SCS-C01 Dump Free – 50 Practice Questions to Sharpen Your Exam Readiness.
Looking for a reliable way to prepare for your SCS-C01 certification? Our SCS-C01 Dump Free includes 50 exam-style practice questions designed to reflect real test scenarios—helping you study smarter and pass with confidence.
Using an SCS-C01 dump free set of questions can give you an edge in your exam prep by helping you:
- Understand the format and types of questions you’ll face
- Pinpoint weak areas and focus your study efforts
- Boost your confidence with realistic question practice
Below, you will find 50 free questions from our SCS-C01 Dump Free collection. These cover key topics and are structured to simulate the difficulty level of the real exam, making them a valuable tool for review or final prep.
A security engineer needs to build a solution to turn AWS CloudTrail back on in multiple AWS Regions in case it is ever turned off. What is the MOST efficient way to implement this solution?
A. Use AWS Config with a managed rule to trigger the AWS-EnableCloudTrail remediation.
B. Create an Amazon EventBridge (Amazon CloudWatch Events) event with a cloudtrail.amazonaws.com event source and a StartLogging event name to trigger an AWS Lambda function to call the StartLogging API.
C. Create an Amazon CloudWatch alarm with a cloudtrail.amazonaws.com event source and a StopLogging event name to trigger an AWS Lambda function to call the StartLogging API.
D. Monitor AWS Trusted Advisor to ensure CloudTrail logging is enabled.
A company’s security engineer needs to restrict access to AWS so that the company can deploy resources only in the eu-west-1 Region. The company uses AWS Organizations and has applied the following SCP at the organization’s root level:The company uses Amazon S3, Amazon Route 53, Amazon CloudFront, and AWS Identity and Access Management (IAM). These services must still work in eu-west-1. Which entry should the security engineer remove from the NotAction element in the Deny policy to achieve this goal?
A. s3:*
B. iam:*
C. cloudfront:*
D. route53:*
A security engineer is configuring a new website that is named example.com. The security engineer wants to secure communications with the website by requiring users to connect to example.com through HTTPS. Which of the following is a valid option for storing SSL/TLS certificates?
A. Custom SSL certificate that is stored in AWS Key Management Service (AWS KMS)
B. Default SSL certificate that is stored in Amazon CloudFront.
C. Custom SSL certificate that is stored in AWS Certificate Manager (ACM)
D. Default SSL certificate that is stored in Amazon S3
A company is implementing new compliance requirements to meet customer needs. According to the new requirements, the company must not use any Amazon RDS DB instances or DB clusters that lack encryption of the underlying storage. The company needs a solution that will generate an email alert when an unencrypted DB instance or DB cluster is created. The solution also must terminate the unencrypted DB instance or DB cluster. Which solution will meet these requirements in the MOST operationally efficient manner?
A. Create an AWS Config managed rule to detect unencrypted RDS storage. Configure an automatic remediation action to publish messages to an Amazon Simple Notification Service (Amazon SNS) topic that includes an AWS Lambda function and an email delivery target as subscribers. Configure the Lambda function to delete the unencrypted resource.
B. Create an AWS Config managed rule to detect unencrypted RDS storage. Configure a manual remediation action to invoke an AWS Lambda function. Configure the Lambda function to publish messages to an Amazon Simple Notification Service (Amazon SNS) topic and to delete the unencrypted resource.
C. Create an Amazon EventBridge rule that evaluates RDS event patterns and is initiated by the creation of DB instances or DB clusters. Configure the rule to publish messages to an Amazon Simple Notification Service (Amazon SNS) topic that includes an AWS Lambda function and an email delivery target as subscribers. Configure the Lambda function to delete the unencrypted resource.
D. Create an Amazon EventBridge rule that evaluates RDS event patterns and is initiated by the creation of DB instances or DB clusters. Configure the rule to invoke an AWS Lambda function. Configure the Lambda function to publish messages to an Amazon Simple Notification Service (Amazon SNS) topic and to delete the unencrypted resource.
An employee accidentally exposed an AWS access key and secret access key during a public presentation. The company Security Engineer immediately disabled the key. How can the Engineer assess the impact of the key exposure and ensure that the credentials were not misused? (Choose two.)
A. Analyze AWS CloudTrail for activity.
B. Analyze Amazon CloudWatch Logs for activity.
C. Download and analyze the IAM Use report from AWS Trusted Advisor.
D. Analyze the resource inventory in AWS Config for IAM user activity.
E. Download and analyze a credential report from IAM.
A company is running a dynamic website by using an Application Load Balancer (ALB). A security engineer notices that bots from different IP addresses are using brute-force attacks to invoke a service endpoint frequently. What is the FASTEST way to mitigate this problem?
A. Create an AWS Lambda function to process ALB logs. Block the bots’ IP addresses in the ALB’s security group.
B. Create an AWS WAF web ACL for the ALAdd a rate-based rule to the web ACL to block the bots.
C. Create an ALB listener rule. Combine source-ip and path-pattern as the conditions to match bots. Specify a fixed-response action to return an HTTP 403 status.
D. Create an AWS WAF web ACL for the ALB. Add a rate-based rule to a rule group to block the bots. Attach the rule to the web ACL.
A large government organization is moving to the cloud and has specific encryption requirements. The first workload to move requires that a customer's data be immediately destroyed when the customer makes that request. Management has asked the security team to provide a solution that will securely store the data, allow only authorized applications to perform encryption and decryption, and allow for immediate destruction of the data. Which solution will meet these requirements?
A. Use AWS Secrets Manager and an AWS SDK to create a unique secret for the customer-specific data.
B. Use AWS Key Management Service (AWS KMS) and the AWS Encryption SDK to generate and store a data encryption key for each customer.
C. Use AWS Key Management Service (AWS KMS) with service-managed keys to generate and store customer-specific data encryption keys.
D. Use AWS Key Management Service (AWS KMS) and create an AWS CloudHSM custom key store. Use CloudHSM to generate and store a new CMK for each customer.
A company has installed a third-party application that is distributed on several Amazon EC2 instances and on-premises servers. Occasionally, the company’s IT team needs to use SSH to connect to each machine to perform software maintenance tasks. Outside these time slots, the machines must be completely isolated from the rest of the network. The company does not want to maintain any SSH keys. Additionally, the company wants to pay only for machine hours when there is an SSH connection. Which solution will meet these requirements?
A. Create a bastion host with port forwarding to connect to the machines.
B. Set up AWS Systems Manager Session Manager to allow temporary connections.
C. Use AWS CloudShell to create serverless connections.
D. Set up an interface VPC endpoint for each machine for private connection.
A company uses AWS CodePipeline for its software builds. Company policy mandates that code must be deployed to the staging environment before it is deployed to the production environment. The company needs to implement monitoring and alerting to detect when a CodePipeline pipeline is used to deploy code to production without the code first being deployed to staging. What should a security engineer do to meet these requirements?
A. Enable Amazon GuardDuty to monitor AWS CloudTrail for CodePipeline. Configure findings through AWS Security Hub, and create a custom action in Security Hub to send to Amazon Simple Notification Service (Amazon SNS).
B. Use the AWS Cloud Development Kit (AWS CDK) to model reference-architecture CodePipeline pipeline that deploys application code through the staging environment and then the production environment.
C. Turn on AWS Config recording. Use a custom AWS Config rule to examine each CodePipeline pipeline for compliance. Configure an Amazon Simple Notification Service (Amazon SNS) notification on any change that is not in compliance with the rule. Add the desired receiver of the notification as a subscriber to the SNS topic.
D. Use Amazon Inspector to conduct an assessment of the CodePipeline pipelines and send a notification upon the discovery of a pipeline that is not in compliance. Add the desired receiver of the notification as a subscriber to the Amazon Simple Notification Service (Amazon SNS) topic.
An application has been written that publishes custom metrics to Amazon CloudWatch. Recently, IAM changes have been made on the account and the metrics are no longer being reported. Which of the following is the LEAST permissive solution that will allow the metrics to be delivered?
A. Add a statement to the IAM policy used by the application to allow logs:putLogEvents and logs:createLogStream
B. Modify the IAM role used by the application by adding the CloudWatchFullAccess managed policy.
C. Add a statement to the IAM policy used by the application to allow cloudwatch:putMetricData.
D. Add a trust relationship to the IAM role used by the application for cloudwatch.amazonaws.com.
A company has implemented AWS WAF and Amazon CloudFront for an application. The application runs on Amazon EC2 instances that are part of an Auto Scaling group. The Auto Scaling group is behind an Application Load Balancer (ALB). The AWS WAF web ACL uses an AWS Managed Rules rule group and is associated with the CloudFront distribution. CloudFront receives the request from AWS WAF and the uses the ALB as the distribution's origin. During a security review, a security engineer discovers that the infrastructure is susceptible to a large, layer 7 DDoS attack. How can the security engineer improve the security at the edge of the solution to defend against this type of attack?
A. Configure the CloudFront distribution to use the Lambda@Edge feature. Create an AWS Lambda function that imposes a rate limit on CloudFront viewer requests. Block the request if the rate limit is exceeded.
B. Configure the AWS WAF web ACL so that the web ACL has more capacity units to process all AWS WAF rules faster.
C. Configure AWS WAF with a rate-based rule that imposes a rate limit that automatically blocks requests when the rate limit is exceeded.
D. Configure the CloudFront distribution to use AWS WAF as its origin instead of the ALB.
A Security Engineer must enforce the use of only Amazon EC2, Amazon S3, Amazon RDS, Amazon DynamoDB, and AWS STS in specific accounts. What is a scalable and efficient approach to meet this requirement?
A. Set up an AWS Organizations hierarchy, and replace the FullAWSAccess policy with the following Service Control Policy for the governed organization units:

B. Create multiple IAM users for the regulated accounts, and attach the following policy statement to restrict services as required:

C. Set up an Organizations hierarchy, replace the global FullAWSAccess with the following Service Control Policy at the top level:

D. Set up all users in the Active Directory for federated access to all accounts in the company. Associate Active Directory groups with IAM groups, and attach the following policy statement to restrict services as required:
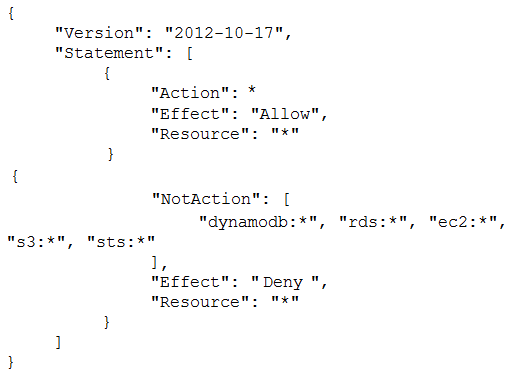
A developer reported that AWS CloudTrail was disabled on their account. A security engineer investigated the account and discovered the event was undetected by the current security solution. The security engineer must recommend a solution that will detect future changes to the CloudTrail configuration and send alerts when changes occur. What should the security engineer do to meet these requirements?
A. Use AWS Resource Access Manager (AWS RAM) to monitor the AWS CloudTrail configuration. Send notifications using Amazon SNS.
B. Create an Amazon CloudWatch Events rule to monitor Amazon GuardDuty findings. Send email notifications using Amazon SNS.
C. Update security contact details in AWS account settings for AWS Support to send alerts when suspicious activity is detected.
D. Use Amazon Inspector to automatically detect security issues. Send alerts using Amazon SNS.
A large company organizes hundreds of AWS accounts in AWS Organizations in Developer, Test, and Production OUs. Developers who have full administrative privileges in their respective accounts use the accounts in the Developer OU. The company wants to allow only certain Amazon EC2 instance types to be used within the Developer OU. How can the company prevent developer accounts from launching unapproved EC2 instance types?
A. Create a now launch template in each AWS account in the Developer OU to deny the ec2:RunInstances API call for instance types that are not in an approved list Associate these templates with all IAM principals in the account.
B. Create an IAM policy to deny the ec2:RunInstances API call for instance types that are not in an approved list. Attach the policy to all IAM principals in all the AWS accounts in the Developer OU.
C. Use a managed SCP that is attached to the organization’s root account to deny the ec2:RunInstances API call for instance types that are not in an approved list
D. Create an SCP to deny the ec2:RunInstances API call for instance types that are not in an approved list. Attach the policy to the Developer OU.
A company has a few dozen application servers in private subnets behind an Elastic Load Balancer (ELB) in an AWS Auto Scaling group. The application is accessed from the web over HTTPS. The data must always be encrypted in transit. The Security Engineer is worried about potential key exposure due to vulnerabilities in the application software. Which approach will meet these requirements while protecting the external certificate during a breach?
A. Use a Network Load Balancer (NLB) to pass through traffic on port 443 from the internet to port 443 on the instances.
B. Purchase an external certificate, and upload it to the AWS Certificate Manager (for use with the ELB) and to the instances. Have the ELB decrypt traffic, and route and re-encrypt with the same certificate.
C. Generate an internal self-signed certificate and apply it to the instances. Use AWS Certificate Manager to generate a new external certificate for the ELB. Have the ELB decrypt traffic, and route and re-encrypt with the internal certificate.
D. Upload a new external certificate to the load balancer. Have the ELB decrypt the traffic and forward it on port 80 to the instances.
A company has two VPCs in the us-east-1 Region: vpc-1 and vpe-2. The company recently created an Amazon API Gateway REST API with the endpoint type set to PRIVATE. The company also created a VPC endpoint for the REST API in vpc-1. Resources in vpc-1 can access the REST API successfully. The company now wants to give resources in vpc-2 the ability to access the REST API. The company creates a VPC endpoint for the REST API in vpc-2, but the resources in vpc-2 cannot access the REST API. A security engineer must make the REST API accessible to resources in vpc-2 by creating a solution that provides the minimum access that is necessary. Which solution will meet these requirements?
A. Set up VPC peering between vpc-1 and vpc-2. Attach an identity-based policy to the resources in vpc-2 to grant access to the REST API.
B. Set up a VPC endpoint of vpc-2 in vpc-1. Attach an identity-based policy to the resources in vpc-2 to grant access to the REST API.
C. Set the API endpoint type to REGIONAL. Attach a resource policy to the REST API to allow access from vpc-2.
D. Keep the API endpoint type as PRIVATE. Attach a resource policy to the REST API to allow access from vpc-2.
An application running on Amazon EC2 instances generates log files in a folder on a Linux file system. The instances block access to the console and file transfer utilities, such as Secure Copy Protocol (SCP) and Secure File Transfer Protocol (SFTP). The Application Support team wants to automatically monitor the application log files so the team can set up notifications in the future. A Security Engineer must design a solution that meets the following requirements: ✑ Make the log files available through an AWS managed service. Allow for automatic monitoring of the logs.✑ Provide an interface for analyzing logs. ✑ Minimize effort. Which approach meets these requirements?
A. Modify the application to use the AWS SDK. Write the application logs to an Amazon S3 bucket.
B. Install the unified Amazon CloudWatch agent on the instances. Configure the agent to collect the application log files on the EC2 file system and send them to Amazon CloudWatch Logs.
C. Install AWS Systems Manager Agent on the instances. Configure an automation document to copy the application log files to AWS DeepLens.
D. Install Amazon Kinesis Agent on the instances. Stream the application log files to Amazon Kinesis Data Firehose and set the destination to Amazon Elasticsearch Service.
An Amazon API Gateway API invokes an AWS Lambda function that needs to interact with a software-as-a-service (SaaS) platform. A unique client token is generated in the SaaS platform to grant access to the Lambda function. A security engineer needs to design a solution to encrypt the access token at rest and pass the token to the Lambda function at runtime. Which solution will meet these requirements MOST cost-effectively?
A. Store the client token as a secret in AWS Secrets Manager. Use the AWS SDK to retrieve the secretin the Lambda function.
B. Configure a token-based Lambda authorizer in API Gateway.
C. Store the client token as a SecureString parameter in AWS Systems Manager Parameter Store. Use the AWS SDK to retrieve the value of the SecureString parameter in the Lambda function.
D. Use AWS Key Management Service (AWS KMS) to encrypt the client token. Pass the token to the Lambda function at runtime through an environment variable.
A company's security officer is concerned about the risk of AWS account root user logins and has assigned a security engineer to implement a notification solution for near-real-time alerts upon account root user logins. How should the security engineer meet these requirements?
A. Create a cron job that runs a script to download the AWS IAM security credentials file, parse the file for account root user logins, and email the security team’s distribution list.
B. Run AWS CloudTrail logs through Amazon CloudWatch Events to detect account root user logins and trigger an AWS Lambda function to send an Amazon SNS notification to the security team’s distribution list.
C. Save AWS CloudTrail logs to an Amazon S3 bucket in the security team’s account. Process the CloudTrail logs with the security engineer’s logging solution for account root user logins. Send an Amazon SNS notification to the security team upon encountering the account root user login events.
D. Save VPC Flow Logs to an Amazon S3 bucket in the security team’s account, and process the VPC Flow Logs with their logging solutions for account root user logins. Send an Amazon SNS notification to the security team upon encountering the account root user login events.
A Security Engineer is asked to update an AWS CloudTrail log file prefix for an existing trail. When attempting to save the change in the CloudTrail console, the Security Engineer receives the following error message: `There is a problem with the bucket policy.` What will enable the Security Engineer to save the change?
A. Create a new trail with the updated log file prefix, and then delete the original trail. Update the existing bucket policy in the Amazon S3 console with the new log file prefix, and then update the log file prefix in the CloudTrail console.
B. Update the existing bucket policy in the Amazon S3 console to allow the Security Engineer’s Principal to perform PutBucketPolicy, and then update the log file prefix in the CloudTrail console.
C. Update the existing bucket policy in the Amazon S3 console with the new log file prefix, and then update the log file prefix in the CloudTrail console.
D. Update the existing bucket policy in the Amazon S3 console to allow the Security Engineer’s Principal to perform GetBucketPolicy, and then update the log file prefix in the CloudTrail console.
An organization wants to be alerted when an unauthorized Amazon EC2 instance in its VPC performs a network port scan against other instances in the VPC. When the Security team performs its own internal tests in a separate account by using pre-approved third-party scanners from the AWS Marketplace, the Security team also then receives multiple Amazon GuardDuty events from Amazon CloudWatch alerting on its test activities. How can the Security team suppress alerts about authorized security tests while still receiving alerts about the unauthorized activity?
A. Use a filter in AWS CloudTrail to exclude the IP addresses of the Security team’s EC2 instances.
B. Add the Elastic IP addresses of the Security team’s EC2 instances to a trusted IP list in Amazon GuardDuty.
C. Install the Amazon Inspector agent on the EC2 instances that the Security team uses.
D. Grant the Security team’s EC2 instances a role with permissions to call Amazon GuardDuty API operations.
A security team is working on a solution that will use Amazon EventBridge (Amazon CloudWatch Events) to monitor new Amazon S3 objects. The solution will monitor for public access and for changes to any S3 bucket policy or setting that result in public access. The security team configures EventBridge to watch for specific API calls that are logged from AWS CloudTrail. EventBridge has an action to send an email notification through Amazon Simple Notification Service (Amazon SNS) to the security team immediately with details of the API call. Specifically, the security team wants EventBridge to watch for the s3:PutObjectAcl, s3:DeleteBucketPolicy, and s3:PutBucketPolicy API invocation logs from CloudTrail. While developing the solution in a single account, the security team discovers that the s3:PutObjectAcl API call does not invoke an EventBridge event. However, the s3:DeleteBucketPolicy API call and the s3:PutBucketPolicy API call do invoke an event. The security team has enabled CloudTrail for AWS management events with a basic configuration in the AWS Region in which EventBridge is being tested. Verification of the EventBridge event pattern indicates that the pattern is set up correctly. The security team must implement a solution so that the s3:PutObjectAcl API call will invoke an EventBridge event. The solution must not generate false notifications. Which solution will meet these requirements?
A. Modify the EventBridge event pattern by selecting Amazon S3. Select All Events as the event type.
B. Modify the EventBridge event pattern by selecting Amazon S3. Select Bucket Level Operations as the event type.
C. Enable CloudTrail Insights to identify unusual API activity.
D. Enable CloudTrail to monitor data events for read and write operations to S3 buckets.
A security engineer has designed a VPC to segment private traffic from public traffic. The VPC includes two Availability Zones. The security engineer has provisioned each Availability Zone with one private subnet and one public subnet. The security engineer has created three route tables for use with the environment. One route table is for the public subnets, and two route tables are for the private subnets (one route table for the private subnet in each Availability Zone). The security engineer discovers that all four subnets are attempting to route traffic out though the internet gateway that is attached to the VPC. Which combination of steps should the security engineer take to remediate this scenario? (Choose two.)
A. Verify that a NAT gateway has been provisioned in the public subnet in each Availability Zone.
B. Verify that a NAT gateway has been provisioned in the private subnet in each Availability Zone.
C. Modify the route tables that are associated with each of the public subnets. Create a new route for local destinations to the VPC CIDR range.
D. Modify the route tables that are associated with each of the private subnets. Create a new route for the destination 0.0.0.0/0. Specify the NAT gateway in the public subnet of the same Availability Zone as the target of the route
E. Modify the route tables that ae associated with each of the private subnets. Create a new route for the destination 0.0.0.0/0. Specify the internet gateway in the public subnet of the same Availability Zone as the target of the route.
A company maintains sensitive data in an Amazon S3 bucket that must be protected using an AWS KMS CMK. The company requires that keys be rotated automatically every year. How should the bucket be configured?
A. Select server-side encryption with Amazon S3-managed keys (SSE-S3) and select an AWS-managed CMK.
B. Select Amazon S3-AWS KMS managed encryption keys (S3-KMS) and select a customer-managed CMK with key rotation enabled.
C. Select server-side encryption with Amazon S3-managed keys (SSE-S3) and select a customer-managed CMK that has imported key material.
D. Select server-side encryption with AWS KMS-managed keys (SSE-KMS) and select an alias to an AWS-managed CMK.
A security engineer is responsible for providing secure access to AWS resources for thousands of developers in a company's corporate identity provider (IdP). The developers access a set of AWS services from their corporate premises using IAM credentials. Due to the volume of requests for provisioning new IAM users, it is taking a long time to grant access permissions. The security engineer receives reports that developers are sharing their IAM credentials with others to avoid provisioning delays. This causes concern about overall security for the security engineer. Which actions will meet the program requirements that address security?
A. Create an Amazon CloudWatch alarm for AWS CloudTrail events. Create a metric filter to send a notification when the same set of IAM credentials is used by multiple developers.
B. Create a federation between AWS and the existing corporate IdP. Leverage IAM roles to provide federated access to AWS resources.
C. Create a VPN tunnel between the corporate premises and the VPC. Allow permissions to all AWS services only if it originates from corporate premises.
D. Create multiple IAM roles for each IAM user. Ensure that users who use the same IAM credentials cannot assume the same IAM role at the same time.
A security audit reveals that several Amazon Elastic Block Store (Amazon EBS) volumes in a company's production account are not encrypted. The unencrypted EBS volumes are attached to Amazon EC2 instances that are provisioned with an Auto Scaling group and a launch template. A security engineer must implement a solution to ensure that all EBS volumes are encrypted now and in the future. Which solution will meet these requirements?
A. Update the launch template by setting the Encrypted flag for all EBS volumes to true, Use the Auto Scaling group’s instance refresh feature to replace existing instances with new instances.
B. Create a new launch template from the old launch template. Set the Encrypted flag for all EBS volumes to true. Update the Auto Scaling group to use the new version of the launch template. Wait for the Auto Scaling group to replace all the old instances that have unencrypted EBS volumes.
C. Use the Amazon EC2 console to enable encryption of new EBS volumes by default for each AWS Region that the company uses. Use the Auto Scaling group’s instance refresh feature to replace existing instances with new instances.
D. Use the Amazon EC2 console to enable encryption of new EBS volumes by default for each AWS Region that the company uses. Update this setting so that Auto Scaling groups will automatically replace existing instances with new instances.
A company uses Amazon Route 53 to create a public DNS zone for the domain example.com in Account A. The company creates another public DNS zone for the subdomain dev.example.com in Account B. A security engineer creates a wildcard certificate (*.dev.example.com) with DNS validation by using AWS Certificate Manager (ACM). The security engineer validates that the corresponding CNAME records have been created in the zone for dev.example.com in Account B. After all these operations are completed, the certificate status is still pending validation. What should the security engineer do to resolve this issue?
A. Purchase a valid wildcard certificate authority (CA) certificate that supports managed renewal. Import this certificate into ACM in Account B.
B. Add NS records for the subdomain dev.example.com to the Route 53 parent zone example.com in Account A.
C. Use AWS Certificate Manager Private Certificate Authority to create a subordinate certificate authority (CA). Use ACM to generate a private certificate that supports managed renewal.
D. Resend the email message that requests ownership validation of dev.example.com.
A company is running batch workloads that use containers on Amazon Elastic Container Service (Amazon ECS). The company needs a secure solution for storing API keys that are required for integration with external services. The company's security policy states that API keys must not be stored or transmitted in plaintext. The company's IT team currently rotates the API keys manually. A security engineer must recommend a solution that meets the security requirements and automates the rotation of the API keys Which solution should the security engineer recommend?
A. Use a secure string parameter in AWS Systems Manager Parameter Store. Activate the feature for automatic rotation.
B. Use Amazon EC2 user data for storing the API keys. Set up a scheduled AWS Lambda function to automatically rotate the API keys.
C. Use AWS Fargate to store the API keys. Set up a scheduled AWS Lambda function to automatically rotate the API keys.
D. Use AWS Secrets Manager to store the API keys. Reference the API keys in the container definition.
A Security Engineer must implement mutually authenticated TLS connections between containers that communicate inside a VPC. Which solution would be MOST secure and easy to maintain?
A. Use AWS Certificate Manager to generate certificates from a public certificate authority and deploy them to all the containers.
B. Create a self-signed certificate in one container and use AWS Secrets Manager to distribute the certificate to the other containers to establish trust.
C. Use AWS Certificate Manager Private Certificate Authority (ACM PCA) to create a subordinate certificate authority, then create the private keys in the containers and sign them using the ACM PCA API.
D. Use AWS Certificate Manager Private Certificate Authority (ACM PCA) to create a subordinate certificate authority, then use AWS Certificate Manager to generate the private certificates and deploy them to all the containers.
A Security Engineer is working with a Product team building a web application on AWS. The application uses Amazon S3 to host the static content, Amazon API Gateway to provide RESTful services; and Amazon DynamoDB as the backend data store. The users already exist in a directory that is exposed through a SAML identity provider. Which combination of the following actions should the Engineer take to enable users to be authenticated into the web application and call APIs? (Choose three.)
A. Create a custom authorization service using AWS Lambda.
B. Configure a SAML identity provider in Amazon Cognito to map attributes to the Amazon Cognito user pool attributes.
C. Configure the SAML identity provider to add the Amazon Cognito user pool as a relying party.
D. Configure an Amazon Cognito identity pool to integrate with social login providers.
E. Update DynamoDB to store the user email addresses and passwords.
F. Update API Gateway to use a COGNITO_USER_POOLS authorizer.
A company is using AWS Organizations with all features enabled. The company has an AWS management account under an organization's root and a small number of AWS accounts under a child OU. The company expects to grow by more than 1,000 AWS accounts in the next year. The company wants to enforce a policy that disallows any configuration changes to AWS Config settings in all AWS Organizations member accounts automatically when the company creates member accounts. The company will enforce this policy on all existing accounts and on any future AWS accounts that the company creates. The company also wants a centralized view of the compliance status of all accounts. Which solution will meet these requirements?
A. Configure AWS Config with trusted access in the Organizations management account.
B. Configure AWS Control Tower to extend governance to the organization. Enroll Organizations member accounts.
C. Use AWS Config to review the enforcement compliance of each AWS account.
D. Create an SCP that denies access to all AWS Config API actions. Apply the SCP to the organization’s root.
A security engineer is setting up a new AWS account. The engineer has been asked to continuously monitor the company's AWS account using automated compliance checks based on AWS best practices and Center for Internet Security (CIS) AWS Foundations Benchmarks. How can the security engineer accomplish this using AWS services?
A. Enable AWS Config and set it to record all resources in all Regions and global resources. Then enable AWS Security Hub and confirm that the CIS AWS Foundations compliance standard is enabled.
B. Enable Amazon Inspector and configure it to scan all Regions for the CIS AWS Foundations Benchmarks. Then enable AWS Security Hub and configure it to ingest the Amazon Inspector findings.
C. Enable Amazon Inspector and configure it to scan all Regions for the CIS AWS Foundations Benchmarks. Then enable AWS Shield in all Regions to protect the account from DDoS attacks.
D. Enable AWS Config and set it to record all resources in all Regions and global resources. Then enable Amazon Inspector and configure it to enforce CIS AWS Foundations Benchmarks using AWS Config rules.
A company has a VPC with an IPv6 address range and a public subnet with an IPv6 address block. The VPC currently hosts some public Amazon EC2 instances, but a security engineer needs to migrate a second application into the VPC that also requires IPv6 connectivity. This new application will occasionally make API requests to an external, internet-accessible endpoint to receive updates. However, the security team does not want the application's EC2 instance exposed directly to the internet. The security engineer intends to create a private subnet with a custom route table and to associate the route table with the private subnet. What else does the security engineer need to do to ensure the application will not be exposed directly to the internet, but can still communicate as required?
A. Launch a NAT instance in the public subnet. Update the custom route table with a new route to the NAT instance.
B. Remove the internet gateway, and add AWS PrivateLink to the VPC. Then update the custom route table with a new route to AWS PrivateLink.
C. Add a managed NAT gateway to the VPC. Update the custom route table with a new route to the gateway.
D. Add an egress-only internet gateway to the VPC. Update the custom route table with a new route to the gateway.
A company requires deep packet inspection on encrypted traffic to its web servers in its VPC. Which solution will meet this requirement?
A. Decrypt traffic by using an Application Load Balancer (ALB) that is configured for TLS termination. Configure the ALB to send the traffic to an AWS Network Firewall endpoint for the deep packet inspection.
B. Decrypt traffic by using a Network Load Balancer (NLB) that is configured for TLS termination. Configure the NLB to send the traffic to an AWS Network Firewall endpoint for the deep packet inspection.
C. Decrypt traffic by using an Application Load Balancer (ALB) that is configured for TLS termination. Configure the ALB to send the traffic to an AWS WAF endpoint for the deep packet inspection.
D. Decrypt traffic by using a Network Load Balancer (NLB) that is configured for TLS termination. Configure the NLB to send the traffic to an AWS WAF endpoint for the deep packet inspection.
A security engineer configures Amazon S3 Cross-Region Replication (CRR) for all objects that are in an S3 bucket in the us-east-1 Region. Some objects in this S3 bucket use server-side encryption with AWS KMS keys (SSE-KMS) for encryption at rest. The security engineer creates a destination S3 bucket in the us-west-2 Region. The destination S3 bucket is in the same AWS account as the source S3 bucket. The security engineer also creates a customer managed key in us-west-2 to encrypt objects at rest in the destination S3 bucket. The replication configuration is set to use the key in us-west-2 to encrypt objects in the destination S3 bucket. The security engineer has provided the S3 replication configuration with an IAM role to perform the replication in Amazon S3. After a day, the security engineer notices that no encrypted objects from the source S3 bucket are replicated to the destination S3 bucket. However, all the unencrypted objects are replicated. Which combination of steps should the security engineer take to remediate this issue? (Choose three.)
A. Change the replication configuration to use the key in us-east-1 to encrypt the objects that are in the destination S3 bucket.
B. Grant the IAM role the kms:Encrypt permission for the key in us-east-1 that encrypts source objects.
C. Grant the IAM role the s3:GetObjectVersionForReplication permission for objects that are in the source S3 bucket.
D. Grant the IAM role the kms:Decrypt permission for the key in us-east-1 that encrypts source objects.
E. Change the key policy of the key in us-east-1 to grant the kms:Decrypt permission to the security engineer’s IAM account.
F. Grant the IAM role the kms:Encrypt permission for the key in us-west-2 that encrypts objects that are in the destination S3 bucket.
A corporate cloud security policy states that communications between the company's VPC and KMS must travel entirely within the AWS network and not use public service endpoints. Which combination of the following actions MOST satisfies this requirement? (Choose two.)
A. Add the aws:sourceVpce condition to the AWS KMS key policy referencing the company’s VPC endpoint ID.
B. Remove the VPC internet gateway from the VPC and add a virtual private gateway to the VPC to prevent direct, public internet connectivity.
C. Create a VPC endpoint for AWS KMS with private DNS enabled.
D. Use the KMS Import Key feature to securely transfer the AWS KMS key over a VPN.
E. Add the following condition to the AWS KMS key policy: “aws:SourceIp”: “10.0.0.0/16”.
The Security Engineer has discovered that a new application that deals with highly sensitive data is storing Amazon S3 objects with the following key pattern, which itself contains highly sensitive data. Pattern: "randomID_datestamp_PII.csv" Example: "1234567_12302017_000-00-0000 csv" The bucket where these objects are being stored is using server-side encryption (SSE). Which solution is the most secure and cost-effective option to protect the sensitive data?
A. Remove the sensitive data from the object name, and store the sensitive data using S3 user-defined metadata.
B. Add an S3 bucket policy that denies the action s3:GetObject
C. Use a random and unique S3 object key, and create an S3 metadata index in Amazon DynamoDB using client-side encrypted attributes.
D. Store all sensitive objects in Binary Large Objects (BLOBS) in an encrypted Amazon RDS instance.
A company has identified two security concerns. One concern is unencrypted Amazon Elastic Block Store (Amazon EBS) volumes. The other concern is public IP addresses that are assigned to Amazon EC2 instances. A security engineer must build a solution to prevent and remediate these security issues. What should the security engineer do to meet these requirements with the LEAST amount of effort?
A. Use AWS CloudTrail to monitor accounts for noncompliant configurations. Use AWS Lambda functions to evaluate configuration state and perform automated remediation actions.
B. Use AWS Config rules to monitor accounts for noncompliant configurations. Use AWS Systems Manager Automation to perform automated remediation actions.
C. Use Amazon GuardDuty to monitor accounts for noncompliant configurations. Use AWS Lambda function to perform automated remediation actions.
D. Use AWS Systems Manager Compliance to monitor accounts for noncompliant configurations. Use Systems Manager Automation to perform automated remediation actions.
An Amazon S3 bucket is encrypted using an AWS KMS CMK. An IAM user is unable to download objects from the S3 bucket using the AWS Management Console; however, other users can download objects from the S3 bucket. Which policies should the Security Engineer review and modify to resolve this issue? (Choose three.)
A. The CMK policy
B. The VPC endpoint policy
C. The S3 bucket policy
D. The S3 ACL
E. The IAM policy
A Developer signed in to a new account within an AWS Organizations organizational unit (OU) containing multiple accounts. Access to the Amazon S3 service is restricted with the following SCP:How can the Security Engineer provide the Developer with Amazon S3 access without affecting other accounts?
A. Move the SCP to the root OU of Organizations to remove the restriction to access Amazon S3.
B. Add an IAM policy for the Developer, which grants S3 access.
C. Create a new OU without applying the SCP restricting S3 access. Move the Developer account to this new OU.
D. Add an allow list for the Developer account for the S3 service.
A company is operating an AWS workload that consists of multiple applications that are deployed on Amazon EC2 instances. Recent changes to a security group caused connectivity issues for some application instances that use the security group. The company now needs all changes to security groups to initiate an alert to a specific company email address. Which solution will meet this requirement in the MOST operationally efficient manner?
A. Implement AWS Config. Configure an AWS Config managed rule to detect changes to security groups. Configure a manual remediation action for noncompliant resources to forward evaluations to an Amazon Simple Notification Service (Amazon SNS) topic.
B. Implement AWS Config. Configure an AWS Config managed rule to detect changes to security groups. Configure a manual remediation action for noncompliant resources to forward evaluations to an Amazon Simple Queue Service (Amazon SQS) queue.
C. Implement AWS CloudTrail. Configure forwarding to Amazon CloudWatch Logs. Configure a CloudWatch Logs metric filter with a pattern match on all security group changes. Configure an Amazon CloudWatch alarm to publish messages to an Amazon Simple Notification Service (Amazon SNS) topic.
D. Implement AWS CloudTrail. Configure forwarding to Amazon S3. Configure an AWS Glue crawler for use with Amazon Athena to query log contents for event patterns that indicate changes to security groups. Publish the query results to an Amazon Simple Queue Service (Amazon SQS) queue.
A company deploys a set of standard IAM roles in AWS accounts. The IAM roles are based on job functions within the company. To balance operational efficiency and security, a security engineer implemented AWS Organizations SCPs to restrict access to critical security services in all company accounts. All of the company's accounts and OUs within AWS Organizations have a default FullAWSAccess SCP that is attached. The security engineer needs to ensure that no one can disable Amazon GuardDuty and AWS Security Hub. The security engineer also must not override other permissions that are granted by IAM policies that are defined in the accounts. Which SCP should the security engineer attach to the root of the organization to meet these requirements?
A.

B.

C.

D.

The Security team believes that a former employee may have gained unauthorized access to AWS resources sometime in the past 3 months by using an identified access key. What approach would enable the Security team to find out what the former employee may have done within AWS?
A. Use the AWS CloudTrail console to search for user activity.
B. Use the Amazon CloudWatch Logs console to filter CloudTrail data by user.
C. Use AWS Config to see what actions were taken by the user.
D. Use Amazon Athena to query CloudTrail logs stored in Amazon S3.
A Security Engineer accidentally deleted the imported key material in an AWS KMS CMK. What should the Security Engineer do to restore the deleted key material?
A. Create a new CMK. Download a new wrapping key and a new import token to import the original key material.
B. Create a new CMK. Use the original wrapping key and import token to import the original key material.
C. Download a new wrapping key and a new import token. Import the original key material into the existing CMK.
D. Use the original wrapping key and import token. Import the original key material into the existing CMK.
A company is developing a mobile shopping web app. The company needs an environment that is configured to encrypt all resources in transit and at rest. A security engineer must develop a solution that will encrypt traffic in transit to the company's Application Load Balancer and Amazon API Gateway resources. The solution also must encrypt traffic at rest for Amazon S3 storage. What should the security engineer do to meet these requirements?
A. Use AWS Certificate Manager (ACM) for encryption in transit. Use AWS Key Management Service for encryption at rest.
B. Use AWS Certificate Manager (ACM) for encryption in transit and encryption at rest.
C. Use AWS Key Management Service for encryption in transit. Use AWS Certificate Manager (ACM) for encryption at rest.
D. Use AWS Key Management Service for encryption in transit and encryption at rest.
A company has two applications: Application A and Application B. The applications run in different VPCs in the same account. The account is not part of an organization in AWS Organizations. The company's development team manages both applications by using AWS CloudFormation. The development team splits into two teams, Now, Team A manages Application A. Team B manages Application B. AWS CloudTrail logs in the account are sent to an Amazon S3 bucket. The company needs to prevent faults in one application from affecting the other application, ensure that teams can access only their own workloads, and send CloudTrail logs to a central S3 bucket. In addition, the company needs granular billing for each application. What is the MOST operationally efficient solution that meets these requirements?
A. Deploy an attribute-based access control (ABAC) tagging strategy to separate the teams. Use cost allocation tags for granular billing.
B. Deploy a role-based access control (RBAC) tagging strategy to separate the teams. Use cost allocation tags for granular billing
C. Deploy AWS Control Tower. Create two accounts: one account for Application A and one account for Application B. Migrate each application to its new account.
D. Migrate Application B to a new account. Use CloudFormation to send CloudTrail logs from the new account to the existing S3 bucket in the original account.
A company has thousands of AWS Lambda functions. While reviewing the Lambda functions, a security engineer discovers that sensitive information is being stored in environment variables and is viewable as plaintext in the Lambda console. The values of the sensitive information are only a few characters long. What is the MOST cost-effective way to address this security issue?
A. Set up IAM policies from the Lambda console to hide access to the environment variables.
B. Use AWS Step Functions to store the environment variables. Access the environment variables at runtime. Use IAM permissions to restrict access to the environment variables to only the Lambda functions that require access.
C. Store the environment variables in AWS Secrets Manager, and access them at runtime. Use IAM permissions to restrict access to the secrets to only the Lambda functions that require access.
D. Store the environment variables in AWS Systems Manager Parameter Store as secure string parameters, and access them at runtime. Use IAM permissions to restrict access to the parameters to only the Lambda functions that require access.
A security team is implementing a centralized logging solution to meet requirements for auditing. The solution must be able to aggregate logs from Amazon CloudWatch and AWS CloudTrail to an account that is controlled by the security team. This approach must be usable across the entire organization in AWS Organizations. Which solution meets these requirements in the MOST operationally efficient manner?
A. In each AWS account, create an Amazon Kinesis Data Firehose delivery stream that has a destination of Amazon S3 in the security team’s account. Create a subscription for each Amazon CloudWatch Logs log group in each AWS account to the Kinesis Data Firehose delivery stream in the same account. For the organization, create a CloudTrail trail that has a destination of Amazon S3.
B. In the security team’s account, create an Amazon Kinesis Data Firehose delivery stream that has a destination of Amazon S3 in the same account. Create a subscription for each Amazon CloudWatch Logs log group in each AWS account to the Kinesis Data Firehose delivery stream in the security team’s account. For each AWS account, create a CloudTrail trail that has a destination of Amazon S3.
C. In each AWS account, create an Amazon Kinesis data stream that has a destination of Amazon S3 in the security team’s account. Create a subscription for each Amazon CloudWatch Logs log group in each AWS account to the Kinesis data stream in the same account. For the organization, create a CloudTrail trail that has a destination of Amazon S3.
D. In the security team’s account, create an Amazon Kinesis data stream that has a destination of Amazon S3 in the same account. Create a subscription for each Amazon CloudWatch Logs log group in each AWS account to the Kinesis data stream in the security team’s account. For each AWS account, create a CloudTrail trail that has a destination of Amazon S3.
An organization operates a web application that serves users globally. The application runs on Amazon EC2 instances behind an Application Load Balancer. There is an Amazon CloudFront distribution in front of the load balancer, and the organization uses AWS WAF. The application is currently experiencing a volumetric attack whereby the attacker is exploiting a bug in a popular mobile game. The application is being flooded with HTTP requests from all over the world with the User-Agent set to the following string: Mozilla/5.0 (compatible; ExampleCorp; ExampleGame/1.22; Mobile/1.0) What mitigation can be applied to block attacks resulting from this bug while continuing to service legitimate requests?
A. Create a rule in AWS WAF rules with conditions that block requests based on the presence of ExampleGame/1.22 in the User-Agent header
B. Create a geographic restriction on the CloudFront distribution to prevent access to the application from most geographic regions
C. Create a rate-based rule in AWS WAF to limit the total number of requests that the web application services.
D. Create an IP-based blacklist in AWS WAF to block the IP addresses that are originating from requests that contain ExampleGame/1.22 in the User-Agent header.
A company's policy requires that all API keys be encrypted and stored separately from source code in a centralized security account. This security account is managed by the company's security team. However, an audit revealed that an API key is stored with the source code of an AWS Lambda function in an AWS CodeCommit repository in the DevOps account. How should the security team securely store the API key?
A. Create a CodeCommit repository in the security account using AWS Key Management Service (AWS KMS) for encryption. Require the development team to migrate the Lambda source code to this repository.
B. Store the API key in an Amazon S3 bucket in the security account using server-side encryption with Amazon S3 managed encryption keys (SSE-S3) to encrypt the key. Create a presigned URL for the S3 key, and specify the URL in a Lambda environmental variable in the AWS CloudFormation template. Update the Lambda function code to retrieve the key using the URL and call the API.
C. Create a secret in AWS Secrets Manager in the security account to store the API key using AWS Key Management Service (AWS KMS) for encryption. Grant access to the IAM role used by the Lambda function so that the function can retrieve the key from Secrets Manager and call the API.
D. Create an encrypted environment variable for the Lambda function to store the API key using AWS Key Management Service (AWS KMS) for encryption. Grant access to the IAM role used by the Lambda function so that the function can decrypt the key at runtime.
Access Full SCS-C01 Dump Free
Looking for even more practice questions? Click here to access the complete SCS-C01 Dump Free collection, offering hundreds of questions across all exam objectives.
We regularly update our content to ensure accuracy and relevance—so be sure to check back for new material.
Begin your certification journey today with our SCS-C01 dump free questions — and get one step closer to exam success!

