SC-900 Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your SC-900 certification exam? Start your preparation the smart way with our SC-900 Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for SC-900 exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our SC-900 Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
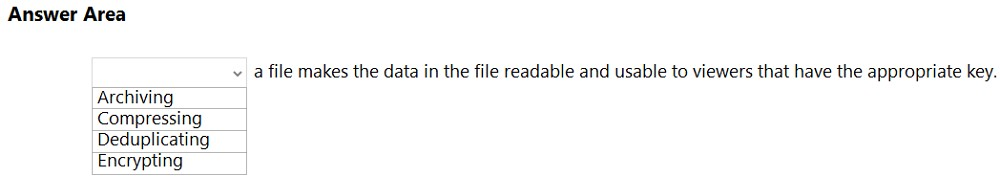
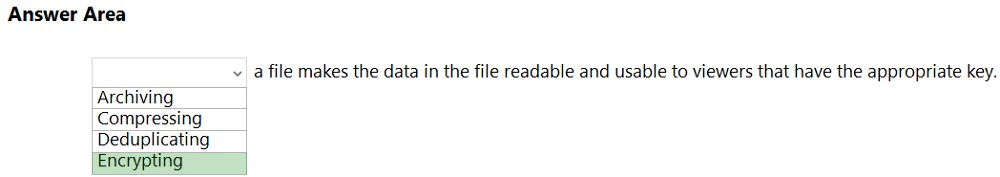
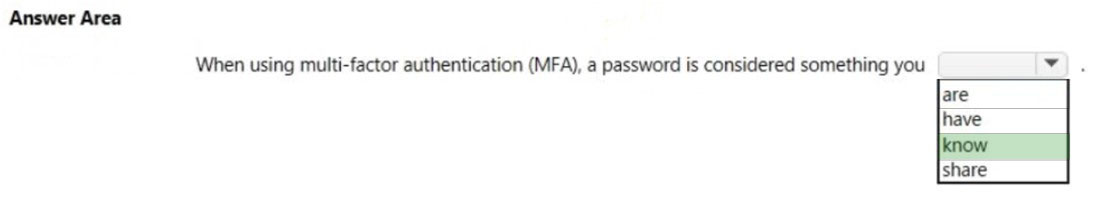
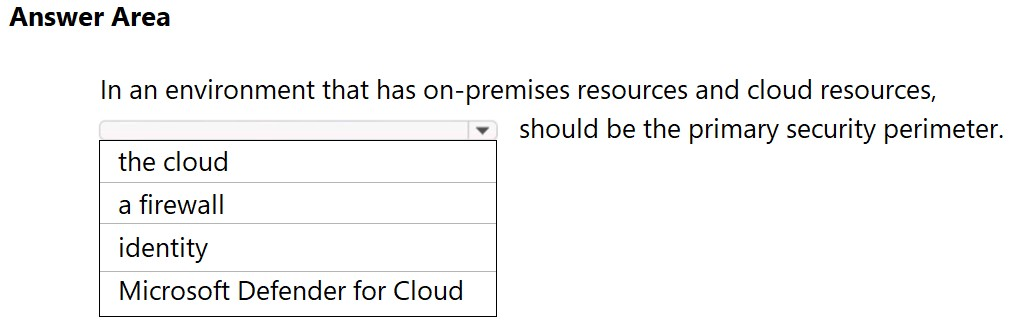
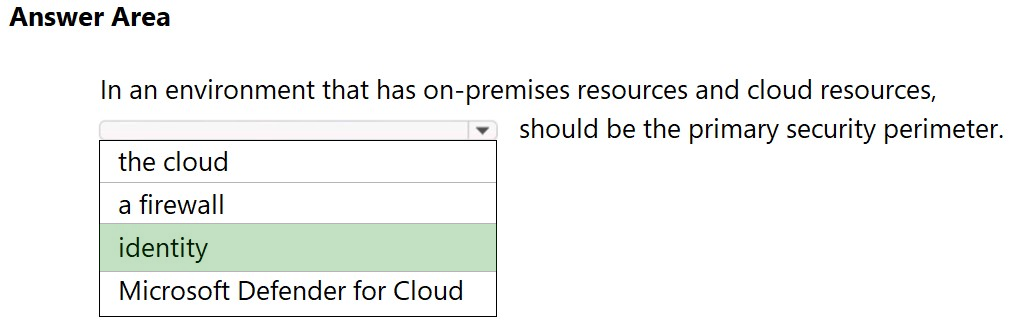
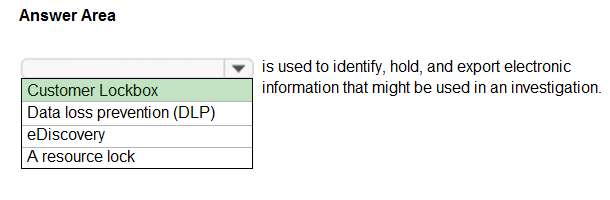
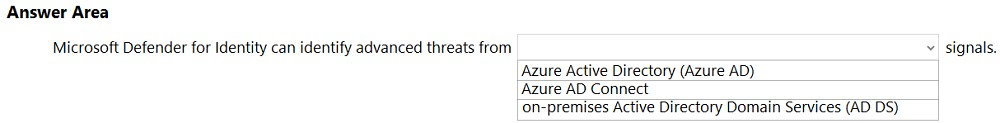
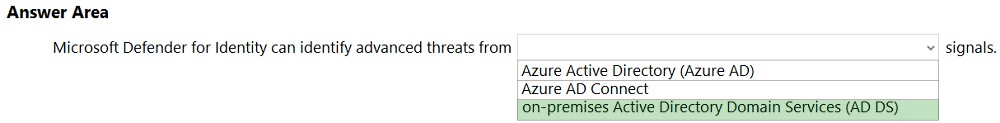
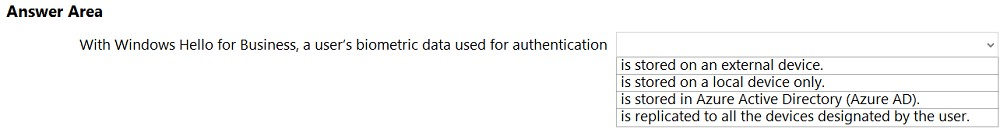
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:
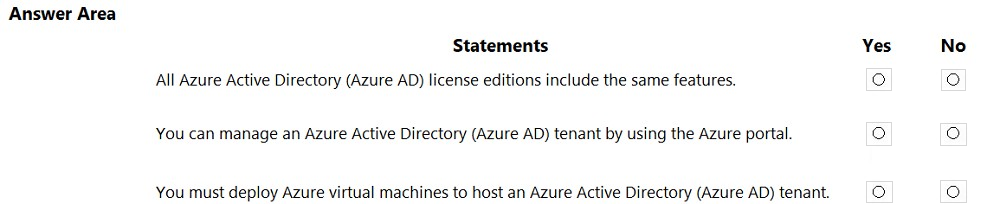
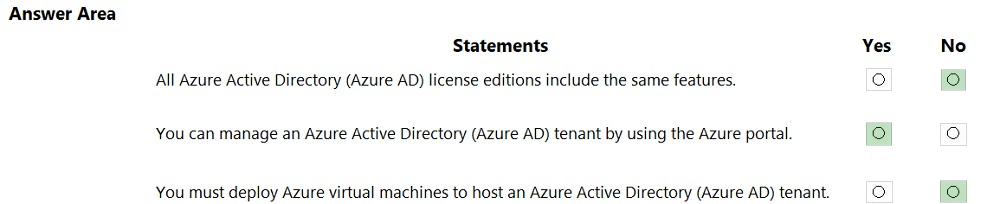
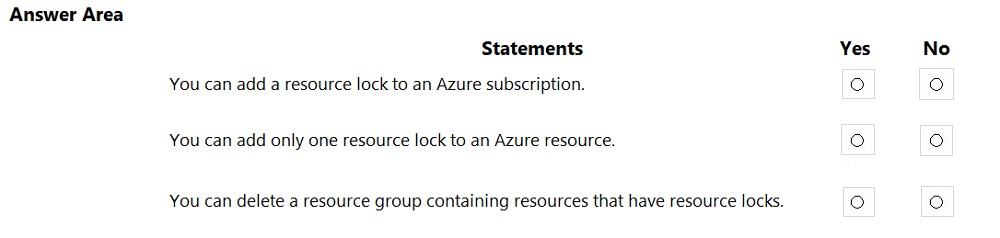
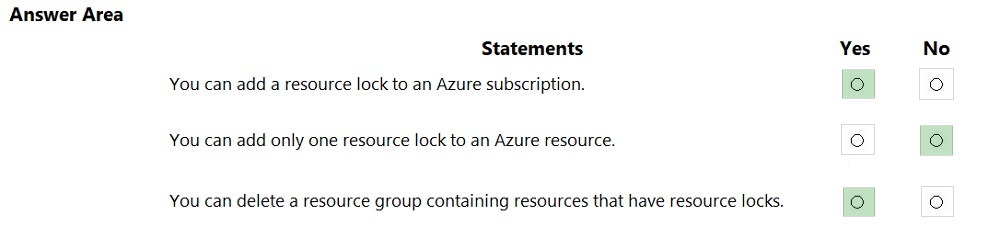
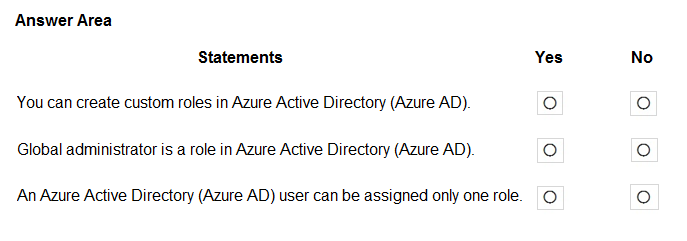
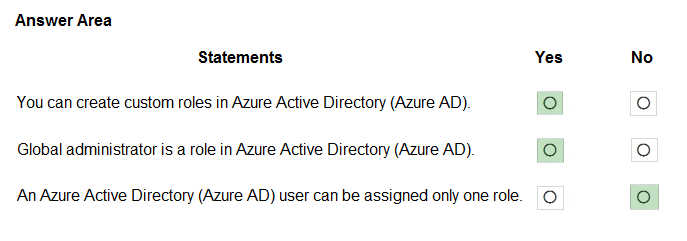
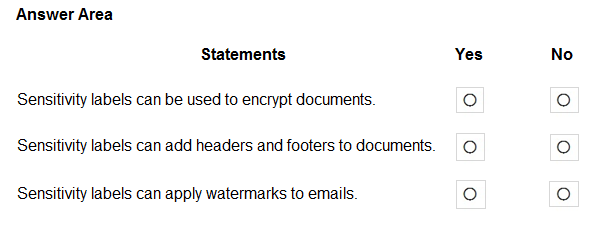
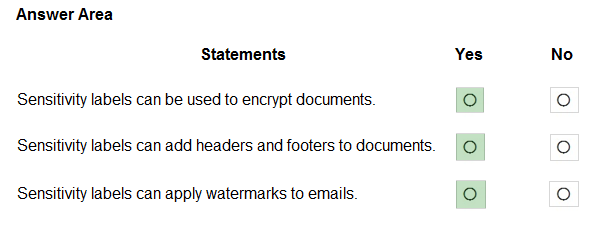
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
What is an example of encryption at rest?
A. encrypting communications by using a site-to-site VPN
B. encrypting a virtual machine disk
C. accessing a website by using an encrypted HTTPS connection
D. sending an encrypted email
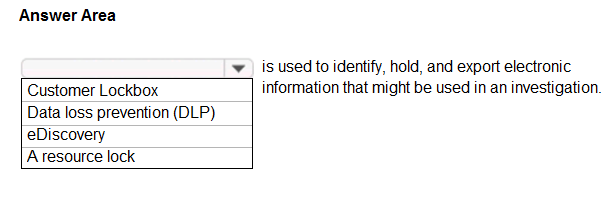
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:
Which Microsoft 365 feature can you use to restrict communication and the sharing of information between members of two departments at your organization?
A. sensitivity label policies
B. Customer Lockbox
C. information barriers
D. Privileged Access Management (PAM)
What does Conditional Access evaluate by using Azure Active Directory (Azure AD) Identity Protection?
A. user actions
B. group membership
C. device compliance
D. user risk
What is the purpose of Azure Active Directory (Azure AD) Password Protection?
A. to control how often users must change their passwords
B. to identify devices to which users can sign in without using multi-factor authentication (MFA)
C. to encrypt a password by using globally recognized encryption standards
D. to prevent users from using specific words in their passwords
Which pillar of identity relates to tracking the resources accessed by a user?
A. authorization
B. auditing
C. administration
D. authentication
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:
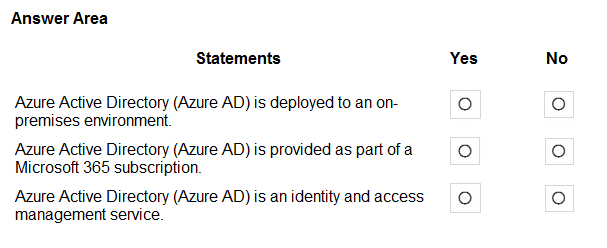
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:
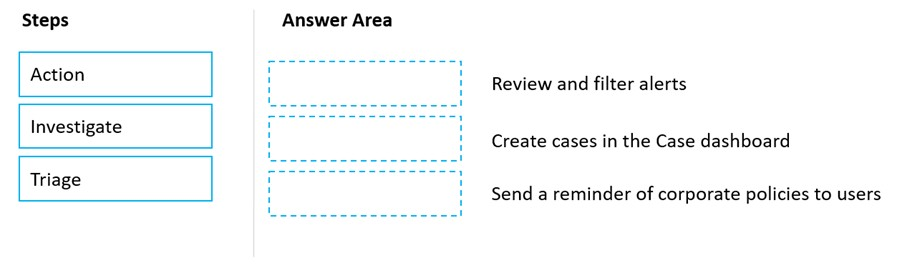
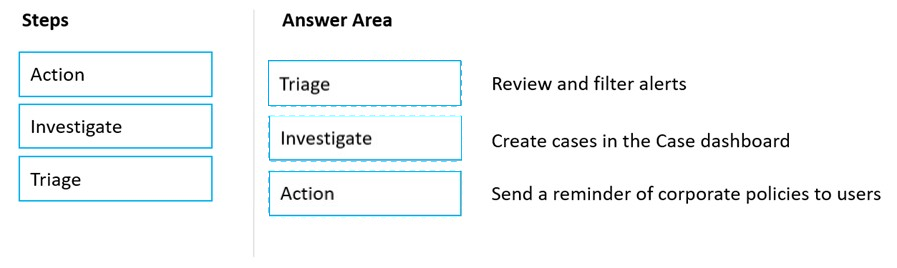
DRAG DROP - Match the Microsoft 365 insider risk management workflow step to the appropriate task. To answer, drag the appropriate step from the column on the left to its task on the right. Each step may be used once, more than once, or not at all. NOTE: Each correct match is worth one point. Select and Place:
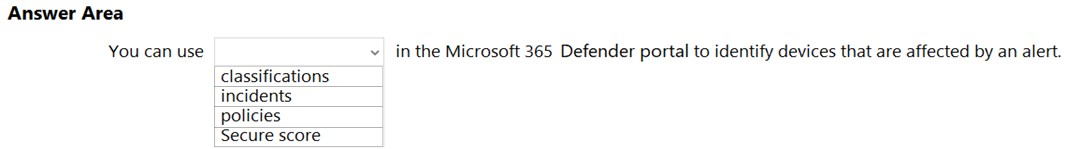
Which Microsoft Defender for Cloud metric displays the overall security health of an Azure subscription?
A. secure score
B. resource health
C. completed controls
D. the status of recommendations
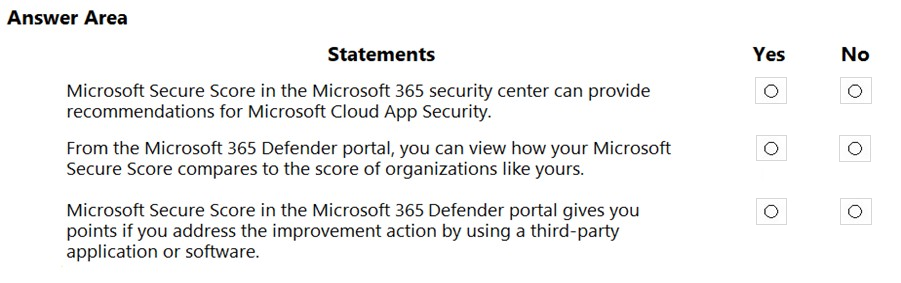
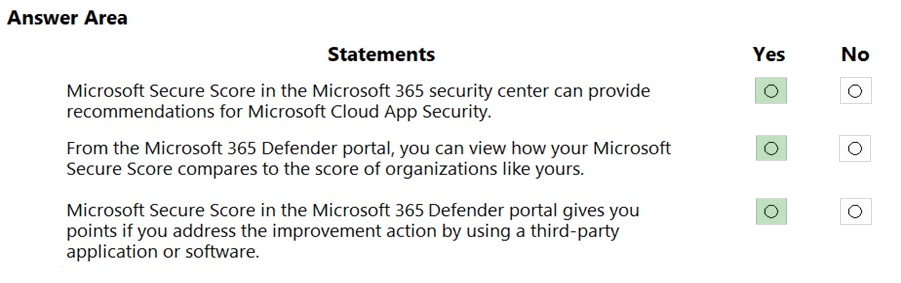
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Which type of identity is created when you register an application with Active Directory (Azure AD)?
A. a user account
B. a user-assigned managed identity
C. a system-assigned managed identity
D. a service principal
Which three statements accurately describe the guiding principles of Zero Trust? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. Define the perimeter by physical locations.
B. Use identity as the primary security boundary.
C. Always verify the permissions of a user explicitly.
D. Always assume that the user system can be breached.
E. Use the network as the primary security boundary.
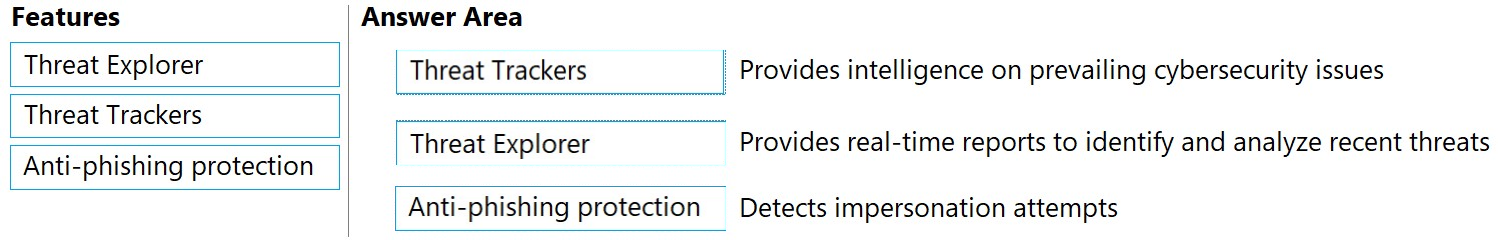
DRAG DROP - Match the Microsoft Defender for Office 365 feature to the correct description. To answer, drag the appropriate feature from the column on the left to its description on the right. Each feature may be used once, more than once, or not at all. NOTE: Each correct match is worth one point. Select and Place:
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
What can you use to protect against malicious links sent in email messages, chat messages, and channels?
A. Microsoft Defender for Cloud Apps
B. Microsoft Defender for Office 365
C. Microsoft Defender for Endpoint
D. Microsoft Defender for Identity
In the Microsoft Cloud Adoption Framework for Azure, which two phases are addressed before the Ready phase? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. Plan
B. Manage
C. Adopt
D. Govern
E. Define Strategy
What can you use to ensure that all the users in a specific group must use multi-factor authentication (MFA) to sign to Azure Active Directory (Azure AD)?
A. Azure Policy
B. a communication compliance policy
C. a Conditional Access policy
D. a user risk policy
What can you protect by using the information protection solution in the Microsoft 365 compliance center?
A. computers from zero-day exploits
B. users from phishing attempts
C. files from malware and viruses
D. sensitive data from being exposed to unauthorized users
What are two reasons to deploy multiple virtual networks instead of using just one virtual network? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. to meet governance policies
B. to connect multiple types of resources
C. to separate the resources for budgeting
D. to isolate the resources
You need to keep a copy of all files in a Microsoft SharePoint site for one year, even if users delete the files from the site. What should you apply to the site?
A. a retention policy
B. an insider risk policy
C. a data loss prevention (DLP) policy
D. a sensitivity label policy
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:
What can you use to view the Microsoft Secure Score for Devices?
A. Microsoft Defender for Cloud Apps
B. Microsoft Defender for Endpoint
C. Microsoft Defender for Identity
D. Microsoft Defender for Office 365
Which Azure Active Directory (Azure AD) feature can you use to restrict Microsoft Intune-managed devices from accessing corporate resources?
A. network security groups (NSGs)
B. Azure AD Privileged Identity Management (PIM)
C. conditional access policies
D. resource locks
What do you use to provide real-time integration between Azure Sentinel and another security source?
A. Azure AD Connect
B. a Log Analytics workspace
C. Azure Information Protection
D. a connector
Which two tasks can you implement by using data loss prevention (DLP) policies in Microsoft 365? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. Display policy tips to users who are about to violate your organization’s policies.
B. Enable disk encryption on endpoints.
C. Protect documents in Microsoft OneDrive that contain sensitive information.
D. Apply security baselines to devices.
You have an Azure subscription. You need to implement approval-based, time-bound role activation. What should you use?
A. Windows Hello for Business
B. Azure Active Directory (Azure AD) Identity Protection
C. access reviews in Azure Active Directory (Azure AD)
D. Azure Active Directory (Azure AD) Privileged Identity Management (PIM)
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
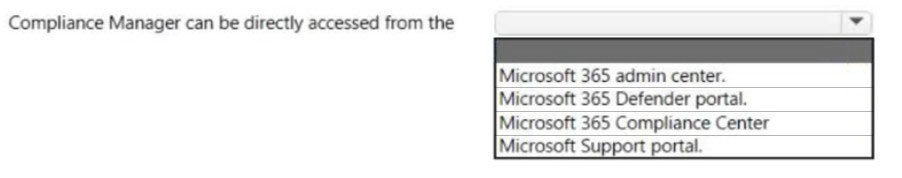
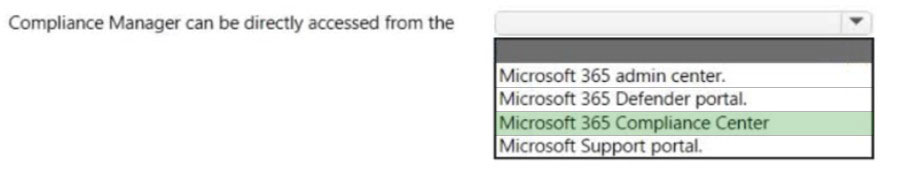
Which Microsoft portal provides information about how Microsoft cloud services comply with regulatory standard, such as International Organization for Standardization (ISO)?
A. the Microsoft Endpoint Manager admin center
B. Azure Cost Management + Billing
C. Microsoft Service Trust Portal
D. the Azure Active Directory admin center
Which feature provides the extended detection and response (XDR) capability of Azure Sentinel?
A. integration with the Microsoft 365 compliance center
B. support for threat hunting
C. integration with Microsoft 365 Defender
D. support for Azure Monitor Workbooks
HOTSPOT - Select the answer that correctly completes the sentence.
HOTSPOT - Select the answer that correctly completes the sentence.
Which three authentication methods does Windows Hello for Business support? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. fingerprint
B. facial recognition
C. PIN
D. email verification
E. security question
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
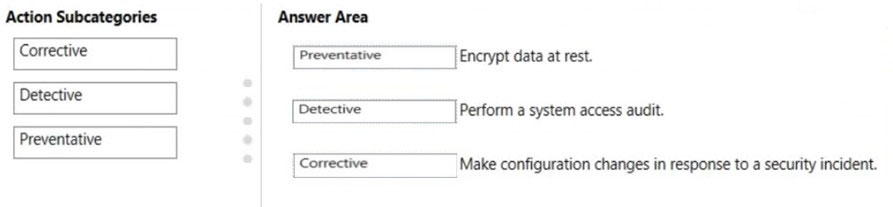
DRAG DROP - You are evaluating the compliance score in Compliance Manager. Match the compliance score action subcategories to the appropriate actions. To answer, drag the appropriate action subcategory from the column on the left to its action on the right. Each action subcategory may be used once, more than once, or not at all. NOTE: Each correct match is worth one point. Select and Place:
HOTSPOT - Select the answer that correctly completes the sentence.
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:
Which Microsoft 365 feature can you use to restrict users from sending email messages that contain lists of customers and their associated credit card numbers?
A. retention policies
B. data loss prevention (DLP) policies
C. conditional access policies
D. information barriers
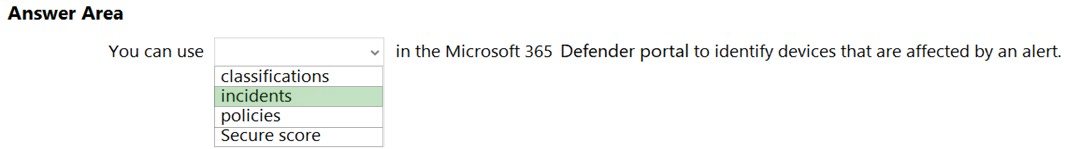
What should you use in the Microsoft 365 Defender portal to view security trends and track the protection status of identities?
A. Reports
B. Incidents
C. Hunting
D. Secure score
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:
Which three tasks can be performed by using Azure Active Directory (Azure AD) Identity Protection? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. Configure external access for partner organizations.
B. Export risk detection to third-party utilities.
C. Automate the detection and remediation of identity based-risks.
D. Investigate risks that relate to user authentication.
E. Create and automatically assign sensitivity labels to data.
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
What are three uses of Microsoft Cloud App Security? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. to discover and control the use of shadow IT
B. to provide secure connections to Azure virtual machines
C. to protect sensitive information hosted anywhere in the cloud
D. to provide pass-through authentication to on-premises applications
E. to prevent data leaks to noncompliant apps and limit access to regulated data
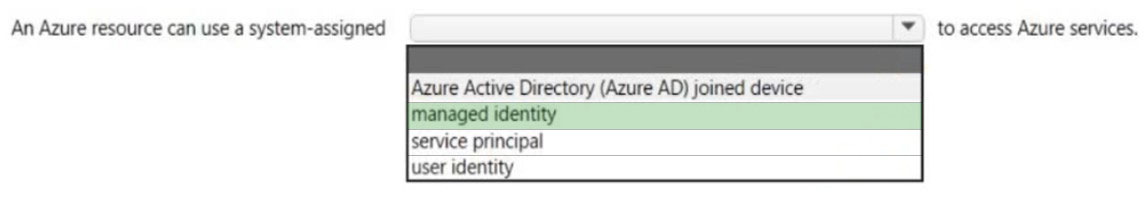
HOTSPOT - Select the answer that correctly completes the sentence. Hot Area:
Access Full SC-900 Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete SC-900 Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our SC-900 mock test free today—and take a major step toward exam success!