MD-100 Exam Prep Free – 50 Practice Questions to Get You Ready for Exam Day
Getting ready for the MD-100 certification? Our MD-100 Exam Prep Free resource includes 50 exam-style questions designed to help you practice effectively and feel confident on test day
Effective MD-100 exam prep free is the key to success. With our free practice questions, you can:
- Get familiar with exam format and question style
- Identify which topics you’ve mastered—and which need more review
- Boost your confidence and reduce exam anxiety
Below, you will find 50 realistic MD-100 Exam Prep Free questions that cover key exam topics. These questions are designed to reflect the structure and challenge level of the actual exam, making them perfect for your study routine.
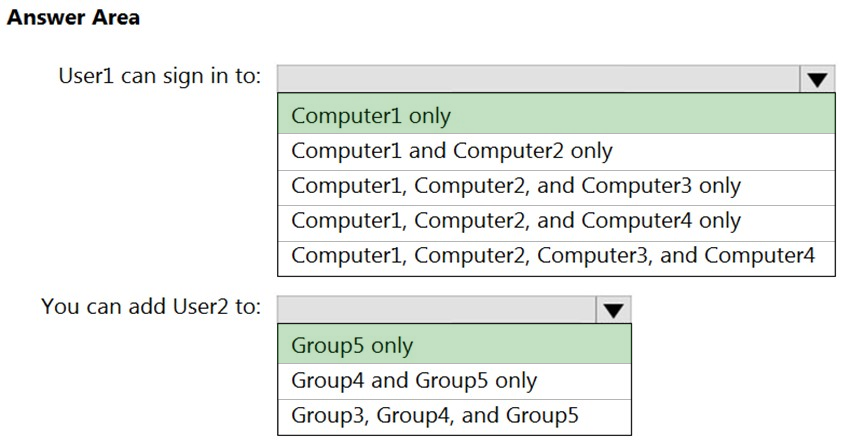
HOTSPOT - You have four computers that run Windows 10. The computers are configured as shown in the following table.On Computer1, you create a user named User1. In the domain, you create a user named User2. You create the groups shown in the following table.
You need to identify to which computers User1 can sign in, and to which groups you can add User2. What should you identify? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You plan to install Windows 10 Pro by using an answer file. You open Windows System Image Manager. You need to create an answer file. What should you do first?
A. Open the Install.wim file from the Windows 10 installation media.
B. Open the Boot.wim file from the Windows 10 installation media.
C. Install the WinPE add-on for the Windows Assessment and Deployment Kit (Windows ADK).
D. Install the Windows Assessment and Deployment Kit (Windows ADK).
You need to meet the technical requirement for User6. What should you do?
A. Add User6 to the Remote Desktop Users group in the domain.
B. Remove User6 from Group2 in the domain.
C. Add User6 to the Remote Desktop Users group on Computer2.
D. And User6 to the Administrators group on Computer2.
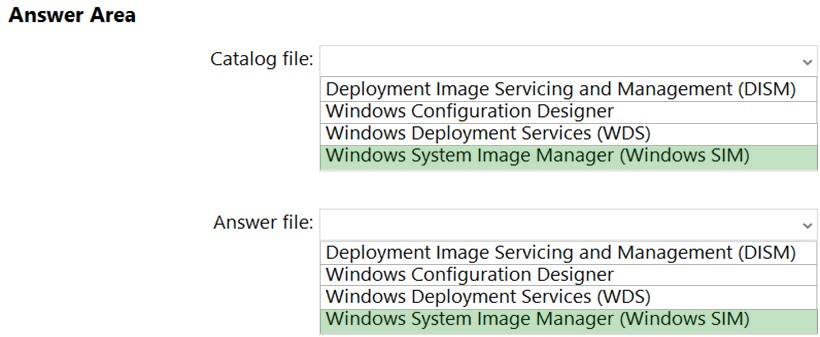
HOTSPOT - You plan to deploy Windows 10 Enterprise to company-owned devices. You capture a Windows 10 image file from a reference device. You need to generate catalog files and answer files for the deployment. What should you use for each file? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You deploy Windows 10 to 20 new laptops. The laptops will be used by users who work at customer sites. Each user will be assigned one laptop and one Android device. You need to recommend a solution to lock the laptop when the users leave their laptop for an extended period. Which two actions should you include in the recommendation? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Enable Bluetooth discovery.
B. From the Settings app, configure the Dynamic lock settings.
C. From Sign-in options, configure the Windows Hello settings.
D. From the Settings app, configure the Lock screen settings.
E. Pair the Android device and the laptop.
F. From the Settings app, configure the Screen timeout settings.
Your network contains an Active Directory domain. The domain contains a user named Admin1. All computers run Windows 10. You enable Windows PowerShell remoting on the computers. You need to ensure that Admin1 can establish remote PowerShell connections to the computers. The solution must use the principle of least privilege. To which group should you add Admin1?
A. Access Control Assistance Operators
B. Power Users
C. Remote Desktop Users
D. Remote Management Users
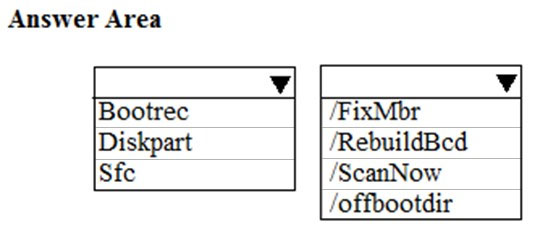
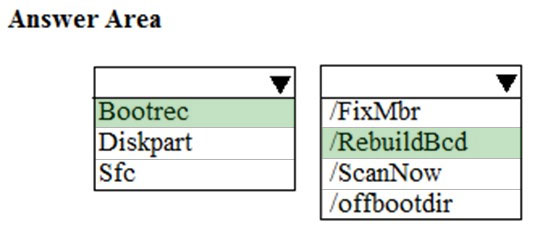
You have a computer that runs Windows 10. The computer fails to start, and you receive the following error message: `BOOTMGR image is corrupt. The system cannot boot`. You need to repair the system partition. Which command should you run from Windows Recovery Environment (WinRE)?
A. fdisk.exe
B. chkdsk.exe
C. diskpart.exe
D. bcdboot.exe
You have 10 computers that run Windows 10 and have BitLocker Drive Encryption (BitLocker) enabled. You plan to update the firmware of the computers. You need to ensure that you are not prompted for the BitLocker recovery key on the next restart. The drive must be protected by BitLocker on subsequent restarts. Which cmdlet should you run?
A. Unlock-BitLocker
B. Disable-BitLocker
C. Add-BitLockerKeyProtector
D. Suspend-BitLocker
You have a computer named Computer1. Computer1 runs Windows 10 Pro. You attempt to start Computer1 but you receive the following error message: Bootmgr is missing. You need to be able to start Computer1. What should you do?
A. Start the computer in recovery mode and run the bootrec /rebuildbcd command.
B. Start the computer in recovery mode and run the diskpart /repair command.
C. Start the computer in recovery mode and run the bcdboot /s command.
D. Start the computer in recovery mode and run the bootcfg /debug command.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. A user named User1 has a computer named Computer1 that runs Windows 10. Computer1 is joined to an Azure Active Directory (Azure AD) tenant named contoso.com. User1 joins Computer1 to contoso.com by using user1@contoso.com . Computer1 contains a folder named Folder1. Folder1 is in drive C and is shared as Share1. Share1 has the permission shown in the following table.A user named User2 has a computer named Computer2 that runs Windows 10. User2 joins Computer2 to contoso.com by using user2@contoso.com . User2 attempts to access Share1 and receives the following error message: `The username or password is incorrect.` You need to ensure that User2 can connect to Share1. Solution: You create a local user account on Computer1 and instruct User2 to use the local account to connect to Share1. Does this meet the goal?
A. Yes
B. No
You have a computer named Computer1 that runs Windows 10. You restart Computer1 by using Advanced startup and select Boot log. In which folder is the boot log file stored?
A. C:
B. C:Windows
C. C:Windowsdebug
D. C:WindowsSystem32LogFiles
You have a computer that runs Windows 10 Pro. The computer contains the users shown in the following table.You need to use a local Group Policy Object (GPO) to configure one group of settings for all the members of the local Administrators group and another group of settings for all non-administrators. What should you do?
A. Use the runas command to open Gpedit.msc as each user.
B. Run mmc as User1 and add the Group Policy Object Editor snap-in twice.
C. Open Gpedit.msc as User1 and add two Administrative Templates.
D. Run mmc as User1 and add the Security Templates snap-in twice.
Your network contains an Active Directory domain. The domain contains a user named User1. User1 creates a Microsoft account. User1 needs to sign in to cloud resources by using the Microsoft account without being prompted for credentials. Which settings should User1 configure?
A. User Accounts in Control Panel
B. Email & app accounts in the Settings app
C. Users in Computer Management
D. Users in Active Directory Users and Computers
You have several computers that run Windows 10. All users have Microsoft OneDrive for Business installed. Users frequently save files to their desktop. You need to ensure that all the users can recover the files on their desktop from OneDrive for Business. Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Copy ADMX and ADML files to C:UsersPublicDesktop
B. From Backup in the Settings app, add a drive
C. Configure the Silently move Windows known folders to OneDrive settings
D. Copy ADMX and ADML files to C:WindowsPolicyDefinitions
E. Configure the Save documents to OneDrive by default setting
Your company has a Remote Desktop Gateway (RD Gateway). You have a server named Server1 that is accessible by using Remote Desktop Services (RDS) through the RD Gateway. You need to configure a Remote Desktop connection to connect through the gateway. Which setting should you configure?
A. Connection settings
B. Server authentication
C. Local devices and resources
D. Connect from anywhere
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a computer that runs Windows 10. The computer contains a folder named D:Scripts. D:Scripts contains several PowerShell scripts. You need to ensure that you can run the PowerShell scripts without specifying the full path to the scripts. The solution must persist between PowerShell sessions. Solution: From PowerShell, you run $env:Path += ";d:scripts". Does this meet the goal?
A. Yes
B. No
Your network contains an Active Directory domain. The domain contains 1,000 computers that run Windows 10. You need to prevent the computers of the research department from appearing in Network in File Explorer. What should you do?
A. Configure DNS to use an external provider
B. Modify the %systemroot%system32driversetcNetworks file.
C. Turn off network discovery.
D. Disable the Network List Service.
Your company has an isolated network used for testing. The network contains 20 computers that run Windows 10. The computers are in a workgroup. During testing, the computers must remain in the workgroup. You discover that none of the computers are activated. You need to recommend a solution to activate the computers without connecting the network to the Internet. What should you include in the recommendation?
A. Volume Activation Management Tool (VAMT)
B. Key Management Service (KMS)
C. Active Directory-based activation
D. the Get-WindowsDeveloperLicense cmdlet
You have a computer named Computer1 that runs Windows 10. Computer1 was off for one year. During that time, two feature updates and 12 quality updates were released. From the Microsoft Update Catalog website, you download the missing updates and save the updates to Computer1. You need to ensure that Computer1 runs the latest version of Windows 10 and is fully updated. The solution must minimize the amount of time required to update the computer. What should you do?
A. Install the last feature update, and then install the last quality update.
B. Install the last quality update, and then install both feature updates.
C. Install the last quality update, and then install the last feature update.
D. Install the last feature update, and then install all the quality updates released after the feature update.
E. Install all the quality and feature updates in the order in which they were released.
SIMULATION - You have a computer named Computer1. Computer1 runs Windows 10 Pro. You have a mobile device. You use Bluetooth to pair the mobile device to Computer1. You want to enable dynamic lock on Computer1. What should you do? To complete this task, sign in to the required computer or computers.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a workgroup computer that runs Windows 10. The computer contains the local user accounts shown in the following table.You need to configure the desktop background for User1 and User2 only. Solution: You create a new local group to which you add User1 and User2. You create a local Group Policy Object (GPO) and configure the Desktop Wallpaper setting in the GPO. At a command prompt, you run the gpupdate.exe /Force command. Does this meet the goal?
A. Yes
B. No
You have a computer that runs Windows 10. You need to configure a picture password. What should you do?
A. From Control Panel, configure the User Accounts settings.
B. From the Settings app, configure the Sign-in options.
C. From the Local Group Policy Editor, configure the Account Policies settings.
D. From Windows PowerShell, run the Set-LocalUser cmdlet and specify the InputObject parameter.
HOTSPOT - You have three devices as shown in the following table.You plan to install Windows 10 on the devices. You need to identify which devices support Secure Boot, and which Windows 10 edition is supported for up to 30 months. What should you identify? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have computers that run Windows 10. The computers are joined to an Azure Active Directory (Azure AD) tenant and enrolled in Microsoft Intune. You need to recommend a solution for help desk administrators that meets the following requirements: ✑ The administrators must assist users remotely by connecting to each user's computer. ✑ The remote connections must be initiated by the administrators. The users must approve the connection. ✑ Both the users and the administrators must be able to see the screen of the users' computer. ✑ The administrators must be able to make changes that require running applications as a member of each computer's Administrators group. Which tool should you include in the recommendation?
A. Remote Desktop
B. Intune
C. Remote Assistance
D. Quick Assist
A user has a computer that runs Windows 10. The user has access to the following storage locations: ✑ A USB flash drive ✑ Microsoft OneDrive ✑ OneDrive for Business ✑ A drive mapped to a network share ✑ A secondary partition on the system drive You need to configure Back up using File History from the Settings app. Which two storage locations can you select for storing File History data? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. OneDrive for Business
B. OneDrive
C. the USB flash drive
D. the secondary partition on the system drive
E. the drive mapped to a network share
You have a Microsoft 365 Enterprise E3 license. You have a computer named Computer1 that runs Windows 10. You need to ensure that you can access the files on Computer1 by using a web browser on another computer. What should you configure?
A. Sync your settings in the Settings app
B. the File Explorer desktop app
C. the Microsoft OneDrive desktop app
D. Default apps in the Settings app
HOTSPOT - You are a network administrator at your company. A user attempts to start a computer and receives the following error message: `Bootmgr is missing.` You need to resolve the issue. You start the computer in recovery mode. Which command should you run next? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
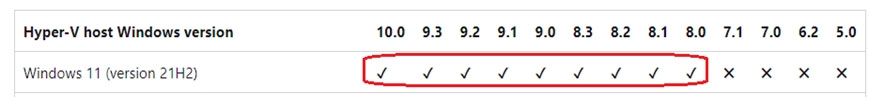
You have a computer that runs Windows 10 and hosts four Hyper-V virtual machines that run Windows 10. You upgrade the computer to Windows 11. You need to ensure that the virtual machines support hibernation. What should you do?
A. Enable integration services.
B. Delete any virtual machine checkpoints.
C. Rebuild the virtual machines as generation 2 virtual machines.
D. Update the configuration version of the virtual machines.
Your network contains an Active Directory domain. The domain contains 500 computers that run Windows 10. The computers are used as shown in the following table.You need to apply updates based on the computer usage. What should you configure?
A. Notifications & actions from System in the Settings apps.
B. the Windows Update for Business settings by using a Group Policy Object (GPO)
C. the Windows Installer settings by using a Group Policy Object (GPO)
D. Delivery Optimization from Update & Security in the Settings apps
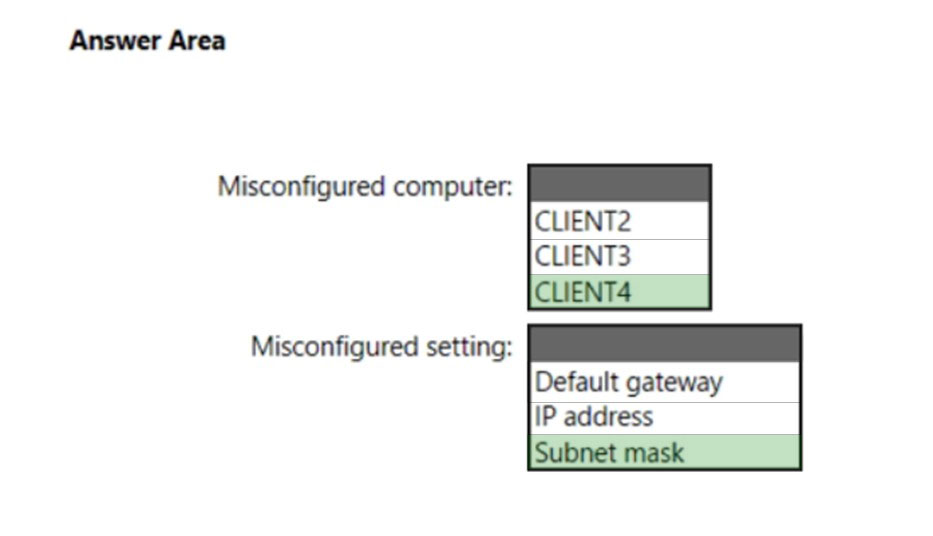
HOTSPOT - You have computers that run Windows 10 as shown in the following table.CLIENT1 has the following IP configuration.
From CLIENT1, you ping CLIENT2 and CLIENT3 successfully, but when you ping CLIENT4, you get a Request timed out response. From CLIENT3, you ping CLIENT4 successfully. Which computer and setting are misconfigured? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You need to meet the technical requirements for EFS on ComputerA. What should you do?
A. Run certutil.exe, and then add a certificate to the local computer certificate store.
B. Run cipher.exe, and then add a certificate to the local computer certificate store.
C. Run cipher.exe, and then add a certificate to the local Group Policy.
D. Run certutil.exe, and then add a certificate to the local Group Policy.
SIMULATION - Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time. When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design. Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn't matter how you accomplish the task, if you successfully perform it, you will earn credit for that task. Labs are not timed separately, and this exam may more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided. Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab. Username and password -Use the following login credentials as needed: To enter your password, place your cursor in the Enter password box and click on the password below. Username: Contoso/Administrator - Password: Passw0rd! The following information is for technical support purposes only: Lab Instance: 10921597 -
You need to create a file named Private.txt in a folder named Folder1 on the C drive of Client2. You need to encrypt Private.txt and ensure that a user named User1 can view the contents of Private.txt. To complete this task, sign in to the required computer or computers.
You have a computer named Computer1 that runs Windows 10. You complete a full back up of Computer1 to an external USB drive. You store the USB drive offsite. You delete several files from your personal Microsoft OneDrive account by using File Explorer, and then you empty the Recycle Bin on Computer1. You need to recover the files 60 days after you deleted them in the least amount of time possible. What should you use?
A. the OneDrive recycle bin
B. the full backup on the external USB drive
C. Recovery in the Settings app
You have a computer that runs Windows 10 and contains a user named User1 and the following local Group Policy Objects (GPOs): • Local Computer Policy • Local ComputerUser1 Policy • Local ComputerAdministrators Policy • Local ComputerNon-Administrators Policy You need to ensure that User1 must use a password that is at least 10 characters. Which GPO should you modify?
A. Local Computer Policy
B. Local ComputerAdministrators Policy
C. Local Computer Non-Administrators Policy
D. Local ComputerUser1 Policy
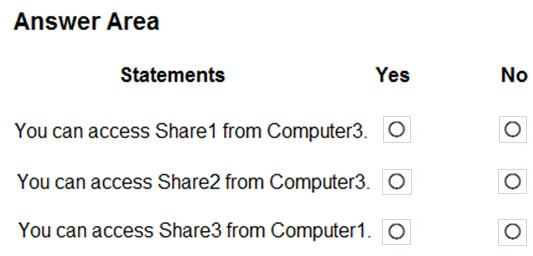
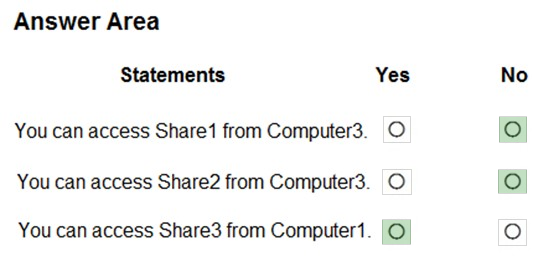
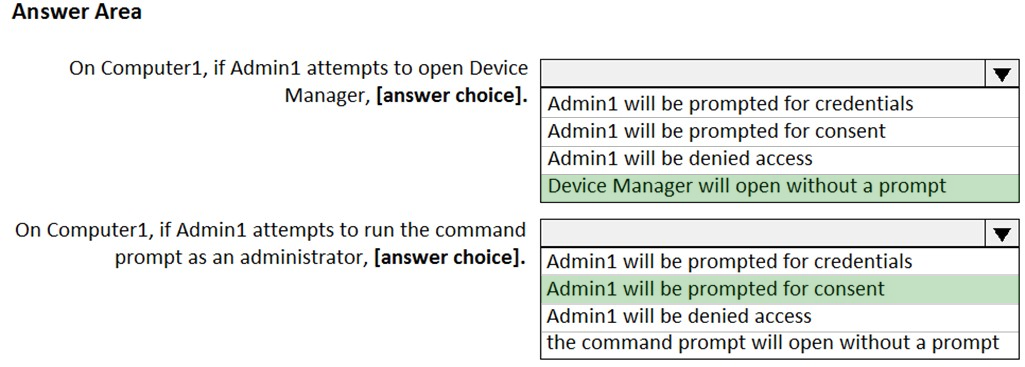
HOTSPOT - Your network contains an Active Directory domain named contoso.com. The domain contains two computers named Computer1 and Computer2 that run Windows 10. The domain contains the users shown in the following table.The relevant group membership on Computer1 is shown in the following table.
The relevant group membership on Computer2 is shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
You have a Windows 11 Pro device. You need to perform a scan in Microsoft Defender to check for rootkits. Which type of scan should you use?
A. full
B. offline
C. custom
D. quick
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You manage devices that run Windows 10. Ten sales users will travel to a location that has limited bandwidth that is expensive. The sales users will be at the location for three weeks. You need to prevent all Windows updates from downloading for the duration of the trip. The solution must not prevent access to email and the Internet. Solution: From Accounts in the Settings app, you turn off Sync settings. Does this meet the goal?
A. Yes
B. No
Your network contains an Active Directory domain. The domain contains 10 computers that run Windows 10. Users in the finance department use the computers. You have a computer named Computer1 that runs Windows 10. From Computer1, you plan to run a script that executes Windows PowerShell commands on the finance department computers. You need to ensure that you can run the PowerShell commands on the finance department computers from Computer1. What should you do on the finance department computers?
A. From the local Group Policy, enable the Allow Remote Shell Access setting.
B. From the local Group Policy, enable the Turn on Script Execution setting.
C. From the Windows PowerShell, run the Enable-MMAgent cmdlet.
D. From the Windows PowerShell, run the Enable-PSRemoting cmdlet.
You have a computer that runs Windows 11 and hosts the Hyper-V virtual machines shown in the following table.You need to install Windows 11 on a virtual machine. On which virtual machine can you install Windows 11?
A. VM2 only
B. VM4 only
C. VM2 and VM4 only
D. VM2 and VM4 only
E. VM1, VM2, VM3, and VM4
You manage devices that run Windows 10. Ten sales users will travel to a location that has limited bandwidth that is expensive. The sales users will be at the location for three weeks. You need to prevent all Windows updates from downloading for the duration of the trip. The solution must not prevent access to email and the Internet. What should you do?
A. From Network & Internet in the Settings app, set a data limit.
B. From Accounts in the Settings app, turn off Sync settings.
C. From Network & Internet in the Settings app, set the network connections as metered connections.
D. From Update & Security in the Settings app, pause updates.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a computer that runs Windows 10. The computer contains a folder. The folder contains sensitive data. You need to log which user reads the contents of the folder and modifies and deletes files in the folder. Solution: From the properties of the folder, you configure the Auditing settings and from the Audit Policy in the local Group Policy, you configure Audit directory service access. Does this meet the goal?
A. Yes
B. No
Which users can create a new group on Computer3?
A. User31 and User32 only
B. Admin1, User31, and User32 only
C. User31 only
D. Admin1 and User31 only
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a computer named Computer1 that runs Windows 10. A service named Application1 is configured as shown in the exhibit.You discover that a user used the Service1 account to sign in to Computer1 and deleted some files. You need to ensure that the identity used by Application1 cannot be used by a user to sign in to sign in to the desktop on Computer1. The solution must use the principle of least privilege. Solution: On Computer1, you assign Service1 the Deny log on as a service user right. Does this meet the goal?
A. Yes
B. No
You install Windows 10 Pro on a computer named CLIENT1 and join the device to an Active Directory domain. You need to ensure that all per-user services are disabled on CLIENT1. The solution must minimize administrative effort. What should you use?
A. the sc command
B. Task Manager
C. Services
D. the sfc command
Your network contains an Active Directory domain. The domain contains a computer named Computer1 that runs Windows 10. The domain contains the users shown in the following table.Computer1 has the local users shown in the following table.
All users have Microsoft accounts. Which two users can be configured to sign in by using their Microsoft account? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. User1
B. User2
C. User3
D. User4
E. User5
HOTSPOT - Your network contains the segments shown in the following table.You have computers that run Windows 10 and are configured as shown in the following table.
Windows Defender Firewall has the File and Printer Sharing allowed apps rule shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
You have a workgroup computer that runs Windows 10. You create a local user named User1. User1 needs to be able to share and manage folders located in a folder named C:Share by using the Shared Folders snap-in. The solution must use the principle of least privilege. To which group should you add User1?
A. Administrators
B. Device Owners
C. Users
D. Power Users
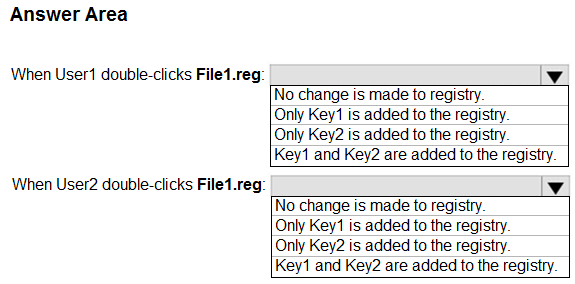
HOTSPOT - You have a workgroup computer named Computer1 that runs Windows 10 and has the users shown in the following table.You have a file named File1.reg that contains the following content.
You need to identify what occurs when User1 and User2 double-click File1.reg. What should you identify? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have a computer named Computer1 that runs Windows 10. You need to prevent standard users from changing the wireless network settings on Computer1. The solution must allow administrators to modify the wireless network settings. What should you use?
A. Windows Configuration Designer
B. MSConfig
C. Local Group Policy Editor
D. an MMC console that has the Group Policy Object Editor snap-in
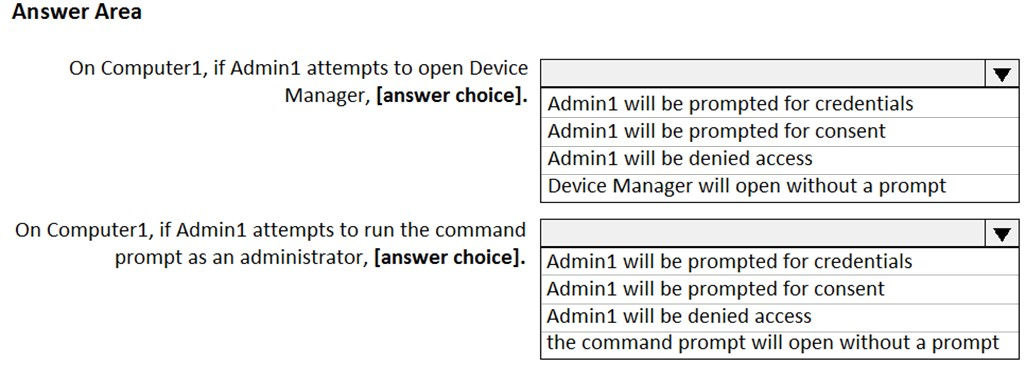
HOTSPOT - You have a computer named Computer1 that runs Windows 10 and is joined to an Active Directory domain named adatum.com. A user named Admin1 signs in to Computer1 and runs the whoami command as shown in the following exhibit.Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point. Hot Area:
Access Full MD-100 Exam Prep Free
Want to go beyond these 50 questions? Click here to unlock a full set of MD-100 exam prep free questions covering every domain tested on the exam.
We continuously update our content to ensure you have the most current and effective prep materials.
Good luck with your MD-100 certification journey!