MD-100 Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your MD-100 certification exam? Start your preparation the smart way with our MD-100 Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for MD-100 exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our MD-100 Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
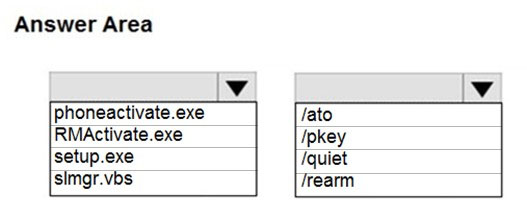
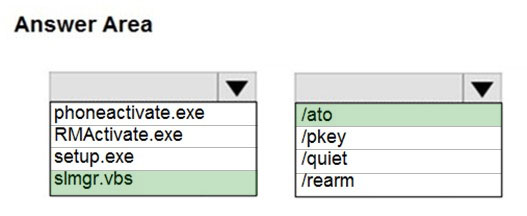
HOTSPOT - Your company uses a Key Management Service (KMS) to activate computers that run Windows 10. A user works remotely and establishes a VPN connection once a month. The computer of the user fails to be activated. Which command should you run on the computer to initiate activation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You install Windows 10 Enterprise on a new computer. You need to force activation on the computer. Which command should you run?
A. slmgr /upk
B. Set-RDLicenseConfiguration -Force
C. Set-MsolLicense -AddLicense
D. slmgr /ato
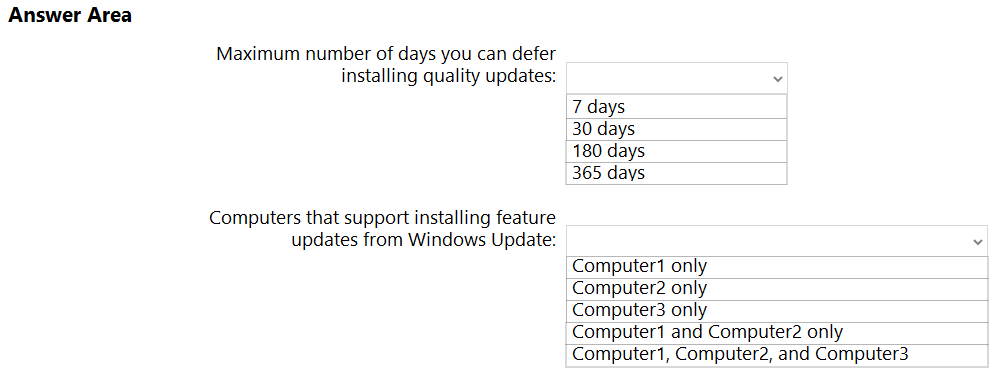
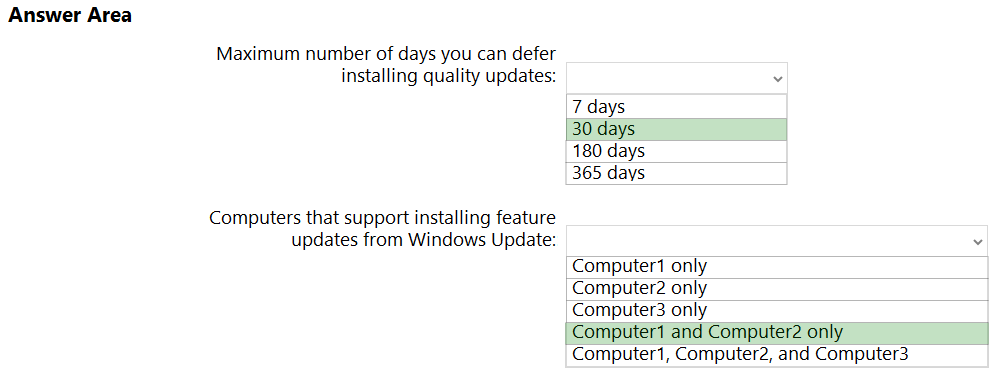
HOTSPOT - You have the computer shown in the following table.You plan to configure deployment rings for Windows 10 quality and feature updates. What is the maximum number of days you can defer installing quality updates, and which computers support installing feature updates from Windows Update? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
Your network contains an Active Directory domain. The domain contains a computer named Computer1 that runs Windows 10. The domain contains the users shown in the following table.Computer1 has four printers as shown in the following table.
Which printers will be available to User1 when the user signs in to Computer1?
A. Printer3 only
B. Printer1 and Printer3 only
C. Printer1, Printer2, and Printer3 only
D. Printer1, Printer3, and Printer4 only
E. Printer1, Printer2, Printer3, and Printer4
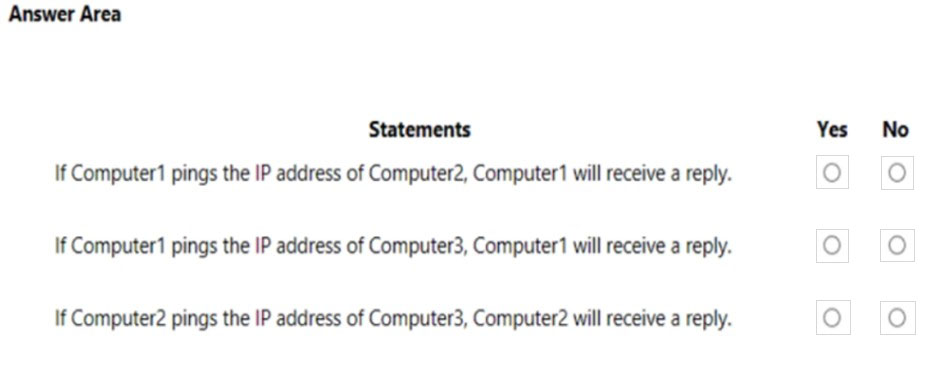
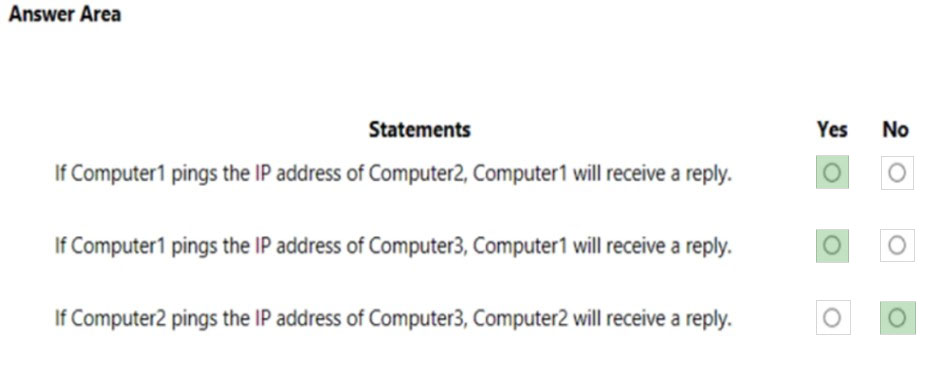
HOTSPOT - You have the network shown in the following exhibit.Computer1, Computer2, and Computer3 run Windows 10. Windows Defender Firewall is configured to allow ICMP traffic. RTR1 is a router. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a laptop named Computer1 that runs Windows 10. When in range, Computer1 connects automatically to a Wi-Fi network named Wireless1. You need to prevent Computer1 from automatically connecting to Wireless1. Solution: From the Services console, you disable the Link-Layer Topology Discovery Mapper service. Does this meet the goal?
A. Yes
B. No
You have a workgroup computer that runs Windows 10. You need to set the minimum password length to 12 characters. What should you use?
A. User Accounts in Control Panel
B. Local Security Policy
C. Credential Manager in Control Panel
D. Email & accounts in the Settings app
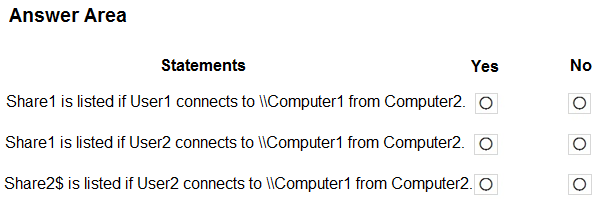
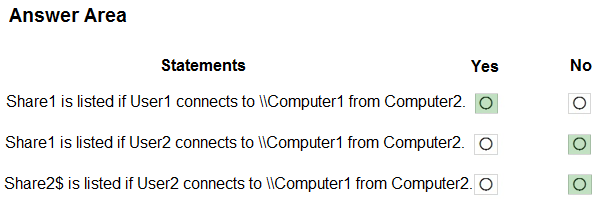
HOTSPOT - Your network contains an Active Directory domain that contains the objects shown in the following table.Computer1 contains the shared folders shown in the following table.
The computers have the network configurations shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a workgroup computer that runs Windows 10. The computer contains the local user accounts shown in the following table.You need to configure the desktop background for User1 and User2 only. Solution: You create two new local Group Policy Objects (GPOs) and apply one GPO to User1 and the other GPO to User2. You configure the Desktop Wallpaper setting in each GPO. Does this meet the goal?
A. Yes
B. No
You have an Azure Active Directory (Azure AD) tenant that contains a user named user1@contoso.com . You have a computer named Computer1 that runs Windows 10. You join Computer1 to Azure AD. You enable Remote Desktop on Computer1. User1@contoso.com attempts to connect to Computer1 by using Remote Desktop and receives the following error message: `The logon attempt failed.` You need to ensure that the user can connect to Computer1 by using Remote Desktop. What should you do first?
A. In Azure AD, assign user1@contoso.com the Cloud device administrator role.
B. From the local Group Policy, modify the Allow log on through Remote Desktop Services user right.
C. In Azure AD, assign user1@contoso.com the Security administrator role.
D. On Computer1, create a local user and add the new user to the Remote Desktop Users group.
You have 100 computers that run Windows 10. The computers are joined to an Azure AD tenant and enrolled in Microsoft Intune. The computers are in remote locations and connected to public networks. You need to recommend a solution for help desk administrators that meets the following requirements: • Connect remotely to a user's computer to perform troubleshooting. • Connect to a user's computer without disrupting the desktop of the computer. • Remotely view services, performance counters, registry settings, and event logs. Which tool should you include in the recommendation?
A. Quick Assist
B. Intune
C. Remote Assistance
D. Windows Admin Center
E. Remote Desktop
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. Your company has an on-premises network that contains an Active Directory domain. The domain is synced to Microsoft Azure Active Directory (Azure AD). All computers in the domain run Windows 10 Enterprise. You are logged on as the local administrator on a Computer named Computer1. A user named Mia Hamm has a computer named Computer2. Mia Hamm reports that she is experiencing problems with Computer2. You want to use Event Viewer on Computer1 to view the event logs on Computer2. What should you do?
A. On Computer1, run the Connect-WSMan -ComputerName “Computer1” cmdlet.
B. On Computer1, run the Get-Eventlog -List -ComputerName “Computer1” cmdlet.
C. On Computer1, log on as a domain administrator, then open Event Viewer and select the Connect to another computer ג€¦ option.
D. On Computer1, open the Windows Defender Firewall and enable the Remote Event Log Management inbound rule.
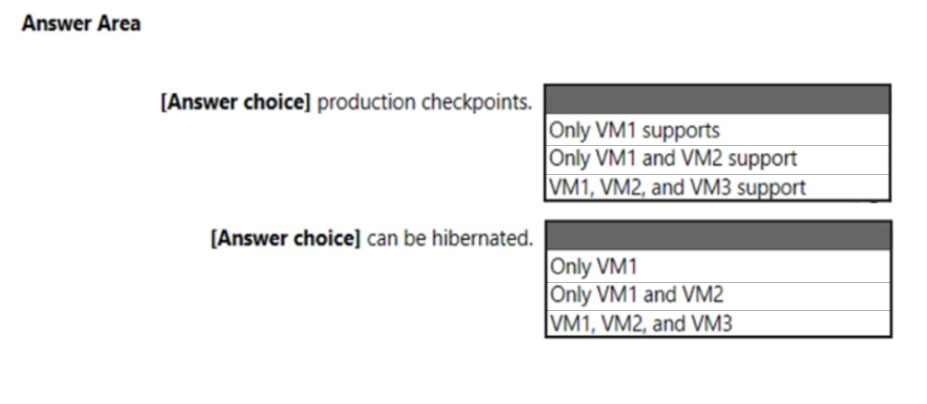
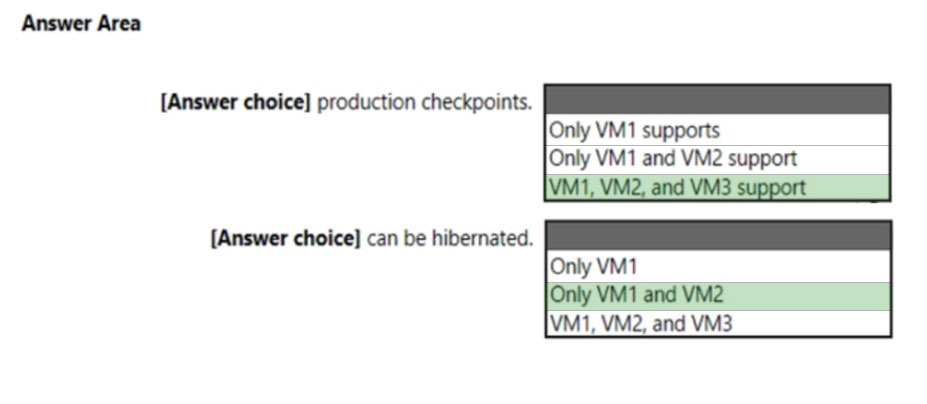
HOTSPOT - You have a computer that runs Windows 11 and hosts three Hyper-V virtual machines named VM1, VM2, and VM3. The virtual machines are configured as shown in the following exhibit.Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point. Hot Area:
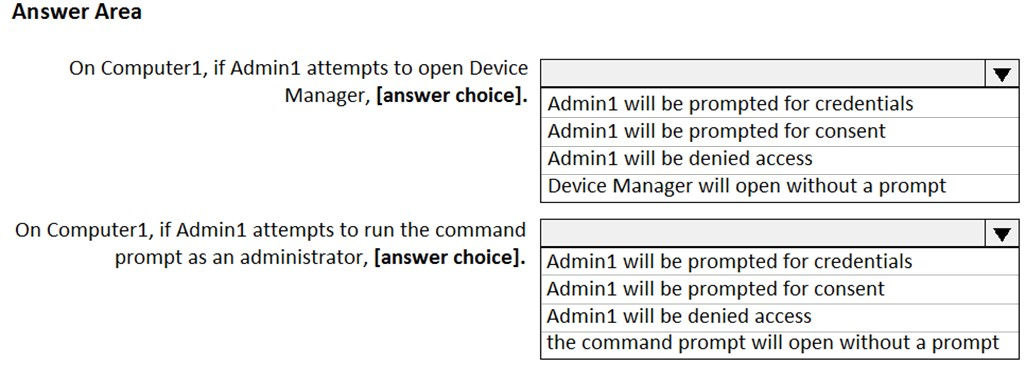
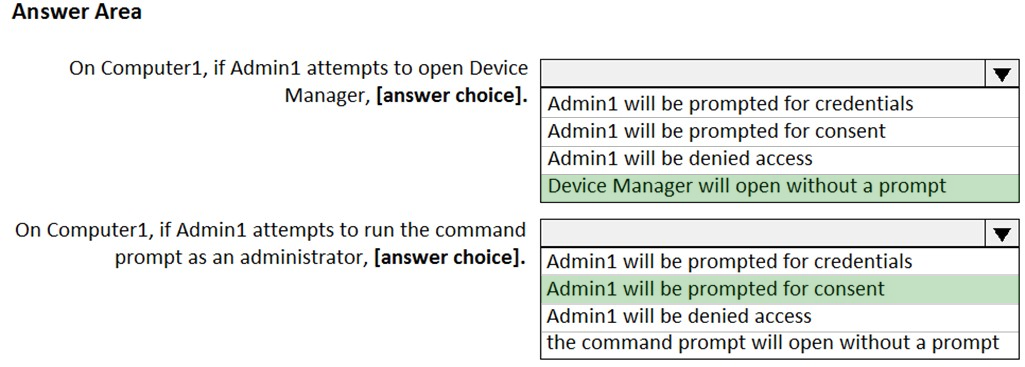
HOTSPOT - You have a computer named Computer1 that runs Windows 10 and is joined to an Active Directory domain named adatum.com. A user named Admin1 signs in to Computer1 and runs the whoami command as shown in the following exhibit.Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point. Hot Area:
Your network contains an Active Directory domain named contoso.com. A user named User1 has a personal computer named Computer1 that runs Windows 10 Pro. User1 has a VPN connection to the corporate network. You need to ensure that when User1 connects to the VPN, network traffic uses a proxy server located in the corporate network. The solution must ensure that User1 can access the Internet when disconnected from the VPN. What should you do?
A. From Control Panel, modify the Windows Defender Firewall settings
B. From the Settings app, modify the Proxy settings for the local computer
C. From Control Panel, modify the properties of the VPN connection
D. From the Settings app, modify the properties of the VPN connection
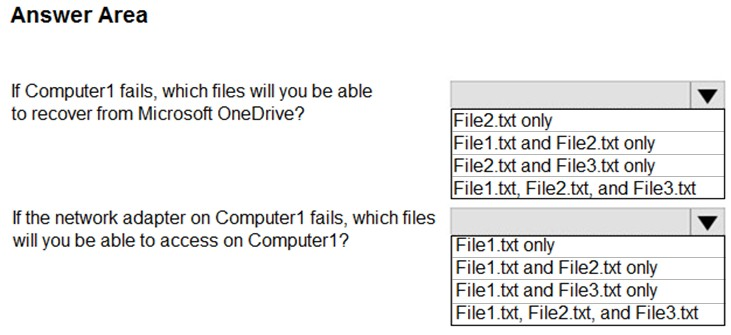
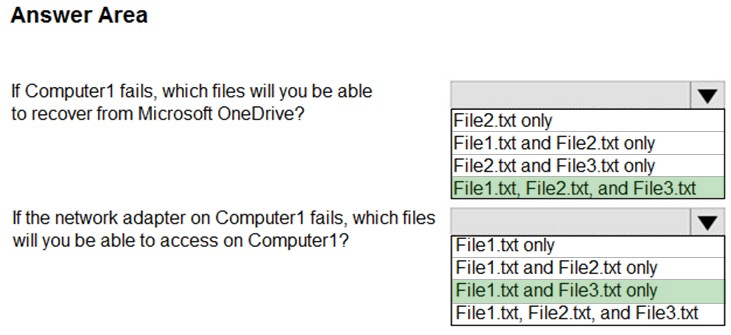
You have a computer that runs Windows 10. You sign in by using your Microsoft account and set up the Microsoft OneDrive sync app to connect to your personal OneDrive account. You plan to configure OneDrive to back up the important PC Folders. Which three folders can be backed up by OneDrive?
A. Desktop, Documents, and Pictures
B. Desktop, Music, and Pictures
C. Documents, Music, and Videos
D. Music, Pictures, and Videos
You have an Azure Active Directory (Azure AD) tenant named contoso.com. You have a workgroup computer named Computer1 that runs Windows 10. You need to add Computer1 to contoso.com. What should you use?
A. Computer Management
B. dsregcmd.exe
C. the Settings app
D. netdom.exe
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You deploy Windows 10 to a computer named Computer1. Computer1 contains a folder named C:Folder1. Folder1 contains multiple documents. You need to ensure that you can recover the files in Folder1 by using the Previous Versions tab. Solution: You select Folder is ready for archiving from the properties of Folder1. Does this meet the goal?
A. Yes
B. No
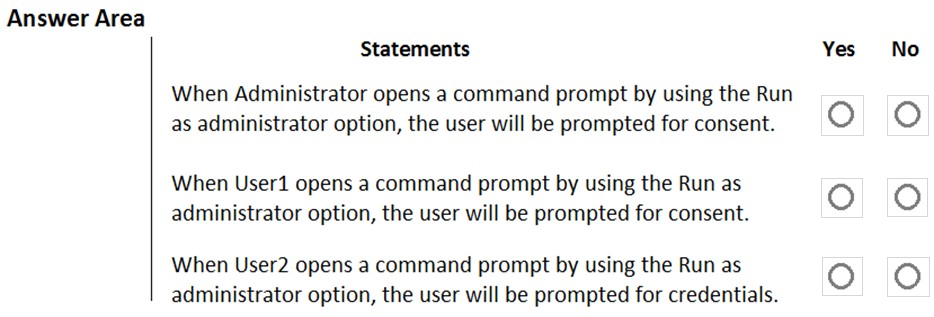
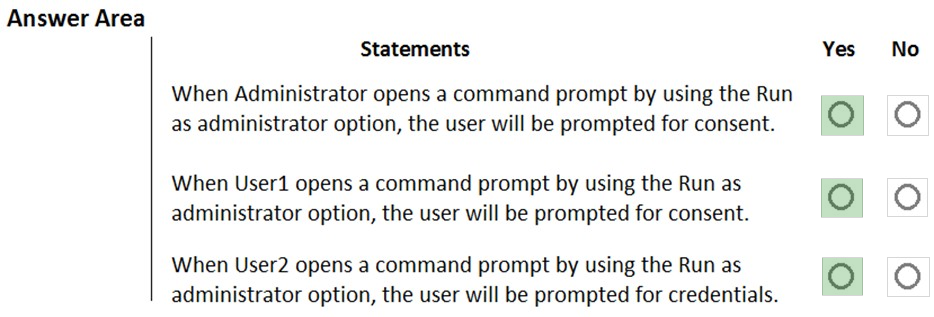
HOTSPOT - You have a workgroup computer named Computer1 that runs Windows 10 and has the users shown in the following table.User Account Control (UAC) on Computer1 is configured as shown in the following exhibit.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
Your company purchases 20 laptops that use a new hardware platform. In a test environment, you deploy Windows 10 to the new laptops. Some laptops frequently generate stop errors. You need to identify the cause of the issue. What should you use?
A. Reliability Monitor
B. Task Manager
C. System Configuration
D. Performance Monitor
HOTSPOT - You have a workgroup computer named Computer1 that runs Windows 10 and contains the users in the following table.You need to identify which users can start the Windows Recovery Environment (WinRE) command prompt on Computer1. Which user should you identify for each scenario? To answer, select the appropriate options in the answer area.
You are troubleshooting the failed installation of a VPN application on a device. During the installation, the application displays a Stop error, and you must restart the device. After the restart, you discover that the device can no longer connect to the network. What should you use to resolve the issue?
A. Network reset
B. Network Adapter troubleshooter
C. Incoming Connections troubleshooter
D. Remote Assistance
A user purchases a new computer that has Windows 10 Home preinstalled. The computer has a biometric fingerprint reader. You need to ensure that the user can use the fingerprint reader to sign in to the computer by using an Azure Active Directory (Azure AD) account. What should you do first?
A. Register the computer to Azure AD.
B. Install the latest feature updates on the computer.
C. Upgrade the computer to Windows 10 Enterprise.
D. Upgrade the computer to Windows 10 Pro.
Your company has an on-premises network that contains an Active Directory domain. The domain is synced to Microsoft Azure Active Directory (Azure AD). All computers in the domain run Windows 10 Enterprise. You have a computer named Computer1 that has a folder named C:Folder1. You want to use File History to protect C:Folder1. Solution: You enable File History on Computer1. You then encrypt the contents of Folder1. Does this meet the goal?
A. Yes
B. No
HOTSPOT - You have a computer that runs Windows 10. You view the domain services status as shown in the following exhibit.Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point. Hot Area:
You have a computer named Computer1 that runs Windows 11 and hosts two Hyper-V virtual machines named VM1 and VM2. You need to ensure that VM1 can connect to the network shares on VM2. The solution must prevent Computer1 from establishing network connections to VM1 or VM2. Which type of virtual switch should you use?
A. external
B. private
C. internal
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. A user named User1 has a computer named Computer1 that runs Windows 10. Computer1 is joined to an Azure Active Directory (Azure AD) tenant named contoso.com. User1 joins Computer1 to contoso.com by using user1@contoso.com . Computer1 contains a folder named Folder1. Folder1 is in drive C and is shared as Share1. Share1 has the permission shown in the following table.A user named User2 has a computer named Computer2 that runs Windows 10. User2 joins Computer2 to contoso.com by using user2@contoso.com . User2 attempts to access Share1 and receives the following error message: `The username or password is incorrect.` You need to ensure that User2 can connect to Share1. Solution: You create a local user account on Computer1 and instruct User2 to use the local account to connect to Share1. Does this meet the goal?
A. Yes
B. No
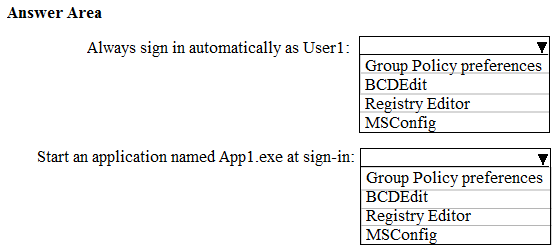
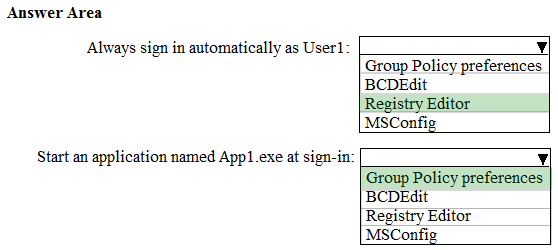
HOTSPOT - You have a computer that runs Windows 10. The computer is in a workgroup. The computer is used to provide visitors with access to the Internet. You need to configure the computer to meet the following requirements: ✑ Always sign in automatically as User1. ✑ Start an application named App1.exe at sign-in. What should you use to meet each requirement? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
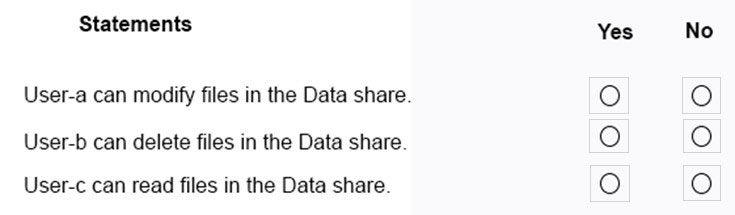
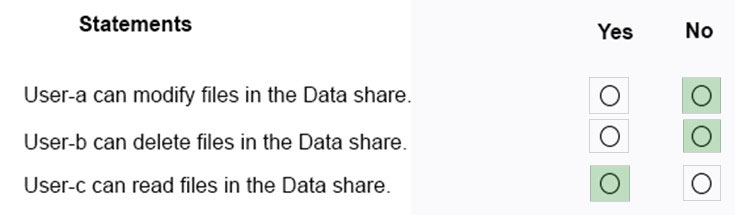
HOTSPOT - You have a computer named Computer5 that runs Windows 10 that is used to share documents in a workgroup. You create three users named User-a, User-b, and User-c by using Computer Management. The users plan to access Computer5 from the network only. You have a folder named Data. The Advanced Security Settings for the Data folder are shown in the Security exhibit. (Click the Security tab).You share the Data folder. The permissions for User-a are shown in the User-a exhibit (Click the User-a tab.)
The permissions for User-b are shown in the User-b exhibit. (Click the User-b tab.)
The permissions for User-c are shown in the User-c exhibit. (Click the User-c tab.)
For each of the following statements, select Yes if the statements is true. Otherwise, select No. NOTE: Reach correct selection is worth one point. Hot Area:
Your company uses Microsoft Deployment Toolkit (MDT) to deploy Windows 10 to new computers. The company purchases 1,000 new computers. You need to ensure that the Hyper-V feature is enabled on the computers during the deployment. What are two possible ways to achieve this goal? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. Add a task sequence step that adds a provisioning package.
B. In a Group Policy object (GPO), from Computer Configuration, configure Application Control Policies.
C. Add a custom command to the Unattend.xml file.
D. Add a configuration setting to Windows Deployment Services (WDS).
E. Add a task sequence step that runs dism.exe.
You have a computer named Computer1 that runs Windows 11. You are often prompted to restart Computer1 after Windows updates are installed. You need to minimize disruptions caused by restarting Computer1. What should you configure?
A. Download updates over metered connections
B. Delivery Optimization
C. Focus assist
D. Active hours
SIMULATION - Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time. When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design. Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn't matter how you accomplish the task, if you successfully perform it, you will earn credit for that task. Labs are not timed separately, and this exam may more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided. Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab. Username and password -Use the following login credentials as needed: To enter your password, place your cursor in the Enter password box and click on the password below. Username: Contoso/Administrator - Password: Passw0rd! The following information is for technical support purposes only: Lab Instance: 10921597 -
You need to ensure that you can successfully ping DC1 from Client3 by using the IP4 address of DC1. To complete this task, sign in to the required computer or computers.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. A user named User1 has a computer named Computer1 that runs Windows 10. Computer1 is joined to an Azure Active Directory (Azure AD) tenant named contoso.com. User1 joins Computer1 to contoso.com by using user1@contoso.com . Computer1 contains a folder named Folder1. Folder1 is in drive C and is shared as Share1. Share1 has the permission shown in the following table.A user named User2 has a computer named Computer2 that runs Windows 10. User2 joins Computer2 to contoso.com by using user2@contoso.com . User2 attempts to access Share1 and receives the following error message: `The username or password is incorrect.` You need to ensure that User2 can connect to Share1. Solution: In Azure AD, you create a group named Group1 that contains User1 and User2. You grant Group1 Modify access to Folder1. Does this meet the goal?
A. Yes
B. No
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have two computers named Computer1 and Computer2 that run Windows 10. You have an Azure Active Directory (Azure AD) user account named admin@contoso.com that is in the local Administrators group on each computer. You sign in to Computer1 by using admin@contoso.com . You need to ensure that you can use Event Viewer on Computer1 to connect to the event logs on Computer2. Solution: On Computer2, you enable the Remote Event Log Management inbound rule from Windows Defender Firewall. Does this meet the goal?
A. Yes
B. No
Your network contains an Active Directory domain. The domain contains 500 computers that run Windows 10. The computers are used as shown in the following table.You need to apply updates based on the computer usage. What should you configure?
A. Notifications & actions from System in the Settings apps.
B. the Windows Update for Business settings by using a Group Policy Object (GPO)
C. the Windows Installer settings by using a Group Policy Object (GPO)
D. Delivery Optimization from Update & Security in the Settings apps
SIMULATION - Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time. When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design. Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn't matter how you accomplish the task, if you successfully perform it, you will earn credit for that task. Labs are not timed separately, and this exam may more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided. Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab. Username and password -Use the following login credentials as needed: To enter your password, place your cursor in the Enter password box and click on the password below. Username: Contoso/Administrator - Password: Passw0rd! The following information is for technical support purposes only: Lab Instance: 11145882 -
You need to ensure that C:ScriptsConfigure.ps1 runs every time a user sign in to Client2. To complete this task, sign in to the required computer or computers.
You have a computer that runs Windows 10. You discover that Windows updates are failing to install on the computer. You need to generate a log file that contains detailed information about the failures. Which cmdlet should you run?
A. Getג€”LogProperties
B. Getג€”WindowsErrorReporting
C. Getג€”WindowsUpdateLog
D. Getג€”WinEvent
You have a computer that runs Windows 10 Pro. The computer contains the users shown in the following table.You need to use a local Group Policy Object (GPO) to configure one group of settings for all the members of the local Administrators group and another group of settings for all non-administrators. What should you do?
A. Use the runas command to open Gpedit.msc as each user.
B. Run mmc as User1 and add the Group Policy Object Editor snap-in twice.
C. Open Gpedit.msc as User1 and add two Administrative Templates.
D. Run mmc as User1 and add the Security Templates snap-in twice.
You have several computers that run Windows 10. The computers are in a workgroup and have BitLocker Drive Encryption (BitLocker) enabled. You join the computers to Microsoft Azure Active Directory (Azure AD). You need to ensure that you can recover the BitLocker recovery key for the computers from Azure AD. What should you do first?
A. Disable BitLocker.
B. Add a BitLocker key protector.
C. Suspend BitLocker.
D. Disable the TMP chip.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a computer named Computer1 that runs Windows 10. You test Windows updates on Computer1 before you make the updates available to other computers. You install a quality update that conflicts with a custom device driver. You need to remove the update from Computer1. Solution: From an elevated command prompt, you run the wusa.exe command and specify the /uninstall parameter. Does this meet the goal?
A. Yes
B. No
You have a computer that runs Windows 10 and is joined to Azure Active Directory (Azure AD). You attempt to open Control Panel and receive the error message shown on the following exhibit.You need to be able to access Control Panel. What should you modify?
A. the PowerShell execution policy
B. the local Group Policy
C. the Settings app
D. a Group Policy preference
You have a computer that is configured as shown in the following exhibit.What can the computer connect to?
A. all the local computers and the remote computers within your corporate network only
B. all the local computers and the remote computers, including Internet hosts
C. only other computers on the same network segment that have automatic private IP addressing (APIPA)
D. only other computers on the same network segment that have an address from a class A network ID
You enable controlled folder access in audit mode for several computers that run Windows 10. You need to review the events audited by controlled folder access. Which Event Viewer log should you view?
A. WindowsSecurity
B. Applications and ServicesMicrosoftWindowsKnown FoldersOperational
C. Applications and ServicesMicrosoftWindowsWindows DefenderOperational
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. A user named User1 has a computer named Computer1 that runs Windows 10. Computer1 is joined to an Azure Active Directory (Azure AD) tenant named contoso.com. User1 joins Computer1 to contoso.com by using user1@contoso.com . Computer1 contains a folder named Folder1. Folder1 is in drive C and is shared as Share1. Share1 has the permission shown in the following table.A user named User2 has a computer named Computer2 that runs Windows 10. User2 joins Computer2 to contoso.com by using user2@contoso.com . User2 attempts to access Share1 and receives the following error message: `The username or password is incorrect.` You need to ensure that User2 can connect to Share1. Solution: In Azure AD, you create a group named Group1 that contains User1 and User2. You grant Group1 Change access to Share1. Does this meet the goal?
A. Yes
B. No
HOTSPOT - You have a workgroup computer named Computer1 that runs Windows 10. From File Explorer, you open OneDrive as shown in the following exhibit.Use the drop-down menus to select the answer choice that answers each question based on the information presented on the graphic. NOTE: Each correct selection is worth one point. Hot Area:
Which users can sign in to Computer3 when the computer starts in Safe Mode?
A. User31 only
B. User31 and User32 only
C. User31 and Admin1 only
D. User31, User 32, User33, and Admin1
E. User31, User32, and User33 only
Your company is not connected to the internet. The company purchases several new computers with Windows 10 Pro for its users. None of the new computers are activated. You need to activate the computers without connecting the network to the Internet. What should you do?
A. Make use of the Volume Activation Management Tool (VAMT).
B. Make use of the Key Management Service (KMS).
C. Make use of the Windows Process Activation Service.
D. Run the Get-WmiObject -query cmdlet.
You have a computer named Computer1 that runs Windows 10. On Computer1, you create the local users shown in the following table.Which two user profiles will persist after each user signs out? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. User1
B. User2
C. User3
D. User4
E. User5
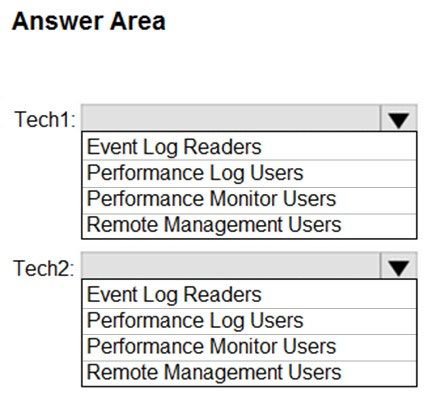
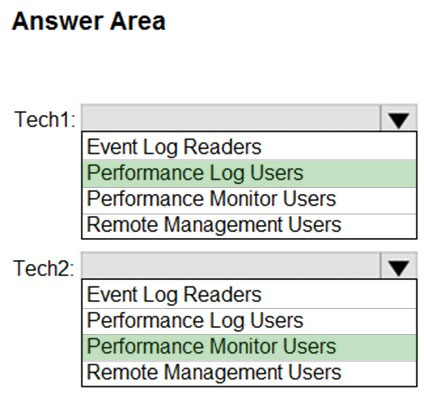
HOTSPOT - You have 100 computers that run Windows 10 and are members of an Active Directory domain. Two support technicians named Tech1 and Tech2 will be responsible for monitoring the performance of the computers. You need to configure the computers to meet the following requirements: ✑ Ensure that Tech1 can create and manage Data Collector Sets (DCSs). ✑ Ensure that Tech2 can start and stop the DCSs. ✑ Use the principle of least privilege. To which group should you add each technician? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a computer that runs Windows 10. The computer contains a folder. The folder contains sensitive data. You need to log which user reads the contents of the folder and modifies and deletes files in the folder. Solution: From the properties of the folder, you configure the Auditing settings and from Audit Policy in the local Group Policy, you configure Audit object access. Does this meet the goal?
A. Yes
B. No
Access Full MD-100 Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete MD-100 Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our MD-100 mock test free today—and take a major step toward exam success!