
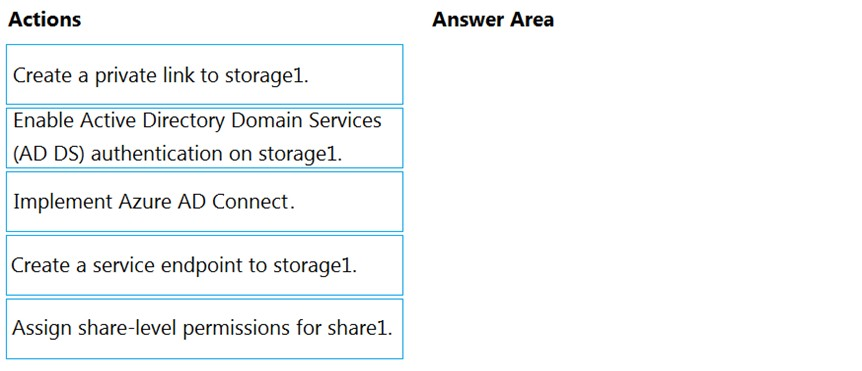
DRAG DROP - Your network contains an on-premises Active Directory domain named contoso.com. The domain contains a user named User1. You have an Azure subscription that is linked to an Azure Active Directory (Azure AD) tenant named contoso.com. The tenant contains an Azure Storage account named storage1. Storage1 contains an Azure file share named share1. Currently, the domain and the tenant are not integrated. You need to ensure that User1 can access share1 by using his domain credentials. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. Select and Place:
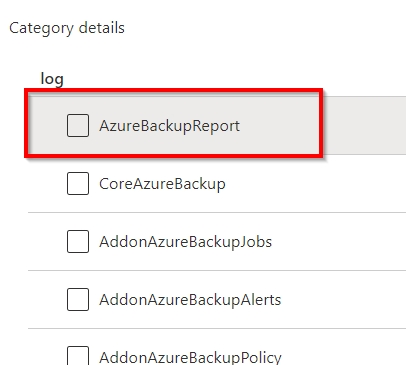
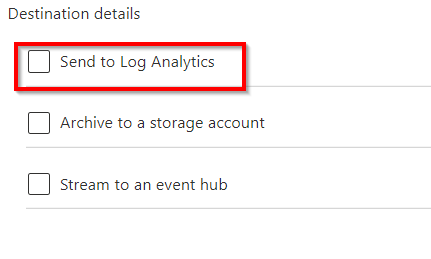
SIMULATION - You need to ensure that the AzureBackupReport log for the Vault1 Recovery Services vault is stored in the WS12345678 Azure Log Analytics workspace. To complete this task, sign in to the Azure portal and modify the Azure resources.
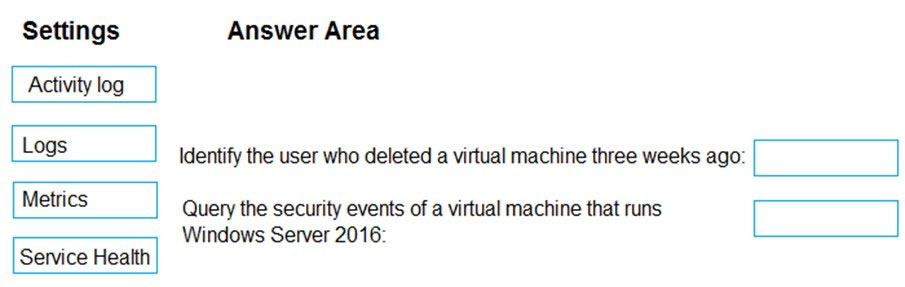
DRAG DROP - You have an Azure subscription that contains 100 virtual machines. Azure Diagnostics is enabled on all the virtual machines. You are planning the monitoring of Azure services in the subscription. You need to retrieve the following details: ✑ Identify the user who deleted a virtual machine three weeks ago. ✑ Query the security events of a virtual machine that runs Windows Server 2016. What should you use in Azure Monitor? To answer, drag the appropriate configuration settings to the correct details. Each configuration setting may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point. Select and Place:
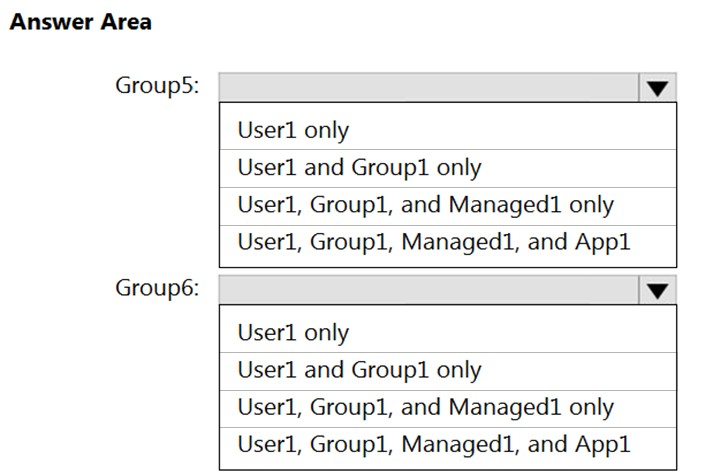
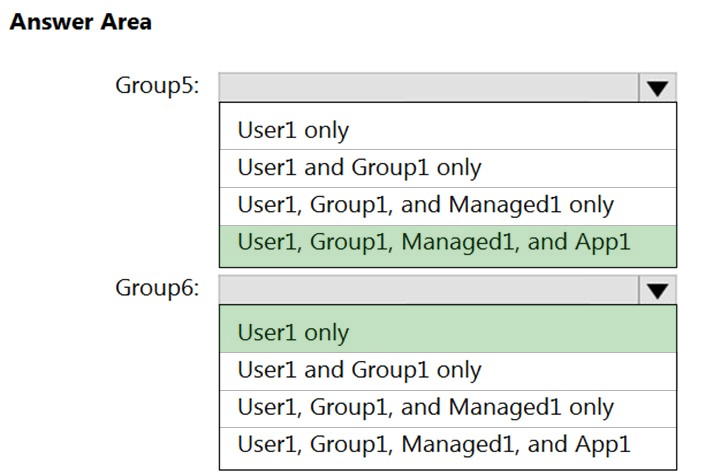
HOTSPOT - You have an Azure subscription that contains the Azure Active Directory (Azure AD) resources shown in the following table.You create the groups shown in the following table.
Which resources can you add to Group5 and Group6? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
SIMULATION - You need to create a new Azure Active Directory (Azure AD) directory named 12345678.onmicrosoft.com. The new directory must contain a new user named user1@12345678.onmicrosoft.com . To complete this task, sign in to the Azure portal.
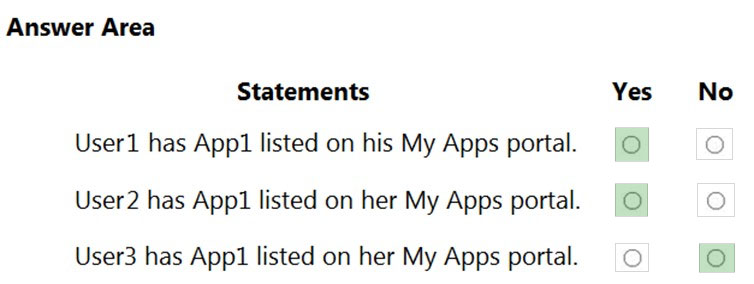
HOTSPOT - You have an Azure AD tenant named contoso.com that contains the users shown in the following table.You add enterprise applications to contoso.com as shown in the following table.
You need to identify which users can grant admin consent for App1 and App2. Which users should you identify for each application? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
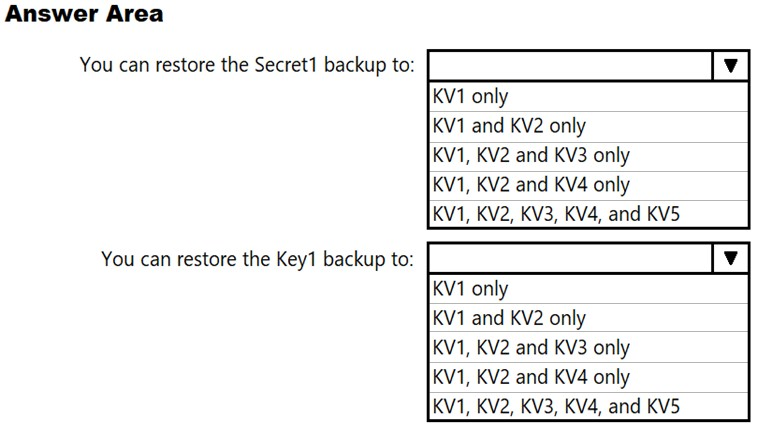
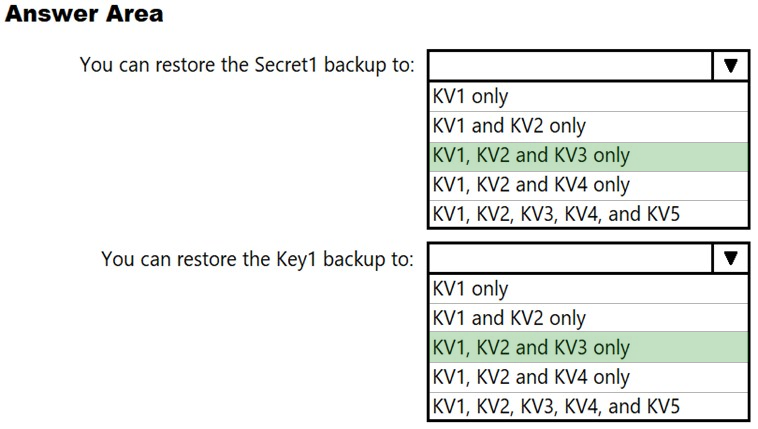
HOTSPOT - You have the Azure key vaults shown in the following table.KV1 stores a secret named Secret1 and a key for a managed storage account named Key1. You back up Secret1 and Key1. To which key vaults can you restore each backup? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
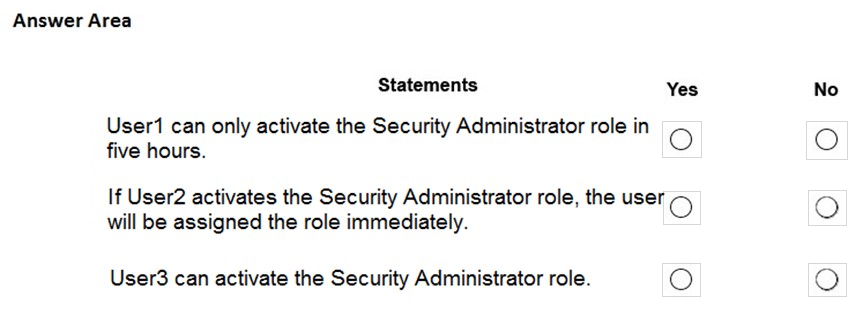
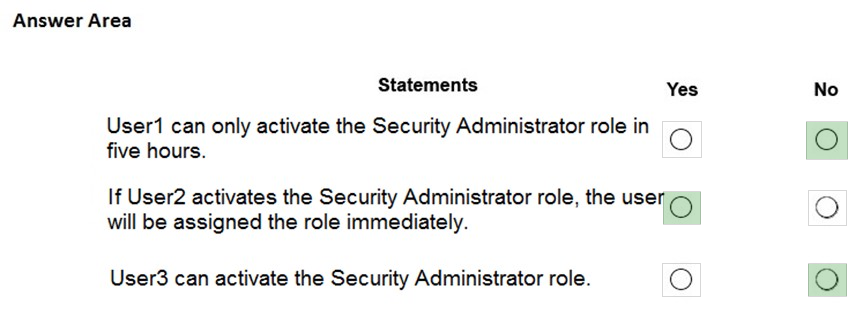
HOTSPOT - You have an Azure Active Directory (Azure AD) tenant that contains the users shown in the following table.From Azure AD Privileged Identity Management (PIM), you configure the settings for the Security Administrator role as shown in the following exhibit.
From PIM, you assign the Security Administrator role to the following groups: ✑ Group1: Active assignment type, permanently assigned ✑ Group2: Eligible assignment type, permanently eligible For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
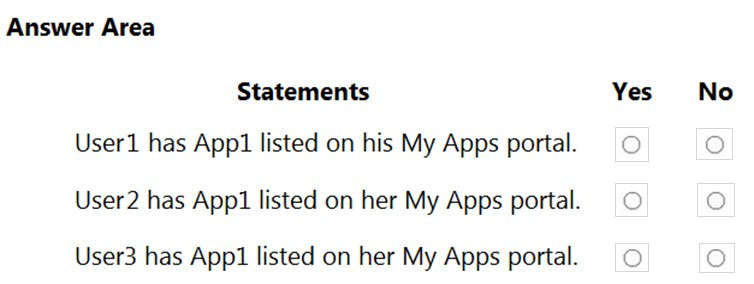
HOTSPOT - You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains three security groups named Group1, Group2, and Group3 and the users shown in the following table.Group3 is a member of Group2. In contoso.com, you register an enterprise application named App1 that has the following settings: ✑ Owners: User1 ✑ Users and groups: Group2 You configure the properties of App1 as shown in the following exhibit.
For each of the following statements, select Yes if the statement is true. Otherwise, select no. NOTE: Each correct selection is worth one point. Hot Area:
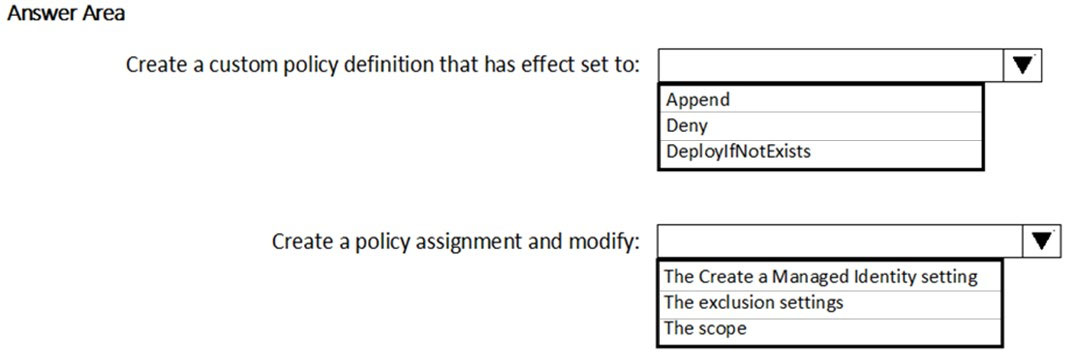
You have an Azure Active Directory (Azure AD) tenant and a root management group. You create 10 Azure subscriptions and add the subscriptions to the root management group. You need to create an Azure Blueprints definition that will be stored in the root management group. What should you do first?
A. Modify the role-based access control (RBAC) role assignments for the root management group.
B. Add an Azure Policy definition to the root management group.
C. Create a user-assigned identity.
D. Create a service principal.
DRAG DROP - You have an Azure subscription named Sub1 that contains the storage accounts shown in the following table.The storage3 storage account is encrypted by using customer-managed keys. You need to enable Microsoft Defender for Storage to meet the following requirements: • The storage1 and storage2 accounts must be included in the Defender for Storage protections. • The storage3 account must be excluded from the Defender for Storage protections. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area.
HOTSPOT - You have an Azure key vault. You need to delegate administrative access to the key vault to meet the following requirements: ✑ Provide a user named User1 with the ability to set advanced access policies for the key vault. ✑ Provide a user named User2 with the ability to add and delete certificates in the key vault. ✑ Use the principle of least privilege. What should you use to assign access to each user? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - You need to deploy Microsoft Antimalware to meet the platform protection requirements. What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have an Azure subscription that contains the Azure App Service web apps shown in the following table.You upload a private key certificate named Cert1.pfx to App1. Which apps can use Cert1?
A. App1 only
B. App1 and App2 only
C. App1 and App4 only
D. App1, App2, and App3 only
E. App1, App2, App3, and App4
You have an Azure subscription that contains an Azure SQL database named sql1. You plan to audit sql1. You need to configure the audit log destination. The solution must meet the following requirements: ✑ Support querying events by using the Kusto query language. ✑ Minimize administrative effort. What should you configure?
A. an event hub
B. a storage account
C. a Log Analytics workspace
SIMULATION - You need to ensure that connections through an Azure Application Gateway named Homepage-AGW are inspected for malicious requests. To complete this task, sign in to the Azure portal. You do not need to wait for the task to complete.
You have an Azure subscription that contains a resource group named RG1 and a security group named ServerAdmins. RG1 contains 10 virtual machines, a virtual network named VNET1, and a network security group (NSG) named NSG1. ServerAdmins can access the virtual machines by using RDP. You need to ensure that NSG1 only allows RDP connections to the virtual machines for a maximum of 60 minutes when a member of ServerAdmins requests access. What should you configure?
A. an Azure policy assigned to RG1
B. a just in time (JIT) VM access policy in Microsoft Defender for Cloud
C. an Azure Active Directory (Azure AD) Privileged Identity Management (PIM) role assignment
D. an Azure Bastion host on VNET1
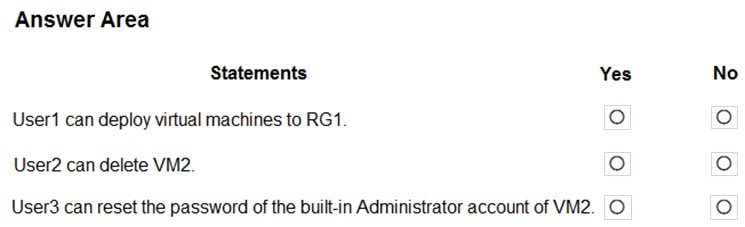
HOTSPOT - You have the hierarchy of Azure resources shown in the following exhibit.RG1, RG2, and RG3 are resource groups. RG2 contains a virtual machine named VM2. You assign role-based access control (RBAC) roles to the users shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
You have an Azure subscription that contains a resource group named RG1 and the identities shown in the following table.You assign Group4 the Contributor role for RG1. Which identities can you add to Group4 as members?
A. User1 only
B. User1 and Group3 only
C. User1, Group1, and Group3 only
D. User1, Group2, and Group3 only
E. User1, Group1, Group2, and Group3
Your company has an Azure subscription named Sub1. You plan to create several security alerts by using Azure Monitor. You need to prepare Sub1 for the alerts. What should you create first?
A. an Azure Automation account
B. an Azure event hub
C. an Azure Log Analytics workspace
D. an Azure Storage account
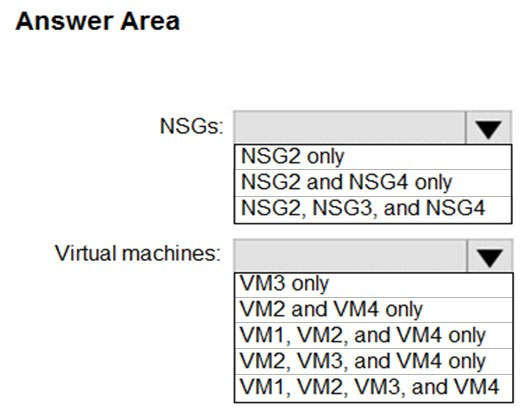
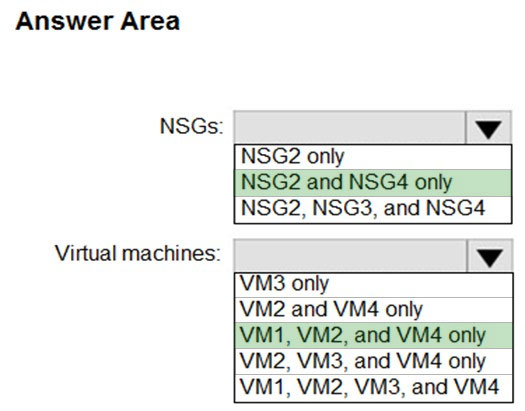
HOTSPOT - You implement the planned changes for ASG1 and ASG2. In which NSGs can you use ASG1, and the network interfaces of which virtual machines can you assign to ASG2? Hot Area:
HOTSPOT - You have an Azure subscription that contains the custom roles shown in the following table.In the Azure portal, you plan to create new custom roles by cloning existing roles. The new roles will be configured as shown in the following table.
Which roles can you clone to create each new role? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
SIMULATION - You need to perform a full malware scan every Sunday at 02:00 on a virtual machine named VM1 by using Microsoft Antimalware for Virtual Machines. To complete this task, sign in to the Azure portal.
HOTSPOT - You have an Azure subscription that contains two users named User1 and User2 and the blob containers shown in the following table.Policy1 is configured as shown in the following exhibit.
You assign the roles for storage1 as shown in the following table.
The storage1 account has the following shared access signature (SAS) named SAS1: • Allowed services: Blob • Allowed resource types: Container • Allowed permissions: Read, Write, List, Add, Create • Blob versioning permissions: enables deletion of versions • Allowed blob index permissions: Read/Write • Starr and expiry date/time: o Start: 12/1/2021 o End: 12/31/2021 For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
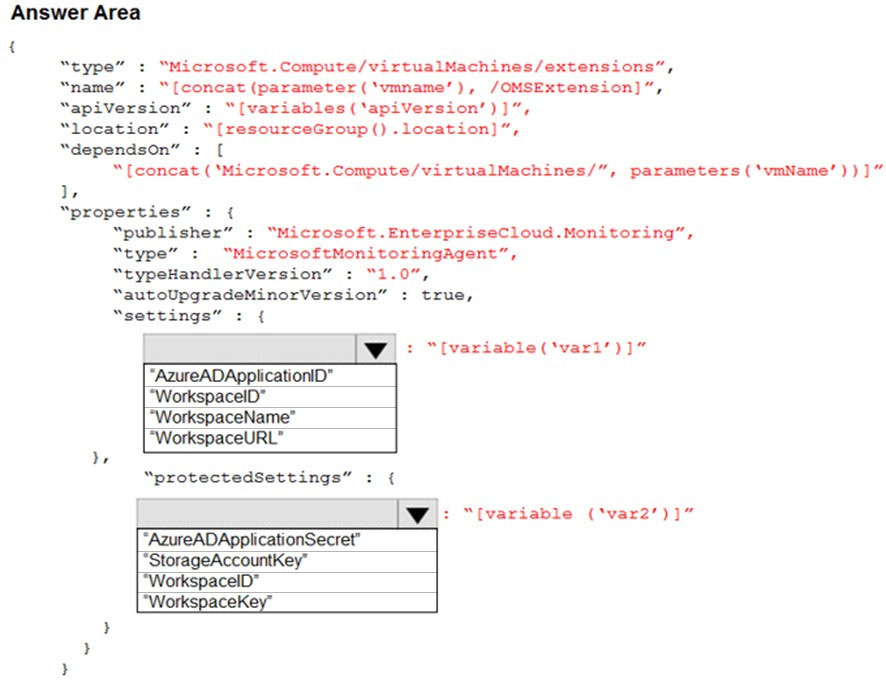
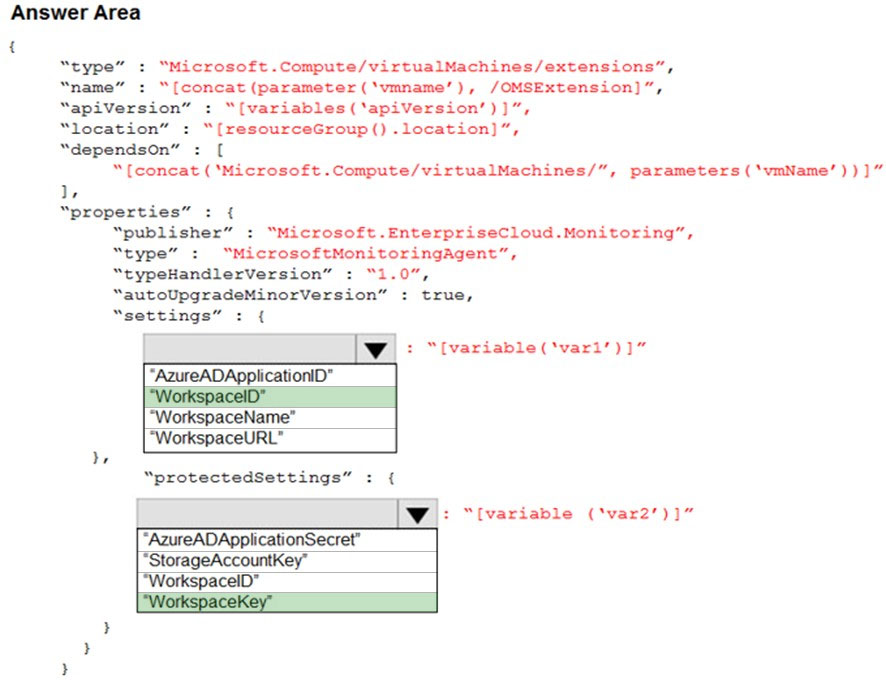
HOTSPOT - You plan to use Azure Log Analytics to collect logs from 200 servers that run Windows Server 2016. You need to automate the deployment of the Microsoft Monitoring Agent to all the servers by using an Azure Resource Manager template. How should you complete the template? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have an Azure subscription that contains an Azure key vault named Vault1. In Vault1, you create a secret named Secret1. An application developer registers an application in Azure Active Directory (Azure AD). You need to ensure that the application can use Secret1. What should you do?
A. In Azure AD, create a role.
B. In Azure Key Vault, create a key.
C. In Azure Key Vault, create an access policy.
D. In Azure AD, enable Azure AD Application Proxy.
You have an Azure subscription. You plan to deploy a new Conditional Access policy named CAPolicy1. You need to use the What if tool to evaluate how CAPolicy1 wall affect users. The solution must minimize the impact of CAPolicy1 on the users. To what should you set the Enable policy setting for CAPolicy1?
A. Off
B. On
C. Report only
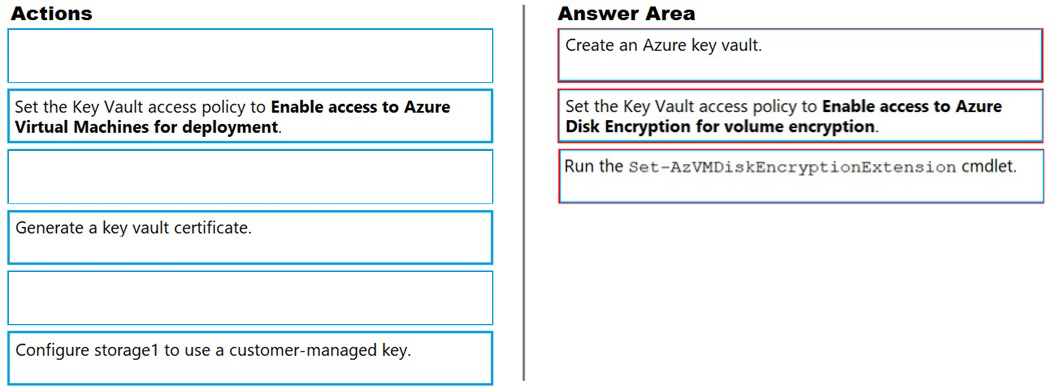
DRAG DROP - You have an Azure Storage account named storage1 and an Azure virtual machine named VM1. VM1 has a premium SSD managed disk. You need to enable Azure Disk Encryption for VM1. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange then in the correct order. Select and Place:
HOTSPOT - You have an Azure Active Directory (Azure AD) tenant that contains two administrative units named AU1 and AU2. Users are assigned to the administrative units as shown in the following table.Users are assigned the roles shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point
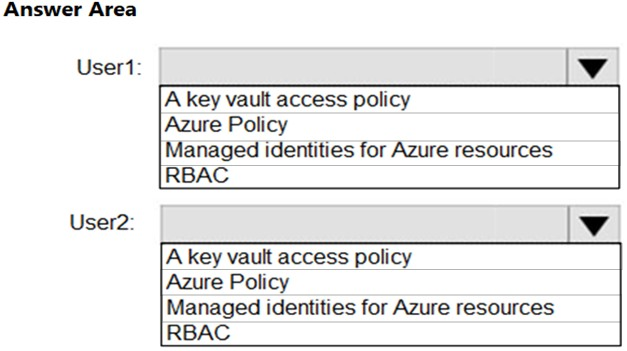
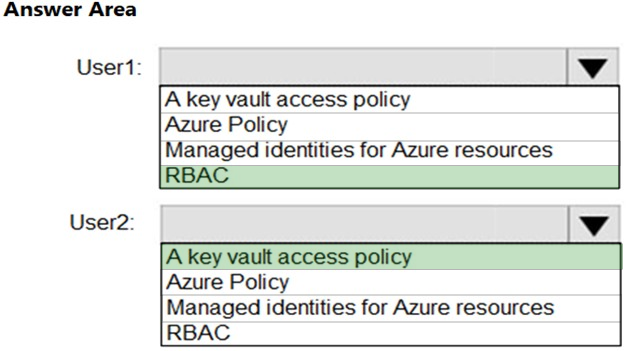
You need to recommend which virtual machines to use to host App1. The solution must meet the technical requirements for KeyVault1. Which virtual machines should you use?
A. VM1 only
B. VM1, VM2, VM3, and VM4
C. VM1 and VM2 only
D. VM1, VM2, and VM4 only
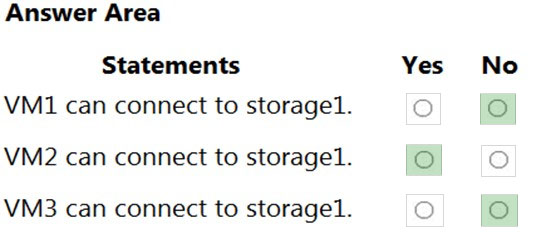
HOTSPOT - You have an Azure subscription that contains a storage account named storage1 and several virtual machines. The storage account and virtual machines are in the same Azure region. The network configurations of the virtual machines are shown in the following table.The virtual network subnets have service endpoints defined as shown in the following table.
You configure the following Firewall and virtual networks settings for storage1: ✑ Allow access from: Selected networks ✑ Virtual networks: VNET3Subnet3 Firewall `" Address range: 52.233.129.0/24
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
Free Access Full AZ-500 Practice Exam Free
Looking for additional practice? Click here to access a full set of AZ-500 practice exam free questions and continue building your skills across all exam domains.
Our question sets are updated regularly to ensure they stay aligned with the latest exam objectives—so be sure to visit often!
Good luck with your AZ-500 certification journey!