312-50V9 Dump Free – 50 Practice Questions to Sharpen Your Exam Readiness.
Looking for a reliable way to prepare for your 312-50V9 certification? Our 312-50V9 Dump Free includes 50 exam-style practice questions designed to reflect real test scenarios—helping you study smarter and pass with confidence.
Using an 312-50V9 dump free set of questions can give you an edge in your exam prep by helping you:
- Understand the format and types of questions you’ll face
- Pinpoint weak areas and focus your study efforts
- Boost your confidence with realistic question practice
Below, you will find 50 free questions from our 312-50V9 Dump Free collection. These cover key topics and are structured to simulate the difficulty level of the real exam, making them a valuable tool for review or final prep.
A Certificate Authority (CA) generates a key pair that will be used for encryption and decryption of email. The integrity of the encrypted email is dependent on the security of which of the following?
A. Public key
B. Private key
C. Modulus length
D. Email server certificate
Which of the following items of a computer system will an anti-virus program scan for viruses?
A. Boot Sector
B. Deleted Files
C. Windows Process List
D. Password Protected Files
An ethical hacker for a large security research firm performs penetration tests, vulnerability tests, and risk assessments. A friend recently started a company and asks the hacker to perform a penetration test and vulnerability assessment of the new company as a favor. What should the hacker's next step be before starting work on this job?
A. Start by foot printing the network and mapping out a plan of attack.
B. Ask the employer for authorization to perform the work outside the company.
C. Begin the reconnaissance phase with passive information gathering and then move into active information gathering.
D. Use social engineering techniques on the friend’s employees to help identify areas that may be susceptible to attack.
Neil notices that a single address is generating traffic from its port 500 to port 500 of several other machines on the network. This scan is eating up most of the network bandwidth and Neil is concerned. As a security professional, what would you infer from this scan?
A. It is a network fault and the originating machine is in a network loop
B. It is a worm that is malfunctioning or hardcoded to scan on port 500
C. The attacker is trying to detect machines on the network which have SSL enabled
D. The attacker is trying to determine the type of VPN implementation and checking for IPSec
Which of the following is a strong post designed to stop a car?
A. Gate
B. Fence
C. Bollard
D. Reinforced rebar
A security analyst is performing an audit on the network to determine if there are any deviations from the security policies in place. The analyst discovers that a user from the IT department had a dial-out modem installed. Which security policy must the security analyst check to see if dial-out modems are allowed?
A. Firewall-management policy
B. Acceptable-use policy
C. Remote-access policy
D. Permissive policy
A company is using Windows Server 2003 for its Active Directory (AD). What is the most efficient way to crack the passwords for the AD users?
A. Perform a dictionary attack.
B. Perform a brute force attack.
C. Perform an attack with a rainbow table.
D. Perform a hybrid attack.
The precaution of prohibiting employees from bringing personal computing devices into a facility is what type of security control?
A. Physical
B. Procedural
C. Technical
D. Compliance
Which of the following represents the initial two commands that an IRC client sends to join an IRC network?
A. USER, NICK
B. LOGIN, NICK
C. USER, PASS
D. LOGIN, USER
What are the three types of compliance that the Open Source Security Testing Methodology Manual (OSSTMM) recognizes?
A. Legal, performance, audit
B. Audit, standards based, regulatory
C. Contractual, regulatory, industry
D. Legislative, contractual, standards based
Which of the following lists are valid data-gathering activities associated with a risk assessment?
A. Threat identification, vulnerability identification, control analysis
B. Threat identification, response identification, mitigation identification
C. Attack profile, defense profile, loss profile
D. System profile, vulnerability identification, security determination
Which of the following techniques will identify if computer files have been changed?
A. Network sniffing
B. Permission sets
C. Integrity checking hashes
D. Firewall alerts
When utilizing technical assessment methods to assess the security posture of a network, which of the following techniques would be most effective in determining whether end-user security training would be beneficial?
A. Vulnerability scanning
B. Social engineering
C. Application security testing
D. Network sniffing
Which system consists of a publicly available set of databases that contain domain name registration contact information?
A. WHOIS
B. IANA
C. CAPTCHA
D. IETF
The use of alert thresholding in an IDS can reduce the volume of repeated alerts, but introduces which of the following vulnerabilities?
A. An attacker, working slowly enough, can evade detection by the IDS.
B. Network packets are dropped if the volume exceeds the threshold.
C. Thresholding interferes with the IDS’ ability to reassemble fragmented packets.
D. The IDS will not distinguish among packets originating from different sources.
Which of the following is a detective control?
A. Smart card authentication
B. Security policy
C. Audit trail
D. Continuity of operations plan
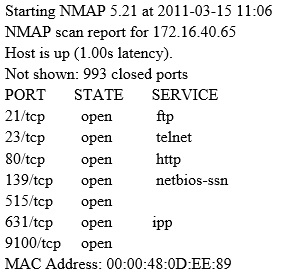
A penetration tester is conducting a port scan on a specific host. The tester found several ports opened that were confusing in concluding the Operating System (OS) version installed. Considering the NMAP result below, which of the following is likely to be installed on the target machine by the OS?
A. The host is likely a Windows machine.
B. The host is likely a Linux machine.
C. The host is likely a router.
D. The host is likely a printer.
Which of the following is the successor of SSL?
A. TLS
B. RSA
C. GRE
D. IPSec
Which security control role does encryption meet?
A. Preventative
B. Detective
C. Offensive
D. Defensive
The network administrator at Spears Technology, Inc has configured the default gateway Cisco router's access-list as below: You are hired to conduct security testing on their network. You successfully brute-force the SNMP community string using a SNMP crack tool. The access-list configured at the router prevents you from establishing a successful connection. You want to retrieve the Cisco configuration from the router. How would you proceed?
A. Use the Cisco’s TFTP default password to connect and download the configuration file
B. Run a network sniffer and capture the returned traffic with the configuration file from the router
C. Run Generic Routing Encapsulation (GRE) tunneling protocol from your computer to the router masking your IP address
D. Send a customized SNMP set request with a spoofed source IP address in the range -192.168.1.0
A company has publicly hosted web applications and an internal Intranet protected by a firewall. Which technique will help protect against enumeration?
A. Reject all invalid email received via SMTP.
B. Allow full DNS zone transfers.
C. Remove A records for internal hosts.
D. Enable null session pipes.
Which of the following conditions must be given to allow a tester to exploit a Cross-Site Request Forgery (CSRF) vulnerable web application?
A. The victim user must open the malicious link with an Internet Explorer prior to version 8.
B. The session cookies generated by the application do not have the HttpOnly flag set.
C. The victim user must open the malicious link with a Firefox prior to version 3.
D. The web application should not use random tokens.
Which of the following is a client-server tool utilized to evade firewall inspection?
A. tcp-over-dns
B. kismet
C. nikto
D. hping A
If a tester is attempting to ping a target that exists but receives no response or a response that states the destination is unreachable, ICMP may be disabled and the network may be using TCP. Which other option could the tester use to get a response from a host using TCP?
A. Hping
B. Traceroute
C. TCP ping
D. Broadcast ping A
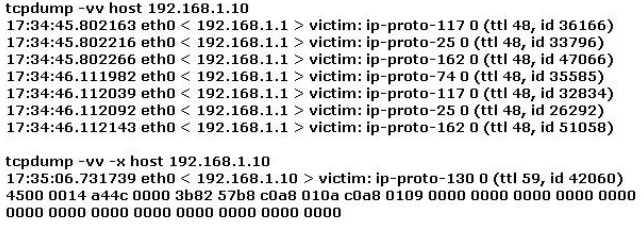
Study the log below and identify the scan type.
A. nmap -sR 192.168.1.10
B. nmap -sS 192.168.1.10
C. nmap -sV 192.168.1.10
D. nmap -sO -T 192.168.1.10
For messages sent through an insecure channel, a properly implemented digital signature gives the receiver reason to believe the message was sent by the claimed sender. While using a digital signature, the message digest is encrypted with which key?
A. Sender’s public key
B. Receiver’s private key
C. Receiver’s public key
D. Sender’s private key
Which set of access control solutions implements two-factor authentication?
A. USB token and PIN
B. Fingerprint scanner and retina scanner
C. Password and PIN
D. Account and password
Which of the following is a symmetric cryptographic standard?
A. DSA
B. PKI
C. RSA
D. 3DES
Why would an attacker want to perform a scan on port 137?
A. To discover proxy servers on a network
B. To disrupt the NetBIOS SMB service on the target host
C. To check for file and print sharing on Windows systems
D. To discover information about a target host using NBTSTAT
Advanced encryption standard is an algorithm used for which of the following?
A. Data integrity
B. Key discovery
C. Bulk data encryption
D. Key recovery C
When an alert rule is matched in a network-based IDS like snort, the IDS does which of the following?
A. Drops the packet and moves on to the next one
B. Continues to evaluate the packet until all rules are checked
C. Stops checking rules, sends an alert, and lets the packet continue
D. Blocks the connection with the source IP address in the packet
Which of the following statements is TRUE?
A. Sniffers operate on Layer 2 of the OSI model
B. Sniffers operate on Layer 3 of the OSI model
C. Sniffers operate on both Layer 2 & Layer 3 of the OSI model.
D. Sniffers operate on the Layer 1 of the OSI model.
What statement is true regarding LM hashes?
A. LM hashes consist in 48 hexadecimal characters.
B. LM hashes are based on AES128 cryptographic standard.
C. Uppercase characters in the password are converted to lowercase.
D. LM hashes are not generated when the password length exceeds 15 characters.
While doing a technical assessment to determine network vulnerabilities, you used the TCP XMAS scan. What would be the response of all open ports?
A. The port will send an ACK
B. The port will send a SYN
C. The port will ignore the packets
D. The port will send an RST
Which of the following describes the characteristics of a Boot Sector Virus?
A. Moves the MBR to another location on the RAM and copies itself to the original location of the MBR
B. Moves the MBR to another location on the hard disk and copies itself to the original location of the MBR
C. Modifies directory table entries so that directory entries point to the virus code instead of the actual program
D. Overwrites the original MBR and only executes the new virus code
Which NMAP command combination would let a tester scan every TCP port from a class C network that is blocking ICMP with fingerprinting and service detection?
A. NMAP -PN -A -O -sS 192.168.2.0/24
B. NMAP -P0 -A -O -p1-65535 192.168.0/24
C. NMAP -P0 -A -sT -p0-65535 192.168.0/16
D. NMAP -PN -O -sS -p 1-1024 192.168.0/8
Which of the following is a component of a risk assessment?
A. Physical security
B. Administrative safeguards
C. DMZ
D. Logical interface
Which of the following statements regarding ethical hacking is incorrect?
A. Ethical hackers should never use tools or methods that have the potential of exploiting vulnerabilities in an organization’s systems.
B. Testing should be remotely performed offsite.
C. An organization should use ethical hackers who do not sell vendor hardware/software or other consulting services.
D. Ethical hacking should not involve writing to or modifying the target systems.
Which of the following business challenges could be solved by using a vulnerability scanner?
A. Auditors want to discover if all systems are following a standard naming convention.
B. A web server was compromised and management needs to know if any further systems were compromised.
C. There is an emergency need to remove administrator access from multiple machines for an employee that quit.
D. There is a monthly requirement to test corporate compliance with host application usage and security policies.
During a wireless penetration test, a tester detects an access point using WPA2 encryption. Which of the following attacks should be used to obtain the key?
A. The tester must capture the WPA2 authentication handshake and then crack it.
B. The tester must use the tool inSSIDer to crack it using the ESSID of the network.
C. The tester cannot crack WPA2 because it is in full compliance with the IEEE 802.11i standard.
D. The tester must change the MAC address of the wireless network card and then use the AirTraf tool to obtain the key.
Windows LAN Manager (LM) hashes are known to be weak. Which of the following are known weaknesses of LM? (Choose three.)
A. Converts passwords to uppercase.
B. Hashes are sent in clear text over the network.
C. Makes use of only 32-bit encryption.
D. Effective length is 7 characters.
SNMP is a protocol used to query hosts, servers, and devices about performance or health status data. This protocol has long been used by hackers to gather great amount of information about remote hosts. Which of the following features makes this possible? (Choose two.)
A. It used TCP as the underlying protocol.
B. It uses community string that is transmitted in clear text.
C. It is susceptible to sniffing.
D. It is used by all network devices on the market.
How can rainbow tables be defeated?
A. Password salting
B. Use of non-dictionary words
C. All uppercase character passwords
D. Lockout accounts under brute force password cracking attempts
What technique is used to perform a Connection Stream Parameter Pollution (CSPP) attack?
A. Injecting parameters into a connection string using semicolons as a separator
B. Inserting malicious Javascript code into input parameters
C. Setting a user’s session identifier (SID) to an explicit known value
D. Adding multiple parameters with the same name in HTTP requests
What is the way to decide how a packet will move from an untrusted outside host to a protected inside that is behind a firewall, which permits the hacker to determine which ports are open and if the packets can pass through the packet-filtering of the firewall.
A. Firewalking
B. Session hijacking
C. Network sniffing
D. Man-in-the-middle attack
If there is an Intrusion Detection System (IDS) in intranet, which port scanning technique cannot be used?
A. Spoof Scan
B. TCP Connect scan
C. TCP SYN
D. Idle Scan
What type of OS fingerprinting technique sends specially crafted packets to the remote OS and analyzes the received response?
A. Passive
B. Reflective
C. Active
D. Distributive
Which of the following is considered the best way to protect Personally Identifiable Information (PII) from Web application vulnerabilities?
A. Use cryptographic storage to store all PII
B. Use encrypted communications protocols to transmit PII
C. Use full disk encryption on all hard drives to protect PII
D. Use a security token to log into all Web applications that use PII
A security policy will be more accepted by employees if it is consistent and has the support of
A. coworkers.
B. executive management.
C. the security officer.
D. a supervisor.
Which type of scan is used on the eye to measure the layer of blood vessels?
A. Facial recognition scan
B. Retinal scan
C. Iris scan
D. Signature kinetics scan
Access Full 312-50V9 Dump Free
Looking for even more practice questions? Click here to access the complete 312-50V9 Dump Free collection, offering hundreds of questions across all exam objectives.
We regularly update our content to ensure accuracy and relevance—so be sure to check back for new material.
Begin your certification journey today with our 312-50V9 dump free questions — and get one step closer to exam success!