SY0-501 Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your SY0-501 certification exam? Start your preparation the smart way with our SY0-501 Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for SY0-501 exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our SY0-501 Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
An administrator discovers the following log entry on a server: Nov 12 2013 00:23:45 httpd[2342]: GET /app2/prod/proc/process.php?input=change;cd%20../../../etc;cat%20shadow Which of the following attacks is being attempted?
A. Command injection
B. Password attack
C. Buffer overflow
D. Cross-site scripting
Which of the following attackers generally possesses minimal technical knowledge to perform advanced attacks and uses widely available tools as well as publicly available information?
A. Hacktivist
B. White hat hacker
C. Script kiddle
D. Penetration tester
Security administrators attempted corrective action after a phishing attack. Users are still experiencing trouble logging in, as well as an increase in account lockouts. Users' email contacts are complaining of an increase in spam and social networking requests. Due to the large number of affected accounts, remediation must be accomplished quickly. Which of the following actions should be taken FIRST? (Choose two.)
A. Disable the compromised accounts
B. Update WAF rules to block social networks
C. Remove the compromised accounts with all AD groups
D. Change the compromised accounts’ passwords
E. Disable the open relay on the email server
F. Enable sender policy framework
Which of the following attack types BEST describes a client-side attack that is used to manipulate an HTML iframe with JavaScript code via a web browser?
A. Buffer overflow
B. MITM
C. XSS
D. SQLi
After attempting to harden a web server, a security analyst needs to determine if an application remains vulnerable to SQL injection attacks. Which of the following would BEST assist the analyst in making this determination?
A. tracert
B. Fuzzer
C. nslookup
D. Nmap
E. netcat
Multiple employees receive an email with a malicious attachment that begins to encrypt their hard drives and mapped shares on their devices when it is opened. The network and security teams perform the following actions: ✑ Shut down all network shares. ✑ Run an email search identifying all employees who received the malicious message. ✑ Reimage all devices belonging to users who opened the attachment. Next, the teams want to re-enable the network shares. Which of the following BEST describes this phase of the incident response process?
A. Eradication
B. Containment
C. Recovery
D. Lessons learned
When connected to a secure WAP, which of the following encryption technologies is MOST likely to be configured when connecting to WPA2-PSK?
A. DES
B. AES
C. MD5
D. WEP
An organization has the following password policies: ✑ Passwords must be at least 16 characters long. ✑ A password cannot be the same as any previous 20 passwords. ✑ Three failed login attempts will lock the account for five minutes. Passwords must have one uppercase letter, one lowercase letter, and one non-alphanumeric symbol.A database server was recently breached, and the incident response team suspects the passwords were compromised. Users with permission on that database server were forced to change their passwords for that server. Unauthorized and suspicious logins are now being detected on a completely separate server. Which of the following is MOST likely the issue and the best solution?
A. Some users are reusing passwords for different systems; the organization should scan for password reuse across systems.
B. The organization has improperly configured single sign-on; the organization should implement a RADIUS server to control account logins.
C. User passwords are not sufficiently long or complex; the organization should increase the complexity and length requirements for passwords.
D. The trust relationship between the two servers has been compromised; the organization should place each server on a separate VLAN.
A manager makes an unannounced visit to the marketing department and performs a walk-through of the office. The manager observes unclaimed documents on printers. A closer look at these documents reveals employee names, addresses, ages, birth dates, marital/dependent statuses, and favorite ice cream flavors. The manager brings this to the attention of the marketing department head. The manager believes this information to be PII, but the marketing head does not agree. Having reached a stalemate, which of the following is the MOST appropriate action to take NEXT?
A. Elevate to the Chief Executive Officer (CEO) for redress; change from the top down usually succeeds.
B. Find the privacy officer in the organization and let the officer act as the arbiter.
C. Notify employees whose names are on these files that their personal information is being compromised.
D. To maintain a working relationship with marketing, quietly record the incident in the risk register.
A network administrator at a small office wants to simplify the configuration of mobile clients connecting to an encrypted wireless network. Which of the following should be implemented in the administrator does not want to provide the wireless password or he certificate to the employees?
A. WPS
B. 802.1x
C. WPA2-PSK
D. TKIP
A company recently implemented a new security system. In the course of configuration, the security administrator adds the following entry: #Whitelist USBVID_13FE&PID_4127&REV_0100 - Which of the following security technologies is MOST likely being configured?
A. Application whitelisting
B. HIDS
C. Data execution prevention
D. Removable media control
A network administrator has been alerted that web pages are experiencing long load times. After determining it is not a routing or DNS issue, the administrator logs in to the router, runs a command, and receives the following output:Which of the following is the router experiencing?
A. DDoS attack
B. Memory leak
C. Buffer overflow
D. Resource exhaustion
An attacker captures the encrypted communication between two parties for a week, but is unable to decrypt the messages. The attacker then compromises the session key during one exchange and successfully compromises a single message. The attacker plans to use this key to decrypt previously captured and future communications, but is unable to. This is because the encryption scheme in use adheres to:
A. Asymmetric encryption
B. Out-of-band key exchange
C. Perfect forward secrecy
D. Secure key escrow
A security analyst is performing a manual audit of captured data from a packet analyzer. The analyst looks for Base64 encoded strings and applies the filter http.authbasic. Which of the following BEST describes what the analyst is looking for?
A. Unauthorized software
B. Unencrypted credentials
C. SSL certificate issues
D. Authentication tokens
When an initialization vector is added to each encryption cycle, it is using the:
A. ECB cipher mode
B. MD5 cipher mode
C. XOR cipher mode
D. CBC cipher mode
Due to regulatory requirements, a security analyst must implement full drive encryption on a Windows file server. Which of the following should the analyst implement on the system to BEST meet this requirement? (Choose two.)
A. Enable and configure EFS on the file system.
B. Ensure the hardware supports TPM, and enable it in the BIOS.
C. Ensure the hardware supports VT-X, and enable it in the BIOS.
D. Enable and configure BitLocker on the drives.
E. Enable and configure DFS across the file system.
Which of the following is a passive method to test whether transport encryption is implemented?
A. Black box penetration test
B. Port scan
C. Code analysis
D. Banner grabbing
A technician suspects that a system has been compromised. The technician reviews the following log entry: WARNING- hash mismatch: C:WindowSysWOW64user32.dll WARNING- hash mismatch: C:WindowSysWOW64kernel32.dll Based solely ono the above information, which of the following types of malware is MOST likely installed on the system?
A. Rootkit
B. Ransomware
C. Trojan
D. Backdoor
Joe, the security administrator, sees this in a vulnerability scan report: "The server 10.1.2.232 is running Apache 2.2.20 which may be vulnerable to a mod_cgi exploit.` Joe verifies that the mod_cgi module is not enabled on 10.1.2.232. This message is an example of:
A. a threat.
B. a risk.
C. a false negative.
D. a false positive.
A security technician is configuring a new firewall appliance for a production environment. The firewall must support secure web services for client workstations on the 10.10.10.0/24 network. The same client workstations are configured to contact a server at 192.168.1.15/24 for domain name resolution. Which of the following rules should the technician add to the firewall to allow this connectivity for the client workstations? (Choose two.)
A. Permit 10.10.10.0/24 0.0.0.0 ג€”p tcp –dport 22
B. Permit 10.10.10.0/24 0.0.0.0 ג€”p tcp –dport 80
C. Permit 10.10.10.0/24 192.168.1.15/24 ג€”p udp –dport 21
D. Permit 10.10.10.0/24 0.0.0.0 ג€”p tcp –dport 443
E. Permit 10.10.10.0/24 192.168.1.15/24 ג€”p tcp –dport 53
F. Permit 10.10.10.0/24 192.168.1.15/24 ג€”p udp –dport 53
The IT department is deploying new computers. To ease the transition, users will be allowed to access their old and new systems. The help desk is receiving reports that users are experiencing the following error when attempting to log in to their previous system: Logon Failure: Access Denied - Which of the following can cause this issue?
A. Permission issues
B. Access violations
C. Certificate issues
D. Misconfigured devices
A security analyst receives an alert from a WAF with the following payload: var data= `` ++ ` Which of the following types of attacks is this?
A. Cross-site request forgery
B. Buffer overflow
C. SQL injection
D. JavaScript data insertion
E. Firewall evasion script
A security analyst is attempting to break into a client's secure network. The analyst was not given prior information about the client, except for a block of public IP addresses that are currently in use. After network enumeration, the analyst's NEXT step is to perform:
A. a risk analysis.
B. a vulnerability assessment.
C. a gray-box penetration test.
D. an external security audit.
E. a red team exercise.
An organization prefers to apply account permissions to groups and not individual users, but allows for exceptions that are justified. Some systems require a machine-to-machine data exchange and an associated account to perform this data exchange. One particular system has data in a folder that must be modified by another system. No user requires access to this folder; only the other system needs access to this folder. Which of the following is the BEST account management practice?
A. Create a service account and apply the necessary permissions directly to the service account itself
B. Create a service account group, place the service account in the group, and apply the permissions on the group
C. Create a guest account and restrict the permissions to only the folder with the data
D. Create a generic account that will only be used for accessing the folder, but disable the account until it is needed for the data exchange
E. Create a shared account that administrators can use to exchange the data, but audit the shared account activity
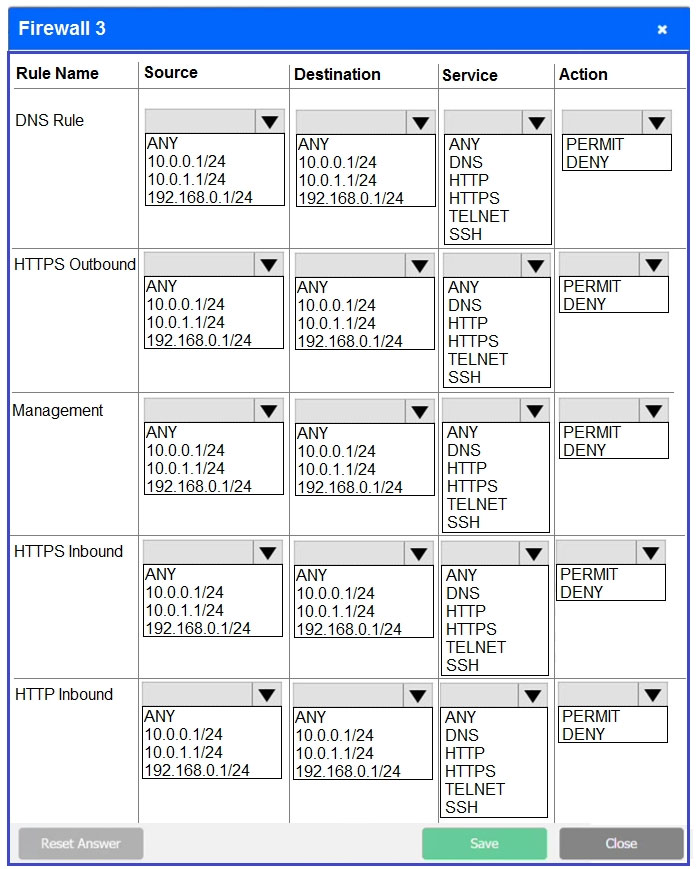
SIMULATION - A company recently added a DR site and is redesigning the network. Users at the DR site are having issues browsing websites. INSTRUCTIONS - Click on each firewall to do the following: 1. Deny cleartext web traffic. 2. Ensure secure management protocols are used. 3. Resolve issues at the DR site. The ruleset order cannot be modified due to outside constraints. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.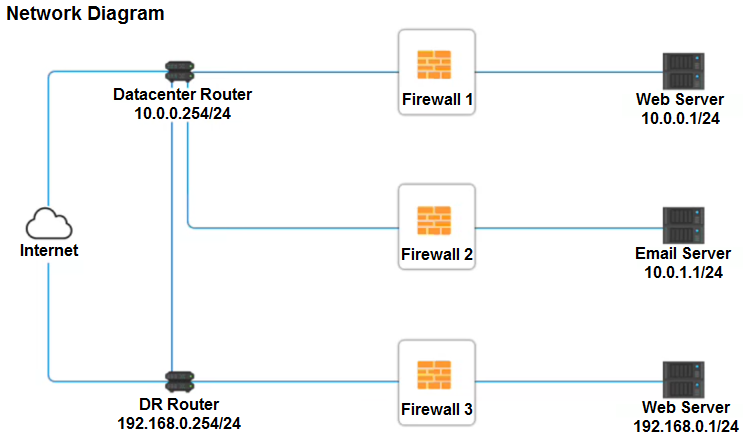
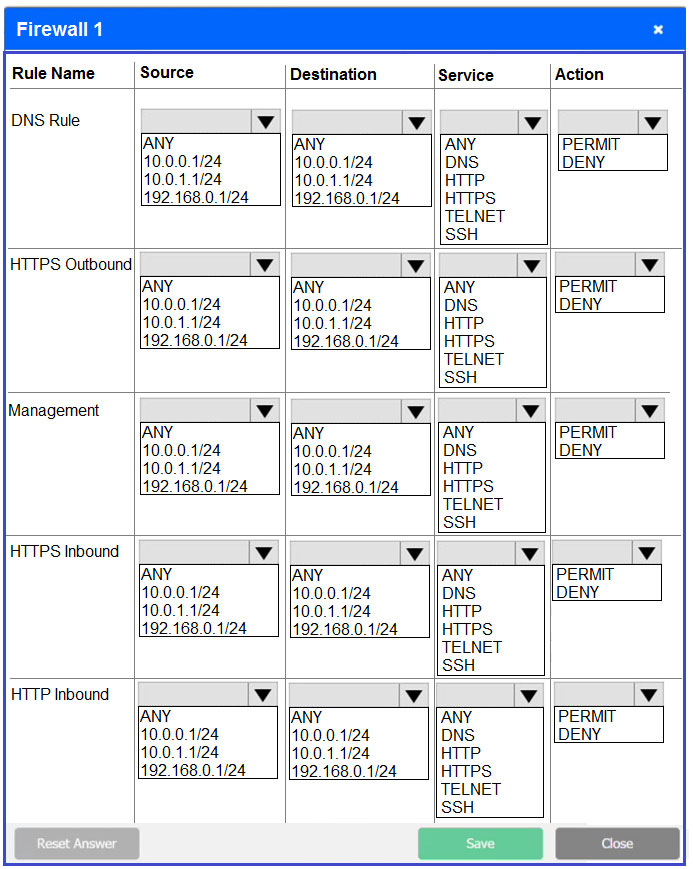
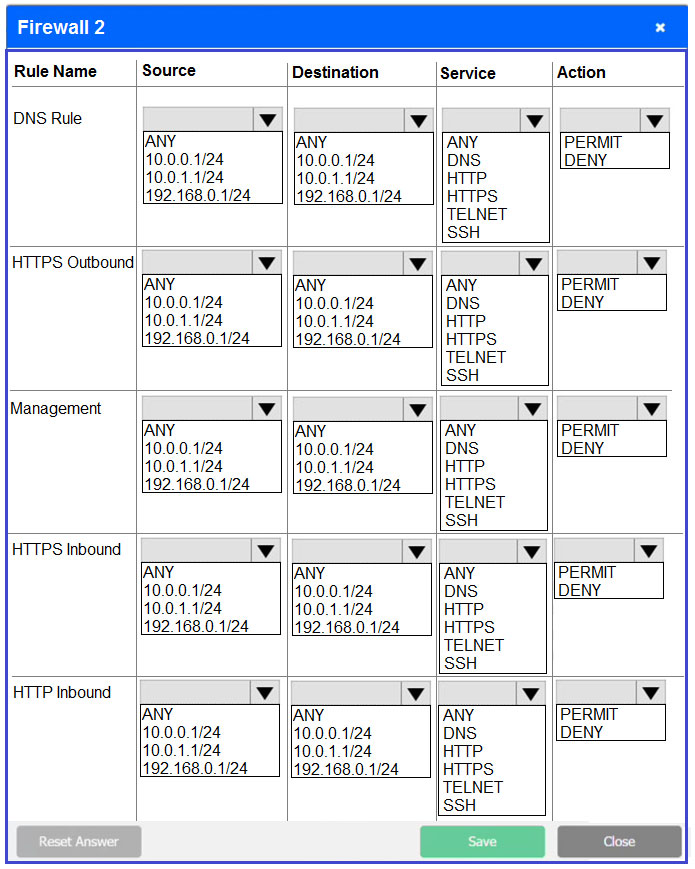
Which of the following is a deployment concept that can be used to ensure only the required OS access is exposed to software applications?
A. Staging environment
B. Sandboxing
C. Secure baseline
D. Trusted OS
A supervisor in your organization was demoted on Friday afternoon. The supervisor had the ability to modify the contents of a confidential database, as well as other managerial permissions. On Monday morning, the database administrator reported that log files indicated that several records were missing from the database. Which of the following risk mitigation strategies should have been implemented when the supervisor was demoted?
A. Incident management
B. Routine auditing
C. IT governance
D. Monthly user rights reviews
A department head at a university resigned on the first day of the spring semester. It was subsequently determined that the department head deleted numerous files and directories from the server-based home directory while the campus was closed. Which of the following policies or procedures could have prevented this from occurring?
A. Time-of-day restrictions
B. Permission auditing and review
C. Offboarding
D. Account expiration
Ann, a user, reports she is receiving emails that appear to be from organizations to which she belongs, but the emails contain links to websites that do not belong to those organizations. Which of the following security scenarios does this describe?
A. A hacker is using Ann’s social media information to create a spear phishing attack
B. The DNS servers for the organizations have been hacked and are pointing to malicious sites
C. The company’s mail system has changed the organization’s links to point to a proxy server for security
D. Ann’s computer is infected with adware that has changed the email links
Due to regulatory requirements, server in a global organization must use time synchronization. Which of the following represents the MOST secure method of time synchronization?
A. The server should connect to external Stratum 0 NTP servers for synchronization
B. The server should connect to internal Stratum 0 NTP servers for synchronization
C. The server should connect to external Stratum 1 NTP servers for synchronization
D. The server should connect to external Stratum 1 NTP servers for synchronization
The SSID broadcast for a wireless router has been disabled but a network administrator notices that unauthorized users are accessing the wireless network. The administer has determined that attackers are still able to detect the presence of the wireless network despite the fact the SSID has been disabled. Which of the following would further obscure the presence of the wireless network?
A. Upgrade the encryption to WPA or WPA2
B. Create a non-zero length SSID for the wireless router
C. Reroute wireless users to a honeypot
D. Disable responses to a broadcast probe request
An organization is concerned about video emissions from users' desktops. Which of the following is the BEST solution to implement?
A. Screen filters
B. Shielded cables
C. Spectrum analyzers
D. Infrared detection
A company is examining possible locations for a hot site. Which of the following considerations is of MOST concern if the replication technology being used is highly sensitive to network latency?
A. Connection to multiple power substations
B. Location proximity to the production site
C. Ability to create separate caged space
D. Positioning of the site across international borders
The CSIRT is reviewing the lessons learned from a recent incident. A worm was able to spread unhindered throughout the network and infect a large number of computers and server. Which of the following recommendations would be BEST to mitigate the impacts of a similar incident in the future?
A. Install a NIDS device at the boundary.
B. Segment the network with firewalls.
C. Update all antivirus signatures daily.
D. Implement application blacklisting.
An analyst is reviewing a simple program for potential security vulnerabilities before being deployed to a Windows server. Given the following code:Which of the following vulnerabilities is present?
A. Bad memory pointer
B. Buffer overflow
C. Integer overflow
D. Backdoor
A recent internal audit is forcing a company to review each internal business unit's VMs because the cluster they are installed on is in danger of running out of computer resources. Which of the following vulnerabilities exists?
A. Buffer overflow
B. End-of-life systems
C. System sprawl
D. Weak configuration
An incident response manager has started to gather all the facts related to a SIEM alert showing multiple systems may have been compromised. The manager has gathered these facts: ✑ The breach is currently indicated on six user PCs ✑ One service account is potentially compromised ✑ Executive management has been notified In which of the following phases of the IRP is the manager currently working?
A. Recovery
B. Eradication
C. Containment
D. Identification
An employer requires that employees use a key-generating app on their smartphones to log into corporate applications. In terms of authentication of an individual, this type of access policy is BEST defined as:
A. Something you have.
B. Something you know.
C. Something you do.
D. Something you are.
A security administrator receives alerts from the perimeter UTM. Upon checking the logs, the administrator finds the following output:
Time: 12/25 0300 -
From Zone: Untrust -
To Zone: DMZ -
Attacker: externalip.com -
Victim: 172.16.0.20 -
To Port: 80 -
Action: Alert -
Severity: Critical -
When examining the PCAP associated with the event, the security administrator finds the following information:
alert ("Click here for important information regarding your account! http://externalip.com/account.php"); </ script>
Which of the following actions should the security administrator take?
A. Upload the PCAP to the IDS in order to generate a blocking signature to block the traffic.
B. Manually copy the data from the PCAP file and generate a blocking signature in the HIDS to block the traffic for future events.
C. Implement a host-based firewall rule to block future events of this type from occurring.
D. Submit a change request to modify the XSS vulnerability signature to TCP reset on future attempts.
Which of the following outcomes is a result of proper error-handling procedures in secure code?
A. Execution continues with no notice or logging of the error condition.
B. Minor fault conditions result in the system stopping to preserve state.
C. The program runs through to completion with no detectable impact or output.
D. All fault conditions are logged and do not result in a program crash.
The help desk is receiving numerous password change alerts from users in the accounting department. These alerts occur multiple times on the same day for each of the affected users' accounts. Which of the following controls should be implemented to curtail this activity?
A. Password Reuse
B. Password complexity
C. Password History
D. Password Minimum age
A coding error has been discovered on a customer-facing website. The error causes each request to return confidential PHI data for the incorrect organization. The IT department is unable to identify the specific customers who are affected. As a result, all customers must be notified of the potential breach. Which of the following would allow the team to determine the scope of future incidents?
A. Intrusion detection system
B. Database access monitoring
C. Application fuzzing
D. Monthly vulnerability scans
Which of the following is the MOST likely motivation for a script kiddie threat actor?
A. Financial gain
B. Notoriety
C. Political expression
D. Corporate espionage
A developer has incorporated routines into the source code for controlling the length of the input passed to the program. Which of the following types of vulnerabilities is the developer protecting the code against?
A. DLL injection
B. Memory leak
C. Buffer overflow
D. Pointer dereference
In determining when it may be necessary to perform a credentialed scan against a system instead of a non-credentialed scan, which of the following requirements is MOST likely to influence this decision?
A. The scanner must be able to enumerate the host OS of devices scanned.
B. The scanner must be able to footprint the network.
C. The scanner must be able to check for open ports with listening services.
D. The scanner must be able to audit file system permissions
A security analyst notices anomalous activity coming from several workstations in the organizations. Upon identifying and containing the issue, which of the following should the security analyst do NEXT?
A. Document and lock the workstations in a secure area to establish chain of custody
B. Notify the IT department that the workstations are to be reimaged and the data restored for reuse
C. Notify the IT department that the workstations may be reconnected to the network for the users to continue working
D. Document findings and processes in the after-action and lessons learned report
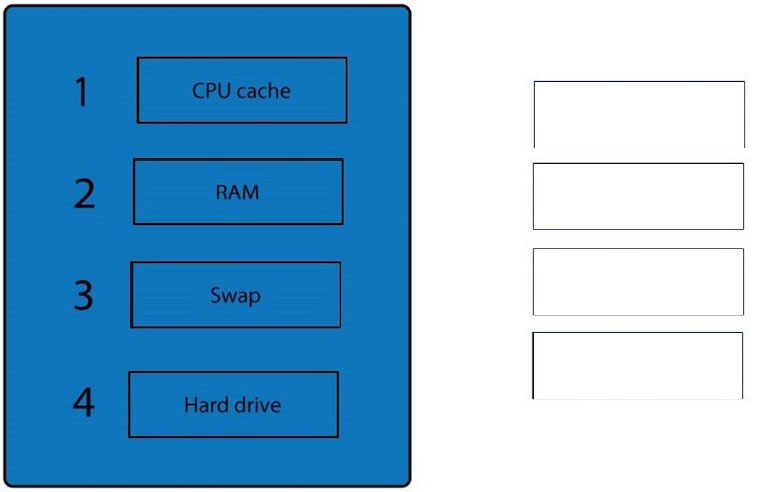
DRAG DROP - A forensic analyst is asked to respond to an ongoing network attack on a server. Place the items in the list below in the correct order in which the forensic analyst should preserve them. Select and Place:
A security analyst receives a notification from the IDS after working hours, indicating a spike in network traffic. Which of the following BEST describes this type of IDS?
A. Anomaly-based
B. Stateful
C. Host-based
D. Signature-based
Which of the following must be intact for evidence to be admissible in court?
A. Chain of custody
B. Order of volatility
C. Legal hold
D. Preservation
The Chief Security Officer (CSO) at a major hospital wants to implement SSO to help improve security in the environment and protect patient data, particularly at shared terminals. The Chief Risk Officer (CRO) is concerned that training and guidance have not been provided to frontline staff, and a risk analysis has not been performed. Which of the following is the MOST likely cause of the CRO's concerns?
A. SSO would simplify username and password management, making it easier for hackers to guess accounts.
B. SSO would reduce password fatigue, but staff would still need to remember more complex passwords.
C. SSO would reduce the password complexity for frontline staff.
D. SSO would reduce the resilience and availability of systems if the identity provider goes offline.
Access Full SY0-501 Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete SY0-501 Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our SY0-501 mock test free today—and take a major step toward exam success!