XK0-004 Exam Prep Free – 50 Practice Questions to Get You Ready for Exam Day
Getting ready for the XK0-004 certification? Our XK0-004 Exam Prep Free resource includes 50 exam-style questions designed to help you practice effectively and feel confident on test day
Effective XK0-004 exam prep free is the key to success. With our free practice questions, you can:
- Get familiar with exam format and question style
- Identify which topics you’ve mastered—and which need more review
- Boost your confidence and reduce exam anxiety
Below, you will find 50 realistic XK0-004 Exam Prep Free questions that cover key exam topics. These questions are designed to reflect the structure and challenge level of the actual exam, making them perfect for your study routine.
A systems administrator is enabling quotas on the /home directory of a Linux server. The administrator makes the appropriate edits to the /etc/fstab file and attempts to issue the commands to enable quotas on the desired directory. However, the administrator receives an error message stating the filesystem does not support quotas. Which of the following commands should the administrator perform to proceed?
A. mount ג€”o remount /home
B. quotacheck -cg
C. edquota /home
D. quotaon /home
An administrator received a request from a security officer to eliminate a blacklisting set called internal-blocked the company is using in the iptables firewall. Which of the following commands will complete the task?
A. ipset swap internal-blocked none
B. ipset destroy internal-blocked
C. ipset del internal-blocked
D. ipset remove internal-blocked
An administrator has a CSV file named hosts.csv. The contents of hosts.csv include the following: 192.168.2.57,lnx1prd.example.com,Linux,Production 192.168.2.58,lnx2prd.example.com,Linux,Production 192.168.1.4,server15.example.com,Windows,Development The administrator needs to create a second comma-separated list of only the Linux server IP addresses. Which of the following commands would achieve this need?
A. for ip in $(grep ג€Linuxג€ hosts.csv | cut ג€”dג€,ג€ ג€”f1); do echo ג€”n ג€$ip,ג€; done
B. for ip in $( cut ג€”dג€,ג€ ג€”f1 hosts.csv | grep ג€Linuxג€); do echo ג€”n ג€$ip,ג€; done
C. for ip in $(grep ג€Linuxג€ hosts.csv | sed ג€/$1//’); do echo ג€”n ג€$ip,ג€; done
D. for ip in $(awk ג€”F, ‘{print $1}’ hosts.csv | grep ג€Linuxג€); do echo ג€”n ג€$ip,ג€; done
While creating a file on a volume, the Linux administrator receives the following message: No space left on device. Running the df `"m command, the administrator notes there is still 50% of usage left. Which of the following is the NEXT step the administrator should take to analyze the issue without losing data?
A. Run the df ג€”i command and notice the inode exhaustion
B. Run the df ג€”h command and notice the space exhaustion
C. Run the df ג€”B command and notice the block size
D. Run the df ג€”k command and notice the storage exhaustion
A Linux user wants to know the type A records for the domain foo.com. Which of the following commands will accomplish this task?
A. dig type A domain foo.com
B. nslookup set a foo.com
C. nslookup set q A foo.com
D. dig A foo.com
Which of the following commands would show the default printer on a Linux system?
A. lpr
B. lpq
C. lpstat
D. lspci
A junior Linux administrator receives a request to add a user, Ann, to the secondary group `cashiers`. Ann is also a member of the secondary group, `managers`. The administrator issues the following command: usermod -G cashiers Ann Later, Ann reports that she is unable to access any of the files or directories in `managers`. Which of the following commands should the administrator issue to resolve Ann's group memberships?
A. usermod -G cashiers,managers Ann
B. usermod -g cashiers,managers Ann
C. groupmod -G Ann cashiers,managers
D. groupmod -ga Ann cashiers,managers
A user needs to modify the IP address of a laptop. Which of the following files can be used to configure the network interface named eth0?
A. /etc/sysconfig/network/interfaces.cnf
B. /system/config/interfaces
C. /etc/sysconfig/network-scripts/ifcfg-eth0
D. /system/networking/ifconfig
E. /etc/interfaces/eth0.conf
A Linux system is running normally when the systems administrator receives an alert that one application spawned many processes. The application is consuming a lot of memory, and it will soon cause the machine to become unresponsive. Which of the following commands will stop each application process?
A. kill `pidof application`
B. killall application
C. kill -9 `ps ג€”aux | grep application`
D. pkill -9 application
A Linux administrator needs to switch from text mode to GUI. Which of the following runlevels will start the GUI by default?
A. Runlevel 3
B. Runlevel 4
C. Runlevel 5
D. Runlevel 6
A systems administrator received a request to change the hostname to a new name. Which of the following file configurations should be changed to fix the hostname in the server?
A. /etc/sysconfig/network
B. /etc/hosts
C. /etc/resolv.conf
D. /etc/sysconfig/nsswitch.conf
A systems administrator wants to increase the existing drive space on a Linux server with a software RAID. After physically adding the new drive to the system, and then adding the drive to the RAID array, the administrator notices the available drive space has not increased. A status of the array shows the new drive and the original storage space: md0 : active Raid sdd1[3]S sdc1[2] sdb1[1] sda1[0] 954585654 blocks level5 64K chunk algorithm 2 [3/3] [UUU] Which of the following should the administrator do to make all storage space available on the RAID array?
A. Run hdparm to alert the kernel to a new drive.
B. Convert the new drive to a hot spare.
C. Set the RAID type to a RAID 1.
D. Grow the array size to four members.
A systems administrator needs to conduct maintenance on a server. Which of the following commands will place the administrator in the appropriate runlevel?
A. init 0
B. telinit 1
C. init 3
D. telinit 6
A Linux administrator retrieved a repository of files from a Git server using git clone. The administrator wants to see if a configuration file was added to the repository. Which of the following Git arguments should be used to see the recent modifications?
A. fetch
B. log
C. init
D. pull
Joe, a user, is unable to log in to the server and contracts the systems administrator to look into the issue. The administrator examines the /etc/passwd file and discovers the following entry: joe:x:505:505::/home/joe:/bin/false Which of the following commands should the administrator execute to resolve the problem?
A. usermod ג€”s /bin/bash joe
B. passwd ג€”u joe
C. useradd ג€”s /bin/bash joe
D. chage ג€”E -l joe
A junior systems administrator has generated a PKI certificate for SSH sessions. The administrator would like to configure authentication without passwords to remote systems. Which of the following should the administrator perform?
A. Add the content of id_rsa.pub file to the remote system ~/.ssh/authorized_keys location.
B. Add the content of id_rsa file to the remote system ~/.ssh/authorized_keys location.
C. Add the content of id_rsa file to the remote system ~/.ssh/known_hosts location.
D. Add the content of id_rsa.pub file to the remote system ~/.ssh/known_hosts location.
A junior Linux administrator needs to create 16 empty files quickly that will contain sales information for each quarter for the past four years. Which of the following commands will meet this requirement?
A. touch {2015,2016,2017,2018}.{q1,q2,q3,q4}
B. touch [2015,2016,2017,2018].[q1,q2,q3,q4]
C. touch ‘2015,2016,2017,2018’.’q1,q2,q3,q4′
D. touch {2015.2016.2017.2018}.{q1.q2.q3.q4}
A Linux administrator needs to schedule a cron job to run at 1:15 p.m. every Friday to report the amount of free disk space on the system and to send the output to a file named `freespace`. Which of the following would meet this requirement?
A. 13 15 * * 5 df > /freespace
B. 15 13 * * 5 df > /freespace
C. 15 1 * * 6 df > /freespace
D. 15 13 6 * * df > /freespace
Joe, a Linux administrator implemented an IP blocking solution to secure a server, but he is now unable to connect to the server from the office. Which of the following should Joe review to determine if the office desktop was blocked by this solution?
A. journalctl
B. /etc/ufw
C. dmesg
D. /var/log/audit
E. /etc/hosts.deny
While trying to access a website hosted on the server, the systems administrator receives the following error message:The administrator then performs some diagnostics:
Which of the following commands should the administrator use to fix the issue?
A. chown -R www:www /var/www/website
B. chcon -t httpd_sys_content_t /etc/httpd
C. chmod -R 777 /var/www/website
D. restorecon /var/www/html/website/index.html
The development team has automated their software build process so each time a change is submitted to the source code repository, a new software build is compiled. They are requesting that the Linux operations team look into automating the deployment of the software build into the test environment. Which of the following is the benefit to the development team for implementing deployment automation?
A. To ensure the build commits are also deployed to the test environment
B. To enable notifications when builds are deployed to the test environment
C. To ensure software builds in test are not accidentally deployed to production
D. To streamline the deployment process for deploying builds into test environments
A server is almost out of free memory and is becoming unresponsive. Which of the following sets of commands will BEST mitigate the issue?
A. free, fack, partprobe
B. lsof, lvcreate, mdadm
C. df, du, rmmod
D. fdisk, mkswap, swapon -a
A Linux administrator needs to remove a USB drive from a system. The unmount command fails, stating the device is busy. Which of the following commands will show the reason for this error?
A. lsusb | grep /mnt/usb
B. mount | grep /mnt/usb
C. ps aux | grep /mnt/usb
D. lsof | grep /mnt/usb
A technician wants to implement a firewall ACL to block external access to the company's SSH server. Which of the following should the technician implement to configure the firewall so it will inform the source of the action taken by the ACL?
A. Use the LOG option
B. Use the REJECT option
C. Use the CONNTRACK option
D. Use the DROP option
Which of the following is used on the client to boot a Linux system from a TFTP server?
A. HTTP
B. GRUB
C. EFI
D. PXE
A Linux systems administrator needs to provision multiple web servers into separate regional datacenters. The systems architect has instructed the administrator to define the server infrastructure using a specific tool that consumes a text-based file. Which of the following is the BEST reason to do this?
A. To document the infrastructure so it can be included in the system security plan
B. To ensure the administrator follows the planning phase of the systems development life cycle
C. To define the infrastructure so it can be provisioned consistently with minimal manual tasks
D. To validate user requirements have been met within each regional datacenter for compliance
A Linux administrator must identify a user with high disk usage. The administrator runs the # du `"s /home/* command and gets the following output:Based on the output, User3 has the largest amount of disk space used. To clean up the file space, the administrator needs to find out more information about the specific files that are using the most disk space. Which of the following commands will accomplish this task?
A. df ג€”k /home/User3/files.txt
B. du ג€”a /home/User3/*
C. du ג€”sh /home/User/
D. find . ג€”name /home/User3 -print
An administrator needs to see a list of the system user's encrypted passwords. Which of the following Linux files does the administrator need to read?
A. /etc/shadow
B. /etc/skel
C. /etc/passwd
D. /etc/pw
Which of the following statements BEST represents what the term `agentless` means regarding orchestration?
A. Installation of a tool is not required on the remote system to perform orchestration tasks
B. It facilitates version control when using infrastructure as code during orchestration
C. It automatically removes malware from the remote system during orchestration
D. A tool can only be accessed remotely to perform orchestration tasks
A four-drive Linux NAS has been improperly configured. Each drive has a capacity of 6TB, for a total storage capacity of 24TB. To reconfigure this unit to be not pluggable for drive replacement and provide total storage of 11TB to 12TB, which of the following would be the correct RAID configuration?
A. RAID 01
B. RAID 03
C. RAID 10
D. RAID 50
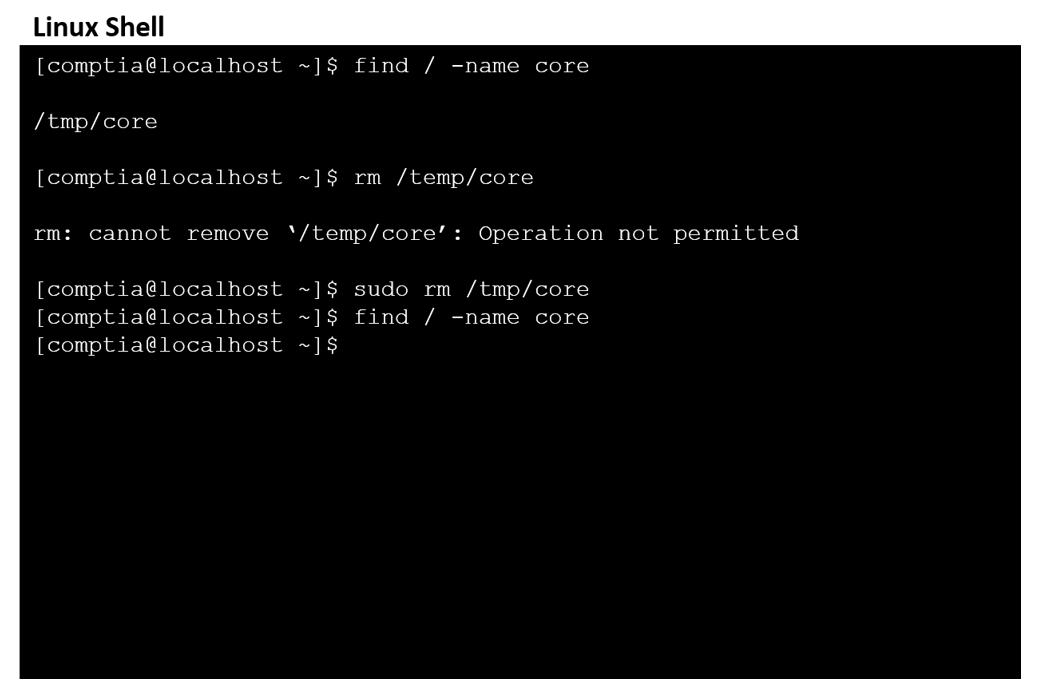
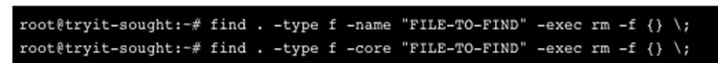
SIMULATION - Find the file named core and remove it from the system. INSTRUCTIONS - Type `help` to display a list of available commands. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A junior administrator needs to display information for an RPM package that contains software from an external provider. Which of the following commands will display the package information?
A. rpm -vp package.noarch.rpm
B. rpm -qp package.noarch.rpm
C. rpm -qf package.noarch.rpm
D. rpm -qi package.noarch.rpm
Which of the following is a difference between YAML and JSON?
A. Users can comment in YAML but not in JSON
B. JSON only uses curly brackets, while YAML only uses square brackets
C. JSON is used in web development, while YAML is used solely in back-end systems.
D. YAML has been deprecated for JSON.
A Linux administrator is troubleshooting an issue with a shell script. Users in the accounting department are unable to run the script, but users in the sales department are not having issues. Users in both departments should be able to run the script. The administrator checks the permissions on the script and receives the following information: -r-xr-xr-- joe sales script.sh Which of the following commands should the administrator execute to resolve the problem?
A. chgrp accounting script.sh
B. chmod 644 script.sh
C. chown accounting script.sh
D. chmod a+x script.sh
A systems administrator is investigating low performance a server. After executing some diagnostic commands, the administrator analyzes the data:Which of the following is the cause of low performance on the server?
A. Lack of swap space
B. Lack of available memory
C. User processes have taken up all the available CPU time
D. High disk activity
A new video card was added to a customer workstation. To get the new video card to work correctly, a systems administrator needs to remove support for the nouveau video driver on the Linux workstation. Which of the following will accomplish this task?
A. Use rmmod -f nouveau.
B. Use modprobe -R nouveau.
C. Add blacklist nouveau to /etc/modprobe.d/blacklist.conf.
D. Add blacklist nouveau to /etc/modprobe.conf.
A corporate server security policy states, `Ensure password hashes are not readable by non-administrative users.` The administrator should check the permissions on which of the following files to ensure the server satisfies this policy?
A. /etc/shadow
B. /etc/passwd
C. /etc/group
D. /etc/security/limits.conf
A company's httpd server has stopped working and restarting the service does not fix the issue. A junior systems administrator is investigating log files for clues. Which of the following commands should the administrator execute?
A. journalctl -u httpd
B. journalctl -l httpd
C. systemctl -s httpd
D. systemctl -l httpd
A systems administrator needs to retrieve specific fields from a CSV file. Which of the following tools would accomplish this task?
A. awk
B. sort
C. print
D. echo
An administrator needs a bootable USB for installing a new Linux machine. The administrator downloaded the image file and named it as Linux_OS.iso in the / tmp directory. Which of the following commands will accomplish that task?
A. dd input=/tmp/Linux_OS.iso of=/dev/sda bs=512
B. dd in=/tmp/Linux_OS.iso out=/dev/sdb bs=512
C. dd if=/tmp/Linux_OS.iso of=/dev/sda bs=512
D. dd if=/tmp/Linux_OS.iso out=/dev/sdb1 bs=512
A Linux administrator is configuring a server to log security events for the ping command while allowing the request to occur. The Linux server is using AppArmor to manage its security services. Which of the following commands is the BEST option?
A. aa-complain /bin/ping
B. aa-disable /bin/ping
C. aa-unconfined /bin/ping
D. aa-enforce /bin/ping
A junior systems administrator needs to schedule a backup script named /scripts/backup.sh and make the correct changes to the crontab. Which of the following crontab entries would run the script every Monday at 2:05 a.m.?
A. 1 * * 5 2 /scripts/backup.sh
B. 2 5 * * 1 /scripts/backup.sh
C. 5 2 * * 1 /scripts/backup.sh
D. 1 * * 2 5 /scripts/backup.sh
E. 5 2 * * 0 /scripts/backup.sh
Which of the following would allow remote users to access a corporate server? (Choose two.)
A. VPN server
B. SMTP server
C. NTP server
D. SSH server
E. DHCP server
F. File server
An issue was discovered on a testing branch of a Git repository. A file was inadvertently modified and needs to be reverted to the master branch version. Which of the following is the BEST option to resolve the issue?
A. git branch -b master file
B. git merge master testing
C. git stash branch master
D. git checkout master — file
Joe, a user, creates a short shell script, shortscript.sh, and saves it in his home directory with default permissions and paths. He then attempts to run the script by typing ./shortscript.sh, but the command fails to execute. Which of the following commands would have allowed the script to run?
A. chmod u+x shortscript.sh
B. source ./shortscript.sh
C. chmod 155 ~/shortscript.sh
D. chgrp shortscript.sh Joe
Ann, a user, has created a new directory and noticed that permissions on the new directory are as follows: drwx------. 1 ann ann 0 Jun 11 08:20 work Which of the following should the administrator do to restore default permissions for newly created directories?
A. Change umask value in /etc/profile.
B. Run chmod command to update permissions.
C. Modify directory ownership to ann:ann with chown.
D. Execute chattr command to restore default access.
A junior administrator is configuring local name lookups for fully qualified domain names in an isolated environment. The administrator is given a checklist and must accomplish the following tasks: ✑ Add localhost with loopback address. ✑ Add 192.168.192.12/24 to resolve to database01.comptia.org Given this scenario, which of the following steps should the administrator perform to accomplish these tasks?
A. Open the /etc/nsswitch.conf file with a file editor and add the following lines: 127.0.0.1 localhost 192.168.192.12 database01.comptia.org
B. Open the /etc/dhcpd.conf file with a file editor and add the following lines: 127.0.0.1 localhost 192.168.192.12 database01.comptia.org
C. Open the /etc/hosts file with a file editor and add the following lines: 127.0.0.1 localhost 192.168.192.12 database01.comptia.org
D. Open the /etc/network file with a file editor and add the following lines: 127.0.0.1 localhost 192.168.192.12 database01.comptia.org
A systems administrator notices a large number of autoloaded device modules are no longer needed and decides to do a cleanup of them. Which of the following commands will accomplish this task?
A. rmmod -c
B. depmod -r
C. insmod -c
D. modprobe -r
Given the output below:[1] [1] [1] C. rm `"rf ./Pictures - [1] [1]
A systems administrator wants to download a package from a remote server. Which of the following are the BEST commands to use for this task? (Choose two.)
A. curl
B. wget
C. make
D. tar
E. zip
F. nc
Access Full XK0-004 Exam Prep Free
Want to go beyond these 50 questions? Click here to unlock a full set of XK0-004 exam prep free questions covering every domain tested on the exam.
We continuously update our content to ensure you have the most current and effective prep materials.
Good luck with your XK0-004 certification journey!