SC-200 Dump Free – 50 Practice Questions to Sharpen Your Exam Readiness.
Looking for a reliable way to prepare for your SC-200 certification? Our SC-200 Dump Free includes 50 exam-style practice questions designed to reflect real test scenarios—helping you study smarter and pass with confidence.
Using an SC-200 dump free set of questions can give you an edge in your exam prep by helping you:
- Understand the format and types of questions you’ll face
- Pinpoint weak areas and focus your study efforts
- Boost your confidence with realistic question practice
Below, you will find 50 free questions from our SC-200 Dump Free collection. These cover key topics and are structured to simulate the difficulty level of the real exam, making them a valuable tool for review or final prep.
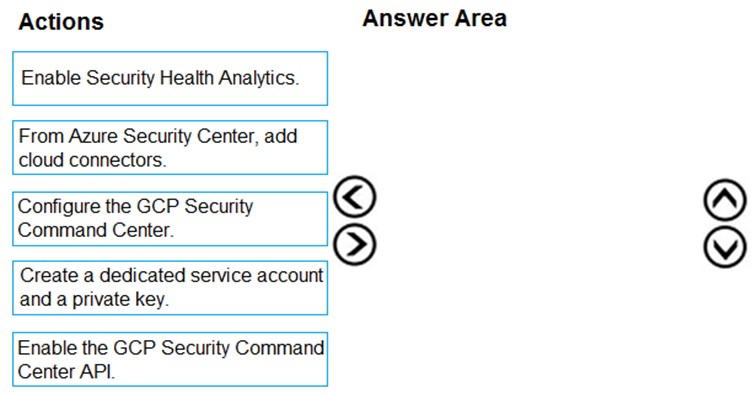
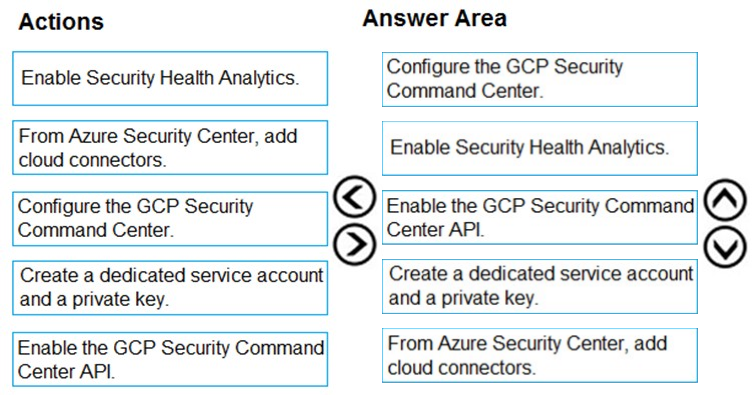
DRAG DROP - You have resources in Azure and Google cloud. You need to ingest Google Cloud Platform (GCP) data into Azure Defender. In which order should you perform the actions? To answer, move all actions from the list of actions to the answer area and arrange them in the correct order. Select and Place:
A company uses Azure Sentinel. You need to create an automated threat response. What should you use?
A. a data connector
B. a playbook
C. a workbook
D. a Microsoft incident creation rule
HOTSPOT - You have a Microsoft 365 subscription that uses Microsoft Defender for Endpoint Plan 2 and contains a Windows device named Device1. You initiated a live response session on Device1. You need to run a command that will download a 250-MB file named File1.exe from the live response library to Device1. The solution must ensure that File1.exe is downloaded as a background process. How should you complete the live response command? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
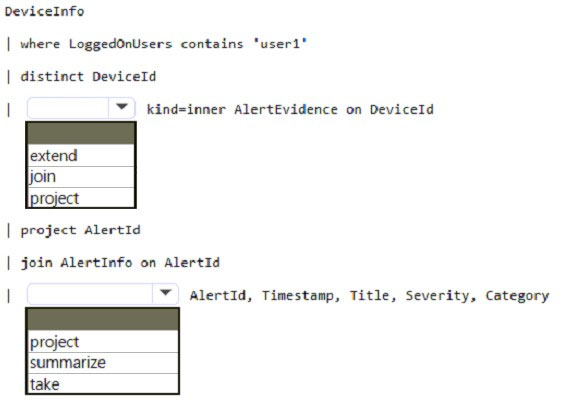
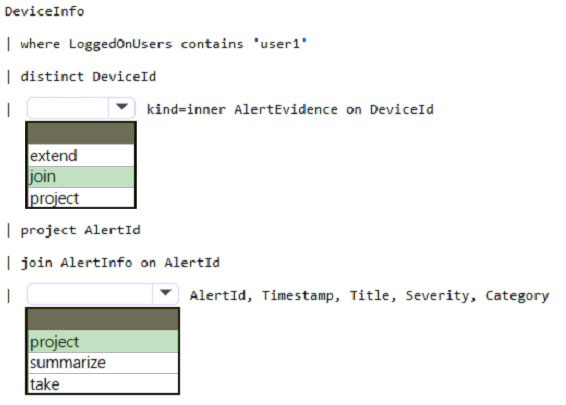
HOTSPOT - You have a Microsoft Sentinel workspace named sws1. You need to create a query that will detect when a user creates an unusually large numbers of Azure AD user accounts. How should you complete the query? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
HOTSPOT - You have a Microsoft Sentinel workspace. A Microsoft Sentinel incident is generated as shown in the following exhibit.Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point.
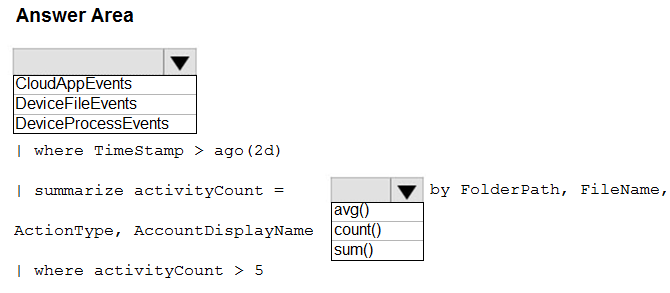
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Endpoint. You need to identify any devices that triggered a malware alert and collect evidence related to the alert. The solution must ensure that you can use the results to initiate device isolation for the affected devices. What should you use in the Microsoft 365 Defender portal?
A. incidents
B. Remediation
C. Investigations
D. Advanced hunting
You are configuring Azure Sentinel. You need to send a Microsoft Teams message to a channel whenever a sign-in from a suspicious IP address is detected. Which two actions should you perform in Azure Sentinel? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Add a playbook.
B. Associate a playbook to an incident.
C. Enable Entity behavior analytics.
D. Create a workbook.
E. Enable the Fusion rule.
You have a Microsoft Sentinel workspace that has User and Entity Behavior Analytics (UEBA) enabled for Signin Logs. You need to ensure that failed interactive sign-ins are detected. The solution must minimize administrative effort. What should you use?
A. a scheduled alert query
B. the Activity Log data connector
C. a UEBA activity template
D. a hunting query
You need to complete the query for failed sign-ins to meet the technical requirements. Where can you find the column name to complete the where clause?
A. Security alerts in Azure Security Center
B. Activity log in Azure
C. Azure Advisor
D. the query windows of the Log Analytics workspace
Overview - Adatum Corporation is a United States-based financial services company that has regional offices in New York, Chicago, and San Francisco. Existing Environment - Identity Environment - The on-premises network contains an Active Directory Domain Services (AD DS) forest named corp.adatum.com that syncs with an Azure AD tenant named adatum.com. All user and group management tasks are performed in corp.adatum.com. The corp.adatum.com domain contains a group named Group1 that syncs with adatum.com. Licensing Status - All the users at Adatum are assigned a Microsoft 365 ES license and an Azure Active Directory Premium P2 license. Cloud Environment - The cloud environment contains a Microsoft 365 subscription, an Azure subscription linked to the adatum.com tenant, and the resources shown in the following table.On-premises Environment - The on-premises network contains the resources shown in the following table.
Requirements - Planned changes - Adatum plans to perform the following changes: • Implement a query named rulequery1 that will include the following KQL query.
• Implement a Microsoft Sentinel scheduled rule that generates incidents based on rulequery1. Microsoft Defender for Cloud Requirements Adatum identifies the following Microsoft Defender for Cloud requirements: • The members of Group1 must be able to enable Defender for Cloud plans and apply regulatory compliance initiatives. • Microsoft Defender for Servers Plan 2 must be enabled on all the Azure virtual machines. • Server2 must be excluded from agentless scanning. Microsoft Sentinel Requirements - Adatum identifies the following Microsoft Sentinel requirements: • Implement an Advanced Security Information Model (ASIM) query that will return a count of DNS requests that results in an NXDOMAIN response from Infoblox1. • Ensure that multiple alerts generated by rulequery1 in response to a single user launching Azure Cloud Shell multiple times are consolidated as a single incident. • Implement the Windows Security Events via AMA connector for Microsoft Sentinel and configure it to monitor the Security event log of Server1. • Ensure that incidents generated by rulequery1 are closed automatically if Azure Cloud Shell is launched by the company’s SecOps team. • Implement a custom Microsoft Sentinel workbook named Workbook1 that will include a query to dynamically retrieve data from Webapp1. • Implement a Microsoft Sentinel near-real-time (NRT) analytics rule that detects sign-ins to a designated break glass account. • Ensure that HuntingQuery1 runs automatically when the Hunting page of Microsoft Sentinel in the Azure portal is accessed. • Ensure that higher than normal volumes of password resets for corp.adatum.com user accounts are detected. • Minimize the overhead associated with queries that use ASIM parsers. • Ensure that the Group1 members can create and edit playbooks. • Use built-in ASIM parsers whenever possible. Business Requirements - Adatum identifies the following business requirements: • Follow the principle of least privilege whenever possible. • Minimize administrative effort whenever possible. You need to ensure that the Group1 members can meet the Microsoft Sentinel requirements. Which role should you assign to Group1?
A. Microsoft Sentinel Playbook Operator
B. Logic App Contributor
C. Automation Operator
D. Microsoft Sentinel Automation Contributor
You have an Azure subscription that has Microsoft Defender for Cloud enabled. You have a virtual machine that runs Windows 10 and has the Log Analytics agent installed. You need to simulate an attack on the virtual machine that will generate an alert. What should you do first?
A. Run the Log Analytics Troubleshooting Tool.
B. Copy and executable and rename the file as ASC_AlertTest_662jfi039N.exe.
C. Modify the settings of the Microsoft Monitoring Agent.
D. Run the MMASetup executable and specify the –foo argument.
You have an Azure subscription that has Azure Defender enabled for all supported resource types. You need to configure the continuous export of high-severity alerts to enable their retrieval from a third-party security information and event management (SIEM) solution. To which service should you export the alerts?
A. Azure Cosmos DB
B. Azure Event Grid
C. Azure Event Hubs
D. Azure Data Lake
HOTSPOT - You have a Microsoft 365 E5 subscription that uses Microsoft Teams. You need to perform a content search of Teams chats for a user by using the Microsoft Purview compliance portal. The solution must minimize the scope of the search. How should you configure the content search? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
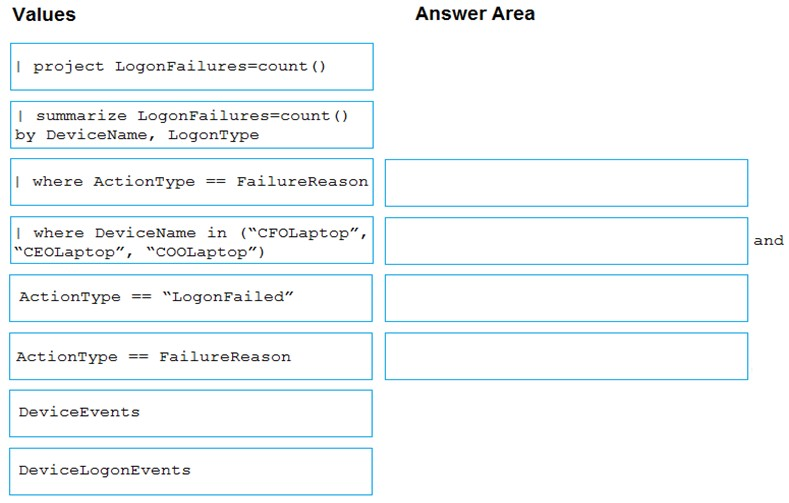
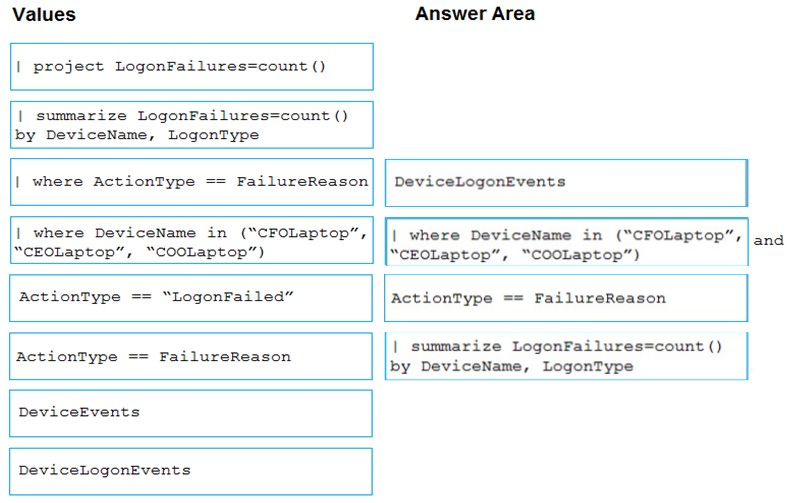
DRAG DROP - You are investigating an incident by using Microsoft 365 Defender. You need to create an advanced hunting query to count failed sign-in authentications on three devices named CFOLaptop, CEOLaptop, and COOLaptop. How should you complete the query? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Select and Place:
You have an Azure subscription that uses Microsoft Defender for Endpoint. You need to ensure that you can allow or block a user-specified range of IP addressed and URLs. What should you enable first in the Advanced features from the Endpoints Settings in the Microsoft 365 Defender portal?
A. custom network indicators
B. live response for servers
C. endpoint detection and response (EDR) in block mode
D. web content filtering
HOTSPOT - Overview - Adatum Corporation is a United States-based financial services company that has regional offices in New York, Chicago, and San Francisco. Existing Environment - Identity Environment - The on-premises network contains an Active Directory Domain Services (AD DS) forest named corp.adatum.com that syncs with an Azure AD tenant named adatum.com. All user and group management tasks are performed in corp.adatum.com. The corp.adatum.com domain contains a group named Group1 that syncs with adatum.com. Licensing Status - All the users at Adatum are assigned a Microsoft 365 ES license and an Azure Active Directory Premium P2 license. Cloud Environment - The cloud environment contains a Microsoft 365 subscription, an Azure subscription linked to the adatum.com tenant, and the resources shown in the following table.On-premises Environment - The on-premises network contains the resources shown in the following table.
Requirements - Planned changes - Adatum plans to perform the following changes: • Implement a query named rulequery1 that will include the following KQL query.
• Implement a Microsoft Sentinel scheduled rule that generates incidents based on rulequery1. Microsoft Defender for Cloud Requirements Adatum identifies the following Microsoft Defender for Cloud requirements: • The members of Group1 must be able to enable Defender for Cloud plans and apply regulatory compliance initiatives. • Microsoft Defender for Servers Plan 2 must be enabled on all the Azure virtual machines. • Server2 must be excluded from agentless scanning. Microsoft Sentinel Requirements Adatum identifies the following Microsoft Sentinel requirements: • Implement an Advanced Security Information Model (ASIM) query that will return a count of DNS requests that results in an NXDOMAIN response from Infoblox1. • Ensure that multiple alerts generated by rulequery1 in response to a single user launching Azure Cloud Shell multiple times are consolidated as a single incident. • Implement the Windows Security Events via AMA connector for Microsoft Sentinel and configure it to monitor the Security event log of Server1. • Ensure that incidents generated by rulequery1 are closed automatically if Azure Cloud Shell is launched by the company’s SecOps team. • Implement a custom Microsoft Sentinel workbook named Workbook1 that will include a query to dynamically retrieve data from Webapp1. • Implement a Microsoft Sentinel near-real-time (NRT) analytics rule that detects sign-ins to a designated break glass account. • Ensure that HuntingQuery1 runs automatically when the Hunting page of Microsoft Sentinel in the Azure portal is accessed. • Ensure that higher than normal volumes of password resets for corp.adatum.com user accounts are detected. • Minimize the overhead associated with queries that use ASIM parsers. • Ensure that the Group1 members can create and edit playbooks. • Use built-in ASIM parsers whenever possible. Business Requirements - Adatum identifies the following business requirements: • Follow the principle of least privilege whenever possible. • Minimize administrative effort whenever possible. You need to implement the query for Workbook1 and Webapp1. The solution must meet the Microsoft Sentinel requirements. How should you configure the query? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have an Azure subscription that uses Microsoft Defender for Cloud and contains 100 virtual machines that run Windows Server. You need to configure Defender for Cloud to collect event data from the virtual machines. The solution must minimize administrative effort and costs. Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. From the workspace created by Defender for Cloud, set the data collection level to Common.
B. From the Microsoft Endpoint Manager admin center, enable automatic enrollment.
C. From the Azure portal, create an Azure Event Grid subscription.
D. From the workspace created by Defender for Cloud, set the data collection level to All Events.
E. From Defender for Cloud in the Azure portal, enable automatic provisioning for the virtual machines.
Overview - Fabrikam, Inc. is a financial services company. The company has branch offices in New York, London, and Singapore. Fabrikam has remote users located across the globe. The remote users access company resources, including cloud resources, by using a VPN connection to a branch office. Existing Environment - Identity Environment - The network contains an Active Directory Domain Services (AD DS) forest named fabrikam.com that syncs with an Azure AD tenant named fabrikam.com. To sync the forest, Fabrikam uses Azure AD Connect with pass-through authentication enabled and password hash synchronization disabled. The fabrikam.com forest contains two global groups named Group1 and Group2. Microsoft 365 Environment - All the users at Fabrikam are assigned a Microsoft 365 E5 license and an Azure Active Directory Premium Plan 2 license. Fabrikam implements Microsoft Defender for Identity and Microsoft Defender for Cloud Apps and enables log collectors. Azure Environment - Fabrikam has an Azure subscription that contains the resources shown in the following table.Amazon Web Services (AWS) Environment Fabrikam has an Amazon Web Services (AWS) account named Account1. Account1 contains 100 Amazon Elastic Compute Cloud (EC2) instances that run a custom Windows Server 2022. The image includes Microsoft SQL Server 2019 and does NOT have any agents installed. Current Issues - When the users use the VPN connections, Microsoft 365 Defender raises a high volume of impossible travel alerts that are false positives. Defender for Identity raises a high volume of Suspected DCSync attack alerts that are false positives. Requirements - Planned changes - Fabrikam plans to implement the following services: • Microsoft Defender for Cloud • Microsoft Sentinel Business Requirements - Fabrikam identifies the following business requirements: • Use the principle of least privilege, whenever possible. • Minimize administrative effort. Microsoft Defender for Cloud Apps Requirements Fabrikam identifies the following Microsoft Defender for Cloud Apps requirements: • Ensure that impossible travel alert policies are based on the previous activities of each user. • Reduce the amount of impossible travel alerts that are false positives. Microsoft Defender for Identity Requirements Minimize the administrative effort required to investigate the false positive alerts. Microsoft Defender for Cloud Requirements Fabrikam identifies the following Microsoft Defender for Cloud requirements: • Ensure that the members of Group2 can modify security policies. • Ensure that the members of Group1 can assign regulatory compliance policy initiatives at the Azure subscription level. • Automate the deployment of the Azure Connected Machine agent for Azure Arc-enabled servers to the existing and future resources of Account1. • Minimize the administrative effort required to investigate the false positive alerts. Microsoft Sentinel Requirements - Fabrikam identifies the following Microsoft Sentinel requirements: • Query for NXDOMAIN DNS requests from the last seven days by using built-in Advanced Security Information Model (ASIM) unifying parsers. • From AWS EC2 instances, collect Windows Security event log entries that include local group membership changes. • Identify anomalous activities of Azure AD users by using User and Entity Behavior Analytics (UEBA). • Evaluate the potential impact of compromised Azure AD user credentials by using UEBA. • Ensure that App1 is available for use in Microsoft Sentinel automation rules. • Identify the mean time to triage for incidents generated during the last 30 days. • Identify the mean time to close incidents generated during the last 30 days. • Ensure that the members of Group1 can create and run playbooks. • Ensure that the members of Group1 can manage analytics rules. • Run hunting queries on Pool1 by using Jupyter notebooks. • Ensure that the members of Group2 can manage incidents. • Maximize the performance of data queries. • Minimize the amount of collected data. You need to meet the Microsoft Sentinel requirements for App1. What should you configure for App1?
A. a trigger
B. a connector
C. authorization
D. an API connection
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have an Azure subscription that uses Microsoft Defender XDR. From the Microsoft Defender portal, you perform an audit search and export the results as a file named File1.csv that contains 10,000 rows. You use Microsoft Excel to perform Get & Transform Data operations to parse the AuditData column from File1.csv. The operations fail to generate columns for specific JSON properties. You need to ensure that Excel generates columns for the specific JSON properties in the audit search results. Solution: From Excel, you apply filters to the existing columns in File1.csv to reduce the number of rows, and then you perform the Get & Transform Data operations to parse the AuditData column. Does this meet the requirement?
A. Yes
B. No
HOTSPOT - You have an Azure subscription that contains a user named User1 and a Microsoft Sentinel workspace named WS1. You need to ensure that User1 can enable User and Entity Behavior Analytics (UEBA) for WS1. The solution must follow the principle of least privilege. Which roles should you assign to User1? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
HOTSPOT - You have a Microsoft 365 subscription that uses Microsoft 365 Defender and contains a user named User1. You are notified that the account of User1 is compromised. You need to review the alerts triggered on the devices to which User1 signed in. How should you complete the query? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 subscription that uses Microsoft Defender for Endpoint Plan 2 and contains a macOS device named Device1. You need to investigate a Defender for Endpoint agent alert on Device1. The solution must meet the following requirements: • Identify all the active network connections on Device1. • Identify all the running processes on Device1. • Retrieve the login history of Device1. • Minimize administrative effort. What should you do first from the Microsoft Defender portal?
A. From Devices, click Collect investigation package for Device1.
B. From Advanced features in Endpoints, enable Live Response unsigned script execution.
C. From Devices, initiate a live response session on Device1.
D. From Advanced features in Endpoints, disable Authenticated telemetry.
Your company stores the data of every project in a different Azure subscription. All the subscriptions use the same Azure Active Directory (Azure AD) tenant. Every project consists of multiple Azure virtual machines that run Windows Server. The Windows events of the virtual machines are stored in a Log Analytics workspace in each machine's respective subscription. You deploy Azure Sentinel to a new Azure subscription. You need to perform hunting queries in Azure Sentinel to search across all the Log Analytics workspaces of all the subscriptions. Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Add the Security Events connector to the Azure Sentinel workspace.
B. Create a query that uses the workspace expression and the union operator.
C. Use the alias statement.
D. Create a query that uses the resource expression and the alias operator.
E. Add the Azure Sentinel solution to each workspace.
HOTSPOT - Overview - Adatum Corporation is a United States-based financial services company that has regional offices in New York, Chicago, and San Francisco. Existing Environment - Identity Environment - The on-premises network contains an Active Directory Domain Services (AD DS) forest named corp.adatum.com that syncs with an Azure AD tenant named adatum.com. All user and group management tasks are performed in corp.adatum.com. The corp.adatum.com domain contains a group named Group1 that syncs with adatum.com. Licensing Status - All the users at Adatum are assigned a Microsoft 365 ES license and an Azure Active Directory Premium P2 license. Cloud Environment - The cloud environment contains a Microsoft 365 subscription, an Azure subscription linked to the adatum.com tenant, and the resources shown in the following table.On-premises Environment - The on-premises network contains the resources shown in the following table.
Requirements - Planned changes - Adatum plans to perform the following changes: • Implement a query named rulequery1 that will include the following KQL query.
• Implement a Microsoft Sentinel scheduled rule that generates incidents based on rulequery1. Microsoft Defender for Cloud Requirements Adatum identifies the following Microsoft Defender for Cloud requirements: • The members of Group1 must be able to enable Defender for Cloud plans and apply regulatory compliance initiatives. • Microsoft Defender for Servers Plan 2 must be enabled on all the Azure virtual machines. • Server2 must be excluded from agentless scanning. Microsoft Sentinel Requirements Adatum identifies the following Microsoft Sentinel requirements: • Implement an Advanced Security Information Model (ASIM) query that will return a count of DNS requests that results in an NXDOMAIN response from Infoblox1. • Ensure that multiple alerts generated by rulequery1 in response to a single user launching Azure Cloud Shell multiple times are consolidated as a single incident. • Implement the Windows Security Events via AMA connector for Microsoft Sentinel and configure it to monitor the Security event log of Server1. • Ensure that incidents generated by rulequery1 are closed automatically if Azure Cloud Shell is launched by the company’s SecOps team. • Implement a custom Microsoft Sentinel workbook named Workbook1 that will include a query to dynamically retrieve data from Webapp1. • Implement a Microsoft Sentinel near-real-time (NRT) analytics rule that detects sign-ins to a designated break glass account. • Ensure that HuntingQuery1 runs automatically when the Hunting page of Microsoft Sentinel in the Azure portal is accessed. • Ensure that higher than normal volumes of password resets for corp.adatum.com user accounts are detected. • Minimize the overhead associated with queries that use ASIM parsers. • Ensure that the Group1 members can create and edit playbooks. • Use built-in ASIM parsers whenever possible. Business Requirements - Adatum identifies the following business requirements: • Follow the principle of least privilege whenever possible. • Minimize administrative effort whenever possible. You need to monitor the password resets. The solution must meet the Microsoft Sentinel requirements. What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have an Azure Sentinel deployment in the East US Azure region. You create a Log Analytics workspace named LogsWest in the West US Azure region. You need to ensure that you can use scheduled analytics rules in the existing Azure Sentinel deployment to generate alerts based on queries to LogsWest. What should you do first?
A. Deploy Azure Data Catalog to the West US Azure region.
B. Modify the workspace settings of the existing Azure Sentinel deployment.
C. Add Azure Sentinel to a workspace.
D. Create a data connector in Azure Sentinel.
You have an Azure subscription that uses Microsoft Defender for Cloud. You need to configure Defender for Cloud to mitigate the following risks: • Vulnerabilities within the application source code • Exploitation toolkits in declarative templates • Operations from malicious IP addresses • Exposed secrets Which two Defender for Cloud services should you use? Each correct answer presents part of the solution. NOTE: Each correct answer is worth one point.
A. Microsoft Defender for Resource Manager
B. Microsoft Defender for DNS
C. Microsoft Defender for App Service
D. Microsoft Defender for Servers
E. Microsoft Defender for DevOps
HOTSPOT - You need to create an advanced hunting query to investigate the executive team issue. How should you complete the query? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
The issue for which team can be resolved by using Microsoft Defender for Office 365?
A. executive
B. marketing
C. security
D. sales
HOTSPOT - You have an Azure subscription that uses Microsoft Defender for Cloud and contains an Azure logic app named app1. You need to ensure that app1 launches when a specific Defender for Cloud security alert is generated. How should you complete the Azure Resource Manager (ARM) template? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Overview - Fabrikam, Inc. is a financial services company. The company has branch offices in New York, London, and Singapore. Fabrikam has remote users located across the globe. The remote users access company resources, including cloud resources, by using a VPN connection to a branch office. Existing Environment - Identity Environment - The network contains an Active Directory Domain Services (AD DS) forest named fabrikam.com that syncs with an Azure AD tenant named fabrikam.com. To sync the forest, Fabrikam uses Azure AD Connect with pass-through authentication enabled and password hash synchronization disabled. The fabrikam.com forest contains two global groups named Group1 and Group2. Microsoft 365 Environment - All the users at Fabrikam are assigned a Microsoft 365 E5 license and an Azure Active Directory Premium Plan 2 license. Fabrikam implements Microsoft Defender for Identity and Microsoft Defender for Cloud Apps and enables log collectors. Azure Environment - Fabrikam has an Azure subscription that contains the resources shown in the following table.Amazon Web Services (AWS) Environment Fabrikam has an Amazon Web Services (AWS) account named Account1. Account1 contains 100 Amazon Elastic Compute Cloud (EC2) instances that run a custom Windows Server 2022. The image includes Microsoft SQL Server 2019 and does NOT have any agents installed. Current Issues - When the users use the VPN connections, Microsoft 365 Defender raises a high volume of impossible travel alerts that are false positives. Defender for Identity raises a high volume of Suspected DCSync attack alerts that are false positives. Requirements - Planned changes - Fabrikam plans to implement the following services: • Microsoft Defender for Cloud • Microsoft Sentinel Business Requirements - Fabrikam identifies the following business requirements: • Use the principle of least privilege, whenever possible. • Minimize administrative effort. Microsoft Defender for Cloud Apps Requirements Fabrikam identifies the following Microsoft Defender for Cloud Apps requirements: • Ensure that impossible travel alert policies are based on the previous activities of each user. • Reduce the amount of impossible travel alerts that are false positives. Microsoft Defender for Identity Requirements Minimize the administrative effort required to investigate the false positive alerts. Microsoft Defender for Cloud Requirements Fabrikam identifies the following Microsoft Defender for Cloud requirements: • Ensure that the members of Group2 can modify security policies. • Ensure that the members of Group1 can assign regulatory compliance policy initiatives at the Azure subscription level. • Automate the deployment of the Azure Connected Machine agent for Azure Arc-enabled servers to the existing and future resources of Account1. • Minimize the administrative effort required to investigate the false positive alerts. Microsoft Sentinel Requirements - Fabrikam identifies the following Microsoft Sentinel requirements: • Query for NXDOMAIN DNS requests from the last seven days by using built-in Advanced Security Information Model (ASIM) unifying parsers. • From AWS EC2 instances, collect Windows Security event log entries that include local group membership changes. • Identify anomalous activities of Azure AD users by using User and Entity Behavior Analytics (UEBA). • Evaluate the potential impact of compromised Azure AD user credentials by using UEBA. • Ensure that App1 is available for use in Microsoft Sentinel automation rules. • Identify the mean time to triage for incidents generated during the last 30 days. • Identify the mean time to close incidents generated during the last 30 days. • Ensure that the members of Group1 can create and run playbooks. • Ensure that the members of Group1 can manage analytics rules. • Run hunting queries on Pool1 by using Jupyter notebooks. • Ensure that the members of Group2 can manage incidents. • Maximize the performance of data queries. • Minimize the amount of collected data. You need to minimize the effort required to investigate the Microsoft Defender for Identity false positive alerts. What should you review?
A. the status update time
B. the resolution method of the source computer
C. the alert status
D. the certainty of the source computer
HOTSPOT - You have an Azure subscription that contains a Microsoft Sentinel workspace. You need to create a hunting query using Kusto Query Language (KQL) that meets the following requirements: • Identifies an anomalous number of changes to the rules of a network security group (NSG) made by the same security principal. • Automatically associates the security principal with a Microsoft Sentinel entity. How should you complete the query? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
DRAG DROP - You have an Azure subscription that uses Microsoft Defender for Cloud. You need to create a workflow that will send a Microsoft Teams message to the IT department of your company when a new Microsoft Secure Score action is generated. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
DRAG DROP - You have a Microsoft 365 E5 subscription that uses Microsoft Exchange Online. You need to identify phishing email messages. Which three cmdlets should you run in sequence? To answer, move the appropriate cmdlets from the list of cmdlets to the answer area and arrange them in the correct order.
Your company uses Azure Security Center and Azure Defender. The security operations team at the company informs you that it does NOT receive email notifications for security alerts. What should you configure in Security Center to enable the email notifications?
A. Security solutions
B. Security policy
C. Pricing & settings
D. Security alerts
E. Azure Defender
You have a Microsoft Sentinel workspace. You receive multiple alerts for failed sign-in attempts to an account. You identify that the alerts are false positives. You need to prevent additional failed sign-in alerts from being generated for the account. The solution must meet the following requirements: • Ensure that failed sign-in alerts are generated for other accounts. • Minimize administrative effort What should do?
A. Modify the analytics rule.
B. Create a watchlist.
C. Add an activity template to the entity behavior.
D. Create an automation rule.
You have an Azure subscription that contains a Log Analytics workspace. You need to enable just-in-time (JIT) VM access and network detections for Azure resources. Where should you enable Azure Defender?
A. at the subscription level
B. at the workspace level
C. at the resource level
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You are configuring Microsoft Defender for Identity integration with Active Directory. From the Microsoft Defender for identity portal, you need to configure several accounts for attackers to exploit. Solution: You add each account as a Sensitive account. Does this meet the goal?
A. Yes
B. No
Overview - Adatum Corporation is a United States-based financial services company that has regional offices in New York, Chicago, and San Francisco. Existing Environment - Identity Environment - The on-premises network contains an Active Directory Domain Services (AD DS) forest named corp.adatum.com that syncs with an Azure AD tenant named adatum.com. All user and group management tasks are performed in corp.adatum.com. The corp.adatum.com domain contains a group named Group1 that syncs with adatum.com. Licensing Status - All the users at Adatum are assigned a Microsoft 365 ES license and an Azure Active Directory Premium P2 license. Cloud Environment - The cloud environment contains a Microsoft 365 subscription, an Azure subscription linked to the adatum.com tenant, and the resources shown in the following table.On-premises Environment - The on-premises network contains the resources shown in the following table.
Requirements - Planned changes - Adatum plans to perform the following changes: • Implement a query named rulequery1 that will include the following KQL query.
• Implement a Microsoft Sentinel scheduled rule that generates incidents based on rulequery1. Microsoft Defender for Cloud Requirements Adatum identifies the following Microsoft Defender for Cloud requirements: • The members of Group1 must be able to enable Defender for Cloud plans and apply regulatory compliance initiatives. • Microsoft Defender for Servers Plan 2 must be enabled on all the Azure virtual machines. • Server2 must be excluded from agentless scanning. Microsoft Sentinel Requirements - Adatum identifies the following Microsoft Sentinel requirements: • Implement an Advanced Security Information Model (ASIM) query that will return a count of DNS requests that results in an NXDOMAIN response from Infoblox1. • Ensure that multiple alerts generated by rulequery1 in response to a single user launching Azure Cloud Shell multiple times are consolidated as a single incident. • Implement the Windows Security Events via AMA connector for Microsoft Sentinel and configure it to monitor the Security event log of Server1. • Ensure that incidents generated by rulequery1 are closed automatically if Azure Cloud Shell is launched by the company’s SecOps team. • Implement a custom Microsoft Sentinel workbook named Workbook1 that will include a query to dynamically retrieve data from Webapp1. • Implement a Microsoft Sentinel near-real-time (NRT) analytics rule that detects sign-ins to a designated break glass account. • Ensure that HuntingQuery1 runs automatically when the Hunting page of Microsoft Sentinel in the Azure portal is accessed. • Ensure that higher than normal volumes of password resets for corp.adatum.com user accounts are detected. • Minimize the overhead associated with queries that use ASIM parsers. • Ensure that the Group1 members can create and edit playbooks. • Use built-in ASIM parsers whenever possible. Business Requirements - Adatum identifies the following business requirements: • Follow the principle of least privilege whenever possible. • Minimize administrative effort whenever possible. You need to configure event monitoring for Server1. The solution must meet the Microsoft Sentinel requirements. What should you create first?
A. a Microsoft Sentinel automation rule
B. an Azure Event Grid topic
C. a Microsoft Sentinel scheduled query rule
D. a Data Collection Rule (DCR)
You have a Microsoft 365 E5 subscription that contains a device named Device1. Device1 is enrolled in Microsoft Defender for Endpoint. Device1 reports an incident that includes a file named File1.exe as evidence. You initiate the Collect Investigation Package action and download the ZIP file. You need to identify the first and last time File1.exe was executed. What should you review in the investigation package?
A. Processes
B. Autoruns
C. Security event log
D. Scheduled tasks
E. Prefetch files
HOTSPOT - You have four Azure subscriptions. One of the subscriptions contains a Microsoft Sentinel workspace. You need to deploy Microsoft Sentinel data connectors to collect data from the subscriptions by using Azure Policy. The solution must ensure that the policy will apply to new and existing resources in the subscriptions. Which type of connectors should you provision, and what should you use to ensure that all the resources are monitored? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
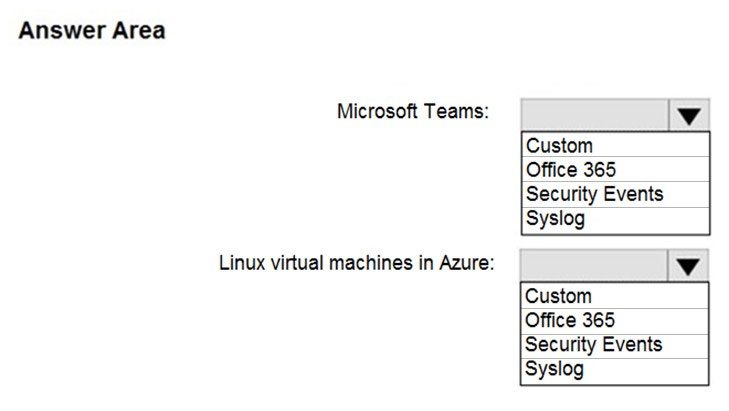
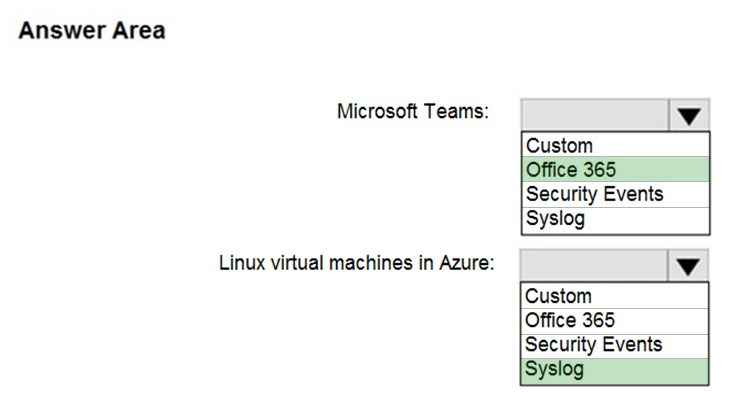
HOTSPOT - You deploy Azure Sentinel. You need to implement connectors in Azure Sentinel to monitor Microsoft Teams and Linux virtual machines in Azure. The solution must minimize administrative effort. Which data connector type should you use for each workload? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You are configuring Microsoft Cloud App Security. You have a custom threat detection policy based on the IP address ranges of your company's United States-based offices. You receive many alerts related to impossible travel and sign-ins from risky IP addresses. You determine that 99% of the alerts are legitimate sign-ins from your corporate offices. You need to prevent alerts for legitimate sign-ins from known locations. Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Configure automatic data enrichment.
B. Add the IP addresses to the corporate address range category.
C. Increase the sensitivity level of the impossible travel anomaly detection policy.
D. Add the IP addresses to the other address range category and add a tag.
E. Create an activity policy that has an exclusion for the IP addresses.
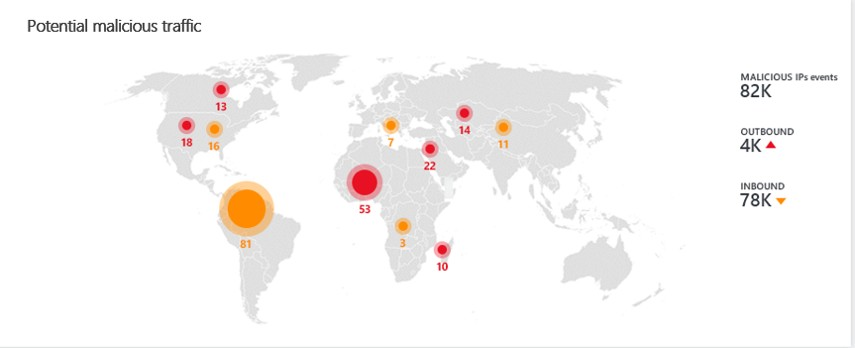
You have a Microsoft Sentinel workspace that contains the following incident. Brute force attack against Azure Portal analytics rule has been triggered. You need to identify the geolocation information that corresponds to the incident. What should you do?
A. From Overview, review the Potential malicious events map.
B. From Incidents, review the details of the IPCustomEntity entity associated with the incident.
C. From Incidents, review the details of the AccountCustomEntity entity associated with the incident.
D. From Investigation, review insights on the incident entity.
You need to implement the Azure Information Protection requirements. What should you configure first?
A. Device health and compliance reports settings in Microsoft Defender Security Center
B. scanner clusters in Azure Information Protection from the Azure portal
C. content scan jobs in Azure Information Protection from the Azure portal
D. Advanced features from Settings in Microsoft Defender Security Center
You have an Azure subscription that uses Microsoft Defender for Cloud. You have an Amazon Web Services (AWS) subscription. The subscription contains multiple virtual machines that run Windows Server. You need to enable Microsoft Defender for Servers on the virtual machines. Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct answer is worth one point.
A. From Defender for Cloud, enable agentless scanning.
B. Onboard the virtual machines to Microsoft Defender for Endpoint.
C. From Defender for Cloud, configure the AWS connector.
D. Install the Azure Virtual Machine Agent (VM Agent) on each virtual machine.
E. From Defender for Cloud, configure auto-provisioning.
HOTSPOT - You have a Microsoft Sentinel workspace named sws1. You plan to create an Azure logic app that will raise an incident in an on-premises IT service management system when an incident is generated in sws1. You need to configure the Microsoft Sentinel connector credentials for the logic app. The solution must meet the following requirements: • Minimize administrative effort. • Use the principle of least privilege. How should you configure the credentials? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Your company uses Microsoft Defender for Endpoint. The company has Microsoft Word documents that contain macros. The documents are used frequently on the devices of the company's accounting team. You need to hide false positive in the Alerts queue, while maintaining the existing security posture. Which three actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Resolve the alert automatically.
B. Hide the alert.
C. Create a suppression rule scoped to any device.
D. Create a suppression rule scoped to a device group.
E. Generate the alert.
HOTSPOT - You have a Microsoft 365 E5 subscription that uses Microsoft Defender 365. Your network contains an on-premises Active Directory Domain Services (AD DS) domain that syncs with Azure AD. You need to identify LDAP requests by AD DS users to enumerate AD DS objects. How should you complete the KQL query? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You create an Azure subscription. You enable Azure Defender for the subscription. You need to use Azure Defender to protect on-premises computers. What should you do on the on-premises computers?
A. Install the Log Analytics agent.
B. Install the Dependency agent.
C. Configure the Hybrid Runbook Worker role.
D. Install the Connected Machine agent.
You have a custom Microsoft Sentinel workbook named Workbook1. You need to add a grid to Workbook1. The solution must ensure that the grid contains a maximum of 100 rows. What should you do?
A. In the grid query, include the take operator.
B. In the grid query, include the project operator.
C. In the query editor interface, configure Settings.
D. In the query editor interface, select Advanced Editor.
Access Full SC-200 Dump Free
Looking for even more practice questions? Click here to access the complete SC-200 Dump Free collection, offering hundreds of questions across all exam objectives.
We regularly update our content to ensure accuracy and relevance—so be sure to check back for new material.
Begin your certification journey today with our SC-200 dump free questions — and get one step closer to exam success!