312-50V11 Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your 312-50V11 certification exam? Start your preparation the smart way with our 312-50V11 Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for 312-50V11 exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our 312-50V11 Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
In the Common Vulnerability Scoring System (CVSS) v3.1 severity ratings, what range does medium vulnerability fall in?
A. 4.0-6.0
B. 3.9-6.9
C. 3.0-6.9
D. 4.0-6.9
Mary found a high vulnerability during a vulnerability scan and notified her server team. After analysis, they sent her proof that a fix to that issue had already been applied. The vulnerability that Marry found is called what?
A. False-negative
B. False-positive
C. Brute force attack
D. Backdoor
Which protocol is used for setting up secure channels between two devices, typically in VPNs?
A. PEM
B. ppp
C. IPSEC
D. SET
John, a professional hacker, performs a network attack on a renowned organization and gains unauthorized access to the target network. He remains in the network without being detected for a long time and obtains sensitive information without sabotaging the organization. Which of the following attack techniques is used by John?
A. Insider threat
B. Diversion theft
C. Spear-phishing sites
D. Advanced persistent threat
Steve, an attacker, created a fake profile on a social media website and sent a request to Stella. Stella was enthralled by Steve's profile picture and the description given for his profile, and she initiated a conversation with him soon after accepting the request. After a few days, Steve started asking about her company details and eventually gathered all the essential information regarding her company. What is the social engineering technique Steve employed in the above scenario?
A. Baiting
B. Piggybacking
C. Diversion theft
D. Honey trap
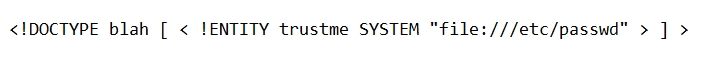
Which of the following web vulnerabilities would an attacker be attempting to exploit if they delivered the following input?
A. SQLi
B. XXE
C. XXS
D. IDOR
Which of the following is the BEST way to defend against network sniffing?
A. Using encryption protocols to secure network communications
B. Register all machines MAC Address in a Centralized Database
C. Use Static IP Address
D. Restrict Physical Access to Server Rooms hosting Critical Servers
What is not a PCI compliance recommendation?
A. Use a firewall between the public network and the payment card data.
B. Use encryption to protect all transmission of card holder data over any public network.
C. Rotate employees handling credit card transactions on a yearly basis to different departments.
D. Limit access to card holder data to as few individuals as possible.
By performing a penetration test, you gained access under a user account. During the test, you established a connection with your own machine via the SMB service and occasionally entered your login and password in plaintext. Which file do you have to clean to clear the password?
A. .xsession-log
B. .profile
C. .bashrc
D. .bash_history
Cross-site request forgery involves:
A. A request sent by a malicious user from a browser to a server
B. A server making a request to another server without the user’s knowledge
C. Modification of a request by a proxy between client and server.
D. A browser making a request to a server without the user’s knowledge
Due to a slowdown of normal network operations, the IT department decided to monitor internet traffic for all of the employees. From a legal standpoint, what would be troublesome to take this kind of measure?
A. All of the employees would stop normal work activities
B. IT department would be telling employees who the boss is
C. Not informing the employees that they are going to be monitored could be an invasion of privacy.
D. The network could still experience traffic slow down.
The collection of potentially actionable, overt, and publicly available information is known as
A. Open-source intelligence
B. Real intelligence
C. Social intelligence
D. Human intelligence
An organization has automated the operation of critical infrastructure from a remote location. For this purpose, all the industrial control systems are connected to the Internet. To empower the manufacturing process, ensure the reliability of industrial networks, and reduce downtime and service disruption, the organization decided to install an OT security tool that further protects against security incidents such as cyber espionage, zero-day attacks, and malware. Which of the following tools must the organization employ to protect its critical infrastructure?
A. Robotium
B. BalenaCloud
C. Flowmon
D. IntentFuzzer
Tony is a penetration tester tasked with performing a penetration test. After gaining initial access to a target system, he finds a list of hashed passwords. Which of the following tools would not be useful for cracking the hashed passwords?
A. Hashcat
B. John the Ripper
C. THC-Hydra
D. netcat
Which type of attack attempts to overflow the content-addressable memory (CAM) table in an Ethernet switch?
A. DDoS attack
B. Evil twin attack
C. DNS cache flooding
D. MAC flooding
What is the Shellshock bash vulnerability attempting to do on a vulnerable Linux host?
A. Removes the passwd file
B. Changes all passwords in passwd
C. Add new user to the passwd file
D. Display passwd content to prompt
PGP, SSL, and IKE are all examples of which type of cryptography?
A. Digest
B. Secret Key
C. Public Key
D. Hash Algorithm
What is the role of test automation in security testing?
A. It is an option but it tends to be very expensive.
B. It should be used exclusively. Manual testing is outdated because of low speed and possible test setup inconsistencies.
C. Test automation is not usable in security due to the complexity of the tests.
D. It can accelerate benchmark tests and repeat them with a consistent test setup. But it cannot replace manual testing completely.
You just set up a security system in your network. In what kind of system would you find the following string of characters used as a rule within its configuration?
A. A firewall IPTable
B. FTP Server rule
C. A Router IPTable
D. An Intrusion Detection System
Your company was hired by a small healthcare provider to perform a technical assessment on the network. What is the best approach for discovering vulnerabilities on a Windows-based computer?
A. Use the built-in Windows Update tool
B. Use a scan tool like Nessus
C. Check MITRE.org for the latest list of CVE findings
D. Create a disk image of a clean Windows installation
The security team of Debry Inc. decided to upgrade Wi-Fi security to thwart attacks such as dictionary attacks and key recovery attacks. For this purpose, the security team started implementing cutting-edge technology that uses a modern key establishment protocol called the simultaneous authentication of equals (SAE), also known as dragonfly key exchange, which replaces the PSK concept. What is the Wi-Fi encryption technology implemented by Debry Inc.?
A. WPA
B. WEP
C. WPA3
D. WPA2
Jim, a professional hacker, targeted an organization that is operating critical industrial infrastructure. Jim used Nmap to scan open ports and running services on systems connected to the organization's OT network. He used an Nmap command to identify Ethernet/IP devices connected to the Internet and further gathered information such as the vendor name, product code and name, device name, and IP address. Which of the following Nmap commands helped Jim retrieve the required information?
A. nmap -Pn -sT –scan-delay 1s –max-parallelism 1 -p
B. nmap -Pn -sU -p 44818 –script enip-info
C. nmap -Pn -sT -p 46824
D. nmap -Pn -sT -p 102 –script s7-info
You are using a public Wi-Fi network inside a coffee shop. Before surfing the web, you use your VPN to prevent intruders from sniffing your traffic. If you did not have a VPN, how would you identify whether someone is performing an ARP spoofing attack on your laptop?
A. You should check your ARP table and see if there is one IP address with two different MAC addresses.
B. You should scan the network using Nmap to check the MAC addresses of all the hosts and look for duplicates.
C. You should use netstat to check for any suspicious connections with another IP address within the LAN.
D. You cannot identify such an attack and must use a VPN to protect your traffic.
Thomas, a cloud security professional, is performing security assessment on cloud services to identify any loopholes. He detects a vulnerability in a bare-metal cloud server that can enable hackers to implant malicious backdoors in its firmware. He also identified that an installed backdoor can persist even if the server is reallocated to new clients or businesses that use it as an IaaS. What is the type of cloud attack that can be performed by exploiting the vulnerability discussed in the above scenario?
A. Cloudborne attack
B. Man-in-the-cloud (MITC) attack
C. Metadata spoofing attack
D. Cloud cryptojacking
In the field of cryptanalysis, what is meant by a `rubber-hose` attack?
A. Forcing the targeted keystream through a hardware-accelerated device such as an ASIC.
B. A backdoor placed into a cryptographic algorithm by its creator.
C. Extraction of cryptographic secrets through coercion or torture.
D. Attempting to decrypt ciphertext by making logical assumptions about the contents of the original plaintext.
Widespread fraud at Enron, WorldCom, and Tyco led to the creation of a law that was designed to improve the accuracy and accountability of corporate disclosures. It covers accounting firms and third parties that provide financial services to some organizations and came into effect in 2002. This law is known by what acronym?
A. SOX
B. FedRAMP
C. HIPAA
D. PCI DSS
Geena, a cloud architect, uses a master component in the Kubernetes cluster architecture that scans newly generated pods and allocates a node to them. This component can also assign nodes based on factors such as the overall resource requirement, data locality, software/hardware/policy restrictions, and internal workload interventions. Which of the following master components is explained in the above scenario?
A. Kube-apiserver
B. Etcd cluster
C. Kube-controller-manager
D. Kube-scheduler
Which tier in the N-tier application architecture is responsible for moving and processing data between the tiers?
A. Presentation tier
B. Application Layer
C. Logic tier
D. Data tier
Which among the following is the best example of the third step (delivery) in the cyber kill chain?
A. An intruder creates malware to be used as a malicious attachment to an email.
B. An intruder’s malware is triggered when a target opens a malicious email attachment.
C. An intruder’s malware is installed on a targets machine.
D. An intruder sends a malicious attachment via email to a target.
What is a `Collision attack` in cryptography?
A. Collision attacks try to get the public key
B. Collision attacks try to break the hash into three parts to get the plaintext value
C. Collision attacks try to break the hash into two parts, with the same bytes in each part to get the private key
D. Collision attacks try to find two inputs producing the same hash
John the Ripper is a technical assessment tool used to test the weakness of which of the following?
A. Passwords
B. File permissions
C. Firewall rulesets
D. Usernames
Firewalk has just completed the second phase (the scanning phase) and a technician receives the output shown below. What conclusions can be drawn based on these scan results? TCP port 21 no response - TCP port 22 no response - TCP port 23 Time-to-live exceeded
A. The lack of response from ports 21 and 22 indicate that those services are not running on the destination server
B. The scan on port 23 was able to make a connection to the destination host prompting the firewall to respond with a TTL error
C. The scan on port 23 passed through the filtering device. This indicates that port 23 was not blocked at the firewall
D. The firewall itself is blocking ports 21 through 23 and a service is listening on port 23 of the target host
Morris, an attacker, warned to check whether the target AP is in a locked state. He attempted using different utilities to identify WPS-enabled APs in the target wireless network. Ultimately, he succeeded with one special command-line utility. Which of the following command-line utilities allowed Morris to discover the WPS-enabled APs?
A. wash
B. net view
C. macof
D. ntptrace
Don, a student, came across a gaming app in a third-party app store and installed it. Subsequently, all the legitimate apps in his smartphone were replaced by deceptive applications that appeared legitimate. He also received many advertisements on his smartphone after installing the app. What is the attack performed on Don in the above scenario?
A. SIM card attack
B. Clickjacking
C. SMS phishing attack
D. Agent Smith attack
An attacker identified that a user and an access point are both compatible with WPA2 and WPA3 encryption. The attacker installed a rogue access point with only WPA2 compatibility in the vicinity and forced the victim to go through the WPA2 four-way handshake to get connected. After the connection was established, the attacker used automated tools to crack WPA2-encrypted messages. What is the attack performed in the above scenario?
A. Cache-based attack
B. Timing-based attack
C. Downgrade security attack
D. Side-channel attack
Jason, an attacker, targeted an organization to perform an attack on its Internet-facing web server with the intention of gaining access to backend servers, which are protected by a firewall. In this process, he used a URL https://xyz.com/feed.php?url=externalsite.com/feed/to to obtain a remote feed and altered the URL input to the local host to view all the local resources on the target server. What is the type of attack Jason performed in the above scenario?
A. Web server misconfiguration
B. Server-side request forgery (SSRF) attack
C. Web cache poisoning attack
D. Website defacement
You are the Network Admin, and you get a complaint that some of the websites are no longer accessible. You try to ping the servers and find them to be reachable. Then you type the IP address and then you try on the browser, and find it to be accessible. But they are not accessible when you try using the URL. What may be the problem?
A. Traffic is Blocked on UDP Port 53
B. Traffic is Blocked on TCP Port 80
C. Traffic is Blocked on TCP Port 54
D. Traffic is Blocked on UDP Port 80
You have compromised a server and successfully gained a root access. You want to pivot and pass traffic undetected over the network and evade any possible Intrusion Detection System. What is the best approach?
A. Use Alternate Data Streams to hide the outgoing packets from this server.
B. Use HTTP so that all traffic can be routed vis a browser, thus evading the internal Intrusion Detection Systems.
C. Install Cryptcat and encrypt outgoing packets from this server.
D. Install and use Telnet to encrypt all outgoing traffic from this server.
What does a firewall check to prevent particular ports and applications from getting packets into an organization?
A. Transport layer port numbers and application layer headers
B. Presentation layer headers and the session layer port numbers
C. Network layer headers and the session layer port numbers
D. Application layer port numbers and the transport layer headers
Which of the following Google advanced search operators helps an attacker in gathering information about websites that are similar to a specified target URL?
A. [inurl:]
B. [info:]
C. [site:]
D. [related:]
To create a botnet, the attacker can use several techniques to scan vulnerable machines. The attacker first collects information about a large number of vulnerable machines to create a list. Subsequently, they infect the machines. The list is divided by assigning half of the list to the newly compromised machines. The scanning process runs simultaneously. This technique ensures the spreading and installation of malicious code in little time. Which technique is discussed here?
A. Subnet scanning technique
B. Permutation scanning technique
C. Hit-list scanning technique.
D. Topological scanning technique
The network in ABC company is using the network address 192.168.1.64 with mask 255.255.255.192. In the network the servers are in the addresses 192.168.1.122, 192.168.1.123 and 192.168.1.124. An attacker is trying to find those servers but he cannot see them in his scanning. The command he is using is: nmap 192.168.1.64/28. Why he cannot see the servers?
A. He needs to add the command ג€ג€ip addressג€ג€ just before the IP address
B. He needs to change the address to 192.168.1.0 with the same mask
C. He is scanning from 192.168.1.64 to 192.168.1.78 because of the mask /28 and the servers are not in that range
D. The network must be dawn and the nmap command and IP address are ok
Josh has finished scanning a network and has discovered multiple vulnerable services. He knows that several of these usually have protections against external sources but are frequently susceptible to internal users. He decides to draft an email, spoof the sender as the internal IT team, and attach a malicious file disguised as a financial spreadsheet. Before Josh sends the email, he decides to investigate other methods of getting the file onto the system. For this particular attempt, what was the last stage of the cyber kill chain that Josh performed?
A. Weaponization
B. Delivery
C. Reconnaissance
D. Exploitation
Attacker Steve targeted an organization's network with the aim of redirecting the company's web traffic to another malicious website. To achieve this goal, Steve performed DNS cache poisoning by exploiting the vulnerabilities in the DNS server software and modified the original IP address of the target website to that of a fake website. What is the technique employed by Steve to gather information for identity theft?
A. Pharming
B. Skimming
C. Pretexting
D. Wardriving
Jane invites her friends Alice and John over for a LAN party. Alice and John access Jane's wireless network without a password. However, Jane has a long, complex password on her router. What attack has likely occurred?
A. Wardriving
B. Wireless sniffing
C. Evil twin
D. Piggybacking
The network users are complaining because their systems are slowing down. Further, every time they attempt to go to a website, they receive a series of pop-ups with advertisements. What type of malware have the systems been infected with?
A. Trojan
B. Spyware
C. Virus
D. Adware
DNS cache snooping is a process of determining if the specified resource address is present in the DNS cache records. It may be useful during the examination of the network to determine what software update resources are used, thus discovering what software is installed. What command is used to determine if the entry is present in DNS cache?
A. nslookup -fullrecursive update.antivirus.com
B. dnsnooping -rt update.antivirus.com
C. nslookup -norecursive update.antivirus.com
D. dns –snoop update.antivirus.com
An organization is performing a vulnerability assessment for mitigating threats. James, a pen tester, scanned the organization by building an inventory of the protocols found on the organization's machines to detect which ports are attached to services such as an email server, a web server, or a database server. After identifying the services, he selected the vulnerabilities on each machine and started executing only the relevant tests. What is the type of vulnerability assessment solution that James employed in the above scenario?
A. Service-based solutions
B. Product-based solutions
C. Tree-based assessment
D. Inference-based assessment
Attacker Rony installed a rogue access point within an organization's perimeter and attempted to intrude into its internal network. Johnson, a security auditor, identified some unusual traffic in the internal network that is aimed at cracking the authentication mechanism. He immediately turned off the targeted network and tested for any weak and outdated security mechanisms that are open to attack. What is the type of vulnerability assessment performed by Johnson in the above scenario?
A. Wireless network assessment
B. Application assessment
C. Host-based assessment
D. Distributed assessment
You are tasked to perform a penetration test. While you are performing information gathering, you find an employee list in Google. You find the receptionist's email, and you send her an email changing the source email to her boss's email (boss@company). In this email, you ask for a pdf with information. She reads your email and sends back a pdf with links. You exchange the pdf links with your malicious links (these links contain malware) and send back the modified pdf, saying that the links don't work. She reads your email, opens the links, and her machine gets infected. You now have access to the company network. What testing method did you use?
A. Social engineering
B. Piggybacking
C. Tailgating
D. Eavesdropping
Access Full 312-50V11 Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete 312-50V11 Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our 312-50V11 mock test free today—and take a major step toward exam success!