300-630 Dump Free – 50 Practice Questions to Sharpen Your Exam Readiness.
Looking for a reliable way to prepare for your 300-630 certification? Our 300-630 Dump Free includes 50 exam-style practice questions designed to reflect real test scenarios—helping you study smarter and pass with confidence.
Using an 300-630 dump free set of questions can give you an edge in your exam prep by helping you:
- Understand the format and types of questions you’ll face
- Pinpoint weak areas and focus your study efforts
- Boost your confidence with realistic question practice
Below, you will find 50 free questions from our 300-630 Dump Free collection. These cover key topics and are structured to simulate the difficulty level of the real exam, making them a valuable tool for review or final prep.
Which mechanism is used by ACI spine switches to maintain a consistent copy of the endpoint address and location information?
A. COOP
B. ISIS
C. BD
D. OSPF
Which requirement applies to migration from Cisco NX-OS mode to Cisco ACI mode with Cisco Nexus 9000 Series Switches?
A. Pre-existing vPC topology must be removed before the migration is started
B. A permit-all contract must be used for traffic that flows inside the data center.
C. Pre-existing FCoE must be removed from the Nexus devices.
D. A minimum of five Cisco APIC appliances must be used in the data center network.
A customer plans to deploy a Cisco ACI Multi-Pod deployment. Which two features must be implemented on the IPN switches?
A. Enable BIDIR-PIM.Configure a minimum multicast range of /15.
B. Enable BIDIR-PIM.Configure a maximum multicast range of /23.
C. Configure PIM anycast RP.Configure a minimum multicast range of /23.
D. Configure PIM anycast RP.Configure a maximum multicast range of /15.
Refer to the exhibit. Which configuration mode must be selected for the VMM vSwitch Port Channel policy to avoid MAC flapping on the Cisco UCS Fls and Cisco ACI leaf switches?
A. LACP Passive
B. MAC Pinning
C. LACP Active
D. Static Channel ג€” Mode On
Refer to the exhibit. Which type of design approach is shown?
A. traditional VLAN/subnet model
B. edge-core-edge model
C. application-centric
D. network-centric
Which two actions are the Cisco best practices to configure NIC teaming load balancing for Cisco UCS B-Series blades that are connected to the Cisco ACI leaf switches? (Choose two.)
A. Create vPC+
B. Enable LACP active mode
C. Create PAgP
D. Create vPC
E. Enable MAC pinning
A customer is deploying a new application across two ACI pods that is sensitive to latency and jitter. The application sets the DSCP values of packets to AF31 and CS6, respectively. Which configuration changes must be made on the APIC to support the new application and prevent packets from being delayed or dropped between pods?
A. disable DSCP translation policy
B. align the ACI QoS levels and IPN QoS policies
C. disable DSCP mapping on the IPN devices
D. align the custom QoS policy on the EPG site in the customer tenant
What is a characteristic of a stretched bridge domain solution between Cisco ACI sites with Layer 2 flood disabled?
A. The application profile that is associated to the bridge domain have local significance in each site.
B. The tenant and VRF that associated to the bridge domain have local significance in each site.
C. Headend replication is used for BUM traffic between sites.
D. IP mobility is ensured between sites for disaster recovery.
Which two actions should be taken to ensure a scalable solution when multiple EPGs in a VRF require unrestricted communication? (Choose two.)
A. Configure a taboo contract between the EPGs that require unrestricted communication between each other.
B. Enable Preferred Group Member under the EPG Collection for VRF section.
C. Set the VRF policy control enforcement preference to Unenforced.
D. Set the EPGs that require unrestricted communication between each other as preferred group members.
E. Set the EPGs that require policy enforcement between each other as preferred group members.
Refer to the exhibit. A customer experiences resource overconsumption on one of its border leaf switches. Which action should be taken to reduce the consumption on this switch?
A. Disable VRF Policy Control Enforcement
B. Disable IP Data Plane Learning
C. Migrate L3Outs to another switch
D. Disable Remote EP Learning
An engineer is configuring a Cisco ACI fabric and requires a shared L3Out network connectivity to external networks. The connectivity must be shared between different tenants. Which tenant type must be created to meet this requirement?
A. common tenant
B. infra tenant
C. management tenant
D. user tenant
What is the purpose of enabling ARP flooding when VMs are migrated from a pre-existing network to Cisco ACI and their gateways remain configured in the legacy setup?
A. to avoid endpoint flapping between the legacy network and the ACI fabric
B. to prevent VMs from communicating with physical servers within the ACI fabric
C. to allow communication between VMs and silent hosts
D. to allow VMs to communicate with devices outside of their subnet
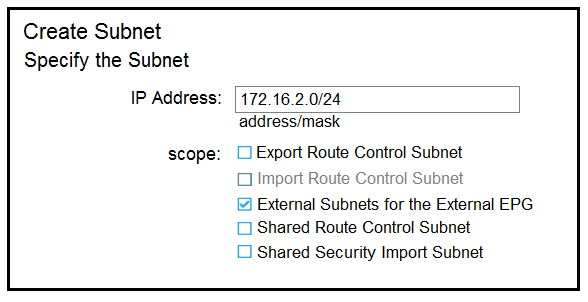
Refer to the exhibit. Which configuration must be implemented on L3Out EBGP to advertise out of the fabric 172.16.2.0/24 network that is learned from L3Out OSPF? A.
B.
C.
D.
What is the purpose of the Forwarding Tag (FTAG) in Cisco ACI?
A. FTAG is used in Cisco ACI to add a label to the iVXLAN traffic in the fabric to apply the correct policy.
B. FTAG is used in Cisco ACI to add a label to the VXLAN traffic in the fabric to apply the correct policy.
C. FTAG trees in Cisco ACI are used to load balance unicast traffic.
D. FTAG trees in Cisco ACI are used to load balance mutli-destination traffic.
Where are STP BPDUs flooded in Cisco ACI fabric?
A. in the bridge domain VLAN
B. in the native VLAN ID
C. in the access encapsulation VLAN part of different VLAN pools
D. in the VNID that is assigned to the FD VLAN
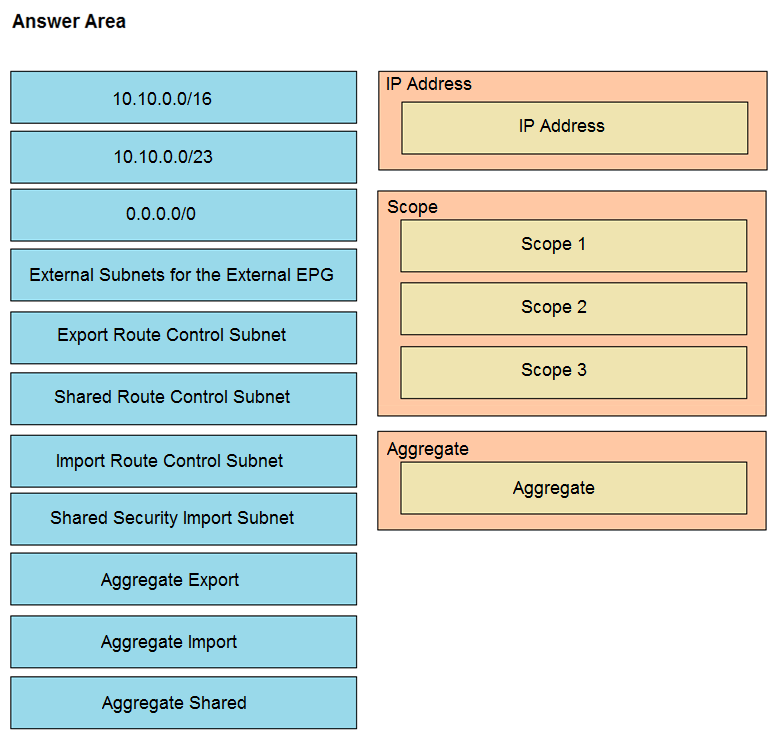
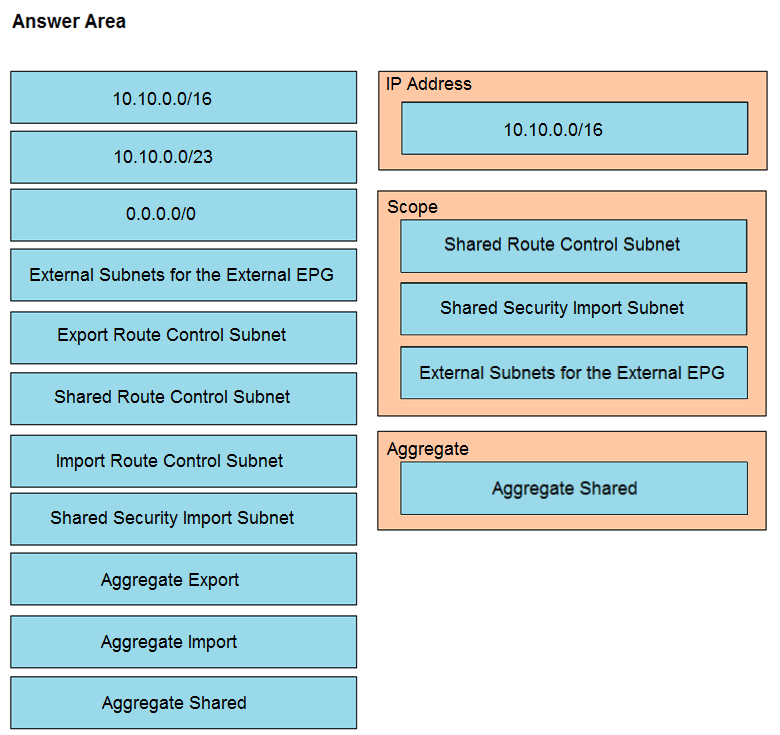
DRAG DROP -Refer to the exhibit. Drag and drop the subnets and flags from the left into the External Network Instance Profile policies on the right to create a setup that advertises only 10.10.0.0/24 and 10.10.1.0/24 prefixes in VRF1 and establishes connectivity between VRFs. Not all options are used. Select and Place:
Refer to the exhibit. Which two sets of actions must be taken to permit subnet 192.168.1.0/24 to communicate with subnet 172.18.1.0/24 using Cisco ACI fabric? (Choose two.)
A. Configure 192.168.1.0/24 with scope Export Route Control subnet under L3out_B.Configure 192.168.1.0/24 with scope External subnet for external EPG under L3out_A.
B. Configure 172.18.1.0/24 with scope External subnet for external EPG under L3out_A.Configure 192.168.1.0/24 with scope External subnet for external EPG under L3out_B.
C. Configure 172.18.1.0/24 with scope Export Route Control subnet under L3out_AConfigure 172.18.1.0/24 with scope External subnet for external EPG under L3out_B.
D. Configure 172.18.1.0/24 with scope Export Route Control subnet under L3out_B.Configure 192.168.1.0/24 with scope External subnet for external EPG under L3out_A.
E. Configure 192.168.1.0/24 with scope Export Route Control subnet under L3out_A.Configure 172.18.1.0/24 with scope External subnet for external EPG under L3out_ B.
Refer to the exhibit. The requirement is to prefer the local PBR node and redirect the traffic to the remote pod PBR node in the case of catastrophic node failure. Which configuration meets these requirements?
A. location-based PBRhost route advertisementresilient hashing
B. symmetric PBRlocation-based PBRresilient hashing
C. symmetric PBRunidirectional PBRresilient hashing
D. location-based PBRhost route advertisementnode tracking
An engineer implements the Cisco ACI solution and needs to confirm that the leaf switch correctly learns the remote endpoint MAC. Which information must be included in the VXLAN packet that is received from the Cisco ACI spine for the Cisco ACI leaf to learn MAC as a remote endpoint?
A. VRF
B. application profile
C. bridge domain
D. EPG
Refer to the exhibit. The 0.0.0.0/0 is configured as a default static route on L3Out-1. Which action should be taken for the 0.0.0.0/0 prefix to advertise out on L3Out-2 OSPF?
A. Enable Shared Security Import Subnet
B. Enable Aggregate Export Subnet
C. Enable Shared Route Control Subnet
D. Enable Export Route Control Subnet
An engineer must implement an L3Out within a tenant to allow the reachability to services outside of the Cisco ACI fabric. The requirement is to allow communication from the EPGs in the same VRF to the external services and save TCAM resource utilization. Which contract insertion method must be used to meet these requirements?
A. Provider: each service EPGs -Consumer: vzAny inside the VRF
B. Provider: each service EPGs -Consumer: L3Out external EPGs
C. Provider: L3Out external EPGs -Consumer: each service EPGs
D. Provider: L3Out external EPGs -Consumer: vzAny inside VRF
Refer to the exhibit. Which two configuration steps are required in ISN for Cisco ACI Multi-Site setup? (Choose two.)
A. Connect Spine2 to ISN routers.
B. Configure BIDIR-PIM throughout the ISN
C. Increase ISN MTU to support the maximum MTU that is sent by endpoints
D. Configure OSPF between spines and ISN routers
E. Enable IGMPv3 on ISN routers
A cloud provider must make a pair of firewalls available to all tenants. Each tenant defines its own service graph. Where should the Layer 4 to Layer 7 service be configured to accomplish this goal?
A. management tenant
B. infrastructure tenant
C. user tenant
D. common tenant
Refer to the exhibit. An engineer must implement a solution to ensure that ingress and egress traffic flows are symmetric for all stretched bridge domains in the customer multisite architecture. Which configuration accomplishes this goal?
A. Configure host route advertisement on the bridge domains.
B. Enable anycast services to the firewalls in both fabrics.
C. Implement a policy-based redirect using a service graph.
D. Add a new stretched external EPG to the existing L3Outs.
A network engineer configured an active-active firewall cluster that is stretched across separate pods in the Cisco ACI fabric. Which two implementation setups for anycast services are available? (Choose two.)
A. Modify the Cisco ACI contract scope
B. Modify the MAC address on the second firewall
C. Configure the firewalls behind an EPG subnet
D. Deselect No Default SVI Gateway under EPG Subnet
E. Deploy a Layer 4 to Layer 7 service graph with PBR
Refer to the exhibit. Which two configurations enable inter-VRF communication? (Choose two.)
A. Set the subnet scope to Shared Between VRFs
B. Enable Advertise Externally under the subnet scope
C. Change the contract scope to Tenant
D. Change the subject scope to VRF
E. Export the contract and import as a contract interface
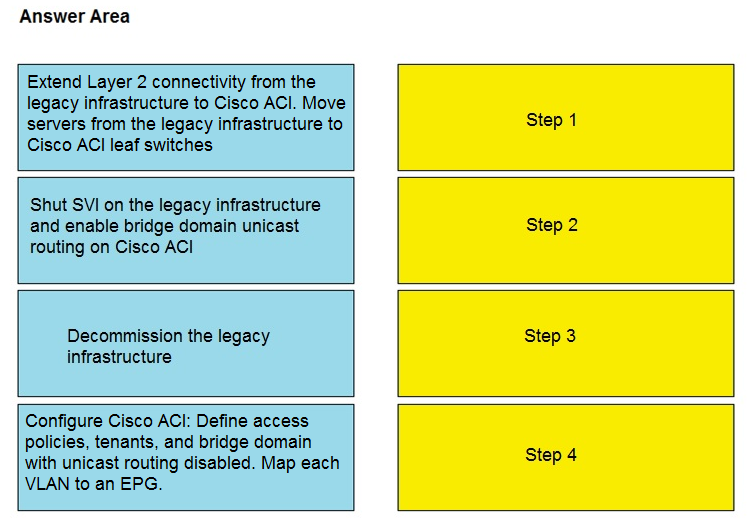
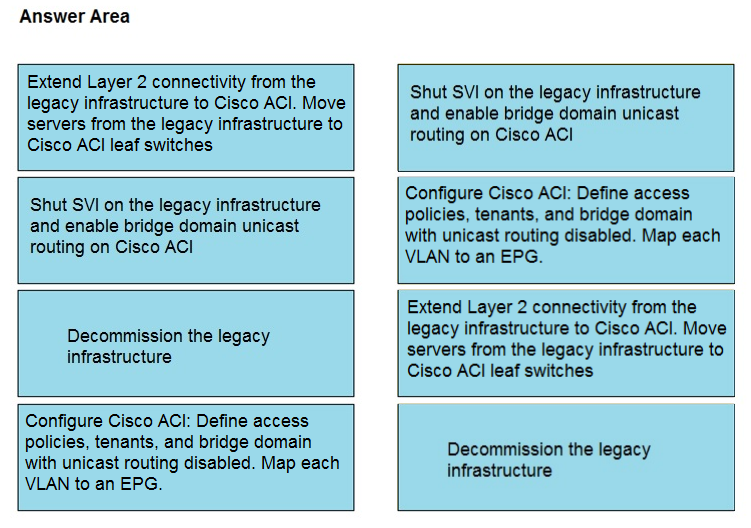
DRAG DROP - An engineer must migrate servers from a legacy data center infrastructure to a Cisco ACI fabric. Drag and drop the steps from the left into the order that they must be completed on the right to ensure the least amount of downtime. Select and Place:
Refer to the exhibit. An engineer extends a Cisco ACI Multi-Pod setup to a Cisco ACI Multi-Site implementation. Which action allows the interconnection?
A. Configure BIDIR-PIM in the IPN and ISN
B. Use dedicated uplinks on Site 1 spines for ISN connections
C. Connect all spines to the IPN and ISN
D. Filter the advertisement of the Site 2 TEP pool into the IPN

Refer to the exhibits. Which subject must be configured for the All_noSSH contract to allow all IP traffic except SSH between the two EPGs? A.
B.
C.
D.
An engineer created a Cisco ACI environment in which multiple tenants reuse the same contract. The requirement is to prevent inter-tenant communication. Which action meets this requirement?
A. Create the contract in the user tenant with the scope set to VRF and exported to other tenants
B. Create the contract in the common tenant with the scope set to Tenant
C. Create the contract in the user tenant with the scope set to Global and exported to other tenants
D. Create the contract in the common tenant with the scope set to Global
Refer to the exhibit. An administrator configures inter-VRF route leaking between Production:vrf-prod and Non-Production:vrf-nonprod. However, the route in the Non-Production:vrf-nonprod VRF to the production tenant is missing. Which action resolves the VRF route leaking issue?
A. Enable the Shared between VRFs option for the BD subnet in the production VRF.
B. Change the contract scope to Global.
C. Enable the Shared between VRFs option for the EPG subnet in the non-production VRF.
D. Export the contract from provider to consumer tenant.
An engineer must limit local and remote endpoint learning to the bridge domain subnet. Which action should be taken inside the Cisco APIC?
A. Disable Remote EP Learn
B. Enable Enforce Subnet Check
C. Disable Endpoint Dataplane Learning
D. Enable Limit IP Learning to Subnet
Refer to the exhibit. In a Cisco ACI Multi-Site deployment, traffic fails to pass between Site-A and Site-B, and an engineer troubleshoots the link between ISN-01 and Node-201. Which set of actions establishes connectivity?
A. Configure the MTU on the link to be at least 1000 bytes larger than the MTU of the ACI fabrics.Configure the link as a routed subinterface by using VLAN-4.
B. Configure the MTU on the link to be at least 100 bytes larger than the MTU of the ACI fabrics.Configure the link as an access interface by using VLAN-4.
C. Configure the MTU on the link to be at least 100 bytes larger than the MTU of the ACI fabrics.Configure the link as a routed subinterface by using VLAN-4.
D. Configure the MTU on the link to be at least 1000 bytes larger than the MTU of the ACI fabrics.Configure the link as an access interface by using VLAN-4.
Refer to the exhibit. The external subnet and internal EPG1 must communicate with each other, and the L3Out traffic must leak into the VRF named “VF1”. Which configuration set accomplishes these goals?
A. External Subnets for External EPGImport Route Control Subnet -Shared Route Control Subnet
B. External Subnets for External EPGShared Route Control Subnet -Shared Security Import Subnet
C. Export Route Control Subnet -Shared Security Import Subnet -Aggregate Shared Routes
D. Export Route Control Subnet -Import Route Control Subnet -Aggregate Shared Routes
Which two components must be configured as stretched to establish intra-VRF communication between two EPGs that are deployed in different sites and different bridge domains? (Choose two.)
A. contract
B. tenant
C. application profile
D. bridge domain
E. EPG
An engineer configures a new Cisco ACI Multi-Site Orchestrator node to join an MSO cluster. Which two components are necessary to ensure that the new node has IP connectivity in this configuration? (Choose two.)
A. Cisco ACI spine interfaces that are connected to ISN
B. Cisco APICs over the OOB management network
C. existing Cisco ACI Multi-Site Orchestrator node
D. management IP of ESXi hosts where the controllers are deployed
E. OOB interface of ISN
Which protocol must be applied between the inter-pod network and spines within each pod to allow broadcast traffic replication between Cisco ACI pods?
A. MSDP Peering
B. Multicast BGP
C. Bidirectional PIM
D. IGMP Registration
Refer to the exhibit. An engineer is configuring a vSwitch policy in the existing Cisco ACI fabric. The requirement is for the Cisco ACI leaf to learn individual MAC addresses from the same physical port. Which vSwitch policy configuration mode must be enabled to meet this requirement?
A. MAC pinning
B. MAC binding
C. LACP passive
D. LACP active
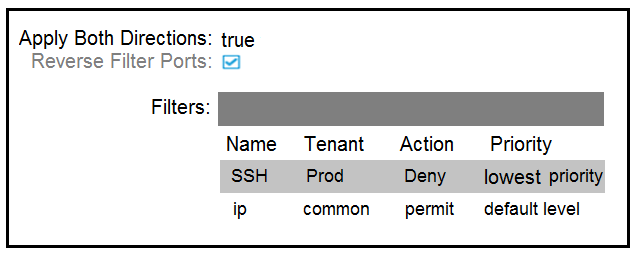
Refer to the exhibit. Which configuration set must be applied to filter 1 to enable SSH communication between Web_EPG to App_EPG?
A. Apply Both Directions: Disabled -Reverse Filter Ports: Enabled
B. Apply Both Directions: Enabled -Reverse Filter Ports: Enabled
C. Apply Both Directions: Disabled -Reverse Filter Ports: Disabled
D. Apply Both Directions: Enabled -Reverse Filter Ports: Disabled
What are two characteristics of Cisco ACI and Spanning Tree Protocol interaction? (Choose two.)
A. When a TCN BPDU is received in a VLAN, Cisco ACI flushes the endpoints for the associated encapsulation.
B. STP BPDUs are dropped due to MCP.
C. MST BPDUs are flooded correctly in Cisco ACI fabric without additional configuration.
D. BPDU filter and BPDU guard can be configured on Cisco ACI leaf edge ports.
E. Cisco ACI must be configured as the STP root for all VLANs.
The engineer notices frequent MAC and IP address moves between different leaf switch ports. Which action prevents this problem from occurring?
A. Disable enforce subnet check.
B. Disable IP bridge domain enforcement.
C. Enable endpoint loop protection.
D. Enable rogue endpoint control.
An engineer is deploying a Cisco ACI fabric and discovers that the traffic to certain endpoints is dropped. The originating bridge domain is configured with hardware proxy. Which action prevents this problem?
A. Set the L2 Unknown Unicast option to Flood for Layer 2 switched traffic.
B. Set the L2 Unknown Unicast option to Hardware-Proxy for Layer 2 switched traffic.
C. Enable the ARP Flooding option under the bridge domain for Layer 3 routed traffic.
D. Disable the ARP Flooding option under the bridge domain for Layer 3 routed traffic.
An engineer deployed a Cisco ACI fabric and noticed that the fabric learns endpoints from subnets that are not configured on a bridge domain. To meet strict security requirements, the engineer must prevent this behavior. Which action must be taken to prevent this behavior?
A. Activate Enable Data Plane Endpoint Learning
B. Implement Pervasive Gateway
C. Configure Static Binding
D. Enable Enforce Subnet Check
As part of a newly deployed ACI fabric, a pair of border leaf switches have been deployed to provide shared services for all tenants. The configured L3Out runs OSPF as the routing protocol. The requirement is to advertise the routes from the border leaf switches to the compute leaf switches. Which configuration must be implemented to meet these requirements?
A. Configure a BGP route reflector policy for the Cisco ACI pod
B. Define the shared L3Out in the common tenant
C. Enable Import Route Control Enforcement in the L3Out policy
D. Define the consumer subnet under the consumer EPG
An engineer configures Cisco ACI Multi-Site and must specify the control plane TEP IP for spines. Which statement describes control plane TEP IP in this situation?
A. The unique IP address is defined on each spine node that belongs to a fabric and is used to establish MP-BGP EVPN and VPNv4 adjacencies with the spine nodes in remote sites.
B. The unique IP address is defined on each spine node that belongs to a fabric and is used to establish VXLAN adjacencies with the spine nodes in remote sites.
C. The common anycast address is shared by all the spine nodes in the same site and is used to perform headend replication for BUM traffic.
D. The common anycast address is shared by all the spine nodes at the same site and is used to source and receive unicast VXLAN data plane traffic.
Which device replicates Broadcast, Unicast, and Multicast (BUM) frames to all remote sites in a Cisco ACI Multi-Site with multiple stretched bridge domains?
A. remote spine node that translates the VNID to the locally significant value
B. receiving leaf that learns the location for the sourced BUM traffic
C. source leaf that floods the traffic to the specific multicast group or GIPo
D. local spine that is elected the designated forwarder for each bridge domain
Refer to the exhibit. How are the STP BPDUs forwarded over Cisco ACI fabric?
A. STP BPDUs that are generated by Switch2 are received by Switch1 and Switch3.
B. Cisco ACI fabric drops all STP BPDUs that are generated by the external switches.
C. Cisco ACI acts as the STP root for all three external switches.
D. STP BPDUs that are generated by Switch1 are received only by Switch3.
An organization expands a Cisco ACI Multi-Pod from two to six pods and must ensure that the control plane scales. What should be configured in the IPN to ensure that BUM traffic is forwarded efficiently across the IPN?
A. spine headend replication
B. BIDIR-PIM
C. MP-BGP
D. MSDP
Refer to the exhibit. Between Cisco UCS Fls and Cisco ACI leaf switches, CDP is disabled, the LLDP is enabled, and LACP is in Active mode. Which two discovery protocols and load-balancing mechanism combinations can be implemented for the DVS? (Choose two.)
A. CDP enabled, LLDP disabled, and LACP Active
B. CDP disabled, LLDP enabled, and MAC Pinning
C. CDP enabled, LLDP disabled, and MAC Pinning
D. CDP enabled, LLDP enabled, and LACP Active
E. CDP enabled, LLDP disabled, and LACP Passive
F. CDP disabled, LLDP enabled, and LACP Passive
What is a use of the Overlay Multicast TEP in Cisco ACI Multi-Site communication?
A. to perform headend replication
B. to act as the source IP for BUM traffic
C. to establish MP-BGP adjacencies with remote spines
D. to send and receive unicast VXLAN data plane traffic
Access Full 300-630 Dump Free
Looking for even more practice questions? Click here to access the complete 300-630 Dump Free collection, offering hundreds of questions across all exam objectives.
We regularly update our content to ensure accuracy and relevance—so be sure to check back for new material.
Begin your certification journey today with our 300-630 dump free questions — and get one step closer to exam success!