SY0-501 Dump Free – 50 Practice Questions to Sharpen Your Exam Readiness.
Looking for a reliable way to prepare for your SY0-501 certification? Our SY0-501 Dump Free includes 50 exam-style practice questions designed to reflect real test scenarios—helping you study smarter and pass with confidence.
Using an SY0-501 dump free set of questions can give you an edge in your exam prep by helping you:
- Understand the format and types of questions you’ll face
- Pinpoint weak areas and focus your study efforts
- Boost your confidence with realistic question practice
Below, you will find 50 free questions from our SY0-501 Dump Free collection. These cover key topics and are structured to simulate the difficulty level of the real exam, making them a valuable tool for review or final prep.
Which of the following controls is implemented in lieu of the primary security controls?
A. Compensating
B. Corrective
C. Detective
D. Deterrent
Which of the following describes the maximum amount of time a mission essential function can operate without the systems it depends on before significantly impacting the organization?
A. MTBF
B. MTTR
C. RTO
D. RPO
An organization handling highly confidential information needs to update its systems. Which of the following is the BEST method to prevent data compromise?
A. Wiping
B. Degaussing
C. Shredding
D. Purging
A user suspects someone has been accessing a home network without permission by spoofing the MAC address of an authorized system. While attempting to determine if an authorized user is logged into the home network, the user reviews the wireless router, which shows the following table for systems that are currently on the home network.Which of the following should be the NEXT step to determine if there is an unauthorized user on the network?
A. Apply MAC filtering and see if the router drops any of the systems.
B. Physically check each of the authorized systems to determine if they are logged onto the network.
C. Deny the ג€unknownג€ host because the hostname is not known and MAC filtering is not applied to this host.
D. Conduct a ping sweep of each of the authorized systems and see if an echo response is received.
A technician wants to implement PKI-based authentication on an enterprise wireless network. Which of the following should the technician configure to enforce the use of client-side certificates?
A. 802.1X with PEAP
B. WPA2-PSK
C. EAP-TLS
D. RADIUS Federation
Which of the following is the proper use of a Faraday cage?
A. To block electronic signals sent to erase a cell phone
B. To capture packets sent to a honeypot during an attack
C. To protect hard disks from access during a forensics investigation
D. To restrict access to a building allowing only one person to enter at a time
Adhering to a layered security approach, a controlled access facility employs security guards who verify the authorization of all personnel entering the facility. Which of the following terms BEST describes the security control being employed?
A. Administrative
B. Corrective
C. Deterrent
D. Compensating
A security administrator is reviewing the following network capture:Which of the following malware is MOST likely to generate the above information?
A. Keylogger
B. Ransomware
C. Logic bomb
D. Adware
A security technician is configuring an access management system to track and record user actions. Which of the following functions should the technician configure?
A. Accounting
B. Authorization
C. Authentication
D. Identification
Phishing emails frequently take advantage of high-profile catastrophes reported in the news. Which of the following principles BEST describes the weakness being exploited?
A. Intimidation
B. Scarcity
C. Authority
D. Social proof
During a recent audit, it was discovered that many services and desktops were missing security patches. Which of the following BEST describes the assessment that was performed to discover this issue?
A. Network mapping
B. Vulnerability scan
C. Port Scan
D. Protocol analysis
A company is performing an analysis of the corporate enterprise network with the intent of identifying any one system, person, function, or service that, when neutralized, will cause or cascade disproportionate damage to the company's revenue, referrals, and reputation. Which of the following an element of the BIA that this action is addressing?
A. Identification of critical systems
B. Single point of failure
C. Value assessment
D. Risk register
A company has purchased a new SaaS application and is in the process of configuring it to meet the company's needs. The director of security has requested that the SaaS application be integrated into the company's IAM processes. Which of the following configurations should the security administrator set up in order to complete this request?
A. LDAP
B. RADIUS
C. SAML
D. NTLM
A systems administrator needs to integrate multiple IoT and small embedded devices into the company's wireless network securely. Which of the following should the administrator implement to ensure low-power and legacy devices can connect to the wireless network?
A. WPS
B. WPA
C. EAP-FAST
D. 802.1X
A security technician has been receiving alerts from several servers that indicate load balancers have had a significant increase in traffic. The technician initiates a system scan. The scan results illustrate that the disk space on several servers has reached capacity. The scan also indicates that incoming internet traffic to the servers has increased. Which of the following is the MOST likely cause of the decreased disk space?
A. Misconfigured devices
B. Logs and events anomalies
C. Authentication issues
D. Unauthorized software
A vice president at a manufacturing organization is concerned about desktops being connected to the network. Employees need to log onto the desktops' local account to verify that a product is being created within specifications; otherwise, the desktops should be as isolated as possible. Which of the following is the BEST way to accomplish this?
A. Put the desktops in the DMZ.
B. Create a separate VLAN for the desktops.
C. Air gap the desktops.
D. Join the desktops to an ad-hoc network.
An employee receives an email, which appears to be from the Chief Executive Officer (CEO), asking for a report of security credentials for all users. Which of the following types of attack is MOST likely occurring?
A. Policy violation
B. Social engineering
C. Whaling
D. Spear phishing
During a security audit of a company's network, unsecure protocols were found to be in use. A network administrator wants to ensure browser-based access to company switches is using the most secure protocol. Which of the following protocols should be implemented?
A. SSH2
B. TLS1.2
C. SSL1.3
D. SNMPv3
Which of the following vulnerability types would the type of hacker known as a script kiddie be MOST dangerous against?
A. Passwords written on the bottom of a keyboard
B. Unpatched exploitable Internet-facing services
C. Unencrypted backup tapes
D. Misplaced hardware token
A penetration tester is checking to see if an internal system is vulnerable to an attack using a remote listener. Which of the following commands should the penetration tester use to verify if this vulnerability exists? (Choose two.)
A. tcpdump
B. nc
C. nmap
D. nslookup
E. tail
F. tracert
Which of the following threat actors is motivated primarily by a desire for personal recognition and a sense of accomplishment?
A. A script kiddie
B. A hacktivist
C. An insider threat
D. An industrial saboteur
Which of the following cryptographic algorithms is irreversible?
A. RC4
B. SHA-256
C. DES
D. AES
A web developer improves client access to the company's REST API. Authentication needs to be tokenized but not expose the client's password. Which of the following methods would BEST meet the developer's requirements?
A. SAML
B. LDAP
C. OAuth
D. Shibboleth
A small organization has implemented a rogue system detection solution. Which of the following BEST explains the organization's intent?
A. To identify weak ciphers being used on the network
B. To identify assets on the network that are subject to resource exhaustion
C. To identify end-of-life systems still in use on the network
D. To identify assets that are not authorized for use on the network
A software development company needs to share information between two remote servers, using encryption to protect it. A programmer suggests developing a new encryption protocol, arguing that using an unknown protocol with secure, existing cryptographic algorithm libraries will provide strong encryption without being susceptible to attacks on other known protocols. Which of the following summarizes the BEST response to the programmer's proposal?
A. The newly developed protocol will only be as secure as the underlying cryptographic algorithms used.
B. New protocols often introduce unexpected vulnerabilities, even when developed with otherwise secure and tested algorithm libraries.
C. A programmer should have specialized training in protocol development before attempting to design a new encryption protocol.
D. The obscurity value of unproven protocols against attacks often outweighs the potential for introducing new vulnerabilities.
Which of the following would provide a safe environment for an application to access only the resources needed to function while not having access to run at the system level?
A. Sandbox
B. Honeypot
C. GPO
D. DMZ
A network administrator wants to implement a method of securing internal routing. Which of the following should the administrator implement?
A. DMZ
B. NAT
C. VPN
D. PAT
An organization just experienced a major cyberattack incident. The attack was well coordinated, sophisticated, and highly skilled. Which of the following targeted the organization?
A. Shadow IT
B. An insider threat
C. A hacktivist
D. An advanced persistent threat
A user loses a COPE device. Which of the following should the user do NEXT to protect the data on the device?
A. Call the company help desk to remotely wipe the device.
B. Report the loss to authorities.
C. Check with corporate physical security for the device.
D. Identify files that are potentially missing on the device.
A penetration tester was able to connect to a company's internal network and perform scans and staged attacks for the duration of the testing period without being noticed. The SIEM did not alert the security team to the presence of the penetration tester's devices on the network. Which of the following would provide the security team with notification in a timely manner?
A. Implement rogue system detection and sensors
B. Create a trigger on the IPS and alert the security team when unsuccessful logins occur
C. Decrease the correlation threshold for alerts on the SIEM
D. Run a credentialed vulnerability scan
Which of the following is the MAIN disadvantage of using SSO?
A. The architecture can introduce a single point of failure.
B. Users need to authenticate for each resource they access.
C. It requires an organization to configure federation.
D. The authentication is transparent to the user.
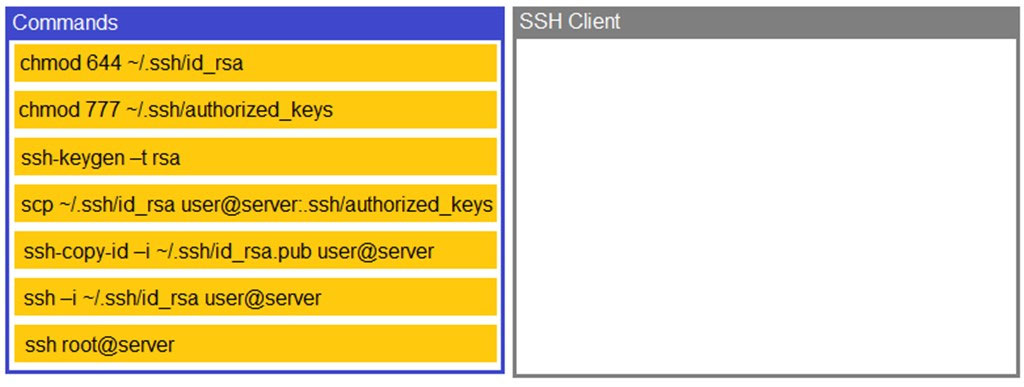
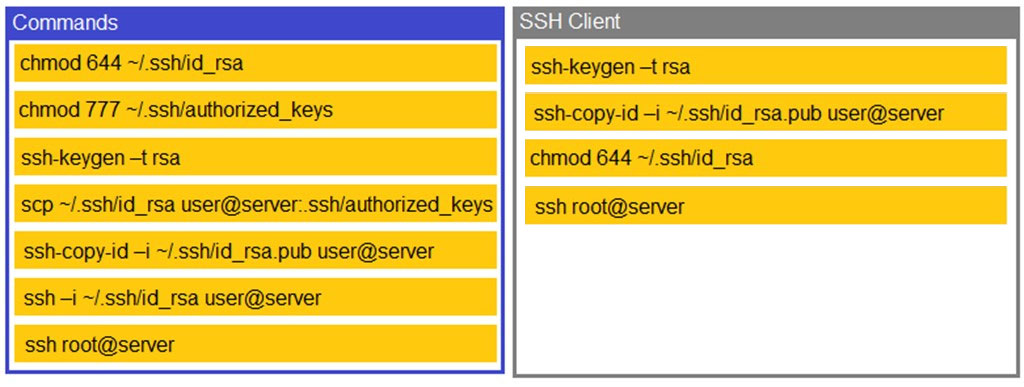
DRAG DROP - A security engineer is setting up passwordless authentication for the first time. INSTRUCTIONS - Use the minimum set of commands to set this up and verify that it works. Commands cannot be reused. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button. Select and Place:
An organization wants to implement a solution that allows for automated logical controls for network defense. An engineer plans to select an appropriate network security component, which automates response actions based on security threats to the network. Which of the following would be MOST appropriate based on the engineer's requirements?
A. NIPS
B. HIDS
C. Web proxy
D. Elastic load balancer
E. NAC
The availability of a system has been labeled as the highest priority. Which of the following should be focused on the MOST to ensure the objective?
A. Authentication
B. HVAC
C. Full-disk encryption
D. File integrity checking
Which of the following types of security testing is the MOST cost-effective approach used to analyze existing code and identity areas that require patching?
A. Black box
B. Gray box
C. White box
D. Red team
E. Blue team
Which of the following represents a multifactor authentication system?
A. An iris scanner coupled with a palm print reader and fingerprint scanner with liveness detection.
B. A secret passcode that prompts the user to enter a secret key if entered correctly.
C. A digital certificate on a physical token that is unlocked with a secret passcode.
D. A one-time password token combined with a proximity badge.
A security administrator suspects that a DDoS attack is affecting the DNS server. The administrator accesses a workstation with the hostname of workstation01 on the network and obtains the following output from the ipconfig command:The administrator successfully pings the DNS server from the workstation. Which of the following commands should be issued from the workstation to verify the DDoS attack is no longer occuring?
A. dig www.google.com
B. dig 192.168.1.254
C. dig workstation01.com
D. dig 192.168.1.26
Which of the following could occur when both strong and weak ciphers are configured on a VPN concentrator? (Choose two.)
A. An attacker could potentially perform a downgrade attack.
B. The connection is vulnerable to resource exhaustion.
C. The integrity of the data could be at risk.
D. The VPN concentrator could revert to L2TP.
E. The IPSec payload is reverted to 16-bit sequence numbers.
A company exchanges information with a business partner. An annual audit of the business partner is conducted against the SLA in order to verify:
A. Performance and service delivery metrics
B. Backups are being performed and tested
C. Data ownership is being maintained and audited
D. Risk awareness is being adhered to and enforced
Which of the following penetration testing concepts is being used when an attacker uses public Internet databases to enumerate and learn more about a target?
A. Reconnaissance
B. Initial exploitation
C. Pivoting
D. Vulnerability scanning
E. White box testing
A company has just completed a vulnerability scan of its servers. A legacy application that monitors the HVAC system in the datacenter presents several challenges, as the application vendor is no longer in business. Which of the following secure network architecture concepts would BEST protect the other company servers if the legacy server were to be exploited?
A. Virtualization
B. Air gap
C. VLAN
D. Extranet
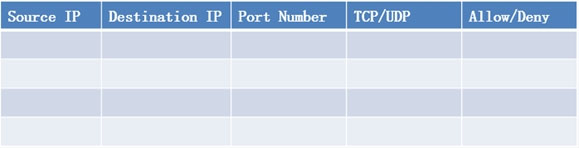
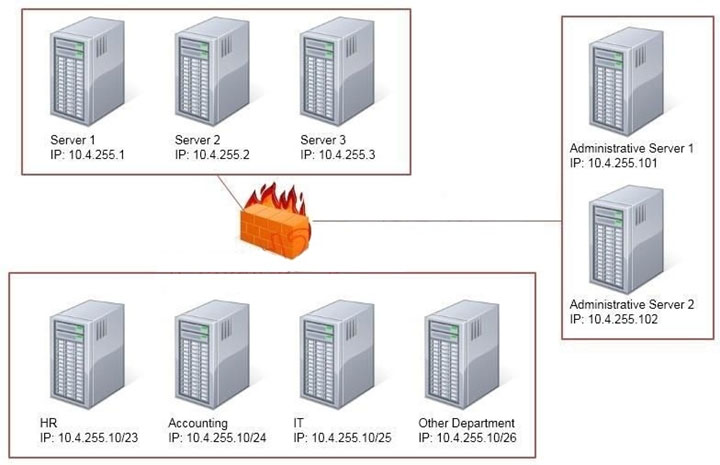
SIMULATION - Task: Configure the firewall (fill out the table) to allow these four rules: ✑ Only allow the Accounting computer to have HTTPS access to the Administrative server. ✑ Only allow the HR computer to be able to communicate with the Server 2 System over SCP. Allow the IT computer to have access to both the Administrative Server 1 and Administrative Server 2
A company is evaluating cloud providers to reduce the cost of its internal IT operations. The company's aging systems are unable to keep up with customer demand. Which of the following cloud models will the company MOST likely select?
A. PaaS
B. SaaS
C. IaaS
D. BaaS
Which of the following attack types BEST describes a client-side attack that is used to manipulate an HTML iframe with JavaScript code via a web browser?
A. Buffer overflow
B. MITM
C. XSS
D. SQLi
A small retail business has a local store and a newly established and growing online storefront. A recent storm caused a power outage to the business and the local ISP, resulting in several hours of lost sales and delayed order processing. The business owner now needs to ensure two things: ✑ Protection from power outages ✑ Always-available connectivity in case of an outage The owner has decided to implement battery backups for the computer equipment. Which of the following would BEST fulfill the owner's second need?
A. Lease a telecommunications line to provide POTS for dial-up access.
B. Connect the business router to its own dedicated UPS.
C. Purchase services from a cloud provider for high availability.
D. Replace the business’s wired network with a wireless network.
A security administrator needs an external vendor to correct an urgent issue with an organization's physical access control system (PACS). The PACS does not currently have internet access because it is running a legacy operation system. Which of the following methods should the security administrator select the best balances security and efficiency?
A. Temporarily permit outbound internet access for the pacs so desktop sharing can be set up
B. Have the external vendor come onsite and provide access to the PACS directly
C. Set up VPN concentrator for the vendor and restrict access to the PACS using desktop sharing
D. Set up a web conference on the administrator’s pc; then remotely connect to the pacs
A developer has incorporated routines into the source code for controlling the length of the input passed to the program. Which of the following types of vulnerabilities is the developer protecting the code against?
A. DLL injection
B. Memory leak
C. Buffer overflow
D. Pointer dereference
A network administrator is brute forcing accounts through a web interface. Which of the following would provide the BEST defense from an account password being discovered?
A. Password history
B. Account lockout
C. Account expiration
D. Password complexity
A systems administrator found a suspicious file in the root of the file system. The file contains URLs, usernames, passwords, and text from other documents being edited on the system. Which of the following types of malware would generate such a file?
A. Keylogger
B. Rootkit
C. Bot
D. RAT
Which of the following should be used to implement voice encryption?
A. SSLv3
B. VDSL
C. SRTP
D. VoIP
Access Full SY0-501 Dump Free
Looking for even more practice questions? Click here to access the complete SY0-501 Dump Free collection, offering hundreds of questions across all exam objectives.
We regularly update our content to ensure accuracy and relevance—so be sure to check back for new material.
Begin your certification journey today with our SY0-501 dump free questions — and get one step closer to exam success!