350-701 Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your 350-701 certification exam? Start your preparation the smart way with our 350-701 Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for 350-701 exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our 350-701 Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
In which two customer environments is the Cisco WSAv connector traffic direction method selected? (Choose two.)A. Customer owns ASA Appliance and Virtual Form Factor is required.
B. Customer does not own Cisco hardware and needs Explicit Proxy.
C. Customer owns ASA Appliance and SSL Tunneling is required.
D. Customer needs to support roaming users.
E. Customer does not own Cisco hardware and needs Transparent Redirection (WCCP).
What are two ways a network administrator transparently identifies users using Active Directory on the Cisco WSA? (Choose two.)A. Create an LDAP authentication realm and disable transparent user identification.
B. Create NTLM or Kerberos authentication realm and enable transparent user identification.
C. Deploy a separate Active Directory agent such as Cisco Context Directory Agent.
D. The eDirectory client must be installed on each client workstation.
E. Deploy a separate eDirectory server; the client IP address is recorded in this server.
Which cryptographic process provides origin confidentiality, integrity, and origin authentication for packets?A. AH
B. IKEv1
C. IKEv2
D. ESP
An engineer recently completed the system setup on a Cisco WSA. Which URL information does the system send to SensorBase Network servers?A. complete URL, without obfuscating the path segments
B. URL information collected from clients that connect to the Cisco WSA using Cisco AnyConnect
C. none because SensorBase Network Participation is disabled by default
D. summarized server-name information and MD5-hashed path information
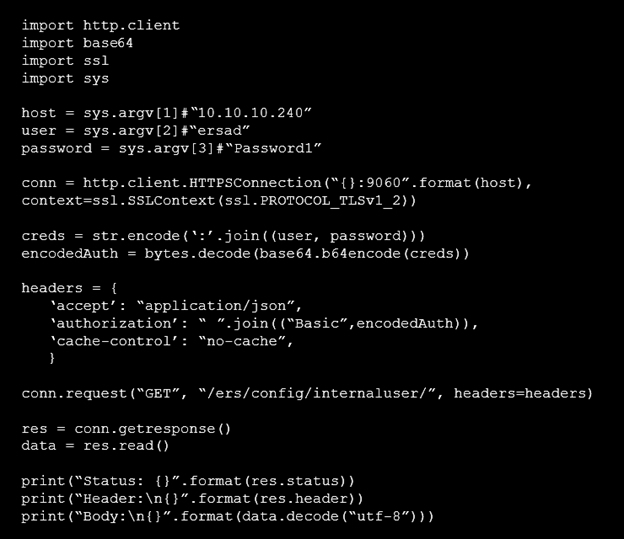
Refer to the exhibit. What does the Python script accomplish?A. It authenticates to a Cisco ISE server using the username or ersad.
B. It lists the LDAP users from the external identity store configured on Cisco ISE.
C. It authenticates to a Cisco ISE with an SSH connection.
D. It allows authentication with TLSv1 SSL protocol.
Refer to the exhibit. Which command results in these messages when attempting to troubleshoot an IPsec VPN connection?A. debug crypto isakmp connection
B. debug crypto ipsec
C. debug crypto ipsec endpoint
D. debug crypto isakmp
Which two conditions are prerequisites for stateful failover for IPsec? (Choose two.)A. Only the IKE configuration that is set up on the active device must be duplicated on the standby device; the IPsec configuration is copied automatically.
B. The active and standby devices can run different versions of the Cisco IOS software but must be the same type of device.
C. The IPsec configuration that is set up on the active device must be duplicated on the standby device.
D. Only the IPsec configuration that is set up on the active device must be duplicated on the standby device; the IKE configuration is copied automatically.
E. The active and standby devices must run the same version of the Cisco IOS software and must be the same type of device.
Which deployment model is the most secure when considering risks to cloud adoption?A. public cloud
B. hybrid cloud
C. community cloud
D. private cloud
What is an advantage of network telemetry over SNMP pulls?A. security
B. scalability
C. accuracy
D. encapsulation
Which threat intelligence standard contains malware hashes?A. advanced persistent threat
B. open command and control
C. structured threat information expression
D. trusted automated exchange of indicator information
Which two protocols must be configured to authenticate end users to the Cisco WSA? (Choose two.)A. TACACS+
B. CHAP
C. NTLMSSP
D. RADIUS
E. Kerberos
What is the definition of phishing?A. malicious email spoofing attack that targets a specific organization or individual
B. impersonation of an authorized website to deceive users into entering their credentials
C. any kind of unwanted, unsolicited digital communication that gets sent out in bulk
D. sending fraudulent communications that appear to come from a reputable source
Which attribute has the ability to change during the RADIUS CoA?A. authorization
B. NTP
C. accessibility
D. membership
What must be used to share data between multiple security products?A. Cisco Platform Exchange Grid
B. Cisco Rapid Threat Containment
C. Cisco Stealthwatch Cloud
D. Cisco Advanced Malware Protection
An MDM provides which two advantages to an organization with regards to device management? (Choose two.)A. asset inventory management
B. allowed application management
C. AD group policy management
D. network device management
E. critical device management
A Cisco FTD engineer is creating a newIKEv2 policy called s2s00123456789 for their organization to allow additional protocols to terminate network devices with.
They currently only have one policy established and need the new policy to be a backup in case some devices cannot support the stronger algorithms listed in the primary policy. What should be done in order to support this?A. Change the encryption to AES* to support all AES algorithms in the primary policy.
B. Make the priority for the primary policy 10 and the new policy 1.
C. Change the integrity algorithms to SHA* to support all SHA algorithms in the primary policy.
D. Make the priority for the new policy 5 and the primary policy 1.
Which two descriptions of AES encryption are true? (Choose two.)A. AES is less secure than 3DES.
B. AES is more secure than 3DES.
C. AES can use a 168-bit key for encryption.
D. AES can use a 256-bit key for encryption.
E. AES encrypts and decrypts a key three times in sequence.
Refer to the exhibit. Logins from internal users to a Cisco Adaptive Security Appliance firewall must be performed by using a TACACS server. The firewall is already configured. Which additional configuration must be performed to configure the TACACS+ server group with a key of Cisco4512!?A.
B.
C.
D.
Why is it important to have logical security controls on endpoints even though the users are trained to spot security threats and the network devices already help prevent them?A. because defense-in-depth stops at the network
B. because human error or insider threats will still exist
C. to prevent theft of the endpoints
D. to expose the endpoint to more threats
An administrator configures a new destination list in Cisco Umbrella so that the organization can block specific domains for its devices. What should be done to ensure that all subdomains of domain.com are blocked?A. Configure the domain.com address in the block list.
B. Configure the *.domain.com address in the block list.
C. Configure the *.com address in the block list.
D. Configure the *domain.com address in the block list.
What are two characteristics of the RESTful architecture used within Cisco DNA Center? (Choose two.)A. REST codes can be compiled with any programming language.
B. REST uses HTTP to send a request to a web service.
C. The POST action replaces existing data at the URL path.
D. REST uses methods such as GET, PUT, POST, and DELETE.
E. REST is a Linux platform-based architecture.
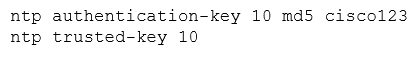
Refer to the exhibit. A network engineer is testing NTP authentication and realizes that any device synchronizes time with this router and that NTP authentication is not enforced. What is the cause of this issue?A. The hashing algorithm that was used was MD5, which is unsupported.
B. The key was configured in plain text.
C. NTP authentication is not enabled.
D. The router was not rebooted after the NTP configuration updated.
What is the difference between EPP and EDR?A. Having an EDR solution gives an engineer the capability to flag offending files at the first sign of malicious behavior.
B. EPP focuses primarily on threats that have evaded front-line defenses that entered the environment.
C. Having an EPP solution allows an engineer to detect, investigate, and remediate modern threats.
D. EDR focuses solely on prevention at the perimeter.
An engineer wants to automatically assign endpoints that have a specific OUI into a new endpoint group. Which probe must be enabled for this type of profiling to work?A. SNMP
B. NMAP
C. DHCP
D. NetFlow
DRAG DROP
-
Drag and drop the descriptions from the left onto the encryption algorithms on the right.

Which Cisco security solution stops exfiltration using HTTPS?A. Cisco CTA
B. Cisco FTD
C. Cisco AnyConnect
D. Cisco ASA
A network administrator received a critical message alert from a Cisco Secure Web Appliance stating that the log partition is at 107% capacity. How does a Cisco Secure Web Appliance respond when its logging partition is full?A. It overwrites the oldest log files.
B. It suspends logging and reporting functions.
C. It deletes logs older than a configurable age.
D. It archives older logs in a compressed file to free space.
Which Cisco solution does Cisco Umbrella integrate with to determine if a URL is malicious?A. Cisco AMP
B. Cisco AnyConnect
C. Cisco Dynamic DNS
D. Cisco Talos
Which attack is preventable by Cisco ESA but not by the Cisco WSA?A. SQL injection
B. phishing
C. buffer overflow
D. DoS
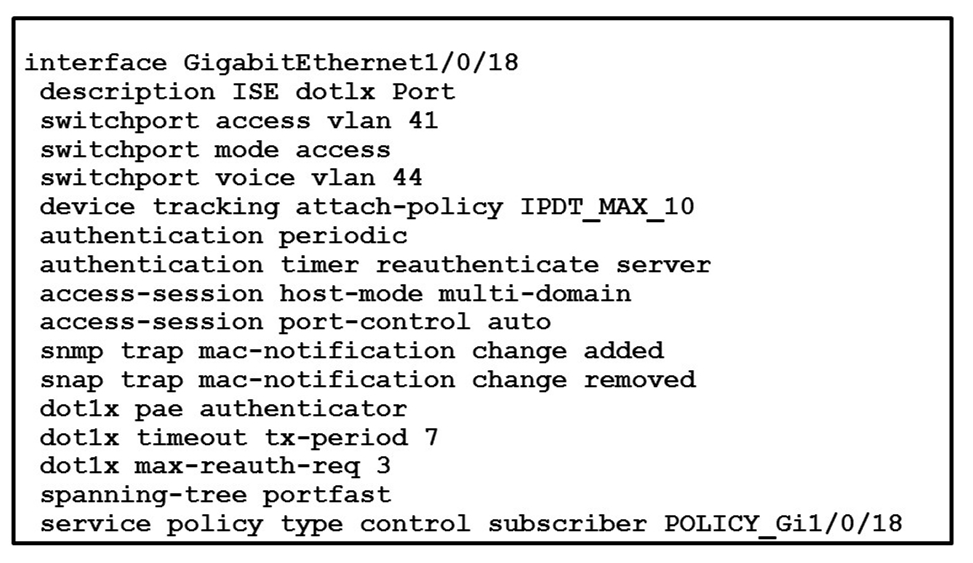
Refer to the exhibit. What will occur when this device tries to connect to the port?A. 802. 1X will not work, but MAB will start and allow the device on the network.
B. 802. 1X will work and the device will be allowed on the network.
C. 802. 1X will not work and the device will not be allowed network access.
D. 802. 1X and MAB will both be used and ISE can use policy to determine the access level.
Which Cisco Umbrella package supports selective proxy for inspection of traffic from risky domains?A. DNS Security Advantage
B. SIG Essentials
C. DNS Security Essentials
D. SIG Advantage
How is DNS tunneling used to exfiltrate data out of a corporate network?A. It leverages the DNS server by permitting recursive lookups to spread the attack to other DNS servers
B. It encodes the payload with random characters that are broken into short strings and the DNS server rebuilds the exfiltrated data
C. It redirects DNS requests to a malicious server used to steal user credentials, which allows further damage and theft on the network
D. It corrupts DNS servers by replacing the actual IP address with a rogue address to collect information or start other attacks
Which system facilitates deploying microsegmentation and multi-tenancy services with a policy-based container?A. SDLC
B. Lambda
C. Contiv
D. Docker
An email administrator is setting up a new Cisco ESA. The administrator wants to enable the blocking of greymail for the end user. Which feature must the administrator enable first?A. Intelligent Multi-Scan
B. Anti-Virus Filtering
C. IP Reputation Filtering
D. File Analysis
What are two trojan malware attacks? (Choose two.)A. frontdoor
B. sync
C. smurf
D. rootkit
E. backdoor
Which Cisco security solution secures public, private, hybrid, and community clouds?A. Cisco ISE
B. Cisco ASAv
C. Cisco Cloudlock
D. Cisco pxGrid
What is a functional difference between a Cisco ASA and Cisco IOS router with Zone-Based Policy Firewall?A. The Cisco ASA can be configured for high availability, whereas the Cisco IOS router with Zone-Based Policy Firewall cannot.
B. The Cisco IOS router with Zone-Based Policy Firewall can be configured for high availability, whereas the Cisco ASA cannot.
C. The Cisco ASA denies all traffic by default, whereas the Cisco IOS router with Zone-Based Policy Firewall starts out by allowing all traffic, even on untrusted interfaces.
D. The Cisco IOS router with Zone-Based Policy Firewall denies all traffic by default, whereas Cisco ASA starts out by allowing traffic until rules are added.
What are the two most commonly used authentication factors in multifactor authentication? (Choose two.)A. biometric factor
B. time factor
C. confidentiality factor
D. knowledge factor
E. encryption factor
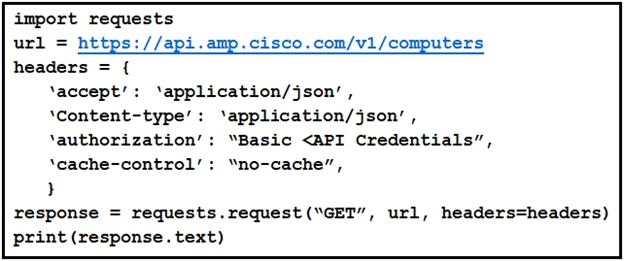
Refer to the exhibit. What will happen when this Python script is run?A. The list of computers, policies, and connector statuses will be received from Cisco AMP.
B. The list of computers and their current vulnerabilities will be received from Cisco AMP.
C. The compromised computers and malware trajectories will be received from Cisco AMP.
D. The compromised computers and what compromised them will be received from Cisco AMP.
What are two list types within Cisco AMP for Endpoints Outbreak Control? (Choose two.)A. blocked ports
B. simple custom detections
C. command and control
D. allowed applications
E. URL
Which two endpoint measures are used to minimize the chances of falling victim to phishing and social engineering attacks? (Choose two.)A. Patch for cross-site scripting.
B. Perform backups to the private cloud.
C. Protect against input validation and character escapes in the endpoint.
D. Install a spam and virus email filter.
E. Protect systems with an up-to-date antimalware program.
Which Cisco ASA Platform mode disables the threat detection features except for Advanced Threat Statistics?A. cluster
B. multiple context
C. routed
D. transparent
Which CoA response code is sent if an authorization state is changed successfully on a Cisco IOS device?A. CoA-NAK
B. CoA-NCL
C. CoA-MAB
D. CoA-ACK
What are two functions of IKEv1 but not IKEv2? (Choose two.)A. IKEv1 conversations are initiated by the IKE_SA_INIT message.
B. With IKEv1, aggressive mode negotiates faster than main mode.
C. IKEv1 uses EAP for authentication.
D. NAT-T is supported in IKEv1 but not in IKEv2.
E. With IKEv1, when using aggressive mode, the initiator and responder identities are passed in cleartext.
How do the features of DMVPN compare to IPsec VPN?A. DMVPN supports high availability routing, and IPsec VPN supports stateless failover.
B. DMVPN uses hub-and-spoke topology, and IPsec VPN uses on-demand spoke topology.
C. DMVPN supports non-IP protocols, and IPsec VPN only supports IP protocols.
D. DMVPN supports multiple vendors, and IPsec VPN only supports Cisco products.
An engineer must deploy a network security management solution to provide the operations team with a unified view of the security environment. The company operates a hybrid cloud with an element of on-premises private hosting for critical applications and data. The operations team requires a single solution that will be used to manage and configure:
• Firewalls
• Intrusion Prevention System
• Application control
• URL filtering
• Advanced malware protection
Which Cisco solution must be deployed?A. Secure Firewall Threat Defense
B. Adaptive Security Device Manager
C. Next-Generation Firewall
D. Secure Firewall Management Center
What are two functionalities of northbound and southbound APIs within Cisco SDN architecture? (Choose two.)A. Northbound APIs utilize RESTful API methods such as GET, POST, and DELETE
B. Southbound APIs utilize CLI, SNMP, and RESTCONF
C. Southbound APIs are used to define how SDN controllers integrate with applications
D. Northbound interfaces utilize OpenFlow and OpFlex to integrate with network devices
E. Southbound interfaces utilize device configurations such as VLANs and IP addresses
What is the difference between deceptive phishing and spear phishing?A. Deceptive phishing is an attacked aimed at a specific user in the organization who holds a C-level role.
B. A spear phishing campaign is aimed at a specific person versus a group of people.
C. Spear phishing is when the attack is aimed at the C-level executives of an organization.
D. Deceptive phishing hijacks and manipulates the DNS server of the victim and redirects the user to a false webpage.
Which Cisco ISE service checks the state of all the endpoints connecting to a network for compliance with corporate security policies?A. Threat Centric NAC service
B. posture service
C. Cisco TrustSec
D. compliance module
A company identified a phishing vulnerability during a pentest. What are two ways the company can protect employees from the attack? (Choose two.)A. using an inline IPS/IDS in the network
B. using Cisco Umbrella
C. using Cisco ESA
D. using Cisco ISE
E. using Cisco FTD
Access Full 350-701 Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete 350-701 Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our 350-701 mock test free today—and take a major step toward exam success!