200-201 Dump Free – 50 Practice Questions to Sharpen Your Exam Readiness.
Looking for a reliable way to prepare for your 200-201 certification? Our 200-201 Dump Free includes 50 exam-style practice questions designed to reflect real test scenarios—helping you study smarter and pass with confidence.
Using an 200-201 dump free set of questions can give you an edge in your exam prep by helping you:
- Understand the format and types of questions you’ll face
- Pinpoint weak areas and focus your study efforts
- Boost your confidence with realistic question practice
Below, you will find 50 free questions from our 200-201 Dump Free collection. These cover key topics and are structured to simulate the difficulty level of the real exam, making them a valuable tool for review or final prep.
What is a difference between inline traffic interrogation and traffic mirroring?
A. Inline inspection acts on the original traffic data flow
B. Traffic mirroring passes live traffic to a tool for blocking
C. Traffic mirroring inspects live traffic for analysis and mitigation
D. Inline traffic copies packets for analysis and security
What are two social engineering techniques? (Choose two.)
A. privilege escalation
B. DDoS attack
C. phishing
D. man-in-the-middle
E. pharming
Which system monitors local system operation and local network access for violations of a security policy?
A. host-based intrusion detection
B. systems-based sandboxing
C. host-based firewall
D. antivirus
What is a difference between SIEM and SOAR?
A. SIEM predicts and prevents security alerts, while SOAR checks attack patterns and applies the mitigation.
B. SIEM’s primary function is to collect and detect anomalies, while SOAR is more focused on security operations automation and response.
C. SOAR’s primary function is to collect and detect anomalies, while SIEM is more focused on security operations automation and response.
D. SOAR predicts and prevents security alerts, while SIEM checks attack patterns and applies the mitigation.
What is a sandbox interprocess communication service?
A. A collection of rules within the sandbox that prevent the communication between sandboxes.
B. A collection of network services that are activated on an interface, allowing for inter-port communication.
C. A collection of interfaces that allow for coordination of activities among processes.
D. A collection of host services that allow for communication between sandboxes.
Refer to the exhibit. Which field contains DNS header information if the payload is a query or response?
A. ID
B. Z
C. QR
D. TC
An engineer is investigating a case of the unauthorized usage of the `Tcpdump` tool. The analysis revealed that a malicious insider attempted to sniff traffic on a specific interface. What type of information did the malicious insider attempt to obtain?
A. tagged protocols being used on the network
B. all firewall alerts and resulting mitigations
C. tagged ports being used on the network
D. all information and data within the datagram
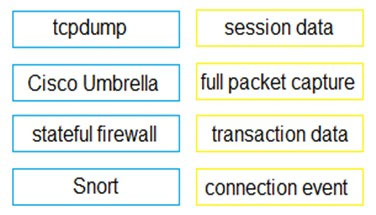
DRAG DROP - Drag and drop the technology on the left onto the data type the technology provides on the right. Select and Place:
Which filter allows an engineer to filter traffic in Wireshark to further analyze the PCAP file by only showing the traffic for LAN 10.11.x.x, between workstations and servers without the Internet?
A. src=10.11.0.0/16 and dst=10.11.0.0/16
B. ip.src==10.11.0.0/16 and ip.dst==10.11.0.0/16
C. ip.src=10.11.0.0/16 and ip.dst=10.11.0.0/16
D. src==10.11.0.0/16 and dst==10.11.0.0/16
Refer to the exhibit. Which application protocol is in this PCAP file?
A. SSH
B. TCP
C. TLS
D. HTTP
An engineer needs to fetch logs from a proxy server and generate actual events according to the data received. Which technology should the engineer use to accomplish this task?
A. Firepower
B. Email Security Appliance
C. Web Security Appliance
D. Stealthwatch
According to the NIST SP 800-86, which two types of data are considered volatile? (Choose two.)
A. temporary files
B. login sessions
C. swap files
D. dump files
E. free space
An organization that develops high-end technology is going through an internal audit. The organization uses two databases. The main database stores patent information and a secondary database stores employee names and contact information. A compliance team is asked to analyze the infrastructure and identify protected data. Which two types of protected data should be identified? (Choose two.)
A. Payment Card Industry (PCI)
B. Sarbanes-Oxley (SOX)
C. Intellectual Property (IP)
D. Protected Health Information (PHI)
E. Personally Identifiable Information (PII)
What are two denial-of-service (DoS) attacks? (Choose two.)
A. port scan
B. phishing
C. man-in-the-middle
D. teardrop
E. SYN flood
Which CVSS metric group identifies other components that are affected by a successful security attack?
A. scope
B. privileges required
C. integrity
D. attack vendor
Which regular expression matches "color" and "colour"?
A. colo?ur
B. col[0גˆ’8]+our
C. colou?r
D. col[0גˆ’9]+our
DRAG DROP -Refer to the exhibit. Drag and drop the element names from the left onto the corresponding pieces of the PCAP file on the right.
Refer to the exhibit. Which type of log is displayed?
A. IDS
B. proxy
C. NetFlow
D. sys
Refer to the exhibit. What does this Cuckoo sandbox report indicate?
A. The file is ransomware.
B. The file is spyware.
C. The file will open unsecure ports when executed.
D. The file will open a command interpreter when executed.
Refer to the exhibit. In which Linux log file is this output found?
A. /var/log/authorization.log
B. /var/log/dmesg
C. var/log/var.log
D. /var/log/auth.log
What is the difference between deep packet inspection and stateful inspection?
A. Stateful inspection is more secure due to its complex signatures, and deep packet inspection requires less human intervention.
B. Deep packet inspection is more secure due to its complex signatures, and stateful inspection requires less human intervention.
C. Deep packet inspection gives insights up to Layer 7, and stateful inspection gives insights only up to Layer 4.
D. Stateful inspection verifies data at the transport layer, and deep packet inspection verifies data at the application layer.
Refer to the exhibit. A company's user HTTP connection to a malicious site was blocked according to configured policy. What is the source technology used for this measure?
A. network application control
B. firewall
C. IPS
D. web proxy
Refer to the exhibit. Which technology generates this log?
A. NetFlow
B. IDS
C. web proxy
D. firewall
Which security model assumes an attacker within and outside of the network and enforces strict verification before connecting to any system or resource within the organization?
A. Take-Grant
B. Object-capability
C. Zero Trust
D. Biba
Which of these describes volatile evidence?
A. logs
B. registers and cache
C. disk and removable drives
D. usernames
What are two differences in how tampered and untampered disk images affect a security incident? (Choose two.)
A. Tampered images are used in the security investigation process.
B. Tampered images are used in the incident recovery process.
C. The image is tampered if the stored hash and the computed hash match.
D. Untampered images are used in the security investigation process.
E. The image is untampered if the stored hash and the computed hash match.
What describes a buffer overflow attack?
A. suppressing the buffers in a process
B. injecting new commands into existing buffers
C. overloading a predefined amount of memory
D. fetching data from memory buffer registers
At which layer is deep packet inspection investigated on a firewall?
A. internet
B. transport
C. application
D. data link
What is personally identifiable information that must be safeguarded from unauthorized access?
A. date of birth
B. driver’s license number
C. gender
D. zip code
How does an attack surface differ from an attack vector?
A. An attack vector recognizes the potential outcomes of an attack, and the attack surface is choosing a method of an attack.
B. An attack vector matches components that can be exploited, and an attack surface classifies the potential path for exploitation.
C. An attack surface mitigates external vulnerabilities, and an attack vector identifies mitigation techniques and possible workarounds.
D. An attack surface identifies vulnerable parts for an attack, and an attack vector specifies which attacks are feasible to those parts.
An organization has recently adjusted its security stance in response to online threats made by a known hacktivist group. What is the initial event called in the NIST SP800-61?
A. online assault
B. precursor
C. trigger
D. instigator
Which event is user interaction?
A. gaining root access
B. executing remote code
C. reading and writing file permission
D. opening a malicious file
DRAG DROP - Cisco’s Zero Trust Architecture simplifies the Zero Trust journey into three critical areas. Drag the definitions onto the graphic to describe Zero Trust from the Cisco perspective
Refer to the exhibit. A security analyst received a ticket about suspicious traffic from one of the workstations. During the investigation, the analyst discovered that the workstation is communicating with an external IP The analyst was not able to investigate further and escalated the case to a T2 security analyst. What are the two data visibility challenges that the security analyst should identify? (Choose two.)
A. A default user agent is present in the headers.
B. Traffic is not encrypted.
C. Encrypted data is being transmitted.
D. POST requests have a “Microsoft-IIS/7.5” server header.
E. HTTP requests and responses are sent in plaintext.
A user received a malicious email attachment named "DS045-report1122345.exe" and executed it. In which step of the Cyber Kill Chain is this event?
A. reconnaissance
B. delivery
C. weaponization
D. installation
Refer to the exhibit. What should be interpreted from this packet capture?
A. 81.179.179.69 is sending a packet from port 80 to port 50272 of IP address 192.168.122.100 using UDP protocol.
B. 192.168.122.100 is sending a packet from port 50272 to port 80 of IP address 81.179.179.69 using TCP protocol.
C. 192.168.122.100 is sending a packet from port 80 to port 50272 of IP address 81.179.179.69 using UDP protocol.
D. 81.179.179.69 is sending a packet from port 50272 to port 80 of IP address 192.168.122.100 using TCP protocol.
A security specialist notices 100 HTTP GET and POST requests for multiple pages on the web servers. The agent in the requests contains PHP code that, if executed, creates and writes to a new PHP file on the webserver. Which event category is described?
A. reconnaissance
B. action on objectives
C. installation
D. exploitation
Which event artifact is used to identify HTTP GET requests for a specific file?
A. destination IP address
B. TCP ACK
C. HTTP status code
D. URI
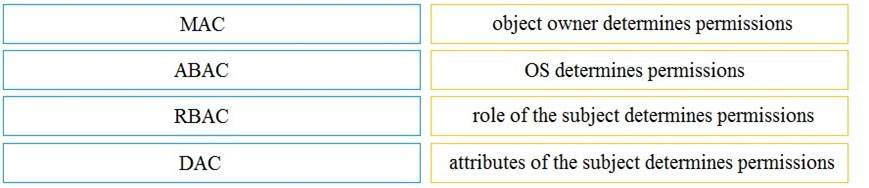
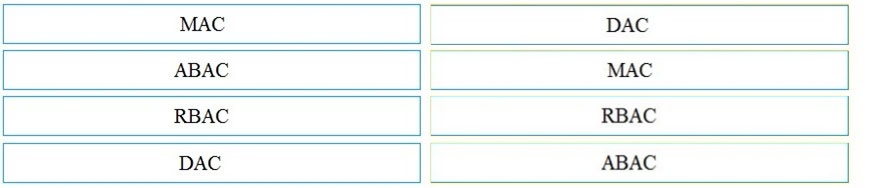
DRAG DROP - Drag and drop the access control models from the left onto its corresponding descriptions on the right. Select and Place:
What describes the concept of data consistently and readily being accessible for legitimate users?
A. accessibility
B. availability
C. integrity
D. confidentiality
Which tool gives the ability to see session data in real time?
A. tcpdstat
B. trafdump
C. trafshow
D. tcptrace
What are the two differences between vulnerability and exploit? (Choose two.)
A. Vulnerabilities can be found in hardware and software, and exploits can be used only for software-based vulnerabilities.
B. Zero-day exploit can be used to take advantage of a vulnerability until the vulnerable software or hardware is patched.
C. Known vulnerabilities are assigned special CVE numbers, and exploits are using process to take advantage of vulnerabilities.
D. Zero-day exploit can be used for taking advantage of a known vulnerability, and cyber-attack can be performed on company assets.
E. Vulnerabilities are usually populated in the dark web, and exploit tools and methods can be found in the public web.
What is the difference between inline traffic interrogation and traffic mirroring?
A. Inline replicates the traffic to preserve integrity rather than modifying packets before sending them to other analysis tools.
B. Traffic mirroring results in faster traffic analysis and inline is considerably slower due to latency.
C. Inline interrogation is less complex as traffic mirroring applies additional tags to data.
D. Traffic mirroring copies the traffic rather than forwarding it directly to the analysis tools.
What is the impact of encryption?
A. Data is unaltered and its integrity is preserved.
B. Data is accessible and available to permitted individuals.
C. Confidentiality of the data is kept secure and permissions are validated.
D. Data is secure and unreadable without decrypting it.
Which data type is necessary to get information about source/destination ports?
A. statistical data
B. session data
C. alert data
D. connectivity data
A threat actor penetrated an organization's network. Using the 5-tuple approach, which data points should the analyst use to isolate the compromised host in a grouped set of logs?
A. event name, log source, time, source IP, and username
B. event name, log source, time, source IP, and host name
C. protocol, log source, source IP, destination IP, and host name
D. protocol, source IP, source port destination IP, and destination port
Which metric is used to capture the level of access needed to launch a successful attack?
A. privileges required
B. user interaction
C. attack complexity
D. attack vector
Refer to the exhibit. Which attack is being attempted against a web application?
A. command injection
B. man-in-the-middle
C. denial of service
D. SQL injection
Which type of access control depends on the job function of the user?
A. role-based access control
B. rule-based access control
C. nondiscretionary access control
D. discretionary access control
Which two components reduce the attack surface on an endpoint? (Choose two.)
A. secure boot
B. load balancing
C. increased audit log levels
D. restricting USB ports
E. full packet captures at the endpoint
Access Full 200-201 Dump Free
Looking for even more practice questions? Click here to access the complete 200-201 Dump Free collection, offering hundreds of questions across all exam objectives.
We regularly update our content to ensure accuracy and relevance—so be sure to check back for new material.
Begin your certification journey today with our 200-201 dump free questions — and get one step closer to exam success!