MS-100 Exam Prep Free – 50 Practice Questions to Get You Ready for Exam Day
Getting ready for the MS-100 certification? Our MS-100 Exam Prep Free resource includes 50 exam-style questions designed to help you practice effectively and feel confident on test day
Effective MS-100 exam prep free is the key to success. With our free practice questions, you can:
- Get familiar with exam format and question style
- Identify which topics you’ve mastered—and which need more review
- Boost your confidence and reduce exam anxiety
Below, you will find 50 realistic MS-100 Exam Prep Free questions that cover key exam topics. These questions are designed to reflect the structure and challenge level of the actual exam, making them perfect for your study routine.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. Your company has a Microsoft Office 365 tenant. You suspect that several Office 365 features were recently updated. You need to view a list of the features that were recently updated in the tenant. Solution: You review the Security & Compliance report in the Microsoft 365 admin center. Does this meet the goal?
A. Yes
B. No
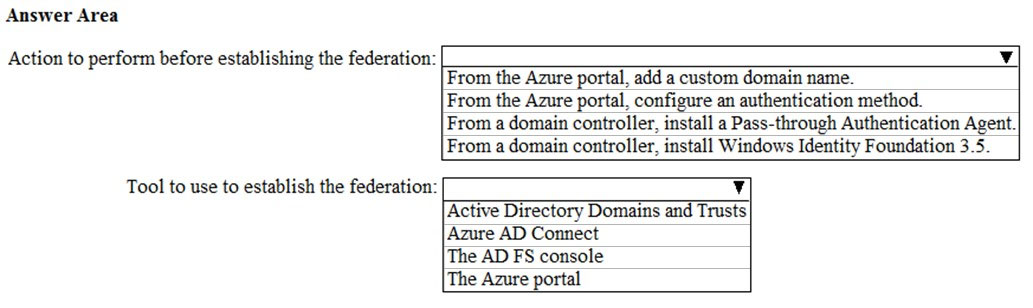
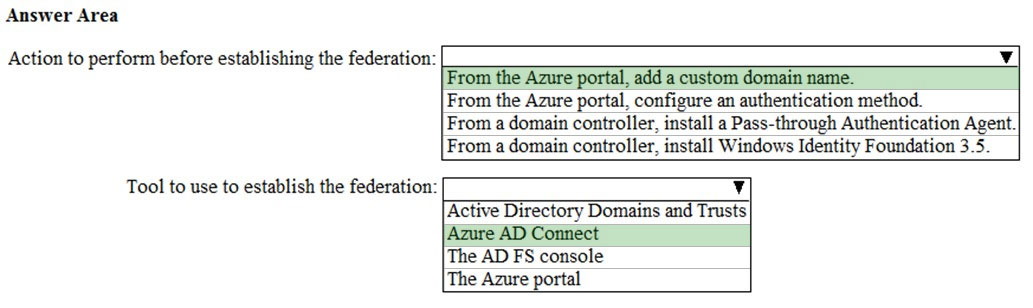
HOTSPOT - Your network contains an on-premises Active Directory domain named contoso.com. The domain contains five domain controllers. Your company purchases Microsoft 365 and creates a Microsoft Azure Directory (Azure AD) tenant named contoso.onmicrosoft,com. You plan to establish federation authentication between on-premises Active Directory and the Azure AD tenant by using Active Directory Federation Services (AD FS). You need to establish the federation. What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
Your network contains an on-premises Active Directory domain. Your company has a security policy that prevents additional software from being installed on domain controllers. You need to monitor a domain controller by using Microsoft Azure Advanced Threat Protection (ATP). What should you do? More than once choice may achieve the goal. Select the BEST answer.
A. Deploy an Azure ATP standalone sensor, and then configure port mirroring.
B. Deploy an Azure ATP standalone sensor, and then configure detections.
C. Deploy an Azure ATP sensor, and then configure detections.
D. Deploy an Azure ATP sensor, and then configure port mirroring.
You need to meet the security requirement for Group1. What should you do?
A. Configure all users to sign in by using multi-factor authentication.
B. Modify the properties of Group1.
C. Assign Group1 a management role.
D. Modify the Password reset properties of the Azure AD tenant.
You have a Microsoft 365 tenant. A partner company has an email domain named contoso.com. You need to prevent out-of-office replies from being sent to contoso.com. What should you create?
A. a rule
B. an organization relationship
C. a remote domain
D. a connector
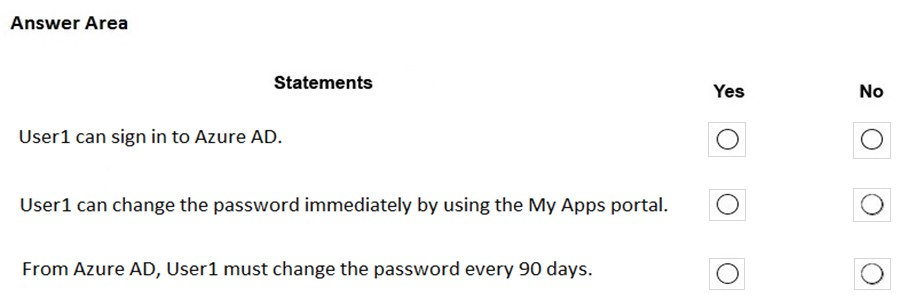
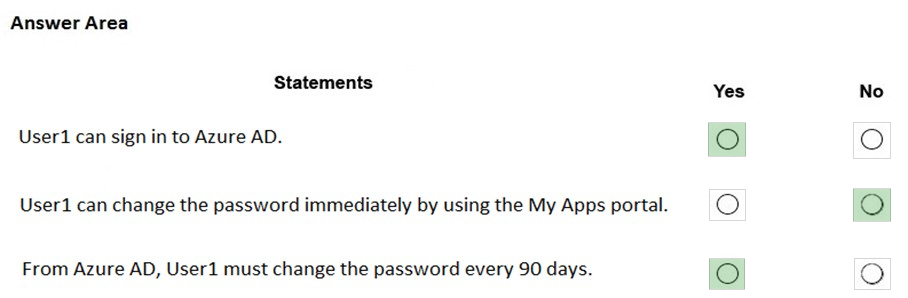
HOTSPOT - Your network contains an on-premises Active Directory domain named adatum.com that syncs to Azure Active Directory (Azure AD) by using the Azure AD Connect Express Settings. Password writeback is disabled. You create a user named User1 and enter Pass in the Password field as shown in the following exhibit.The Azure AD password policy is configured as shown in the following exhibit. Hot Area:
Which migration solution should you recommend for Project1?
A. From the Microsoft 365 admin center, start a data migration and click Exchange as the data service.
B. From the Exchange admin center, start a migration and select Cutover migration.
C. From the Exchange admin center, start a migration and select Staged migration.
D. From the Microsoft 365 admin center, start a data migration and click Upload PST as the data service.
You have a Microsoft 365 subscription. You create a new Conditional Access policy named CAPolicy1. You need to be able to review how CAPolicy1 has affected users after 90 days. What should you do?
A. From the Microsoft 365 admin center, view the Email activity report.
B. Run the Get-AzureADAuditSignInLogs cmdlet.
C. From the Azure Active Directory admin center, review the sign-in logs for each user.
D. Deploy the Conditional Access insights and reporting workbook.
Your network contains an Active Directory domain named contoso.com. You have a Microsoft 365 subscription. You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.onmicrosoft.com. You implement directory synchronization. The developers at your company plan to build an app named App1. App1 will connect to the Microsoft Graph API to provide access to several Microsoft Office 365 services. You need to provide the URI for the authorization endpoint that App1 must use. What should you provide?
A. https://login.microsoftonline.com/
B. https://contoso.com/contoso.onmicrosoft.com/app1
C. https://login.microsoftonline.com/contoso.onmicrosoft.com/
D. https://myapps.microsoft.com
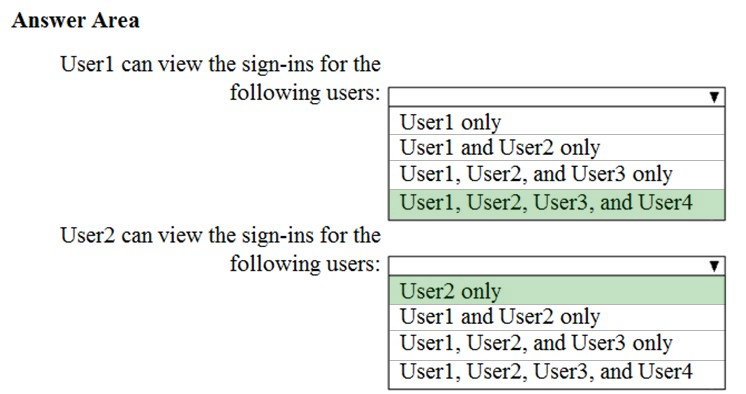
HOTSPOT - You have a Microsoft 365 subscription that uses an Azure Active Directory (Azure AD) tenant named contoso.com. The tenant contains the users shown in the following table.From the Sign-ins blade of the Azure Active Directory admin center, for which users can User1 and User2 view the sign-ins? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 subscription. You plan to implement Microsoft Purview Privileged Access Management. Which Microsoft Office 365 workloads support privileged access?
A. Microsoft Teams and SharePoint Online only
B. Microsoft Teams, Exchange Online, and SharePoint Online
C. Microsoft Exchange Online and SharePoint Online only
D. Microsoft Exchange Online only
E. Microsoft Teams only
You need to meet the security requirement for the vendors. What should you do?
A. From Azure Cloud Shell, run the Set-MsolUserPrincipalName and specify the ג€”tenantID parameter.
B. From Azure Cloud Shell, run the Set-AzureADUserExtension cmdlet.
C. Azure Cloud Shell, run the New-AzureADUser cmdlet and specify the ג€”UserPrincipalName parameter.
D. From Azure Cloud Shell, run the New-AzureADMSInvitation cmdlet and specify the ג€”InvitedUserEmailAddress parameter.
You have a Microsoft 365 E5 tenant. You plan to create the Microsoft Power Platform environments shown in the following table.What is the minimum amount of available database capacity required to create the environments?
A. 1 GB
B. 2 GB
C. 3 GB
D. 4 GB
E. 7 GB
You have a Microsoft 365 subscription that contains a user named User1. You need to ensure that User1 receives Microsoft 365 feature and service updates before the updates are released to all users. What should you do in the Microsoft 365 admin center?
A. Modify the privileged access management settings.
B. Modify Office software download settings.
C. Modify the Release preferences settings.
D. Submit a new service request.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. Your network contains an Active Directory domain. You deploy a Microsoft Azure Active Directory (Azure AD) tenant. Another administrator configures the domain to synchronize to Azure AD. You discover that 10 user accounts in an organizational unit (OU) are NOT synchronized to Azure AD. All the other user accounts synchronized successfully. You review Azure AD Connect Health and discover that all the user account synchronizations completed successfully. You need to ensure that the 10 user accounts are synchronized to Azure AD. Solution: From Azure AD Connect, you modify the filtering settings. Does this meet the goal?
A. Yes
B. No
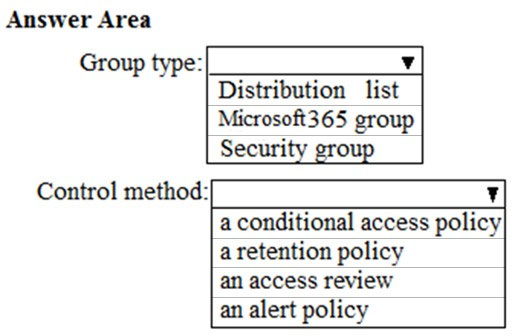
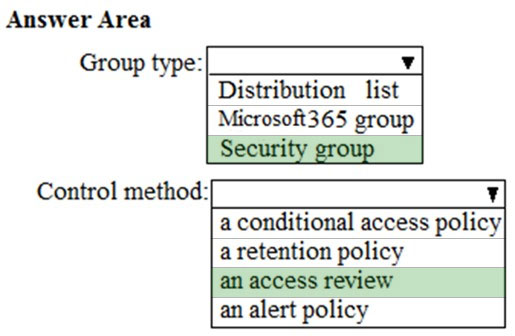
HOTSPOT - You need to create the UserLicenses group. The solution must meet the security requirements. Which group type and control method should you use? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
SIMULATION - Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time. When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design. Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn't matter how you accomplish the task, if you successfully perform it, you will earn credit for that task. Labs are not timed separately, and this exam may have more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided. Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab. You may now click next to proceed to the lab. Lab information - Use the following login credentials as needed: To enter your username, place your cursor in the Sign in box and click on the username below. To enter your password, place your cursor in the Enter password box and click on the password below. Microsoft 365 Username: admin@admin.onmicrosoft.com Microsoft 365 Password: xxxxxxxxxx If the Microsoft 365 portal does not load successfully in the browser, press CTRL-K to reload the portal in a new browser tab. The following information is for technical support purposes only: Lab Instance: 111111111 - You need to prevent the users in your organization from establishing voice calls from Microsoft Skype for Business to external Skype users.
You have a Microsoft 365 E5 subscription that uses Microsoft Teams and SharePoint Online. You create a team and a SharePoint Online site for a new project named Project1. You need to manage access to the team and the site. The solution must meet the following requirements: * Members of Project1 must be able to control who has access to the team and the site. * Only users in the subscription must be able to request access to the team and the site. * Access to the team and the site must be removed after 12 months. * Access to the team and the site must be reviewed every month. What should you create first?
A. a Conditional Access policy
B. a catalog
C. an access package
D. an access review
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. Your company has a main office and three branch offices. All the branch offices connect to the main office by using a WAN link. The main office has a high-speed Internet connection. All the branch offices connect to the Internet by using the main office connection. Users use Microsoft Outlook 2016 to connect to a Microsoft Exchange Server mailbox hosted in the main office. The users report that when the WAN link in their office becomes unavailable, they cannot access their mailbox. You create a Microsoft 365 subscription, and then migrate all the user data to Microsoft 365. You need to ensure that all the users can continue to use Outlook to receive email messages if a WAN link fails. Solution: For each device, you configure an additional Outlook profile that uses IMAP. Does this meet the goal?
A. Yes
B. No
SIMULATION - Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time. When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design. Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn't matter how you accomplish the task, if you successfully perform it, you will earn credit for that task. Labs are not timed separately, and this exam may have more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided. Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab. You may now click next to proceed to the lab. Lab information - Use the following login credentials as needed: To enter your username, place your cursor in the Sign in box and click on the username below. To enter your password, place your cursor in the Enter password box and click on the password below. Microsoft 365 Username: admin@admin.onmicrosoft.com Microsoft 365 Password: xxxxxxxxxx If the Microsoft 365 portal does not load successfully in the browser, press CTRL-K to reload the portal in a new browser tab. The following information is for technical support purposes only: Lab Instance: 111111111 - You plan to allow the users in your organization to invite external users as guest users to your Microsoft 365 tenant. You need to prevent the organization's users from inviting guests who have an email address that uses a suffix of @gmail.com.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. Your company plans to deploy several Microsoft Office 365 services. You need to design an authentication strategy for the planned deployment. The solution must meet the following requirements: ✑ Users must be able to authenticate during business hours only. ✑ Authentication requests must be processed successfully if a single server fails. ✑ When the password for an on-premises user account expires, the new password must be enforced the next time the user signs in. ✑ Users who connect to Office 365 services from domain-joined devices that are connected to the internal network must be signed in automatically. Solution: You design an authentication strategy that uses federation authentication by using Active Directory Federation Services (AD FS). The solution contains two AD FS servers and two Web Application Proxies. Does this meet the goal?
A. Yes
B. No
You have a Microsoft 365 subscription. From the Microsoft 365 portal, users download and install Microsoft Office apps on their devices. You need to ensure that Office feature updates are installed by using the Semi-Annual Channel. What should you configure from the Services page of the Microsoft 365 admin center?
A. Office Scripts
B. User owned apps and services
C. Office installation options
D. Office on the web
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. Your network contains an on-premises Active Directory forest named contoso.com. The forest contains the following domains: ✑ Contoso.com ✑ East.contoso.com An Azure AD Connect server is deployed to contoso.com. Azure AD Connect syncs to an Azure Active Directory (Azure AD) tenant. You deploy a new domain named west.contoso.com to the forest. You need to ensure that west.contoso.com syncs to the Azure AD tenant. Solution: From the Azure AD Connect server in contoso.com, you return the setup wizard and include the west.contoso.com domain. Does this meet the goal?
A. Yes
B. No
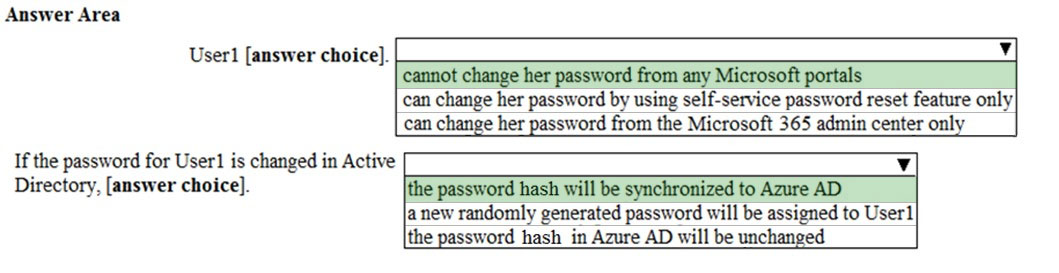
HOTSPOT - Your company has a hybrid deployment of Microsoft 365. An on-premises user named User1 is synced to Microsoft Azure Active Directory (Azure AD). Azure AD Connect is configured as shown in the following exhibit.Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point. Hot Area:
Your company has a Microsoft 365 subscription and a Microsoft Azure Active Directory (Azure AD) tenant named contoso.onmicrosoft.com. An external vendor has a Microsoft account that has a username of user1@outlook.com . You plan to provide user1@outlook.com with access to several resources in the subscription. You need to add the external user account to contoso.onmicrosoft.com. The solution must ensure that the external vendor can authenticate by using user1@outlook.com . What should you do?
A. From Azure Cloud Shell, run the New-AzureADUser cmdlet and specify ג€”UserPrincipalName user1@outlook.com.
B. From the Microsoft 365 admin center, add a contact, and then specify user1@outlook.com as the email address.
C. From the Azure portal, add a new guest user, and then specify user1@outlook.com as the email address.
D. From the Azure portal, add a custom domain name, and then create a new Azure AD user and use user1@outlook.com as the username.
You have a Microsoft 365 subscription. You register two applications named App1 and App2 to Azure Active Directory (Azure AD). You need to ensure that users who connect to App1 require multi-factor authentication (MFA). MFA is required only for App1. What should you do?
A. From the Microsoft 365 admin center, configure the Modern authentication settings.
B. From Multi-Factor Authentication, configure the service settings.
C. From the Enterprise applications blade of the Azure Active Directory admin center, configure the Users settings.
D. From the Azure Active Directory admin center, create a conditional access policy.
You need to configure just in time access to meet the technical requirements. What should you use?
A. access reviews
B. entitlement management
C. Azure Active Directory (Azure AD) Privileged Identity Management (PIM)
D. Azure Active Directory (Azure AD) Identity Protection
Your network contains an on-premises Active Directory domain. The domain contains 2,000 computers that run Windows 10. You purchase a Microsoft 365 subscription. You implement password hash synchronization and Azure Active Directory (Azure AD) Seamless Single Sign-On (Seamless SSO). You need to ensure that users can use Seamless SSO from the Windows 10 computers. What should you do?
A. Create a conditional access policy in Azure AD.
B. Deploy an Azure AD Connect staging server.
C. Join the computers to Azure AD.
D. Modify the Intranet zone settings by using Group Policy
Your company has a Microsoft 365 subscription. You upload several archive PST files to Microsoft 365 by using the Microsoft 365 compliance center. A month later, you attempt to run an import job for the PST files. You discover that the PST files were deleted from Microsoft 365. What is the most likely cause of the files being deleted? More than one answer choice may achieve the goal. Select the BEST answer.
A. The PST files were corrupted and deleted by Microsoft 365 security features.
B. PST files are deleted automatically from Microsoft 365 after 30 days.
C. The size of the PST files exceeded a storage quota and caused the files to be deleted.
D. Another administrator deleted the PST files.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. Your company has 3,000 users. All the users are assigned Microsoft 365 E3 licenses. Some users are assigned licenses for all Microsoft 365 services. Other users are assigned licenses for only certain Microsoft 365 services. You need to determine whether a user named User1 is licensed for Exchange Online only. Solution: You run the Get-MsolAccountSku cmdlet. Does this meet the goal?
A. Yes
B. No
Your on-premises network contains an Active Directory domain that syncs with an Azure Active Directory (Azure AD) tenant named contoso.com by using Azure AD Connect. Your company purchases another company that has an on-premises Active Directory domain named litwareinc.com. You need to sync litwareinc.com with contoso.com. What should you install in the litwareinc.com domain?
A. an Azure AD application proxy connector
B. an Azure AD Connect instance in staging mode
C. an Azure AD Connect provisioning agent
D. an active instance of Azure AD Connect
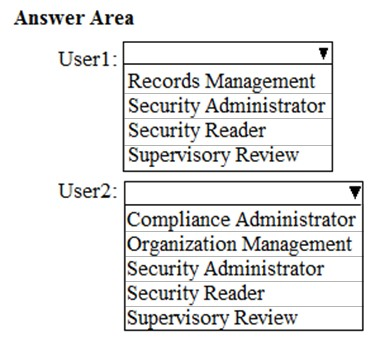
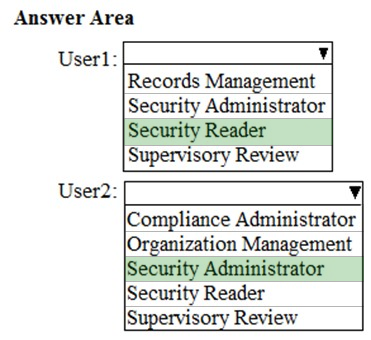
HOTSPOT - You have a Microsoft 365 subscription. You are configuring permissions for Security & Compliance. You need to ensure that the users can perform the tasks shown in the following table.The solution must use the principle of least privilege. To which role should you assign each user? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 subscription. You suspect that several Microsoft Office 365 applications or services were recently updated. You need to identify which applications or services were recently updated. What are two possible ways to achieve the goal? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. From the Microsoft 365 admin center, review the Message center blade.
B. From the Office 365 Admin mobile app, review the messages.
C. From the Microsoft 365 admin center, review the Products blade.
D. From the Microsoft 365 admin center, review the Service health blade.
You have a Microsoft 365 subscription. You view the service advisories shown in the following exhibit.You need to ensure that users who administer Microsoft SharePoint Online can view the advisories to investigate service health issues. Which role should you assign to the users?
A. Compliance administrator
B. Message Center reader
C. Reports reader
D. Service administrator
Your company uses email, calendar, contact, and task services in Microsoft Outlook.com. You purchase a Microsoft 365 subscription and plan to migrate all users from Outlook.com to Microsoft 365. You need to identify which user data can be migrated to Microsoft 365. Which type of data should you identify?
A. task
B. email
C. calendar
D. contacts
You have a Microsoft 365 E5 subscription that uses Endpoint security. You need to create a group and assign the Endpoint Security Manager role to the group. Which type of group can you use?
A. security only
B. mail-enabled security, Microsoft 365, and security only
C. distribution, mail-enabled security, Microsoft 365, and security
D. Microsoft 365 only
E. mail-enabled security and security only
HOTSPOT - You have a Microsoft 365 E5 subscription. You create a Conditional Access policy named Policy1 and assign Policy1 to all users. You need to configure Policy 1 to enforce multi-factor authentication (MFA) if the user risk level is high. Which two settings should you configure in Policy1? To answer, select the appropriate settings in the answer area. NOTE: Each correct selection is worth one point.
You have an on-premises web application that is published by using a URL of https://app.contoso.local. You purchase a Microsoft 365 subscription. Several external users must be able to connect to the web application. You need to recommend a solution for external access to the application. The solution must support multi-factor authentication. Which two actions should you recommend? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. From an on-premises server, install a connector, and then publish the app.
B. From the Azure Active Directory admin center, enable an Application Proxy.
C. From the Azure Active Directory admin center, create a conditional access policy.
D. From an on-premises server, install an Authentication Agent.
E. Republish the web application by using https://app.contoso.com.
You have a Microsoft 365 E5 subscription. You need to ensure that users are prompted for multi-factor authentication (MFA) when they attempt to access Microsoft SharePoint Online resources. Users must NOT be prompted for MFA when they attempt to access other Microsoft 365 services. What should you do?
A. From the Microsoft Endpoint Manager admin center, create an app protection policy.
B. From the multi-factor authentication page, configure the users settings.
C. From the Azure Active Directory admin center, create a conditional access policy.
D. From the Cloud App Security admin center, create an app access policy.
Your company has a main office and three new branch offices. The company has a Microsoft 365 subscription. From the Microsoft 365 admin center, you open Microsoft 365 network connectivity. You need to configure the prerequisites for enabling Microsoft 365 network connectivity. What should you do first?
A. Select a SD-WAN solution and the data location.
B. Enable Productivity Score.
C. Update the organization information.
D. Add location data to Microsoft 365.
You have an on-premises Microsoft Exchange Server organization that contains 100 mailboxes. You have a hybrid Microsoft 365 tenant. You run the Hybrid Configuration wizard and migrate the mailboxes to the tenant. You need to ensure that Microsoft 365 spam filtering is applied to incoming email. What should you do?
A. Run the Hybrid Configuration wizard again.
B. Update the Sender Policy Framework (SPF) TXT record to point to the on-premises Exchange IP address.
C. Run the Azure Active Directory Connect wizard again.
D. Update the MX record to point to Exchange Online.
You have a Microsoft 365 tenant. You have a line-of-business application named App1 that users access by using the My Apps portal. After some recent security breaches, you implement a conditional access policy for App1 that uses Conditional Access App Control. You need to be alerted by email if impossible travel is detected for a user of App1. The solution must ensure that alerts are generated for App1 only. What should you do?
A. From Microsoft Cloud App Security, modify the impossible travel alert policy.
B. From Microsoft Cloud App Security, create a Cloud Discovery anomaly detection policy.
C. From the Azure Active Directory admin center, modify the conditional access policy.
D. From Microsoft Cloud App Security, create an app discovery policy.
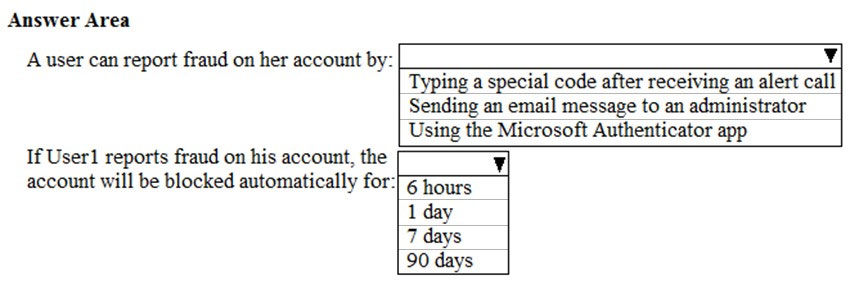
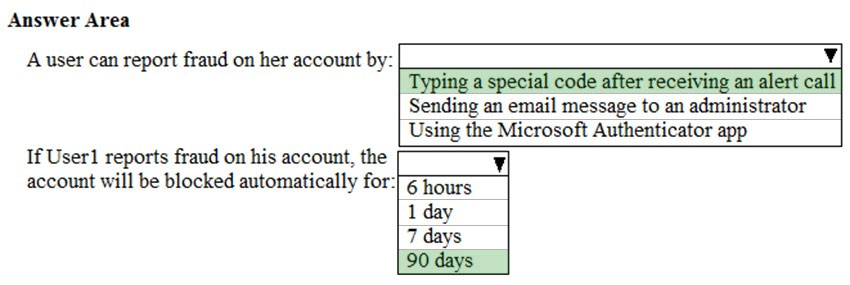
HOTSPOT - You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com that includes a user named User1. You enable multi-factor authentication for contoso.com and configure the following two fraud alert settings: ✑ Set Allow users to submit fraud alerts: On ✑ Automatically block users who report fraud: On You need to instruct the users in your organization to use the fraud reporting features correctly. What should you tell the users to do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You recently migrated your on-premises email solution to Microsoft Exchange Online and are evaluating which licenses to purchase. You want the members of two groups named IT and Managers to be able to use the features shown in the following table.The IT group contains 50 users. The Managers group contains 200 users. You need to recommend which licenses must be purchased for the planned solution. The solution must minimize licensing costs. Which licenses should you recommend?
A. 250 Microsoft 365 E3 only
B. 50 Microsoft 365 E3 and 200 Microsoft 365 E5
C. 250 Microsoft 365 E5 only
D. 200 Microsoft 365 E3 and 50 Microsoft 365 E5
Your company has configured all user email to be stored in Microsoft Exchange Online. You have been tasked with keeping a duplicate of all the email messages from a specified user that includes a specific word. Solution: You start by initiating a message trace via the Security & Compliance admin center. Does the solution meet the goal?
A. Yes
B. No
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. Your network contains an Active Directory forest. You deploy Microsoft 365. You plan to implement directory synchronization. You need to recommend a security solution for the synchronized identities. The solution must meet the following requirements: ✑ Users must be able to authenticate successfully to Microsoft 365 services if Active Directory becomes unavailable. ✑ User passwords must be 10 characters or more. Solution: Implement password hash synchronization and configure password protection in the Azure AD tenant. Does this meet the goal?
A. Yes
B. No
Your network contains an on-premises Active Directory domain named contoso.com that is synced to a Microsoft Azure Active Directory (Azure AD) tenant. The on-premises network contains a file server named Server1. Server1 has a share named Share1 that contains company documents. Your company purchases a Microsoft 365 subscription. You plan to migrate data from Share1 to Microsoft 365. Only data that was created or modified during the last three months will be migrated. You need to identify all the files in Share1 that were modified or created during the last 90 days. What should you use?
A. Server Manager
B. Microsoft SharePoint Migration Tool
C. Resource Monitor
D. Usage reports from the Microsoft 365 admin center
Your network contains an Active Directory domain. The domain contains a server named Server1 that runs Windows Server 2016. Server1 has a share named Share1. You have a hybrid deployment of Microsoft 365. You need to migrate the content in Share1 to Microsoft OneDrive. What should you use?
A. Windows Server Migration Tools
B. Microsoft SharePoint Migration Tool
C. Storage Migration Service
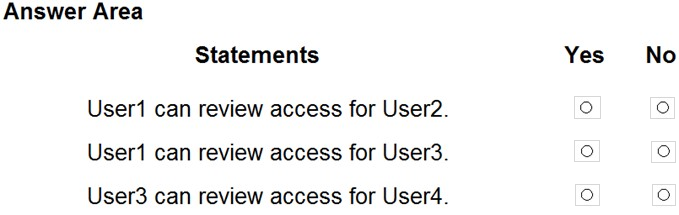
HOTSPOT - You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table.User1 is the owner of Group1. User2 is the owner of Group2. You create an access review that contains the following configurations: ✑ Users to review: Members of a group ✑ Scope: Everyone ✑ Group: Group1, Group2 Reviewers: Group owners -
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
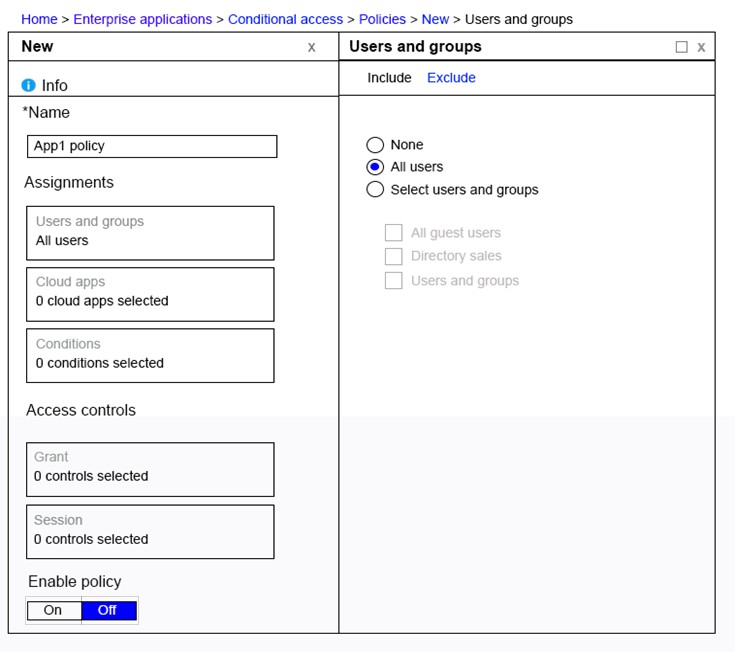
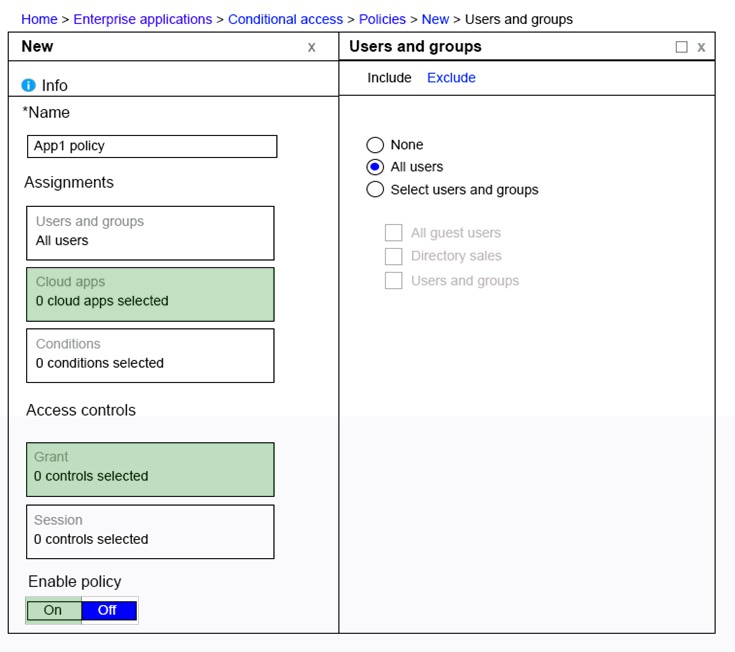
HOTSPOT - You have a Microsoft 365 Enterprise E5 subscription. You add a cloud-based app named App1 to the Microsoft Azure Active Directory (Azure AD) enterprise applications list. You need to ensure that two-step verification is enforced for all user accounts the next time they connect to App1. Which three settings should you configure from the policy? To answer, select the appropriate settings in the answer area. Hot Area:
Access Full MS-100 Exam Prep Free
Want to go beyond these 50 questions? Click here to unlock a full set of MS-100 exam prep free questions covering every domain tested on the exam.
We continuously update our content to ensure you have the most current and effective prep materials.
Good luck with your MS-100 certification journey!