PSE Strata Exam Prep Free – 50 Practice Questions to Get You Ready for Exam Day
Getting ready for the PSE Strata certification? Our PSE Strata Exam Prep Free resource includes 50 exam-style questions designed to help you practice effectively and feel confident on test day
Effective PSE Strata exam prep free is the key to success. With our free practice questions, you can:
- Get familiar with exam format and question style
- Identify which topics you’ve mastered—and which need more review
- Boost your confidence and reduce exam anxiety
Below, you will find 50 realistic PSE Strata Exam Prep Free questions that cover key exam topics. These questions are designed to reflect the structure and challenge level of the actual exam, making them perfect for your study routine.
When HTTP header logging is enabled on a URL Filtering profile, which attribute-value can be logged?
A. HTTP method
B. HTTP response status code
C. Content type
D. X-Forwarded-For
A large number of next-generation firewalls (NGFWs), along with Panorama and WildFire have been positioned for a prospective customer. The customer is concerned about storing retrieving and archiving firewall logs and has indicated that logs must be retained for a minimum of 60 days. An additional requirement is ingestion of a maximum of 10,000 logs per second. What will best meet the customer’s logging requirements?
A. NGFWs that have at least 10TB of internal storage
B. Appropriately sized NGFW based on use of the POPSICLE tool
C. Appropriate Data Lake storage determined by using the Data Lake Calculator
D. A pair of fully populated M-300 storage appliances
What three Tabs are available in the Detailed Device Health on Panorama for hardware-based firewalls? (Choose three.)
A. Errors
B. Environments
C. Interfaces
D. Mounts
E. Throughput
F. Sessions
G. Status
Which proprietary technology solutions will allow a customer to identify and control traffic sources regardless of internet protocol (IP) address or network segment?
A. User-ID and Device-ID
B. Source-ID and Device-ID
C. Source-ID and Network-ID
D. User-ID and Source-ID
Which three considerations should be made prior to installing a decryption policy on the NGFW? (Choose three.)
A. Include all traffic types in decryption policy
B. Inability to access websites
C. Exclude certain types of traffic in decryption policy
D. Deploy decryption setting all at one time
E. Ensure throughput is not an issue
What is the key benefit of Palo Alto Networks single-pass architecture (SPA) design?
A. It requires only one processor to complete all the functions within the box.
B. It allows the addition of new functions to existing hardware without affecting performance.
C. It allows the addition of new devices to existing hardware without affecting performance.
D. It decodes each network flow multiple times, therefore reducing throughput.
Which two configuration elements can be used to prevent abuse of stolen credentials? (Choose two.)
A. multi-factor authentication (MFA)
B. URL Filtering Profiles
C. WildFire analysis
D. dynamic user groups (DUGs)
Which two actions should be taken prior to installing a decryption policy on an NGFW? (Choose two.)
A. Ensure throughput will not be an issue.
B. Determine whether local / regional decryption laws apply.
C. Deploy decryption settings all at one time.
D. Include all traffic types in decryption policy.
Access to a business site is blocked by URL Filtering inline machine learning (ML) and considered as a false-positive. How should the site be made available?
A. Create a custom URL category and add it on exception of the inline ML profile.
B. Change the action of real-time-detection category on URL filtering profile.
C. Create a custom URL category and add it to the Security policy.
D. Disable URL Filtering inline ML.
You have enabled the WildFire ML for PE files in the antivirus profile and have added the profile to the appropriate firewall rules. When you go to Palo Alto Networks WildFire test av file and attempt to download the test file it is allowed through. In order to verify that the machine learning is working from the command line, which command returns a valid result?
A. show mlav cloud-status
B. show wfml cloud-status
C. show ml cloud-status
D. show wfav cloud-status
Which two features can be enabled to support asymmetric routing with redundancy on a Palo Alto Networks next-generation firewall (NGFW)? (Choose two.)
A. multiple virtual systems
B. active / active high availability (HA)
C. non-SYN first packet
D. asymmetric routing profile
A customer with a fully licensed Palo Alto Networks firewall is concerned about threats based on domain generation algorithms (DGAs). Which Security profile is used to configure Domain Name Security (DNS) to identify and block previously unknown DGA-based threats in real time?
A. Anti-Spyware profile
B. URL Filtering profile
C. Vulnerability Protection profile
D. WildFire Analysis profile
Which two of the following are required when configuring the Domain Credential Filter method for preventing phishing attacks? (Choose two.)
A. LDAP connector
B. Group mapping
C. IP-address-to-username mapping
D. Windows User-ID agent
What is an advantage of having WildFire machine learning (ML) capability inline on the firewall?
A. It eliminates of the necessity for dynamic analysis in the cloud.
B. It is always able to give more accurate verdicts than the cloud ML analysis, reducing false positives and false negatives,
C. It improves the CPU performance of content inspection.
D. It enables the firewall to block unknown malicious files in real time and prevent patient zero without disrupting business productivity.
The Palo Alto Networks Cloud Identity Engine (CIE) includes which service that supports Identity Providers (IdP)?
A. Directory Sync and Cloud Authentication Service that support IdP using SAML 2.0
B. Directory Sync that supports IdP using SAML 2.0
C. Directory Sync and Cloud Authentication Service that support IdP using SAML 2.0 and OAuth2
D. Cloud Authentication Service that supports IdP using SAML 2.0 and OAuth2
In Panorama, which three reports or logs will help identify the inclusion of a host / source in a command-and-control (C2) incident? (Choose three.)
A. WildFire analysis reports
B. data filtering logs
C. hotnet reports
D. threat logs
E. SaaS reports
Which two methods will help avoid Split Brain when running HA in Active/Active mode? (Choose two.)
A. Configure a Backup HA1 Interface
B. Configure a Heartbeat Backup
C. Create a loopback IP address and use that as a Source Interface
D. Place your management interface in an Aggregate Interface Group configuration
Which three components are specific to the Query Builder found in the Custom Report creation dialog of the firewall? (Choose three.)
A. Connector
B. Database
C. Recipient
D. Operator
E. Attribute
F. Schedule
If a Palo Alto Networks Next-Generation Firewall (NGFW) already has Advanced Threat Prevention (ATP) enabled what is the throughput impact of also enabling Wildfire and Advanced URL Filtering (AURLF)?
A. The throughput will decrease with each additional subscription enabled.
B. The throughput will remain consistent, but the maximum number of simultaneous sessions will decrease.
C. The throughput will remain consistent regardless of the additional subscriptions enabled.
D. The throughput will decrease, but the maximum simultaneous sessions will remain consistent.
Within the Five-Step Methodology of Zero Trust, in which step would application access and user access be defined?
A. Step 1: Define the Protect Surface
B. Step 3: Architect a Zero Trust Network
C. Step 5: Monitor and Maintain the Network
D. Step 2: Map the Protect Surface Transaction Flows
E. Step 4: Create the Zero Trust Policy
A customer requests that a known spyware threat signature be triggered based on a rate of occurrence, for example, 10 hits in 5 seconds. How is this goal accomplished?
A. Create a custom spyware signature matching the known signature with the time attribute
B. Add a correlation object that tracks the occurrences and triggers above the desired threshold
C. Submit a request to Palo Alto Networks to change the behavior at the next update
D. Configure the Anti-Spyware profile with the number of rule counts to match the occurrence frequency
Which two features are key in preventing unknown targeted attacks? (Choose two.)
A. Single Pass Parallel Processing (SP3)
B. nightly botnet report
C. App-ID with the Zero Trust model
D. WildFire Cloud threat analysis
Which CLI allows you to view the names of SD-WAN policy rules that send traffic to the specified virtual SD-WAN interface, along with the performance metrics?
A. >show sdwan connection all |
B. >show sdwan path-monitor stats vif
C. >show sdwan rule vif sdwan.x
D. >show sdwan session distribution policy-name
What are three valid sources that are supported for user IP address mapping in Palo Alto Networks NGFW? (Choose three.)
A. RADIUS
B. Client Probing
C. Lotus Domino
D. Active Directory monitoring
E. TACACS
F. eDirectory monitoring
Which PAN-OS feature helps prevent user credential theft?
A. Drive-by download protection
B. Advanced URL Filtering (AURLF)
C. Data loss prevention (DLP)
D. Multi-factor authentication (MFA)
Which two actions can be configured in an Anti-Spyware profile to address command-and-control (C2) traffic from compromised hosts? (Choose two.)
A. Redirect
B. Alert
C. Quarantine
D. Reset
Which three steps in the cyberattack lifecycle does Palo Alto Networks Security Operating Platform prevent? (Choose three.)
A. recon the target
B. deliver the malware
C. exfiltrate data
D. weaponize vulnerabilities
E. lateral movement
Which two of the following does decryption broker provide on a NGFW? (Choose two.)
A. Decryption broker allows you to offload SSL decryption to the Palo Alto Networks next-generation firewall and decrypt traffic only once
B. Eliminates the need for a third party SSL decryption option which allows you to reduce the total number of third party devices performing analysis and enforcement
C. Provides a third party SSL decryption option which allows you to increase the total number of third party devices performing analysis and enforcement
D. Decryption broker allows you to offload SSL decryption to the Palo Alto Networks next-generation firewall and decrypt traffic multiple times
When having a customer pre-sales call, which aspects of the NGFW should be covered?
A. The NGFW simplifies your operations through analytics and automation while giving you consistent protection through exceptional visibility and control across the data center, perimeter, branch, mobile and cloud networks
B. The Palo Alto Networks-developed URL filtering database, PAN-DB provides high-performance local caching for maximum inline performance on URL lookups, and offers coverage against malicious URLs and IP addresses. As WildFire identifies unknown malware, zero-day exploits, and advanced persistent threats (APTs), the PAN-DB database is updated with information on malicious URLs so that you can block malware downloads and disable Command and Control (C2) communications to protect your network from cyberthreats. URL categories that identify confirmed malicious content ג€” malware, phishing, and C2 are updated every five minutes ג€” to ensure that you can manage access to these sites within minutes of categorization
C. The NGFW creates tunnels that allow users/systems to connect securely over a public network, as if they were connecting over a local area network (LAN). To set up a VPN tunnel you need a pair of devices that can authenticate each other and encrypt the flow of information between them The devices can be a pair of Palo Alto Networks firewalls, or a Palo Alto Networks firewall along with a VPN-capable device from another vendor
D. Palo Alto Networks URL Filtering allows you to monitor and control the sites users can access, to prevent phishing attacks by controlling the sites to which users can submit valid corporate credentials, and to enforce safe search for search engines like Google and Bing
What is the key benefit of Palo Alto Networks Single Pass Parallel Processing design?
A. There are no benefits other than slight performance upgrades
B. It allows Palo Alto Networks to add new functions to existing hardware
C. Only one processor is needed to complete all the functions within the box
D. It allows Palo Alto Networks to add new devices to existing hardware
Which two interface types can be associated to a virtual router? (Choose two.)
A. Loopback
B. Virtual Wire
C. VLAN
D. Layer 2
Which functionality is available to firewall users with an active Threat Prevention subscription, but no WildFire license?
A. Access to the WildFire API
B. WildFire hybrid deployment
C. PE file upload to WildFire
D. 5 minute WildFire updates to threat signatures
A customer is designing a private data center to host their new web application along with a separate headquarters for users. Which cloud-delivered security service (CDSS) would be recommended for the headquarters only?
A. WildFire
B. Threat Prevention
C. Advanced URL Filtering (AURLF)
D. DNS Security
What will best enhance security of a production online system while minimizing the impact for the existing network?
A. active/active high availability (HA)
B. Layer 2 interfaces
C. virtual systems
D. virtual wire
WildFire can discover zero-day malware in which three types of traffic? (Choose three.)
A. TFTP
B. SMTP
C. DNS
D. FTP
E. HTTPS
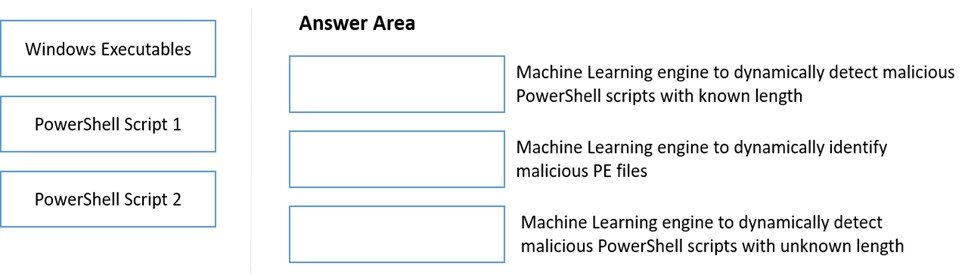
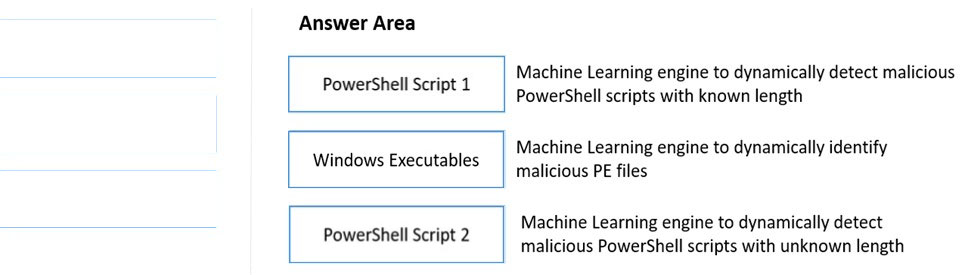
DRAG DROP - Match the WildFire Inline Machine Learning Model to the correct description for that model. Select and Place:
Which action will protect against port scans from the internet?
A. Assign an Interface Management profile to the zone of the ingress interface
B. Assign Security profiles to Security policy rules for traffic sourcing from the untrust zone
C. Apply a Zone Protection profile on the zone of the ingress interface
D. Apply App-ID Security policy rules to block traffic sourcing from the untrust zone
What filtering criteria is used to determine what users to include as members of a dynamic user group?
A. Tags
B. Login IDs
C. Security Policy Rules
D. IP Addresses
The WildFire Inline Machine Learning is configured using which Content-ID profiles?
A. Antivirus Profile
B. WildFire Analysis Profile
C. Threat Prevention Profile
D. File Blocking Profile
Which two statements correctly describe what a Network Packet Broker does for a Palo Alto Networks NGFW? (Choose two.)
A. It provides a third-party SSL decryption option, which can increase the total number of third-party devices performing analysis and enforcement.
B. It allows SSL decryption to be offloaded to the NGFW and traffic to be decrypted only once.
C. It eliminates the need for a third-party SSL decryption option, which reduces the total number of third-party devices performing decryption.
D. It allows SSL decryption to be offloaded to the NGFW and traffic to be decrypted multiple times.
A potential customer requires an NGFW solution that enables high-throughput, low-latency network security and also inspects the application. Which aspect of the Palo Alto Networks NGFW capabilities should be highlighted to help address these requirements?
A. single-pass architecture (SPA)
B. threat prevention
C. GlobalProtect
D. Elastic Load Balancing (ELB)
What action would address the sub-optimal traffic path shown in the figure? Key: RN - Remote Network - SC - Service Connection - MU GW - Mobile User Gateway -
A. Onboard a Service Connection in the Americas region
B. Remove the Service Connection in the EMEA region
C. Onboard a Service Connection in the APAC region
D. Onboard a Remote Network location in the EMEA region
A customer is concerned about zero-day targeted attacks against its intellectual property. Which solution informs a customer whether an attack is specifically targeted at them?
A. Cortex XDR Prevent
B. AutoFocus
C. Cortex XSOAR Community edition
D. Panorama Correlation Report
Which two methods are used to check for Corporate Credential Submissions? (Choose two.)
A. domain credential filter
B. IP user mapping
C. User-ID credential check
D. LDAP query
A Fortune 500 customer has expressed interest in purchasing WildFire; however, they do not want to send discovered malware outside of their network. Which version of WildFire will meet this customer’s requirements?
A. WildFire Government Cloud
B. WildFire Public Cloud
C. WildFire Private Cloud
D. WildFire Secure Cloud
What are three considerations when deploying User-ID? (Choose three.)
A. Specify included and excluded networks when configuring User-ID
B. Only enable User-ID on trusted zones
C. Use a dedicated service account for User-ID services with the minimal permissions necessary
D. User-ID can support a maximum of 15 hops
E. Enable WMI probing in high security networks
Which three categories are identified as best practices in the Best Practice Assessment tool? (Choose three.)
A. use of device management access and settings
B. identify sanctioned and unsanctioned SaaS applications
C. expose the visibility and presence of command-and-control sessions
D. measure the adoption of URL filters, App-ID, User-ID
E. use of decryption policies
What is the default behavior in PAN-OS when a 12 MB portable executable (PE) file is forwarded to the WildFire cloud service?
A. Flash file is not forwarded.
B. Flash file is forwarded.
C. PE File is forwarded.
D. PE File is not forwarded.
Which PAN-OS feature should be discussed if a prospect wants to apply Security policy actions to traffic by using tags from their virtual environment?
A. Machine learning (ML)
B. Dynamic User Groups
C. URL blocking
D. MineMeld
What are the three possible verdicts in WildFire Submissions log entries for a submitted sample? (Choose four.)
A. Benign
B. Spyware
C. Malicious
D. Phishing
E. Grayware
Access Full PSE Strata Exam Prep Free
Want to go beyond these 50 questions? Click here to unlock a full set of PSE Strata exam prep free questions covering every domain tested on the exam.
We continuously update our content to ensure you have the most current and effective prep materials.
Good luck with your PSE Strata certification journey!