SC-300 Exam Prep Free – 50 Practice Questions to Get You Ready for Exam Day
Getting ready for the SC-300 certification? Our SC-300 Exam Prep Free resource includes 50 exam-style questions designed to help you practice effectively and feel confident on test day
Effective SC-300 exam prep free is the key to success. With our free practice questions, you can:
- Get familiar with exam format and question style
- Identify which topics you’ve mastered—and which need more review
- Boost your confidence and reduce exam anxiety
Below, you will find 50 realistic SC-300 Exam Prep Free questions that cover key exam topics. These questions are designed to reflect the structure and challenge level of the actual exam, making them perfect for your study routine.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft 365 tenant. All users must use the Microsoft Authenticator app for multi-factor authentication (MFA) when accessing Microsoft 365 services. Some users report that they received an MFA prompt on their Microsoft Authenticator app without initiating a sign-in request. You need to block the users automatically when they report an MFA request that they did not initiate. Solution: From the Azure portal, you configure the Account lockout settings for multi-factor authentication (MFA). Does this meet the goal?
A. Yes
B. No
You have a Microsoft 365 tenant. The Azure Active Directory (Azure AD) tenant syncs to an on-premises Active Directory domain. Users connect to the internet by using a hardware firewall at your company. The users authenticate to the firewall by using their Active Directory credentials. You plan to manage access to external applications by using Azure AD. You need to use the firewall logs to create a list of unmanaged external applications and the users who access them. What should you use to gather the information?
A. Application Insights in Azure Monitor
B. access reviews in Azure AD
C. Cloud App Discovery in Microsoft Cloud App Security
D. enterprise applications in Azure AD
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft 365 tenant. You have 100 IT administrators who are organized into 10 departments. You create the access review shown in the exhibit. (Click the Exhibit tab.)You discover that all access review requests are received by Megan Bowen. You need to ensure that the manager of each department receives the access reviews of their respective department. Solution: You add each manager as a fallback reviewer. Does this meet the goal?
A. Yes
B. No
Overview - ADatum Corporation is a consulting company in Montreal. ADatum recently acquired a Vancouver-based company named Litware, Inc. Existing Environment. ADatum Environment The on-premises network of ADatum contains an Active Directory Domain Services (AD DS) forest named adatum.com. ADatum has a Microsoft 365 E5 subscription. The subscription contains a verified domain that syncs with the adatum.com AD DS domain by using Azure AD Connect. ADatum has an Azure Active Directory (Azure AD) tenant named adatum.com. The tenant has Security defaults disabled. The tenant contains the users shown in the following table.The tenant contains the groups shown in the following table.
Existing Environment. Litware Environment Litware has an AD DS forest named litware.com Existing Environment. Problem Statements ADatum identifies the following issues: • Multiple users in the sales department have up to five devices. The sales department users report that sometimes they must contact the support department to join their devices to the Azure AD tenant because they have reached their device limit. • A recent security incident reveals that several users leaked their credentials, a suspicious browser was used for a sign-in, and resources were accessed from an anonymous IP address. • When you attempt to assign the Device Administrators role to IT_Group1, the group does NOT appear in the selection list. • Anyone in the organization can invite guest users, including other guests and non-administrators. • The helpdesk spends too much time resetting user passwords. • Users currently use only passwords for authentication. Requirements. Planned Changes - ADatum plans to implement the following changes: • Configure self-service password reset (SSPR). • Configure multi-factor authentication (MFA) for all users. • Configure an access review for an access package named Package1. • Require admin approval for application access to organizational data. • Sync the AD DS users and groups of litware.com with the Azure AD tenant. • Ensure that only users that are assigned specific admin roles can invite guest users. • Increase the maximum number of devices that can be joined or registered to Azure AD to 10. Requirements. Technical Requirements ADatum identifies the following technical requirements: • Users assigned the User administrator role must be able to request permission to use the role when needed for up to one year. • Users must be prompted to register for MFA and provided with an option to bypass the registration for a grace period. • Users must provide one authentication method to reset their password by using SSPR. Available methods must include: - Email - Phone - Security questions - The Microsoft Authenticator app • Trust relationships must NOT be established between the adatum.com and litware.com AD DS domains. • The principle of least privilege must be used. You need implement the planned changes for application access to organizational data. What should you configure?
A. authentication methods
B. the User consent settings
C. access packages
D. an application proxy
You have a Microsoft 365 tenant. All users have mobile phones and Windows 10 laptops. The users frequently work from remote locations that do not have Wi-Fi access or mobile phone connectivity. While working from the remote locations, the users connect their laptops to a wired network that has internet access. You plan to implement multi-factor authentication (MFA). Which MFA authentication method can the users use from the remote location?
A. a notification through the Microsoft Authenticator app
B. SMS
C. email
D. Windows Hello for Business
You have a Microsoft 365 tenant. All users have mobile phones and Windows 10 laptops. The users frequently work from remote locations that do not have Wi-Fi access or mobile phone connectivity. While working from the remote locations, the users connect their laptops to a wired network that has internet access. You plan to implement multi-factor authentication (MFA). Which MFA authentication method can the users use from the remote location?
A. voice
B. Windows Hello for Business
C. email
D. security questions
You have an Azure AD tenant that contains an access package named Package1 and a user named User1. Package1 is configured as shown in the following exhibit.You need to ensure that User1 can modify the review frequency of Package1. The solution must use the principle of least privilege. Which role should you assign to User1?
A. Security administrator
B. Privileged role administrator
C. External Identity Provider administrator
D. User administrator
You have an Azure Active Directory (Azure AD) tenant that contains the following objects: ✑ A device named Device1 ✑ Users named User1, User2, User3, User4, and User5 ✑ Groups named Group1, Group2, Group3, Group4, and Group5 The groups are configured as shown in the following table.To which groups can you assign a Microsoft Office 365 Enterprise E5 license directly?
A. Group1 and Group4 only
B. Group1, Group2, Group3, Group4, and Group5
C. Group1 and Group2 only
D. Group1 only
E. Group1, Group2, Group4, and Group5 only
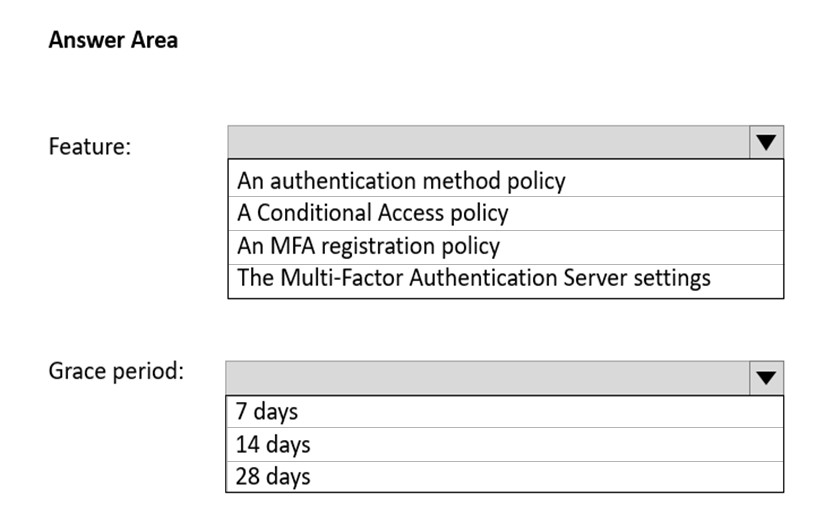
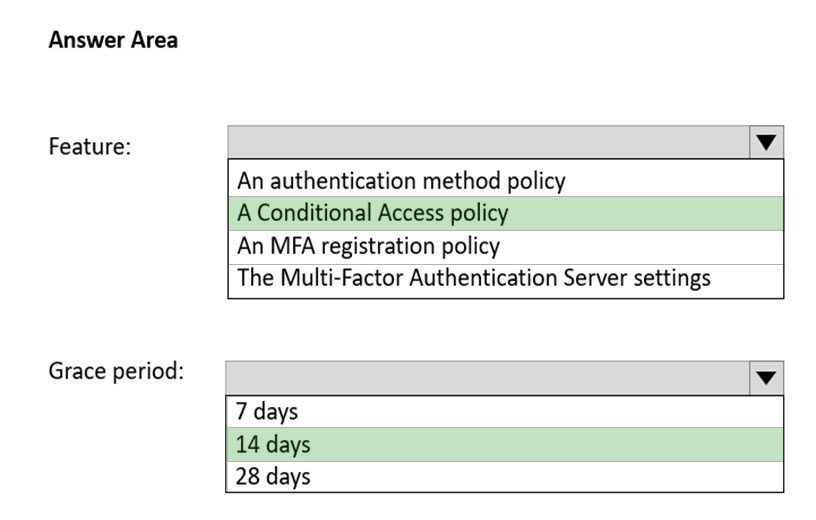
HOTSPOT - You need to support the planned changes and meet the technical requirements for MFA. Which feature should you use, and how long before the users must complete the registration? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
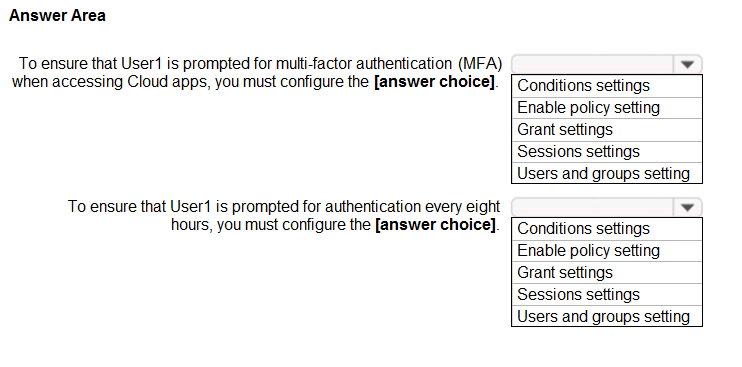
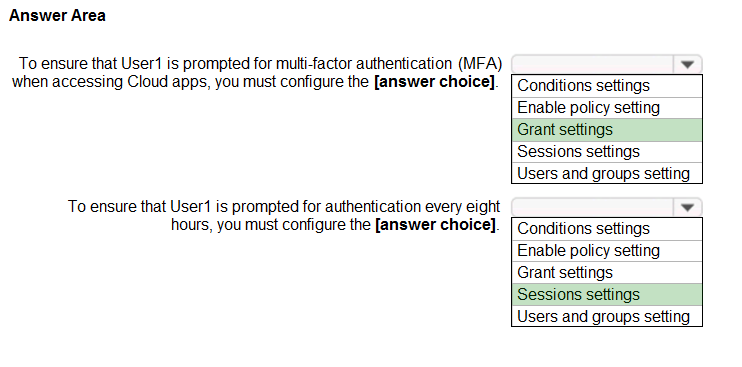
HOTSPOT - You have an Azure Active Directory (Azure AD) tenant that has Security defaults disabled. You are creating a conditional access policy as shown in the following exhibit.Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point. Hot Area:
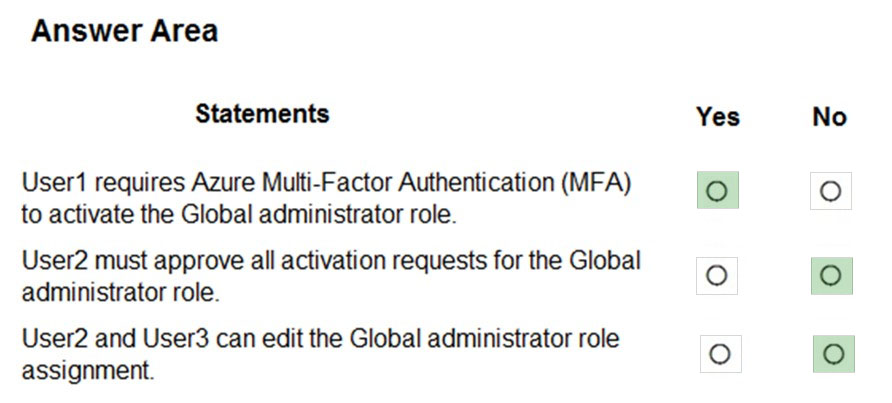
HOTSPOT - You have an Azure Active Directory (Azure AD) tenant contains the users shown in the following table.In Azure AD Privileged Identity Management (PIM), you configure the Global administrator role as shown in the following exhibit.
User1 is eligible for the Global administrator role. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
You have an Azure Active Directory (Azure AD) tenant. You open the risk detections report. Which risk detection type is classified as a user risk?
A. impossible travel
B. anonymous IP address
C. atypical travel
D. leaked credentials
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have an Amazon Web Services (AWS) account, a Google Workspace subscription, and a GitHub account. You deploy an Azure subscription and enable Microsoft 365 Defender. You need to ensure that you can monitor OAuth authentication requests by using Microsoft Defender for Cloud Apps. Solution: From the Microsoft 365 Defender portal, you add the GitHub app connector. Does this meet the goal?
A. Yes
B. No
You have an Azure AD tenant. You need to implement smart lockout with a lockout threshold of 10 failed sign-ins. What should you configure in the Azure AD admin center?
A. Authentication strengths
B. Password protection
C. User risk policy
D. Sign-in risk policy
You need to resolve the issue of the guest user invitations. What should you do for the Azure AD tenant?
A. Configure the Continuous access evaluation settings.
B. Configure a Conditional Access policy.
C. Configure the Access reviews settings.
D. Modify the External collaboration settings.
HOTSPOT - You have a Microsoft 365 E5 subscription. You need to configure app consent for the subscription. The solution must meet the following requirements: • Disable user consent to apps. • Configure admin consent workflow for apps. Which portal should you use for each requirement? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Cloud Apps and Conditional Access policies. You need to block access to cloud apps when a user is assessed as high risk. Which type of policy should you create in the Microsoft Defender for Cloud Apps portal?
A. access policy
B. OAuth app policy
C. anomaly detection policy
D. activity policy
DRAG DROP - Your network contains an on-premises Active Directory domain named contoso.com that syncs with Microsoft Entra ID by using Microsoft Entra Connect. The domain contains the users shown in the following table.From Active Directory Users and Computers, you add the following user: • Name: User3 • UPN: user3@contoso.com • Proxy addresses: smtp: user3@contoso.com , smtp: sales@contoso.com From Active Directory Users and Computers, you update the proxyAddresses attribute for each user as shown in the following table.
You trigger a manual synchronization. Which sync status will Microsoft Entra Connect sync return for each user? To answer, drag the appropriate status to the correct users. Each status may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription. You plan to deploy an app named App1 that will have the following configurations: • Will be registered in Microsoft Entra • Will access the signed-in user's Microsoft Outlook calendar by using the Microsoft Graph API You need to ensure that App1 can access Microsoft Graph. What should you use?
A. application permissions
B. delegated permissions
C. a custom role-based access control (RBAC) role
D. a built-in role-based access control (RBAC) role
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft 365 E5 subscription. You create a user named User1. You need to ensure that User1 can update the status of Identity Secure Score improvement actions. Solution: You assign the SharePoint Administrator role to User1. Does this meet the goal?
A. Yes
B. No
You have a Microsoft 365 tenant. All users have mobile phones and laptops. The users frequently work from remote locations that do not have Wi-Fi access or mobile phone connectivity. While working from the remote locations, the users connect their laptop to a wired network that has internet access. You plan to implement multi-factor authentication (MFA). Which MFA authentication method can the users use from the remote location?
A. a verification code from the Microsoft Authenticator app
B. security questions
C. voice
D. SMS
You have an Azure subscription that contains a resource group named RG1 and four users named User1, User2, User3, and User4. You plan to assign the users the following roles for RG1: • User1: Reader • User2: Contributor • User3: Storage Blob Data Reader • User4: Virtual Machine Contributor You are evaluating the use of attribute-based access control (ABAC). Which user's role will support the use of ABAC?
A. User1
B. User2
C. User3
D. User4
You need to sync the ADatum users. The solution must meet the technical requirements. What should you do?
A. From the Microsoft Azure Active Directory Connect wizard, select Customize synchronization options.
B. From PowerShell, run Set-ADSyncScheduler.
C. From PowerShell, run Start-ADSyncSyncCycle.
D. From the Microsoft Azure Active Directory Connect wizard, select Change user sign-in.
You have an Azure AD tenant that contains the users shown in the following table.You need to compare the role permissions of each user. The solution must minimize administrative effort. What should you use?
A. the Microsoft 365 Defender portal
B. the Microsoft 365 admin center
C. the Microsoft Entra admin center
D. the Microsoft Purview compliance portal
You have a Microsoft 365 E5 subscription that contains a web app named App1. Guest users are regularly granted access to App1. You need to ensure that the guest users that have NOT accessed App1 during the past 30 days have their access removed. The solution must minimize administrative effort. What should you configure?
A. a Conditional Access policy
B. a compliance policy
C. a guest access review
D. an access review for application access
You have a Microsoft 365 subscription that contains the following: ✑ An Azure Active Directory (Azure AD) tenant that has an Azure Active Directory Premium P2 license ✑ A Microsoft SharePoint Online site named Site1 ✑ A Microsoft Teams team named Team1 You need to create an entitlement management workflow to manage Site1 and Team1. What should you do first?
A. Configure an app registration.
B. Create an Administrative unit.
C. Create an access package.
D. Create a catalog.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft 365 E5 subscription. You create a user named User1. You need to ensure that User1 can update the status of Identity Secure Score improvement actions. Solution: You assign the Security Operator role to User1. Does this meet the goal?
A. Yes
B. No
You have a Microsoft 365 tenant. All users have mobile phones and Windows 10 laptops. The users frequently work from remote locations that do not have Wi-Fi access or mobile phone connectivity. While working from the remote locations, the users connect their laptop to a wired network that has internet access. You plan to implement multi-factor authentication (MFA). Which MFA authentication method can the users use from the remote location?
A. SMS
B. email
C. security questions
D. a verification code from the Microsoft Authenticator app
You have an Azure Active Directory (Azure AD) tenant. You configure self-service password reset (SSPR) by using the following settings: ✑ Require users to register when signing in: Yes ✑ Number of methods required to reset: 1 What is a valid authentication method available to users?
A. an email to an address outside your organization
B. a smartcard
C. an FID02 security token
D. a Microsoft Teams chat
HOTSPOT - You have an Azure subscription named Sub1 that contains a storage account named storage1. You need to deploy two apps named App1 and App2 that will have the following configurations: • App1 will be deployed as a registered app in Sub1. • App1 will access storage1 by using Microsoft Entra authentication. • App2 will access storage1 by using a single Microsoft Entra identity. • App2 be hosted on two new virtual machines named VM1 and VM2. The solution must minimize administrative effort. Which type of identity will each app use to access storage1? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have an Azure subscription that contains a user named User1. You need to meet the following requirements: • Prevent User1 from being added as an owner of newly registered apps. • Ensure that User1 can manage the application proxy settings. • Ensure that User1 can register apps. • Use the principle of least privilege. Which role should you assign to User1?
A. Application developer
B. Cloud application administrator
C. Service support administrator
D. Application administrator
You have a Microsoft 365 E5 subscription that contains a user named User1. User is eligible for the Application administrator role. User1 needs to configure a new connector group for an application proxy. What should you use to activate the role for User1?
A. the Microsoft Defender for Cloud Apps portal
B. the Microsoft 365 admin center
C. the Azure Active Directory admin center
D. the Microsoft 365 Defender portal
You have an Azure Active Directory (Azure AD) tenant that contains the users shown in the following table.You have an administrative unit named Au1. Group1, User2, and User3 are members of Au1. User5 is assigned the User administrator role for Au1. For which users can User5 reset passwords?
A. User1, User2, and User3
B. User1 and User2 only
C. User3 and User4 only
D. User2 and User3 only
HOTSPOT - You have a Microsoft 365 tenant. Sometimes, users use external, third-party applications that require limited access to the Microsoft 365 data of the respective user. The users register the applications in Azure AD. You need to receive an alert if a registered application gains read and write access to the users’ email. What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Cloud Apps. You need to identify which users access Facebook from their devices and browsers. The solution must minimize administrative effort. What should you do first?
A. From the Microsoft 365 Defender portal, unsanction Facebook.
B. Create a Defender for Cloud Apps access policy.
C. Create an app configuration policy in Microsoft Intune.
D. Create a Conditional Access policy.
HOTSPOT - You have a Microsoft 365 tenant that has 5,000 users. One hundred of the users are executives. The executives have a dedicated support team. You need to ensure that the support team can reset passwords and manage multi-factor authentication (MFA) settings for only the executives. The solution must use the principle of least privilege. Which object type and Azure Active Directory (Azure AD) role should you use? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft 365 tenant. You have 100 IT administrators who are organized into 10 departments. You create the access review shown in the exhibit. (Click the Exhibit tab.)You discover that all access review requests are received by Megan Bowen. You need to ensure that the manager of each department receives the access reviews of their respective department. Solution: You set Reviewers to Member (self). Does this meet the goal?
A. Yes
B. No
You have an Azure AD tenant. You deploy a new enterprise application named App1. When users attempt to provide App1 with access to the tenant, the attempt fails. You need to ensure that the users can request admin consent for App1. The solution must follow the principle of least privilege. What should you do first?
A. Enable admin consent requests for the tenant.
B. Designate a reviewer of admin consent requests for the tenant.
C. From the Permissions settings of App1, grant App1 admin consent for the tenant.
D. Create a Conditional Access policy for App1.
HOTSPOT - You have an Azure AD tenant. You perform the tasks shown in the following table.On April 5, an administrator deletes App1, App2, App3, and App4. You need to restore the apps and the settings. Which apps can you restore on April 16, and which settings can you restore for App4 on April 16? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Your company has an Azure AD tenant that contains a user named User1. The company has two departments named marketing and finance. You need to grant permissions to User1 to manage only the users in the marketing department. The solution must ensure that User1 does NOT have permissions to manage the users in the finance department. What should you create first?
A. a management group
B. an administrative unit
C. a resource group
D. a Microsoft 365 group
HOTSPOT - You have a Microsoft 365 E5 subscription that contains the users shown in the following table.The users are assigned the roles shown in the following table.
For which users can User1 and User4 reset passwords? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint Online site named Site1. You need to ensure that users can request access to Site1. The solution must meet the following requirements: • Automatically approve requests from users based on their group membership. • Automatically remove the access after 30 days. What should you do?
A. Create a Conditional Access policy.
B. Create an access package.
C. Configure Role settings in Azure AD Privileged Identity Management.
D. Create a Microsoft Defender for Cloud Apps access policy.
You have a Microsoft 365 tenant. In Azure Active Directory (Azure AD), you configure the terms of use. You need to ensure that only users who accept the terms of use can access the resources in the tenant. Other users must be denied access. What should you configure?
A. an access policy in Microsoft Cloud App Security.
B. Terms and conditions in Microsoft Endpoint Manager.
C. a conditional access policy in Azure AD
D. a compliance policy in Microsoft Endpoint Manager
The Azure Active Directory (Azure AD) tenant contains the groups shown in the following table.In Azure AD, you add a new enterprise application named App1. Which groups can you assign to App1?
A. Group1 only
B. Group2 only
C. Group3 only
D. Group1 and Group4
E. Group1 and Group3
You have 2,500 users who are assigned Microsoft Office 365 Enterprise E3 licenses. The licenses are assigned to individual users. From the Groups blade in the Microsoft Entra admin center, you assign Microsoft Office 365 Enterprise E5 licenses to a group that includes all users. You need to remove the Office 365 Enterprise E3 licenses from the users by using the least amount of administrative effort. What should you use?
A. the Licenses blade in the Microsoft Entra admin center
B. the Administrative units blade in the Microsoft Entra admin center
C. the Identity Governance blade in the Microsoft Entra admin center
D. the Update-MgUser cmdlet
HOTSPOT - You have a hybrid Microsoft 365 subscription that contains the users shown in the following table.You plan to deploy an on-premises app named App1. App1 will be registered in Azure AD and will use Azure AD Application Proxy. You need to delegate the installation of the Application Proxy connector and ensure that User1 can register App1 in Azure AD. The solution must use the principle of least privilege. Which user should perform the installation, and which role should you assign to User1? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have an Azure Active Directory (Azure AD) tenant that contains cloud-based enterprise apps. You need to group related apps into categories in the My Apps portal. What should you create?
A. tags
B. collections
C. naming policies
D. dynamic groups
Your company recently implemented Azure Active Directory (Azure AD) Privileged Identity Management (PIM). While you review the roles in PIM, you discover that all 15 users in the IT department at the company have permanent security administrator rights. You need to ensure that the IT department users only have access to the Security administrator role when required. What should you configure for the Security administrator role assignment?
A. Expire eligible assignments after from the Role settings details
B. Expire active assignments after from the Role settings details
C. Assignment type to Active
D. Assignment type to Eligible
You have an Azure subscription named Sub1 that uses Microsoft Entra Permissions Management. Sub1 contains a user named User1. User1 is granted multiple permissions across Sub1. You need to replace all the permissions granted to User1 with read-only permissions. The solution must minimize administrative effort. What should you do on the Remediation tab in Permissions Management?
A. From the Role/Policy Template subtab, create a template.
B. From the My Requests subtab, create a new request.
C. From the Roles/Policies subtab, create a role.
D. From the Permissions subtab, use a quick action.
You have an Azure AD tenant that contains the external user shown in the following exhibit.You update the email address of the user. You need to ensure that the user can authenticate by using the updated email address. What should you do for the user?
A. Modify the Authentication methods settings.
B. Reset the password.
C. Revoke the active sessions.
D. Reset the redemption status.
Access Full SC-300 Exam Prep Free
Want to go beyond these 50 questions? Click here to unlock a full set of SC-300 exam prep free questions covering every domain tested on the exam.
We continuously update our content to ensure you have the most current and effective prep materials.
Good luck with your SC-300 certification journey!