SCS-C01 Exam Prep Free – 50 Practice Questions to Get You Ready for Exam Day
Getting ready for the SCS-C01 certification? Our SCS-C01 Exam Prep Free resource includes 50 exam-style questions designed to help you practice effectively and feel confident on test day
Effective SCS-C01 exam prep free is the key to success. With our free practice questions, you can:
- Get familiar with exam format and question style
- Identify which topics you’ve mastered—and which need more review
- Boost your confidence and reduce exam anxiety
Below, you will find 50 realistic SCS-C01 Exam Prep Free questions that cover key exam topics. These questions are designed to reflect the structure and challenge level of the actual exam, making them perfect for your study routine.
A Security Engineer has created an Amazon CloudWatch event that invokes an AWS Lambda function daily. The Lambda function runs an Amazon Athena query that checks AWS CloudTrail logs in Amazon S3 to detect whether any IAM user accounts or credentials have been created in the past 30 days. The results of the Athena query are created in the same S3 bucket. The Engineer runs a test execution of the Lambda function via the AWS Console, and the function runs successfully. After several minutes, the Engineer finds that his Athena query has failed with the error message: `Insufficient Permissions`. The IAM permissions of the Security Engineer and the Lambda function are shown below: Security Engineer -Lambda function execution role -
What is causing the error?
A. The Lambda function does not have permissions to start the Athena query execution.
B. The Security Engineer does not have permissions to start the Athena query execution.
C. The Athena service does not support invocation through Lambda.
D. The Lambda function does not have permissions to access the CloudTrail S3 bucket.
A company recently had a security audit in which the auditors identified multiple potential threats. These potential threats can cause usage pattern changes such as DNS access peak, abnormal instance traffic, abnormal network interface traffic, and unusual Amazon S3 API calls. The threats can come from different sources and can occur at any time. The company needs to implement a solution to continuously monitor its system and identify all these incoming threats in near-real time. Which solution will meet these requirements?
A. Enable AWS CloudTrail logs, VPC flow logs, and DNS logs. Use Amazon CloudWatch Logs to manage these logs from a centralized account.
B. Enable AWS CloudTrail logs, VPC flow logs, and DNS logs. Use Amazon Macie to monitor these logs from a centralized account.
C. Enable Amazon GuardDuty from a centralized account. Use GuardDuty to manage AWS CloudTrail logs, VPC flow logs, and DNS logs.
D. Enable Amazon Inspector from a centralized account. Use Amazon Inspector to manage AWS CloudTrail logs, VPC flow logs, and DNS logs.
Auditors for a health care company have mandated that all data volumes be encrypted at rest. Infrastructure is deployed mainly via AWS CloudFormation; however, third-party frameworks and manual deployment are required on some legacy systems. What is the BEST way to monitor, on a recurring basis, whether all EBS volumes are encrypted?
A. On a recurring basis, update all IAM user policies to require that EC2 instances are created with an encrypted volume.
B. Configure an AWS Config rule to run on a recurring basis for volume encryption.
C. Set up Amazon Inspector rules for volume encryption to run on a recurring schedule.
D. Use CloudWatch Logs to determine whether instances were created with an encrypted volume.
A company’s security team needs to receive a notification whenever an AWS access key has not been rotated in 90 or more days. A security engineer must develop a solution that provides these notifications automatically. Which solution will meet these requirements with the LEAST amount of effort?
A. Deploy an AWS Config managed rule to run on a periodic basis of 24 hours. Select the access-keys-rotated managed rule, and set the maxAccessKeyAge parameter to 90 days. Create an Amazon EventBridge (Amazon CloudWatch Events) rule with an event pattern that matches the compliance type of NON_COMPLIANT from AWS Config for the managed rule. Configure EventBridge (CloudWatch Events) to send an Amazon Simple Notification Service (Amazon SNS) notification to the security team.
B. Create a script to export a .csv file from the AWS Trusted Advisor check for IAM access key rotation. Load the script into an AWS Lambda function that will upload the .csv file to an Amazon S3 bucket. Create an Amazon Athena table query that runs when the .csv file is uploaded to the S3 bucket. Publish the results for any keys older than 90 days by using an invocation of an Amazon Simple Notification Service (Amazon SNS) notification to the security team.
C. Create a script to download the IAM credentials report on a periodic basis. Load the script into an AWS Lambda function that will run on a schedule through Amazon EventBridge (Amazon CloudWatch Events). Configure the Lambda script to load the report into memory and to filter the report for records in which the key was last rotated at least 90 days ago. If any records are detected, send an Amazon Simple Notification Service (Amazon SNS) notification to the security team.
D. Create an AWS Lambda function that queries the IAM API to list all the users. Iterate through the users by using the ListAccessKeys operation. Verify that the value in the CreateDate field is not at least 90 days old. Send an Amazon Simple Notification Service (Amazon SNS) notification to the security team if the value is at least 90 days old. Create an Amazon EventBridge (Amazon CloudWatch Events) rule to schedule the Lambda function to run each day.
A company is outsourcing its operational support to an external company. The company's security officer must implement an access solution for delegating operational support that minimizes overhead. Which approach should the security officer take to meet these requirements?
A. Implement Amazon Cognito identity pools with a role that uses a policy that denies the actions related to Amazon Cognito API management. Allow the external company to federate through its identity provider.
B. Federate AWS Identity and Access Management (IAM) with the external company’s identity provider. Create an IAM role and attach a policy with the necessary permissions.
C. Create an IAM group for the external company. Add a policy to the group that denies IAM modifications. Securely provide the credentials to the external company.
D. Use AWS SSO with the external company’s identity provider. Create an IAM group to map to the identity provider user group, and attach a policy with the necessary permissions.
A company uses AWS Organizations. According to compliance requirements, the company’s applications that are hosted on Amazon EC2 instances must never use IAM credentials from Instance Metadata Service Version 1 (IMDSv1). What should a security engineer do to meet this requirement?
A. Create a security group that denies access on HTTP to 169.254.169.254. Attach this security group to all EC2 instances.
B. Deactivate all access to IMDSv1 through the instance metadata options when using the AWS CLI, AWS API, or AWS Management Console to launch an EC2 instance.
C. Attach the following SCP to the root OU in AWS Organizations:

D. Attach the following SCP to the root OU in AWS Organizations:

A Security Analyst attempted to troubleshoot the monitoring of suspicious security group changes. The Analyst was told that there is an Amazon CloudWatch alarm in place for these AWS CloudTrail log events. The Analyst tested the monitoring setup by making a configuration change to the security group but did not receive any alerts. Which of the following troubleshooting steps should the Analyst perform?
A. Ensure that CloudTrail and S3 bucket access logging is enabled for the Analyst’s AWS account. B. Verify that a metric filter was created and then mapped to an alarm. Check the alarm notification action.
B. Check the CloudWatch dashboards to ensure that there is a metric configured with an appropriate dimension for security group changes.
C. Verify that the Analyst’s account is mapped to an IAM policy that includes permissions for cloudwatch: GetMetricStatistics and Cloudwatch: ListMetrics.
A company plans to move most of its IT infrastructure to AWS. They want to leverage their existing on-premises Active Directory as an identity provider for AWS. Which combination of steps should a Security Engineer take to federate the company's on-premises Active Directory with AWS? (Choose two.)
A. Create IAM roles with permissions corresponding to each Active Directory group.
B. Create IAM groups with permissions corresponding to each Active Directory group.
C. Configure Amazon Cloud Directory to support a SAML provider.
D. Configure Active Directory to add relying party trust between Active Directory and AWS.
E. Configure Amazon Cognito to add relying party trust between Active Directory and AWS.
A company wants to monitor the deletion of customer managed CMKs. A security engineer must create an alarm that will notify the company before a CM׀ is deleted. The security engineer has configured the integration of AWS CloudTrail with Amazon CloudWatch. What should the security engineer do next to meet this requirement?
A. Within AWS Key Management Service (AWS KMS), specify the deletion time of the key material during CMK creation. AWS KMS will automatically create a CloudWatch alarm.
B. Create an Amazon EventBridge (Amazon CloudWatch Events) rule to look for API calls of DeleteAlias. Create an AWS Lambda function to send an Amazon Simple Notification Service (Amazon SNS) message to the company. Add the Lambda function as the target of the Eventbridge (CloudWatch Events) rule.
C. Create an Amazon EventBridge (Amazon CloudWatch Events) rule to look for API calls of DisableKey and ScheduleKeyDeletion. Create an AWS Lambda function to send an Amazon Simple Notification Service (Amazon SNS) message to the company. Add the Lambda function as the target of the Eventbridge (CloudWatch Events) rule.
D. Create an Amazon Simple Notification Service (Amazon SNS) policy to look for AWS Key Management Service (AWS KMS) API calls of RevokeGrant and ScheduleKeyDeletion. Create an AWS Lambda function to generate the alarm and send the notification to the company. Add the Lambda function as the target of the SNS policy.
A company decides to use AWS Key Management Service (AWS KMS) for data encryption operations. The company must create a KMS key and automate the rotation of the key. The company also needs the ability to deactivate the key and schedule the key for deletion. Which solution will meet these requirements?
A. Create an asymmetric customer managed KMS key. Enable automatic key rotation.
B. Create a symmetric customer managed KMS key. Disable the envelope encryption option.
C. Create a symmetric customer managed KMS key. Enable automatic key rotation.
D. Create an asymmetric customer managed KMS key. Disable the envelope encryption option.
A security engineer is responsible for providing secure access to AWS resources for thousands of developers in a company's corporate identity provider (IdP). The developers access a set of AWS services from their corporate premises using IAM credentials. Due to the volume of requests for provisioning new IAM users, it is taking a long time to grant access permissions. The security engineer receives reports that developers are sharing their IAM credentials with others to avoid provisioning delays. This causes concern about overall security for the security engineer. Which actions will meet the program requirements that address security?
A. Create an Amazon CloudWatch alarm for AWS CloudTrail events. Create a metric filter to send a notification when the same set of IAM credentials is used by multiple developers.
B. Create a federation between AWS and the existing corporate IdP. Leverage IAM roles to provide federated access to AWS resources.
C. Create a VPN tunnel between the corporate premises and the VPC. Allow permissions to all AWS services only if it originates from corporate premises.
D. Create multiple IAM roles for each IAM user. Ensure that users who use the same IAM credentials cannot assume the same IAM role at the same time.
A security engineer receives an AWS abuse email message. According to the message, an Amazon EC2 instance that is running in the security engineer's AWS account is sending phishing email messages. The EC2 instance is part of an application that is deployed in production. The application runs on many EC2 instances behind an Application Load Balancer. The instances run in an Amazon EC2 Auto Scaling group across multiple subnets and multiple Availability Zones. The instances normally communicate only over the HTTP, HTTPS, and MySQL protocols. Upon investigation, the security engineer discovers that email messages are being sent over port 587. All other traffic is normal. The security engineer must create a solution that contains the compromised EC2 instance, preserves forensic evidence for analysis, and minimizes application downtime. Which combination of steps must the security engineer take to meet these requirements? (Choose three.)
A. Add an outbound rule to the security group that is attached to the compromised EC2 instance to deny traffic to 0.0.0.0/0 and port 587.
B. Add an outbound rule to the network ACL for the subnet that contains the compromised EC2 instance to deny traffic to 0.0.0.0/0 and port 587.
C. Gather volatile memory from the compromised EC2 instance. Suspend the compromised EC2 instance from the Auto Scaling group. Then take a snapshot of the compromised EC2 instance.
D. Take a snapshot of the compromised EC2 instance. Suspend the compromised EC2 instance from the Auto Scaling group. Then gather volatile memory from the compromised EC2 instance.
E. Move the compromised EC2 instance to an isolated subnet that has a network ACL that has no inbound rules or outbound rules.
F. Replace the existing security group that is attached to the compromised EC2 instance with a new security group that has no inbound rules or outbound rules.
A user in account 111122223333 is receiving an access denied error message while calling the AWS Key Management Service (AWS KMS) GenerateDataKey API operation. The key policy contains the following statement:Account 111122223333 is not using AWS Organizations SCPs. Which combination of steps should a security engineer take to ensure that KMSUser can perform the action on the key? (Choose two.)
A. Modify the key policy to include the key’s key ID in the Resource field.
B. Verify that KMSUser has no explicit denies for the GenerateDataKey action in its attached IAM policies.
C. Verify that KMSUser is allowed to perform the GenerateDataKey action in its attached IAM policies for the encryption context.
D. Ensure that KMSUser is including the encryption context key-value pair in its GenerateDataKey.
E. Revoke any KMS grants on the key that are denying the GenerateDataKey action for KMSUser.
A company that builds document management systems recently performed a security review of its application on AWS. The review showed that uploads of documents through signed URLs into Amazon S3 could occur in the application without encryption in transit. A security engineer must implement a solution that prevents uploads that are not encrypted in transit. Which solution will meet this requirement?
A. Ensure that all client implementations are using HTTPS to upload documents into the application.
B. Configure the s3-bucket-ssl-requests-only managed rule in AWS Config.
C. Add an S3 bucket policy that denies all S3 actions for condition “aws:secureTransport”: “false”.
D. Add an S3 bucket ACL with a grantee of AllUsers, a permission of WRITE, and a condition of secureTransport.
A company uses AWS Organizations. The company has teams that use an AWS CloudHSM hardware security module (HSM) that is hosted in a central AWS account. One of the teams creates its own new dedicated AWS account and wants to use the HSM that is hosted in the central account. How should a security engineer share the HSM that is hosted in the central account with the new dedicated account?
A. Use AWS Resource Access Manager (AWS RAM) to share the VPC subnet ID of the HSM that is hosted in the central account with the new dedicated account. Configure the CloudHSM security group to accept inbound traffic from the private IP addresses of client instances in the new dedicated account.
B. Use AWS Identity and Access Management (IAM) to create a cross-account role to access the CloudHSM cluster that is in the central account. Create a new IAM user in the new dedicated account. Assign the cross-account role the new IAM user.
C. Use AWS Single Sign-On to create an AWS Security Token Service (AWS STS) token to authenticate from the new dedicated account to the central account. Use the cross-account permissions that are assigned to the STS token to invoke an operation on the HSM in the central account.
D. Use AWS Resource Access Manager (AWS RAM) to share the ID of the HSM that is hosted in the central account with the new dedicated account. Configure the CloudHSM security group to accept inbound traffic from the private IP addresses of client instances in the new dedicated account.
The Security Engineer for a mobile game has to implement a method to authenticate users so that they can save their progress. Because most of the users are part of the same OpenID-Connect compatible social media website, the Security Engineer would like to use that as the identity provider. Which solution is the SIMPLEST way to allow the authentication of users using their social media identities?
A. Amazon Cognito
B. AssumeRoleWithWebIdentity API
C. Amazon Cloud Directory
D. Active Directory (AD) Connector
A company runs an application on Amazon EC2 instances that run on Amazon Linux 2. The application outputs important information to a custom log file. To support troubleshooting and incident response, new events in the log files must be available to the company's operations staff within 30 minutes. The operations staff needs a solution to retrieve the latest custom log information without using interactive sessions to connect to the instances. Which solutions will meet these requirements? (Choose two.)
A. Create a script on the EC2 instances to copy the log file contents to an Amazon S3 bucket. Add the script to an hourly cron schedule. Instruct the operations staff to retrieve the information from the S3 bucket directly.
B. Configure the Amazon CloudWatch agent configuration file to include the application log file details in the logs section. Instruct the operations staff to retrieve the information from the correct log group in Amazon CloudWatch Logs.
C. Configure the EC2 instances to use AWS Systems Manager. Configure appropriate permissions. Instruct the operations staff to examine the log file by invoking AWS Systems Manager Run Command.
D. Configure the EC2 instances to use AWS Systems Manager. Configure appropriate permissions. Instruct the operations staff to examine the log file by using AWS Systems Manager Session Manager.
E. Create a script on the EC2 instances to copy the log file contents to an Amazon S3 bucket. Add the script to an hourly cron schedule. Instruct the operations staff to retrieve the information by running Amazon Athena queries against the S3 data.
Two Amazon EC2 instances in different subnets should be able to connect to each other but cannot. It has been confirmed that other hosts in the same subnets are able to communicate successfully, and that security groups have valid ALLOW rules in place to permit this traffic. Which of the following troubleshooting steps should be performed?
A. Check inbound and outbound security groups, looking for DENY rules
B. Check inbound and outbound Network ACL rules, looking for DENY rules
C. Review the rejected packet reason codes in the VPC Flow Logs
D. Use AWS X-Ray to trace the end-to-end application flow
A company plans to use AWS CodeDeploy to deploy code to multiple Amazon EC2 instances in a VPC at the same time. The company needs to allow the CodeDeploy service to communicate with the instances in the VPC without going through the public internet for CodeDeploy API operations. What should a security engineer do to meet this requirement?
A. Use a NAT gateway in the VPC.
B. Use an interface VPC endpoint for CodeDeploy API operations.
C. Use a gateway VPC endpoint for CodeDeploy API operations.
D. Use a VPN connection to the VPC.
A company is designing a multi-account structure for its development teams. The company is using AWS Organizations and AWS Single Sign-On (AWS SSO). The company must implement a solution so that the development teams can use only specific AWS Regions and so that each AWS account allows access to only specific AWS services. Which solution will meet these requirements with the LEAST operational overhead?
A. Use AWS SSO to set up service-linked roles with IAM policy statements that include the Condition, Resource, and NotAction elements to allow access to only the Regions and services that are needed.
B. Deactivate AWS Security Token Service (AWS STS) in Regions that the developers are not allowed to use.
C. Create SCPs that include the Condition, Resource, and NotAction elements to allow access to only the Regions and services that are needed.
D. For each AWS account, create tailored identity-based policies for AWS SSO. Use statements that include the Condition, Resource, and NotAction elements to allow access to only the Regions and services that are needed.
A company plans to move most of its IT infrastructure to AWS. The company wants to leverage its existing on-premises Active Directory as an identity provider for AWS. Which steps should be taken to authenticate to AWS services using the company's on-premises Active Directory? (Choose three.)
A. Create IAM roles with permissions corresponding to each Active Directory group.
B. Create IAM groups with permissions corresponding to each Active Directory group.
C. Create a SAML provider with IAM.
D. Create a SAML provider with Amazon Cloud Directory.
E. Configure AWS as a trusted relying party for the Active Directory
F. Configure IAM as a trusted relying party for Amazon Cloud Directory.
A company is testing a new version of its application. The company is using a public Amazon API Gateway API to expose the application. Currently, the company wants to allow only testers from its network to access the new application. Which solutions can the company use to meet these requirements? (Choose two.)
A. Create and configure a security group that allows access from the company’s IP address range. Apply the security group to the API Gateway API.
B. Create and configure a network ACL that allows traffic from the company’s IP address range. Apply the network ACL to the API Gateway API subnet.
C. Create an AWS WAF web ACL. Configure an IP match rule that allows traffic from the company’s IP address range. Apply the web ACL to the API Gateway API.
D. Use a condition in the API Gateway resource policy to allow access only from the company’s IP address range.
E. Create an interface VPC endpoint for the API Gateway execute-api. Instruct testers to use this endpoint.
A company deployed Amazon GuardDuty in the us-east-1 Region. The company wants all DNS logs that relate to the company's Amazon EC2 instances to be inspected. What should a security engineer do to ensure that the EC2 instances are logged?
A. Use IPv6 addresses that are configured for hostnames.
B. Configure external DNS resolvers as internal resolvers that are visible only to AWS.
C. Use AWS DNS resolvers for all EC2 instances.
D. Configure a third-party DNS resolver with logging for all EC2 instances.
Which of the following minimizes the potential attack surface for applications?
A. Use security groups to provide stateful firewalls for Amazon EC2 instances at the hypervisor level.
B. Use network ACLs to provide stateful firewalls at the VPC level to prevent access to any specific AWS resource.
C. Use AWS Direct Connect for secure trusted connections between EC2 instances within private subnets.
D. Design network security in a single layer within the perimeter network (also known as DMZ, demilitarized zone, and screened subnet) to facilitate quicker responses to threats.
A company deployed an Amazon EC2 instance to a VPC on AWS. A recent alert indicates that the EC2 instance is receiving a suspicious number of requests over an open TCP port from an external source. The TCP port remains open for long periods of time. The company's security team needs to stop all activity to this port from the external source to ensure that the EC2 instance is not being compromised. The application must remain available to other users. Which solution will meet these requirements?
A. Update the network ACL that is attached to the subnet that is associated with the EC2 instance. Add a Deny statement for the port and the source IP addresses.
B. Update the elastic network interface security group that is attached to the EC2 instance to remove the port from the inbound rule list.
C. Update the elastic network interface security group that is attached to the EC2 instance by adding a Deny entry in the inbound list for the port and the source IP addresses.
D. Create a new network ACL for the subnet. Deny all traffic from the EC2 instance to prevent data from being removed.
A Security Administrator at a university is configuring a fleet of Amazon EC2 instances. The EC2 instances are shared among students, and non-root SSH access is allowed. The Administrator is concerned about students attacking other AWS account resources by using the EC2 instance metadata service. What can the Administrator do to protect against this potential attack?
A. Disable the EC2 instance metadata service.
B. Log all student SSH interactive session activity.
C. Implement iptables-based restrictions on the instances.
D. Install the Amazon Inspector agent on the instances.
A company has an application on Amazon EC2 instances that store confidential customer data. The company must restrict access to customer data. A security engineer requires secure access to the instances that host the application. According to company policy, users must not open any inbound ports, maintain bastion hosts, or manage SSH keys for the EC2 instances. The security engineer wants to monitor, store, and access all session activity logs. The logs must be encrypted. Which solution will meet these requirements?
A. Use AWS Control Tower to connect to the EC2 instances. Configure Amazon CloudWatch logging for the sessions. Select the upload session logs option and allow only encrypted CloudWatch Logs log groups.
B. Use AWS Security Hub to connect to the EC2 instances. Configure Amazon CloudWatch logging for the sessions. Select the upload session logs option and allow only encrypted CloudWatch Logs log groups.
C. Use AWS Systems Manager Session Manager to connect to the EC2 instances. Configure Amazon CloudWatch monitoring to record the sessions. Select the store session logs option for the desired CloudWatch Logs log groups.
D. Use AWS Systems Manager Session Manager to connect to the EC2 instances. Configure Amazon CloudWatch logging. Select the upload session logs option and allow only encrypted CloudWatch Logs log groups.
An application makes calls to AWS services using the AWS SDK. The application runs on Amazon EC2 instances with an associated IAM role. When the application attempts to access an object within an Amazon S3 bucket; the Administrator receives the following error message: HTTP 403: Access Denied. Which combination of steps should the Administrator take to troubleshoot this issue? (Choose three.)
A. Confirm that the EC2 instance’s security group authorizes S3 access.
B. Verify that the KMS key policy allows decrypt access for the KMS key for this IAM principle.
C. Check the S3 bucket policy for statements that deny access to objects.
D. Confirm that the EC2 instance is using the correct key pair.
E. Confirm that the IAM role associated with the EC2 instance has the proper privileges.
F. Confirm that the instance and the S3 bucket are in the same Region.
An application team is developing an internal application in its AWS account. Employees will use the application to access their employee benefits information. The application has an Amazon S3 bucket that is encrypted with an AWS Key Management Service (AWS KMS) customer managed key. The application team has configured an S3 gateway VPC endpoint for the application to use. During testing, an IAM user is unable to download objects from the S3 bucket by using the AWS Management Console. However, other IAM users in the same AWS account can download objects from the S3 bucket. Which policies or ACL should a security engineer review and modify to resolve this issue? (Choose three.)
A. The KMS customer managed key policy.
B. The S3 VPC endpoint policy.
C. The S3 bucket policy.
D. The S3 ACL.
E. The IAM policy.
F. The KMS VPC endpoint policy.
A company has two web applications that run on Amazon EC2 and Amazon S3. The applications failed an HTTP security audit, and users are reporting latency issues. The applications need to deliver web content at low latencies while improving security and privacy for users and content providers. The company must implement a solution that does not require changes to the application code. Which combination of actions should the company take to meet these requirements? (Choose two.)
A. Deploy Amazon API Gateway. Cache the endpoint’s responses.
B. Configure Amazon API Gateway with a request parameter-based AWS Lambda authorizer to add HTTP security headers on origin responses.
C. Write a Lambda@Edge function to add HTTP security headers on origin responses.
D. Configure Amazon CloudFront. Create a distribution for the EC2 and S3 origins.
E. Implement an Application Load Balancer (ALB) to honor the connection header from the incoming client request after forwarding the response back to the client.
A security team is using Amazon EC2 Image Builder to build a hardened AMI with forensic capabilities. An AWS Key Management Service (AWS KMS) key will encrypt the forensic AMI. EC2 Image Builder successfully installs the required patches and packages in the security team’s AWS account. The security team uses a federated IAM role in the same AWS account to sign in to the AWS Management Console and attempts to launch the forensic AMI. The EC2 instance launches and immediately terminates. What should the security team do to launch the EC2 instance successfully?
A. Update the policy that is associated with the federated IAM role to allow the ec2:DescribeImages action for the forensic AML.
B. Update the policy that is associated with the federated IAM role to allow the ec2:StartInstances action in the security team’s AWS account.
C. Update the policy that is associated with the KMS key that is used to encrypt the forensic AMI. Configure the policy to allow the kms:Encrypt and kms:Decrypt actions for the federated IAM role.
D. Update the policy that is associated with the federated IAM role to allow the kms:DescribeKey action for the KMS key that is used to encrypt the forensic AMI.
A company has a web-based application using Amazon CloudFront and running on Amazon Elastic Container Service (Amazon ECS) behind an Application Load Balancer (ALB). The ALB is terminating TLS and balancing load across ECS service tasks. A security engineer needs to design a solution to ensure that application content is accessible only through CloudFront and that it is never accessible directly. How should the security engineer build the MOST secure solution?
A. Add an origin custom header. Set the viewer protocol policy to HTTP and HTTPS. Set the origin protocol policy to HTTPS only. Update the application to validate the CloudFront custom header.
B. Add an origin custom header. Set the viewer protocol policy to HTTPS only. Set the origin protocol policy to match viewer. Update the application to validate the CloudFront custom header.
C. Add an origin custom header. Set the viewer protocol policy to redirect HTTP to HTTPS. Set the origin protocol policy to HTTP only. Update the application to validate the CloudFront custom header.
D. Add an origin custom header. Set the viewer protocol policy to redirect HTTP to HTTPS. Set the origin protocol policy to HTTPS only. Update the application to validate the CloudFront custom header.
A security engineer needs to implement automation for AWS resources at scale. The goal is to block traffic to and from suspicious remote hosts by specifying IP addresses that are associated with known command and control servers for botnets. The security engineer is using AWS Step Functions to orchestrate the solution. What should the security engineer do to meet these requirements?
A. Use Amazon GuardDuty to detect suspicious communication. Use an Amazon DynamoDB table to store IP addresses of suspected malicious hosts. Use AWS. Lambda functions to update the DynamoDB table and to update an AWS WAF web ACL rule to block the traffic.
B. Use Amazon GuardDuty to detect suspicious communication. Use an Amazon DynamoDB table to store IP addresses of suspected malicious hosts. Use AWS Lambda functions to update the DynamoDB table and to update an AWS Network Firewall rule group to block the traffic.
C. Use Amazon Inspector to detect suspicious communication. Use an Amazon DynamoDB table to store IP addresses of suspected malicious hosts. Use AWS Lambda functions to update the DynamoDB table and to update an AWS WAF web ACL rule to block the traffic.
D. Use Traffic Mirroring. Direct the mirrored traffic to an Amazon EC2 instance that has the Amazon Inspector agent configured to search for suspicious communication. Use an Amazon DynamoDB table to store IP addresses of suspected malicious hosts. Use AWS Lambda functions to update the DynamoDB table and to update an AWS Network Firewall rule group to block the traffic.
A recent security audit found that AWS CloudTrail logs are insufficiently protected from tampering and unauthorized access. Which actions must the Security Engineer take to access these audit findings? (Choose three.)
A. Ensure CloudTrail log file validation is turned on.
B. Configure an S3 lifecycle rule to periodically archive CloudTrail logs into Glacier for long-term storage.
C. Use an S3 bucket with tight access controls that exists in a separate account.
D. Use Amazon Inspector to monitor the file integrity of CloudTrail log files.
E. Request a certificate through ACM and use a generated certificate private key to encrypt CloudTrail log files.
F. Encrypt the CloudTrail log files with server-side encryption AWS KMS-managed keys (SSE-KMS).
A company needs to use HTTPS when connecting to its web applications to meet compliance requirements. These web applications run in Amazon VPC on Amazon EC2 instances behind an Application Load Balancer (ALB). A security engineer wants to ensure that the load balancer will only accept connections over port 443, even if the ALB is mistakenly configured with an HTTP listener. Which configuration steps should the security engineer take to accomplish this task?
A. Create a security group with a rule that denies inbound connections from 0.0.0.0/0 on port 80. Attach this security group to the ALB to overwrite more permissive rules from the ALB’s default security group.
B. Create a network ACL that denies inbound connections from 0.0.0.0/0 on port 80. Associate the network ACL with the VPC’s internet gateway.
C. Create a network ACL that allows outbound connections to the VPC IP range on port 443 only. Associate the network ACL with the VPC’s internet gateway.
D. Create a security group with a single inbound rule that allows connections from 0.0.0.0/0 on port 443. Ensure this security group is the only one associated with the ALB.
A company has multiple AWS accounts in an organization in AWS Organizations. The company is operating its business only in the United States (US) and stores sensitive information in Amazon S3 buckets. Because of the sensitivity of the data, the company wants to block access to S3 buckets that are located in AWS Regions outside the US. Which SCP should a security engineer use to meet this requirement?
A.

B.

C.

D.

A threat assessment has identified a risk whereby an internal employee could exfiltrate sensitive data from production host running inside AWS (Account 1). The threat was documented as follows: Threat description: A malicious actor could upload sensitive data from Server X by configuring credentials for an AWS account (Account 2) they control and uploading data to an Amazon S3 bucket within their control. Server X has outbound internet access configured via a proxy server. Legitimate access to S3 is required so that the application can upload encrypted files to an S3 bucket. Server X is currently using an IAM instance role. The proxy server is not able to inspect any of the server communication due to TLS encryption. Which of the following options will mitigate the threat? (Choose two.)
A. Bypass the proxy and use an S3 VPC endpoint with a policy that whitelists only certain S3 buckets within Account 1.
B. Block outbound access to public S3 endpoints on the proxy server.
C. Configure Network ACLs on Server X to deny access to S3 endpoints.
D. Modify the S3 bucket policy for the legitimate bucket to allow access only from the public IP addresses associated with the application server.
E. Remove the IAM instance role from the application server and save API access keys in a trusted and encrypted application config file.
A security engineer is configuring a new website that is named example.com. The security engineer wants to secure communications with the website by requiring users to connect to example.com through HTTPS. Which of the following is a valid option for storing SSL/TLS certificates?
A. Custom SSL certificate that is stored in AWS Key Management Service (AWS KMS)
B. Default SSL certificate that is stored in Amazon CloudFront.
C. Custom SSL certificate that is stored in AWS Certificate Manager (ACM)
D. Default SSL certificate that is stored in Amazon S3
A security engineer is setting up a new AWS account. The engineer has been asked to continuously monitor the company's AWS account using automated compliance checks based on AWS best practices and Center for Internet Security (CIS) AWS Foundations Benchmarks. How can the security engineer accomplish this using AWS services?
A. Enable AWS Config and set it to record all resources in all Regions and global resources. Then enable AWS Security Hub and confirm that the CIS AWS Foundations compliance standard is enabled.
B. Enable Amazon Inspector and configure it to scan all Regions for the CIS AWS Foundations Benchmarks. Then enable AWS Security Hub and configure it to ingest the Amazon Inspector findings.
C. Enable Amazon Inspector and configure it to scan all Regions for the CIS AWS Foundations Benchmarks. Then enable AWS Shield in all Regions to protect the account from DDoS attacks.
D. Enable AWS Config and set it to record all resources in all Regions and global resources. Then enable Amazon Inspector and configure it to enforce CIS AWS Foundations Benchmarks using AWS Config rules.
A company has a security team that manages its AWS Key Management Service (AWS KMS) CMKs. Members of the security team must be the only ones to administer the CMKs. The company's application team has a software process that needs temporary access to the CMKS occasionally. The security team must provide the application team’s software process access to the CMKs. Which solution meets these requirements with the LEAST overhead?
A. Export the CMK key material to an on-premises hardware security module (HSM). Give the application team access to the key material.
B. Edit the key policy that grants the security team access to the CMKs by adding the application team as principals. Revert this change when the application team no longer needs access.
C. Create a key grant to allow the application team to use the CMKs. Revoke the grant when the application team no longer needs access.
D. Create a new CMK by generating key material on premises. Import the key material to AWS KMS whenever the application team needs access. Grant the application team permissions to use the CMK.
A company requires that IP packet data be inspected for invalid or malicious content. Which of the following approaches achieve this requirement? (Choose two.)
A. Configure a proxy solution on Amazon EC2 and route all outbound VPC traffic through it. Perform inspection within proxy software on the EC2 instance.
B. Configure the host-based agent on each EC2 instance within the VPC. Perform inspection within the host-based agent.
C. Enable VPC Flow Logs for all subnets in the VPC. Perform inspection from the Flow Log data within Amazon CloudWatch Logs.
D. Configure Elastic Load Balancing (ELB) access logs. Perform inspection from the log data within the ELB access log files.
E. Configure the CloudWatch Logs agent on each EC2 instance within the VPC. Perform inspection from the log data within CloudWatch Logs.
A security engineer needs to implement an intrusion detection system (IDS) for a shipping company. The findings from the system must generate alerts that can be sent to an email distribution group that the company’s operations team uses. The security engineer must maximize the coverage that the IDS provides. Which combination of steps should the security engineer take to meet these requirements? (Choose two.)
A. Create an AWS CloudTrail trail to capture management events and Amazon S3 data events. Create VPC flow logs for all VPCs. Specify for the flow logs to capture all traffic.
B. Create an AWS CloudTrail trail to capture management events and Amazon S3 data events. Create VPC flow logs for all VPCS. Specify for the flow logs to capture accepted traffic.
C. Configure Amazon GuardDuty. Create an Amazon EventBridge (Amazon CloudWatch Events) rule to forward finding events to an Amazon Simple Notification Service (Amazon SNS) topic
D. Configure AWS Security Hub. Create an Amazon EventBridge (Amazon CloudWatch Events) rue to forward finding events to an Amazon Simple Notification Service (Amazon SNS) topic.
E. Create an AWS CloudTrail trail to capture management events and Amazon S3 data events. Configure an AWS Lambda function to analyze VPC flow logs and to inspect all flow log traffic that matches the ACCEPT filter type.
A security engineer is defining the controls required to protect the AWS account root user credentials in an AWS Organizations hierarchy. The controls should also limit the impact in case these credentials have been compromised. Which combination of controls should the security engineer propose? (Choose three.)
A. Apply the following SCP:
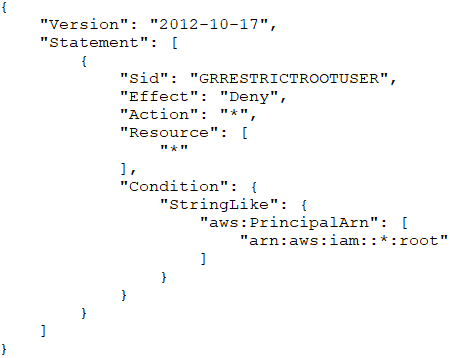
B. Apply the following SCP:
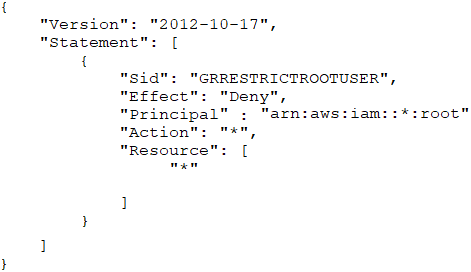
C. Enable multi-factor authentication (MFA) for the root user.
D. Set a strong randomized password and store it in a secure location.
E. Create an access key ID and secret access key, and store them in a secure location.
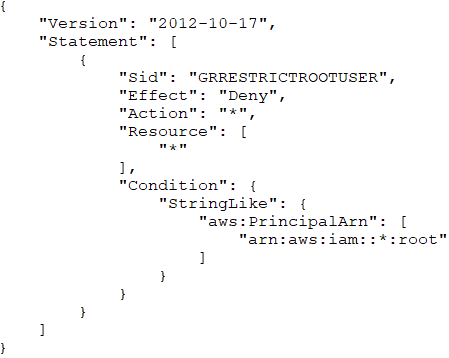
F. Apply the following permissions boundary to the root user:
A security engineer recently enabled the me-south-1 Region. The security engineer is now assuming an IAM role and is making an API call to an endpoint in me-south-1. The API call returns the following error: “AuthFailure: AWS was not able to validate the provided access credentials”. Which solutions will resolve this error? (Choose two.)
A. Add the iam:SetSecurityTokenServicePreferences action to the security engineer’s IAM role.
B. Use the AWS Security Token Service (AWS STS) endpoint in me-south-1 to obtain an STS token.
C. Use the AWS Security Token Service (AWS STS) endpoint in the us-east-1 Region to obtain an STS token.
D. Manually activate the AWS Security Token Service (AWS STS) endpoint in me-south-1.
E. Change the AWS Security Token Service (AWS STS) global endpoint to issue Region-compatible session tokens.
A company is implementing new compliance requirements to meet customer needs. According to the new requirements, the company must not use any Amazon RDS DB instances or DB clusters that lack encryption of the underlying storage. The company needs a solution that will generate an email alert when an unencrypted DB instance or DB cluster is created. The solution also must terminate the unencrypted DB instance or DB cluster. Which solution will meet these requirements in the MOST operationally efficient manner?
A. Create an AWS Config managed rule to detect unencrypted RDS storage. Configure an automatic remediation action to publish messages to an Amazon Simple Notification Service (Amazon SNS) topic that includes an AWS Lambda function and an email delivery target as subscribers. Configure the Lambda function to delete the unencrypted resource.
B. Create an AWS Config managed rule to detect unencrypted RDS storage. Configure a manual remediation action to invoke an AWS Lambda function. Configure the Lambda function to publish messages to an Amazon Simple Notification Service (Amazon SNS) topic and to delete the unencrypted resource.
C. Create an Amazon EventBridge rule that evaluates RDS event patterns and is initiated by the creation of DB instances or DB clusters. Configure the rule to publish messages to an Amazon Simple Notification Service (Amazon SNS) topic that includes an AWS Lambda function and an email delivery target as subscribers. Configure the Lambda function to delete the unencrypted resource.
D. Create an Amazon EventBridge rule that evaluates RDS event patterns and is initiated by the creation of DB instances or DB clusters. Configure the rule to invoke an AWS Lambda function. Configure the Lambda function to publish messages to an Amazon Simple Notification Service (Amazon SNS) topic and to delete the unencrypted resource.
A company has a strict policy against using root credentials. The company's security team wants to be alerted as soon as possible when root credentials are used to sign in to the AWS Management Console. How should the security team achieve this goal?
A. Use AWS Lambda to periodically query AWS CloudTrail for console login events and send alerts using Amazon Simple Notification Service (Amazon SNS).
B. Use Amazon EventBridge (Amazon CloudWatch Events) to monitor console logins and direct them to Amazon Simple Notification Service (Amazon SNS).
C. Use Amazon Athena to query AWS SSO logs and send alerts using Amazon Simple Notification Service (Amazon SNS) for root login events.
D. Configure AWS Resource Access Manager to review the access logs and send alerts using Amazon Simple Notification Service (Amazon SNS).
A company is using AWS Organizations to create OUs for its accounts. The company has more than 20 accounts that are all part of the OUs. A security engineer must implement a solution to ensure that no account can stop log file delivery to AWS CloudTrail. Which solution will meet this requirement?
A. Use the –is-multi-region-trail option while running the create-trail command to ensure that logs are configured across all AWS Regions.
B. Create an SCP that includes a Deny rule for the cloudtrail:StopLogging action. Apply the SCP to all accounts in the OUs.
C. Create an SCP that includes an Allow rule for the cloudtrail:StopLogging action. Apply the SCP to all accounts in the OUs.
D. Use AWS Systems Manager to ensure that CloudTrail is always turned on.
A company's security engineer is configuring Amazon S3 permissions to ban all current and future public buckets. However, the company hosts several websites directly off S3 buckets with public access enabled. The engineer needs to block the public S3 buckets without causing any outages on the existing websites. The engineer has set up an Amazon CloudFront distribution for each website. Which set of steps should the security engineer implement next?
A. Configure an S3 bucket as the origin with an origin access identity (OAI) for the CloudFront distribution. Switch the DNS records for websites to point to the CloudFront distribution. Enable block public access settings at the account level.
B. Configure an S3 bucket as the origin with an origin access identity (OAI) for the CloudFront distribution. Switch the DNS records for the websites to point to the CloudFront distribution. Then, for each S3 bucket, enable block public access settings.
C. Configure an S3 bucket as the origin with an origin access identity (OAI) for the CloudFront distribution. Enable block public access settings at the account level.
D. Configure an S3 bucket as the origin for the CloudFront distribution. Configure the S3 bucket policy to accept connections from the CloudFront points of presence only. Switch the DNS records for the websites to point to the CloudFront distribution. Enable block public access settings at the account level.
A company has a serverless application for internal users deployed on AWS. The application uses AWS Lambda for the front end and for business logic. The Lambda function accesses an Amazon RDS database inside a VPC. The company uses AWS Systems Manager Parameter Store for storing database credentials. A recent security review highlighted the following issues: ✑ The Lambda function has internet access. ✑ The relational database is publicly accessible. ✑ The database credentials are not stored in an encrypted state. Which combination of steps should the company take to resolve these security issues? (Choose three.)
A. Disable public access to the RDS database inside the VPC.
B. Move all the Lambda functions inside the VPC.
C. Edit the IAM role used by Lambda to restrict internet access.
D. Create a VPC endpoint for Systems Manager. Store the credentials as a string parameter. Change the parameter type to an advanced parameter.
E. Edit the IAM role used by RDS to restrict internet access.
F. Create a VPC endpoint for Systems Manager. Store the credentials as a SecureString parameter.
A company has an IAM group. All of the IAM users in the group have been assigned a multi-factor authentication (MFA) device and have full access to Amazon S3. The company needs to ensure that users in the group can perform S3 actions only after the users authenticate with MFA. A security engineer must design a solution that accomplishes this goal with the least maintenance overhead. Which combination of actions will meet these requirements? (Choose two.)
A. Add a customer managed Deny policy to users in the group for s3:*actions.
B. Add a customer managed Deny policy to the group for s3:*actions.
C. Add a customer managed Allow policy to the group for s3:*actions.
D. Add a condition to the policy: ג€Conditionג€ : { ג€BoolIfExistsג€ : { ג€aws:MultiFactorAuthPresentג€ : false } }
E. Add a condition to the policy: ג€Conditionג€ : { ג€Boolג€ : { ג€aws:MultiFactorAuthPresentג€ : false } }
Access Full SCS-C01 Exam Prep Free
Want to go beyond these 50 questions? Click here to unlock a full set of SCS-C01 exam prep free questions covering every domain tested on the exam.
We continuously update our content to ensure you have the most current and effective prep materials.
Good luck with your SCS-C01 certification journey!

