CCNA Exam Prep Free – 50 Practice Questions to Get You Ready for Exam Day
Getting ready for the CCNA certification? Our CCNA Exam Prep Free resource includes 50 exam-style questions designed to help you practice effectively and feel confident on test day
Effective CCNA exam prep free is the key to success. With our free practice questions, you can:
- Get familiar with exam format and question style
- Identify which topics you’ve mastered—and which need more review
- Boost your confidence and reduce exam anxiety
Below, you will find 50 realistic CCNA Exam Prep Free questions that cover key exam topics. These questions are designed to reflect the structure and challenge level of the actual exam, making them perfect for your study routine.
Which physical component is distributed among multiple virtual machines running on the same hypervisor?
A. external storage
B. network interfaces
C. backplane network
D. hardware resources
What is a requirement for nonoverlapping Wi-Fi channels?
A. different security settings
B. discontinuous frequency ranges
C. unique SSIDs
D. different transmission speeds
Refer to the exhibit. Which path is used by the router for Internet traffic?
A. 209.165.200.0/27
B. 0.0.0.0/0
C. 10.10.13.0/24
D. 10.10.10.0/28
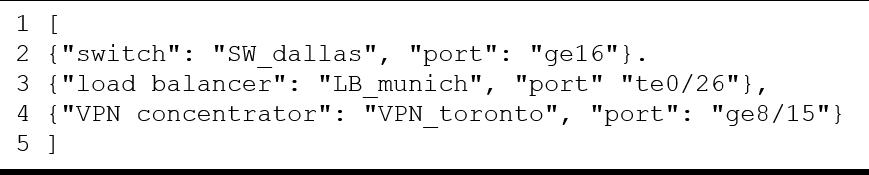
What is represented in line 2 within this JSON schema?
A. object
B. value
C. key
D. array
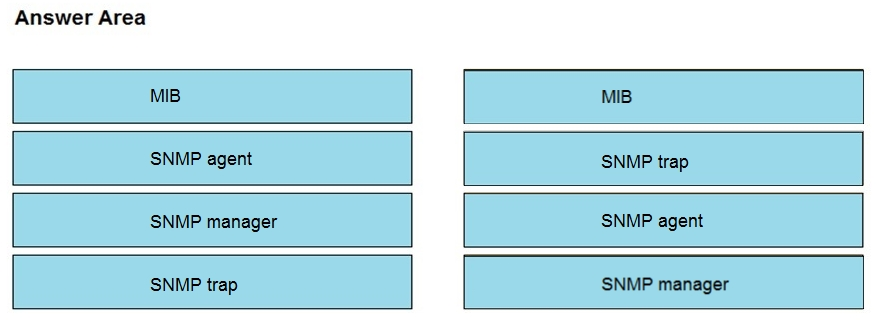
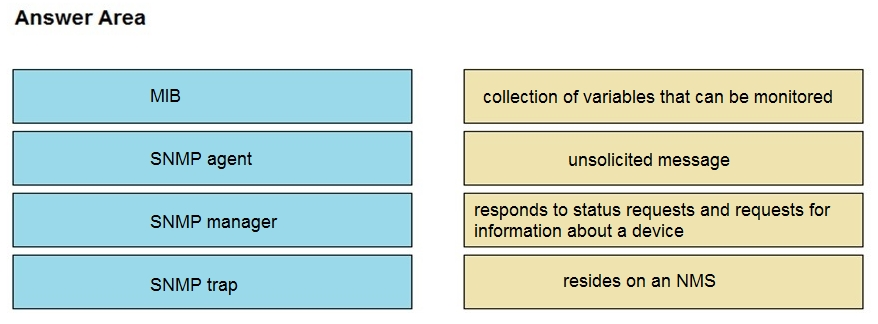
Drag and drop the SNMP components from the left onto the descriptions on the right.
Select and Place:
Which cable type must be used to interconnect one switch using 1000 BASE-SX GBIC modules and another switch using 1000 BASE-SX SFP modules?
A. LC to SC
B. SC to SC
C. LC to LC
D. SC to ST
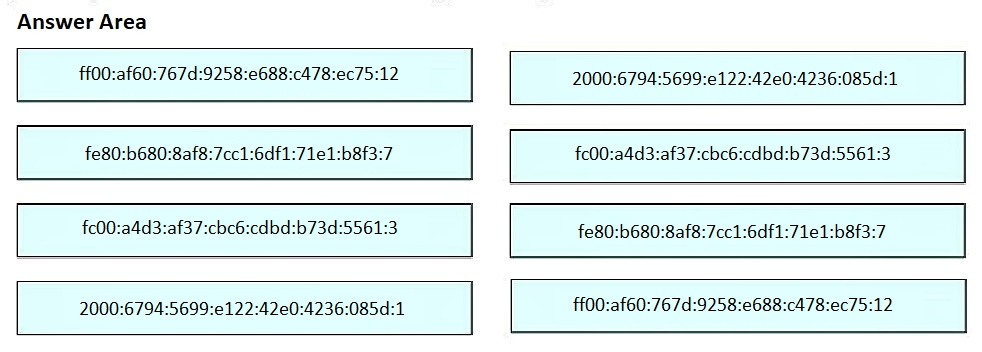
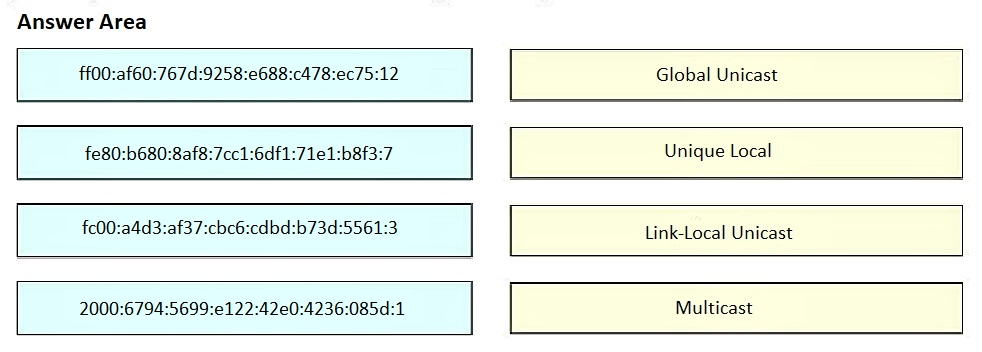
Drag and drop the IPv6 address from the left onto the type on the right.
Select and Place:
Refer to the exhibit. An engineer is asked to configure router R1 so that it forms an OSPF single-area neighbor relationship with R2. Which command sequence must be implemented to configure the router?
A. router ospf 100 network 10.0.0.0 0.0.0.252 area0 network 10.0.1.0 0.0.0.255 area0
B. router ospf 100 network 10.0.0.0 0.0.0.3 area0 network 10.0.2.0 255.255.255.0 area0
C. router ospf 10 network 10.0.0.0 0.0.0.3 area0 network 10.0.1.0 0.0.0.255 area0
D. router ospf 10 network 10.0.0.0 0.0.0.3 area0 network 10.0.2.0 0.0.0.255 area0 C
Which device performs stateful inspection of traffic?
A. switch
B. firewall
C. access point
D. wireless controller
Which syslog message logging level displays interface line protocol up/down events?
A. informational
B. alerts
C. debugging
D. notifications
What is used as a solution for protecting an individual network endpoint from attack?
A. antivirus software
B. wireless controller
C. router
D. Cisco DNA Center
Refer to the exhibit. A packet is being sent across router R1 to host 172.16.0.14. What is the destination route for the packet?
A. 209.165.200.250 via Serial0/0/0
B. 209.165.200.254 via Serial0/0/0
C. 209.165.200.254 via Serial0/0/1
D. 209.165.200.246 via Serial0/1/0
In which circumstance would a network architect decide to implement a global unicast subnet instead of a unique local unicast subnet?
A. when the subnet must be available only within an organization
B. when the subnet does not need to be routable
C. when the addresses on the subnet must be equivalent to private IPv4 addresses
D. when the subnet must be routable over the internet
Which three describe the reasons large OSPF networks use a hierarchical design? (Choose three.)
A. to speed up convergence
B. to reduce routing overhead
C. to lower costs by replacing routers with distribution layer switches
D. to decrease latency by increasing bandwidth
E. to con ne network instability to single areas of the network
F. to reduce the complexity of router configuration
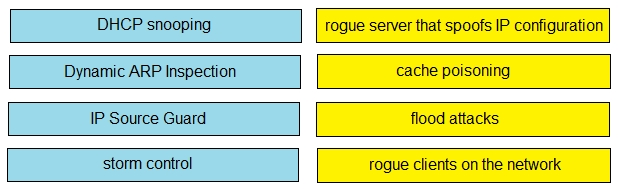
A network administrator must enable DHCP services between two sites. What must be configured for the router to pass DHCPDISCOVER messages on to the server?
A. DHCP Binding
B. a DHCP Relay Agent
C. DHCP Snooping
D. a DHCP Pool
Refer to the exhibit. An administrator must connect SW_1 and the printer to the network. SW_2 requires DTP to be used for the connection to SW_1. The printer is configured as an access port with VLAN 5. Which set of commands completes the connectivity?
A. switchport mode dynamic auto
switchport private-vlan association host 5
B. switchport mode trunk
switchport trunk pruning vlan add 5
C. switchport mode dynamic desirable
switchport trunk allowed vlan add 5
D. switchport mode dynamic auto
switchport trunk encapsulation negotiate
What is the primary function of a Layer 3 device?
A. to transmit wireless traffic between hosts
B. to analyze traffic and drop unauthorized traffic from the Internet
C. to forward traffic within the same broadcast domain
D. to pass traffic between different networks
Which interface mode must be configured to connect the lightweight APs in a centralized architecture?
A. WLAN dynamic
B. trunk
C. access
D. management
Which type if network attack overwhelms the target server by sending multiple packets to a port until the half-open TCP resources of the target are exhausted?
A. SYN ood
B. reflection
C. teardrop
D. ampli cation
How do TCP and UDP differ in the way they provide reliability for delivery of packets?
A. TCP does not guarantee delivery or error checking to ensure that there is no corruption of data, UDP provides message acknowledgement and retransmits data if lost.
B. TCP provides flow control to avoid overwhelming a receiver by sending too many packets at once, UDP sends packets to the receiver in a continuous stream without checking.
C. TCP is a connectionless protocol that does not provide reliable delivery of data; UDP is a connection-oriented protocol that uses sequencing to provide reliable delivery.
D. TCP uses windowing to deliver packets reliably; UDP provides reliable message transfer between hosts by establishing a three-way handshake.
Refer to the exhibit. An engineer assumes a configuration task from a peer. Router A must establish an OSPF neighbor relationship with neighbor 172.1.1.1. The output displays the status of the adjacency after 2 hours. What is the next step in the configuration process for the routers to establish an adjacency?
A. configure router A to use the same MTU size as router
B. configure a point-to-point link between router A and router
C. Set the router B OSPF ID to the same value as its IP address.
D. Set the router B OSPF ID to a nonhost address.
When deploying a new network that includes both Cisco and third-party network devices, which redundancy protocol avoids the interruption of network traffic if the default gateway router fails?
A. VRRP
B. FHRP
C. GLBP
D. HSRP
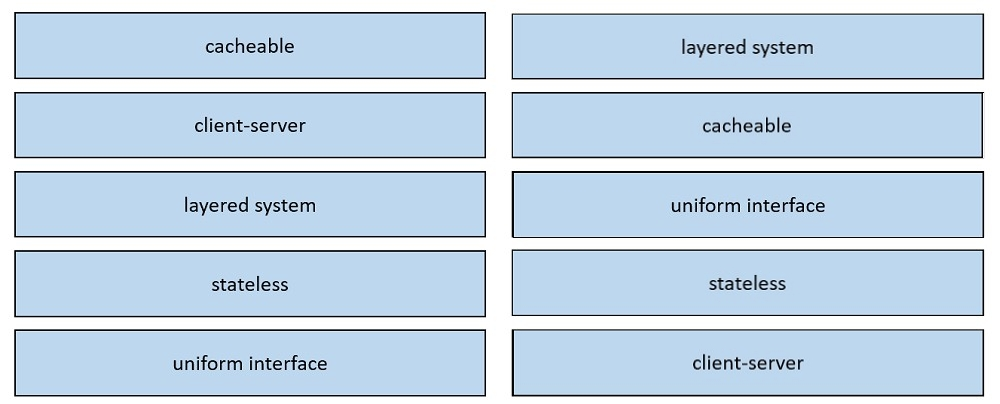
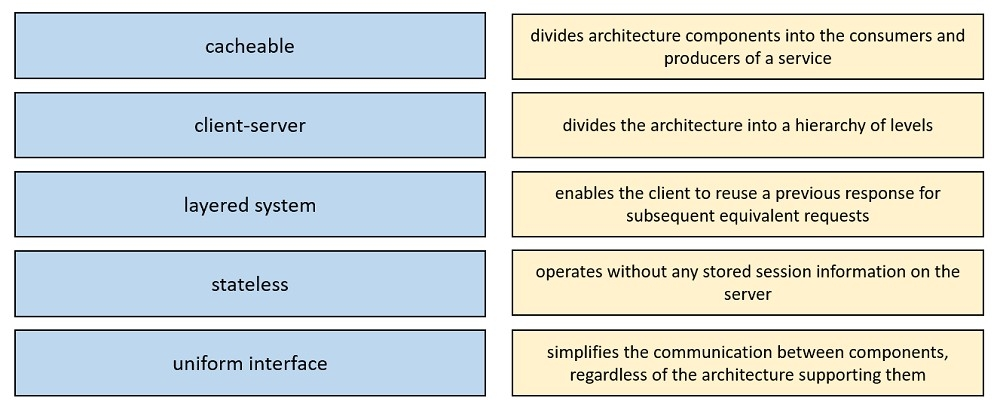
Drag and drop the REST principles from the left onto their definitions on the right.
Select and Place:

Refer to the exhibit. Which switch becomes the root of the spanning tree?
A. Switch 1
B. Switch 2
C. Switch 3
D. Switch 4
Drag and drop the characteristic from the left onto the cable type on the right.
Select and Place:

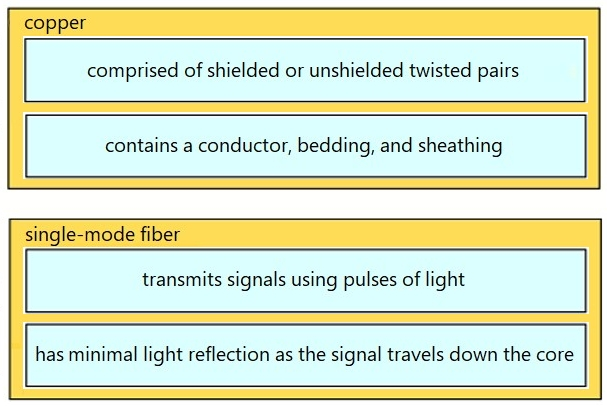
Refer to the exhibit. The engineer configured the VLANs on the new AccSw2 switch. A router-on-a-stick is connected to both switches. How must the ports be configured on AccSw2 to establish full connectivity between the two switches and for Server1?
A. interface GigabitEthernet1/1
switchport access vlan 11
interface GigabitEthernet1/24
switchport mode trunk
switchport trunk allowed vlan 10,11
B. interface GigabitEthernet1/3
switchport mode access
switchport access vlan 10
interface GigabitEthernet1/24
switchport mode trunk
switchport trunk allowed vlan 2,10
C. interface GigabitEthernet1/3
switchport mode access
switchport access vlan 10
interface GigabitEthernet1/24
switchport mode trunk
D. interface GigabitEthernet1/1
switchport mode access
switchport access vlan 11
interface GigabitEthernet1/24
switchport mode trunk
Which command enables HTTP access to the Cisco WLC?
A. config network telnet enable
B. config network secureweb enable
C. config certificate generate webadmin
D. config network webmode enable
Why would a network administrator choose to implement automation in a network environment?
A. To simplify the process of maintaining a consistent configuration state across all devices
B. Tofficentralize device information storage
C. To implement centralized user account management
D. To deploy the management plane separately from the rest of the network
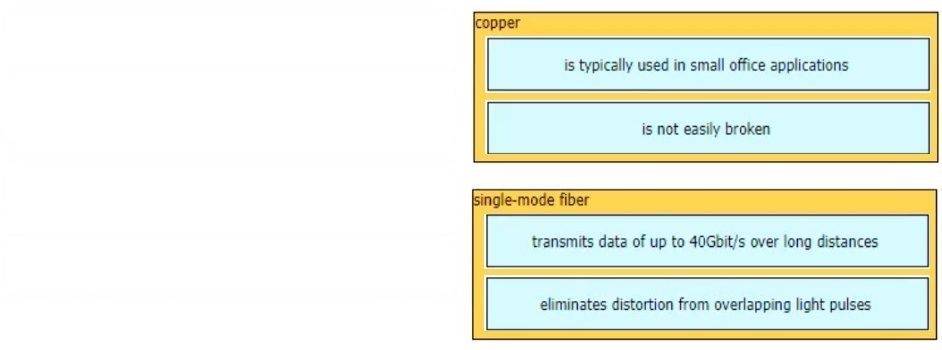
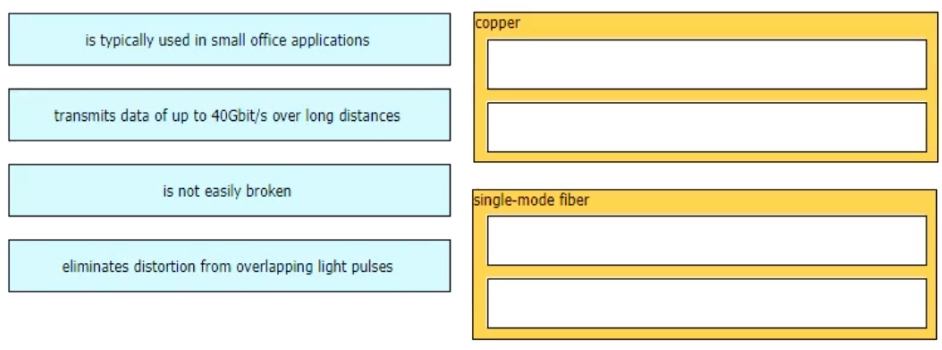
What are two differences between optical- fiber cabling and copper cabling? (Choose two.)
A. A BNC connector is used for fiber connections
B. The glass core component is encased in a cladding
C. The data can pass through the cladding
D. Light is transmitted through the core of the fiber
E. Fiber connects to physical interfaces using RJ-45 connections
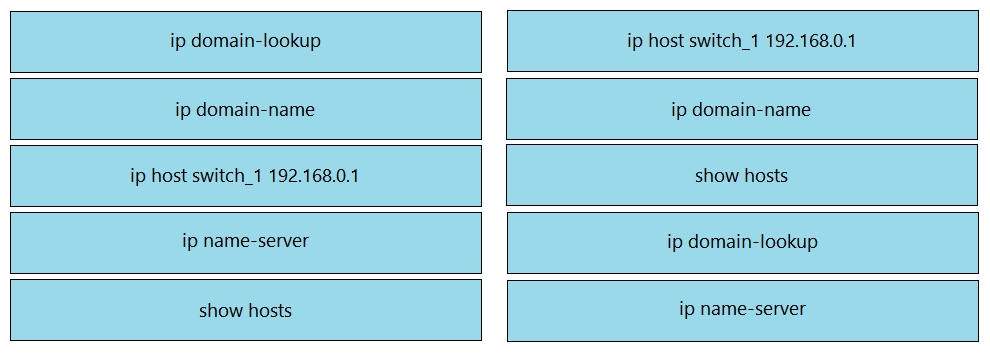
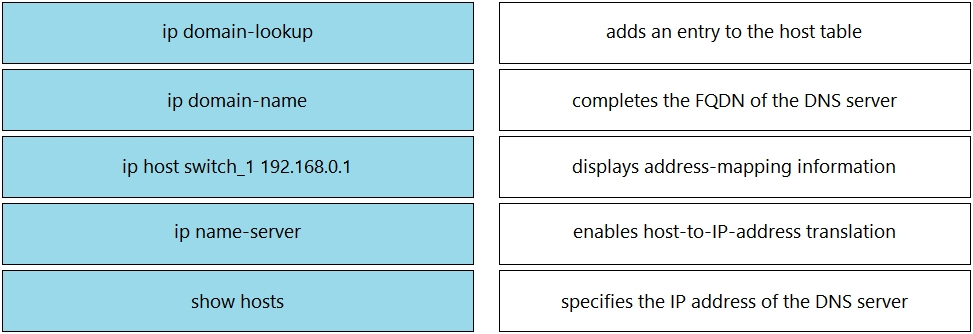
Drag and drop the DNS commands from the left onto their effects on the right.
Select and Place:
DRAG DROP - Drag and drop the characteristic from the left onto the IPv6 address type on the right.
Drag and drop the characteristic from the left onto the cable type on the right.
Select and Place:
0 What is a characteristic of private IPv4 addressing?
A. is used when the ISP requires the new subnet to be advertised to the internet for web services
B. allows multiple companies to use the same addresses without conflict
C. is used on the external interface of a firewall
D. allows endpoints to communicate across public network boundaries
Which command implies the use of SNMPv3?
A. snmp-server user
B. snmp-server host
C. snmp-server enable traps
D. snmp-server community
How does MAC learning function?
A. sends a retransmission request when a new frame is received
B. enabled by default on all VLANs and interfaces
C. populates the ARP table with the egress port
D. protects against denial of service attacks
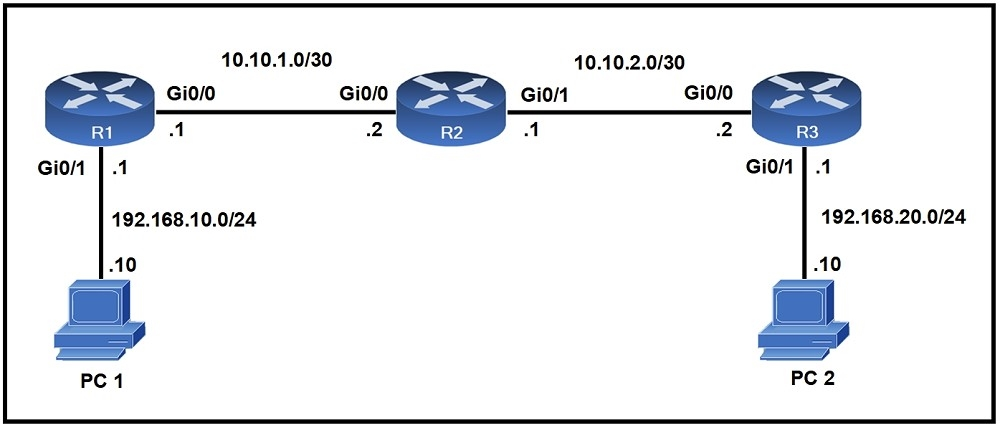
Refer to the exhibit. When PC1 sends a packet to PC2, the packet has which source and destination IP address when it arrives at interface Gi0/0 on router R2?
A. source 192.168.10.10 and destination 10.10.2.2
B. source 192.168.20.10 and destination 192.168.20.1
C. source 192.168.10.10 and destination 192.168.20.10
D. source 10.10.1.1 and destination 10.10.2.2
Refer to the exhibit. Which switch becomes the root bridge?
A. SW 1 –
Bridge Priority – 20480 –
mac-address 00:10:a1:71 :e3:35
B. SW 2 –
Bridge Priority – 20480 –
mac-address 00:10:a1:54:4e:50
C. SW 3 –
Bridge Priority – 57344 –
mac-address 00:10:a1:93:09:2d
D. SW 4 –
Bridge Priority – 57344 –
mac-address 00:10:a1:57:61:80
Which spanning-tree enhancement avoids the learning and listening states and immediately places ports in the forwarding state?
A. BPDU filter
B. PortFast
C. Backbonefast
D. BPDUguard
Drag and drop the Cisco IOS attack mitigation features from the left onto the types of network attack they mitigate on the right.
Select and Place:

Refer to the exhibit. Wireless LAN access must be set up to force all clients from the NA WLAN to authenticate against the local database. The WLAN is configured for local EAP authentication. The time that users access the network must not be limited. Which action completes this configuration?
A. Check the Guest User Role check box.
B. Uncheck the Guest User check box.
C. Set the Lifetime (seconds) value to 0.
D. Clear the Lifetime (seconds) value.
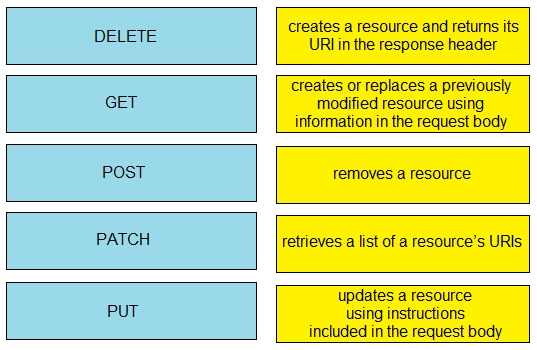
Drag and drop the HTTP methods used with REST based APIs from the left onto the descriptions on the right.
Select and Place:
Which interface is used to send traffic to the destination network?
A. F0/9
B. F0/16
C. F0/7
D. F0/24
What is a function of Opportunistic Wireless Encryption in an environment?
A. provide authentication
B. protect traffic on open networks
C. offer compression
D. increase security by using a WEP connection
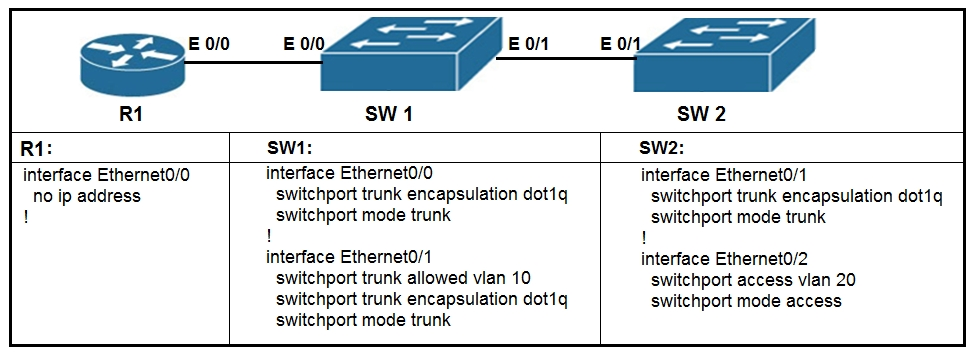
Refer to the exhibit. What commands are needed to add a sub-interface to Ethernet0/0 on R1 to allow for VLAN 20, with IP address 10.20.20.1/24?
A. R1(config)#interface ethernet0/0 R1(config-if)#encapsulation dot1q 20 R1(config-if)#ip address 10.20.20.1 255.255.255.0
B. R1(config)#interface ethernet0/0.20 R1(config-if)#encapsulation dot1q 20 R1(config-if)#ip address 10.20.20.1 255.255.255.0
C. R1(config)#interface ethernet0/0.20 R1(config-if)#ip address 10.20.20.1 255.255.255.0
D. R1(config)#interface ethernet0/0 R1(config-if)#ip address 10.20.20.1 255.255.255.0
Refer to the exhibit. After the switch configuration, the ping test fails between PC A and PC
A. Based on the output for switch 1, which error must be corrected?
B. The PCs are in the incorrect VLAN.
C. All VLANs are not enabled on the trunk.
D. Access mode is configured on the switch ports.
E. There is a native VLAN mismatch.
What is represented in line 3 within this JSON schema?
A. object
B. key
C. value
D. array
Which encryption mode is used when a packet is sent from a site-to-site VPN connection where the source and destination IP address portion of a packet is unencrypted?
A. PPTP
B. Secure Shell
C. Transport
D. PPPoE
Which configuration command can you apply to a HSRP router so that its local interface becomes active if all other routers in the group fail?
A. no additional config is required
B. standby 1 track ethernet
C. standby 1 preempt
D. standby 1 priority 250
With preemption disabled, the new router does not preempt the current active router, unless routers in the group have to renegotiate their roles based on each router’s priority at the time of negotiation.
Refer to the exhibit. Which configuration allows routers R14 and R86 to form an OSPFv2 adjacency while acting as a central point for exchanging OSPF information between routers?
A. R14# interface FastEthernet0/0 ip address 10.73.65.65 255.255.255.252 ip ospf network broadcast ip ospf priority 0 ip mtu 1400 router ospf 10 router-id 10.10.1.14 network 10.10.1.14 0.0.0.0 area0 network 10.73.65.64 0.0.0.3 area0 R86# interface Loopback0 ip address 10.10.1.86 255.255.255.255 interface FastEthernet0/0 ip address 10.73.65.66 255.255.255.252 ip ospf network broadcast ip mtu 1500 router ospf 10 router-id 10.10.1.86 network 10.10.1.86 0.0.0.0 area 0 network 10.73.65.64 0.0.0.3 area 0
B. R14# interface Loopback0 ip ospf 10 area 0 interface FastEthernet0/0 ip address 10.73.65.65 255.255.255.252 ip ospf network broadcast ip ospf 10 area 0 ip mtu 1500 router ospf 10 ip ospf priority 255 router-id 10.10.1 14 R86# interface Loopback0 ip ospf 10 area 0 interface FastEthernet0/0 ip address 10.73.65.66 255.255.255.252 ip ospf network broadcast ip ospf 10 area 0 ip mtu 1500 router ospf 10 router-id 10.10.1.86
C. R14# interface FastEthernet0/0 ip address 10.73.65.65 255.255.255.252 ip ospf network broadcast ip ospf priority 255 ip mtu 1500 router ospf 10 router-id 10.10.1.14 network 10.10.1.14 0.0.0.0 area0 network 10.73.65.64 0.0.0.3 area0 R86# interface FastEthernet0/0 ip address 10.73.65.66 255.255.255.252 ip ospf network broadcast ip mtu 1500 router ospf 10 router-id 10.10.1.86 network 10.10.1.86 0.0.0.0 area 0 network 10.73.65.64 0.0.0.3 area 0
D. R14# interface FastEthernet0/0 ip address 10.73.65.65 255.255.255.252 ip ospf network broadcast ip ospf priority 255 ip mtu 1500 router ospf 10 router-id 10.10.1.14 network 10.10.1.14 0.0.0.0 area0 network 10.73.65.64 0.0.0.3 area0 R86# interface FastEthernet0/0 ip address 10.73.65.66 255.255.255.252 ip ospf network broadcast ip mtu 1400 router ospf 10 router-id 10.10.1.86 network 10.10.1.86 0.0.0.0 area 0 network 10.73.65.64 0.0.0.3 area 0
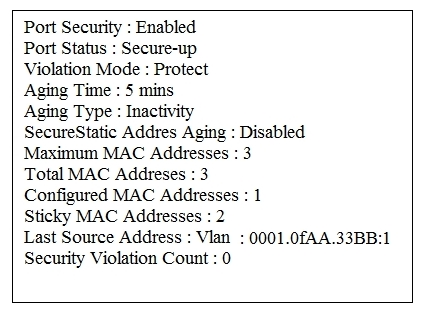
Refer to the exhibit. Which two statements about the interface that generated the output are true? (Choose two.)
A. learned MAC addresses are deleted after five minutes of inactivity
B. the interface is error-disabled if packets arrive from a new unknown source address
C. it has dynamically learned two secure MAC addresses
D. it has dynamically learned three secure MAC addresses
E. the security violation counter increments if packets arrive from a new unknown source address AC
Access Full CCNA Exam Prep Free
Want to go beyond these 50 questions? Click here to unlock a full set of CCNA exam prep free questions covering every domain tested on the exam.
We continuously update our content to ensure you have the most current and effective prep materials.
Good luck with your CCNA certification journey!