CS0-001 Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your CS0-001 certification exam? Start your preparation the smart way with our CS0-001 Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for CS0-001 exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our CS0-001 Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
An organization recently had its strategy posted to a social media website. The document posted to the website is an exact copy of a document stored on only one server in the organization. A security analyst sees the following output from a command-line entry on the server suspected of the problem:Which of the following would be the BEST course of action?
A. Remove the malware associated with PID 773
B. Monitor all the established TCP connections for data exfiltration
C. Investigate the malware associated with PID 123
D. Block all TCP connections at the firewall
E. Figure out which of the Firefox processes is the malware
The computer incident response team at a multinational company has determined that a breach of sensitive data has occurred in which a threat actor has compromised the organization's email system. Per the incident response procedures, this breach requires notifying the board immediately. Which of the following would be the BEST method of communication?
A. Post of the company blog
B. Corporate-hosted encrypted email
C. VoIP phone call
D. Summary sent by certified mail
E. Externally hosted instant message
Which of the following is a vulnerability when using Windows as a host OS for virtual machines?
A. Windows requires frequent patching.
B. Windows virtualized environments are typically unstable.
C. Windows requires hundreds of open firewall ports to operate.
D. Windows is vulnerable to the “ping of death”.
A security analyst received an email with the following key: Xj3XJ3LLc - A second security analyst received an email with following key: 3XJ3xjcLLC The security manager has informed the two analysts that the email they received is a key that allows access to the company's financial segment for maintenance. This is an example of:
A. dual control
B. private key encryption
C. separation of duties
D. public key encryption
E. two-factor authentication
A threat intelligence analyst who works for a technology firm received this report from a vendor. "There has been an intellectual property theft campaign executed against organizations in the technology industry. Indicators for this activity are unique to each intrusion. The information that appears to be targeted is R&D data. The data exfiltration appears to occur over months via uniform TTPs. Please execute a defensive operation regarding this attack vector." Which of the following combinations suggests how the threat should MOST likely be classified and the type of analysis that would be MOST helpful in protecting against this activity?
A. Polymorphic malware and secure code analysis
B. Insider threat and indicator analysis
C. APT and behavioral analysis
D. Ransomware and encryption
A worm was detected on multiple PCs within the remote office. The security analyst recommended that the remote office be blocked from the corporate network during the incident response. Which of the following processes BEST describes this recommendation?
A. Logical isolation of the remote office
B. Sanitization of the network environment
C. Segmentation of the network
D. Secure disposal of affected systems
An analyst is observing unusual network traffic from a workstation. The workstation is communicating with a known malicious site over an encrypted tunnel. A full antivirus scan with an updated antivirus signature file does not show any sign of infection. Which of the following has occurred on the workstation?
A. Zero-day attack
B. Known malware attack
C. Session hijack
D. Cookie stealing
An analyst was testing the latest version of an internally developed CRM system. The analyst created a basic user account. Using a few tools in Kali's latest distribution, the analyst was able to access configuration files, change permissions on folders and groups, and delete and create new system objects. Which of the following techniques did the analyst use to perform these unauthorized activities?
A. Impersonation
B. Privilege escalation
C. Directory traversal
D. Input injection
A security administrator needs to create an IDS rule to alert on FTP login attempts by root. Which of the following rules is the BEST solution?
A. Option A
B. Option B
C. Option C
D. Option D
A cybersecurity analyst has received the laptop of a user who recently left the company. The analyst types "˜history' into the prompt, and sees this line of code in the latest bash history:This concerns the analyst because this subnet should not be known to users within the company. Which of the following describes what this code has done on the network?
A. Performed a ping sweep of the Class C network.
B. Performed a half open SYB scan on the network.
C. Sent 255 ping packets to each host on the network.
D. Sequentially sent an ICMP echo reply to the Class C network.
In the development stage of the incident response policy, the security analyst needs to determine the stakeholders for the policy. Who of the following would be the policy stakeholders?
A. Human resources, legal, public relations, management
B. Chief Information Officer (CIO), Chief Executive Officer, board of directors, stockholders
C. IT, human resources, security administrator, finance
D. Public information officer, human resources, audit, customer service
A vulnerability scan returned the following results for a web server that hosts multiple wiki sites: Apache-HTTPD-cve-2014-023: Apache HTTPD: mod_cgid denial of service CVE-2014-0231 Due to a flaw found in mod_cgid, a server using mod_cgid to host CGI scripts could be vulnerable to a DoS attack caused by a remote attacker who is exploiting a weakness in non-standard input, causing processes to hang indefinitely.The security analyst has confirmed the server hosts standard CGI scripts for the wiki sites, does not have mod_cgid installed, is running Apache 2.2.22, and is not behind a WAF. The server is located in the DMZ, and the purpose of the server is to allow customers to add entries into a publicly accessible database. Which of the following would be the MOST efficient way to address this finding?
A. Place the server behind a WAF to prevent DoS attacks from occurring.
B. Document the finding as a false positive.
C. Upgrade to the newest version of Apache.
D. Disable the HTTP service and use only HTTPS to access the server.
A Chief Information Security Officer (CISO) wants to standardize the company's security program so it can be objectively assessed as part of an upcoming audit requested by management. Which of the following would holistically assist in this effort?
A. ITIL
B. NIST
C. Scrum
D. AUP
E. Nessus
An ATM in a building lobby has been compromised. A security technician has been advised that the ATM must be forensically analyzed by multiple technicians. Which of the following items in a forensic tool kit would likely be used FIRST? (Choose two.)
A. Drive adapters
B. Chain of custody form
C. Write blockers
D. Crime tape
E. Hashing utilities
F. Drive imager
A company has been a victim of multiple volumetric DoS attacks. Packet analysis of the offending traffic shows the following:Which of the following mitigation techniques is MOST effective against the above attack?
A. The company should contact the upstream ISP and ask that RFC1918 traffic be dropped.
B. The company should implement a network-based sinkhole to drop all traffic coming from 192.168.1.1 at their gateway router.
C. The company should implement the following ACL at their gateway firewall: DENY IP HOST 192.168.1.1 170.43.30.0/24.
D. The company should enable the DoS resource starvation protection feature of the gateway NIPS.
A SIEM alert occurs with the following output:Which of the following BEST describes this alert?
A. The alert is a false positive; there is a device with dual NICs
B. The alert is valid because IP spoofing may be occurring on the network
C. The alert is a false positive; both NICs are of the same brand
D. The alert is valid because there may be a rogue device on the network
The security team for a large, international organization is developing a vulnerability management program. The development staff has expressed concern that the new program will cause service interruptions and downtime as vulnerabilities are remedied. Which of the following should the security team implement FIRST as a core component of the remediation process to address this concern?
A. Automated patch management
B. Change control procedures
C. Security regression testing
D. Isolation of vulnerable servers
A software development company in the manufacturing sector has just completed the alpha version of its flagship application. The application has been under development for the past three years. The SOC has seen intrusion attempts made by indicators associated with a particular APT. The company has a hot site location for COOP. Which of the following threats would most likely incur the BIGGEST economic impact for the company?
A. DDoS
B. ICS destruction
C. IP theft
D. IPS evasion
Which of the following BEST describes why vulnerabilities found in ICS and SCADA can be difficult to remediate?
A. ICS/SCADA systems are not supported by the CVE publications.
B. ICS/SCADA systems rarely have full security functionality.
C. ICS/SCADA systems do not allow remote connections.
D. ICS/SCADA systems use encrypted traffic to communicate between devices.
A security analyst is attempting to configure a vulnerability scan for a new segment on the network. Given the requirement to prevent credentials from traversing the network while still conducting a credentialed scan, which of the following is the BEST choice?
A. Install agents on the endpoints to perform the scan
B. Provide each endpoint with vulnerability scanner credentials
C. Encrypt all of the traffic between the scanner and the endpoint
D. Deploy scanners with administrator privileges on each endpoint
Joe, an analyst, has received notice that a vendor who is coming in for a presentation will require access to a server outside the network. Currently, users are only able to access remote sites through a VPN connection. Which of the following should Joe use to BEST accommodate the vendor?
A. Allow incoming IPSec traffic into the vendor’s IP address.
B. Set up a VPN account for the vendor, allowing access to the remote site.
C. Turn off the firewall while the vendor is in the office, allowing access to the remote site.
D. Write a firewall rule to allow the vendor to have access to the remote site.
Which of the following describes why it is important to include scope within the rules of engagement of a penetration test?
A. To ensure the network segment being tested has been properly secured
B. To ensure servers are not impacted and service is not degraded
C. To ensure all systems being scanned are owned by the company
D. To ensure sensitive hosts are not scanned
A recent audit included a vulnerability scan that found critical patches released 60 days prior were not applied to servers in the environment. The infrastructure team was able to isolate the issue and determined it was due to a service being disabled on the server running the automated patch management application. Which of the following would be the MOST efficient way to avoid similar audit findings in the future?
A. Implement a manual patch management application package to regain greater control over the process.
B. Create a patch management policy that requires all servers to be patched within 30 days of patch release.
C. Implement service monitoring to validate that tools are functioning properly.
D. Set services on the patch management server to automatically run on start-up.
An analyst has received unusual alerts on the SIEM dashboard. The analyst wants to get payloads that the hackers are sending toward the target systems without impacting the business operation. Which of the following should the analyst implement?
A. Honeypot
B. Jump box
C. Sandboxing
D. Virtualization
A retail corporation with widely distributed store locations and IP space must meet PCI requirements relating to vulnerability scanning. The organization plans to outsource this function to a third party to reduce costs. Which of the following should be used to communicate expectations related to the execution of scans?
A. Vulnerability assessment report
B. Lessons learned documentation
C. SLA
D. MOU
The IT department at a growing law firm wants to begin using a third-party vendor for vulnerability monitoring and mitigation. The executive director of the law firm wishes to outline the assumptions and expectations between the two companies. Which of the following documents might be referenced in the event of a security breach at the law firm?
A. SLA
B. MOU
C. SOW
D. NDA
A network technician is concerned that an attacker is attempting to penetrate the network, and wants to set a rule on the firewall to prevent the attacker from learning which IP addresses are valid on the network. Which of the following protocols needs to be denied?
A. TCP
B. SMTP
C. ICMP
D. ARP
Ann, a user, reports to the security team that her browser began redirecting her to random sites while using her Windows laptop. Ann further reports that the OS shows the C: drive is out of space despite having plenty of space recently. Ann claims she not downloaded anything. The security team obtains the laptop and begins to investigate, noting the following: ✑ File access auditing is turned off. When clearing up disk space to make the laptop functional, files that appear to be cached web pages are immediately created in a temporary directory, fillingup the available drive space. ✑ All processes running appear to be legitimate processes for this user and machine. ✑ Network traffic spikes when the space is cleared on the laptop. ✑ No browser is open. Which of the following initial actions and tools would provide the BEST approach to determining what is happening?
A. Delete the temporary files, run an Nmap scan, and utilize Burp Suite.
B. Disable the network connection, check Sysinternals Process Explorer, and review netstat output.
C. Perform a hard power down of the laptop, take a dd image, and analyze with FTK.
D. Review logins to the laptop, search Windows Event Viewer, and review Wireshark captures.
A user received an invalid password response when trying to change the password. Which of the following policies could explain why the password is invalid?
A. Access control policy
B. Account management policy
C. Password policy
D. Data ownership policy
An organization has recently recovered from an incident where a managed switch had been accessed and reconfigured without authorization by an insider. The incident response team is working on developing a lessons learned report with recommendations. Which of the following recommendations will BEST prevent the same attack from occurring in the future?
A. Remove and replace the managed switch with an unmanaged one.
B. Implement a separate logical network segment for management interfaces.
C. Install and configure NAC services to allow only authorized devices to connect to the network.
D. Analyze normal behavior on the network and configure the IDS to alert on deviations from normal.
While reviewing three months of logs, a security analyst notices probes from random company laptops going to SCADA equipment at the company's manufacturing location. Some of the probes are getting responses from the equipment even though firewall rules are in place, which should block this type of unauthorized activity. Which of the following should the analyst recommend to keep this activity from originating from company laptops?
A. Implement a group policy on company systems to block access to SCADA networks.
B. Require connections to the SCADA network to go through a forwarding proxy.
C. Update the firewall rules to block SCADA network access from those laptop IP addresses.
D. Install security software and a host-based firewall on the SCADA equipment.
A SIEM analyst noticed a spike in activities from the guest wireless network to several electronic health record (EHR) systems. After further analysis, the analyst discovered that a large volume of data has been uploaded to a cloud provider in the last six months. Which of the following actions should the analyst do FIRST?
A. Contact the Office of Civil Rights (OCR) to report the breach
B. Notify the Chief Privacy Officer (CPO)
C. Activate the incident response plan
D. Put an ACL on the gateway router
A cybersecurity analyst is investigating an incident report concerning a specific user workstation. The workstation is exhibiting high CPU and memory usage, even when first started, and network bandwidth usage is extremely high. The user reports that applications crash frequently, despite the fact that no significant changes in work habits have occurred. An antivirus scan reports no known threats. Which of the following is the MOST likely reason for this?
A. Advanced persistent threat
B. Zero day
C. Trojan
D. Logic bomb
While preparing for a third-party audit, the vice president of risk management and the vice president of information technology have stipulated that the vendor may not use offensive software during the audit. This is an example of:
A. organizational control.
B. service-level agreement.
C. rules of engagement.
D. risk appetite
A new security manager was hired to establish a vulnerability management program. The manager asked for a corporate strategic plan and risk register that the project management office developed. The manager conducted a tools and skill sets inventory to document the plan. Which of the following is a critical task for the establishment of a successful program?
A. Establish continuous monitoring
B. Update vulnerability feed
C. Perform information classification
D. Establish corporate policy
A security analyst's daily review of system logs and SIEM showed fluctuating patterns of latency. During the analysis, the analyst discovered recent attempts of intrusion related to malware that overwrites the MBR. The facilities manager informed the analyst that a nearby construction project damaged the primary power lines, impacting the analyst's support systems. The electric company has temporarily restored power, but the area may experience temporary outages. Which of the following issues the analyst focus on to continue operations?
A. Updating the ACL
B. Conducting backups
C. Virus scanning
D. Additional log analysis
A production web server is experiencing performance issues. Upon investigation, new unauthorized applications have been installed and suspicious traffic was sent through an unused port. Endpoint security is not detecting any malware or virus. Which of the following types of threats would this MOST likely be classified as?
A. Advanced persistent threat
B. Buffer overflow vulnerability
C. Zero day
D. Botnet
A cybersecurity analyst is hired to review the security measures implemented within the domain controllers of a company. Upon review, the cybersecurity analyst notices a brute force attack can be launched against domain controllers that run on a Windows platform. The first remediation step implemented by the cybersecurity analyst is to make the account passwords more complex. Which of the following is the NEXT remediation step the cybersecurity analyst needs to implement?
A. Disable the ability to store a LAN manager hash.
B. Deploy a vulnerability scanner tool.
C. Install a different antivirus software.
D. Perform more frequent port scanning.
E. Move administrator accounts to a new security group.
Which of the following has the GREATEST impact to the data retention policies of an organization?
A. The CIA classification matrix assigned to each piece of data
B. The level of sensitivity of the data established by the data owner
C. The regulatory requirements concerning the data set
D. The technical constraints of the technology used to store the data
Which of the following policies BEST explains the purpose of a data ownership policy?
A. The policy should describe the roles and responsibilities between users and managers, and the management of specific data types.
B. The policy should establish the protocol for retaining information types based on regulatory or business needs.
C. The policy should document practices that users must adhere to in order to access data on the corporate network or Internet.
D. The policy should outline the organization’s administration of accounts for authorized users to access the appropriate data.
A security analyst wants to confirm a finding from a penetration test report on the internal web server. To do so, the analyst logs into the web server using SSH to send the request locally. The report provides a link to https://hrserver.internal/../../etc/passwd, and the server IP address is 10.10.10.15. However, after several attempts, the analyst cannot get the file, despite attempting to get it using different ways, as shown below.Which of the following would explain this problem? (Choose two.)
A. The web server uses SNI to check for a domain name
B. Requests can only be sent remotely to the web server
C. The password file is write protected
D. The web service has not started
E. There is no local name resolution for hrserver internal.
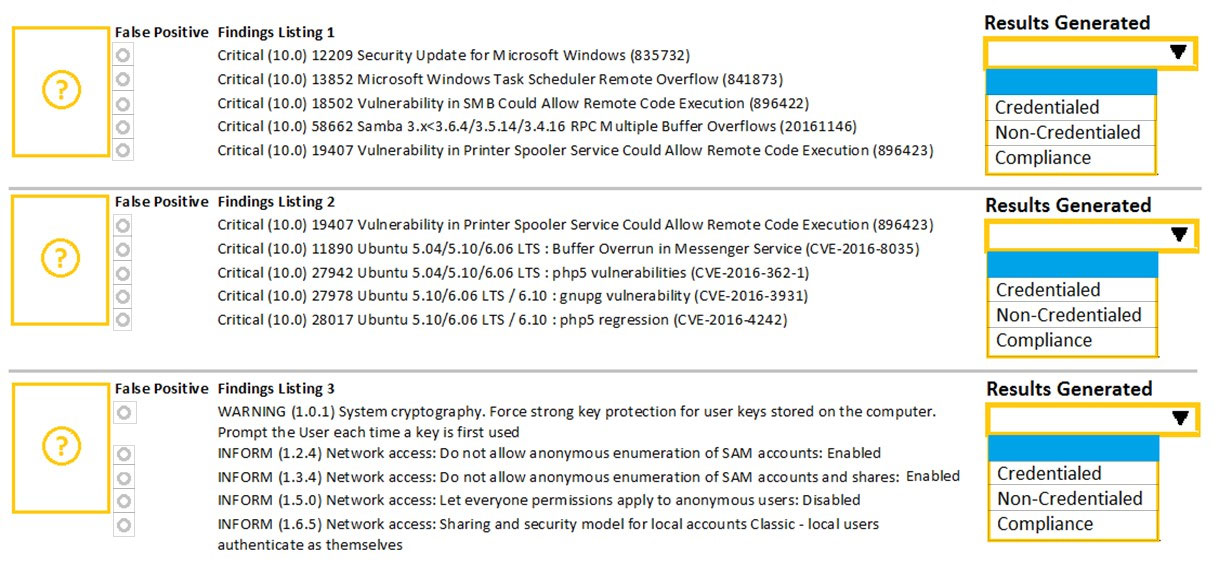
HOTSPOT - A security analyst performs various types of vulnerability scans. Review the vulnerability scan results to determine the type of scan that was executed and if a false positive occurred for each device. Instructions: Select the Results Generated drop-down option to determine if the results were generated from a credentialed scan, non-credentialed scan, or a compliance scan. For ONLY the credentialed and non-credentialed scans, evaluate the results for false positives and check the findings that display false positives. NOTE: If you would like to uncheck an option that is currently selected, click on the option a second time. Lastly, based on the vulnerability scan results, identify the type of Server by dragging the Server to the results. The Linux Web Server, File-Print Server and Directory Server are draggable. If at any time you would like to bring back the initial state of the simulation, please select the Reset All button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.Hot Area:
A security analyst has just completed a vulnerability scan of servers that support a business critical application that is managed by an outside vendor. The results of the scan indicate the devices are missing critical patches. Which of the following factors can inhibit remediation of these vulnerabilities? (Choose two.)
A. Inappropriate data classifications
B. SLAs with the supporting vendor
C. Business process interruption
D. Required sandbox testing
E. Incomplete asset inventory
An HR employee began having issues with a device becoming unresponsive after attempting to open an email attachment. When informed, the security analyst became suspicious of the situation, even though there was not any unusual behavior on the IDS or any alerts from the antivirus software. Which of the following BEST describes the type of threat in this situation?
A. Packet of death
B. Zero-day malware
C. PII exfiltration
D. Known virus
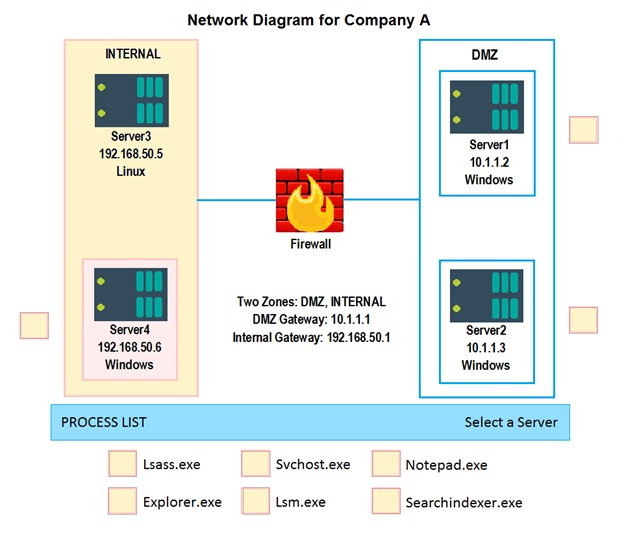
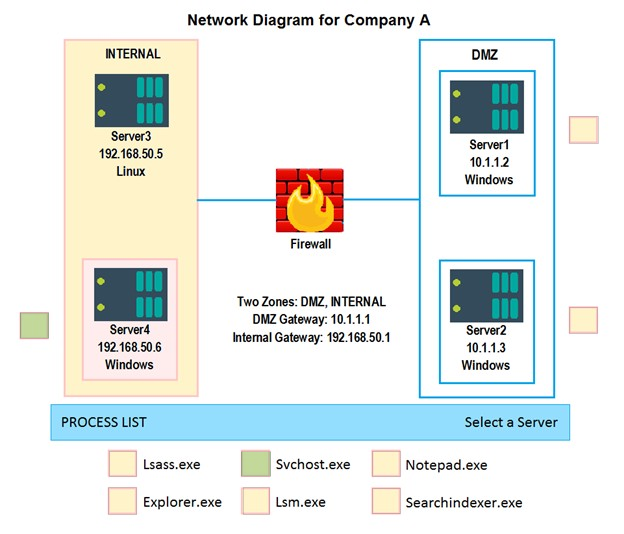
HOTSPOT - Malware is suspected on a server in the environment. The analyst is provided with the output of commands from servers in the environment and needs to review all output files in order to determine which process running on one of the servers may be malware. Instructions: Servers 1, 2 and 4 are clickable. Select the Server which hosts the malware, and select the process which hosts this malware. If any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.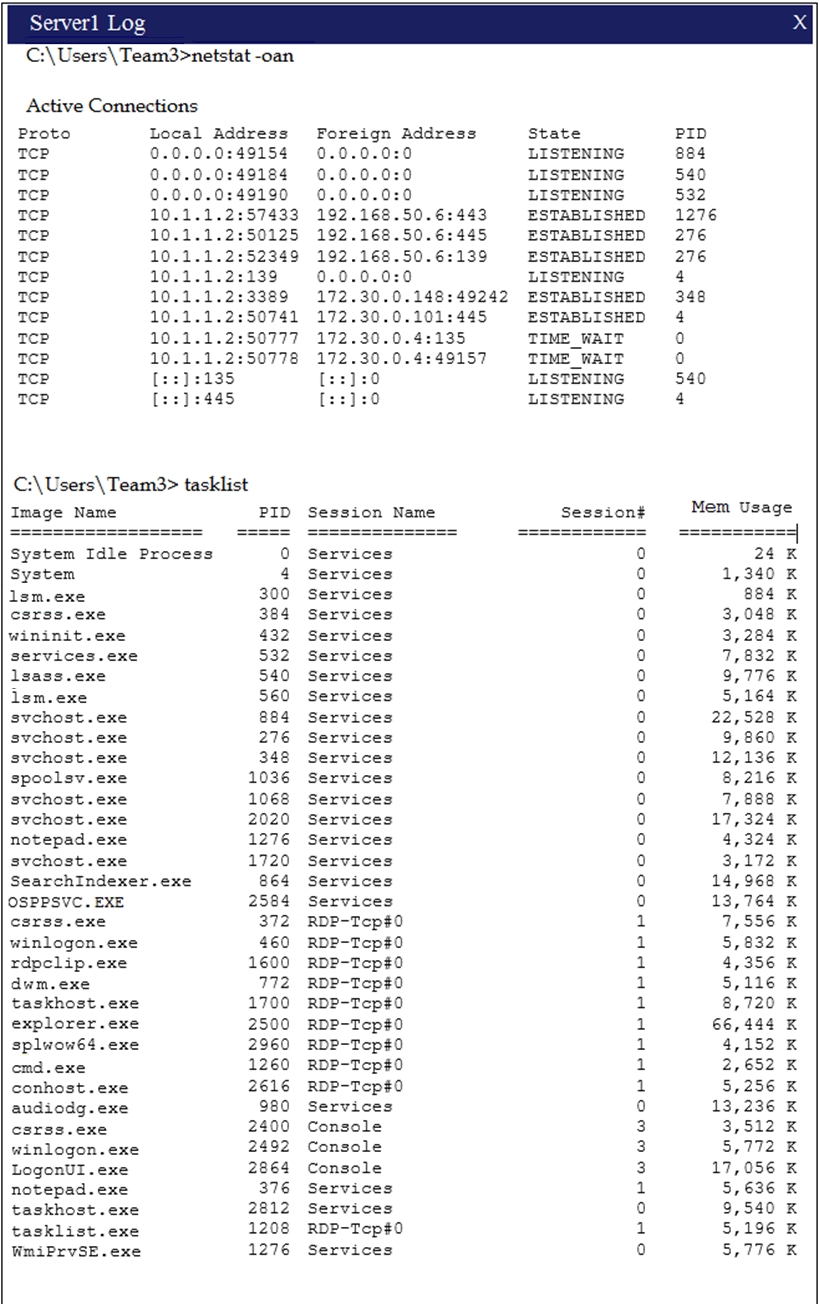
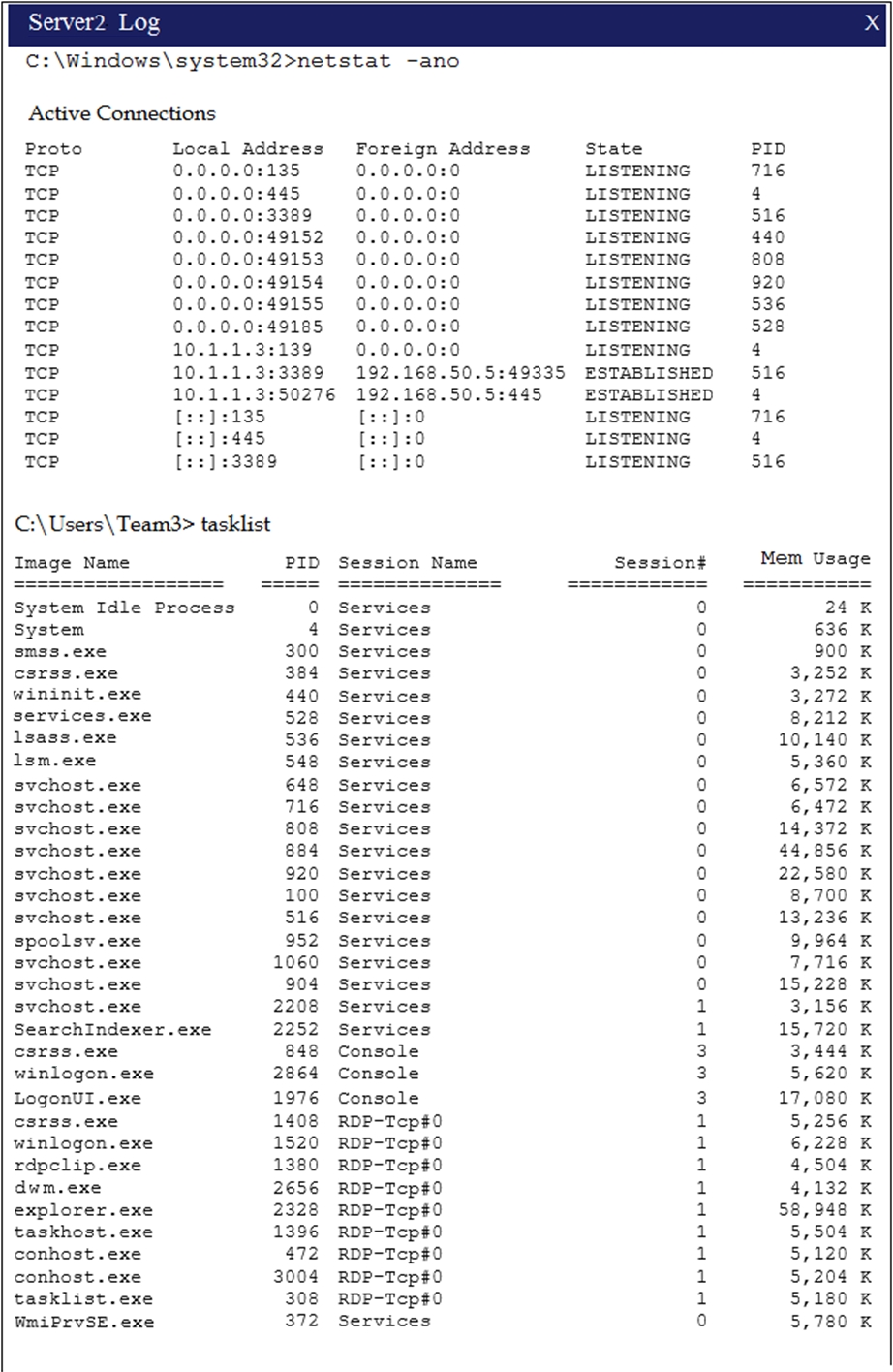
Hot Area:
Given the following code:Which of the following types of attacks is occurring?
A. MITM
B. Session hijacking
C. XSS
D. Privilege escalation
E. SQL injection
Which of the following principles describes how a security analyst should communicate during an incident?
A. The communication should be limited to trusted parties only.
B. The communication should be limited to security staff only.
C. The communication should come from law enforcement.
D. The communication should be limited to management only.
An analyst wants to use a command line tool to identify open ports and running services on a host along with the application that is associated with those services and port. Which of the following should the analyst use?
A. Wireshark
B. Qualys
C. netstat
D. nmap
E. ping
A company discovers an unauthorized device accessing network resources through one of many network drops in a common area used by visitors. The company decides that it wants to quickly prevent unauthorized devices from accessing the network but policy prevents the company from making changes on every connecting client. Which of the following should the company implement?
A. Port security
B. WPA2
C. Mandatory Access Control
D. Network Intrusion Prevention
A cybersecurity consultant is reviewing the following output from a vulnerability scan against a newly installed MS SQL Server 2012 that is slated to go into production in one week:Based on the above information, which of the following should the system administrator do? (Choose two.)
A. Verify the vulnerability using penetration testing tools or proof-of-concept exploits.
B. Review the references to determine if the vulnerability can be remotely exploited.
C. Mark the result as a false positive so it will show in subsequent scans.
D. Configure a network-based ACL at the perimeter firewall to protect the MS SQL port.
E. Implement the proposed solution by installing Microsoft patch Q316333.
Access Full CS0-001 Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete CS0-001 Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our CS0-001 mock test free today—and take a major step toward exam success!