AZ-204 Practice Test Free – 50 Real Exam Questions to Boost Your Confidence
Preparing for the AZ-204 exam? Start with our AZ-204 Practice Test Free – a set of 50 high-quality, exam-style questions crafted to help you assess your knowledge and improve your chances of passing on the first try.
Taking a AZ-204 practice test free is one of the smartest ways to:
- Get familiar with the real exam format and question types
- Evaluate your strengths and spot knowledge gaps
- Gain the confidence you need to succeed on exam day
Below, you will find 50 free AZ-204 practice questions to help you prepare for the exam. These questions are designed to reflect the real exam structure and difficulty level. You can click on each Question to explore the details.
A company is developing a solution that allows smart refrigerators to send temperature information to a central location. The solution must receive and store messages until they can be processed. You create an Azure Service Bus instance by providing a name, pricing tier, subscription, resource group, and location. You need to complete the configuration. Which Azure CLI or PowerShell command should you run?
A.

B.

C.

D.

You need to store the user agreements. Where should you store the agreement after it is completed?
A. Azure Storage queue
B. Azure Event Hub
C. Azure Service Bus topic
D. Azure Event Grid topic
You need to ensure that the solution can meet the scaling requirements for Policy Service. Which Azure Application Insights data model should you use?
A. an Application Insights dependency
B. an Application Insights event
C. an Application Insights trace
D. an Application Insights metric
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You are developing an Azure solution to collect point-of-sale (POS) device data from 2,000 stores located throughout the world. A single device can produce 2 megabytes (MB) of data every 24 hours. Each store location has one to five devices that send data. You must store the device data in Azure Blob storage. Device data must be correlated based on a device identifier. Additional stores are expected to open in the future. You need to implement a solution to receive the device data. Solution: Provision an Azure Event Grid. Configure event filtering to evaluate the device identifier. Does the solution meet the goal?
A. Yes
B. No
You are developing a road tollway tracking application that sends tracking events by using Azure Event Hubs using premium tier. Each road must have a throttling policy uniquely assigned. You need to configure the event hub to allow for per-road throttling. What should you do?
A. Use a unique consumer group for each road.
B. Ensure each road stores events in a different partition.
C. Ensure each road has a unique connection string.
D. Use a unique application group for each road.
You develop and deploy a web app to Azure App Service. The Azure App Service uses a Basic plan in a single region. Users report that the web app is responding slow. You must capture the complete call stack to help identify performance issues in the code. Call stack data must be correlated across app instances. You must minimize cost and impact to users on the web app. You need to capture the telemetry. Which three actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Restart all apps in the App Service plan.
B. Enable Application Insights site extensions.
C. Upgrade the Azure App Service plan to Premium.
D. Enable Profiler.
E. Enable the Always On setting for the app service.
F. Enable Snapshot debugger.
G. Enable remote debugging.
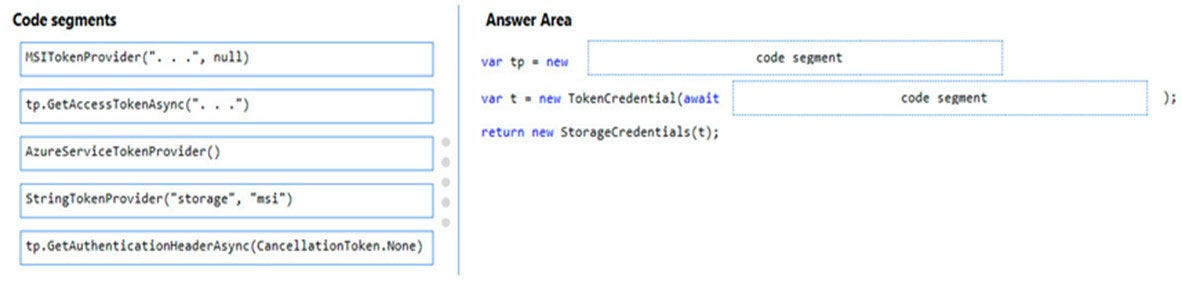
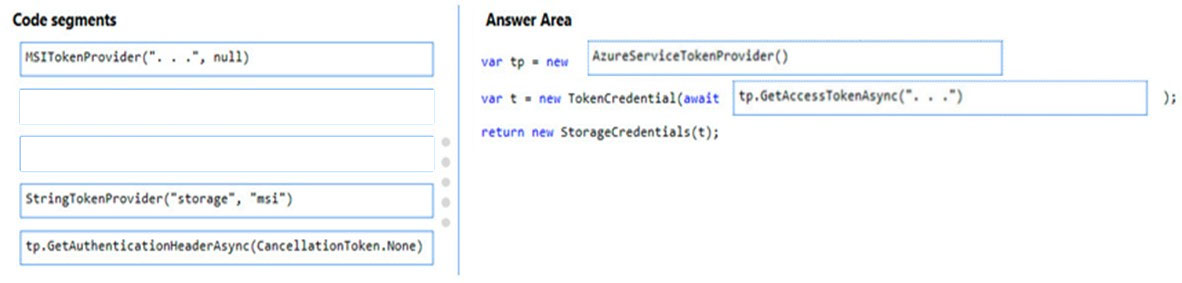
DRAG DROP - You are developing a web service that will run on Azure virtual machines that use Azure Storage. You configure all virtual machines to use managed identities. You have the following requirements: • Secret-based authentication mechanisms are not permitted for accessing an Azure Storage account. • Must use only Azure Instance Metadata Service endpoints. You need to write code to retrieve an access token to access Azure Storage. To answer, drag the appropriate code segments to the correct locations. Each code segment may be used once or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
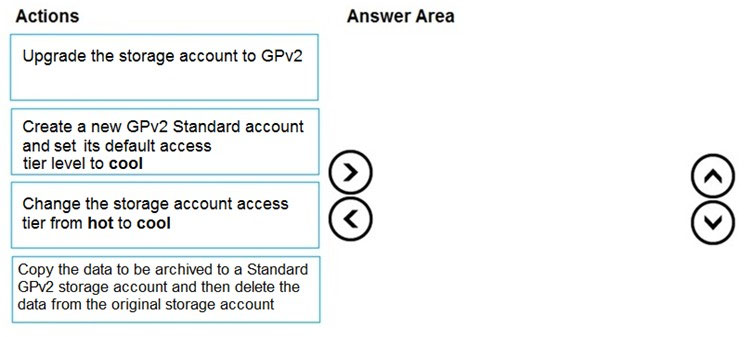
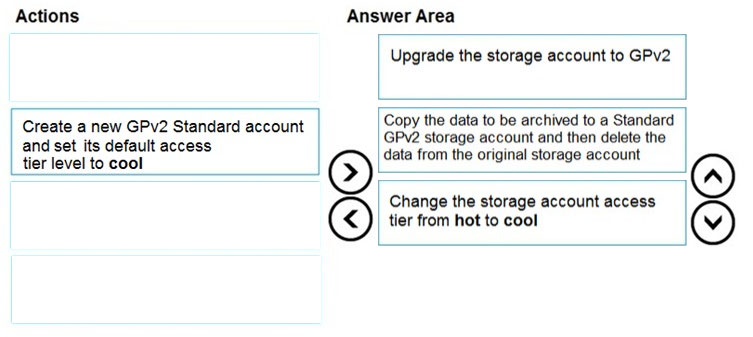
DRAG DROP - You are maintaining an existing application that uses an Azure Blob GPv1 Premium storage account. Data older than three months is rarely used. Data newer than three months must be available immediately. Data older than a year must be saved but does not need to be available immediately. You need to configure the account to support a lifecycle management rule that moves blob data to archive storage for data not modified in the last year. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. Select and Place:
HOTSPOT - You need to retrieve the database connection string. Which values should you use? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
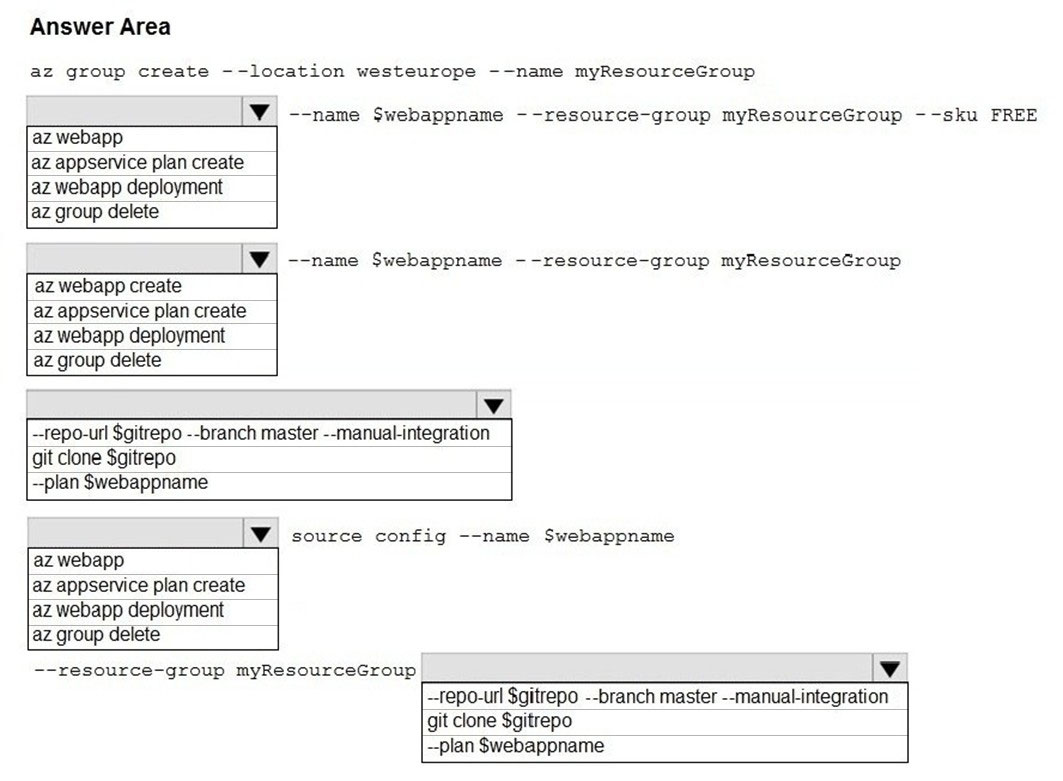
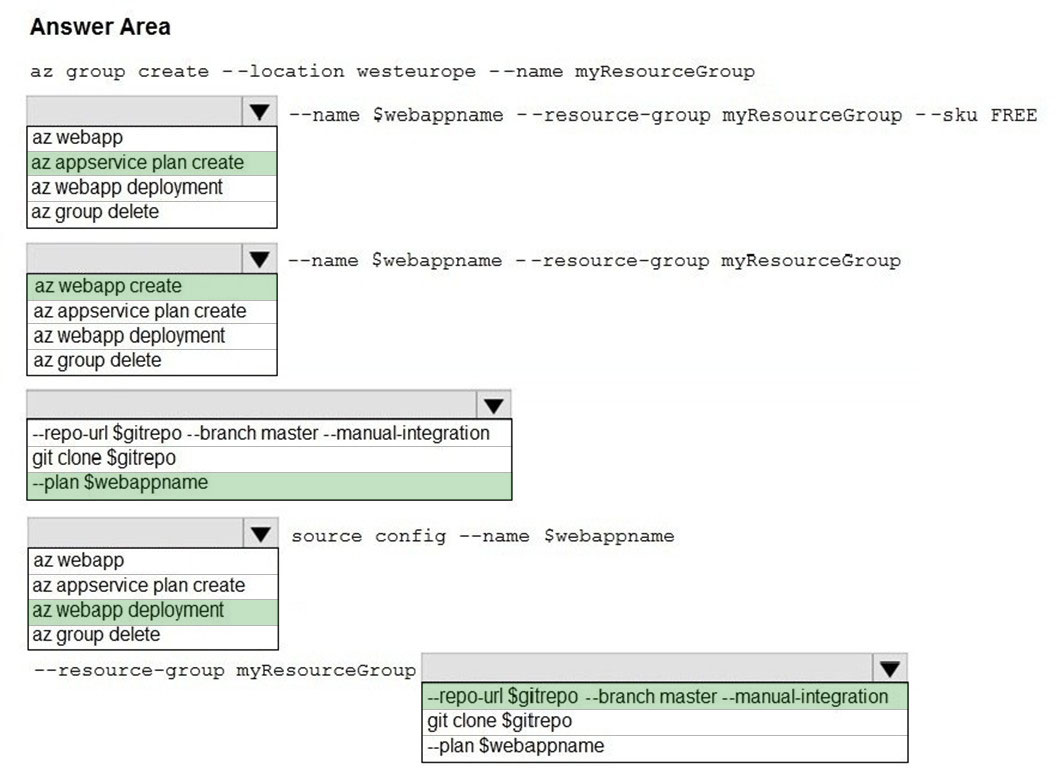
HOTSPOT - You are creating a CLI script that creates an Azure web app and related services in Azure App Service. The web app uses the following variables:You need to automatically deploy code from GitHub to the newly created web app. How should you complete the script? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You are configuring a web app that delivers streaming video to users. The application makes use of continuous integration and deployment. You need to ensure that the application is highly available and that the users' streaming experience is constant. You also want to configure the application to store data in a geographic location that is nearest to the user. Solution: You include the use of Azure Redis Cache in your design. Does the solution meet the goal?
A. Yes
B. No
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You are developing an Azure solution to collect point-of-sale (POS) device data from 2,000 stores located throughout the world. A single device can produce 2 megabytes (MB) of data every 24 hours. Each store location has one to five devices that send data. You must store the device data in Azure Blob storage. Device data must be correlated based on a device identifier. Additional stores are expected to open in the future. You need to implement a solution to receive the device data. Solution: Provision an Azure Service Bus. Configure a topic to receive the device data by using a correlation filter. Does the solution meet the goal?
A. Yes
B. No
A company is developing a solution that allows smart refrigerators to send temperature information to a central location. The solution must receive and store messages until they can be processed. You create an Azure Service Bus instance by providing a name, pricing tier, subscription, resource group, and location. You need to complete the configuration. Which Azure CLI or PowerShell command should you run?
A.

B.

C.

D.

After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You develop a software as a service (SaaS) offering to manage photographs. Users upload photos to a web service which then stores the photos in Azure Storage Blob storage. The storage account type is General-purpose V2. When photos are uploaded, they must be processed to produce and save a mobile-friendly version of the image. The process to produce a mobile-friendly version of the image must start in less than one minute. You need to design the process that starts the photo processing. Solution: Create an Azure Function app that uses the Consumption hosting model and that is triggered from the blob upload. Does the solution meet the goal?
A. Yes
B. No
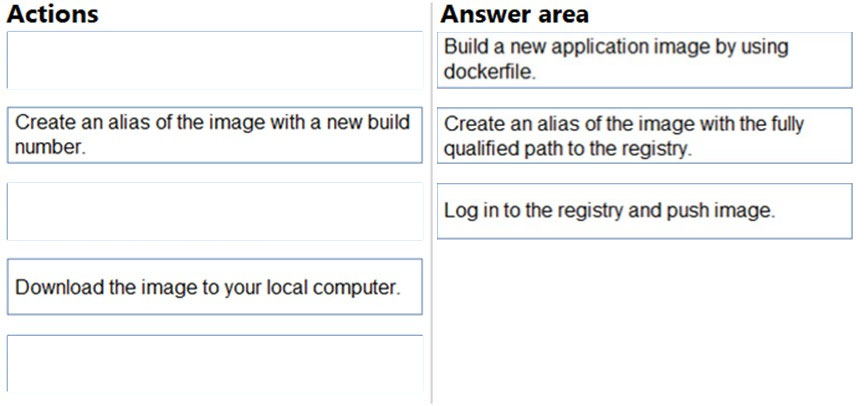
DRAG DROP - You need to deploy a new version of the LabelMaker application to ACR. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. Select and Place:
Case study - This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided. To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study. At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section. To start the case study - To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. When you are ready to answer a question, click the Question button to return to the question. Background - VanArsdel, Ltd. is a global office supply company. The company is based in Canada and has retail store locations across the world. The company is developing several cloud-based solutions to support their stores, distributors, suppliers, and delivery services. Current environment - Corporate website - The company provides a public website located at http://www.vanarsdelltd.com. The website consists of a React JavaScript user interface, HTML, CSS, image assets, and several APIs hosted in Azure Functions. Retail Store Locations - The company supports thousands of store locations globally. Store locations send data every hour to an Azure Blob storage account to support inventory, purchasing and delivery services. Each record includes a location identifier and sales transaction information. Requirements - The application components must meet the following requirements: Corporate website - • Secure the website by using SSL. • Minimize costs for data storage and hosting. • Implement native GitHub workflows for continuous integration and continuous deployment (CI/CD). • Distribute the website content globally for local use. • Implement monitoring by using Application Insights and availability web tests including SSL certificate validity and custom header value verification. • The website must have 99.95 percent uptime. Retail store locations - • Azure Functions must process data immediately when data is uploaded to Blob storage. Azure Functions must update Azure Cosmos DB by using native SQL language queries. • Audit store sale transaction information nightly to validate data, process sales financials, and reconcile inventory. Delivery services - • Store service telemetry data in Azure Cosmos DB by using an Azure Function. Data must include an item id, the delivery vehicle license plate, vehicle package capacity, and current vehicle location coordinates. • Store delivery driver profile information in Azure Active Directory (Azure AD) by using an Azure Function called from the corporate website. Inventory services - The company has contracted a third-party to develop an API for inventory processing that requires access to a specific blob within the retail store storage account for three months to include read-only access to the data. Security - • All Azure Functions must centralize management and distribution of configuration data for different environments and geographies, encrypted by using a company-provided RSA-HSM key. • Authentication and authorization must use Azure AD and services must use managed identities where possible. Issues - Retail Store Locations - • You must perform a point-in-time restoration of the retail store location data due to an unexpected and accidental deletion of data. • Azure Cosmos DB queries from the Azure Function exhibit high Request Unit (RU) usage and contain multiple, complex queries that exhibit high point read latency for large items as the function app is scaling. You need to test the availability of the corporate website. Which two test types can you use? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. Standard
B. URL ping
C. Custom testing using the TrackAvailability API method
D. Multi-step
Your company is developing an Azure API. You need to implement authentication for the Azure API. You have the following requirements: All API calls must be secure.✑ Callers to the API must not send credentials to the API. Which authentication mechanism should you use?
A. Basic
B. Anonymous
C. Managed identity
D. Client certificate
You are creating a hazard notification system that has a single signaling server which triggers audio and visual alarms to start and stop. You implement Azure Service Bus to publish alarms. Each alarm controller uses Azure Service Bus to receive alarm signals as part of a transaction. Alarm events must be recorded for audit purposes. Each transaction record must include information about the alarm type that was activated. You need to implement a reply trail auditing solution. Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Assign the value of the hazard message SessionID property to the ReplyToSessionId property.
B. Assign the value of the hazard message MessageId property to the DevileryCount property.
C. Assign the value of the hazard message SessionID property to the SequenceNumber property.
D. Assign the value of the hazard message MessageId property to the CorrelationId property.
E. Assign the value of the hazard message SequenceNumber property to the DeliveryCount property.
F. Assign the value of the hazard message MessageId property to the SequenceNumber property.
An organization deploys Azure Cosmos DB. You need to ensure that the index is updated as items are created, updated, or deleted. What should you do?
A. Set the indexing mode to Lazy.
B. Set the value of the automatic property of the indexing policy to False.
C. Set the value of the EnableScanInQuery option to True.
D. Set the indexing mode to Consistent.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You develop a software as a service (SaaS) offering to manage photographs. Users upload photos to a web service which then stores the photos in Azure Storage Blob storage. The storage account type is General-purpose V2. When photos are uploaded, they must be processed to produce and save a mobile-friendly version of the image. The process to produce a mobile-friendly version of the image must start in less than one minute. You need to design the process that starts the photo processing. Solution: Use the Azure Blob Storage change feed to trigger photo processing. Does the solution meet the goal?
A. Yes
B. No
You are developing an Azure-based web application. The application goes offline periodically to perform offline data processing. While the application is offline, numerous Azure Monitor alerts fire which result in the on-call developer being paged. The application must always log when the application is offline for any reason. You need to ensure that the on-call developer is not paged during offline processing. What should you do?
A. Add Azure Monitor alert processing rules to suppress notifications.
B. Disable Azure Monitor Service Health Alerts during offline processing.
C. Create an Azure Monitor Metric Alert.
D. Build an Azure Monitor action group that suppresses the alerts.
DRAG DROP - You need to add code at line PC32 in Processing.cs to implement the GetCredentials method in the Processing class. How should you complete the code? To answer, drag the appropriate code segments to the correct locations. Each code segment may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point. Select and Place:
HOTSPOT - You develop and deploy an Azure App Service web app that connects to Azure Cache for Redis as a content cache. All resources have been deployed to the East US 2 region. The security team requires the following audit information from Azure Cache for Redis: • The number of Redis client connections from an associated IP address. • Redis operations completed on the content cache. • The location (region) in which the Azure Cach3e for Redis instance was accessed. The audit information must be captured and analyzed by a security team application deployed to the Central US region. You need to log information on all client connections to the cache. Which configuration values should you use? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
DRAG DROP - You are preparing to deploy an Azure virtual machine (VM)-based application. The VMs that run the application have the following requirements: ✑ When a VM is provisioned the firewall must be automatically configured before it can access Azure resources. ✑ Supporting services must be installed by using an Azure PowerShell script that is stored in Azure Storage. You need to ensure that the requirements are met. Which features should you use? To answer, drag the appropriate features to the correct requirements. Each feature may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point. Select and Place:
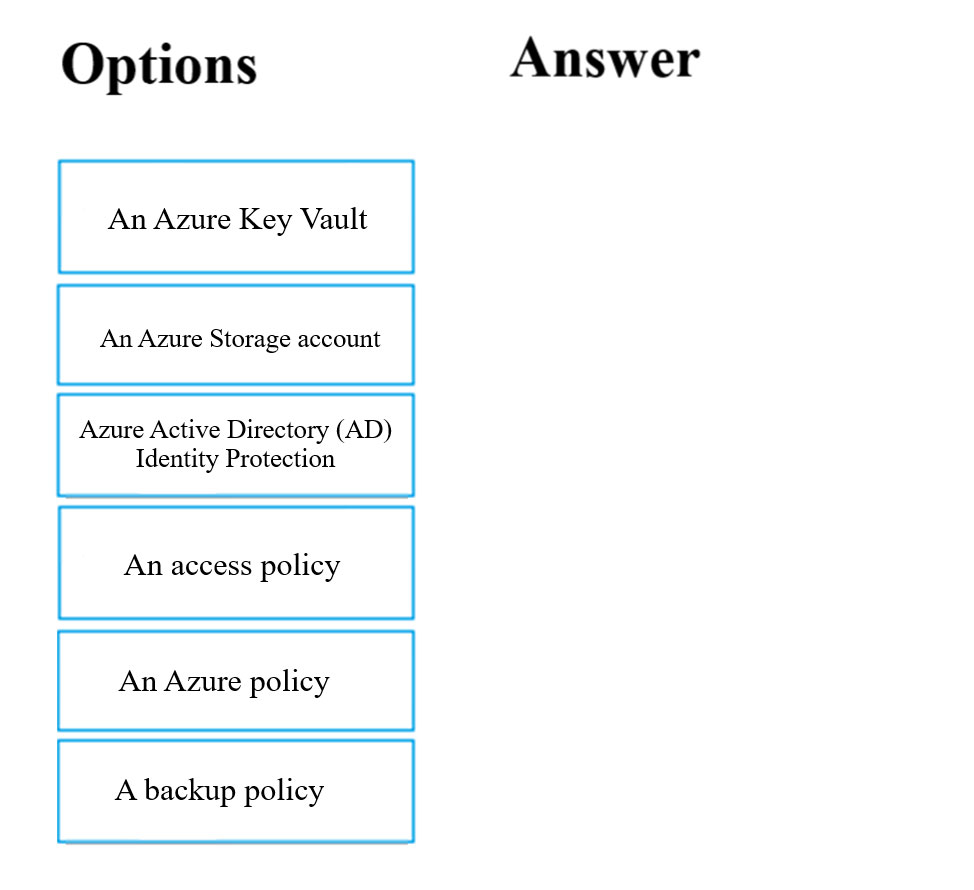
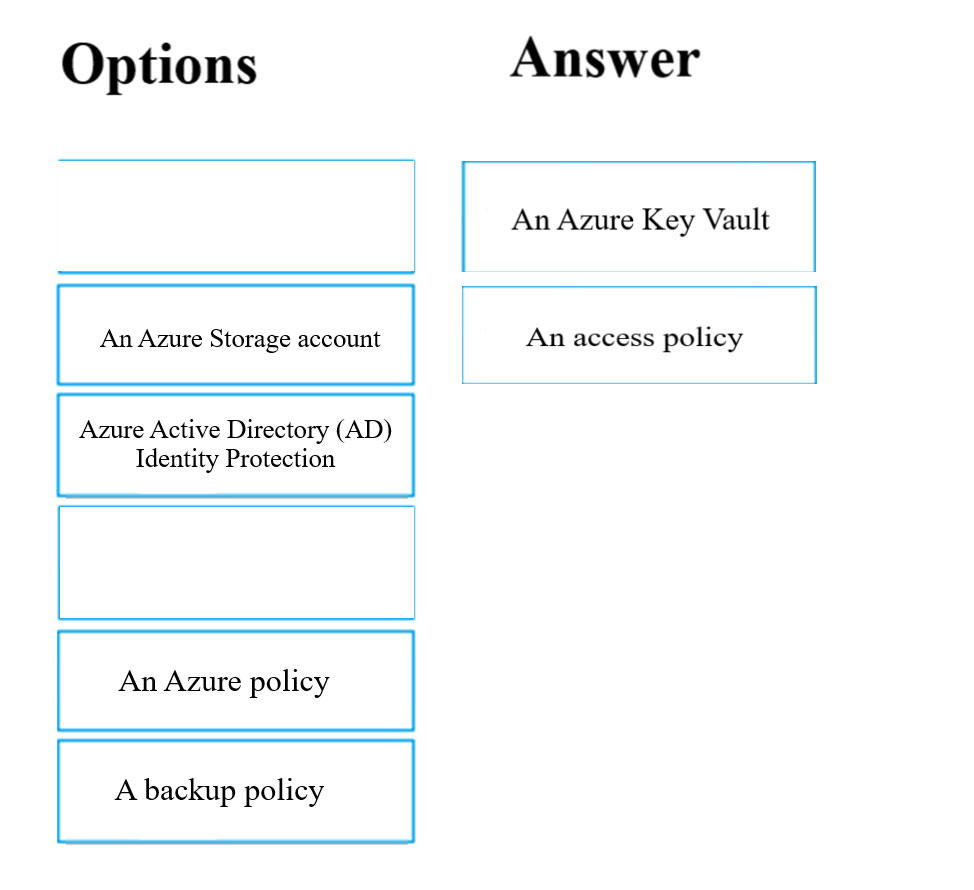
DRAG DROP - You have downloaded an Azure Resource Manager template to deploy numerous virtual machines. The template is based on a current virtual machine, but must be adapted to reference an administrative password. You need to make sure that the password is not stored in plain text. You are preparing to create the necessary components to achieve your goal. Which of the following should you create to achieve your goal? Answer by dragging the correct option from the list to the answer area. Select and Place:
HOTSPOT - You need to implement the Azure Function for delivery driver profile information. Which configurations should you use? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - You are developing an Azure Function app. All functions in the app meet the following requirements: • Run until either a successful run or until 10 run attempts occur. • Ensure that there are at least 20 seconds between attempts for up to 15 minutes. You need to configure the host.json file. How should you complete the code segment? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You are developing a .NET Core MVC application that allows customers to research independent holiday accommodation providers. You want to implement Azure Search to allow the application to search the index by using various criteria to locate documents related to accommodation venues. You want the application to list holiday accommodation venues that fall within a specific price range and are within a specified distance to an airport. What should you do?
A. Configure the SearchMode property of the SearchParameters class.
B. Configure the QueryType property of the SearchParameters class.
C. Configure the Facets property of the SearchParameters class.
D. Configure the Filter property of the SearchParameters class.
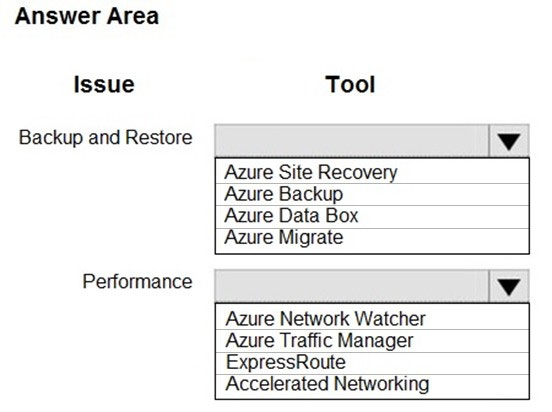
HOTSPOT - You need to correct the VM issues. Which tools should you use? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
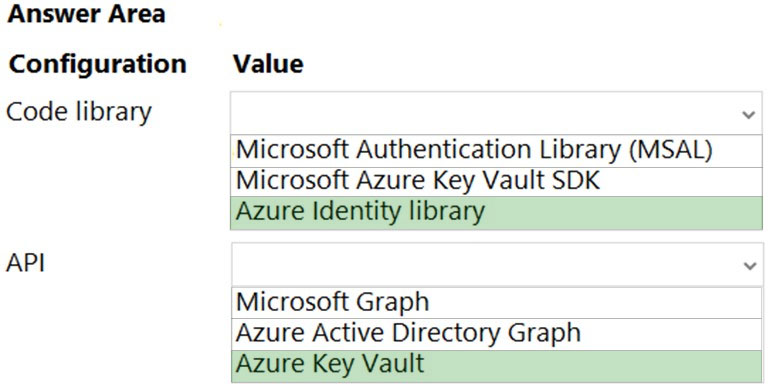
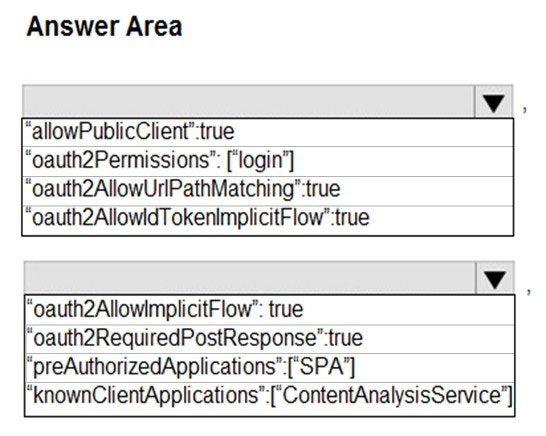
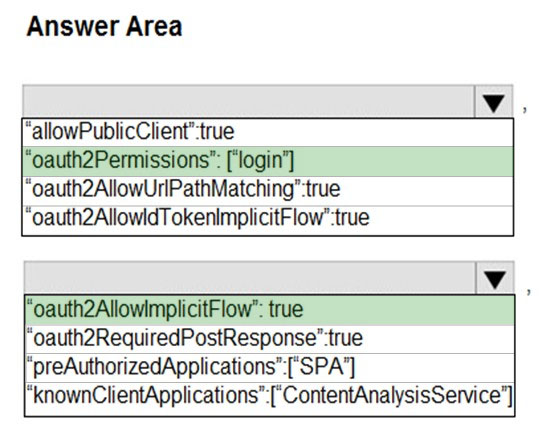
HOTSPOT - You need to add code at line AM09 to ensure that users can review content using ContentAnalysisService. How should you complete the code? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You manage an Azure SQL database that allows for Azure AD authentication. You need to make sure that database developers can connect to the SQL database via Microsoft SQL Server Management Studio (SSMS). You also need to make sure the developers use their on-premises Active Directory account for authentication. Your strategy should allow for authentication prompts to be kept to a minimum. Which of the following should you implement?
A. Azure AD token.
B. Azure Multi-Factor authentication.
C. Active Directory integrated authentication.
D. OATH software tokens.
HOTSPOT - You have an Azure API Management instance named API1 that uses a managed gateway. You plan to implement a policy that will apply at a product scope and will set the header of inbound requests to include information about the region hosting the gateway of API1. The policy definition contains the following content:You have the following requirements for the policy definition: • Ensure that the header contains the information about the region hosting the gateway of API1. • Ensure the policy applies only after any global level policies are processed first. You need to complete the policy definition. Which values should you choose? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
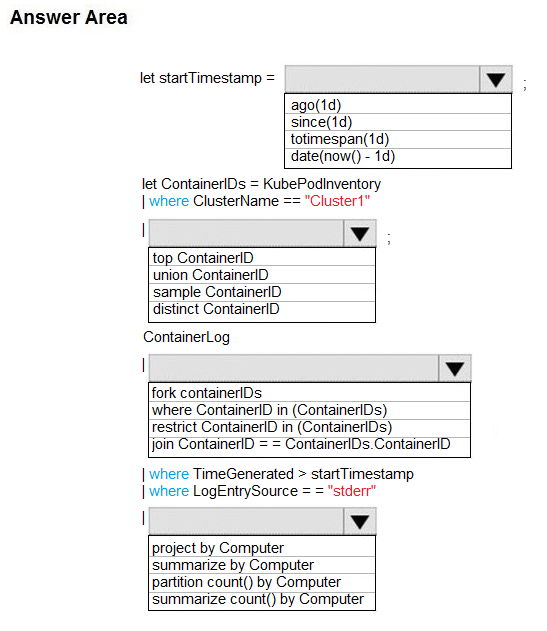
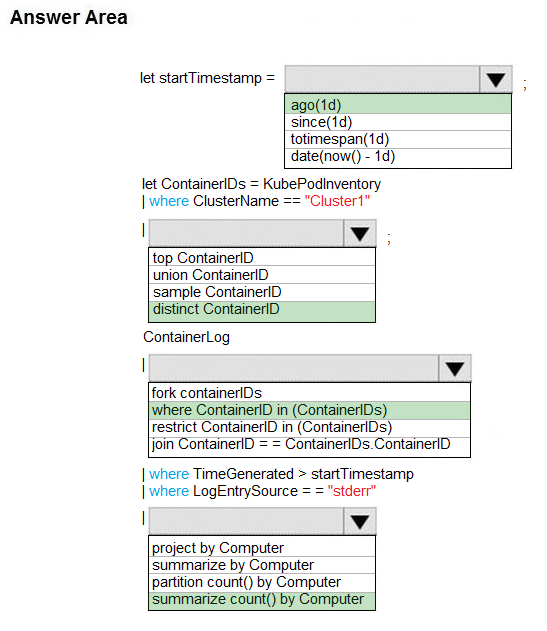
HOTSPOT - You are debugging an application that is running on Azure Kubernetes cluster named cluster1. The cluster uses Azure Monitor for containers to monitor the cluster. The application has sticky sessions enabled on the ingress controller. Some customers report a large number of errors in the application over the last 24 hours. You need to determine on which virtual machines (VMs) the errors are occurring. How should you complete the Azure Monitor query? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You are developing a medical records document management website. The website is used to store scanned copies of patient intake forms. If the stored intake forms are downloaded from storage by a third party, the contents of the forms must not be compromised. You need to store the intake forms according to the requirements. Solution: Store the intake forms as Azure Key Vault secrets. Does the solution meet the goal?
A. Yes
B. No
You develop and deploy an ASP.NET Core application that connects to an Azure Database for MySQL instance. Connections to the database appear to drop intermittently and the application code does not handle the connection failure. You need to handle the transient connection errors in code by implementing retries. What are three possible ways to achieve this goal? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Close the database connection and immediately report an error.
B. Disable connection pooling and configure a second Azure Database for MySQL instance.
C. Wait five seconds before repeating the connection attempt to the database.
D. Set a maximum number of connection attempts to 10 and report an error on subsequent connections.
E. Increase connection repeat attempts exponentially up to 120 seconds.
HOTSPOT - A company uses Azure Container Apps. A container app named App1 resides in a resource group named RG1. The company requires testing of updates to App1. You enable multiple revision modes on App1. You need to ensure traffic is routed to each revision of App1. How should you complete the code segment? NOTE: Each correct selection is worth one point.
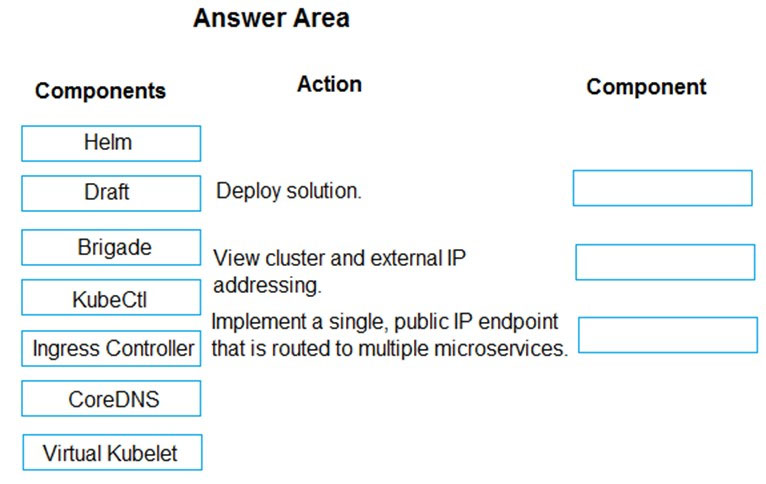
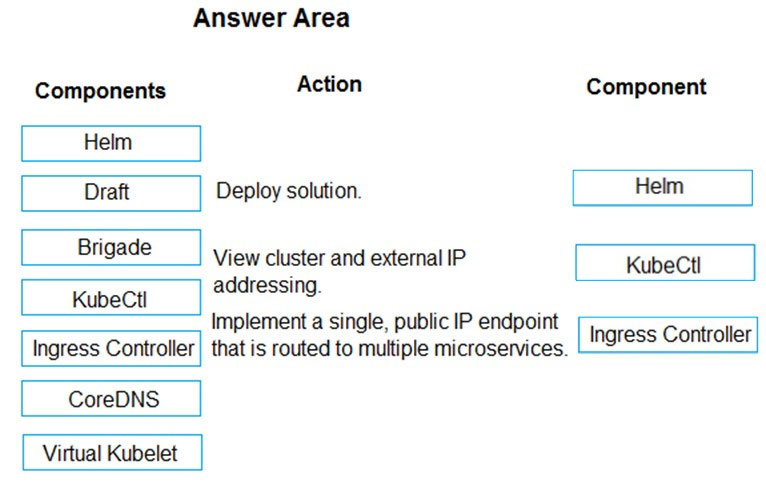
DRAG DROP - You are developing a microservices solution. You plan to deploy the solution to a multinode Azure Kubernetes Service (AKS) cluster. You need to deploy a solution that includes the following features: ✑ reverse proxy capabilities ✑ configurable traffic routing ✑ TLS termination with a custom certificate Which components should you use? To answer, drag the appropriate components to the correct requirements. Each component may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point. Select and Place:
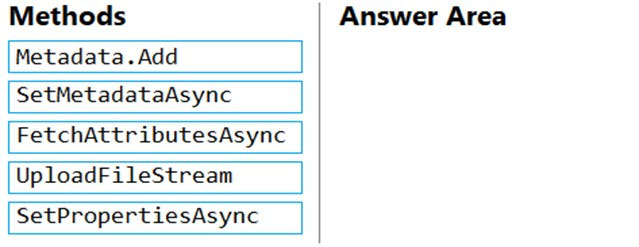
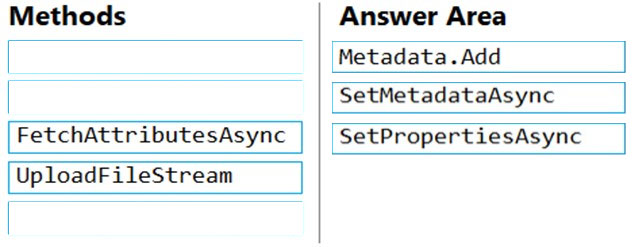
DRAG DROP - You have an application that uses Azure Blob storage. You need to update the metadata of the blobs. Which three methods should you use to develop the solution? To answer, move the appropriate methods from the list of methods to the answer area and arrange them in the correct order. Select and Place:
You are updating an application that stores data on Azure and uses Azure Cosmos DB for storage. The application stores data in multiple documents associated with a single username. The application requires the ability to update multiple documents for a username in a single ACID operation. You need to configure Azure Cosmos DB. Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Create a collection sharded on username to store documents.
B. Configure Azure Cosmos DB to use the Gremlin API.
C. Create an unsharded collection to store documents.
D. Configure Azure Cosmos DB to use the MongoDB API.
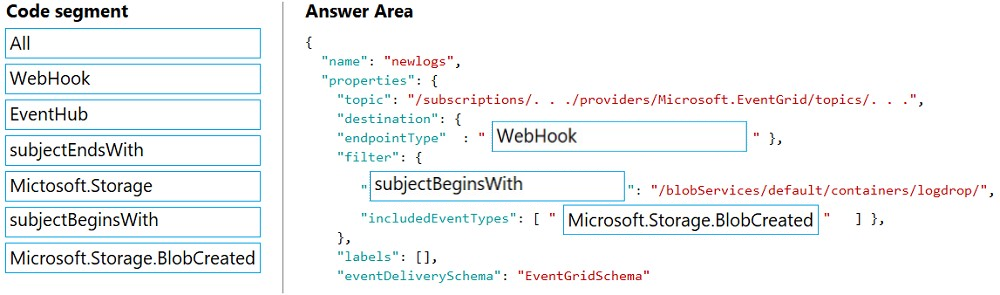
DRAG DROP - You need to implement the Log policy. How should you complete the Azure Event Grid subscription? To answer, drag the appropriate JSON segments to the correct locations. Each JSON segment may be used once, more than once, or not at all. You may need to drag the split bar between panes to view content. NOTE: Each correct selection is worth one point. Select and Place:
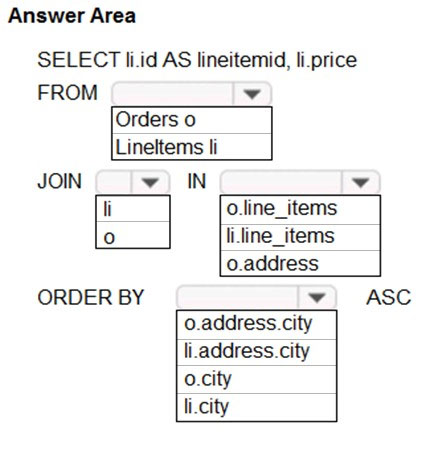
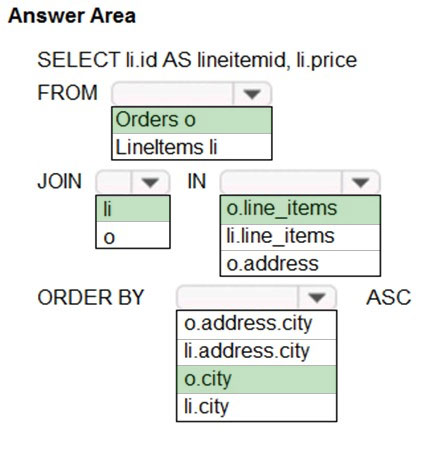
HOTSPOT - You need to retrieve all order line items from Order.json and sort the data alphabetically by the city. How should you complete the code? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
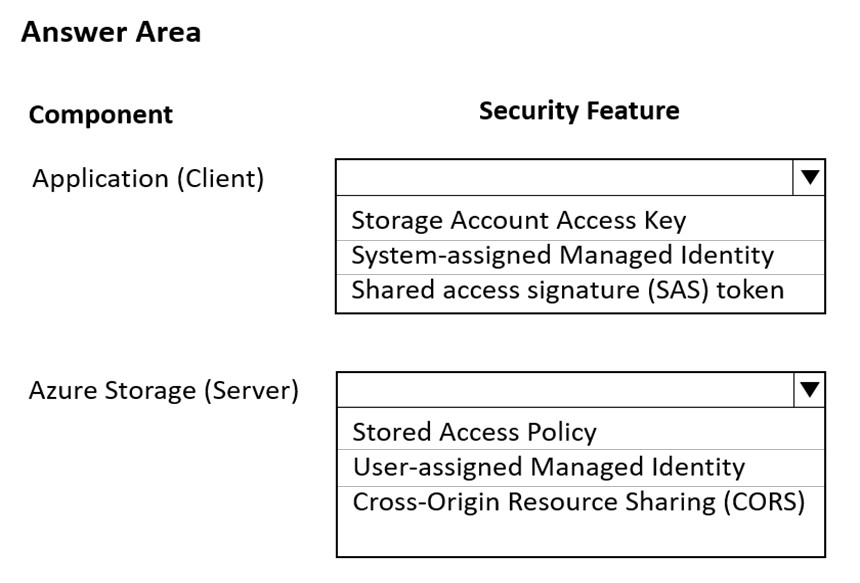
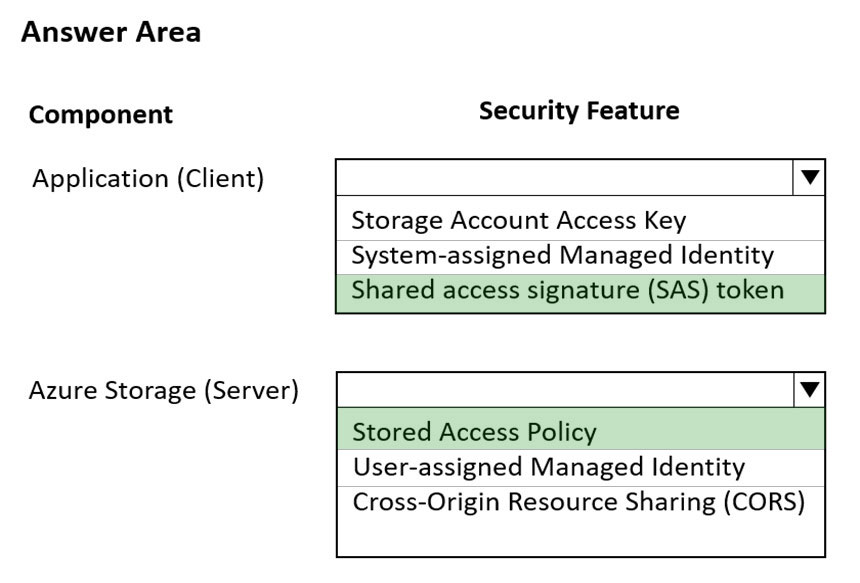
HOTSPOT - You are developing an application to store and retrieve data in Azure Blob storage. The application will be hosted in an on-premises virtual machine (VM). The VM is connected to Azure by using a Site-to-Site VPN gateway connection. The application is secured by using Azure Active Directory (Azure AD) credentials. The application must be granted access to the Azure Blob storage account with a start time, expiry time, and read permissions. The Azure Blob storage account access must use the Azure AD credentials of the application to secure data access. Data access must be able to be revoked if the client application security is breached. You need to secure the application access to Azure Blob storage. Which security features should you use? To answer select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - You have an App Service plan named asp1 based on the Free pricing tier. You plan to use asp1 to implement an Azure Function app with a queue trigger. Your solution must minimize cost. You need to identify the configuration options that will meet the requirements. Which value should you configure? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You are developing an Azure Cosmos DB solution by using the Azure Cosmos DB SQL API. The data includes millions of documents. Each document may contain hundreds of properties. The properties of the documents do not contain distinct values for partitioning. Azure Cosmos DB must scale individual containers in the database to meet the performance needs of the application by spreading the workload evenly across all partitions over time. You need to select a partition key. Which two partition keys can you use? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. a single property value that does not appear frequently in the documents
B. a value containing the collection name
C. a single property value that appears frequently in the documents
D. a concatenation of multiple property values with a random suffix appended
E. a hash suffix appended to a property value
HOTSPOT - You have an Azure Web app that uses Cosmos DB as a data store. You create a CosmosDB container by running the following PowerShell script: $resourceGroupName = "testResourceGroup" $accountName = "testCosmosAccount" $databaseName = "testDatabase" $containerName = "testContainer" $partitionKeyPath = "/EmployeeId" $autoscaleMaxThroughput = 5000 New-AzCosmosDBSqlContainer - -ResourceGroupName $resourceGroupName -AccountName $accountName -DatabaseName $databaseName -Name $containerName -PartitionKeyKind Hash -PartitionKeyPath $partitionKeyPath -AutoscaleMaxThroughput $autoscaleMaxThroughput You create the following queries that target the container: SELECT * FROM c WHERE c.EmployeeId > '12345' SELECT * FROM c WHERE c.UserID = '12345' For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
You are developing several Azure API Management (APIM) hosted APIs. You must inspect request processing of the APIs in APIM. Requests to APIM by using a REST client must also be included. The request inspection must include the following information: • requests APIM sent to the API backend and the response it received • policies applied to the response before sending back to the caller • errors that occurred during the processing of the request and the policies applied to the errors • original request APIM received from the caller and the policies applied to the request You need to inspect the APIs. Which three actions should you do? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Enable the Allow tracing setting for the subscription used to inspect the API.
B. Add the Ocp-Apim-Trace header value to the API call whit a value set to true.
C. Add the Ocp-Apim-Subscription-Key header value to the key for a subscription that allows access to the API.
D. Create and configure a custom policy. Apply the policy to the inbound policy section with a global scope.
E. Create and configure a custom policy. Apply the policy to the outbound policy section with an API scope.
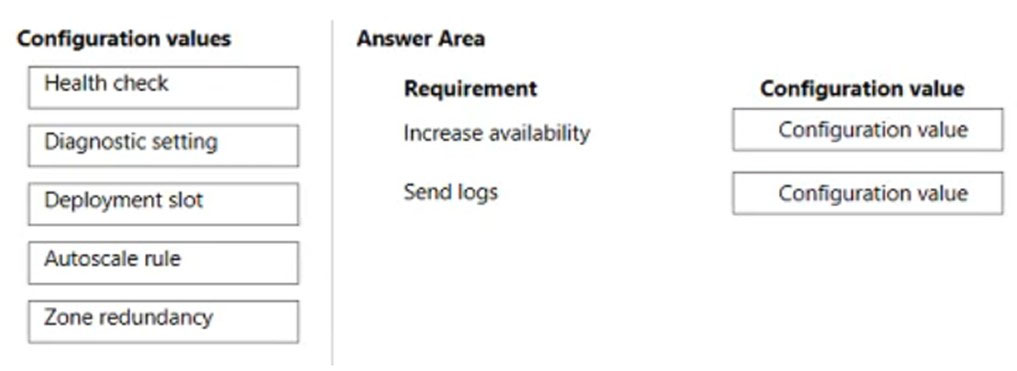
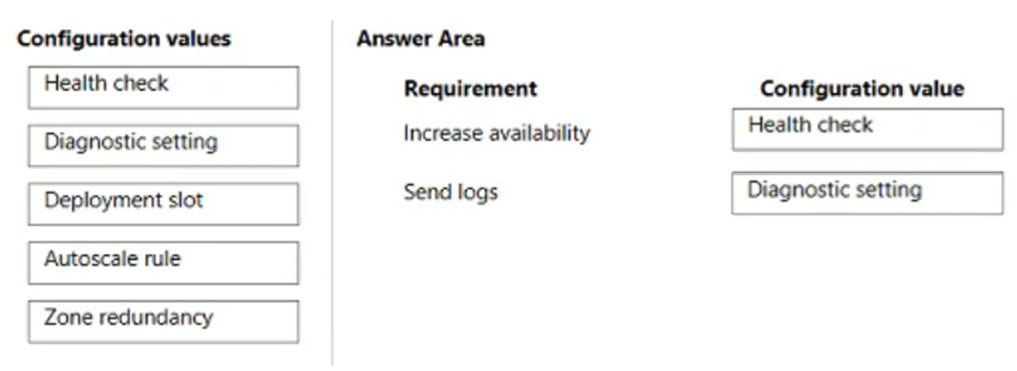
DRAG DROP - You develop and deploy a web app to Azure App Service in a production environment. You scale out the web app to four instances and configure a staging slot to support changes. You must monitor the web app in the environment to include the following requirements: ✑ Increase web app availability by re-routing requests away from instances with error status codes and automatically replace instances if they remain in an error state after one hour. ✑ Send web server logs, application logs, standard output, and standard error messaging to an Azure Storage blob account. You need to configure Azure App Service. Which values should you use? To answer, drag the appropriate configuration value to the correct requirements. Each configuration value may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point. Select and Place:
HOTSPOT - You develop a containerized application. The application must be deployed to an existing Azure Kubernetes Service (AKS) cluster from an Azure Container Registry (ACR) instance. You use the Azure command-line interface (Azure CLI) to deploy the application image to AKS. Images must be pulled from the registry. You must be able to view all registries within the current Azure subscription. Authentication must be managed by Microsoft Entra ID and removed when the registry is deleted. The solution must use the principle of least privilege. You need to configure authentication to the registry. Which authentication configuration should you use? To answer, select the appropriate configuration values in the answer area, NOTE: Each correct selection is worth one point.
You are configuring a web app that delivers streaming video to users. The application makes use of continuous integration and deployment. You need to ensure that the application is highly available and that the users' streaming experience is constant. You also want to configure the application to store data in a geographic location that is nearest to the user. Solution: You include the use of a Storage Area Network (SAN) in your design. Does the solution meet the goal?
A. Yes
B. No
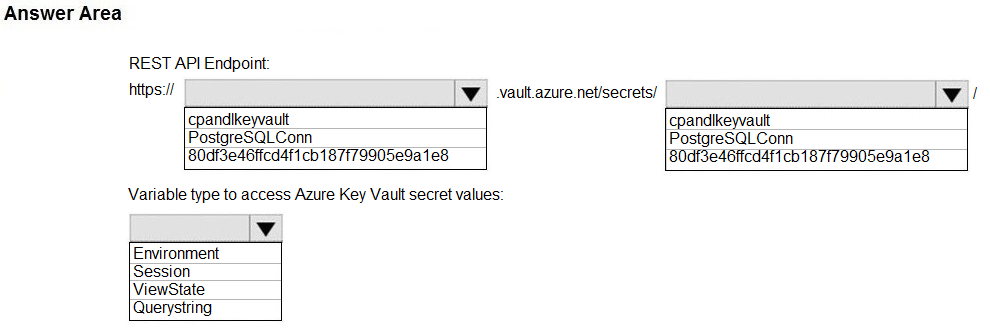
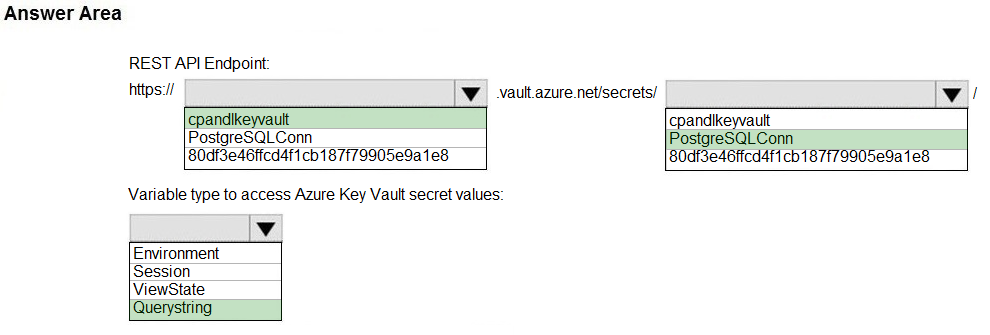
You are developing an Azure Function that calls external APIs by providing an access token for the API. The access token is stored in a secret named token in an Azure Key Vault named mykeyvault. You need to ensure the Azure Function can access to the token. Which value should you store in the Azure Function App configuration?
A. KeyVault:mykeyvault;Secret:token
B. App:Settings:Secret:mykeyvault:token
C. AZUREKVCONNSTR_ https://mykeyveult.vault.ezure.net/secrets/token/
D. @Microsoft.KeyVault(SecretUri=https://mykeyvault.vault.azure.net/secrets/token/)
Free Access Full AZ-204 Practice Test Free Questions
If you’re looking for more AZ-204 practice test free questions, click here to access the full AZ-204 practice test.
We regularly update this page with new practice questions, so be sure to check back frequently.
Good luck with your AZ-204 certification journey!