AZ-500 Exam Prep Free – 50 Practice Questions to Get You Ready for Exam Day
Getting ready for the AZ-500 certification? Our AZ-500 Exam Prep Free resource includes 50 exam-style questions designed to help you practice effectively and feel confident on test day
Effective AZ-500 exam prep free is the key to success. With our free practice questions, you can:
- Get familiar with exam format and question style
- Identify which topics you’ve mastered—and which need more review
- Boost your confidence and reduce exam anxiety
Below, you will find 50 realistic AZ-500 Exam Prep Free questions that cover key exam topics. These questions are designed to reflect the structure and challenge level of the actual exam, making them perfect for your study routine.
SIMULATION - You need to configure Azure to allow RDP connections from the Internet to a virtual machine named VM1. The solution must minimize the attack surface of VM1. To complete this task, sign in to the Azure portal.
You have an Azure subscription that contains a user named User1. You need to ensure that User1 can perform the following tasks: • Create groups. • Create access reviews for role-assignable groups. • Assign Azure AD roles to groups. The solution must use the principle of least privilege. Which role should you assign to User1?
A. Groups administrator
B. Authentication administrator
C. Identity Governance Administrator
D. Privileged role administrator
Your company has an Azure subscription named Sub1 that is associated to an Azure Active Directory (Azure AD) tenant named contoso.com. The company develops an application named App1. App1 is registered in Azure AD. You need to ensure that App1 can access secrets in Azure Key Vault on behalf of the application users. What should you configure?
A. an application permission without admin consent
B. a delegated permission without admin consent
C. a delegated permission that requires admin consent
D. an application permission that requires admin consent
You have an Azure subscription that contains an Azure key vault named Vault1. In Vault1, you create a secret named Secret1. An application developer registers an application in Azure Active Directory (Azure AD). You need to ensure that the application can use Secret1. What should you do?
A. In Azure AD, create a role.
B. In Azure Key Vault, create a key.
C. In Azure Key Vault, create an access policy.
D. In Azure AD, enable Azure AD Application Proxy.
SIMULATION - You need to ensure that when administrators deploy resources by using an Azure Resource Manager template, the deployment can access secrets in an Azure key vault named KV12345678. To complete this task, sign in to the Azure portal.
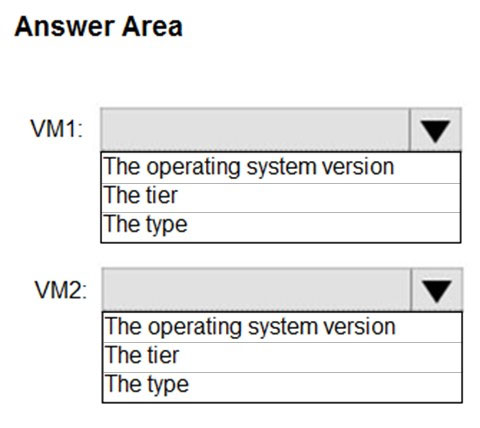
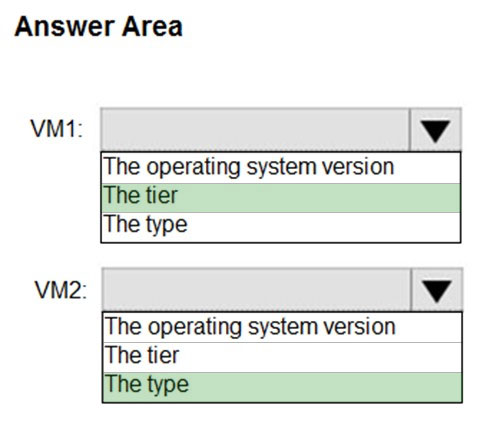
HOTSPOT - You have two Azure virtual machines in the East US 2 region as shown in the following table.You deploy and configure an Azure Key vault. You need to ensure that you can enable Azure Disk Encryption on VM1 and VM2. What should you modify on each virtual machine? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
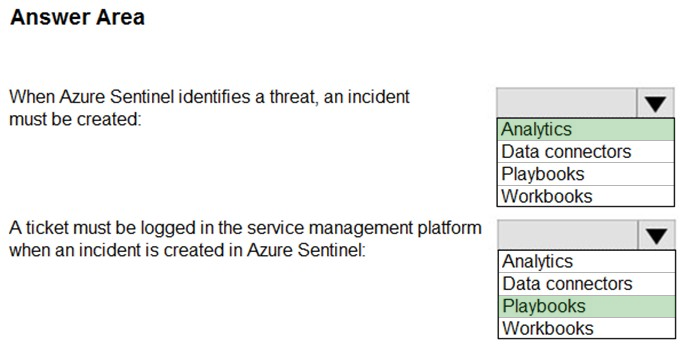
HOTSPOT - You have an Azure subscription that contains an Azure Sentinel workspace. Azure Sentinel is configured to ingest logs from several Azure workloads. A third-party service management platform is used to manage incidents. You need to identify which Azure Sentinel components to configure to meet the following requirements: ✑ When Azure Sentinel identifies a threat, an incident must be created. ✑ A ticket must be logged in the service management platform when an incident is created in Azure Sentinel. Which component should you identify for each requirement? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
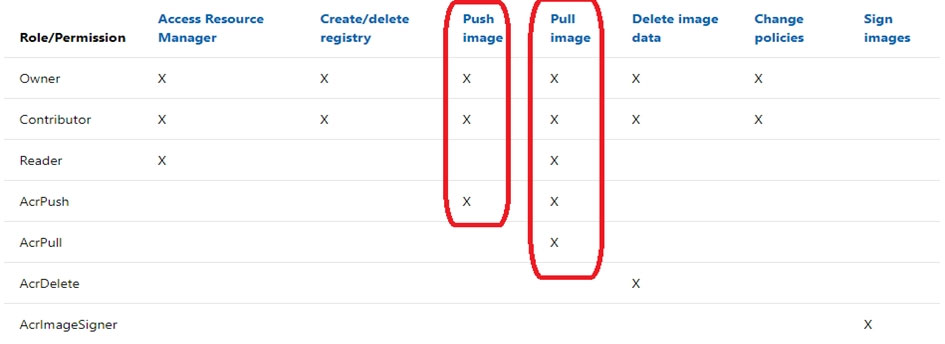
You have an Azure Kubernetes Service (AKS) cluster that will connect to an Azure Container Registry. You need to use the automatically generated service principal for the AKS cluster to authenticate to the Azure Container Registry. What should you create?
A. a secret in Azure Key Vault
B. a role assignment
C. an Azure Active Directory (Azure AD) user
D. an Azure Active Directory (Azure AD) group
Your company has an Azure subscription named Sub1 that is associated to an Azure Active Directory (Azure AD) tenant named contoso.com. The company develops a mobile application named App1. App1 uses the OAuth 2 implicit grant type to acquire Azure AD access tokens. You need to register App1 in Azure AD. What information should you obtain from the developer to register the application?
A. a redirect URI
B. a reply URL
C. a key
D. an application ID
HOTSPOT - You have an Azure subscription that contains a user named User1 and a storage account named storage1. The storage1 account contains the resources shown in the following table.In storage1, you create a shared access signature (SAS) named SAS1 as shown in the following exhibit.
To which resources can User1 write on July 1, 2022 by using SAS1 and key1? To answer select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
HOTSPOT - You have an Azure subscription named Subscription1 that contains the resources shown in the following table.You create an Azure role by using the following JSON file.
You assign Role1 to User1 for RG1. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
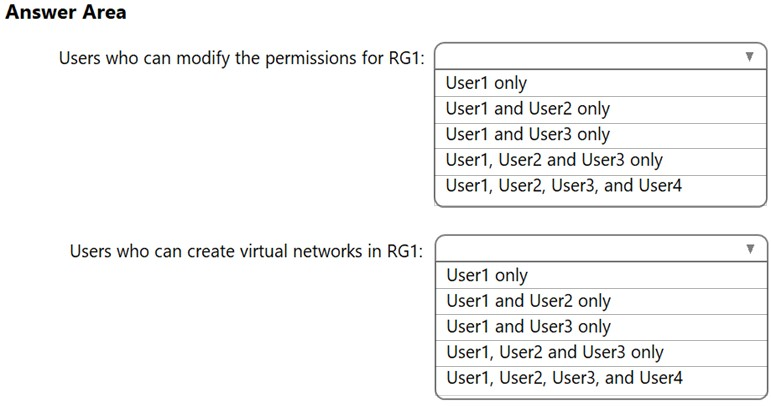
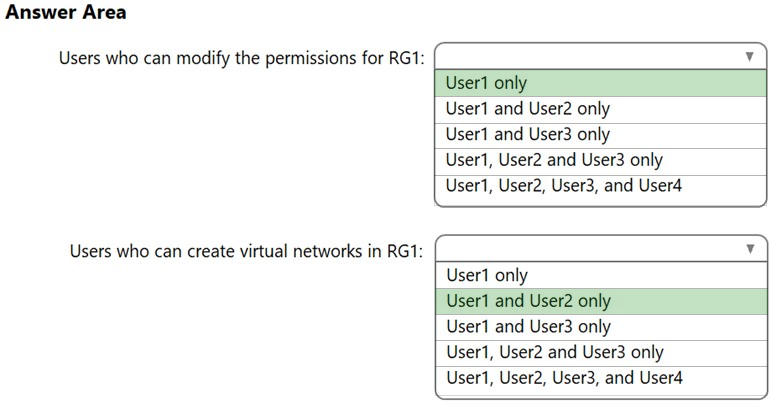
HOTSPOT - You have an Azure subscription that contains an Azure Active Directory (Azure AD) tenant named contoso.com. The tenant contains the users shown in the following table.You create a resource group named RG1. Which users can modify the permissions for RG1 and which users can create virtual networks in RG1? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You are troubleshooting a security issue for an Azure Storage account. You enable the diagnostic logs for the storage account. What should you use to retrieve the diagnostics logs?
A. Azure Security Center
B. Azure Monitor
C. the Security admin center
D. Azure Storage Explorer
You have an Azure subscription. You plan to create a workflow automation in Azure Security Center that will automatically remediate a security vulnerability. What should you create first?
A. an automation account
B. a managed identity
C. an Azure logic app
D. an Azure function app
E. an alert rule
HOTSPOT - You have an Azure subscription named Sub1 that contains two resource groups named RGnet and NET. You have the Azure Policy definition shown in the following exhibit.You assign the policy definition to Sub1 and NET. You plan to deploy the resources shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
You have an Azure AD tenant that contains a user named User1. You purchase an app named App1. User1 needs to publish App1 by using Azure AD Application Proxy. Which role should you assign to User1?
A. Cloud application administrator
B. Application administrator
C. Hybrid identity administrator
D. Cloud App Security Administrator
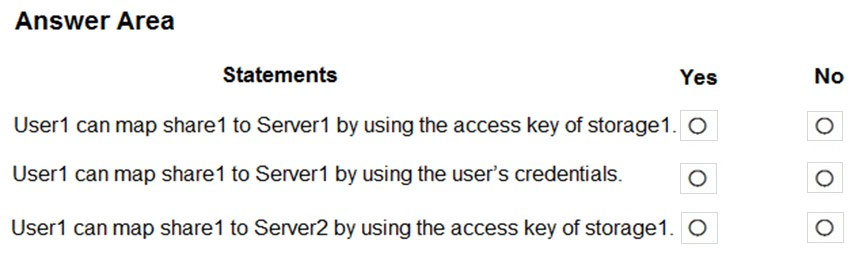
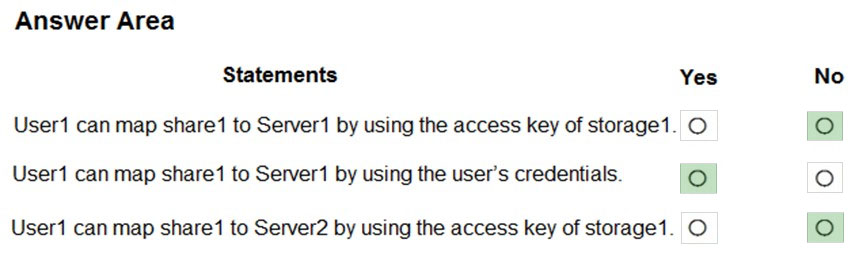
HOTSPOT - You have a hybrid Azure Active Directory (Azure AD) tenant named contoso.com that contains a user named User1 and the servers shown in the following table.The tenant is linked to an Azure subscription that contains a storage account named storage1. The storage1 account contains a file share named share1. User1 is assigned the Storage File Data SMB Share Contributor role for storage1. The Security protocol settings for the file shares of storage1 are configured as shown in the following exhibit.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
Your company's Azure subscription is linked to their Azure Active Directory (Azure AD) tenant. After an internally developed application is registered in Azure AD, you are tasked with making sure that the application has the ability to access Azure Key Vault secrets on application the users' behalf. Solution: You configure a delegated permission with no admin consent. Does the solution meet the goal?
A. Yes
B. No
You are testing an Azure Kubernetes Service (AKS) cluster. The cluster is configured as shown in the exhibit. (Click the Exhibit tab.)You plan to deploy the cluster to production. You disable HTTP application routing. You need to implement application routing that will provide reverse proxy and TLS termination for AKS services by using a single IP address. What should you do?
A. Create an AKS Ingress controller.
B. Install the container network interface (CNI) plug-in.
C. Create an Azure Standard Load Balancer.
D. Create an Azure Basic Load Balancer.
You have Azure Resource Manager templates that you use to deploy Azure virtual machines. You need to disable unused Windows features automatically as instances of the virtual machines are provisioned. What should you use?
A. device compliance policies in Microsoft Intune
B. Azure Automation State Configuration
C. application security groups
D. Azure Advisor
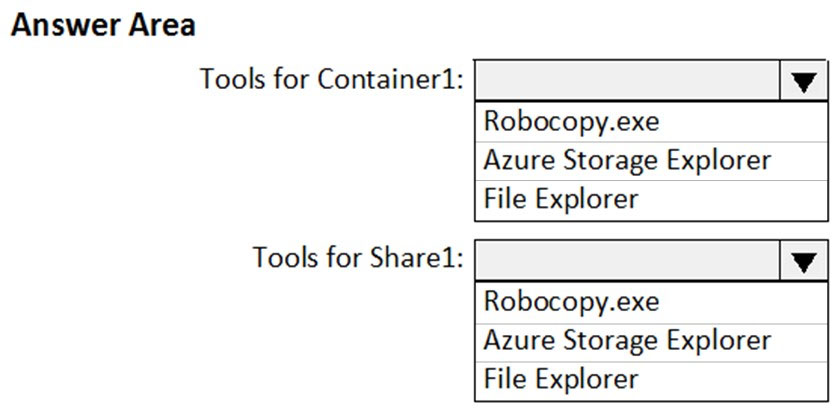
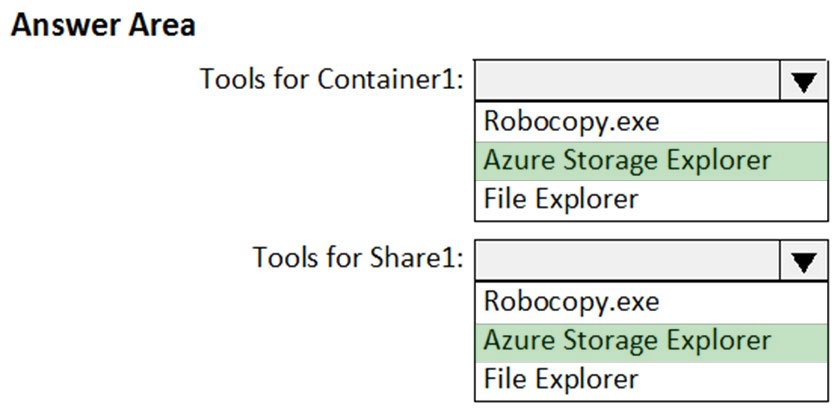
HOTSPOT - You have an Azure subscription named Sub1. Sub1 has an Azure Storage account named storage1 that contains the resources shown in the following table.You generate a shared access signature (SAS) to connect to the blob service and the file service. Which tool can you use to access the contents in Container1 and Share1 by using the SAS? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
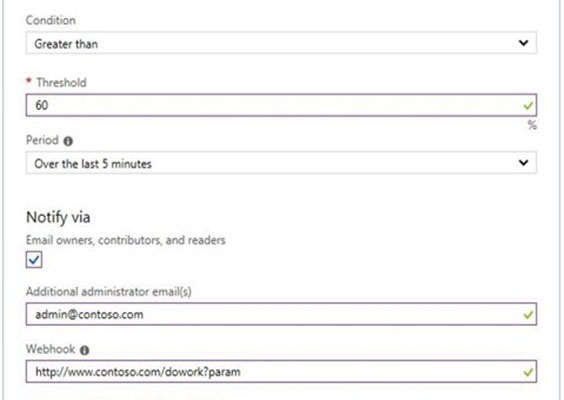
SIMULATION - You need to email an alert to a user named admin1@contoso.com if the average CPU usage of a virtual machine named VM1 is greater than 70 percent for a period of 15 minutes. To complete this task, sign in to the Azure portal.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution. After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You use Microsoft Defender for Cloud for the centralized policy management of three Azure subscriptions. You use several policy definitions to manage the security of the subscriptions. You need to deploy the policy definitions as a group to all three subscriptions. Solution: You create a policy definition and assignments that are scoped to resource groups. Does this meet the goal?
A. Yes
B. No
HOTSPOT - You have a Microsoft Sentinel deployment. You need to connect a third-party security solution to the deployment. The third-party solution will send Common Event Format (CEF)-formatted messages. What should you include in the solution? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution. After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You use Microsoft Defender for Cloud for the centralized policy management of three Azure subscriptions. You use several policy definitions to manage the security of the subscriptions. You need to deploy the policy definitions as a group to all three subscriptions. Solution: You create an initiative and an assignment that is scoped to a management group. Does this meet the goal?
A. Yes
B. No
You plan to deploy an app that will modify the properties of Azure Active Directory (Azure AD) users by using Microsoft Graph. You need to ensure that the app can access Azure AD. What should you configure first?
A. an app registration
B. an external identity
C. a custom role-based access control (RBAC) role
D. an Azure AD Application Proxy
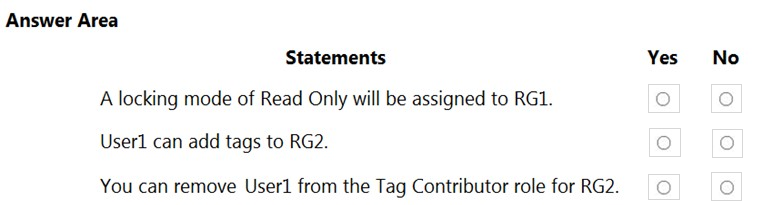
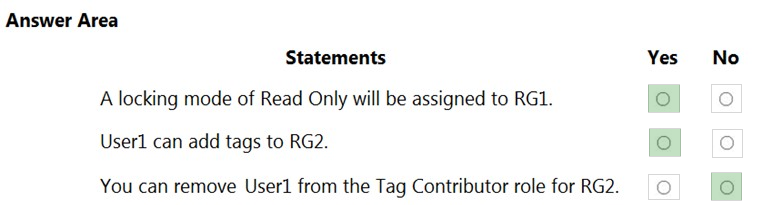
HOTSPOT - You have an Azure subscription named Subscription1 that contains a resource group named RG1 and a user named User1. User1 is assigned the Owner role for RG1. You create an Azure Blueprints definition named Blueprint1 that includes a resource group named RG2 as shown in the following exhibit.You assign Blueprint1 to Subscription1 by using the following settings: ✑ Lock assignment: Read Only ✑ Managed Identity: System assigned For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
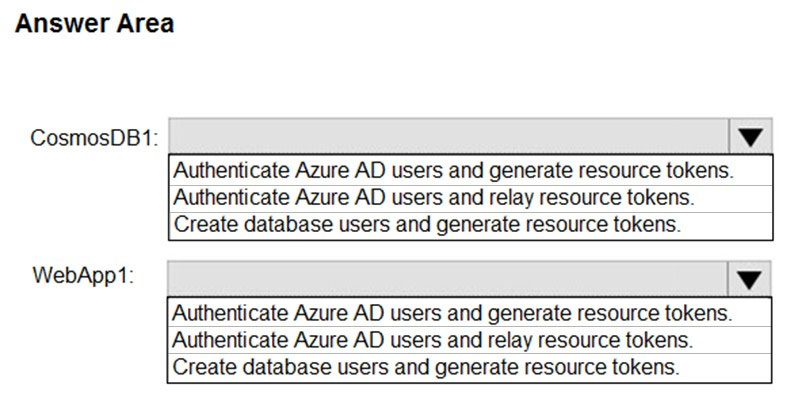
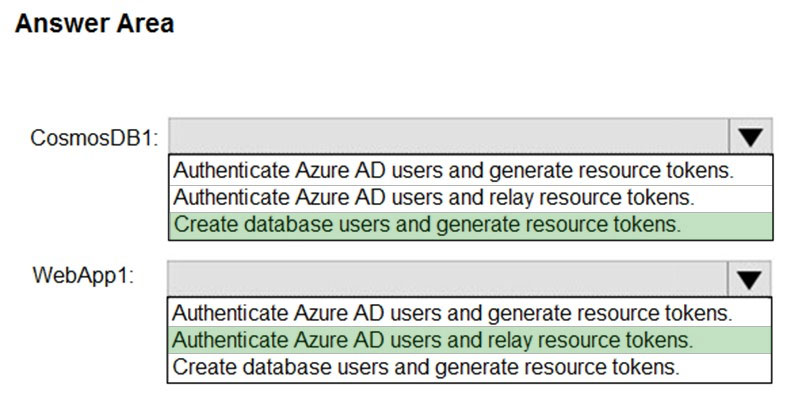
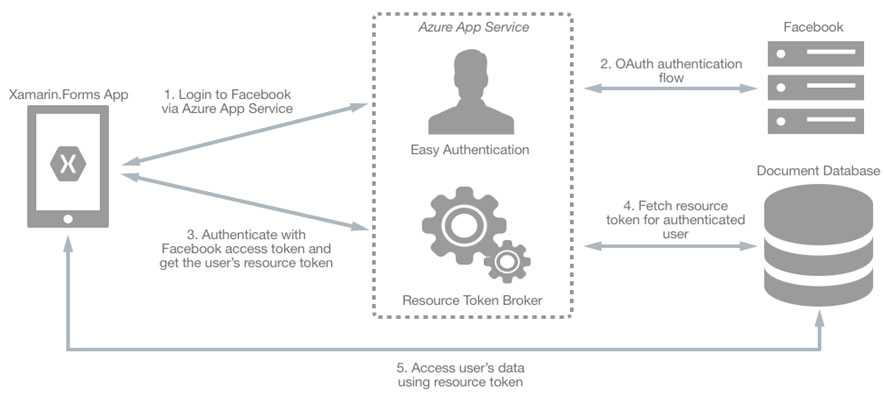
HOTSPOT - You have an Azure subscription named Sub1 that is associated to an Azure Active Directory (Azure AD) tenant named contoso.com. You plan to implement an application that will consist of the resources shown in the following table.Users will authenticate by using their Azure AD user account and access the Cosmos DB account by using resource tokens. You need to identify which tasks will be implemented in CosmosDB1 and WebApp1. Which task should you identify for each resource? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
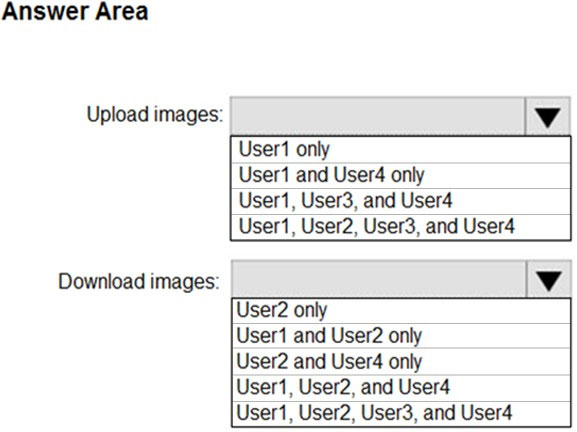
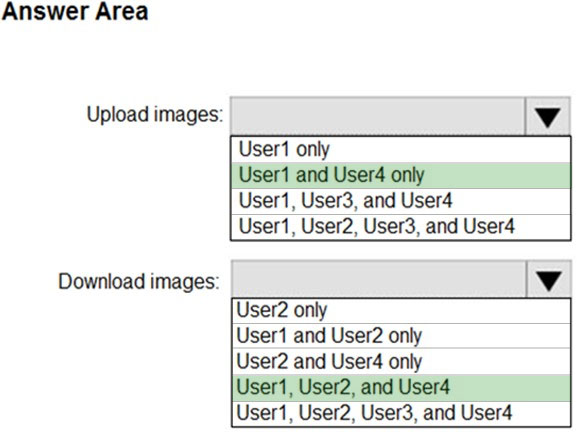
HOTSPOT - You have an Azure Container Registry named Registry1. You add role assignments for Registry1 as shown in the following table.Which users can upload images to Registry1 and download images from Registry1? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
SIMULATION - You need to configure network connectivity between a virtual network named VNET1 and a virtual network named VNET2. The solution must ensure that virtual machines connected to VNET1 can communicate with virtual machines connected to VNET2. To complete this task, sign in to the Azure portal and modify the Azure resources.
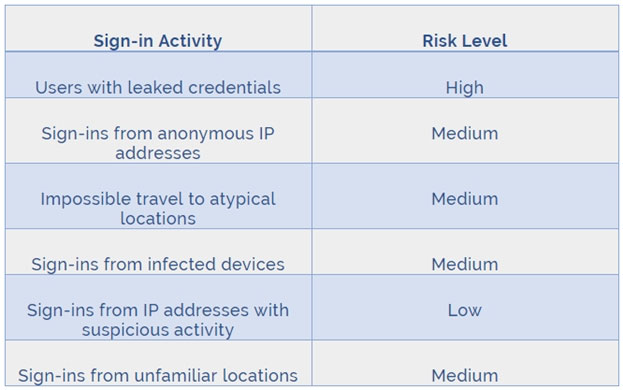
DRAG DROP - You are implementing conditional access policies. You must evaluate the existing Azure Active Directory (Azure AD) risk events and risk levels to configure and implement the policies. You need to identify the risk level of the following risk events: ✑ Users with leaked credentials ✑ Impossible travel to atypical locations ✑ Sign-ins from IP addresses with suspicious activity Which level should you identify for each risk event? To answer, drag the appropriate levels to the correct risk events. Each level may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point. Select and Place:
Your company makes use of Azure Active Directory (Azure AD) in a hybrid configuration. All users are making use of hybrid Azure AD joined Windows 10 computers. You manage an Azure SQL database that allows for Azure AD authentication. You need to make sure that database developers are able to connect to the SQL database via Microsoft SQL Server Management Studio (SSMS). You also need to make sure the developers use their on-premises Active Directory account for authentication. Your strategy should allow for authentication prompts to be kept to a minimum. Which of the following is the authentication method the developers should use?
A. Azure AD token.
B. Azure Multi-Factor authentication.
C. Active Directory integrated authentication.
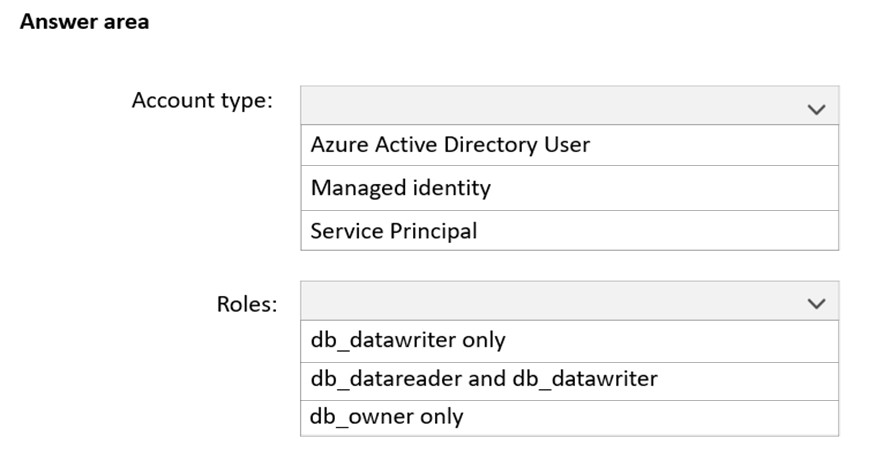
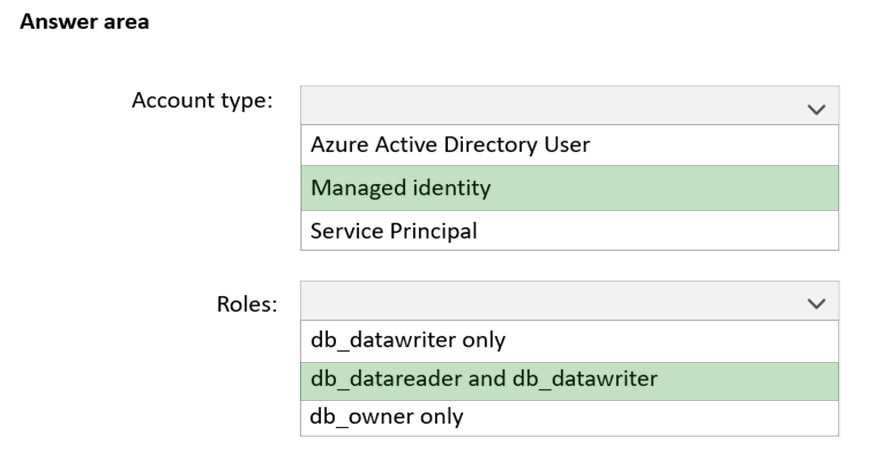
HOTSPOT - You have an Azure subscription that contains an Azure SQL database named SQL1. You plan to deploy a web app named App1. You need to provide App1 with read and write access to SQL1. The solution must meet the following requirements: ✑ Provide App1 with access to SQL1 without storing a password. ✑ Use the principle of least privilege. ✑ Minimize administrative effort. Which type of account should App1 use to access SQL1, and which database roles should you assign to App1? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft Entra tenant named Contoso.com and an Azure Kubernetes Service (AKS) cluster AKS1. You discover that AKS1 cannot be accessed by using accounts from Contoso.com. You need to ensure AKS1 can be accessed by using accounts from Contoso.com. The solution must minimize administrative effort. What should you do first?
A. From Azure, recreate AKS1.
B. From AKS1, upgrade the version of Kubernetes.
C. From Microsoft Entra, add a Microsoft Entra ID P2 license.
D. From Microsoft Entra, configure the User settings.
Your on-premises network contains a Hyper-V virtual machine named VM1. You need to use Azure Arc to onboard VM1 to Microsoft Defender for Cloud. What should you install first?
A. the guest configuration agent
B. the Azure Monitor agent
C. the Log Analytics agent
D. the Azure Connected Machine agent
You have an Azure subscription that uses Microsoft Defender for Cloud. You need to use Defender for Cloud to review regulatory compliance with the Azure CIS 1.4.0 standard. The solution must minimize administrative effort. What should you do first?
A. Assign an Azure policy.
B. Disable one of the Out of the box standards.
C. Manually add the Azure CIS 1.4.0 standard.
D. Add a custom initiative.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution. After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have an Azure subscription. The subscription contains 50 virtual machines that run Windows Server 2012 R2 or Windows Server 2016. You need to deploy Microsoft Antimalware to the virtual machines. Solution: You connect to each virtual machine and add a Windows feature. Does this meet the goal?
A. Yes
B. No
Your company has an Azure subscription named Sub1. You plan to create several security alerts by using Azure Monitor. You need to prepare Sub1 for the alerts. What should you create first?
A. an Azure Automation account
B. an Azure event hub
C. an Azure Log Analytics workspace
D. an Azure Storage account
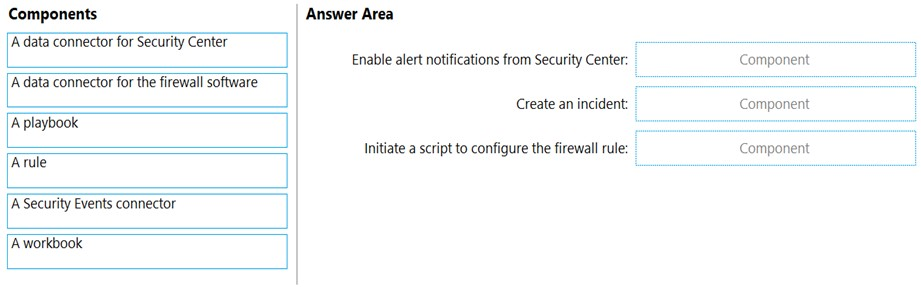
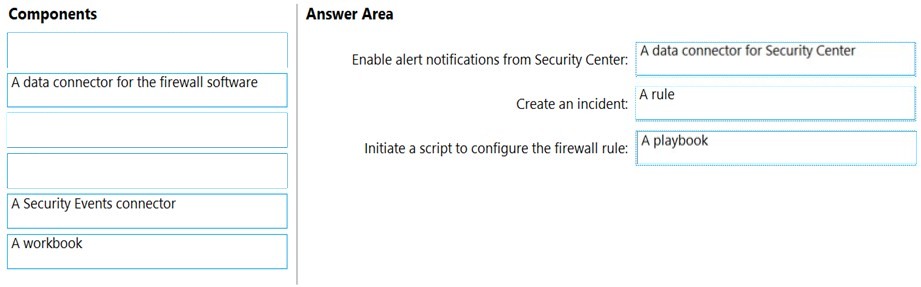
DRAG DROP - You have an Azure subscription that contains the following resources: ✑ A network virtual appliance (NVA) that runs non-Microsoft firewall software and routes all outbound traffic from the virtual machines to the internet ✑ An Azure function that contains a script to manage the firewall rules of the NVA ✑ Azure Security Center standard tier enabled for all virtual machines ✑ An Azure Sentinel workspace ✑ 30 virtual machines You need to ensure that when a high-priority alert is generated in Security Center for a virtual machine, an incident is created in Azure Sentinel and then a script is initiated to configure a firewall rule for the NVA. How should you configure Azure Sentinel to meet the requirements? To answer, drag the appropriate components to the correct requirements. Each component may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point. Select and Place:
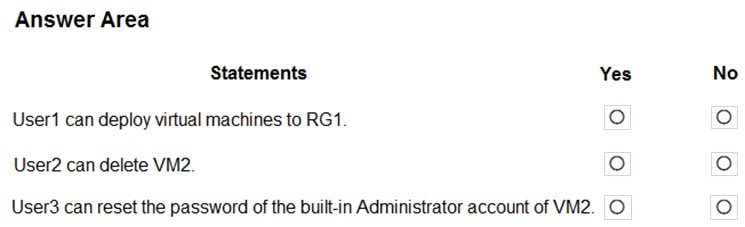
HOTSPOT - You have the hierarchy of Azure resources shown in the following exhibit.RG1, RG2, and RG3 are resource groups. RG2 contains a virtual machine named VM2. You assign role-based access control (RBAC) roles to the users shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
Your company's Azure subscription includes a hundred virtual machines that have Azure Diagnostics enabled. You have been tasked with retrieving the identity of the user that removed a virtual machine fifteen days ago. You have already accessed Azure Monitor. Which of the following options should you use?
A. Application Log
B. Metrics
C. Activity Log
D. Logs
HOTSPOT - You have an Azure subscription that contains a web app named App1 and an Azure key vault named Vault1. You need to configure App1 to store and access the secrets in Vault1. How should you configure App1? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You need to ensure that you can meet the security operations requirements. What should you do first?
A. Turn on Auto Provisioning in Security Center.
B. Integrate Security Center and Microsoft Cloud App Security.
C. Upgrade the pricing tier of Security Center to Standard.
D. Modify the Security Center workspace configuration.
You create a new Azure subscription. You need to ensure that you can create custom alert rules in Azure Security Center. Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Onboard Azure Active Directory (Azure AD) Identity Protection.
B. Create an Azure Storage account.
C. Implement Azure Advisor recommendations.
D. Create an Azure Log Analytics workspace.
E. Upgrade the pricing tier of Security Center to Standard.
SIMULATION - You need to ensure that only devices connected to a 131.107.0.0/16 subnet can access data in the rg1lod1234578 Azure Storage account. To complete this task, sign in to the Azure portal.
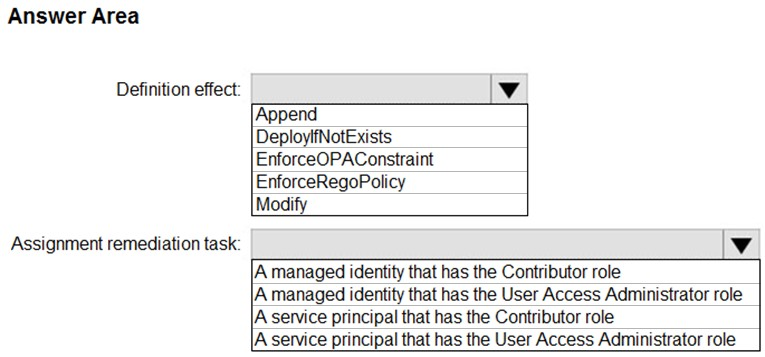
HOTSPOT - You have an Azure subscription. You need to create and deploy an Azure policy that meets the following requirements: ✑ When a new virtual machine is deployed, automatically install a custom security extension. ✑ Trigger an autogenerated remediation task for non-compliant virtual machines to install the extension. What should you include in the policy? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
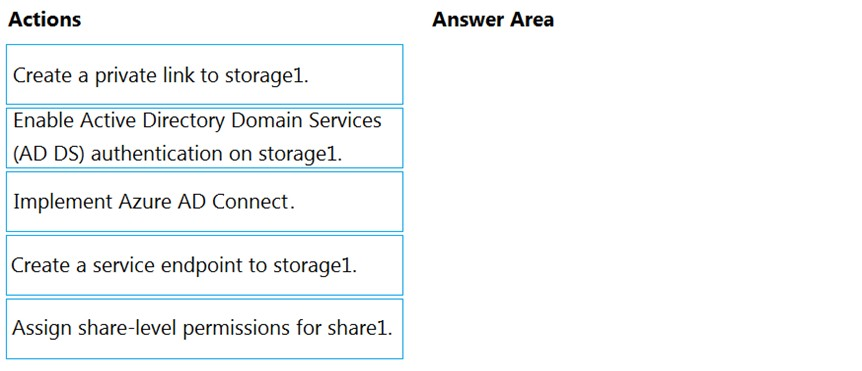
DRAG DROP - Your network contains an on-premises Active Directory domain named contoso.com. The domain contains a user named User1. You have an Azure subscription that is linked to an Azure Active Directory (Azure AD) tenant named contoso.com. The tenant contains an Azure Storage account named storage1. Storage1 contains an Azure file share named share1. Currently, the domain and the tenant are not integrated. You need to ensure that User1 can access share1 by using his domain credentials. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. Select and Place:
You have an Azure Sentinel workspace. You need to create a playbook. Which two triggers will start the playbook? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. An Azure Sentinel scheduled query rule is executed.
B. An Azure Sentinel data connector is added.
C. An Azure Sentinel alert is generated.
D. An Azure Sentinel hunting query result is returned.
E. An Azure Sentinel incident is created.
SIMULATION - You need to ensure that the rg1lod28681041n1 Azure Storage account is encrypted by using a key stored in the KeyVault28681041 Azure key vault. To complete this task, sign in to the Azure portal.
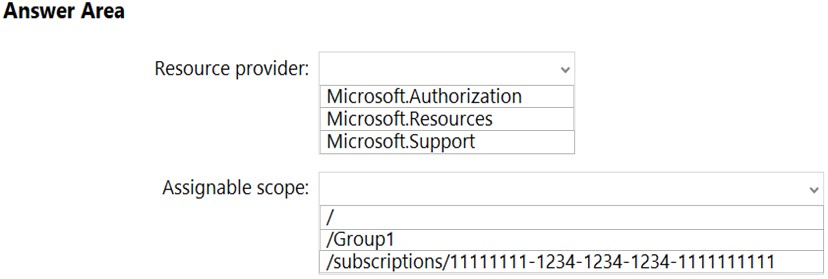
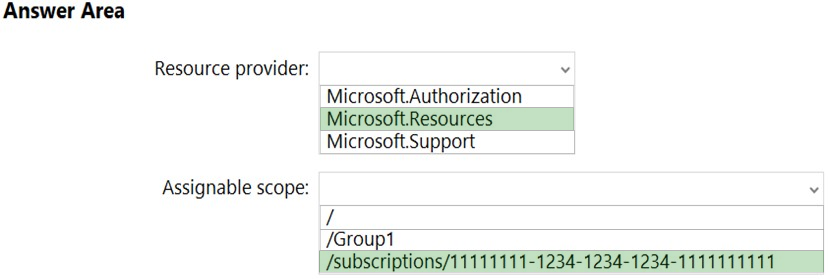
HOTSPOT - You have a management group named Group1 that contains an Azure subscription named sub1. Sub1 has a subscription ID of 11111111-1234-1234-1234- 1111111111. You need to create a custom Azure role-based access control (RBAC) role that will delegate permissions to manage the tags on all the objects in Group1. What should you include in the role definition of Role1? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
Access Full AZ-500 Exam Prep Free
Want to go beyond these 50 questions? Click here to unlock a full set of AZ-500 exam prep free questions covering every domain tested on the exam.
We continuously update our content to ensure you have the most current and effective prep materials.
Good luck with your AZ-500 certification journey!