SC-100 Exam Prep Free – 50 Practice Questions to Get You Ready for Exam Day
Getting ready for the SC-100 certification? Our SC-100 Exam Prep Free resource includes 50 exam-style questions designed to help you practice effectively and feel confident on test day
Effective SC-100 exam prep free is the key to success. With our free practice questions, you can:
- Get familiar with exam format and question style
- Identify which topics you’ve mastered—and which need more review
- Boost your confidence and reduce exam anxiety
Below, you will find 50 realistic SC-100 Exam Prep Free questions that cover key exam topics. These questions are designed to reflect the structure and challenge level of the actual exam, making them perfect for your study routine.
You have an Azure subscription that contains virtual machines, storage accounts, and Azure SQL databases. All resources are backed up multiple times a day by using Azure Backup. You are developing a strategy to protect against ransomware attacks. You need to recommend which controls must be enabled to ensure that Azure Backup can be used to restore the resources in the event of a successful ransomware attack. Which two controls should you include in the recommendation? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. Enable soft delete for backups.
B. Require PINs for critical operations.
C. Encrypt backups by using customer-managed keys (CMKs).
D. Perform offline backups to Azure Data Box.
E. Use Azure Monitor notifications when backup configurations change.
You are planning the security requirements for Azure Cosmos DB Core (SQL) API accounts. You need to recommend a solution to audit all users that access the data in the Azure Cosmos DB accounts. Which two configurations should you include in the recommendation? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Send the Azure Active Directory (Azure AD) sign-in logs to a Log Analytics workspace.
B. Enable Microsoft Defender for Identity.
C. Send the Azure Cosmos DB logs to a Log Analytics workspace.
D. Disable local authentication for Azure Cosmos DB.
E. Enable Microsoft Defender for Cosmos DB.
To meet the application security requirements, which two authentication methods must the applications support? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. Security Assertion Markup Language (SAML)
B. NTLMv2
C. certificate-based authentication
D. Kerberos
You are designing security for an Azure landing zone. Your company identifies the following compliance and privacy requirements: ✑ Encrypt cardholder data by using encryption keys managed by the company. ✑ Encrypt insurance claim files by using encryption keys hosted on-premises. Which two configurations meet the compliance and privacy requirements? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Store the cardholder data in an Azure SQL database that is encrypted by using Microsoft-managed keys.
B. Store the insurance claim data in Azure Blob storage encrypted by using customer-provided keys.
C. Store the cardholder data in an Azure SQL database that is encrypted by using keys stored in Azure Key Vault Managed HSM.
D. Store the insurance claim data in Azure Files encrypted by using Azure Key Vault Managed HSM.
You design cloud-based software as a service (SaaS) solutions. You need to recommend a recovery solution for ransomware attacks. The solution must follow Microsoft Security Best Practices. What should you recommend doing first?
A. Develop a privileged identity strategy.
B. Implement data protection.
C. Develop a privileged access strategy.
D. Prepare a recovery plan.
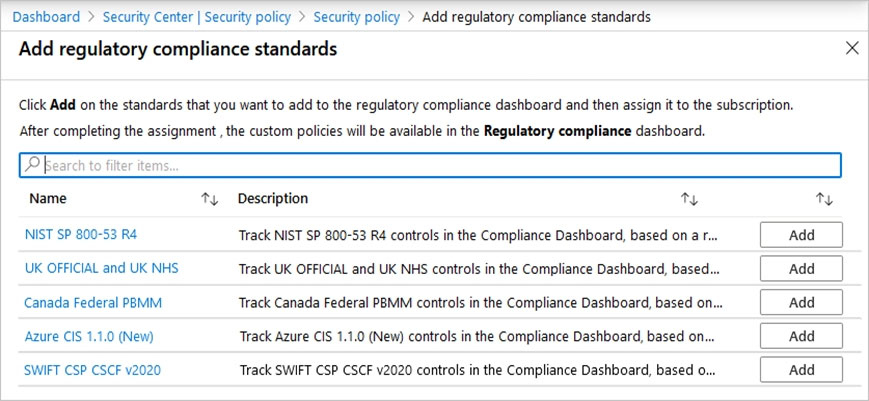
Your company has an Azure subscription that has enhanced security enabled for Microsoft Defender for Cloud. The company signs a contract with the United States government. You need to review the current subscription for NIST 800-53 compliance. What should you do first?
A. From Defender for Cloud, review the secure score recommendations.
B. From Microsoft Sentinel, configure the Microsoft Defender for Cloud data connector.
C. From Defender for Cloud, review the Azure security baseline for audit report.
D. From Defender for Cloud, add a regulatory compliance standard.
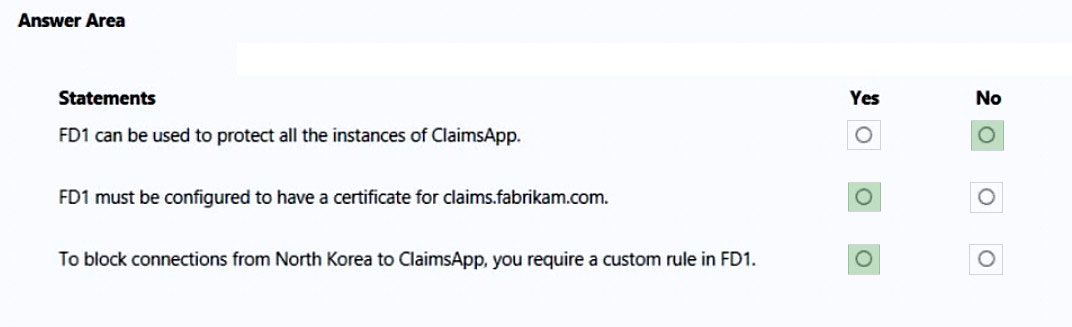
HOTSPOT - You are evaluating the security of ClaimsApp. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
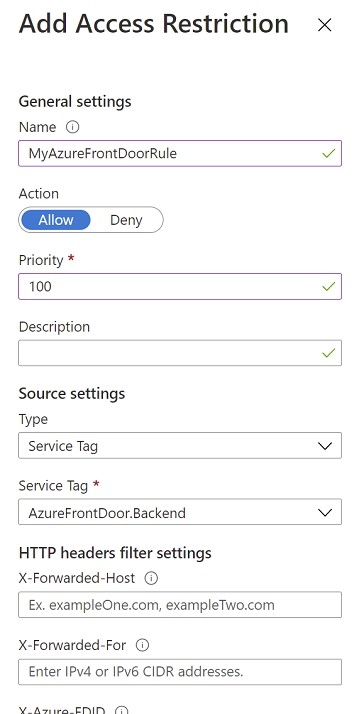
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You are designing a security strategy for providing access to Azure App Service web apps through an Azure Front Door instance. You need to recommend a solution to ensure that the web apps only allow access through the Front Door instance. Solution: You recommend access restrictions based on HTTP headers that have the Front Door ID. Does this meet the goal?
A. Yes
B. No
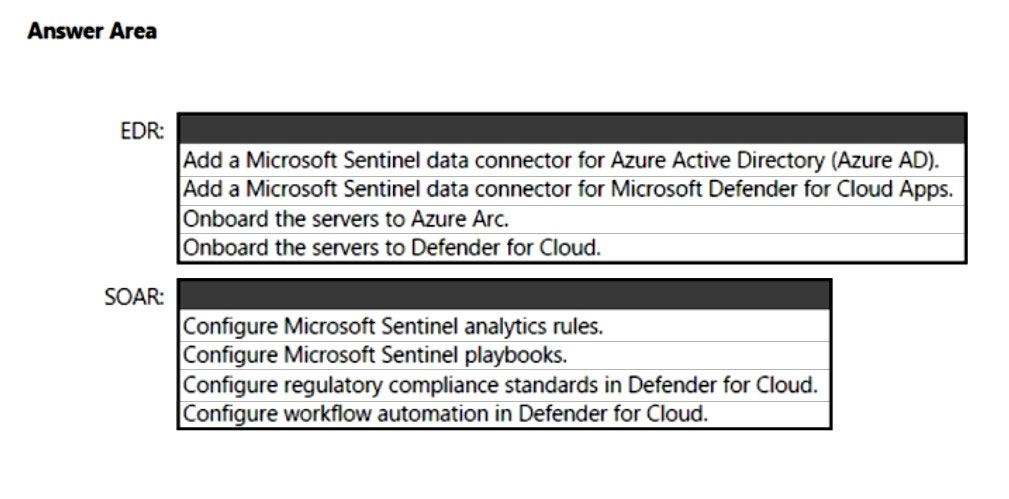
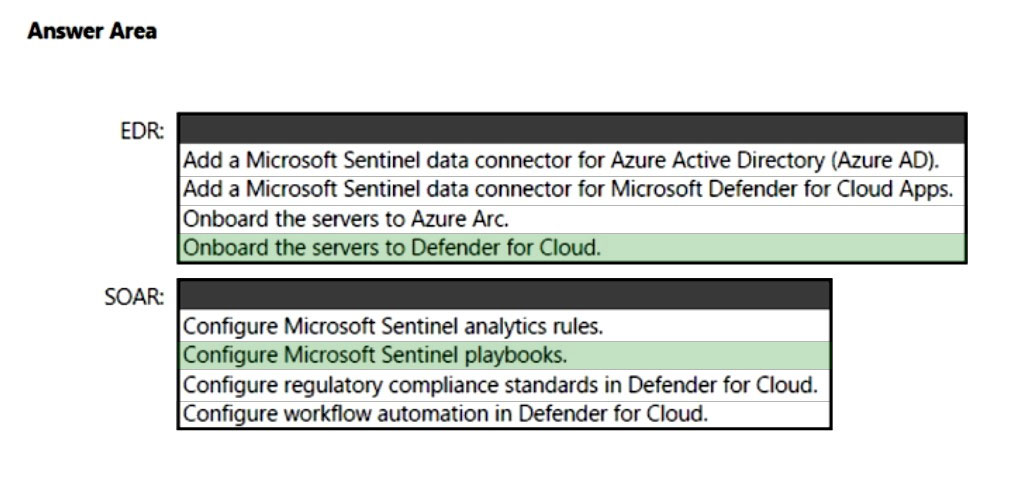
HOTSPOT - You have a Microsoft 365 subscription and an Azure subscription. Microsoft 365 Defender and Microsoft Defender for Cloud are enabled. The Azure subscription contains a Microsoft Sentinel workspace. Microsoft Sentinel data connectors are configured for Microsoft 365, Microsoft 365 Defender, Defender for Cloud, and Azure. You plan to deploy Azure virtual machines that will run Windows Server. You need to enable extended detection and response (EDR) and security orchestration, automation, and response (SOAR) capabilities for Microsoft Sentinel. How should you recommend enabling each capability? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
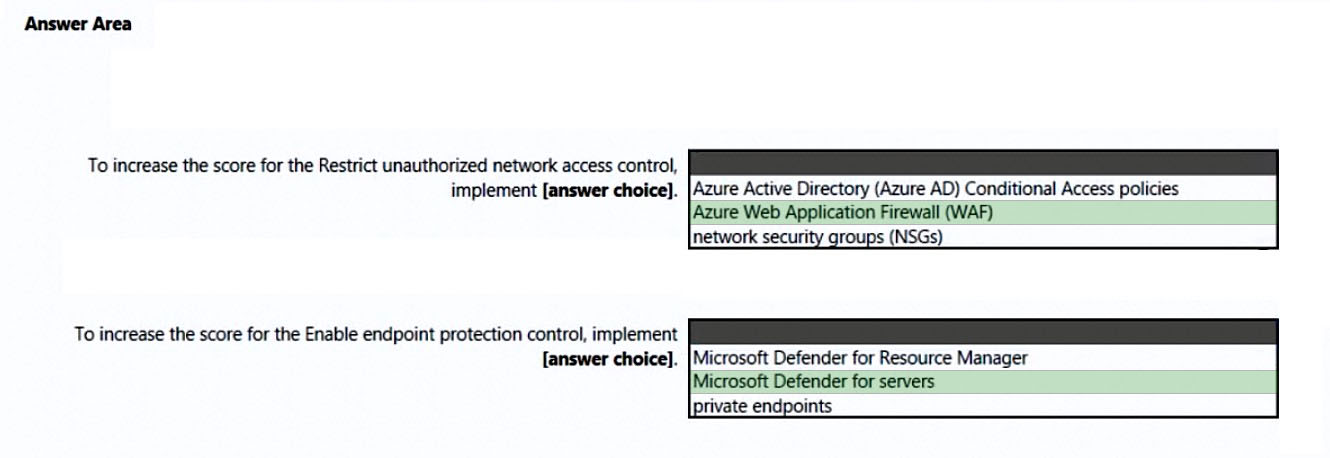
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have an Azure subscription that has Microsoft Defender for Cloud enabled. You are evaluating the Azure Security Benchmark V3 report. In the Secure management ports controls, you discover that you have 0 out of a potential 8 points. You need to recommend configurations to increase the score of the Secure management ports controls. Solution: You recommend enabling adaptive network hardening. Does this meet the goal?
A. Yes
B. No
HOTSPOT - You have a Microsoft 365 E5 subscription that uses Microsoft Exchange Online. You need to recommend a solution to prevent malicious actors from impersonating the email addresses of internal senders. What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Your company has the virtual machine infrastructure shown in the following table.The company plans to use Microsoft Azure Backup Server (MABS) to back up the virtual machines to Azure. You need to provide recommendations to increase the resiliency of the backup strategy to mitigate attacks such as ransomware. What should you include in the recommendation?
A. Use geo-redundant storage (GRS).
B. Maintain multiple copies of the virtual machines.
C. Encrypt the backups by using customer-managed keys (CMKS).
D. Require PINs to disable backups.
Your company has a Microsoft 365 subscription and uses Microsoft Defender for Identity. You are informed about incidents that relate to compromised identities. You need to recommend a solution to expose several accounts for attackers to exploit. When the attackers attempt to exploit the accounts, an alert must be triggered. Which Defender for Identity feature should you include in the recommendation?
A. sensitivity labels
B. custom user tags
C. standalone sensors
D. honeytoken entity tags
Your company is developing an invoicing application that will use Azure Active Directory (Azure AD) B2C. The application will be deployed as an App Service web app. You need to recommend a solution to the application development team to secure the application from identity-related attacks. Which two configurations should you recommend? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Azure AD workbooks to monitor risk detections
B. Azure AD Conditional Access integration with user flows and custom policies
C. smart account lockout in Azure AD B2C
D. access packages in Identity Governance
E. custom resource owner password credentials (ROPC) flows in Azure AD B2C
Your company plans to evaluate the security of its Azure environment based on the principles of the Microsoft Cloud Adoption Framework for Azure. You need to recommend a cloud-based service to evaluate whether the Azure resources comply with the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF). What should you recommend?
A. Compliance Manager in Microsoft Purview
B. Microsoft Defender for Cloud
C. Microsoft Sentinel
D. Microsoft Defender for Cloud Apps
Your company has a third-party security information and event management (SIEM) solution that uses Splunk and Microsoft Sentinel. You plan to integrate Microsoft Sentinel with Splunk. You need to recommend a solution to send security events from Microsoft Sentinel to Splunk. What should you include in the recommendation?
A. a Microsoft Sentinel data connector
B. Azure Event Hubs
C. a Microsoft Sentinel workbook
D. Azure Data Factory
Your company is developing a serverless application in Azure that will have the architecture shown in the following exhibit.You need to recommend a solution to isolate the compute components on an Azure virtual network. What should you include in the recommendation?
A. Azure Active Directory (Azure AD) enterprise applications
B. an Azure App Service Environment (ASE)
C. Azure service endpoints
D. an Azure Active Directory (Azure AD) application proxy
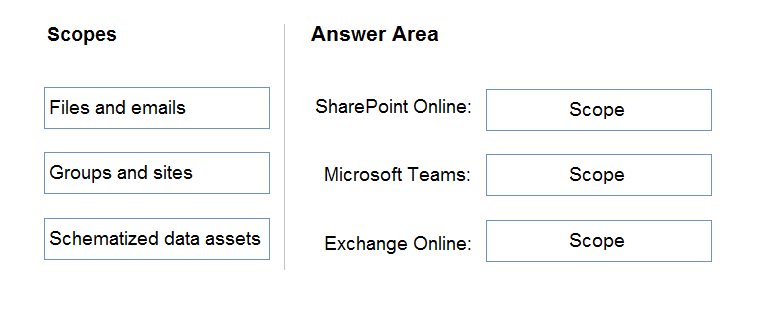
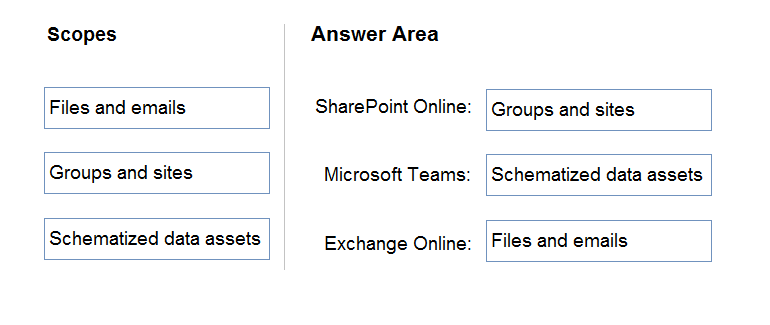
DRAG DROP - Your company has Microsoft 365 E5 licenses and Azure subscriptions. The company plans to automatically label sensitive data stored in the following locations: ✑ Microsoft SharePoint Online ✑ Microsoft Exchange Online ✑ Microsoft Teams You need to recommend a strategy to identify and protect sensitive data. Which scope should you recommend for the sensitivity label policies? To answer, drag the appropriate scopes to the correct locations. Each scope may only be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point. Select and Place:
You have an Azure subscription that has Microsoft Defender for Cloud enabled. Suspicious authentication activity alerts have been appearing in the Workload protections dashboard. You need to recommend a solution to evaluate and remediate the alerts by using workflow automation. The solution must minimize development effort. What should you include in the recommendation?
A. Azure Monitor webhooks
B. Azure Event Hubs
C. Azure Functions apps
D. Azure Logics Apps
Your company has an on-premises network, an Azure subscription, and a Microsoft 365 E5 subscription. The company uses the following devices: ✑ Computers that run either Windows 10 or Windows 11 ✑ Tablets and phones that run either Android or iOS You need to recommend a solution to classify and encrypt sensitive Microsoft Office 365 data regardless of where the data is stored. What should you include in the recommendation?
A. eDiscovery
B. Microsoft Information Protection
C. Compliance Manager
D. retention policies
Your company develops several applications that are accessed as custom enterprise applications in Azure Active Directory (Azure AD). You need to recommend a solution to prevent users on a specific list of countries from connecting to the applications. What should you include in the recommendation?
A. activity policies in Microsoft Defender for Cloud Apps
B. sign-in risk policies in Azure AD Identity Protection
C. Azure AD Conditional Access policies
D. device compliance policies in Microsoft Endpoint Manager
E. user risk poticies in Azure AD Identity Protection
You have an Azure subscription. You have a DNS domain named contoso.com that is hosted by a third-party DNS registrar. Developers use Azure DevOps to deploy web apps to App Service Environments. When a new app is deployed, a CNAME record for the app is registered in contoso.com. You need to recommend a solution to secure the DNS record for each web app. The solution must meet the following requirements: • Ensure that when an app is deleted, the CNAME record for the app is removed also. • Minimize administrative effort. What should you include in the recommendation?
A. Microsoft Defender for Cloud Apps
B. Microsoft Defender for DevOps
C. Microsoft Defender for App Service
D. Microsoft Defender for DNS
Your company has an Azure subscription that has enhanced security enabled for Microsoft Defender for Cloud. The company signs a contract with the United States government. You need to review the current subscription for NIST 800-53 compliance. What should you do first?
A. From Azure Policy, assign a built-in initiative that has a scope of the subscription.
B. From Microsoft Sentinel, configure the Microsoft Defender for Cloud data connector.
C. From Defender for Cloud, review the Azure security baseline for audit report.
D. From Microsoft Defender for Cloud Apps, create an access policy for cloud applications.
For an Azure deployment, you are designing a security architecture based on the Microsoft Cloud Security Benchmark. You need to recommend a best practice for implementing service accounts for Azure API management. What should you include in the recommendation?
A. application registrations in Azure AD
B. managed identities in Azure
C. Azure service principals with usernames and passwords
D. device registrations in Azure AD
E. Azure service principals with certificate credentials
You have a Microsoft 365 subscription and an Azure subscription. Microsoft 365 Defender and Microsoft Defender for Cloud are enabled. The Azure subscription contains 50 virtual machines. Each virtual machine runs different applications on Windows Server 2019. You need to recommend a solution to ensure that only authorized applications can run on the virtual machines. If an unauthorized application attempts to run or be installed, the application must be blocked automatically until an administrator authorizes the application. Which security control should you recommend?
A. Azure AD Conditional Access App Control policies
B. Azure Security Benchmark compliance controls in Defender for Cloud
C. app protection policies in Microsoft Endpoint Manager
D. application control policies in Microsoft Defender for Endpoint
Your company has an Azure subscription that has enhanced security enabled for Microsoft Defender for Cloud. The company signs a contract with the United States government. You need to review the current subscription for NIST 800-53 compliance. What should you do first?
A. From Azure Policy, assign a built-in initiative that has a scope of the subscription.
B. From Azure Policy, assign a built-in policy definition that has a scope of the subscription.
C. From Defender for Cloud, review the Azure security baseline for audit report.
D. From Microsoft Defender for Cloud Apps, create an access policy for cloud applications.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You are designing a security strategy for providing access to Azure App Service web apps through an Azure Front Door instance. You need to recommend a solution to ensure that the web apps only allow access through the Front Door instance. Solution: You recommend configuring gateway-required virtual network integration. Does this meet the goal?
A. Yes
B. No
You need to design a strategy for securing the SharePoint Online and Exchange Online data. The solution must meet the application security requirements. Which two services should you leverage in the strategy? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Azure AD Conditional Access
B. access reviews in Azure AD
C. Microsoft Defender for Cloud
D. Microsoft Defender for Cloud Apps
E. Microsoft Defender for Endpoint
You have a Microsoft 365 tenant. Your company uses a third-party software as a service (SaaS) app named App1 that is integrated with an Azure AD tenant. You need to design a security strategy to meet the following requirements: • Users must be able to request access to App1 by using a self-service request. • When users request access to App1, they must be prompted to provide additional information about their request. • Every three months, managers must verify that the users still require access to App1. What should you include in the design?
A. Microsoft Entra Identity Governance
B. connected apps in Microsoft Defender for Cloud Apps
C. access policies in Microsoft Defender for Cloud Apps
D. Azure AD Application Proxy
Your company has a Microsoft 365 E5 subscription. The company wants to identify and classify data in Microsoft Teams, SharePoint Online, and Exchange Online. You need to recommend a solution to identify documents that contain sensitive information. What should you include in the recommendation?
A. data classification content explorer
B. data loss prevention (DLP)
C. eDiscovery
D. Information Governance
You have a Microsoft 365 E5 subscription. You are designing a solution to protect confidential data in Microsoft SharePoint Online sites that contain more than one million documents. You need to recommend a solution to prevent Personally Identifiable Information (PII) from being shared. Which two components should you include in the recommendation? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. data loss prevention (DLP) policies
B. retention label policies
C. eDiscovery cases
D. sensitivity label policies
Your company has on-premises Microsoft SQL Server databases. The company plans to move the databases to Azure. You need to recommend a secure architecture for the databases that will minimize operational requirements for patching and protect sensitive data by using dynamic data masking. The solution must minimize costs. What should you include in the recommendation?
A. Azure SQL Managed Instance
B. Azure Synapse Analytics dedicated SQL pools
C. Azure SQL Database
D. SQL Server on Azure Virtual Machines
You have an Azure subscription that contains a Microsoft Sentinel workspace. Your on-premises network contains firewalls that support forwarding event logs in the Common Event Format (CEF). There is no built-in Microsoft Sentinel connector for the firewalls. You need to recommend a solution to ingest events from the firewalls into Microsoft Sentinel. What should you include in the recommendation?
A. an Azure logic app
B. an on-premises Syslog server
C. an on-premises data gateway
D. Azure Data Factory
HOTSPOT - You open Microsoft Defender for Cloud as shown in the following exhibit.Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point. Hot Area:
Your company finalizes the adoption of Azure and is implementing Microsoft Defender for Cloud. You receive the following recommendations in Defender for Cloud ✑ Access to storage accounts with firewall and virtual network configurations should be restricted. ✑ Storage accounts should restrict network access using virtual network rules. ✑ Storage account should use a private link connection. ✑ Storage account public access should be disallowed. You need to recommend a service to mitigate identified risks that relate to the recommendations. What should you recommend?
A. Azure Policy
B. Azure Network Watcher
C. Azure Storage Analytics
D. Microsoft Sentinel
Your company has an Azure subscription that uses Azure Storage. The company plans to share specific blobs with vendors. You need to recommend a solution to provide the vendors with secure access to specific blobs without exposing the blobs publicly. The access must be time- limited. What should you include in the recommendation?
A. Configure private link connections.
B. Configure encryption by using customer-managed keys (CMKs).
C. Share the connection string of the access key.
D. Create shared access signatures (SAS).
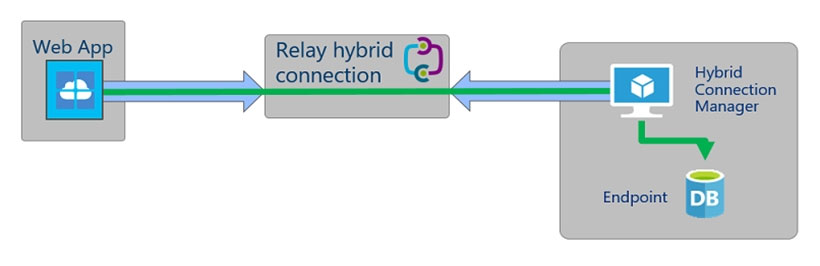
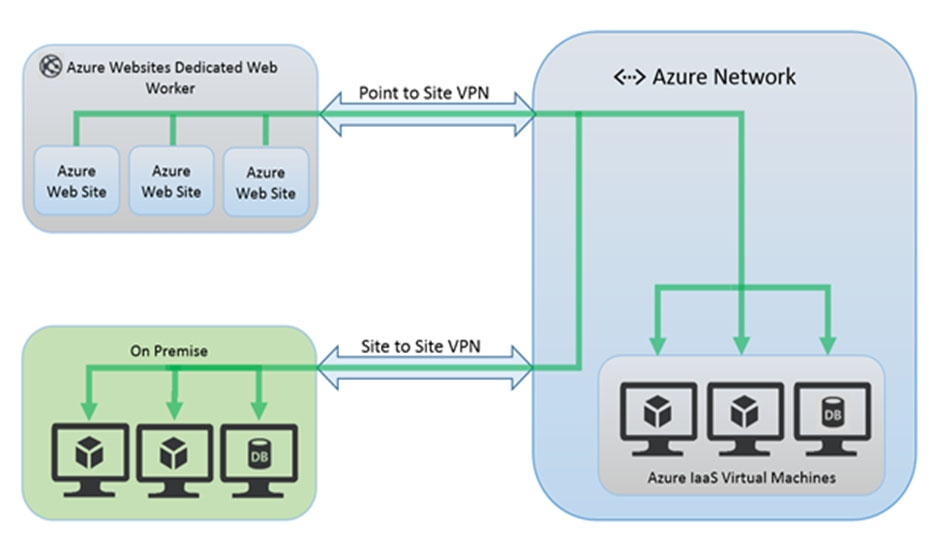
Your company has an on-premises network and an Azure subscription. The company does NOT have a Site-to-Site VPN or an ExpressRoute connection to Azure. You are designing the security standards for Azure App Service web apps. The web apps will access Microsoft SQL Server databases on the network. You need to recommend security standards that will allow the web apps to access the databases. The solution must minimize the number of open internet- accessible endpoints to the on-premises network. What should you include in the recommendation?
A. virtual network NAT gateway integration
B. hybrid connections
C. virtual network integration
D. a private endpoint
You are designing the security standards for containerized applications onboarded to Azure. You are evaluating the use of Microsoft Defender for Containers. In which two environments can you use Defender for Containers to scan for known vulnerabilities? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. Linux containers deployed to Azure Container Instances
B. Windows containers deployed to Azure Kubernetes Service (AKS)
C. Windows containers deployed to Azure Container Registry
D. Linux containers deployed to Azure Container Registry
E. Linux containers deployed to Azure Kubernetes Service (AKS)
Your company has an office in Seattle. The company has two Azure virtual machine scale sets hosted on different virtual networks. The company plans to contract developers in India. You need to recommend a solution provide the developers with the ability to connect to the virtual machines over SSL from the Azure portal. The solution must meet the following requirements: ✑ Prevent exposing the public IP addresses of the virtual machines. ✑ Provide the ability to connect without using a VPN. ✑ Minimize costs. Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Create a hub and spoke network by using virtual network peering.
B. Deploy Azure Bastion to each virtual network.
C. Deploy Azure Bastion to one virtual network.
D. Create NAT rules and network rules in Azure Firewall.
E. Enable just-in-time VM access on the virtual machines.
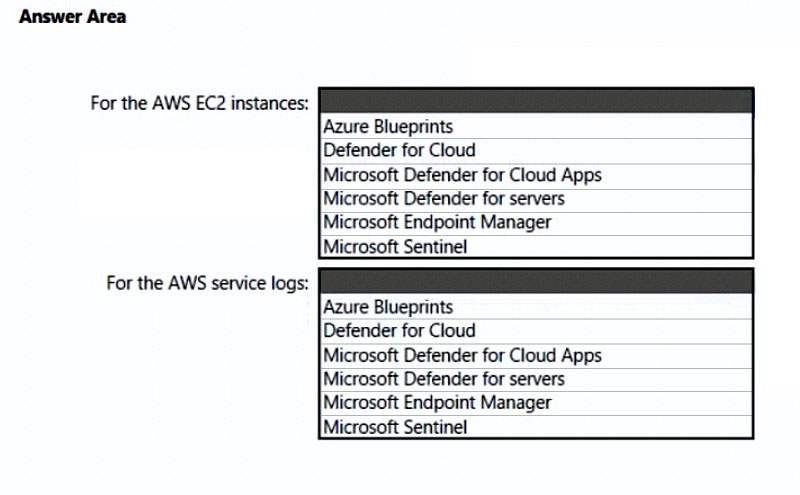
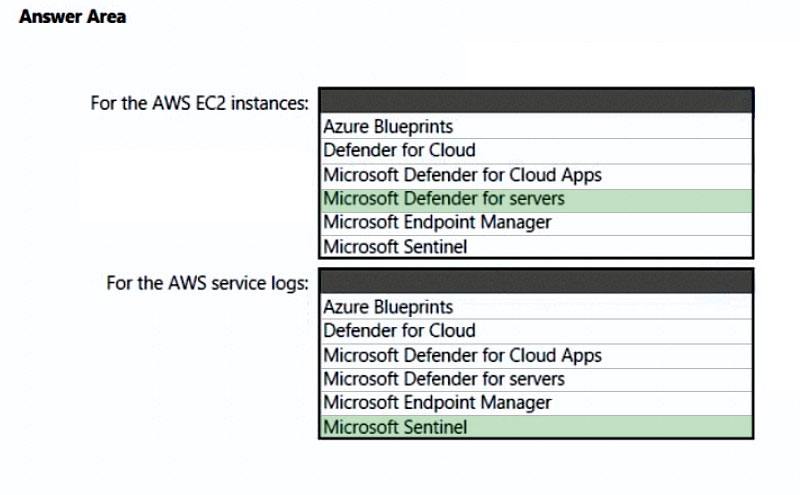
HOTSPOT - You need to recommend a solution to meet the AWS requirements. What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You are designing the encryption standards for data at rest for an Azure resource. You need to provide recommendations to ensure that the data at rest is encrypted by using AES-256 keys. The solution must support rotating the encryption keys monthly. Solution: For blob containers in Azure Storage, you recommend encryption that uses customer-managed keys (CMKs). Does this meet the goal?
A. Yes
B. No
You have an Azure subscription that has Microsoft Defender for Cloud enabled. You have an Amazon Web Services (AWS) implementation. You plan to extend the Azure security strategy to the AWS implementation. The solution will NOT use Azure Arc. Which three services can you use to provide security for the AWS resources? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. Microsoft Defender for Containers
B. Microsoft Defender for servers
C. Azure Active Directory (Azure AD) Conditional Access
D. Azure Active Directory (Azure AD) Privileged Identity Management (PIM)
E. Azure Policy
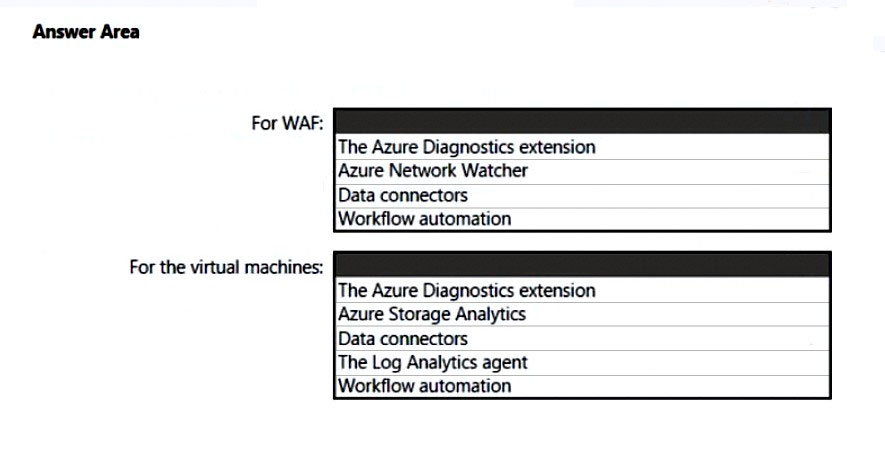
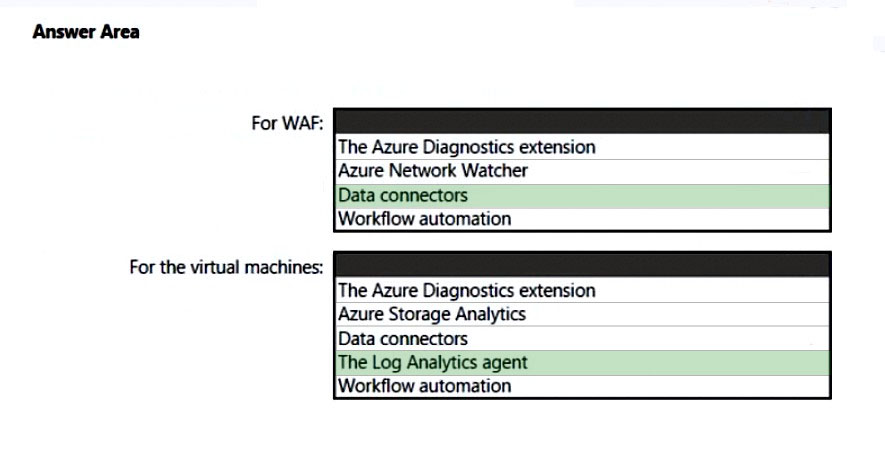
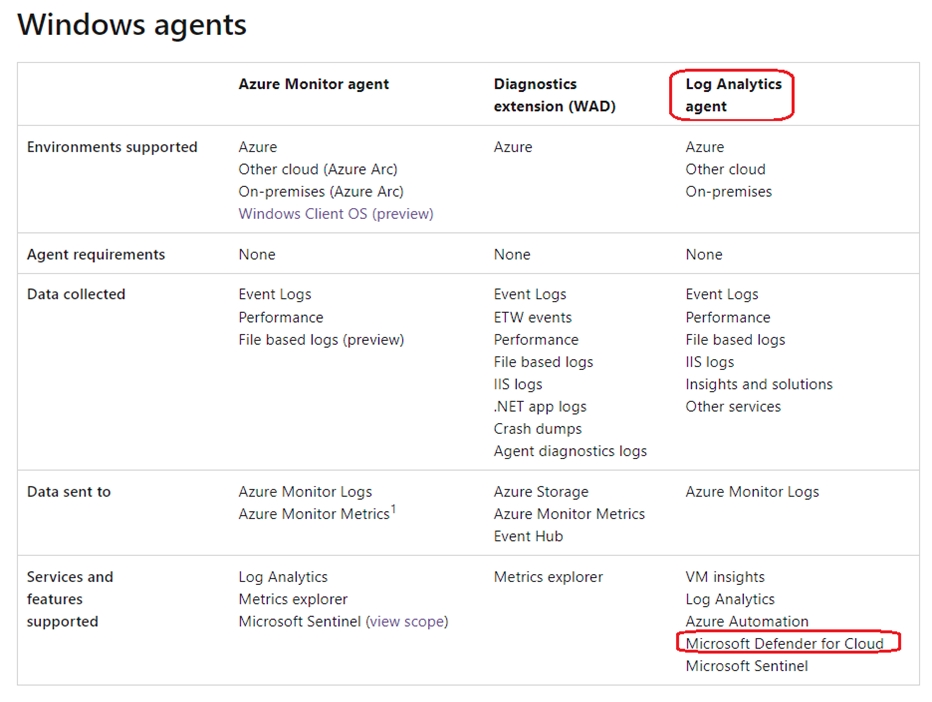
HOTSPOT - Your company uses Microsoft Defender for Cloud and Microsoft Sentinel. The company is designing an application that will have the architecture shown in the following exhibit.You are designing a logging and auditing solution for the proposed architecture. The solution must meet the following requirements: ✑ Integrate Azure Web Application Firewall (WAF) logs with Microsoft Sentinel. ✑ Use Defender for Cloud to review alerts from the virtual machines. What should you include in the solution? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - You are designing the security architecture for a cloud-only environment. You are reviewing the integration point between Microsoft 365 Defender and other Microsoft cloud services based on Microsoft Cybersecurity Reference Architectures (MCRA). You need to recommend which Microsoft cloud services integrate directly with Microsoft 365 Defender and meet the following requirements: • Enforce data loss prevention (DLP) policies that can be managed directly from the Microsoft 365 Defender portal. • Detect and respond to security threats based on User and Entity Behavior Analytics (UEBA) with unified alerting. What should you include in the recommendation for each requirement? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
HOTSPOT - You need to recommend a security methodology for a DevOps development process based on the Microsoft Cloud Adoption Framework for Azure. During which stage of a continuous integration and continuous deployment (CI/CD) DevOps process should each security-related task be performed? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Your company plans to provision blob storage by using an Azure Storage account. The blob storage will be accessible from 20 application servers on the internet. You need to recommend a solution to ensure that only the application servers can access the storage account. What should you recommend using to secure the blob storage?
A. managed rule sets in Azure Web Application Firewall (WAF) policies
B. inbound rules in network security groups (NSGs)
C. firewall rules for the storage account
D. inbound rules in Azure Firewall
E. service tags in network security groups (NSGs)
You need to recommend a solution to meet the security requirements for the virtual machines. What should you include in the recommendation?
A. just-in-time (JIT) VM access
B. an Azure Bastion host
C. Azure Virtual Desktop
D. a network security group (NSG)
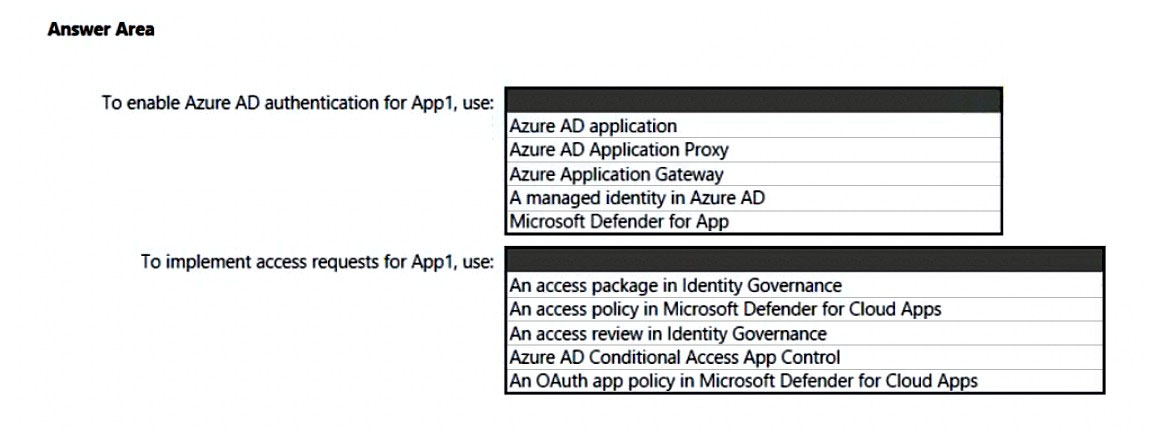
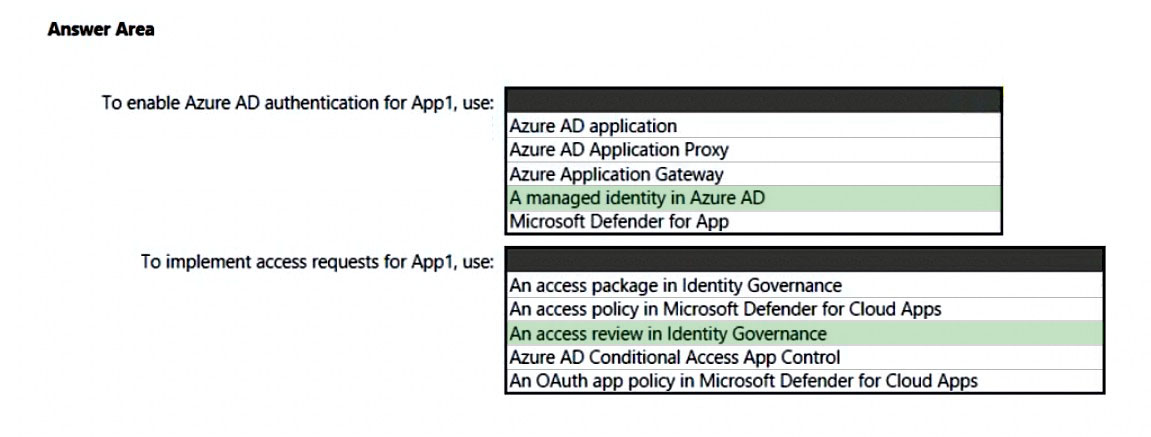
HOTSPOT - You are creating the security recommendations for an Azure App Service web app named App1. App1 has the following specifications: ✑ Users will request access to App1 through the My Apps portal. A human resources manager will approve the requests. ✑ Users will authenticate by using Azure Active Directory (Azure AD) user accounts. You need to recommend an access security architecture for App1. What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You are designing the encryption standards for data at rest for an Azure resource. You need to provide recommendations to ensure that the data at rest is encrypted by using AES-256 keys. The solution must support rotating the encryption keys monthly. Solution: For Azure SQL databases, you recommend Transparent Data Encryption (TDE) that uses Microsoft-managed keys. Does this meet the goal?
A. Yes
B. No
You have a Microsoft 365 subscription that syncs with Active Directory Domain Services (AD DS). You need to define the recovery steps for a ransomware attack that encrypted data in the subscription. The solution must follow Microsoft Security Best Practices. What is the first step in the recovery plan?
A. From Microsoft Defender for Endpoint, perform a security scan.
B. Recover files to a cleaned computer or device.
C. Contact law enforcement.
D. Disable Microsoft OneDrive sync and Exchange ActiveSync.
Access Full SC-100 Exam Prep Free
Want to go beyond these 50 questions? Click here to unlock a full set of SC-100 exam prep free questions covering every domain tested on the exam.
We continuously update our content to ensure you have the most current and effective prep materials.
Good luck with your SC-100 certification journey!