350-901 Exam Prep Free – 50 Practice Questions to Get You Ready for Exam Day
Getting ready for the 350-901 certification? Our 350-901 Exam Prep Free resource includes 50 exam-style questions designed to help you practice effectively and feel confident on test day
Effective 350-901 exam prep free is the key to success. With our free practice questions, you can:
- Get familiar with exam format and question style
- Identify which topics you’ve mastered—and which need more review
- Boost your confidence and reduce exam anxiety
Below, you will find 50 realistic 350-901 Exam Prep Free questions that cover key exam topics. These questions are designed to reflect the structure and challenge level of the actual exam, making them perfect for your study routine.
An application is hosted on Google Kubernetes Engine. A new JavaScript module is created to work with the existing application. Which task is mandatory to make the code ready to deploy?
A. Create a Dockerfile for the code base.
B. Rewrite the code in Python.
C. Build a wrapper for the code to ג€containerizeג€ it.
D. Rebase the code from the upstream git repo.
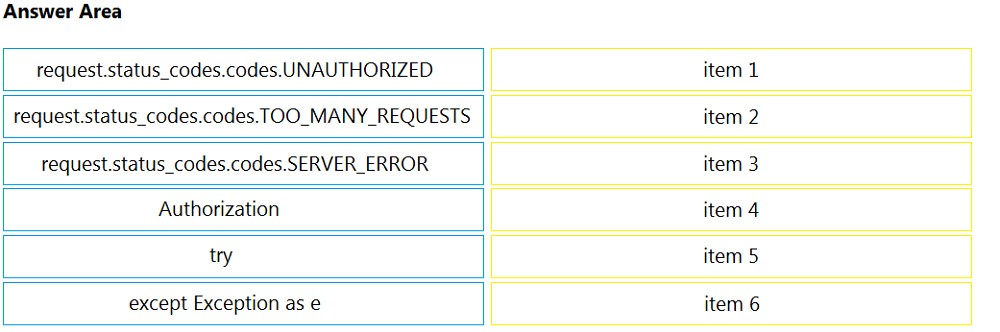
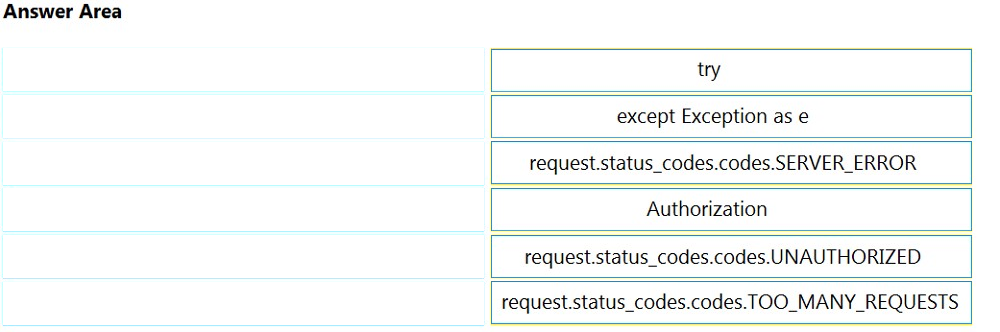
DRAG DROP - Drag and drop the components from the left into the order on the right to create the flow of the three-legged OAuth2.
What are two benefits of using a centralized logging service? (Choose two.)
A. reduces the time required to query log data across multiple hosts
B. reduces the loss of logs after a single disk failure
C. improves application performance by reducing CPU usage
D. improves application performance by reducing memory usage
E. provides compression and layout of log data
DRAG DROP - Drag and drop the code from the bottom onto the box where the code is missing to retrieve location data for network devices. Not all options are used.

Refer to the exhibits which show the documentation associated with the create port object API call in Cisco Firepower Threat Defense, and a cURL command. Which data payload completes the cURL command to run the API call?
A. “icmpv4Type”: “ANY”, “name”: “string”, “type”: “icmpv4portobject”
B. “description”: “This is an ICMP Echo”, “icmpv4Code”: “8”, “icmpv4Type”: “Echo”, “isSystemDefined”: true, “name”: “ICMP Echo”, “version”: “2.2”
C. “description”: “string”, “icmpv4Code”: “ANY_IPV4”, “icmpv4Type”: “ANY”, “id”: “string”, “isSystemDefined”: “string”, “name”: “string”, “type”: “icmpv4portobject”, “version”: “string”
D. “description”: “string”, “icmpv4Code”: “ANY_IPV4”, “icmpv4Type”: null, “isSystemDefined”: true, “name”: “string”, “type”: “icmpv4portobject”
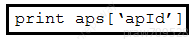
Refer to the exhibit. A Python developer is creating a wireless network device inventory application for local deployment of Cisco access points. The developer is retrieving an access point ID by using a REST API. The output indicates that there was a KeyError when parsing the JSON response. What returns the expected output of 266 at line 14? A.
B.
C.
D.
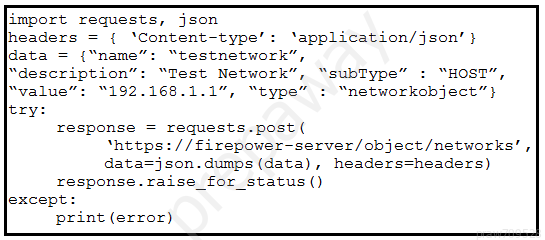
Refer to the exhibit. A developer must create a new network object named testnetwork by using the Cisco Firepower Device Management API. The script must also handle any exceptions that occur during the request and print out any resulting errors. Which script must be used? A.
B.
C.
D.
A developer must deploy a containerized application for network device inventory management. The developer sets up a Kubernetes cluster on two separate hypervisors. The SLA is not currently meeting a specified maximum value for network latency/jitter. CPU/memory and disk I/O are functioning properly. Which two design approaches resolve the issue? (Choose two.)
A. Enable IPv6 within the cluster.
B. Upgrade the server NIC card.
C. Deploy the cluster to a bare metal server.
D. Replace the HDD drives with SSD drives.
E. Collocate services in the same pod.
Refer to the exhibit. The application follows a containerized microservices architecture that has one container per microservice. The microservices communicate with each other by using REST APIs. The double-headed arrows in the diagram display chains of synchronous HTTP calls needed for a single user request. Which action ensures the resilience of the application in the scope of a single user request?
A. Implement retries with exponential backoff during HTTP API calls.
B. Set up multiple instances of each microservice in active/active mode by using the Orchestrator.
C. Redesign the application to be separated into these three layers: Presentation, API, and Data.
D. Create two virtual machines that each host an instance of the application and set up a cluster.

Refer to the exhibits. An engineer writes a script to retrieve data from a REST API and must build support for cases where the response that contains data from the server may take a longer time than normal. Which code must be added to the snippet where the code is missing to catch such a timeout?
A. requests.exceptions.HTTPError
B. requests.exceptions.DataTimeout
C. requests.exceptions.ConnectTimeout
D. requests.exceptions.ReadTimeout
DRAG DROP - Drag and drop the code from the bottom onto the box where the code is missing to construct a Puppet manifest to configure DNS. Not all options are used.
A web application is being developed to provide online sales to a retailer. The customers will need to use their username and passwords to login into their profile and complete their order. For this reason, the application must store user passwords. Which approach ensures that an attacker will need to crack the passwords one at a time?
A. Store the passwords by using asymmetric encryption.
B. Apply the salting technique.
C. Store the passwords by using symmetric encryption.
D. Apply the peppering technique.
A developer is designing a modern, distributed microservice enterprise application. The application will be integrating with other systems and focus on a large deployment, so control of API calls is necessary. What is the best practice to reduce application response latency and protect the application from excessive use?
A. Implement rate limiting on the client side.
B. Do not enforce any rate limiting.
C. Implement rate limiting on the client and server sides.
D. Implement rate limiting on the server side.
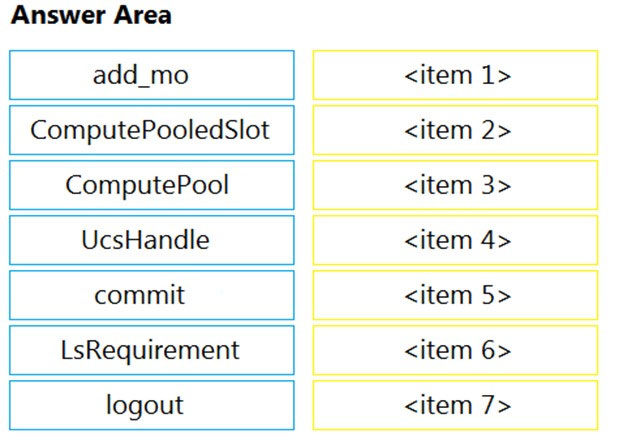
DRAG DROP -Refer to the exhibit above and click on the resource tabs in the top left corner to view resources to help with this question. Python code using the UCS Python SDK is creating a server pool named "devcore_pool" and populating the pool with all servers from chassis 7, and then the server pool is associated to existing Service Profile template "devcore_template". Drag and drop the code from the left onto the item numbers on the right that match the missing sections in the Python exhibit. Select and Place:
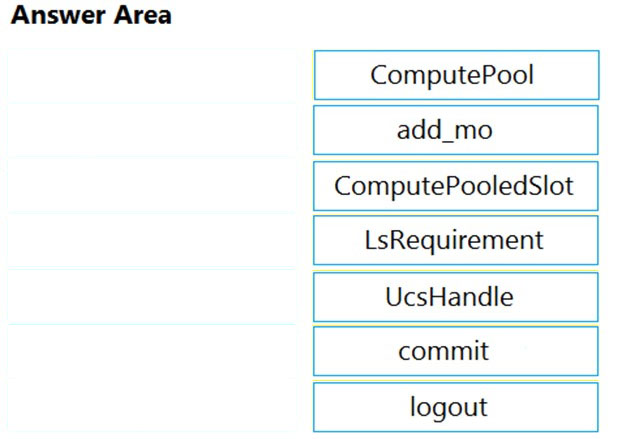
DRAG DROP -Refer to the exhibit. Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to complete the script to implement control flow. Select and Place:
How do end-to-end encryption principles apply to APIs?
A. The owners of the service are prevented from accessing data that is being transferred.
B. Sensitive information is protected against backdoor attacks.
C. The API data is protected against man-in-the-middle attacks.
D. Both endpoints that are using the API resources are hardened against hacking.
A cloud native project is being worked on in which all source code and dependencies are written in Python, Ruby, and/or JavaScnpt. A change in code triggers a notification to the CI/CD tool to run the CI/CD pipeline. Which step should be omitted from the pipeline?
A. Deploy the code to one or more environments, such as staging and/or production.
B. Build one of more containers that package up code and all its dependencies.
C. Compile code.
D. Run automated tests to validate the code.
Which database type should be used with highly structured data and provides support for ACID transactions?
A. time series
B. document
C. graph
D. relational
How is an OAuth2 three-legged authentication flow initiated?
A. Construct an API call to retrieve the credentials.
B. The user makes a request to the OAuth client.
C. Get the authorization code.
D. Exchange the key for an access token.
DRAG DROP - Drag and drop the code from the bottom onto the box where the code is missing to list objects that use the paginated Cisco FDM API. Some options may be used more than once. Not all options are used.
DRAG DROP - Drag and drop the code from the bottom onto the box where the code is missing in the Ansible script to get the existing firewall rules from Cisco Meraki and store the results to a new variable. Not all options are used.
Refer to the exhibit. The virtual next-generation firewalls running in the public cloud must be scaled out to meet the throughput requirements of the application layer. Which component is deployed to location A in the diagram?
A. internal load balancer
B. frontend caching server
C. forward proxy
D. backend database
DRAG DROP - Drag and drop the steps from the left into the order on the right to build and run a customized Python Docker image. Not all options are used.
A developer deployed a web application in a local data center that is experiencing high traffic load from users that access data through REST API calls. Caching helps to enhance the responsiveness and performance of the API usage. Which approach must be used to improve cache performance?
A. Ensure that all read requests are clearly identified by the PUT method.
B. Implement surrogate key tagging to purge requests.
C. Use HTTP POST or other non-read methods for read requests when it is possible.
D. Configure the API payload to return errors in HTTP 200 responses.
125 DRAG DROP Drag and drop the code snippets from the bottom onto the blanks in the code to retrieve location data for floor plans. Not all options are used.
Refer to the exhibit. What is the output of this IOS-XE configuration program?
A. interface operational status in IPv6 addresses
B. interface administrative status in IPv4 addresses
C. interface operational status in IPv4 addresses
D. interface administrative status in IPv6 addresses
A timeframe custom dashboard must be developed to present data collected from Cisco Meraki. The dashboard must include a wireless health alert count. What needs to be built as a prerequisite?
A. A publicly available HTTP server to receive Meraki Webhooks from the Meraki Scanning API.
B. A publicly available HTTP server to receive Meraki Webhooks from the Meraki Dashboard API.
C. A daemon to consume the Wireless Health endpoint of the Meraki Dashboard API.
D. A daemon to consume the Wireless Health endpoint of the Meraki Scanning API.
FILL BLANK - A local Docker image has an image ID of 385001111. Fill in the blanks to complete the command in order to tag the image into the "cisco" repository with "version1.0"
A web application has these requirements for HTTP cache control: • The client browser must be prevented from storing responses that contain sensitive information. • Assets must be downloaded from the remote server every time. Which header must the engineer use?
A. no-store
B. must-revalidate
C. public
D. private
Which data encoding format uses gRPC by default for serializing structured sets of information?
A. XML
B. JSON
C. YAML
D. Protobuf
Which two data encoding techniques are supported by gRPC? (Choose two.)
A. XML
B. JSON
C. ASCII
D. ProtoBuf
E. YAML
Which database type should be used to store data received from model-driven telemetry?
A. BigQuery database
B. Time series database
C. NoSQL database
D. PostgreSQL database
DRAG DROP - Drag and drop the code from the bottom onto the box where the code is missing to configure a router that runs Cisco IOS XE by using RESTCONF. The API call is made to the management URL of the IOS XE device and on a registered port number. Errors that are caught during HTTP operation are registered. Not all options are used.
Refer to the exhibit. Which set of API requests must be executed by a Webex bot after receiving a webhook callback to process messages in a room and reply with a new message back to the same room? A.
B.
C.
D.
A new monitoring solution has these requirements: • Collect real-time telemetry. • Pull SNMP data from all network devices. • Visualize data in graphs. Which type of database should be used to store the data?
A. graph database
B. relational database
C. time-series database
D. document database
Which process decouples PII from a set of data and provides anonymity, but allows identification of the person to whom the data belongs under strictly controlled cases?
A. data anonymization
B. data de-identification
C. data split
D. data encryption
Refer to the exhibit. A developer must review an intern's code for a script they wrote to automate backups to the storage server. The script must connect to the network device and copy the running-config to the server. When considering maintainability, which two changes must be made to the code? (Choose two.)
A. Refactor the code placing the “for” loop steps inside a single nc method.
B. The intern must use IP addresses because DNS is unreliable.
C. The command sent to the network device is incorrect.
D. The code is incorrect because the class does not have an __init__() method.
E. Rename the class to “ArchiveManaqer”.
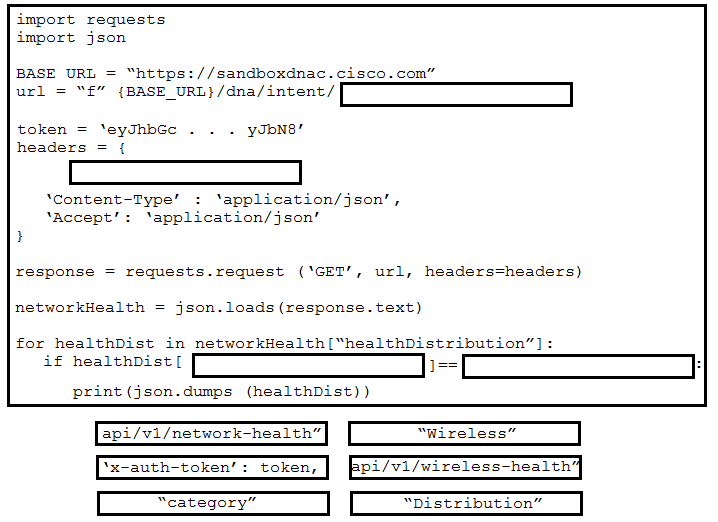
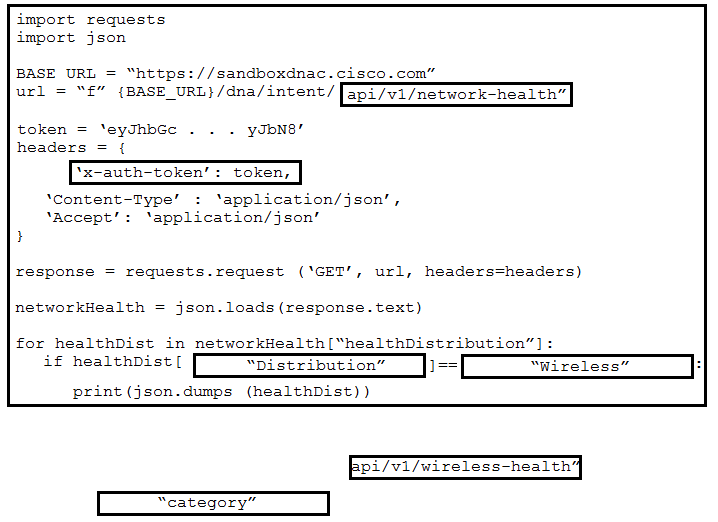
DRAG DROP - Drag and drop the code from the bottom onto the box where the code is missing to retrieve and display wireless network health information. The wireless network devices are being managed by Cisco DNA Center and are compatible with REST API. Not all options are used. Select and Place:
An enterprise refactors its monolithic application into a modern cloud-native application that is based on microservices. A key requirement of the application design is to ensure that the IT team is aware of performance issues or bottlenecks in the new application. Which two approaches must be part of the design considerations? (Choose two.)
A. Adopt a service-oriented architecture to handle communication between the services that make up the application.
B. Implement infrastructure monitoring to ensure that pipeline components interoperate smoothly and reliably.
C. Instrument the application code to gather telemetry data from logs, metrics, or tracing.
D. Periodically scale up the resources of the host machines when the application starts to experience high loads.
E. Deploy infrastructure monitoring agents into the operating system of the host machines.
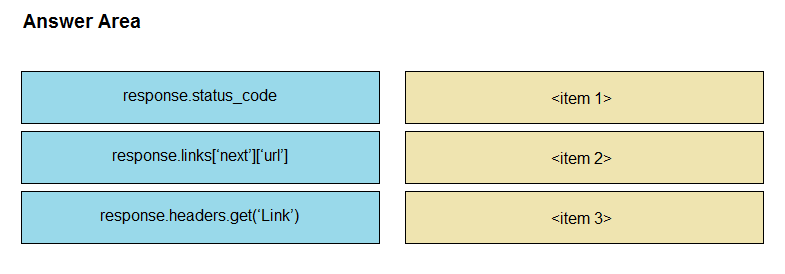
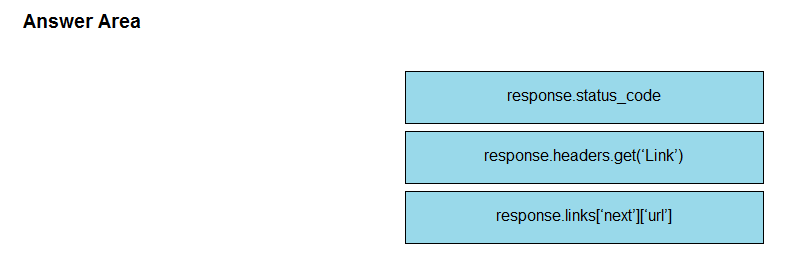
DRAG DROP -Refer to the exhibit. Drag and drop the parts of the Python code from the left onto the item numbers on the right that match the missing sections in the exhibit that consumes REST API pagination. Select and Place:
Refer to the exhibit. Information was obtained by using RESTCONF and querying URI /restconf/data/ietf-interfaces:interfaces. Which RESTCONF call and which JSON code enables GigabitEthernet2? (Choose two.) A.
B.
C.
D.
E.
F.
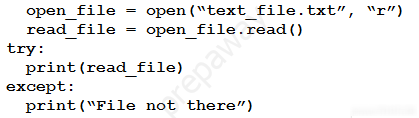
Refer to the exhibit. A developer created the code, but it fails to execute. Which code snippet helps to identify the issue? A.
B.
C.
D.
DRAG DROP - Drag and drop the code from the bottom onto the box where the code is missing to configure a Python script that uses RESTCOMF to add an IP address and subnet mask to an interface. Not all options are used.
What is a benefit of continuous testing?
A. increases the number of bugs found in production
B. enables parallel testing
C. removes the requirement for test environments
D. decreases the frequency of code check-ins
Refer to the exhibit. The command docker build --tag=friendlyhello . is run to build a docker image from the given Dockerfile, reguirements.txt, and app.py. Then the command docker run -p 4000:80 friendlyhello is executed to run the application. Which URL is entered in the web browser to see the content served by the application?
A. http://127.0.0.1:80
B. http://4000:80
C. http://localhost:4000
D. http://localhost:80
DRAG DROP - A developer must package an application for Kubernetes to integrate into a prebuilt CD environment. The application utilizes a Docker image from Cisco DevNet public repository and is accessible from a specific port of the container. Drag and drop the code from the bottom onto the box where the code is missing in the Kubernetes YAML configuration file. Not all options are used.
Refer to the exhibit. A Docker swarm cluster is configured to load balance services across data centers in three different geographical regions: west, central, and east. The cluster has three manager nodes and three worker nodes. A new service named cisco_devnet is being deployed. The service has these design requirements: ✑ All containers must be hosted only on nodes in the central region. ✑ The service must run only on nodes that are ineligible for the manager role. Which approach fulfills the requirements?
A. Use placement constraints to control nodes to which the service can be assigned.
B. Create the service manually in the central region and set replicas to 0.
C. Enable the control flag in the containers of the west and east regions to prevent the service from starting.
D. Create a second swarm cluster that is hosted only in the central region.
Refer to the exhibit. Many faults have occurred in the ACI environment and a sample of them needs to be examined. Which API call retrieves faults 31 through 45?
A. GET https://apic-ip-address/api/class/faultInfo.json?order-by=faultInst.severity|desc&page=1&page-size=15
B. GET https://apic-ip-address/api/class/faultInfo.json?order-by=faultInst.severity|desc&page=2&page-size=15
C. GET https://apic-ip-address/api/class/faultInfo.json?order-by=faultInst.severity|desc&page-size=30
D. GET https://apic-ip-address/api/class/faultInfo.json?order-by=faultInst.severity|desc&page=2&page-size=30
DRAG DROP - A Python application is being written to run inside a Cisco IOS XE device to assist with gathering telemetry data. Drag and drop the elements of the stack from the left onto the functions on the right to collect and display the telemetry streaming data. Select and Place:
What is the result of a successful OAuth2 authorization grant flow?
A. The third-party service is provided with a token that allows actions to be performed.
B. The user has the application rights that correspond to the user’s role within the application’s database.
C. The application is provided with a token that allows actions on services on the user’s behalf.
D. The user has administrative rights to the application’s backend services.
Access Full 350-901 Exam Prep Free
Want to go beyond these 50 questions? Click here to unlock a full set of 350-901 exam prep free questions covering every domain tested on the exam.
We continuously update our content to ensure you have the most current and effective prep materials.
Good luck with your 350-901 certification journey!