N10-007 Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your N10-007 certification exam? Start your preparation the smart way with our N10-007 Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for N10-007 exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our N10-007 Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
A technician needs to order cable that meets 10GBaseT and fire safety requirements for an installation between a drop ceiling and a standard ceiling. Which of the following should the technician order to ensure compliance with the requirements?
A. PVC Cat 5
B. Plenum Cat 5e
C. Plenum Cat 6a
D. PVC Cat 7
A local firm has hired a consulting company to clean up its IT infrastructure. The consulting company notices remote printing is accomplished by port forwarding via publicly accessible IPs through the firm's firewall. Which of the following would be the MOST appropriate way to enable secure, remote printing?
A. SSH
B. VPN
C. Telnet
D. SSL
A technician must determine if a web page user's visits are connecting to a suspicious website's IP address in the background. Which of the following tools would provide the information on TCP connections?
A. netstat
B. tracert
C. arp
D. ipconfig
E. route
A technician has been asked to install biometric controls at the entrance of a new datacenter. Which of the following would be appropriate authentication methods to meet this requirement? (Choose two.)
A. Badge reader
B. Retina scanner
C. Random number-generating token
D. Device proximity sensor
E. Challenge question
F. Combination lock
G. Fingerprint reader
A device operating at Layer 3 of the OSI model uses which of the following protocols to determine the path to a different network?
A. STP
B. RTP
C. RIP
D. NTP
E. SIP
A vendor is installing an Ethernet network in a new hospital wing. The cabling is primarily run above the celling grid near air conditioning ducts and sprinkler pipes. Which of the following cable types is required for this installation?
A. Plenum
B. PVC
C. Single-mode
D. Cat 7
A network technician at a small office upgrades the LAN switch. After the upgrade, a user reports being unable to access network resources. When the technician checks the switchport, the LED light is not lit. Which of the following should the technician check FIRST?
A. The device is using the correct cable type.
B. The switchport is functioning properly.
C. The device is connected to the switch.
D. The switch is connected to the router.
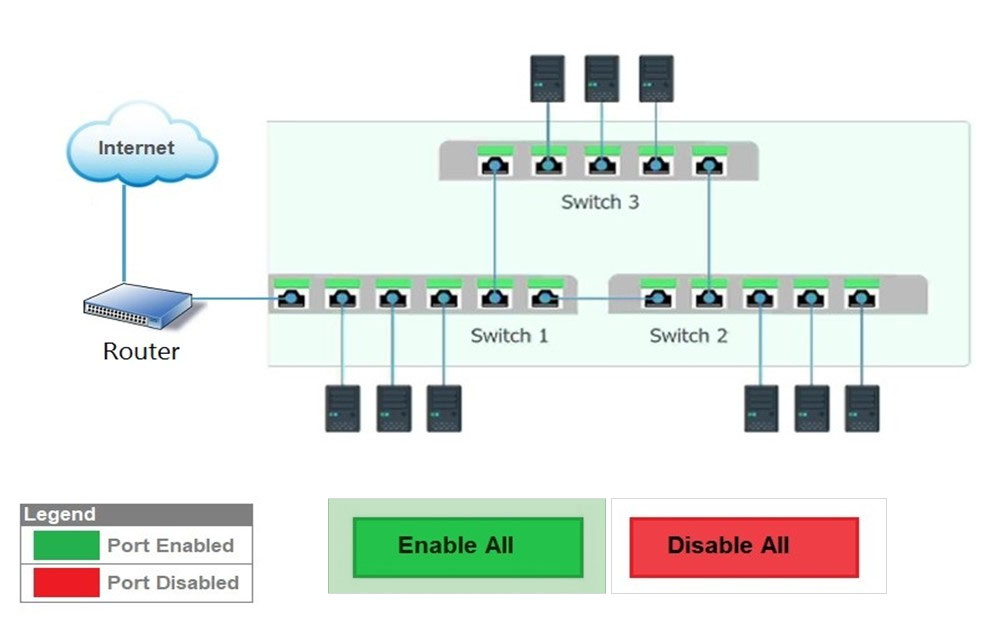
HOTSPOT - Workstations are unable to access the Internet after a recent power outage. Configure the appropriate devices to ensure All workstations have Internet connectivity. Instructions - All ports can be enabled (fill) or disabled (no fill). If at any time you would like to bring back the initial state of the simulation, please click the Reset All button. Hot Area:
A NGFW is continuously sending alerts regarding traffic from an internal database server. An old DHCP service, which was used before a dedicated server was installed, is still running on the server. Which of the following practices could have prevented this incident?
A. Preventing UDP on the host firewall
B. Enabling DHCP relay
C. Disabling unused services
D. Disabling DHCP spoofing
A user checks an IP address using an external website. The address is different than the one the user sees when opening a command prompt and typing in ipconfig/all. The user does not understand why the two tools show different IP addresses. This is BEST explained by the interworking of:
A. network devices
B. packet flow
C. public/private networks
D. traffic-routing protocols
A network engineer needs to connect two network switches with a gigabit link. The proposed route to run the 164ft (50m) cable is directly underneath a large electrical generator. Which of the following cable types would BEST fit the needs of the network engineer?
A. UTP
B. Cat 5 plenum
C. Coaxial
D. STP
A technician set up a small network, which is not connected to the company LAN, for several employees to play a peer-to-peer networking game during breaks. The users know how to set up the software, but they do not know anything about networking. The technician has wired the network but has not configured any networking information and does not want the employees to have access outside the network. Which of the following should be used to apply addressing to the network?
A. NAT
B. VLSM
C. APIPA
D. CIDR
After deployment of a second network link to load balance the network traffic, the quality of voice calls degrades. The network administrator discovers the voice packets are arriving at uneven intervals that cannot be handled by the voice application buffer. Which of the following actions will improve the quality of the voice calls?
A. Control the attenuation of the non-voice traffic across the network links
B. Control the latency of traffic across the network links
C. Control the EMI of the multimedia traffic across the network links
D. Control the jitter of the affected traffic across the network links
A vendor has installed new wireless access points in an office. After completing the installation, users in one area of the office report they cannot connect to the wireless network. A network technician confirms the users in that area cannot see the wireless SSID. Which of the following MOST likely explains the issue?
A. The AP power levels are too low.
B. The wireless network is over capacity.
C. A directional antenna was installed incorrectly.
D. The channels are overlapping.
A network administrator needs to implement a new IP subnet containing 29 hosts. It is possible that the number of hosts in that subnet could eventually double. The company only has a single, unused public IP network left to work with: 164.10.12.0/24. Which of the following would be the BEST way to divide this network without wasting addresses?
A. 164.10.12.0/24
B. 164.10.12.64/29
C. 164.10.12.128/26
D. 164.10.12.191/28
A technician is troubleshooting a workstation's network connectivity and wants to confirm which switchport corresponds to the wall jack the PC is using. Which of the following concepts would BEST help the technician?
A. Consistent labeling
B. Change management
C. Standard work instructions
D. Inventory management
E. Network baseline
A technician notices clients are receiving a 169.254.x.x IP address following the upgrade of a server. Which of the following ports should the technician check on the local server firewall?
A. ports 20 and 21
B. ports 67 and 68
C. ports 80 and 443
D. port 123 and 8080
Which of the following network security practices is focused on securing endpoints?
A. Switchport protection
B. Device hardening
C. Network segmentation
D. Connection encryption
A company decides to deploy customer-facing, touch-screen kiosks. The kiosks appear to have several open source service ports that could potentially become compromised. Which of the following is the MOST effective way to protect the kiosks?
A. Install an IDS to monitor all traffic to and from the kiosks.
B. Install honeypots on the network to detect and analyze potential kiosk attacks before they occur.
C. Enable switchport security on the ports to which the kiosks are connected to prevent network-level attacks.
D. Create a new network segment with ACLs, limiting kiosks’ traffic with the internal network.
When speaking with a client, an employee realizes a proposed solution may contain a specific cryptographic technology that is prohibited for non-domestic use. Which of the following documents or regulations should be consulted for confirmation?
A. Incident response policy
B. International export controls
C. Data loss prevention
D. Remote access policies
E. Licensing restrictions
A network technician sets up a new schedule on the backup server. Management has informed the technician that a full backup does not need to be completed every day. The technician sets up weekly full backups. Which of the following should the technician configure for the remaining days to MINIMIZE the daily backup size?
A. Snapshots
B. Incremental
C. Replica
D. Differential
The IT manager at a small firm is in the process of renegotiating an SLA with the organization's ISP. As part of the agreement, the organization will agree to a dynamic bandwidth plan to provide 150Mbps of bandwidth. However, if the ISP determines that a host on the organization's internal network produces malicious traffic, the ISP reserves the right to reduce available bandwidth to 1.5 Mbps. Which of the following policies is being agreed to in the SLA?
A. Session hijacking
B. Blocking
C. Throttling
D. Data usage limits
E. Bandwidth quotas
A technician logs onto a system using Telnet because SSH is unavailable. SSH is enabled on the target device, and access is allowed from all subnets. The technician discovers a critical step was missed. Which of the following would allow SSH to function properly?
A. Perform file hashing
B. Generate new keys
C. Update firmware
D. Change default credentials
A network technician has been attempting to gain access to a switch over the network after an extended power outage but has been unsuccessful. The technician runs a network scan and does not find the switch in the results. The switch is turned on, and the link lights are all green. Which of the following should the technician use to gain access to the switch?
A. SSH
B. OOB
C. VNC
D. Telnet
Two buildings used to be connected by a wireless bridge, but they are upgrading to fiber. Which of the following new devices would be required at the demarcation points?
A. Wireless access point
B. Router
C. Media converter
D. Firewall
A WAP has been dropping off the network sporadically and reconnecting shortly thereafter. The Cat 5 wire connecting the access point is a long run of 265ft (81m) and goes through the business area and the mechanical room. Which of the following should the technician do to fix the AP connectivity issue?
A. Install a repeater to boost the signal to its destination
B. Replace the UTP cable with plenum cable.
C. Upgrade the cable from Cat 5 to Cat 5e.
D. Set the AP to half duplex to compensate for signal loss.
Users report that the network is slow. Upon investigation, the technician notices all users are on one large subnet. Which of the following devices should be used to break up broadcast domains?
A. Layer 2 switch
B. Layer 3 switch
C. Signal repeater
D. Bridge
E. Domain server
A network technician is troubleshooting a DOCSIS network. Which of the following devices marks the termination of the ISP's network and the start of the customer's network?
A. Router
B. Hub
C. Modem
D. Switch
Which of the following is a purpose of a syslog server?
A. Aggregates switch logs for easier review and correlation
B. Polls SNMP-enabled server logs for current status
C. Distributes logging applications to monitoring servers
D. Purges switch logs when they reach capacity
Under which of the following layers of the OSI model do ATM cells operate?
A. Data link
B. Network
C. Session
D. Transport
E. Presentation
An administrator implemented a wireless network in a warehouse for an employee to scan inventory as it arrives and is shipped out. The scanners are proprietary devices that connect to the wireless network, but they have no configuration options beyond connecting via DHCP. Which of the following should the administrator implement to harden the wireless network without negatively affecting the scanners' ability to connect?
A. Secure the wireless network using PEAP authentication for connecting devices.
B. Implement a two-factor authentication method for the wireless network.
C. Allow only devices with statically assigned IP addresses to connect to the network.
D. Configure the wireless network to allow connections based on hardware address only.
In which of the following ways does a DDoS attack differ from a spoofing attack?
A. DDoS attacks target multiple networks
B. Spoofing attacks originate from a single host
C. DDoS attacks are launched from multiple hosts
D. Spoofing attacks require physical presence
An administrator recently implemented new SOHO routers for a company's teleworking employees. Before deploying the routers, the administrator changed the default credentials and disabled unnecessary services. Within a few days of deployment, hackers gained access to the routers. Which of the following is the MOST important thing the administrator forgot to do?
A. Disable unused physical router ports.
B. Generate new encryption keys.
C. Upgrade the router firmware.
D. Create a database of file hashes on the router.
A user no longer has access to network resources after a recent office move, but all other users in the building are able to connect at 100MB connections. After further investigation, a network technician notices the following information:Which of the following is causing the network connection issues?
A. Open/short pins
B. VLAN mismatch
C. Distance limitation
D. Crosstalk
E. Port configuration
Which of the following can be used to prevent unauthorized employees from entering restricted areas?
A. Sign-in sheets
B. Video cameras
C. Motion sensors
D. Swipe badges
A workstation is configured with the following network details:Software on the workstation needs to send a query to the local subnet broadcast address. To which of the following addresses should the software be configured to send the query?
A. 10.1.2.0
B. 10.1.2.1
C. 10.1.2.23
D. 10.1.2.255
E. 10.1.2.31
A network technician is attempting to update firmware on a router but cannot physically locate the router. Which of the following would show where to locate router?
A. Diagram symbols
B. Rack diagram
C. Logical diagram
D. Port locations
A network technician receives a spool of Cat 6a cable and is asked to build several cables for a new set of Ethernet runs between devices. Which of the following tools are MOST likely needed to complete the task? (Choose three.)
A. Wire stripper
B. Cable crimper
C. RJ-11 connectors
D. RJ-45 connectors
E. Multimeter
F. Punchdown tool
G. Tone generator
A network administrator is setting up a web-based application that needs to be continually accessible to the end users. Which of the following concepts would BEST ensure this requirement?
A. High availability
B. Snapshots
C. NIC teaming
D. Cold site
A network technician is assisting a user who has relocated to a newly constructed office space. The user has no network connectivity. A cable tester was used on the port and is reporting that the pairs are open. Which of the following should be used to remedy this problem?
A. Loopback adapter
B. Tone generator
C. Multimeter
D. Punchdown tool
The help desk is receiving reports of intermittent connections to a server. A help desk technician suspects the server is unable to establish a three-way handshake due to a DoS attack. Which of the following commands should a network administrator use to confirm the help desk technician's claim?
A. nmap
B. arp
C. tcpdump
D. dig
A wireless technician needs to deploy a single 802.11 standard that supports both 2.4GHz and 5GHz frequencies with up to 40MHz channel widths. Which of the following wireless standards should the technician configure?
A. ac
B. b
C. g
D. n
A company hires some temporary workers. On day one, the temporary employees report they are unable to connect to the network. A network technician uses a packet analysis tool and finds that many clients are continuously sending out requests for an IP address, but many of them are not receiving a response. Which of the following could be the cause of this issue?
A. Exhausted DHCP scope
B. Untrusted SSL certificates
C. Duplicate MAC addresses
D. Incorrect firewall settings
The security department is looking to install a new IP-based camera. Plugging the camera into the available Ethernet jack does not power on the camera. Upon further investigation, the cable tests fine, and it does provide power to a VoIP phone. Which of the following is MOST likely causing the issue?
A. The brown pair UTP has a short.
B. The camera requires 802.3at power.
C. The camera requires Cat 7 cabling.
D. The switchport has PoE disabled.
A user has reported an issue with wireless VoIP phones dropping calls during business hours. When working late or in the evenings, the user does not experience call drops. When the network technician investigates the issue, all WAPs have balanced the number of connections evenly and are not dropping off the network. The network technician connects to the wireless network in the user's office and starts a continuous ping to an external server. The results show a drastic and varied response time for each packet. Which of the following is the MOST likely cause of the dropped calls?
A. No QoS configured on the network
B. Signal-to-noise ratio
C. Interference from the microwave in the breakroom
D. Rogue AP installed in the office
Which of the following would be the BEST way to track all the networks that are in use at an organization?
A. DHCP
B. IPAM
C. Scope options
D. Lookup zone
Which of the following is the physical topology for an Ethernet LAN?
A. Bus
B. Ring
C. Mesh
D. Star
A technician wants to configure a SOHO network to use a specific public DNS server. Which of the following network components should the technician configure to point all clients on a network to a new DNS server?
A. Router
B. Switch
C. Load balancer
D. Proxy server
A technician is troubleshooting a host that is having intermittent issues connecting to internal network resources and the company servers. Using a packet sniffer, the technician notices there are several TCP communications that are missing packets in sequence and need to be retransmitted. The technician receives several SYN-ACK packets with incorrect addressing. Which of the following is the MOST likely cause of these issues?
A. DNS poisoning attack
B. Evil twin on the company network
C. ARP poisoning attack
D. Misconfigured VLAN on the local switch
A technician has a remote site that often has congestion issues. When this happens, the remote router cannot be managed using SSH because the session drops. Which of the following is a possible solution to the issue?
A. Out-of-band management
B. HTTPS management URL
C. Client-to-site VPN
D. Router ACL
Access Full N10-007 Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete N10-007 Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our N10-007 mock test free today—and take a major step toward exam success!