312-50V9 Exam Prep Free – 50 Practice Questions to Get You Ready for Exam Day
Getting ready for the 312-50V9 certification? Our 312-50V9 Exam Prep Free resource includes 50 exam-style questions designed to help you practice effectively and feel confident on test day
Effective 312-50V9 exam prep free is the key to success. With our free practice questions, you can:
- Get familiar with exam format and question style
- Identify which topics you’ve mastered—and which need more review
- Boost your confidence and reduce exam anxiety
Below, you will find 50 realistic 312-50V9 Exam Prep Free questions that cover key exam topics. These questions are designed to reflect the structure and challenge level of the actual exam, making them perfect for your study routine.
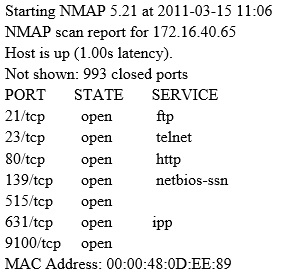
Which of the following parameters describe LM Hash (see exhibit): Exhibit:
A. I, II, and III
B. I
C. II
D. I and II
What is the main difference between a "Normal" SQL Injection and a "Blind" SQL Injection vulnerability?
A. The request to the web server is not visible to the administrator of the vulnerable application.
B. The attack is called “Blind” because, although the application properly filters user input, it is still vulnerable to code injection.
C. The successful attack does not show an error message to the administrator of the affected application.
D. The vulnerable application does not display errors with information about the injection results to the attacker.
A security analyst is performing an audit on the network to determine if there are any deviations from the security policies in place. The analyst discovers that a user from the IT department had a dial-out modem installed. Which security policy must the security analyst check to see if dial-out modems are allowed?
A. Firewall-management policy
B. Acceptable-use policy
C. Remote-access policy
D. Permissive policy
Jimmy is standing outside a secure entrance to a facility. He is pretending to have a tense conversation on his cell phone as an authorized employee badges in. Jimmy, while still on the phone, grabs the door as it begins to close. What just happened?
A. Piggybacking
B. Masqurading
C. Phishing
D. Whaling
Which of the following is an example of an asymmetric encryption implementation?
A. SHA1
B. PGP
C. 3DES
D. MD5
In order to show improvement of security over time, what must be developed?
A. Reports
B. Testing tools
C. Metrics
D. Taxonomy of vulnerabilities
Which of the following algorithms provides better protection against brute force attacks by using a 160-bit message digest?
A. MD5
B. SHA-1
C. RC4
D. MD4
Fingerprinting VPN firewalls is possible with which of the following tools?
A. Angry IP
B. Nikto
C. Ike-scan
D. Arp-scan
Which NMAP command combination would let a tester scan every TCP port from a class C network that is blocking ICMP with fingerprinting and service detection?
A. NMAP -PN -A -O -sS 192.168.2.0/24
B. NMAP -P0 -A -O -p1-65535 192.168.0/24
C. NMAP -P0 -A -sT -p0-65535 192.168.0/16
D. NMAP -PN -O -sS -p 1-1024 192.168.0/8
A person approaches a network administrator and wants advice on how to send encrypted email from home. The end user does not want to have to pay for any license fees or manage server services. Which of the following is the most secure encryption protocol that the network administrator should recommend?
A. IP Security (IPSEC)
B. Multipurpose Internet Mail Extensions (MIME)
C. Pretty Good Privacy (PGP)
D. Hyper Text Transfer Protocol with Secure Socket Layer (HTTPS) C
Which of the following represents the initial two commands that an IRC client sends to join an IRC network?
A. USER, NICK
B. LOGIN, NICK
C. USER, PASS
D. LOGIN, USER
While performing online banking using a Web browser, Kyle receives an email that contains an image of a well-crafted art. Upon clicking the image, a new tab on the web browser opens and shows an animated GIF of bills and coins being swallowed by a crocodile. After several days, Kyle noticed that all his funds on the bank was gone. What Web browser-based security vulnerability got exploited by the hacker?
A. Clickjacking
B. Web Form Input Validation
C. Cross-Site Request Forgery
D. Cross-Site Scripting
Password cracking programs reverse the hashing process to recover passwords. (True/False.)
A. True
B. False
Pentest results indicate that voice over IP traffic is traversing a network. Which of the following tools will decode a packet capture and extract the voice conversations?
A. Cain
B. John the Ripper
C. Nikto
D. Hping
Which of the following levels of algorithms does Public Key Infrastructure (PKI) use?
A. RSA 1024 bit strength
B. AES 1024 bit strength
C. RSA 512 bit strength
D. AES 512 bit strength
Emil uses nmap to scan two hosts using this command. nmap -sS -T4 -O 192.168.99.1 192.168.99.7 He receives this output: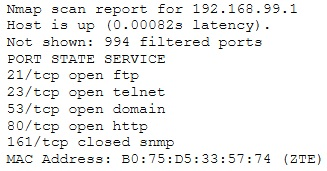
What is his conclusion?
A. Host 192.168.99.7 is an iPad.
B. He performed a SYN scan and OS scan on hosts 192.168.99.1 and 192.168.99.7.
C. Host 192.168.99.1 is the host that he launched the scan from.
D. Host 192.168.99.7 is down. B
What technique is used to perform a Connection Stream Parameter Pollution (CSPP) attack?
A. Injecting parameters into a connection string using semicolons as a separator
B. Inserting malicious Javascript code into input parameters
C. Setting a user’s session identifier (SID) to an explicit known value
D. Adding multiple parameters with the same name in HTTP requests
You've gained physical access to a Windows 2008 R2 server which has an accessible disc drive. When you attempt to boot the server and log in, you are unable to guess the password. In your tool kit you have an Ubuntu 9.10 Linux LiveCD. Which Linux based tool has the ability to change any user's password or to activate disabled Windows accounts?
A. CHNTPW
B. Cain & Abel
C. SET
D. John the Ripper
One way to defeat a multi-level security solution is to leak data via
A. a bypass regulator.
B. steganography.
C. a covert channel.
D. asymmetric routing.
Which of the following business challenges could be solved by using a vulnerability scanner?
A. Auditors want to discover if all systems are following a standard naming convention.
B. A web server was compromised and management needs to know if any further systems were compromised.
C. There is an emergency need to remove administrator access from multiple machines for an employee that quit.
D. There is a monthly requirement to test corporate compliance with host application usage and security policies.
An ethical hacker for a large security research firm performs penetration tests, vulnerability tests, and risk assessments. A friend recently started a company and asks the hacker to perform a penetration test and vulnerability assessment of the new company as a favor. What should the hacker's next step be before starting work on this job?
A. Start by foot printing the network and mapping out a plan of attack.
B. Ask the employer for authorization to perform the work outside the company.
C. Begin the reconnaissance phase with passive information gathering and then move into active information gathering.
D. Use social engineering techniques on the friend’s employees to help identify areas that may be susceptible to attack.
The chance of a hard drive failure is known to be once every four years. The cost of a new hard drive is $500. EF (Exposure Factor) is about 0.5. Calculate for the Annualized Loss Expectancy (ALE).
A. $62.5
B. $250
C. $125
D. $65.2
What does a firewall check to prevent particular ports and applications from getting packets into an organization?
A. Transport layer port numbers and application layer headers
B. Presentation layer headers and the session layer port numbers
C. Network layer headers and the session layer port numbers
D. Application layer port numbers and the transport layer headers
What is the main reason the use of a stored biometric is vulnerable to an attack?
A. The digital representation of the biometric might not be unique, even if the physical characteristic is unique.
B. Authentication using a stored biometric compares a copy to a copy instead of the original to a copy.
C. A stored biometric is no longer “something you are” and instead becomes “something you have”.
D. A stored biometric can be stolen and used by an attacker to impersonate the individual identified by the biometric.
An incident investigator asks to receive a copy of the event logs from all firewalls, proxy servers, and Intrusion Detection Systems (IDS) on the network of an organization that has experienced a possible breach of security. When the investigator attempts to correlate the information in all of the logs, the sequence of many of the logged events do not match up. What is the most likely cause?
A. The network devices are not all synchronized.
B. Proper chain of custody was not observed while collecting the logs.
C. The attacker altered or erased events from the logs.
D. The security breach was a false positive.
Which of the following types of firewalls ensures that the packets are part of the established session?
A. Stateful inspection firewall
B. Circuit-level firewall
C. Application-level firewall
D. Switch-level firewall
A company has five different subnets: 192.168.1.0, 192.168.2.0, 192.168.3.0, 192.168.4.0 and 192.168.5.0. How can NMAP be used to scan these adjacent Class C networks?
A. NMAP -P 192.168.1-5.
B. NMAP -P 192.168.0.0/16
C. NMAP -P 192.168.1.0,2.0,3.0,4.0,5.0
D. NMAP -P 192.168.1/17
Which of the following lists are valid data-gathering activities associated with a risk assessment?
A. Threat identification, vulnerability identification, control analysis
B. Threat identification, response identification, mitigation identification
C. Attack profile, defense profile, loss profile
D. System profile, vulnerability identification, security determination
When an alert rule is matched in a network-based IDS like snort, the IDS does which of the following?
A. Drops the packet and moves on to the next one
B. Continues to evaluate the packet until all rules are checked
C. Stops checking rules, sends an alert, and lets the packet continue
D. Blocks the connection with the source IP address in the packet
Which of the following network attacks takes advantage of weaknesses in the fragment reassembly functionality of the TCP/IP protocol stack?
A. Teardrop
B. SYN flood
C. Smurf attack
D. Ping of death
Which statement is TRUE regarding network firewalls preventing Web Application attacks?
A. Network firewalls can prevent attacks because they can detect malicious HTTP traffic.
B. Network firewalls cannot prevent attacks because ports 80 and 443 must be opened.
C. Network firewalls can prevent attacks if they are properly configured.
D. Network firewalls cannot prevent attacks because they are too complex to configure.
Which of the following is considered the best way to protect Personally Identifiable Information (PII) from Web application vulnerabilities?
A. Use cryptographic storage to store all PII
B. Use encrypted communications protocols to transmit PII
C. Use full disk encryption on all hard drives to protect PII
D. Use a security token to log into all Web applications that use PII
A penetration tester is hired to do a risk assessment of a company's DMZ. The rules of engagement states that the penetration test be done from an external IP address with no prior knowledge of the internal IT systems. What kind of test is being performed?
A. white box
B. grey box
C. red box
D. black box
You are the Systems Administrator for a large corporate organization. You need to monitor all network traffic on your local network for suspicious activities and receive notifications when an attack is occurring. Which tool would allow you to accomplish this goal?
A. Network-based IDS
B. Firewall
C. Proxy
D. Host-based IDS
A penetration tester is conducting a port scan on a specific host. The tester found several ports opened that were confusing in concluding the Operating System (OS) version installed. Considering the NMAP result below, which of the following is likely to be installed on the target machine by the OS?
A. The host is likely a Windows machine.
B. The host is likely a Linux machine.
C. The host is likely a router.
D. The host is likely a printer.
Which of the following statements regarding ethical hacking is incorrect?
A. Ethical hackers should never use tools or methods that have the potential of exploiting vulnerabilities in an organization’s systems.
B. Testing should be remotely performed offsite.
C. An organization should use ethical hackers who do not sell vendor hardware/software or other consulting services.
D. Ethical hacking should not involve writing to or modifying the target systems.
Which results will be returned with the following Google search query? site:target.com -site:Marketing.target.com accounting
A. Results matching all words in the query
B. Results matching “accounting” in domain target.com but not on the site Marketing.target.com
C. Results from matches on the site marketing.target.com that are in the domain target.com but do not include the word accounting
D. Results for matches on target.com and Marketing.target.com that include the word “accounting”
The use of technologies like IPSec can help guarantee the following: authenticity, integrity, confidentiality and
A. non-repudiation.
B. operability.
C. security.
D. usability.
Using Windows CMD, how would an attacker list all the shares to which the current user context has access?
A. NET USE
B. NET CONFIG
C. NET FILE
D. NET VIEW
An engineer is learning to write exploits in C++ and is using the exploit tool Backtrack. The engineer wants to compile the newest C++ exploit and name it calc.exe. Which command would the engineer use to accomplish this?
A. g++ hackersExploit.cpp -o calc.exe
B. g++ hackersExploit.py -o calc.exe
C. g++ -i hackersExploit.pl -o calc.exe
D. g++ –compile –i hackersExploit.cpp -o calc.exe
What is the name of the international standard that establishes a baseline level of confidence in the security functionality of IT products by providing a set of requirements for evaluation?
A. Blue Book
B. ISO 26029
C. Common Criteria
D. The Wassenaar Agreement
The security concept of "separation of duties" is most similar to the operation of which type of security device?
A. Firewall
B. Bastion host
C. Intrusion Detection System
D. Honeypot
Which of the following is a characteristic of Public Key Infrastructure (PKI)?
A. Public-key cryptosystems are faster than symmetric-key cryptosystems.
B. Public-key cryptosystems distribute public-keys within digital signatures.
C. Public-key cryptosystems do not require a secure key distribution channel.
D. Public-key cryptosystems do not provide technical non-repudiation via digital signatures.
How is sniffing broadly categorized?
A. Active and passive
B. Broadcast and unicast
C. Unmanaged and managed
D. Filtered and unfiltered
The following is a sample of output from a penetration tester's machine targeting a machine with the IP address of 192.168.1.106:What is most likely taking place?
A. Ping sweep of the 192.168.1.106 network
B. Remote service brute force attempt
C. Port scan of 192.168.1.106
D. Denial of service attack on 192.168.1.106
Which set of access control solutions implements two-factor authentication?
A. USB token and PIN
B. Fingerprint scanner and retina scanner
C. Password and PIN
D. Account and password
Which of the following is a symmetric cryptographic standard?
A. DSA
B. PKI
C. RSA
D. 3DES
Which command lets a tester enumerate alive systems in a class C network via ICMP using native Windows tools?
A. ping 192.168.2.
B. ping 192.168.2.255
C. for %V in (1 1 255) do PING 192.168.2.%V
D. for /L %V in (1 1 254) do PING -n 1 192.168.2.%V | FIND /I “Reply”
Which of the following items of a computer system will an anti-virus program scan for viruses?
A. Boot Sector
B. Deleted Files
C. Windows Process List
D. Password Protected Files
Which among the following is a Windows command that a hacker can use to list all the shares to which the current user context has access?
A. NET FILE
B. NET USE
C. NET CONFIG
D. NET VIEW
Access Full 312-50V9 Exam Prep Free
Want to go beyond these 50 questions? Click here to unlock a full set of 312-50V9 exam prep free questions covering every domain tested on the exam.
We continuously update our content to ensure you have the most current and effective prep materials.
Good luck with your 312-50V9 certification journey!