300-820 Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your 300-820 certification exam? Start your preparation the smart way with our 300-820 Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for 300-820 exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our 300-820 Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
Which two steps are needed to disable local spam quarantine before external quarantine is enabled? (Choose two.)
A. Uncheck the Enable Spam Quarantine check box.
B. Select Monitor and click Spam Quarantine.
C. Check the External Safelist/Blocklist check box.
D. Select External Spam Quarantine and click on Configure.
E. Select Security Services and click Spam Quarantine.
Refer to the exhibit. What is the correct order of commands to set filter 2 to active?
A. filters-> edit-> 2-> Active
B. filters-> modify-> All-> Active
C. filters-> detail-> 2-> 1
D. filters-> set-> 2-> 1
How are Cisco Webex Video Mesh deployments supported?
A. Video Mesh Dual NIC are supported in demilitarized deployments.
B. Mixed Single NIC and Dual NIC are supported in the same data center deployments.
C. Clustering Video Mesh Nodes over the WAN are supported if Round Trip Time is low.
D. IPv6 and IPv4 deployments are supported for Video Mesh clusters.
DRAG DROP - Drag and drop the required SAN field items from the left onto the features within the server categories on the right.
Which two licenses are required for the B2B feature to work? (Choose two.)
A. Traversal Server
B. TURN Relays
C. Rich Media Sessions
D. Advanced Networking
E. Device Provisioning
An administrator is managing multiple Cisco ESA devices and wants to view the quarantine emails from all devices in a central location. How is this accomplished?
A. Disable the VOF feature before sending SPAM to the external quarantine.
B. Configure a mail policy to determine whether the message is sent to the local or external quarantine.
C. Disable the local quarantine before sending SPAM to the external quarantine.
D. Configure a user policy to determine whether the message is sent to the local or external quarantine.
Which dial plan component is configured in Expressway-C to route a call to the Cisco UCM?
A. call routing
B. traversal subzone
C. call policy
D. search rule
Which setting affects the aggressiveness of spam detection?
A. protection level
B. spam threshold
C. spam timeout
D. maximum depth of recursion scan
Which mechanism does TLS use to validate identity?
A. server certificate
B. shared secret
C. username and a password
D. IP address of the peer
What it is the purpose of using ICE for Mobile and Remote Access endpoints in the Cisco Collaboration infrastructure?
A. ICE controls the bandwidth usage for Cisco Collaboration endpoints if the endpoints are located outside the company network.
B. ICE enables Cisco Collaboration endpoints to determine if there is direct connectivity between them.
C. ICE uses FAST updates to optimize the video quality in case of packet loss. This technology is available only from Cisco Unified CM version 11.5 and later.
D. ICE enablement allows for the Cisco Collaboration endpoint to register through Expressway servers to Cisco Unified Communications Manager behind a firewall.
Refer to the exhibit. An ISDN gateway is registered to Expressway-C with a prefix of 9 and/or it has a neighbor zone specified that routes calls starting with a 9. Which value should be entered into the "Source" field to prevent toll fraud regardless at origin of the call?
A. Traversal Zone
B. Any
C. Neighbor Zone
D. All
The CEO added a sender to a safelist but does not receive an important message expected from the trusted sender. An engineer evaluates message tracking on a Cisco ESA and determines that the message was dropped by the antivirus engine. What is the reason for this behavior?
A. End-user safelists apply to antispam engines only.
B. The sender didn’t mark the message as urgent.
C. Administrative access is required to create a safelist.
D. The sender is included in an ISP blocklist.
Which feature must be configured before an administrator can use the outbreak filter for nonviral threats?
A. quarantine threat level
B. antispam
C. data loss prevention
D. antivirus
Which action on the Cisco ESA provides direct access to view the safelist/blocklist?
A. Show the SLBL cache on the CLI.
B. Monitor Incoming/Outgoing Listener.
C. Export the SLBL to a .csv file.
D. Debug the mail flow policy.
When configuring a Cisco Expressway solution and need to design the dial plan with various rules for URIs and numbers coming through the device. To do so, it is important that some dial plan rules are applied in a certain order. When configuring the transform section, you must know the range of the priorities. Which range is correct?
A. any number in the drop-down menu
B. any number in the dialog box
C. any number between 1-128
D. any number between 1-65534
A company has deployed a new mandate that requires all emails sent externally from the Sales Department to be scanned by DLP for PCI-DSS compliance. A new DLP policy has been created on the Cisco ESA and needs to be assigned to a mail policy named ‘Sales’ that has yet to be created. Which mail policy should be created to accomplish this task?
A. Outgoing Mail Policy
B. Preliminary Mail Policy
C. Incoming Mail Flow Policy
D. Outgoing Mail Flow Policy
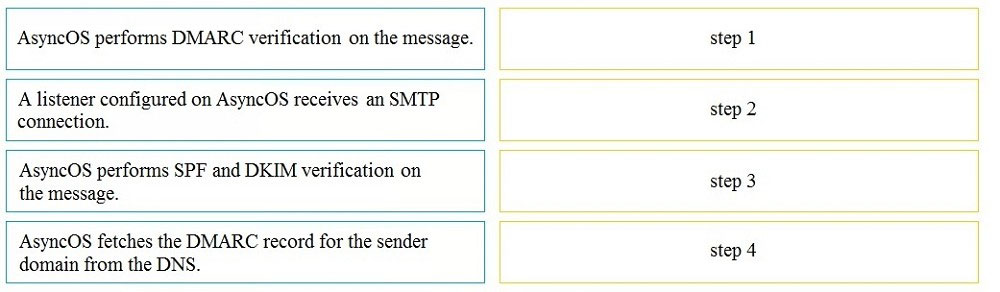
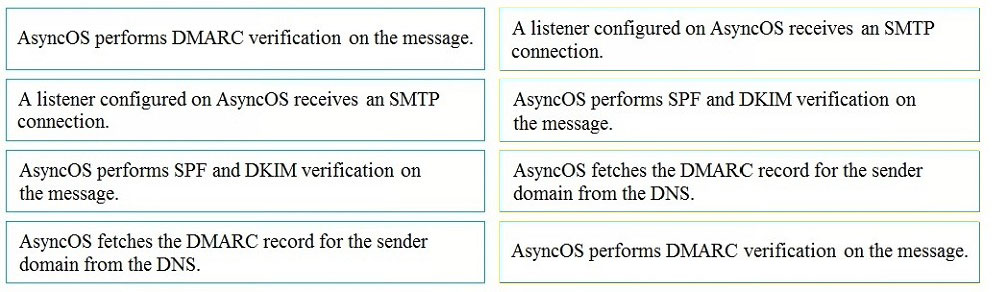
DRAG DROP - Drag and drop the AsyncOS methods for performing DMARC verification from the left into the correct order on the right. Select and Place:
What are two primary components of content filters? (Choose two.)
A. conditions
B. subject
C. content
D. actions
E. policies
An administrator has been tasked to bulk entitle 200 existing users and ensure all future users are automatically configured for the Webex Hybrid Calendar Service. Which two options should be used to configure these users? (Choose two.)
A. Export a CSV list of users in the Cisco Webex Control Hub, set the Hybrid Calendar Service to TRUE for users to be enabled, then import the file back to Manage Users menu in the Cisco Webex Control Hub.
B. Set up an Auto-Assign template that enables Hybrid Calendar.
C. Select the Hybrid Services settings card in the Cisco Webex Control Hub and import a User Status report that contains only users to be enabled.
D. On the Users tab in the Cisco Webex Control Hub, check the box next to each user who should be enabled, then click the toggle for the Hybrid Calendar service to turn it on.
E. From Cisco Webex Control Hub, verify the domain that your Hybrid Calendar users will use, which automatically activates them for the service.
An engineer is deploying an Expressway solution for the SIP domain Cisco.com. Which SRV record should be configured in the public DNS to support inbound B2B calls?
A. _collab-edge._tls.cisco.com
B. _cisco-uds._tcp.cisco.com
C. _sip._tcp.cisco.com
D. _cuplogin._tcp.cisco.com
Which two items are configured when deploying a B2B collaboration solution? (Choose two.)
A. SIP trunk between Cisco Unified Communications Manager and Cisco Expressway-C
B. search rules in Cisco Expressway-E
C. SIP trunk between Cisco Unified Communications Manager and Cisco Expressway-E
D. traversal client on a Cisco Expressway-E
E. DNS zone on a Cisco Expressway-C
What is a benefit of deploying Cisco SMA?
A. centralized management of logs for Cisco ESA appliances
B. centralized management of botnet directories
C. centralized management of software updates for Cisco ESA appliances
D. centralized management of quarantined email
Refer to the exhibit. Which SIP trunk security profile configuration on the Cisco UCM server is used for a secured SIP trunk to an Expressway server that is already integrated with the Cisco UCM for Mobile and Remote Access?
A. Device Security Mode: Encrypted -Incoming Transport Type: TLS -Outgoing Transport Type: TLS -Incoming Port*: 5061
B. Device Security Mode: Encrypted -Incoming Transport Type: TLS -Outgoing Transport Type: TLS -Incoming Port*: 6061
C. Device Security Mode: Non-SecureIncoming Transport Type: TCP+UDPOutgoing Transport Type: TCP -Incoming Port*: 5060
D. Device Security Mode: AuthenticatedIncoming Transport Type: TLS -Outgoing Transport Type: TLS -Incoming Port*: 6061
An administrator notices that incoming emails with certain attachments do not get delivered to all recipients when the emails have multiple recipients in different domains like cisco.com and test.com. The same emails when sent only to recipients in cisco.com are delivered properly. How must the Cisco ESA be configured to avoid this behavior?
A. Modify DLP configuration to ensure that all attachments are permitted for test.com.
B. Modify DLP configuration to exempt DLP scanning for messages sent to test.com domain.
C. Modify mail policies so email recipients do not match multiple policies.
D. Modify mail policies for cisco.com to ensure that emails are not dropped.
DRAG DROP - Drag and drop the services from the left onto their descriptions on the right. Some services are used more than once.
Which two steps configure Forged Email Detection? (Choose two.)
A. Configure a content dictionary with executive email addresses.
B. Configure a filter to use the Forged Email Detection rule and dictionary.
C. Configure a filter to check the Header From value against the Forged Email Detection dictionary.
D. Enable Forged Email Detection on the Security Services page.
E. Configure a content dictionary with friendly names.
A network administrator enabled McAfee antivirus scanning on a Cisco ESA and configured the virus scanning action of “scan for viruses only.” If the scanner finds a virus in an attachment for an incoming email, what action will be applied to this message?
A. The attachment is dropped and replaced with a “Removed Attachment” file.
B. The email and attachment are forwarded to the network administrator.
C. The system will attempt to repair the attachment.
D. No repair is attempted, and the attachment is either dropped or delivered.
Refer to the exhibit. If the Webex Teams device cannot connect to Video Mesh Cluster-1 because it is busy, which media node does the Webex Teams device connect to next?
A. Both Cloud Node US-EAST and US-WEST
B. Video Mesh Cluster-2
C. Cloud Node US-EAST
D. Cloud Node US-WEST
Jabber cannot log in via Mobile and Remote Access. You inspect Expressway-C logs and see this error message: XCP_JABBERD Detail="Unable to connect to host '%IP%', port 7400:(111) Connection refused" Which is the cause of this issue?
A. Rich Media Session licenses are not activated on Expressway-E.
B. Expressway-E is listening on the wrong IP interface.
C. The destination port for Expressway-E is set to 7400 instead of 8443 on the Expressway-C.
D. The XCP Service is not activated on Expressway-E.
A call is sent by Cisco UCM to Expressway with a URI of 75080001@expc1a.pod8.test.lab . If (7508`¦)@expc1a.pod8.test.lab.* is the pattern string, what would be the replacement string of the transform in Expressway to re-write the call so that it becomes 75080001@conf.pod8.test.lab ?
A. 1@conf.pod8.test.lab.@
B. 1@conf.pod8.testlab.*
C. 1@conf.pod8.test.lab
D. 1@conf.pod8.test.lab.!
A Cisco ESA administrator is creating a Mail Flow Policy to receive outbound email from Microsoft Exchange. Which Connection Behavior must be selected to properly process the messages?
A. Delay
B. Accept
C. Relay
D. Reject
An engineer must configure Mobile and Remote Access. One of the requirements is to expect Cisco Jabber users to enter username@cisco.com as the login userid. Which DNS record must the engineer modify to start implementing this requirement?
A. _cuplogin._tcp.cisco.com
B. _collab-edge._tls.cisco.com
C. _cisco-uds._tls.cisco.com
D. _cisco-uds._tcp.cisco.com
Which two query types are available when an LDAP profile is configured? (Choose two.)
A. proxy consolidation
B. user
C. recursive
D. group
E. routing
Which two are configured in the DMARC verification profile? (Choose two.)
A. name of the verification profile
B. minimum number of signatures to verify
C. ESA listeners to use the verification profile
D. message action into an incoming or outgoing content filter
E. message action to take when the policy is reject/quarantine
Refer to the exhibit. In an environment SIP devices are registered to CUCM and H.323 devices to VCS. What would be required to enable these calls to setup correctly?
A. Create a presearch transform.
B. Change the domain of SIP endpoint A to cisco.com.
C. Disable SIP in the external zone.
D. Change the interworking mode to On.
Refer to the exhibit. The firewall has been configured from NAT 192.168.108.2 to 100.64.0.1. Which configuration changes are needed for an Expressway-E with dual network interfaces? A.
B.
C.
D.
Which SMTP extension does Cisco ESA support for email security?
A. ETRN
B. UTF8SMTP
C. PIPELINING
D. STARTTLS
Refer to the exhibit. While troubleshooting Cisco Jabber login issues, there are some error messages. Why is the Jabber client unable to sign in?
A. down Cisco Unified Communications Manager server
B. XMPP bind failures
C. incorrect login credentials
D. service discovery issues
DRAG DROP - An administrator must ensure that emails sent from cisco_123@externally.com are routed through an alternate virtual gateway. Drag and drop the snippet from the bottom onto the blank in the graphic to finish the message filter syntax. Not all snippets are used.
Which mode should be used when Call Policy is configured on Expressways?
A. extended CPL
B. local CPL, policy service, and off
C. on
D. remote CPL
With QoS enabled, which two statements about the Cisco Webex Video Mesh Node signaling and media traffic are true? (Choose two.)
A. From VMN to CUCM SIP endpoints, the source UDP ports from 52500 to 62999 is used for audio traffic.
B. From VMN to Webex Teams clients, the source UDP port 5004 is used for video traffic.
C. From Webex cloud to VMN, the source UDP port 9000 is used for audio traffic.
D. From VMN to video endpoints, the destination UDP port 5004 is used for audio traffic.
E. From VMN to Webex cloud, the destination UDP port 9000 is used for video traffic.
What are two prerequisites for implementing undesirable URL protection in Cisco ESA? (Choose two.)
A. Enable outbreak filters.
B. Enable email relay.
C. Enable antispam scanning.
D. Enable port bouncing.
E. Enable antivirus scanning.
A network engineer is editing the default DMARC verification profile on a Cisco ESA and must ensure that the configured Message Action in the profile matches the policy in the DMARC record. What must be set to achieve this result?
A. “Message Action when the Policy in DMARC Record is Reject” to Reject
B. “Message Action when the Policy in DMARC Record is None” to Quarantine
C. “Message Action when the Policy in DMARC Record is None” to No Action
D. “Message Action when the Policy in DMARC Record is Reject” to Quarantine
Which two statements about Mobile and Remote Access certificate are true? (Choose two.)
A. Expressway Core can use private CA signed certificate.
B. You must upload the root certificates in the phone trust store.
C. Expressway must generate certificate signing request.
D. Expressway Edge must use public CA signed certificate.
E. The Jabber client can work with public or private CA signed certificate.
When external video endpoints are called via a DNS zone, which dialing method requires DNS to be configured in the Expressway server?
A. IP dialing
B. URI dialing
C. DN dialing
D. E.164
Which interworking option must be used on the Expressway for it to act as a SIP/H.323 gateway when no endpoint is registered?
A. enabled
B. registered only
C. off
D. on
A company is installing Cisco Collaboration infrastructure and one of the requirements is that they must be able to communicate with many external parties that are using H.323 and SIP. Internally they want to register the endpoints only on SIP. Which functionality would describe the feature that needs to be enabled and where to achieve this?
A. Interworking in Expressway-C
B. Transcoding in Cisco Unified Communications Manager
C. Transcoding in Expressway-C
D. Interworking in Cisco Unified Communications Manager
An administrator is configuring DNS to allow Mobile and Remote Access logins for the domain cisco.com. Where must the _collab-edge_tls.cisco.com DNS SRV record be configured?
A. in the public DNS server
B. in DNS SRV settings under Cisco Unified OS Administration in Cisco UCM
C. in DNS settings in the Expressway-E on the interface that faces the Internet
D. in DNS settings under Cisco Unified OS Administration in Cisco UCM
Which process is skipped when an email is received from safedomain.com, which is on the safelist?
A. message filter
B. antivirus scanning
C. outbreak filter
D. antispam scanning
What should be considered when using the Cisco Webex hybrid service?
A. Directory Connector must be deployed for OBTP to work with on-premises video devices
B. Directory Connector is required for Azure AD
C. Hybrid Message service works only with Jabber cloud deployment
D. Expressway Connector is required for an on-premises Exchange server
Access Full 300-820 Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete 300-820 Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our 300-820 mock test free today—and take a major step toward exam success!