AZ-304 Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your AZ-304 certification exam? Start your preparation the smart way with our AZ-304 Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for AZ-304 exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our AZ-304 Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You are designing an Azure solution for a company that has four departments. Each department will deploy several Azure app services and Azure SQL databases. You need to recommend a solution to report the costs for each department to deploy the app services and the databases. The solution must provide a consolidated view for cost reporting that displays cost broken down by department. Solution: Place all resources in the same resource group. Assign tags to each resource. Does the solution meet the goal?
A. Yes
B. No
You have 100 devices that write performance data to Azure Blob storage. You plan to store and analyze the performance data in an Azure SQL database. You need to recommend a solution to move the performance data to the SQL database. What should you include in the recommendation?
A. Azure Database Migration Service
B. Azure Data Factory
C. Azure Data Box
D. Data Migration Assistant
Your company has an on-premises Windows HPC cluster. The cluster runs a parallel, compute-intensive workload that performs financial risk modeling. You plan to migrate the workload to Azure Batch. You need to design a solution that will support the workload. The solution must meet the following requirements: ✑ Support the large-scale parallel execution of Azure Batch jobs. ✑ Minimize cost. What should you include in the solution?
A. burstable virtual machines
B. low-priority virtual machines
C. Azure virtual machine sizes that support the Message Passing Interface (MPI) API
D. Basic A-series virtual machines
You have an Azure Active Directory (Azure AD) tenant and Windows 10 devices. You configure a conditional access policy as shown in the exhibit. (Click the Exhibit tab.)What is the result of the policy?
A. All users will always be prompted for multi-factor authentication (MFA).
B. Users will be prompted for multi-factor authentication (MFA) only when they sign in from devices that are NOT joined to Azure AD.
C. All users will be able to sign in without using multi-factor authentication (MFA).
D. Users will be prompted for multi-factor authentication (MFA) only when they sign in from devices that are joined to Azure AD.
Your company has the divisions shown in the following table.Sub1 contains an Azure web app that runs an ASP.NET application named App1. App1 uses the Microsoft identity platform (v2.0) to handle user authentication. Users from east.contoso.com can authenticate to App1. You need to recommend a solution to allow users from west.contoso.com to authenticate to App1. What should you recommend for the west.contoso.com Azure AD tenant?
A. a conditional access policy
B. pass-through authentication
C. guest accounts
D. an app registration
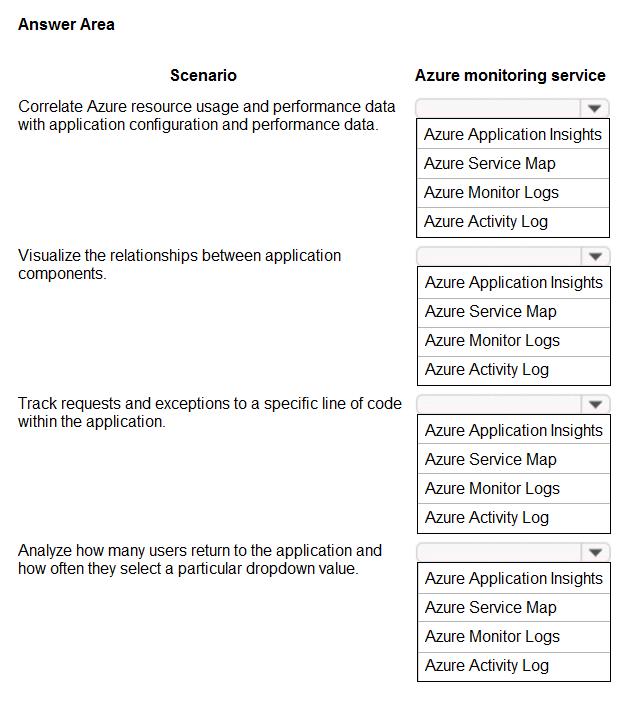
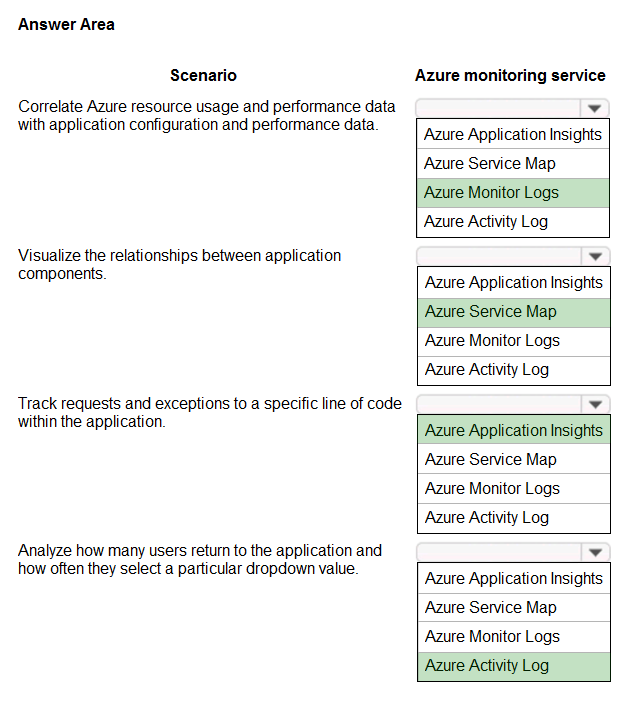
HOTSPOT - You have an Azure App Service Web App that includes Azure Blob storage and an Azure SQL Database instance. The application is instrumented by using the Application Insights SDK. You need to design a monitoring solution for the web app. Which Azure monitoring services should you use? To answer, select the appropriate Azure monitoring services in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have an Azure Storage v2 account named storage1. You plan to archive data to storage1. You need to ensure that the archived data cannot be deleted for five years. The solution must prevent administrators from deleting the data. Solution: You create a file share, and you configure an access policy. Does this meet the goal?
A. Yes
B. No
Your company has the offices shown in the following table.The network contains an Active Directory domain named contoso.com that is synced to Azure Active Directory (Azure AD). All users connect to an Exchange Online. You need to recommend a solution to ensure that all the users use Azure Multi-Factor Authentication (MFA) to connect to Exchange Online from one of the offices. What should you include in the recommendation?
A. a virtual network and two Microsoft Cloud App Security policies
B. a named location and two Microsoft Cloud App Security policies
C. a conditional access policy and two virtual networks
D. a conditional access policy and two named locations
You need to recommend a disaster recovery solution for the back-end tier of the payment processing system. What should you include in the recommendation?
A. Azure Site Recovery
B. an auto-failover group
C. Always On Failover Cluster Instances
D. geo-redundant database backups
You plan to store data in Azure Blob storage for many years. The stored data will be accessed rarely. You need to ensure that the data in Blob storage is always available for immediate access. The solution must minimize storage costs. Which storage tier should you use?
A. Cool
B. Archive
C. Hot
You have an Azure subscription. You need to recommend a solution to provide developers with the ability to provision Azure virtual machines. The solution must meet the following requirements: ✑ Only allow the creation of the virtual machines in specific regions. ✑ Only allow the creation of specific sizes of virtual machines. What should you include in the recommendation?
A. Azure Resource Manager templates
B. Azure Policy
C. conditional access policies
D. role-based access control (RBAC)
You are designing a data protection strategy for Azure virtual machines. All the virtual machines use managed disks. You need to recommend a solution that meets the following requirements: ✑ The use of encryption keys is audited. ✑ All the data is encrypted at rest always. ✑ You manage the encryption keys, not Microsoft. What should you include in the recommendation?
A. client-side encryption
B. Azure Storage Service Encryption
C. Azure Disk Encryption
D. Encrypting File System (EFS)
Your company, named Contoso, Ltd, implements several Azure logic apps that have HTTP triggers. The logic apps provide access to an on-premises web service. Contoso establishes a partnership with another company named Fabrikam, Inc. Fabrikam does not have an existing Azure Active Directory (Azure AD) tenant and uses third-party OAuth 2.0 identity management to authenticate its users. Developers at Fabrikam plan to use a subset of the logic apps to build applications that will integrate with the on-premises web service of Contoso. You need to design a solution to provide the Fabrikam developers with access to the logic apps. The solution must meet the following requirements: ✑ Requests to the logic apps from the developers must be limited to lower rates than the requests from the users at Contoso. ✑ The developers must be able to rely on their existing OAuth 2.0 provider to gain access to the logic apps. ✑ The solution must NOT require changes to the logic apps. ✑ The solution must NOT use Azure AD guest accounts. What should you include in the solution?
A. Azure AD business-to-business (B2B)
B. Azure Front Door
C. Azure API Management
D. Azure AD Application Proxy
You are designing an Azure resource deployment that will use Azure Resource Manager templates. The deployment will use Azure Key Vault to store secrets. You need to recommend a solution to meet the following requirements: ✑ Prevent the IT staff that will perform the deployment from retrieving the secrets directly from Key Vault. ✑ Use the principle of least privilege. Which two actions should you recommend? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Create a Key Vault access policy that allows all get key permissions, get secret permissions, and get certificate permissions.
B. From Access policies in Key Vault, enable access to the Azure Resource Manager for template deployment.
C. Create a Key Vault access policy that allows all list key permissions, list secret permissions, and list certificate permissions.
D. Assign the IT staff a custom role that includes the Microsoft.KeyVault/Vaults/Deploy/Action permission.
E. Assign the Key Vault Contributor role to the IT staff.
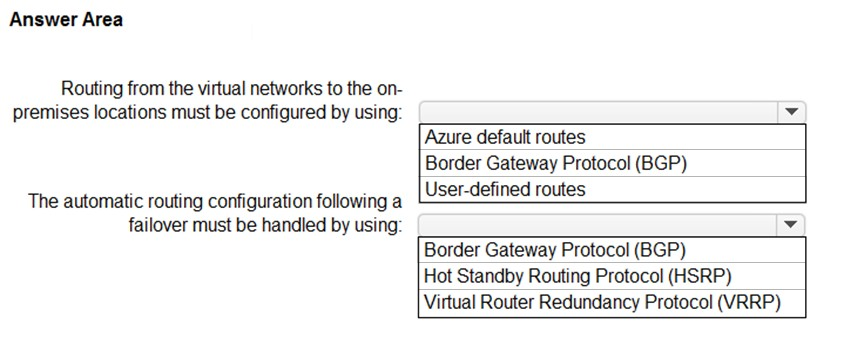
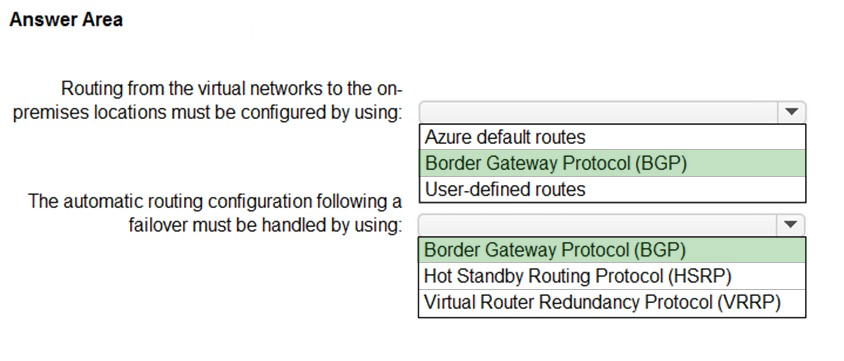
HOTSPOT - Your company has two on-premises sites in New York and Los Angeles and Azure virtual networks in the East US Azure region and the West US Azure region. Each on-premises site has Azure ExpressRoute Global Reach circuits to both regions. You need to recommend a solution that meets the following requirements: ✑ Outbound traffic to the Internet from workloads hosted on the virtual networks must be routed through the closest available on-premises site. ✑ If an on-premises site fails, traffic from the workloads on the virtual networks to the Internet must reroute automatically to the other site. What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
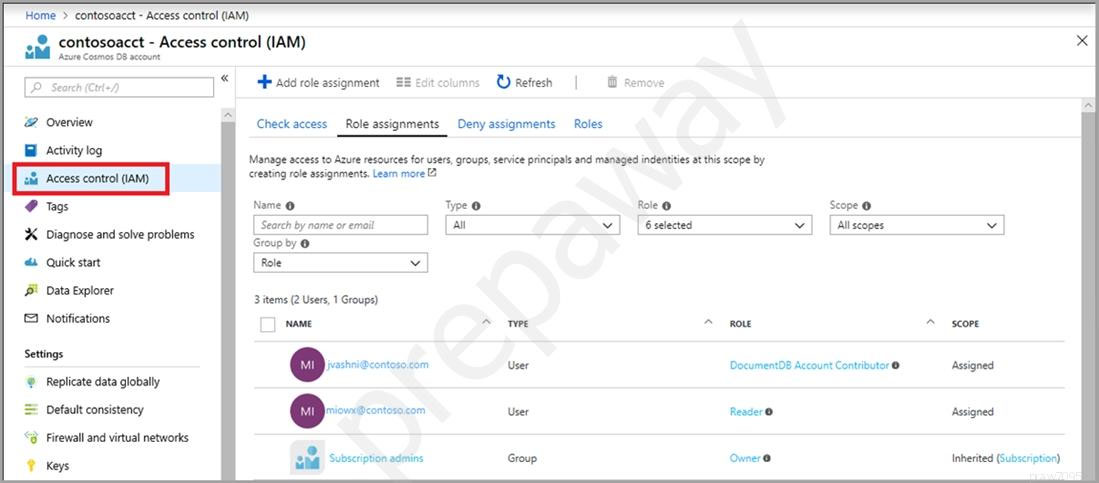
You have an Azure Active Directory (Azure AD) tenant. You plan to deploy Azure Cosmos DB databases that will use the SQL API. You need to recommend a solution to provide specific Azure AD user accounts with read access to the Cosmos DB databases. What should you include in the recommendation?
A. shared access signatures (SAS) and conditional access policies
B. certificates and Azure Key Vault
C. a resource token and an Access control (IAM) role assignment
D. master keys and Azure Information Protection policies
You are designing a SQL database solution. The solution will include 20 databases that will be 20 GB each and have varying usage patterns. You need to recommend a database platform to host the databases. The solution must meet the following requirements: ✑ The compute resources allocated to the databases must scale dynamically. ✑ The solution must meet an SLA of 99.99% uptime. ✑ The solution must have reserved capacity. ✑ Compute charges must be minimized. What should you include in the recommendation?
A. 20 databases on a Microsoft SQL server that runs on an Azure virtual machine in an availability set
B. 20 instances of Azure SQL Database serverless
C. 20 databases on a Microsoft SQL server that runs on an Azure virtual machine
D. an elastic pool that contains 20 Azure SQL databases
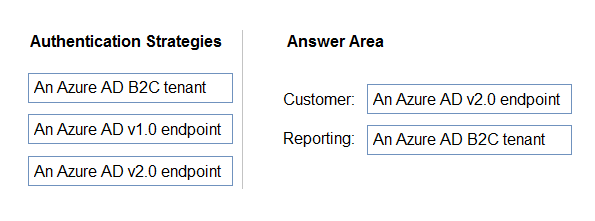
DRAG DROP - A company named Contoso, Ltd. has an Azure Active Directory (Azure AD) tenant that uses the Basic license. You plan to deploy two applications to Azure. The applications have the requirements shown in the following table.Which authentication strategy should you recommend for each application? To answer, drag the appropriate authentication strategies to the correct applications. Each authentication strategy may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point. Select and Place:
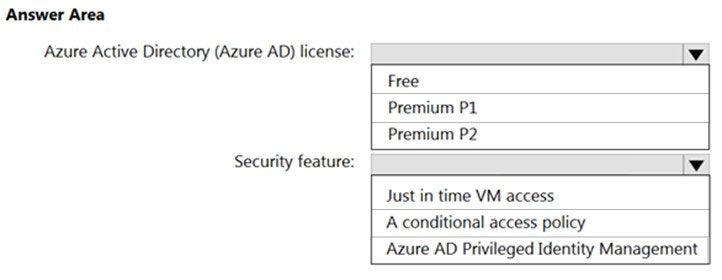
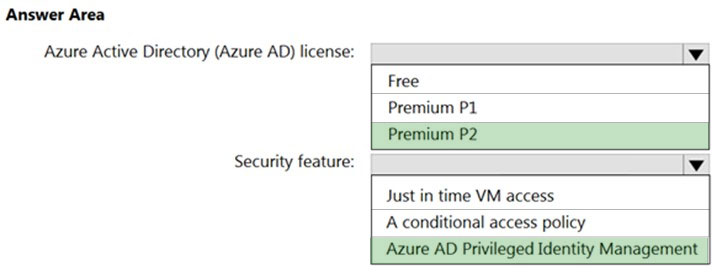
You have an Azure Active Directory (Azure AD) tenant named contoso.com that has a security group named Group1. Group1 is configured for assigned membership. Group1 has 50 members, including 20 guest users. You need to recommend a solution for evaluating the membership of Group1. The solution must meet the following requirements: ✑ The evaluation must be repeated automatically every three months. ✑ Every member must be able to report whether they need to be in Group1. ✑ Users who report that they do not need to be in Group1 must be removed from Group1 automatically. ✑ Users who do not report whether they need to be in Group1 must be removed from Group1 automatically. What should you include in the recommendation?
A. Change the Membership type of Group1 to Dynamic User.
B. Implement Azure AD Privileged Identity Management.
C. Implement Azure AD Identity Protection.
D. Create an access review.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You need to deploy resources to host a stateless web app in an Azure subscription. The solution must meet the following requirements: ✑ Provide access to the full .NET framework. ✑ Provide redundancy if an Azure region fails. ✑ Grant administrators access to the operating system to install custom application dependencies. Solution: You deploy two Azure virtual machines to two Azure regions, and you deploy an Azure Application Gateway. Does this meet the goal?
A. Yes
B. No
You need to recommend a backup solution for the data store of the payment processing system. What should you include in the recommendation?
A. Microsoft System Center Data Protection Manager (DPM)
B. Azure Backup Server
C. Azure SQL long-term backup retention
D. Azure Managed Disks
You need to design a solution that will execute custom C# code in response to an event routed to Azure Event Grid. The solution must meet the following requirements: ✑ The executed code must be able to access the private IP address of a Microsoft SQL Server instance that runs on an Azure virtual machine. ✑ Costs must be minimized. What should you include in the solution?
A. Azure Logic Apps in the integrated service environment
B. Azure Functions in the Dedicated plan and the Basic Azure App Service plan
C. Azure Logic Apps in the Consumption plan
D. Azure Functions in the Consumption plan
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have an Azure Storage account that contains two 1-GB data files named File1 and File2. The data files are set to use the archive access tier. You need to ensure that File1 is accessible immediately when a retrieval request is initiated. Solution: You add a new file share to the storage account. Does this meet the goal?
A. Yes
B. No
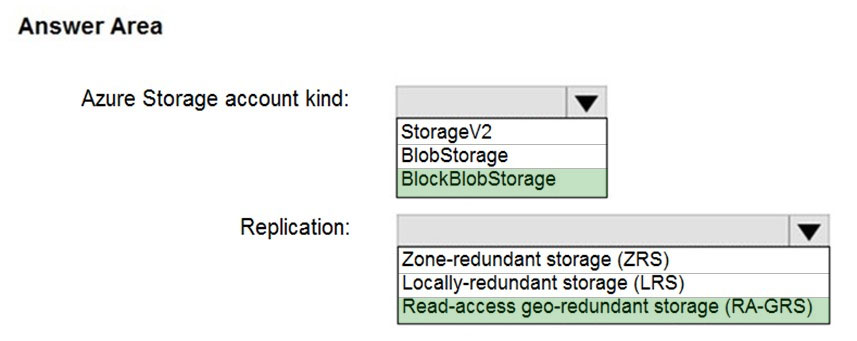
HOTSPOT - You plan to develop a new app that will store business critical data. The app must meet the following requirements: ✑ Prevent new data from being modified for one year. ✑ Minimize read latency. ✑ Maximize data resiliency. You need to recommend a storage solution for the app. What should you recommend? To answer, select the appropriate options in the answer area. Hot Area:
You are designing a microservices architecture that will use Azure Kubernetes Service (AKS) to host pods that run containers. Each pod deployment will host a separate API. Each API will be implemented as a separate service. You need to recommend a solution to make the APIs available to external users from Azure API Management. The solution must meet the following requirements: ✑ Control access to the APIs by using mutual TLS authentication between API Management and the AKS-based APIs. ✑ Provide access to the APIs by using a single IP address. What should you recommend to provide access to the APIs?
A. the LoadBalancer service in AKS
B. custom network security groups (NSGs)
C. the Ingress Controller in AKS
You have 70 TB of files on your on-premises file server. You need to recommend solution for importing data to Azure. The solution must minimize cost. What Azure service should you recommend?
A. Azure StorSimple
B. Azure Batch
C. Azure Data Box
D. Azure Stack Hub
You have a hybrid deployment of Azure Active Directory (Azure AD). You need to recommend a solution to ensure that the Azure AD tenant can be managed only from the computers on your on-premises network. What should you include in the recommendation?
A. a conditional access policy
B. Azure AD roles and administrators
C. Azure AD Application Proxy
D. Azure AD Privileged Identity Management
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You need to deploy resources to host a stateless web app in an Azure subscription. The solution must meet the following requirements: ✑ Provide access to the full .NET framework. ✑ Provide redundancy if an Azure region fails. ✑ Grant administrators access to the operating system to install custom application dependencies. Solution: You deploy a web app in an Isolated App Service plan. Does this meet the goal?
A. Yes
B. No
A company deploys Azure Active Directory (Azure AD) Connect to synchronize identity information from their on-premises Active Directory Domain Services (AD DS) directory to their Azure AD tenant. The identity information that is synchronized includes user accounts, credential hashes for authentication (password sync), and group memberships. The company plans to deploy several Windows and Linux virtual machines (VMs) to support their applications. The VMs have the following requirements: ✑ Support domain join, LDAP read, LDAP bind, NTLM and Kerberos authentication, and Group Policy. ✑ Allow users to sign in to the domain using their corporate credentials and connect remotely to the VM by using Remote Desktop. You need to support the VM deployment. Which service should you use?
A. Active Directory Federation Services (AD FS)
B. Azure AD Privileged Identity Management
C. Azure Managed Identity
D. Azure AD Domain Services
You plan to move a web application named App! from an on-premises data center to Azure. App1 depends on a custom COM component that is installed on the host server. You need to recommend a solution to host App1 in Azure. The solution must meet the following requirements: ✑ App1 must be available to users if an Azure data center becomes unavailable. ✑ Costs must be minimized. What should you include in the recommendation?
A. In two Azure regions, deploy a load balancer and a virtual machine scale set.
B. In two Azure regions, deploy a Traffic Manager profile and a web app.
C. In two Azure regions, deploy a load balancer and a web app.
D. Deploy a load balancer and a virtual machine scale set across two availability zones.
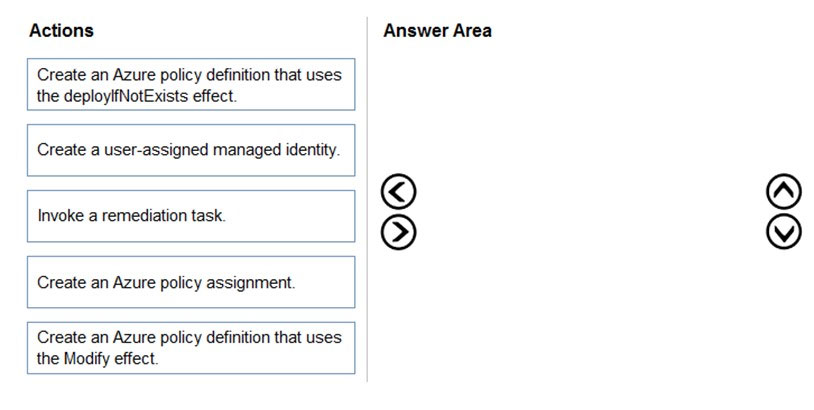
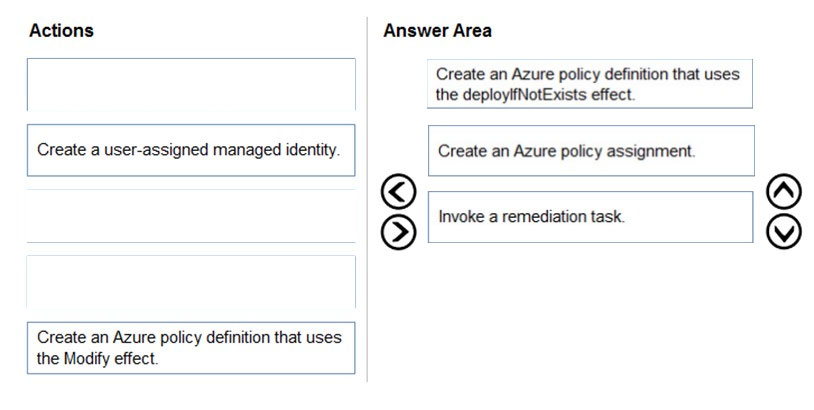
DRAG DROP - You need to configure an Azure policy to ensure that the Azure SQL databases have TDE enabled. The solution must meet the security and compliance requirements. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. Select and Place:
You have an Azure subscription that contains a storage account. An application sometimes writes duplicate files to the storage account. You have a PowerShell script that identifies and deletes duplicate files in the storage account. Currently, the script is run manually after approval from the operations manager. You need to recommend a serverless solution that performs the following actions: ✑ Runs the script once an hour to identify whether duplicate files exist ✑ Sends an email notification to the operations manager requesting approval to delete the duplicate files ✑ Processes an email response from the operations manager specifying whether the deletion was approved ✑ Runs the script if the deletion was approved What should you include in the recommendation?
A. Azure Logic Apps and Azure Functions
B. Azure Pipelines and Azure Service Fabric
C. Azure Logic Apps and Azure Event Grid
D. Azure Functions and Azure Batch
You plan to deploy 10 applications to Azure. The applications will be deployed to two Azure Kubernetes Service (AKS) clusters. Each cluster will be deployed to a separate Azure region. The application deployment must meet the following requirements: ✑ Ensure that the applications remain available if a single AKS cluster fails. ✑ Ensure that the connection traffic over the internet is encrypted by using SSL without having to configure SSL on each container. Which Azure service should you include in the recommendation?
A. AKS ingress controller
B. Azure Load Balancer
C. Azure Traffic Manager
D. Azure Front Door
You deploy an Azure virtual machine that runs an ASP.NET application. The application will be accessed from the internet by the users at your company. You need to recommend a solution to ensure that the users are pre-authenticated by using their Azure Active Directory (Azure AD) account before they can connect to the ASP.NET application. What should you include in the recommendation?
A. a public Azure Load Balancer
B. Azure Application Gateway
C. Azure Traffic Manager
D. an Azure AD enterprise application
Your company has offices in the United States, Europe, Asia, and Australia. You have an on-premises app named App1 that uses Azure Table storage. Each office hosts a local instance of App1. You need to upgrade the storage for App1. The solution must meet the following requirements: ✑ Enable simultaneous write operations in multiple Azure regions. ✑ Ensure that write latency is less than 10 ms. ✑ Support indexing on all columns. Minimize development effort.Which data platform should you use?
A. Azure SQL Database
B. Azure SQL Managed Instance
C. Azure Cosmos DB
D. Table storage that uses geo-zone-redundant storage (GZRS) replication
You need to design a highly available Azure SQL database that meets the following requirements: ✑ Failover between replicas of the database must occur without any data loss. ✑ The database must remain available in the event of a zone outage. ✑ Costs must be minimized. Which deployment option should you use?
A. Azure SQL Database Standard
B. Azure SQL Database Serverless
C. Azure SQL Database Business Critical
D. Azure SQL Database Basic
DRAG DROP - You are designing a virtual machine that will run Microsoft SQL Server and will contain two data disks. The first data disk will store log files, and the second data disk will store data. Both disks are P40 managed disks. You need to recommend a caching policy for each disk. The policy must provide the best overall performance for the virtual machine while preserving integrity of the SQL data and logs. Which caching policy should you recommend for each disk? To answer, drag the appropriate policies to the correct disks. Each policy may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. Select and Place:
You plan to deploy an application that will run in a Linux-based Docker container. You need to recommend a solution to host the application in Azure. The solution must meet the following requirements: ✑ Support a custom domain name and an associated SSL certificate. ✑ Scale-out automatically based on demand. ✑ Minimize administrative effort and costs. What should you include in the recommendation?
A. Azure App Service
B. Azure Container Instances
C. an Azure virtual machine
D. Azure Kubernetes Service (AKS)
You are designing an Azure solution. The network traffic for the solution must be securely distributed by providing the following features: ✑ HTTPS protocol ✑ Round robin routing ✑ SSL offloading You need to recommend a load balancing option. What should you recommend?
A. Azure Load Balancer
B. Azure Internal Load Balancer (ILB)
C. Azure Traffic Manager
D. Azure Application Gateway
You are reviewing an Azure architecture as shown in the Architecture exhibit. (Click the Architecture tab.)The estimated monthly costs for the architecture are shown in the Costs exhibit. (Click the Costs tab.)
The log files are generated by user activity to Apache web servers. The log files are in a consistent format. Approximately 1 GB of logs are generated per day. Microsoft Power BI is used to display weekly reports of the user activity. You need to recommend a solution to minimize costs while maintaining the functionality of the architecture. What should you recommend?
A. Replace Azure Synapse Analytics and Azure Analysis Services with SQL Server on an Azure virtual machine.
B. Replace Azure Synapse Analytics with Azure SQL Database Hyperscale.
C. Replace Azure Data Factory with CRON jobs that use AzCopy.
D. Replace Azure Databricks with Azure Machine Learning.
HOTSPOT - You are designing an access policy for your company. Occasionally, the developers at the company must stop, start, and restart Azure virtual machines. The development team changes often. You need to recommend a solution to provide the developers with the required access to the virtual machines. The solution must meet the following requirements: ✑ Provide permissions only when needed. ✑ Use the principle of least privilege. ✑ Minimize costs. What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You need to recommend a solution to deploy containers that run an application. The application has two tiers. Each tier is implemented as a separate Docker Linux-based image. The solution must meet the following requirements: ✑ The front-end tier must be accessible by using a public IP address on port 80. ✑ The backend tier must be accessible by using port 8080 from the front-end tier only. ✑ Both containers must be able to access the same Azure file share. ✑ If a container fails, the application must restart automatically. ✑ Costs must be minimized. What should you recommend using to host the application?
A. Azure Kubernetes Service (AKS)
B. Azure Service Fabric
C. Azure Container instances
You plan to migrate App1 to Azure. You need to recommend a network connectivity solution for the Azure Storage account that will host the App1 data. The solution must meet the security and compliance requirements. What should you include in the recommendation?
A. a private endpoint
B. a service endpoint that has a service endpoint policy
C. Azure public peering for an ExpressRoute circuit
D. Microsoft peering for an ExpressRoute circuit
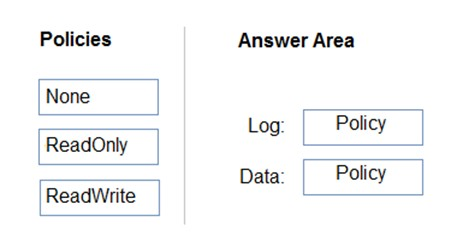
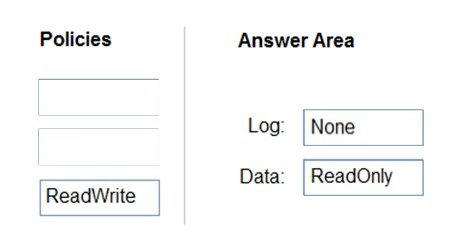
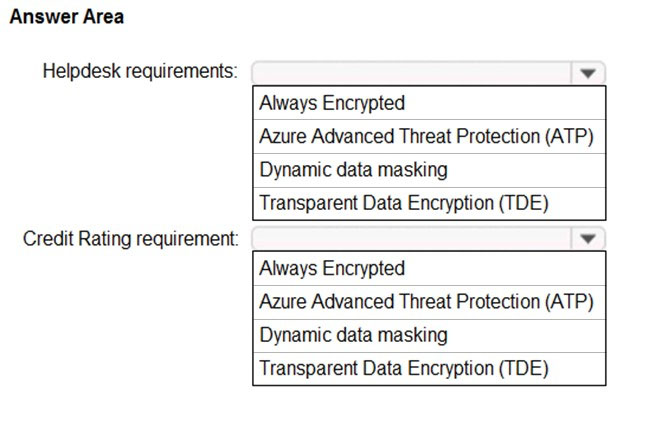
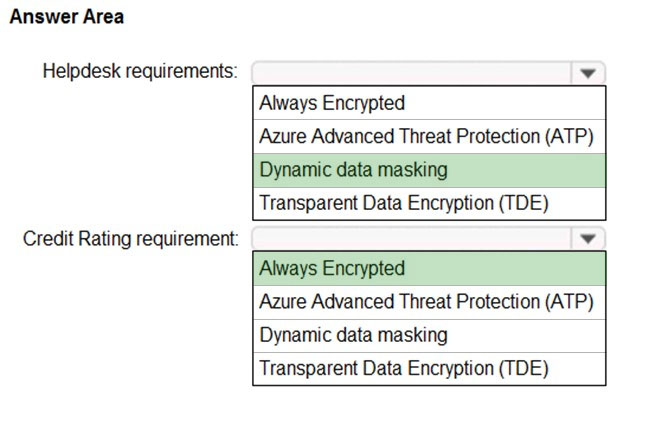
HOTSPOT - You have an Azure SQL database named DB1. You need to recommend a data security solution for DB1. The solution must meet the following requirements: ✑ When helpdesk supervisors query DB1, they must see the full number of each credit card. ✑ When helpdesk operators query DB1, they must see only the last four digits of each credit card number. ✑ A column named Credit Rating must never appear in plain text within the database system, and only client applications must be able to decrypt the Credit Rating column. What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You plan to run an image rendering workload in Azure. The workload uses parallel compute processes. What is the best service to use to run the workload? More than one answer choice may achieve the goal. Select the BEST answer.
A. an Azure virtual machine scale set
B. Azure Function App
C. Azure Kubernetes Service (AKS)
D. Azure Batch
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have an Azure Storage v2 account named storage1. You plan to archive data to storage1. You need to ensure that the archived data cannot be deleted for five years. The solution must prevent administrators from deleting the data. Solution: You create a file share and snapshots. Does this meet the goal?
A. Yes
B. No
You have an Azure web app that uses an Azure key vault named KeyVault1 in the West US Azure region. You are designing a disaster recovery plan for KeyVault1. You plan to back up the keys in KeyVault1. You need to identify to where you can restore the backup. What should you identify?
A. KeyVault1 only
B. the same region only
C. the same geography only
D. any region worldwide
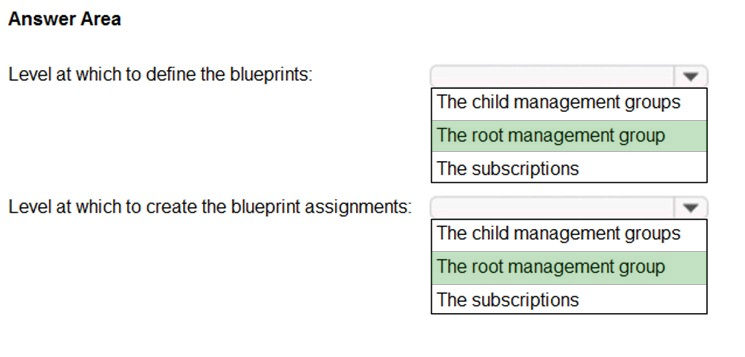
HOTSPOT - You plan to create an Azure environment that will contain a root management group and 10 child management groups. Each child management group will contain five Azure subscriptions. You plan to have between 10 and 30 resource groups in each subscription. You need to design an Azure governance solution. The solution must meet the following requirements: ✑ Use Azure Blueprints to control governance across all the subscriptions and resource groups. ✑ Ensure that Blueprints-based configurations are consistent across all the subscriptions and resource groups. ✑ Minimize the number of blueprint definitions and assignments. What should you include in the solution? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You are developing a sales application that will contain several Azure cloud services and will handle different components of a transaction. Different cloud services will process customer orders, billing, payment, inventory, and shipping. You need to recommend a solution to enable the cloud services to asynchronously communicate transaction information by using REST messages. What should you include in the recommendation?
A. Azure Service Fabric
B. Azure Blob storage
C. Azure Queue storage
D. Azure Traffic Manager
You need to recommend a strategy for migrating the database content of WebApp1 to Azure. What should you include in the recommendation?
A. Use Azure Site Recovery to replicate the SQL servers to Azure.
B. Copy the BACPAC file that contains the Azure SQL database files to Azure Blob storage.
C. Use SQL Server transactional replication.
D. Copy the VHD that contains the Azure SQL database files to Azure Blob storage.
Access Full AZ-304 Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete AZ-304 Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our AZ-304 mock test free today—and take a major step toward exam success!