AZ-500 Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your AZ-500 certification exam? Start your preparation the smart way with our AZ-500 Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for AZ-500 exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our AZ-500 Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
You have a hybrid configuration of Azure Active Directory (Azure AD) that has Single Sign-On (SSO) enabled. You have an Azure SQL Database instance that is configured to support Azure AD authentication. Database developers must connect to the database instance from the domain joined device and authenticate by using their on-premises Active Directory account. You need to ensure that developers can connect to the instance by using Microsoft SQL Server Management Studio. The solution must minimize authentication prompts. Which authentication method should you recommend?
A. Active Directory – Password
B. Active Directory – Universal with MFA support
C. SQL Server Authentication
D. Active Directory – Integrated
You have an Azure subscription that contains an Azure key vault. You need to configure the maximum number of days for which new keys are valid. The solution must minimize administrative effort. What should you use?
A. Azure Purview
B. Key Vault properties
C. Azure Blueprints
D. Azure Policy
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution. After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a hybrid configuration of Azure Active Directory (Azure AD). You have an Azure HDInsight cluster on a virtual network. You plan to allow users to authenticate to the cluster by using their on-premises Active Directory credentials. You need to configure the environment to support the planned authentication. Solution: You create a site-to-site VPN between the virtual network and the on-premises network. Does this meet the goal?
A. Yes
B. No
You have a web app hosted on an on-premises server that is accessed by using a URL of https://www.contoso.com. You plan to migrate the web app to Azure. You will continue to use https://www.contoso.com. You need to enable HTTPS for the Azure web app. What should you do first?
A. Export the public key from the on-premises server and save the key as a P7b file.
B. Export the private key from the on-premises server and save the key as a PFX file that is encrypted by using TripleDES.
C. Export the public key from the on-premises server and save the key as a CER file.
D. Export the private key from the on-premises server and save the key as a PFX file that is encrypted by using AES256.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution. After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have an Azure subscription named Sub1. You have an Azure Storage account named sa1 in a resource group named RG1. Users and applications access the blob service and the file service in sa1 by using several shared access signatures (SASs) and stored access policies. You discover that unauthorized users accessed both the file service and the blob service. You need to revoke all access to sa1. Solution: You create a new stored access policy. Does this meet the goal?
A. Yes
B. No
You have an Azure subscription that contains the resources shown in the following table.You need to configure storage1 to regenerate keys automatically every 90 days. Which cmdlet should you run?
A. Add-AzKeyVaultflanagedStorageAccount
B. Set-AzStorageAccountManagementPolicy
C. Set-AzStorageAccount
D. Add-AzStorageAccountManagementPolicyAction
You have an Azure Active Directory (Azure AD) tenant that contains a group named Group1. You need to ensure that the members of Group1 sign in by using passwordless authentication. What should you do?
A. Configure the sign-in risk policy.
B. Create a Conditional Access policy.
C. Configure the Microsoft Authenticator authentication method policy.
D. Configure the certificate-based authentication (CBA) policy.
You have an Azure Kubernetes Service (AKS) cluster that will connect to an Azure Container Registry. You need to use the automatically generated service principal for the AKS cluster to authenticate to the Azure Container Registry. What should you create?
A. a secret in Azure Key Vault
B. a role assignment
C. an Azure Active Directory (Azure AD) user
D. an Azure Active Directory (Azure AD) group
Your network contains an on-premises Active Directory domain named corp.contoso.com. You have an Azure subscription named Sub1 that is associated to an Azure Active Directory (Azure AD) tenant named contoso.com. You sync all on-premises identities to Azure AD. You need to prevent users who have a givenName attribute that starts with TEST from being synced to Azure AD. The solution must minimize administrative effort. What should you use?
A. Synchronization Rules Editor
B. Web Service Configuration Tool
C. the Azure AD Connect wizard
D. Active Directory Users and Computers
HOTSPOT - You have an Azure SQL database named DB1 that contains a table named Tablet. You need to configure DB1 to meet the following requirements: • Sensitive data in Table1 must be identified automatically. • Only the first character and last character of the sensitive data must be displayed in query results. Which two features should you configure? To answer, select the features in the answer area. NOTE: Each correct selection is worth one point.
HOTSPOT - You have an Azure AD tenant that contains the groups shown in the following table.You assign licenses to the groups as shown in the following table.
On May1, you delete Group1, Group2, and Group3. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Your on-premises network contains a Hyper-V virtual machine named VM1. You need to use Azure Arc to onboard VM1 to Microsoft Defender for Cloud. What should you install first?
A. the guest configuration agent
B. the Azure Monitor agent
C. the Log Analytics agent
D. the Azure Connected Machine agent
You have an Azure subscription that contains the virtual machines shown in the following table.Which computers will support file integrity monitoring?
A. Computer2 only
B. Computer1 and Computer2 only
C. Computer2 and Computer3 only
D. Computer1, Computer2, and Computer3
You have an Azure subscription that contains an Azure SQL Database logic server named SQL1 and an Azure virtual machine named VM1. VM1 uses a private IP address only. The Firewall and virtual networks settings for SQL1 are shown in the following exhibit.You need to ensure that VM1 can connect to SQL1. The solution must use the principle of least privilege. What should you do?
A. Set Connection Policy to Proxy.
B. Set Allow Azure services and resources to access this server to Yes.
C. Add an existing virtual network.
D. Create a new firewall rule.
HOTSPOT - You have an Azure subscription that contains the resources shown in the following table.SQL1 has the following configurations: • Auditing: Enabled • Audit log destination: storage1, Workspace1 DB1 has the following configurations: • Auditing: Enabled • Audit log destination: storage2 DB2 has auditing disabled. Where are the audit logs for DB1 and DB2 stored? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution. After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have an Azure subscription named Sub1. You have an Azure Storage account named sa1 in a resource group named RG1. Users and applications access the blob service and the file service in sa1 by using several shared access signatures (SASs) and stored access policies. You discover that unauthorized users accessed both the file service and the blob service. You need to revoke all access to sa1. Solution: You regenerate the Azure storage account access keys. Does this meet the goal?
A. Yes
B. No
You have an Azure subscription and the computers shown in the following table.You need to perform a vulnerability scan of the computers by using Microsoft Defender for Cloud. Which computers can you scan?
A. VM1 only
B. VM1 and VM2 only
C. Server1 and VMSS1_0 only
D. VM1, VM2, and Server1 only
E. VM1, VM2, Server 1, and VMSS1_0
You plan to configure Azure Disk Encryption for VM4. Which key vault can you use to store the encryption key?
A. KeyVault1
B. KeyVault2
C. KeyVault3
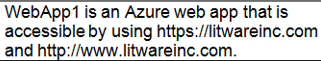
You need to configure WebApp1 to meet the data and application requirements. Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Upload a public certificate.
B. Turn on the HTTPS Only protocol setting.
C. Set the Minimum TLS Version protocol setting to 1.2.
D. Change the pricing tier of the App Service plan.
E. Turn on the Incoming client certificates protocol setting.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution. After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You use Microsoft Defender for Cloud for the centralized policy management of three Azure subscriptions. You use several policy definitions to manage the security of the subscriptions. You need to deploy the policy definitions as a group to all three subscriptions. Solution: You create a policy definition and assignments that are scoped to resource groups. Does this meet the goal?
A. Yes
B. No
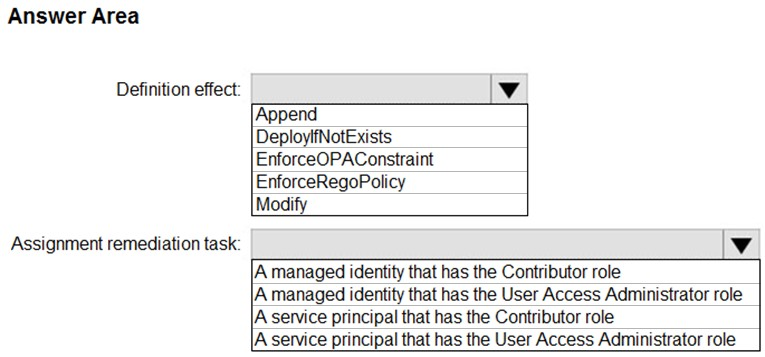
HOTSPOT - You have an Azure subscription. You need to create and deploy an Azure policy that meets the following requirements: ✑ When a new virtual machine is deployed, automatically install a custom security extension. ✑ Trigger an autogenerated remediation task for non-compliant virtual machines to install the extension. What should you include in the policy? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - You have an Azure AD tenant named contoso.com that contains the users shown in the following table.You add enterprise applications to contoso.com as shown in the following table.
You need to identify which users can grant admin consent for App1 and App2. Which users should you identify for each application? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have an Azure subscription named Subscription1. You need to view which security settings are assigned to Subscription1 by default. Which Azure policy or initiative definition should you review?
A. the Audit diagnostic setting policy definition
B. the Enable Monitoring in Azure Security Center initiative definition
C. the Enable Azure Monitor for VMs initiative definition
D. the Azure Monitor solution ‘Security and Audit’ must be deployed policy definition
Your company has Azure subscription linked to their Azure Active Directory (Azure AD) tenant. As a Global administrator for the tenant, part of your responsibilities involves managing Azure Security Center settings. You are currently preparing to create a custom sensitivity label. Solution: You start by creating a custom sensitive information type. Does the solution meet the goal?
A. Yes
B. No
You have an Azure subscription that contains an Azure Active Directory (Azure AD) tenant and a user named User1. The App registrations settings for the tenant are configured as shown in the following exhibit.You plan to deploy an app named App1. You need to ensure that User1 can register App1 in Azure AD. The solution must use the principle of least privilege. Which role should you assign to User1?
A. App Configuration Data Owner for the subscription
B. Managed Application Contributor for the subscription
C. Cloud application administrator in Azure AD
D. Application developer in Azure AD
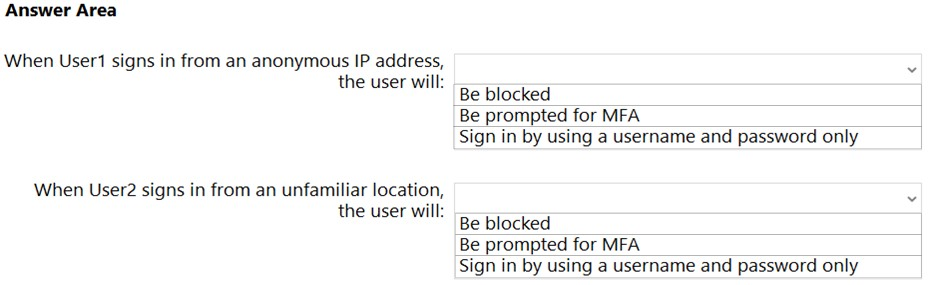
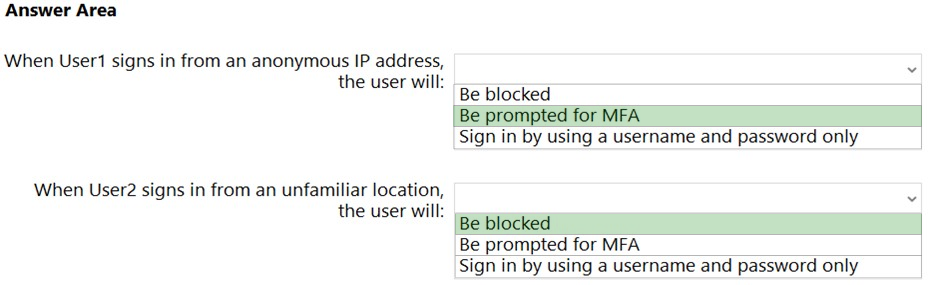
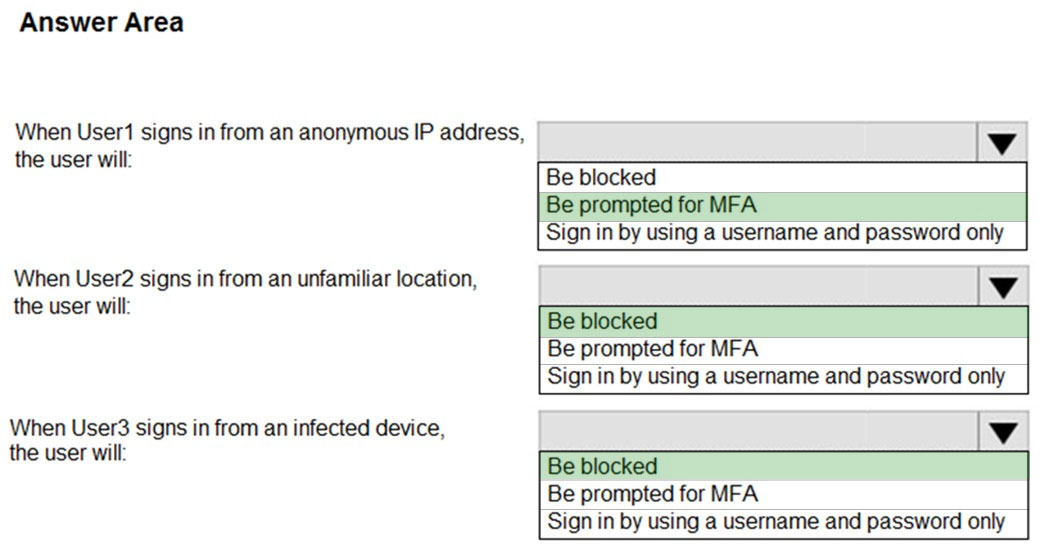
HOTSPOT - You have an Azure Active Directory (Azure AD) tenant that contains the users shown in the following table.You create and enforce an Azure AD Identity Protection sign-in risk policy that has the following settings: ✑ Assignments: Include Group1, exclude Group2 ✑ Conditions: Sign-in risk level: Low and above ✑ Access: Allow access, Require multi-factor authentication You need to identify what occurs when the users sign in to Azure AD. What should you identify for each user? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have an Azure subscription. You plan to create a workflow automation in Azure Security Center that will automatically remediate a security vulnerability. What should you create first?
A. an automation account
B. a managed identity
C. an Azure logic app
D. an Azure function app
E. an alert rule
You are in the process of creating an Azure Kubernetes Service (AKS) cluster. The Azure Kubernetes Service (AKS) cluster must be able to connect to an Azure Container Registry. You want to make sure that Azure Kubernetes Service (AKS) cluster authenticates to the Azure Container Registry by making use of the auto-generated service principal. Solution: You create an Azure Active Directory (Azure AD) role assignment. Does the solution meet the goal?
A. Yes
B. No
HOTSPOT - You have an Azure Active Directory (Azure AD) tenant that contains the users shown in the following table.You create and enforce an Azure AD Identity Protection sign-in risk policy that has the following settings: ✑ Assignments: Include Group1, exclude Group2 ✑ Conditions: Sign-in risk level: Medium and above ✑ Access: Allow access, Require multi-factor authentication You need to identify what occurs when the users sign in to Azure AD. What should you identify for each user? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
SIMULATION - You need to ensure that the events in the NetworkSecurityGroupRuleCounter log of the VNET01-Subnet0-NSG network security group (NSG) are stored in the logs1234578 Azure Storage account for 30 days. To complete this task, sign in to the Azure portal.
You plan to deploy Azure container instances. You have a containerized application that is comprised of two containers: an application container and a validation container. The application container is monitored by the validation container. The validation container performs security checks by making requests to the application container and waiting for responses after every transaction. You need to ensure that the application container and the validation container are scheduled to be deployed together. The containers must communicate to each other only on ports that are not externally exposed. What should you include in the deployment?
A. application security groups
B. network security groups (NSGs)
C. management groups
D. container groups
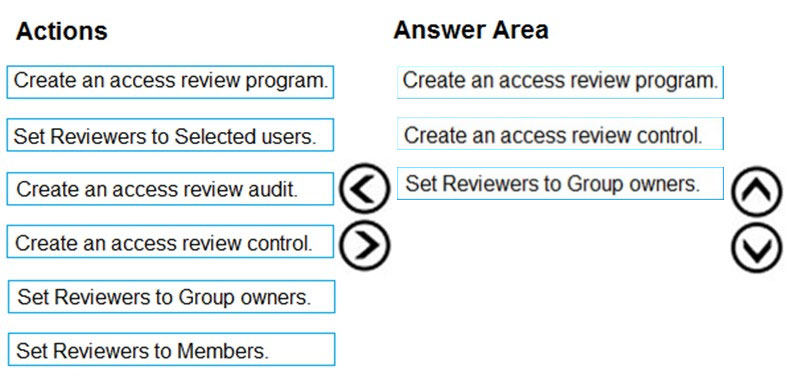
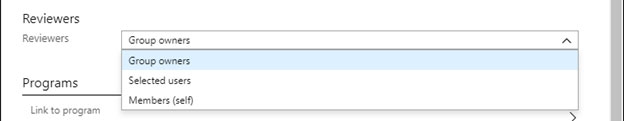
DRAG DROP - You need to configure an access review. The review will be assigned to a new collection of reviews and reviewed by resource owners. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. Select and Place:
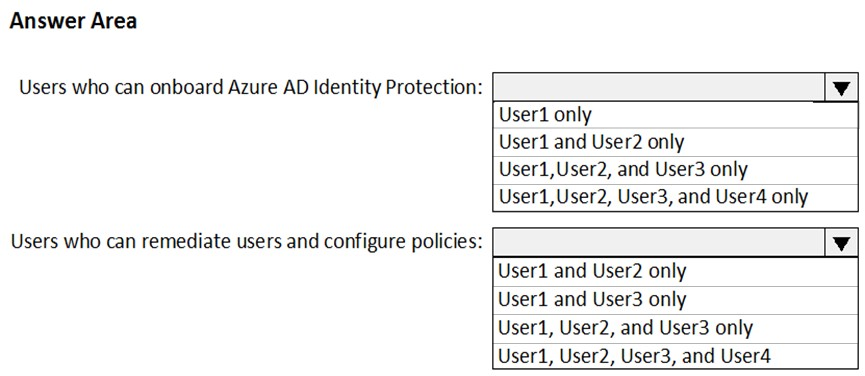
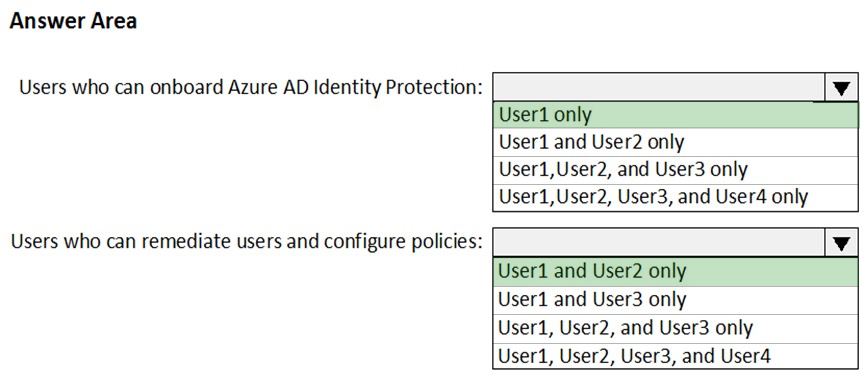
HOTSPOT - You have an Azure subscription named Sub 1 that is associated to an Azure Active Directory (Azure AD) tenant named contoso.com. The tenant contains the users shown in the following table.Each user is assigned an Azure AD Premium P2 license. You plan to onboard and configure Azure AD Identity Protection. Which users can onboard Azure AD Identity Protection, remediate users, and configure policies? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
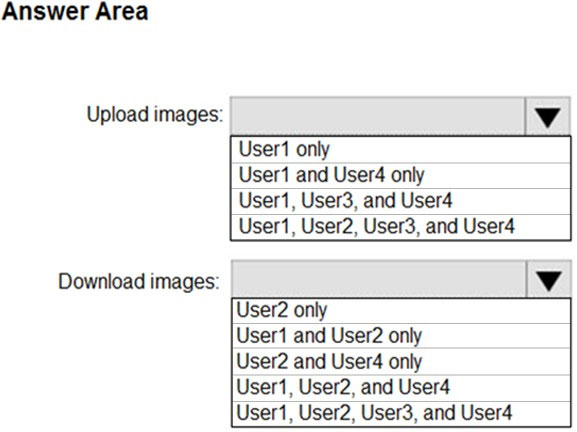
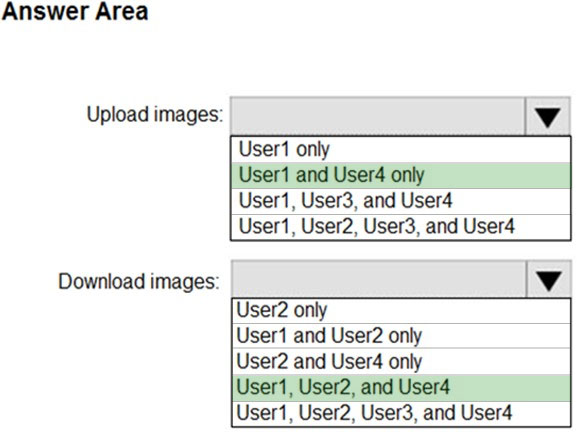
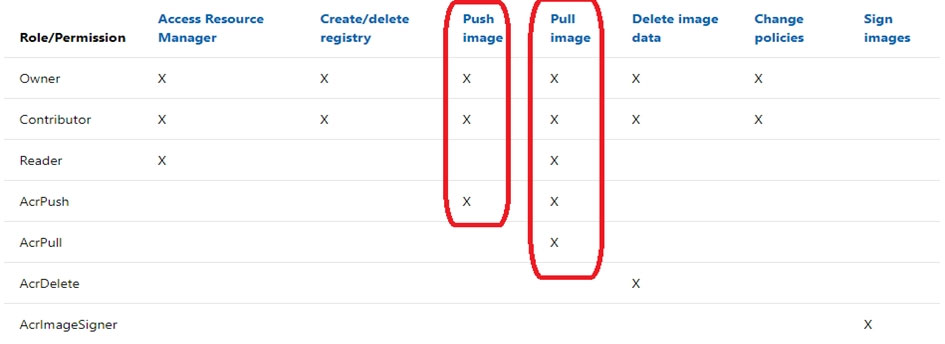
HOTSPOT - You have an Azure Container Registry named Registry1. You add role assignments for Registry1 as shown in the following table.Which users can upload images to Registry1 and download images from Registry1? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have an Azure subscription named Sub1. In Microsoft Defender for Cloud, you have a workflow automation named WF1. WF1 is configured to send an email message to a user named User1. You need to modify WF1 to send email messages to a distribution group named Alerts. What should you use to modify WF1?
A. Azure Logic Apps Designer
B. Azure Application Insights
C. Azure DevOps
D. Azure Monitor
SIMULATION - You need to perform a full malware scan every Sunday at 02:00 on a virtual machine named VM1 by using Microsoft Antimalware for Virtual Machines. To complete this task, sign in to the Azure portal.
You have an Azure subscription that contains the virtual machines shown in the following table.From Azure Security Center, you turn on Auto Provisioning. You deploy the virtual machines shown in the following table.
On which virtual machines is the Microsoft Monitoring Agent installed?
A. VM3 only
B. VM1 and VM3 only
C. VM3 and VM4 only
D. VM1, VM2, VM3, and VM4
You have an Azure subscription named Sub1 that contains the Azure key vaults shown in the following table:In Sub1, you create a virtual machine that has the following configurations: ✑ Name: VM1 ✑ Size: DS2v2 ✑ Resource group: RG1 ✑ Region: West Europe ✑ Operating system: Windows Server 2016 You plan to enable Azure Disk Encryption on VM1. In which key vaults can you store the encryption key for VM1?
A. Vault1 or Vault3 only
B. Vault1, Vault2, Vault3, or Vault4
C. Vault1 only
D. Vault1 or Vault2 only
SIMULATION - You need to ensure that a user named Danny1234578 can sign in to any SQL database on a Microsoft SQL server named web1234578 by using SQL Server Management Studio (SSMS) and Azure Active Directory (Azure AD) credentials. To complete this task, sign in to the Azure portal.
You have Azure Resource Manager templates that you use to deploy Azure virtual machines. You need to disable unused Windows features automatically as instances of the virtual machines are provisioned. What should you use?
A. device configuration policies in Microsoft Intune
B. an Azure Desired State Configuration (DSC) virtual machine extension
C. security policies in Azure Security Center
D. Azure Logic Apps
You plan to deploy an app that will modify the properties of Azure Active Directory (Azure AD) users by using Microsoft Graph. You need to ensure that the app can access Azure AD. What should you configure first?
A. an app registration
B. an external identity
C. a custom role-based access control (RBAC) role
D. an Azure AD Application Proxy
HOTSPOT - You have an Azure subscription that contains a user named Admin1 and an Azure key vault named Vault1. You plan to implement Microsoft Entra Verified ID. You need to create an access policy to ensure that Admin1 has permissions to Vault1 that support the implementation of the Verified ID service. The solution must use the principle of least privilege. Which three key permissions should you select? To answer, select the appropriate permissions in the answer area. NOTE: Each correct selection is worth one point.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution. After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a hybrid configuration of Azure Active Directory (Azure AD). You have an Azure HDInsight cluster on a virtual network. You plan to allow users to authenticate to the cluster by using their on-premises Active Directory credentials. You need to configure the environment to support the planned authentication. Solution: You deploy Azure Active Directory Domain Services (Azure AD DS) to the Azure subscription. Does this meet the goal?
A. Yes
B. No
You have an Azure AD tenant that contains the users shown in the following table.You need to ensure that the users cannot create app passwords. The solution must ensure that User1 can continue to use the Mail and Calendar app. What should you do?
A. Assign User1 the Authentication Policy Administrator role.
B. Enable Azure AD Password Protection.
C. Configure a multi-factor authentication (MFA) registration policy.
D. Create a new app registration.
E. From multi-factor authentication, configure the service settings.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution. After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You use Microsoft Defender for Cloud for the centralized policy management of three Azure subscriptions. You use several policy definitions to manage the security of the subscriptions. You need to deploy the policy definitions as a group to all three subscriptions. Solution: You create an initiative and an assignment that is scoped to a management group. Does this meet the goal?
A. Yes
B. No
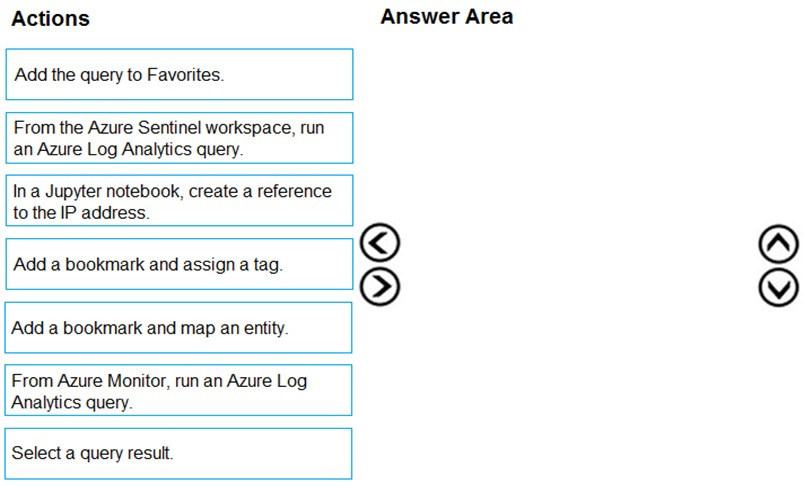
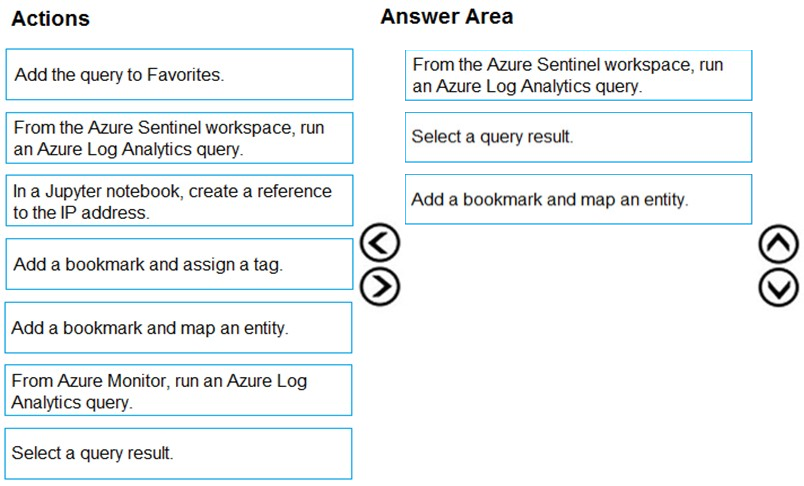
DRAG DROP - You have an Azure Sentinel workspace that has an Azure Active Directory (Azure AD) data connector. You are threat hunting suspicious traffic from a specific IP address. You need to annotate an intermediate event stored in the workspace and be able to reference the IP address when navigating through the investigation graph. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. Select and Place:
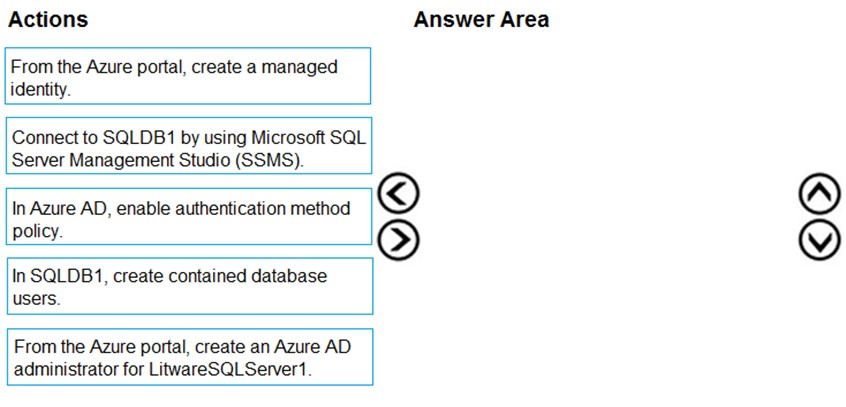
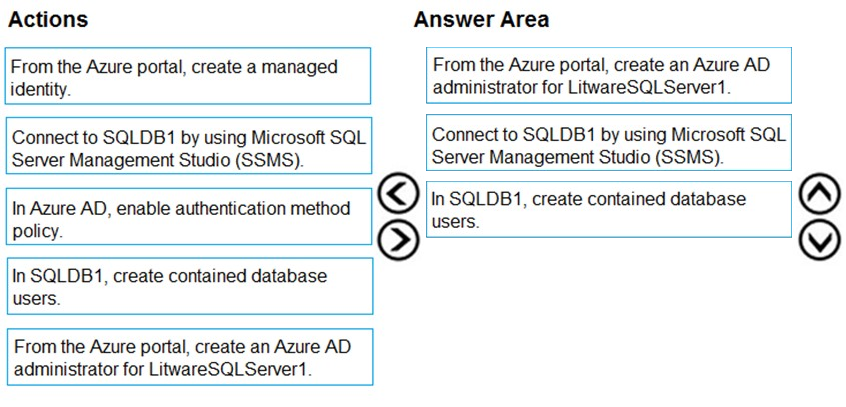
DRAG DROP - You need to configure SQLDB1 to meet the data and application requirements. Which three actions should you recommend be performed in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. Select and Place:
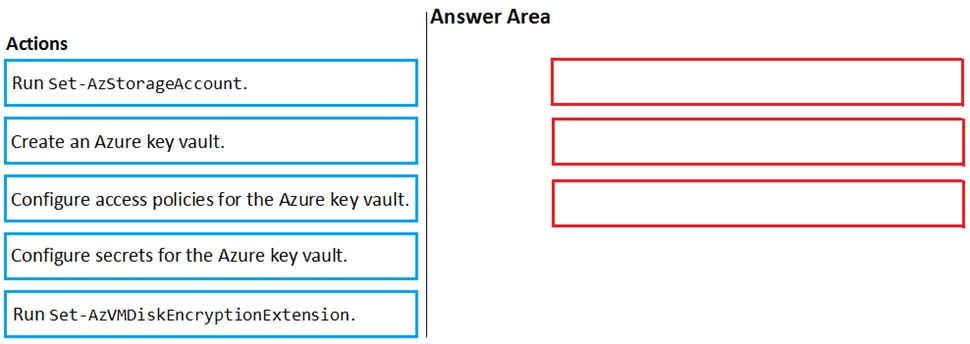
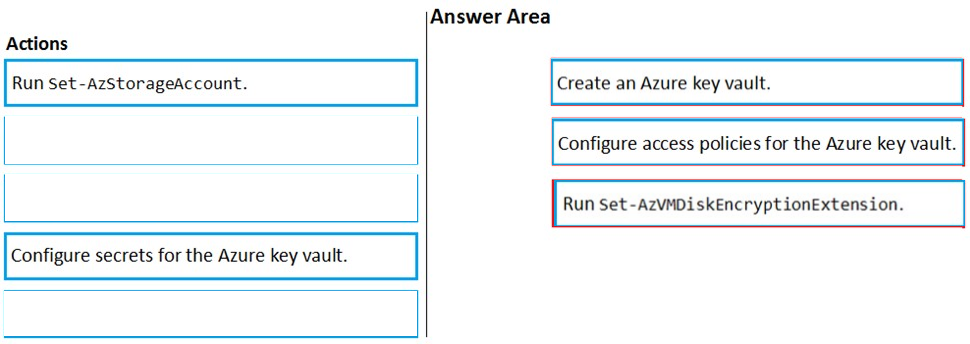
DRAG DROP - You have an Azure subscription named Sub1. Sub1 contains an Azure virtual machine named VM1 that runs Windows Server 2016. You need to encrypt VM1 disks by using Azure Disk Encryption. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. Select and Place:
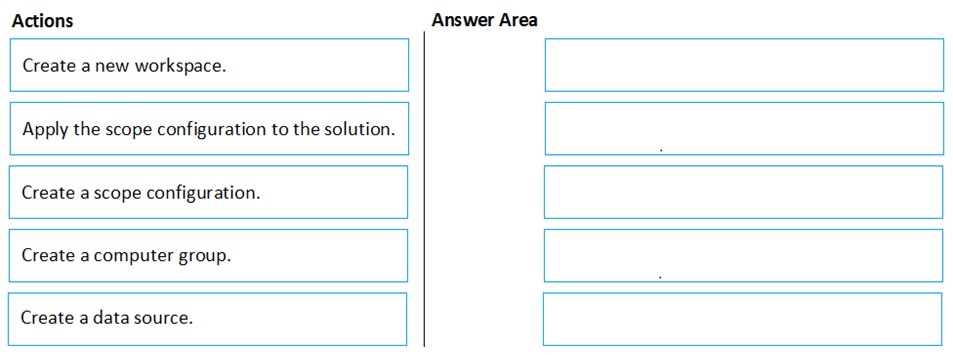
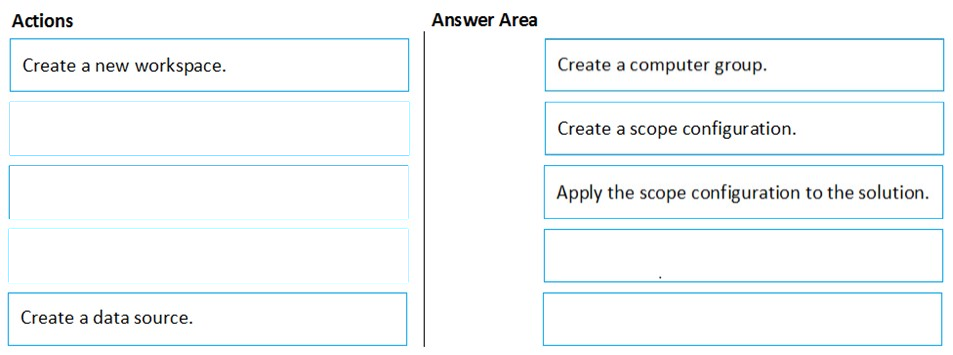
DRAG DROP - You have an Azure subscription named Sub1 that contains an Azure Log Analytics workspace named LAW1. You have 500 Azure virtual machines that run Windows Server 2016 and are enrolled in LAW1. You plan to add the System Update Assessment solution to LAW1. You need to ensure that System Update Assessment-related logs are uploaded to LAW1 from 100 of the virtual machines only. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. Select and Place:
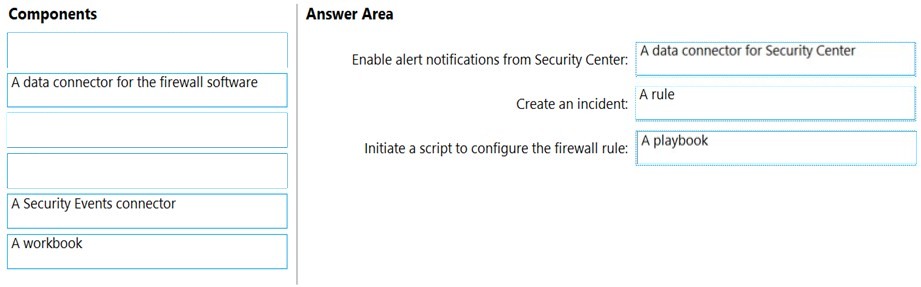
DRAG DROP - You have an Azure subscription that contains the following resources: ✑ A network virtual appliance (NVA) that runs non-Microsoft firewall software and routes all outbound traffic from the virtual machines to the internet ✑ An Azure function that contains a script to manage the firewall rules of the NVA ✑ Azure Security Center standard tier enabled for all virtual machines ✑ An Azure Sentinel workspace ✑ 30 virtual machines You need to ensure that when a high-priority alert is generated in Security Center for a virtual machine, an incident is created in Azure Sentinel and then a script is initiated to configure a firewall rule for the NVA. How should you configure Azure Sentinel to meet the requirements? To answer, drag the appropriate components to the correct requirements. Each component may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point. Select and Place:
Access Full AZ-500 Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete AZ-500 Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our AZ-500 mock test free today—and take a major step toward exam success!