SC-300 Dump Free – 50 Practice Questions to Sharpen Your Exam Readiness.
Looking for a reliable way to prepare for your SC-300 certification? Our SC-300 Dump Free includes 50 exam-style practice questions designed to reflect real test scenarios—helping you study smarter and pass with confidence.
Using an SC-300 dump free set of questions can give you an edge in your exam prep by helping you:
- Understand the format and types of questions you’ll face
- Pinpoint weak areas and focus your study efforts
- Boost your confidence with realistic question practice
Below, you will find 50 free questions from our SC-300 Dump Free collection. These cover key topics and are structured to simulate the difficulty level of the real exam, making them a valuable tool for review or final prep.
You have 2,500 users who are assigned Microsoft Office 365 Enterprise E3 licenses. The licenses are assigned to individual users. From the Groups blade in the Microsoft Entra admin center, you assign Microsoft Office 365 Enterprise E5 licenses to a group that includes all users. You need to remove the Office 365 Enterprise E3 licenses from the users by using the least amount of administrative effort. What should you use?
A. the Licenses blade in the Microsoft Entra admin center
B. the Administrative units blade in the Microsoft Entra admin center
C. the Identity Governance blade in the Microsoft Entra admin center
D. the Update-MgUser cmdlet
DRAG DROP - You have an Azure subscription that contains the resources shown in the following table.The subscription uses Privileged Identity Management (PIM). You need to configure the following access controls by using PIM: • Ensure that User1 can read and update Secret1. • Ensure that User2 can read the contents of the secrets stored in Vault2. The solution must follow the principle of least privilege. Which authorization method should you use for each user? To answer, drag the appropriate authorization methods to the correct users. Each authorization method may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
Overview - ADatum Corporation is a consulting company in Montreal. ADatum recently acquired a Vancouver-based company named Litware, Inc. Existing Environment. ADatum Environment The on-premises network of ADatum contains an Active Directory Domain Services (AD DS) forest named adatum.com. ADatum has a Microsoft 365 E5 subscription. The subscription contains a verified domain that syncs with the adatum.com AD DS domain by using Azure AD Connect. ADatum has an Azure Active Directory (Azure AD) tenant named adatum.com. The tenant has Security defaults disabled. The tenant contains the users shown in the following table.The tenant contains the groups shown in the following table.
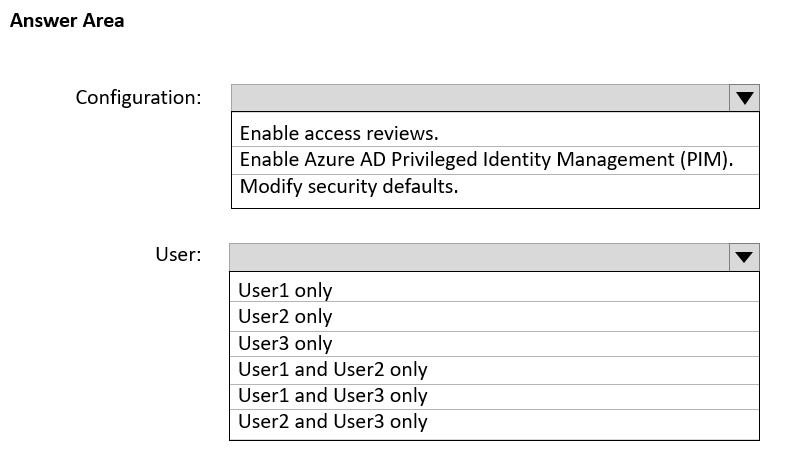
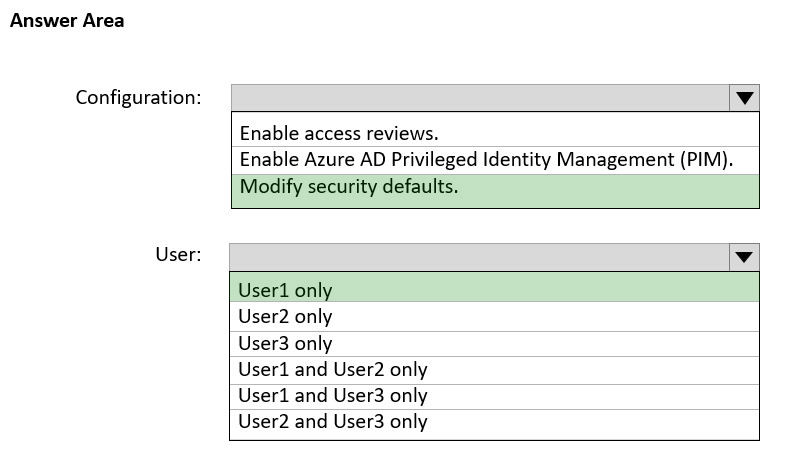
Existing Environment. Litware Environment Litware has an AD DS forest named litware.com Existing Environment. Problem Statements ADatum identifies the following issues: • Multiple users in the sales department have up to five devices. The sales department users report that sometimes they must contact the support department to join their devices to the Azure AD tenant because they have reached their device limit. • A recent security incident reveals that several users leaked their credentials, a suspicious browser was used for a sign-in, and resources were accessed from an anonymous IP address. • When you attempt to assign the Device Administrators role to IT_Group1, the group does NOT appear in the selection list. • Anyone in the organization can invite guest users, including other guests and non-administrators. • The helpdesk spends too much time resetting user passwords. • Users currently use only passwords for authentication. Requirements. Planned Changes - ADatum plans to implement the following changes: • Configure self-service password reset (SSPR). • Configure multi-factor authentication (MFA) for all users. • Configure an access review for an access package named Package1. • Require admin approval for application access to organizational data. • Sync the AD DS users and groups of litware.com with the Azure AD tenant. • Ensure that only users that are assigned specific admin roles can invite guest users. • Increase the maximum number of devices that can be joined or registered to Azure AD to 10. Requirements. Technical Requirements ADatum identifies the following technical requirements: • Users assigned the User administrator role must be able to request permission to use the role when needed for up to one year. • Users must be prompted to register for MFA and provided with an option to bypass the registration for a grace period. • Users must provide one authentication method to reset their password by using SSPR. Available methods must include: - Email - Phone - Security questions - The Microsoft Authenticator app • Trust relationships must NOT be established between the adatum.com and litware.com AD DS domains. • The principle of least privilege must be used. You need to resolve the issue of IT_Group1. What should you do first?
A. Change Membership type of IT_Group1 to Dynamic User.
B. Recreate the IT_Group1 group.
C. Change Membership type of IT Group1 to Dynamic Device.
D. Add an owner to IT_Group1.
HOTSPOT - Your network contains an on-premises Active Directory Domain Services (AD DS) domain that syncs with an Azure AD tenant. You need to ensure that user authentication always occurs by validating passwords against the AD DS domain. What should you configure, and what should you use? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 tenant. All users have mobile phones and Windows 10 laptops. The users frequently work from remote locations that do not have Wi-Fi access or mobile phone connectivity. While working from the remote locations, the users connect their laptops to a wired network that has internet access. You plan to implement multi-factor authentication (MFA). Which MFA authentication method can the users use from the remote location?
A. voice
B. Windows Hello for Business
C. email
D. security questions
You have a Microsoft Entra tenant. You need to query risky user activity for the tenant. How long will the logs of risky user activity be retained?
A. 30 days
B. 60 days
C. 90 days
D. 180 days
HOTSPOT - You have an Azure AD tenant that contains a user named User1. User1 is assigned the User Administrator role. You need to configure External collaboration settings for the tenant to meet the following requirements: • Guest users must be prevented from querying staff email addresses. • Guest users must be able to access the tenant only if they are invited by User1. Which three settings should you configure? To answer, select the appropriate settings in the answer area. NOTE: Each correct selection is worth one point.
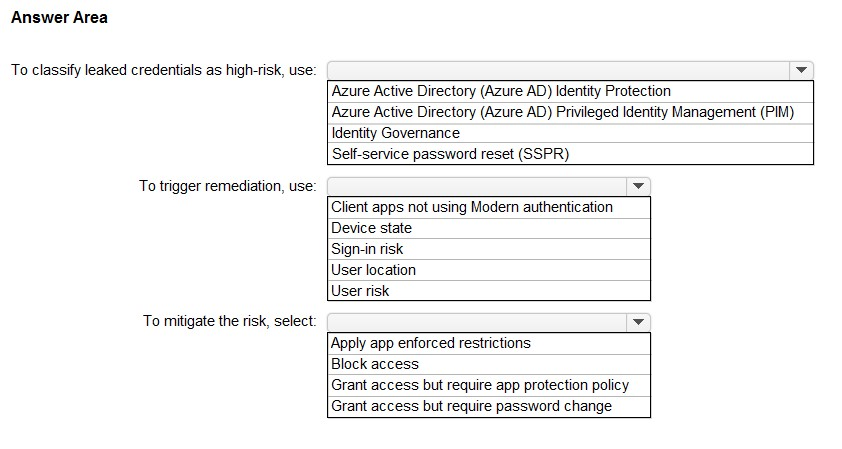
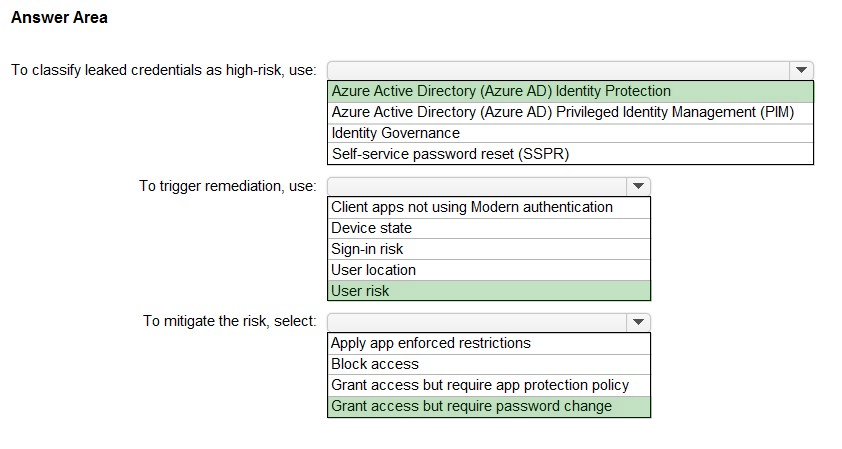
HOTSPOT - You have a Microsoft 365 tenant. You need to identify users who have leaked credentials. The solution must meet the following requirements: ✑ Identify sign-ins by users who are suspected of having leaked credentials. ✑ Flag the sign-ins as a high-risk event. ✑ Immediately enforce a control to mitigate the risk, while still allowing the user to access applications. What should you use? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have an Azure Active Directory (Azure AD) tenant. For the tenant, Users can register applications is set to No. A user named Admin1 must deploy a new cloud app named App1. You need to ensure that Admin1 can register App1 in Azure AD. The solution must use the principle of least privilege. Which role should you assign to Admin1?
A. Managed Application Contributor for Subscription1.
B. Application developer in Azure AD.
C. Cloud application administrator in Azure AD.
D. App Configuration Data Owner for Subscription1.
You have a Microsoft 365 tenant. The Azure Active Directory (Azure AD) tenant syncs to an on-premises Active Directory domain. You plan to create an emergency-access administrative account named Emergency1. Emergency1 will be assigned the Global administrator role in Azure AD. Emergency1 will be used in the event of Azure AD functionality failures and on-premises infrastructure failures. You need to reduce the likelihood that Emergency1 will be prevented from signing in during an emergency. What should you do?
A. Configure Azure Monitor to generate an alert if Emergency1 is modified or signs in.
B. Require Azure AD Privileged Identity Management (PIM) activation of the Global administrator role for Emergency1.
C. Configure a conditional access policy to restrict sign-in locations for Emergency1 to only the corporate network.
D. Configure a conditional access policy to require multi-factor authentication (MFA) for Emergency1.
You have an Azure AD tenant. You plan to implement Azure AD Privileged Identity Management (PIM). Which roles can you manage by using PIM?
A. Global Administrator only
B. Global Administrator and Security Administrator only
C. Global Administrator, Security Administrator, and Security Contributor only
D. Account Administrator, Global Administrator, Security Administrator, and Security Contributor only
DRAG DROP - You have a Microsoft 365 E5 subscription. You need to perform the following tasks: • Identify the locations and IP addresses used by Azure AD users to sign in. • Review the Azure AD security settings and identify improvement recommendations. • Identify changes to Azure AD users or service principals. What should you use for each task? To answer, drag the appropriate resources to the correct requirements. Each resource may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
You have 2,500 users who are assigned Microsoft Office 365 Enterprise E3 licenses. The licenses are assigned to individual users. From the Groups blade in the Microsoft Entra admin center, you assign Microsoft Office 365 Enterprise E5 licenses to a group that includes all users. You need to remove the Office 365 Enterprise E3 licenses from the users by using the least amount of administrative effort. What should you use?
A. the Set-WindowsProductKey cmdlet
B. the Update-MgGroup cmdlet
C. the Set-MgUserLicense cmdlet
D. the Update-MgUser cmdlet
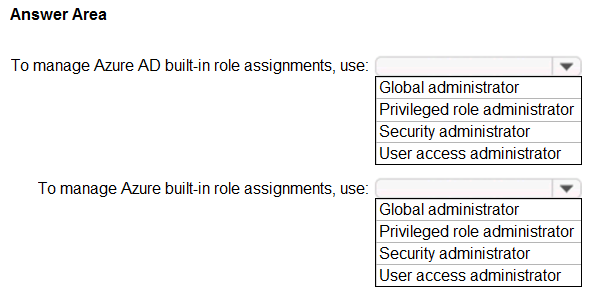
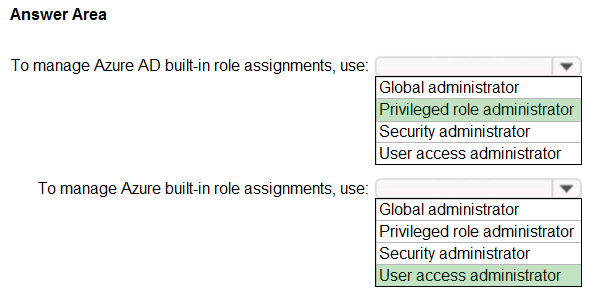
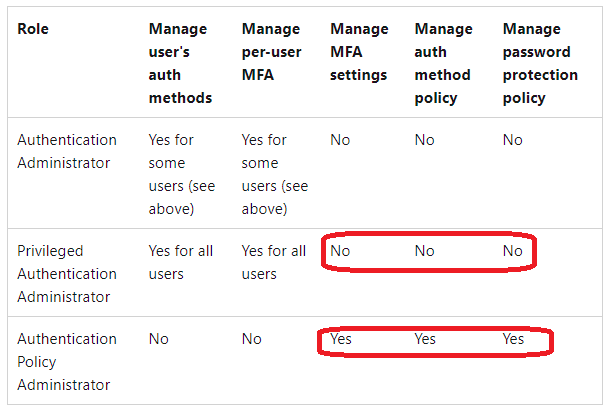
HOTSPOT - You need to identify which roles to use for managing role assignments. The solution must meet the delegation requirements. What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint Online site named Site1. You need to be notified if a user downloads more than 50 files in one minute from Site1. Which type of policy should you create in the Microsoft Defender for Cloud Apps portal?
A. session policy
B. activity policy
C. file policy
D. anomaly detection policy
You have an Azure Active Directory (Azure AD) tenant that contains the users shown in the following table.User1 is the owner of Group1. You create an access review that has the following settings: ✑ What to review: Teams + Groups ✑ Scope: All users ✑ Group: Group1 ✑ Reviewers: Users review their own access Which users can perform access reviews for User3?
A. User1 only
B. User3 only
C. User1 and User2 only
D. User1, User2, and User3
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have an Amazon Web Services (AWS) account, a Google Workspace subscription, and a GitHub account. You deploy an Azure subscription and enable Microsoft 365 Defender. You need to ensure that you can monitor OAuth authentication requests by using Microsoft Defender for Cloud Apps. Solution: From the Microsoft 365 Defender portal, you add the Amazon Web Services app connector. Does this meet the goal?
A. Yes
B. No
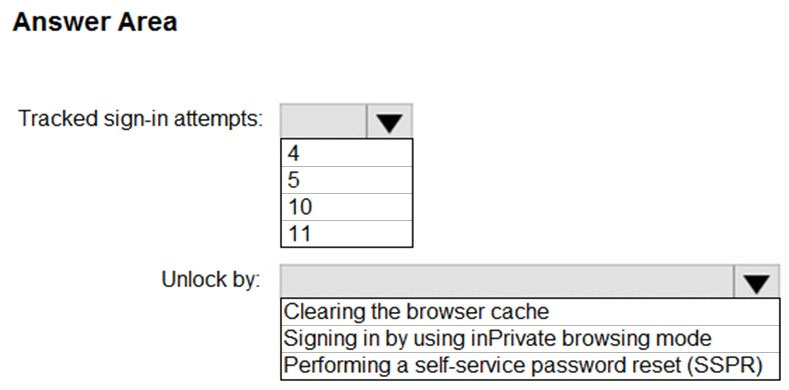
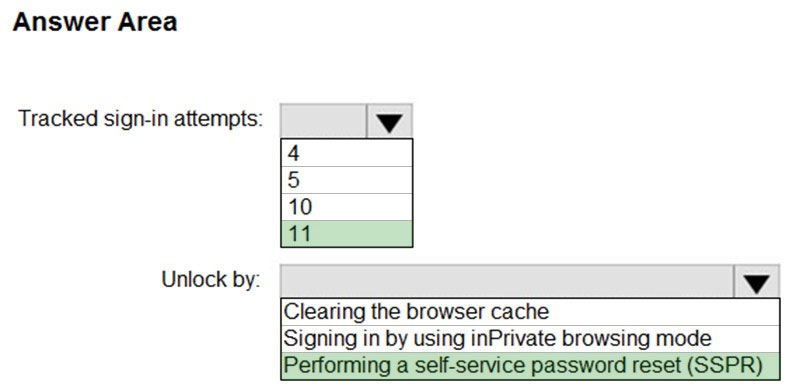
HOTSPOT - A user named User1 attempts to sign in to the tenant by entering the following incorrect passwords: ✑ Pa55w0rd12 ✑ Pa55w0rd12 ✑ Pa55w0rd12 ✑ Pa55w.rd12 ✑ Pa55w.rd123 ✑ Pa55w.rd123 ✑ Pa55w.rd123 ✑ Pa55word12 ✑ Pa55word12 ✑ Pa55word12 ✑ Pa55w.rd12 You need to identify how many sign-in attempts were tracked for User1, and how User1 can unlock her account before the 300-second lockout duration expires. What should identify? To answer, select the appropriate NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 subscription that contains a Microsoft SharePoint Online site named Site1 and a Microsoft 365 group named Group1. You need to ensure that the members of Group1 can access Site1 for 90 days. The solution must minimize administrative effort. What should you use?
A. an access package
B. an access review
C. a lifecycle workflow
D. a Conditional Access policy
Overview - ADatum Corporation is a consulting company in Montreal. ADatum recently acquired a Vancouver-based company named Litware, Inc. Existing Environment. ADatum Environment The on-premises network of ADatum contains an Active Directory Domain Services (AD DS) forest named adatum.com. ADatum has a Microsoft 365 E5 subscription. The subscription contains a verified domain that syncs with the adatum.com AD DS domain by using Azure AD Connect. ADatum has an Azure Active Directory (Azure AD) tenant named adatum.com. The tenant has Security defaults disabled. The tenant contains the users shown in the following table.The tenant contains the groups shown in the following table.
Existing Environment. Litware Environment Litware has an AD DS forest named litware.com Existing Environment. Problem Statements ADatum identifies the following issues: • Multiple users in the sales department have up to five devices. The sales department users report that sometimes they must contact the support department to join their devices to the Azure AD tenant because they have reached their device limit. • A recent security incident reveals that several users leaked their credentials, a suspicious browser was used for a sign-in, and resources were accessed from an anonymous IP address. • When you attempt to assign the Device Administrators role to IT_Group1, the group does NOT appear in the selection list. • Anyone in the organization can invite guest users, including other guests and non-administrators. • The helpdesk spends too much time resetting user passwords. • Users currently use only passwords for authentication. Requirements. Planned Changes - ADatum plans to implement the following changes: • Configure self-service password reset (SSPR). • Configure multi-factor authentication (MFA) for all users. • Configure an access review for an access package named Package1. • Require admin approval for application access to organizational data. • Sync the AD DS users and groups of litware.com with the Azure AD tenant. • Ensure that only users that are assigned specific admin roles can invite guest users. • Increase the maximum number of devices that can be joined or registered to Azure AD to 10. Requirements. Technical Requirements ADatum identifies the following technical requirements: • Users assigned the User administrator role must be able to request permission to use the role when needed for up to one year. • Users must be prompted to register for MFA and provided with an option to bypass the registration for a grace period. • Users must provide one authentication method to reset their password by using SSPR. Available methods must include: - Email - Phone - Security questions - The Microsoft Authenticator app • Trust relationships must NOT be established between the adatum.com and litware.com AD DS domains. • The principle of least privilege must be used. You need to implement the planned changes for Package1. Which users can create and manage the access review?
A. User3 only
B. User4 only
C. User5 only
D. User3 and User4
E. User3 and User5
F. User4 and User5
You have an Azure subscription that uses Azure AD Privileged Identity Management (PIM). You need to identify users that are eligible for the Cloud Application Administrator role. Which blade in the Privileged Identity Management settings should you use?
A. Azure resources
B. Privileged access groups
C. Review access
D. Azure AD roles
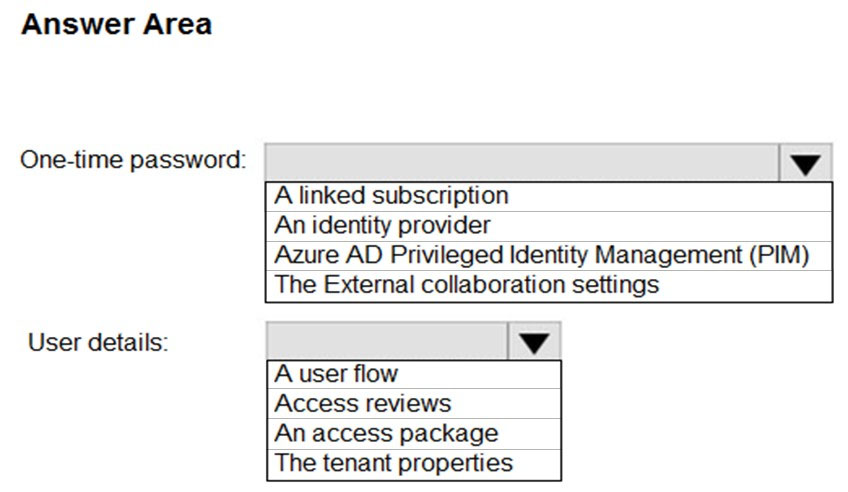
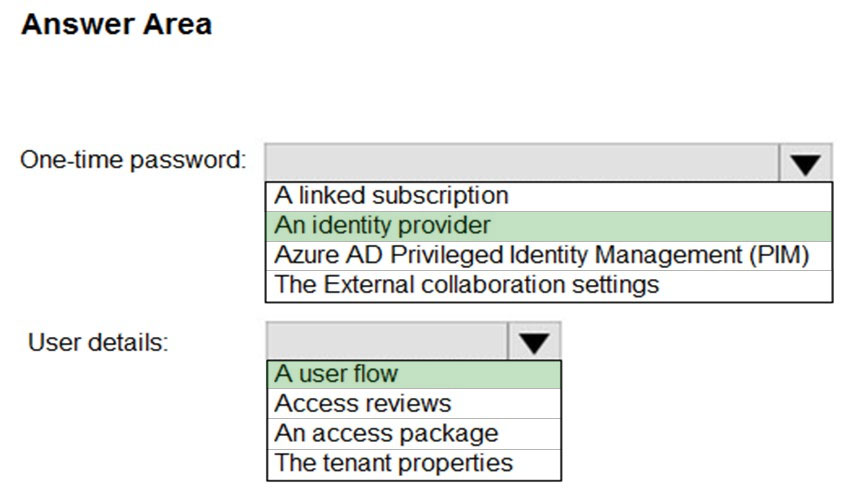
HOTSPOT - You have an Azure Active Directory (Azure AD) tenant and an Azure web app named App1. You need to provide guest users with self-service sign-up for App1. The solution must meet the following requirements: ✑ Guest users must be able to sign up by using a one-time password. ✑ The users must provide their first name, last name, city, and email address during the sign-up process. What should you configure in the Azure Active Directory admin center for each requirement? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - You have an Azure AD tenant. You need to configure the following External Identities features: • B2B collaboration • Monthly active users (MAU)-based pricing Which two settings should you configure? To answer, select the settings in the answer area. NOTE: Each correct selection is worth one point.
HOTSPOT - You have a hybrid Microsoft 365 subscription that contains the users shown in the following table.You plan to deploy an on-premises app named App1. App1 will be registered in Azure AD and will use Azure AD Application Proxy. You need to delegate the installation of the Application Proxy connector and ensure that User1 can register App1 in Azure AD. The solution must use the principle of least privilege. Which user should perform the installation, and which role should you assign to User1? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have an Azure Active Directory (Azure AD) tenant that contains the users shown in the following table.You have an administrative unit named Au1. Group1, User2, and User3 are members of Au1. User5 is assigned the User administrator role for Au1. For which users can User5 reset passwords?
A. User1, User2, and User3
B. User1 and User2 only
C. User3 and User4 only
D. User2 and User3 only
A company uses Dynamics 365 Supply Chain Management master planning. The company plans to run master planning throughout the day. Planning Optimization is not configured. The company administrator reports that they are not able to configure any master planning features or enable master planning in Dynamics 365. You need to implement Planning Optimization. What should you do first?
A. Place the environment into maintenance mode.
B. Deallocate the current environment.
C. Enable the Planning Optimization configuration key.
D. Set the value of the Use Planning Optimization field to yes.
E. Activate the Planning Optimization license.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have an Azure Active Directory (Azure AD) tenant that syncs to an Active Directory forest. You discover that when a user account is disabled in Active Directory, the disabled user can still authenticate to Azure AD for up to 30 minutes. You need to ensure that when a user account is disabled in Active Directory, the user account is immediately prevented from authenticating to Azure AD. Solution: You configure conditional access policies. Does this meet the goal?
A. Yes
B. No
Overview - ADatum Corporation is a consulting company in Montreal. ADatum recently acquired a Vancouver-based company named Litware, Inc. Existing Environment. ADatum Environment The on-premises network of ADatum contains an Active Directory Domain Services (AD DS) forest named adatum.com. ADatum has a Microsoft 365 E5 subscription. The subscription contains a verified domain that syncs with the adatum.com AD DS domain by using Azure AD Connect. ADatum has an Azure Active Directory (Azure AD) tenant named adatum.com. The tenant has Security defaults disabled. The tenant contains the users shown in the following table.The tenant contains the groups shown in the following table.
Existing Environment. Litware Environment Litware has an AD DS forest named litware.com Existing Environment. Problem Statements ADatum identifies the following issues: • Multiple users in the sales department have up to five devices. The sales department users report that sometimes they must contact the support department to join their devices to the Azure AD tenant because they have reached their device limit. • A recent security incident reveals that several users leaked their credentials, a suspicious browser was used for a sign-in, and resources were accessed from an anonymous IP address. • When you attempt to assign the Device Administrators role to IT_Group1, the group does NOT appear in the selection list. • Anyone in the organization can invite guest users, including other guests and non-administrators. • The helpdesk spends too much time resetting user passwords. • Users currently use only passwords for authentication. Requirements. Planned Changes - ADatum plans to implement the following changes: • Configure self-service password reset (SSPR). • Configure multi-factor authentication (MFA) for all users. • Configure an access review for an access package named Package1. • Require admin approval for application access to organizational data. • Sync the AD DS users and groups of litware.com with the Azure AD tenant. • Ensure that only users that are assigned specific admin roles can invite guest users. • Increase the maximum number of devices that can be joined or registered to Azure AD to 10. Requirements. Technical Requirements ADatum identifies the following technical requirements: • Users assigned the User administrator role must be able to request permission to use the role when needed for up to one year. • Users must be prompted to register for MFA and provided with an option to bypass the registration for a grace period. • Users must provide one authentication method to reset their password by using SSPR. Available methods must include: - Email - Phone - Security questions - The Microsoft Authenticator app • Trust relationships must NOT be established between the adatum.com and litware.com AD DS domains. • The principle of least privilege must be used. You need to resolve the issue of the guest user invitations. What should you do for the Azure AD tenant?
A. Configure the Continuous access evaluation settings.
B. Configure a Conditional Access policy.
C. Modify the External collaboration settings.
D. Configure the Access reviews settings.
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Cloud Apps and Yammer. You need prevent users from signing in to Yammer from high-risk locations. What should you do in the Microsoft Defender for Cloud Apps portal?
A. Create an access policy.
B. Create an activity policy.
C. Unsanction Yammer.
D. Create an anomaly detection policy.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You use Azure Monitor to analyze Azure Active Directory (Azure AD) activity logs. You receive more than 100 email alerts each day for failed Azure AD user sign-in attempts. You need to ensure that a new security administrator receives the alerts instead of you. Solution: From Azure Monitor, you create a data collection rule. Does this meet the goal?
A. Yes
B. No
You have an Azure Active Directory (Azure AD) tenant that contains the following objects. ✑ A device named Device1 ✑ Users named User1, User2, User3, User4, and User5 Five groups named Group1, Group2, Group3, Group4, and Group5The groups are configured as shown in the following table.
How many licenses are used if you assign the Microsoft 365 Enterprise E5 license to Group1?
A. 0
B. 2
C. 3
D. 4
You have 2,500 users who are assigned Microsoft Office 365 Enterprise E3 licenses. The licenses are assigned to individual users. From the Groups blade in the Azure Active Directory admin center, you assign Microsoft Office 365 Enterprise E5 licenses to a group that includes all users. You need to remove the Office 365 Enterprise E3 licenses from the users by using the least amount of administrative effort. What should you use?
A. the Update-MgGroup cmdlet
B. the Licenses blade in the Azure Active Directory admin center
C. the Set-WindowsProductKey cmdlet
D. the Administrative units blade in the Azure Active Directory admin center
HOTSPOT - You have a Microsoft Entra tenant that contains a group named Group3 and an administrative unit named Department1. Department1 has the users shown in the Users exhibit. (Click the Users tab.)Department1 has the groups shown in the Groups exhibit. (Click the Groups tab.)
The User Administrator role assignments are shown in the Assignments exhibit (Click the Assignments tab.)
The members of Group2 are shown in the Group2 exhibit. (Click the Group2 tab.)
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
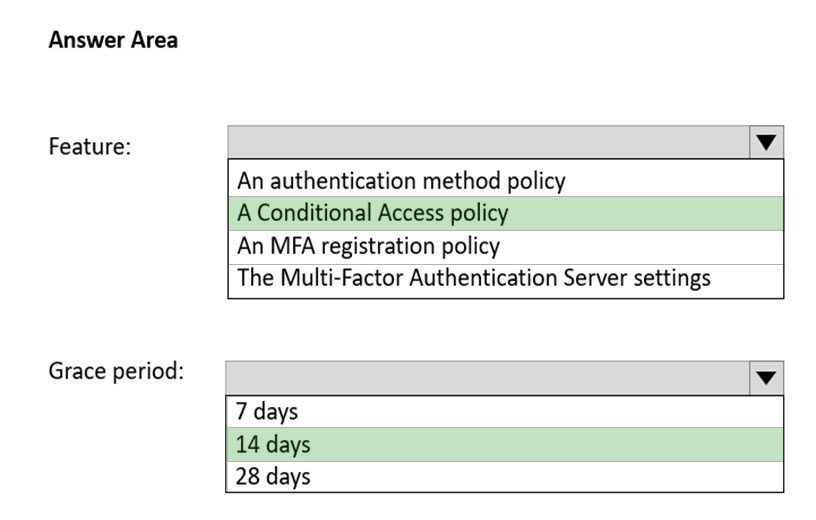
HOTSPOT - You need to support the planned changes and meet the technical requirements for MFA. Which feature should you use, and how long before the users must complete the registration? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains an Azure AD enterprise application named App1. A contractor uses the credentials of user1@outlook.com . You need to ensure that you can provide the contractor with access to App1. The contractor must be able to authenticate as user1@outlook.com . What should you do?
A. Run the New-AzureADMSInvitation cmdlet.
B. Configure the External collaboration settings.
C. Add a WS-Fed identity provider.
D. Implement Azure AD Connect.
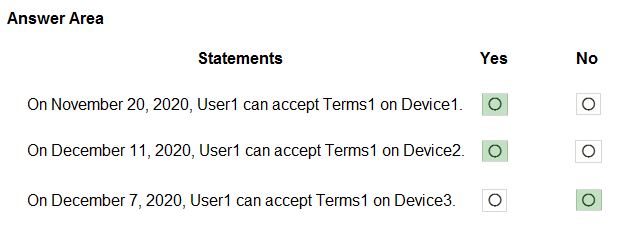
HOTSPOT - You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains a user named User1. User1 has the devices shown in the following table.On November 5, 2020, you create and enforce terms of use in contoso.com that has the following settings: ✑ Name: Terms1 ✑ Display name: Contoso terms of use ✑ Require users to expand the terms of use: On ✑ Require users to consent on every device: On ✑ Expire consents: On ✑ Expire starting on: December 10, 2020 ✑ Frequency: Monthly On November 15, 2020, User1 accepts Terms1 on Device3. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
Your network contains an on-premises Active Directory domain that syncs to an Azure Active Directory (Azure AD) tenant. The tenant contains the users shown in the following table.All the users work remotely. Azure AD Connect is configured in Azure AD as shown in the following exhibit.
Connectivity from the on-premises domain to the internet is lost. Which users can sign in to Azure AD?
A. User1 and User3 only
B. User1 only
C. User1, User2, and User3
D. User1 and User2 only
You have an Azure Active Directory (Azure AD) tenant that contains the following objects: ✑ A device named Device1 ✑ Users named User1, User2, User3, User4, and User5 ✑ Groups named Group1, Group2, Group3, Group4, and Group5 The groups are configured as shown in the following table.To which groups can you assign a Microsoft Office 365 Enterprise E5 license directly?
A. Group1 and Group4 only
B. Group1, Group2, Group3, Group4, and Group5
C. Group1 and Group2 only
D. Group1 only
E. Group1, Group2, Group4, and Group5 only
HOTSPOT - You have an Azure Active Directory (Azure AD) tenant that contains the users shown in the following table.User2 reports that he can only configure multi-factor authentication (MFA) to use the Microsoft Authenticator app. You need to ensure that User2 can configure alternate MFA methods. Which configuration is required, and which user should perform the configuration? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have an Azure Active Directory (Azure AD) tenant. You configure self-service password reset (SSPR) by using the following settings: ✑ Require users to register when signing in: Yes ✑ Number of methods required to reset: 1 What is a valid authentication method available to users?
A. a Microsoft Teams chat
B. a mobile app notification
C. a mobile app code
D. an FIDO2 security token
You have an Azure AD tenant that contains a user named User1. User1 needs to manage license assignments and reset user passwords. Which role should you assign to User1?
A. Helpdesk administrator
B. Billing administrator
C. License administrator
D. User administrator
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have an Active Directory forest that syncs to an Azure Active Directory (Azure AD) tenant. You discover that when a user account is disabled in Active Directory, the disabled user can still authenticate to Azure AD for up to 30 minutes. You need to ensure that when a user account is disabled in Active Directory, the user account is immediately prevented from authenticating to Azure AD. Solution: You configure pass-through authentication. Does this meet the goal?
A. Yes
B. No
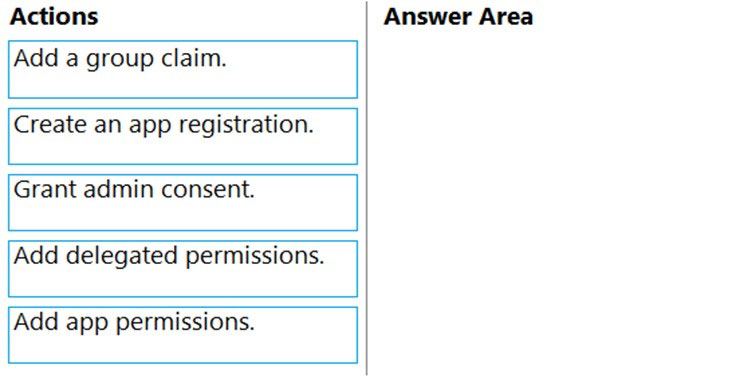
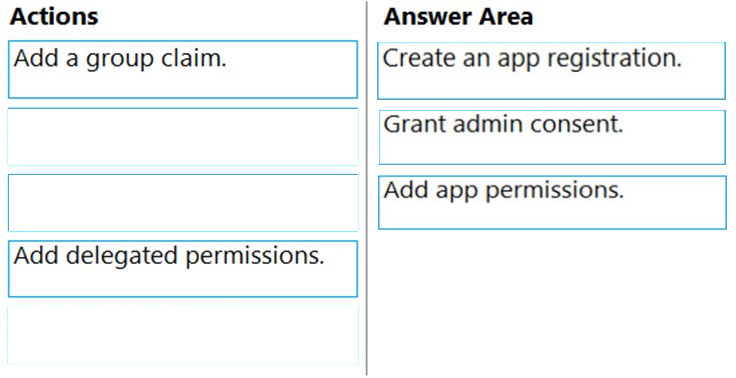
DRAG DROP - Your company has an Azure Active Directory (Azure AD) tenant named contoso.com. The company is developing a web service named App1. You need to ensure that App1 can use Microsoft Graph to read directory data in contoso.com. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange then in the correct order. Select and Place:
You have a Microsoft 365 tenant. All users have mobile phones and Windows 10 laptops. The users frequently work from remote locations that do not have Wi-Fi access or mobile phone connectivity. While working from the remote locations, the users connect their laptops to a wired network that has internet access. You plan to implement multi-factor authentication (MFA). Which MFA authentication method can the users use from the remote location?
A. an app password
B. voice
C. Windows Hello for Business
D. security questions
You have accounts for the following cloud platforms: • Azure • Alibaba Cloud • Amazon Web Services (AWS) • Google Cloud Platform (GCP) You configure an Azure subscription to use Microsoft Entra Permissions Management to manage the permissions in Azure only. Which additional cloud platforms can be managed by using Permissions Management?
A. AWS only
B. Alibaba Cloud and AWS only
C. Alibaba Cloud and GCP only
D. AWS and GCP only
E. Alibaba Cloud, AWS, and GCP
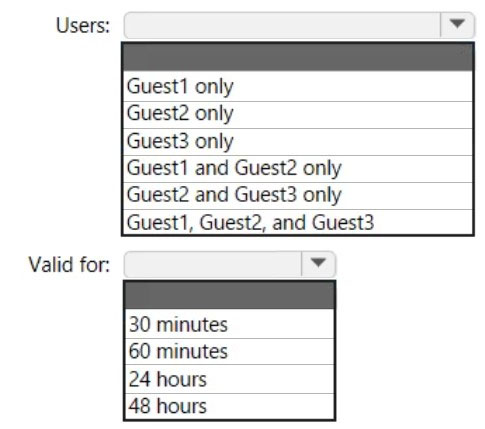
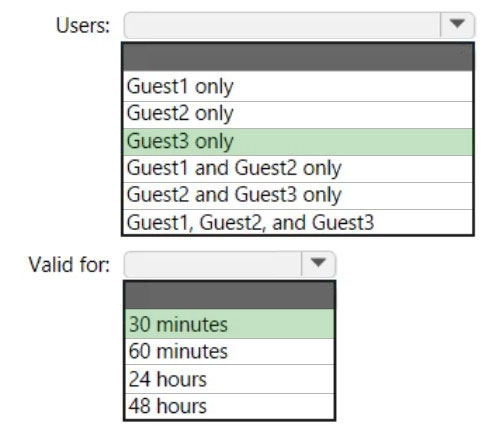
HOTSPOT - You have an Azure Active Directory (Azure AD) tenant named contoso.com that has Email one-time passcode for guests set to Yes. You invite the guest users shown in the following table.Which users will receive a one-time passcode, and how long will the passcode be valid? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - You need to configure app registration in Azure AD to meet the delegation requirements. What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - You have a Microsoft 365 tenant and an Active Directory domain named adatum.com. You deploy Azure AD Connect by using the Express Settings. You need to configure self-service password reset (SSPR) to meet the following requirements: ✑ When users reset their password, they must be prompted to respond to a mobile app notification or answer three predefined security questions. ✑ Passwords must be synced between the tenant and the domain regardless of where the password was reset. What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You configure a new Microsoft 365 tenant to use a default domain name of contoso.com. You need to ensure that you can control access to Microsoft 365 resources by using conditional access policies. What should you do first?
A. Disable Security defaults.
B. Configure password protection for the Azure AD tenant.
C. Configure a multi-factor authentication (MFA) registration policy.
D. Disable the User consent settings.
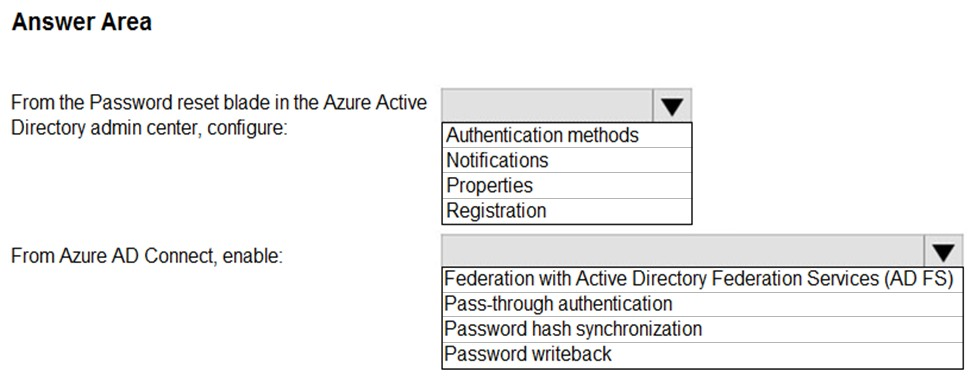
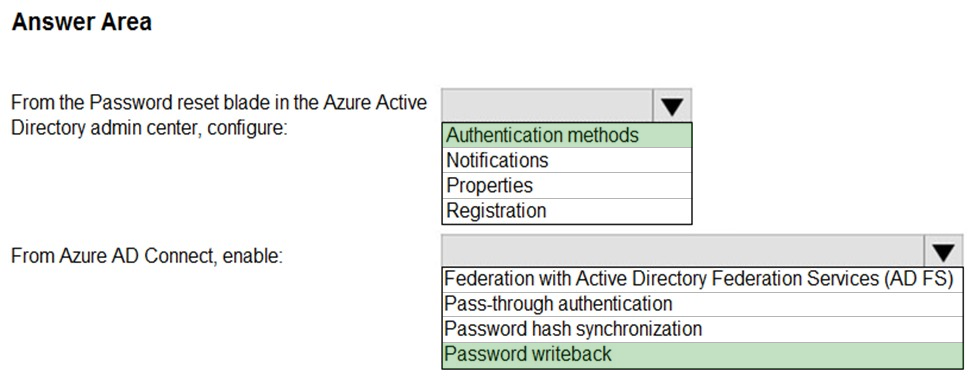
HOTSPOT - Your on-premises network contains an Active Directory domain that uses Azure AD Connect to sync with an Azure AD tenant. You need to configure Azure AD Connect to meet the following requirements: • User sign-ins to Azure AD must be authenticated by an Active Directory domain controller. • Active Directory domain users must be able to use Azure AD self-service password reset (SSPR). What should you use for each requirement? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Access Full SC-300 Dump Free
Looking for even more practice questions? Click here to access the complete SC-300 Dump Free collection, offering hundreds of questions across all exam objectives.
We regularly update our content to ensure accuracy and relevance—so be sure to check back for new material.
Begin your certification journey today with our SC-300 dump free questions — and get one step closer to exam success!