312-50V10 Exam Prep Free – 50 Practice Questions to Get You Ready for Exam Day
Getting ready for the 312-50V10 certification? Our 312-50V10 Exam Prep Free resource includes 50 exam-style questions designed to help you practice effectively and feel confident on test day
Effective 312-50V10 exam prep free is the key to success. With our free practice questions, you can:
- Get familiar with exam format and question style
- Identify which topics you’ve mastered—and which need more review
- Boost your confidence and reduce exam anxiety
Below, you will find 50 realistic 312-50V10 Exam Prep Free questions that cover key exam topics. These questions are designed to reflect the structure and challenge level of the actual exam, making them perfect for your study routine.
Scenario: 1. Victim opens the attacker's web site. 2. Attacker sets up a web site which contains interesting and attractive content like 'Do you want to make $1000 in a day?'. 3. Victim clicks to the interesting and attractive content URL. 4. Attacker creates a transparent 'iframe' in front of the URL which victim attempts to click, so victim thinks that he/she clicks to the 'Do you want to make $1000 in a day?' url but actually he/she clicks to the content or UPL that exists in the transparent 'iframe' which is setup by the attacker. What is the name of the attack which is mentioned in the scenario?
A. Session Fixation
B. HTML Injection
C. HTTP Parameter Pollution
D. Clickjacking Attack
What mechanism in Windows prevents a user from accidentally executing a potentially malicious batch (.bat) or PowerShell (.ps1) script?
A. User Access Control (UAC)
B. Data Execution Prevention (DEP)
C. Address Space Layout Randomization (ASLR)
D. Windows firewall
In which of the following cryptography attack methods, the attacker makes a series of interactive queries, choosing subsequent plaintexts based on the information from the previous encryptions?
A. Chosen-plaintext attack
B. Ciphertext-only attack
C. Adaptive chosen-plaintext attack
D. Known-plaintext attack
Which of the following is a low-tech way of gaining unauthorized access to systems?
A. Scanning
B. Sniffing
C. Social Engineering
D. Eavesdropping
What does the ""oX flag do in an Nmap scan?
A. Perform an Xmas scan
B. Perform an eXpress scan
C. Output the results in truncated format to the screen
D. Output the results in XML format to a file
What is the difference between the AES and RSA algorithms?
A. Both are symmetric algorithms, but AES uses 256-bit keys
B. AES is asymmetric, which is used to create a public/private key pair; RSA is symmetric, which is used to encrypt data
C. Both are asymmetric algorithms, but RSA uses 1024-bit keys
D. RSA is asymmetric, which is used to create a public/private key pair; AES is symmetric, which is used to encrypt data
You have successfully comprised a server having an IP address of 10.10.0.5. You would like to enumerate all machines in the same network quickly. What is the best Nmap command you will use?
A. nmap -T4 -q 10.10.0.0/24
B. nmap -T4 -F 10.10.0.0/24
C. nmap -T4 -r 10.10.1.0/24
D. nmap -T4 -O 10.10.0.0/24
Email is transmitted across the Internet using the Simple Mail Transport Protocol. SMTP does not encrypt email, leaving the information in the message vulnerable to being read by an unauthorized person. SMTP can upgrade a connection between two mail servers to use TLS. Email transmitted by SMTP over TLS is encrypted. What is the name of the command used by SMTP to transmit email over TLS?
A. OPPORTUNISTICTLS
B. UPGRADETLS
C. FORCETLS
D. STARTTLS
What would you enter, if you wanted to perform a stealth scan using Nmap?
A. nmap -sU
B. nmap -sS
C. nmap -sM
D. nmap -sT
Shellshock allowed an unauthorized user to gain access to a server. It affected many Internet-facing services, which OS did it not directly affect?
A. Linux
B. Unix
C. OS X
D. Windows
Chandler works as a pen-tester in an IT-firm in New York. As a part of detecting viruses in the systems, he uses a detection method where the anti-virus executes the malicious codes on a virtual machine to simulate CPU and memory activities. Which type of virus detection method did Chandler use in this context?
A. Heuristic Analysis
B. Code Emulation
C. Integrity checking
D. Scanning
As a Certified Ethical Hacker, you were contracted by a private firm to conduct an external security assessment through penetration testing. What document describes the specifics of the testing, the associated violations, and essentially protects both the organization's interest and your liabilities as a tester?
A. Service Level Agreement
B. Project Scope
C. Rules of Engagement
D. Non-Disclosure Agreement
A hacker named Jack is trying to compromise a bank's computer system. He needs to know the operating system of that computer to launch further attacks. What process would help him?
A. Banner Grabbing
B. IDLE/IPID Scanning
C. SSDP Scanning
D. UDP Scanning
What is the minimum number of network connections in a multihomed firewall?
A. 3
B. 2
C. 5
D. 4
Jimmy is standing outside a secure entrance to a facility. He is pretending to have a tense conversation on his cell phone as an authorized employee badges in. Jimmy, while still on the phone, grabs the door as it begins to close. What just happened?
A. Masquerading
B. Tailgating
C. Phishing
D. Whaling
Which of the following is a passive wireless packet analyzer that works on Linux-based systems?
A. OpenVAS
B. Burp Suite
C. tshark
D. Kismet
Bob, your senior colleague, has sent you a mail regarding aa deal with one of the clients. You are requested to accept the offer and you oblige. After 2 days, Bob denies that he had ever sent a mail. What do you want to "know" to prove yourself that it was Bob who had send a mail?
A. Confidentiality
B. Integrity
C. Non-Repudiation
D. Authentication
You want to do an ICMP scan on a remote computer using hping2. What is the proper syntax?
A. hping2 -1 host.domain.com
B. hping2-i host.domain.com
C. hping2 “”set-ICMP host.domain.com
D. hping2 host.domain.com
Ricardo wants to send secret messages to a competitor company. To secure these messages, he uses a technique of hiding a secret message within an ordinary message. The technique provides "˜security through obscurity'. What technique is Ricardo using?
A. Encryption
B. Steganography
C. RSA algorithm
D. Public-key cryptography
Which of the following is a serious vulnerability in the popular OpenSSL cryptographic software library? This weakness allows stealing the information protected, under normal conditions, by the SSL/TLS encryption used to secure the Internet.
A. SSL/TLS Renegotiation Vulnerability
B. Shellshock
C. Heartbleed Bug
D. POODLE
Which utility will tell you in real time which ports are listening or in another state?
A. Netsat
B. Loki
C. Nmap
D. TCPView
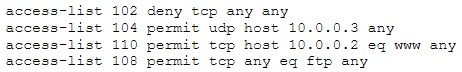
The security administrator of ABC needs to permit Internet traffic in the host 10.0.0.2 and UDP traffic in the host 10.0.0.3. He also needs to permit all FTP traffic to the rest of the network and deny all other traffic. After he applied his ACL configuration in the router, nobody can access to the ftp, and the permitted hosts cannot access the Internet. According to the next configuration, what is happening in the network?
A. The ACL 104 needs to be first because is UDP
B. The ACL 110 needs to be changed to port 80
C. The ACL for FTP must be before the ACL 110
D. The first ACL is denying all TCP traffic and the other ACLs are being ignored by the router
What is the least important information when you analyze a public IP address in a security alert?
A. ARP
B. Whois
C. DNS
D. Geolocation
Which of the following statements regarding ethical hacking is incorrect?
A. An organization should use ethical hackers who do not sell vendor hardware/software or other consulting services
B. Ethical hackers should never use tools or methods that have the potential of exploiting vulnerabilities in an organization’s systems
C. Ethical hacking should not involve writing to or modifying the target systems.
D. Testing should be remotely performed offsite.
A new wireless client is configured to join a 802.11 network. This client uses the same hardware and software as many of the other clients on the network. The client can see the network, but cannot connect. A wireless packet sniffer shows that the Wireless Access Point (WAP) is not responding to the association requests being sent by the wireless client. What is a possible source of this problem?
A. The WAP does not recognize the client’s MAC address
B. The client cannot see the SSID of the wireless network
C. Client is configured for the wrong channel
D. The wireless client is not configured to use DHCP
An Intrusion Detection System (IDS) has alerted the network administrator to a possibly malicious sequence of packets sent to a Web server in the network's external DMZ. The packet traffic was captured by the IDS and saved to a PCAP file. What type of network tool can be used to determine if these packets are genuinely malicious or simply a false positive?
A. Protocol analyzer
B. Network sniffer
C. Intrusion Prevention System (IPS)
D. Vulnerability scanner
This asymmetry cipher is based on factoring the product of two large prime numbers. What cipher is described above?
A. SHA
B. RSA
C. MD5
D. RC5
What type of OS fingerprinting technique sends specially crafted packets to the remote OS and analyzes the received response?
A. Passive
B. Active
C. Reflective
D. Distributive
PGP, SSL, and IKE are all examples of which type of cryptography?
A. Hash Algorithm
B. Digest
C. Secret Key
D. Public Key
........is an attack type for a rogue Wi-Fi access point that appears to be a legitimate one offered on the premises, but actually has been set up to eavesdrop on wireless communications. It is the wireless version of the phishing scam. An attacker fools wireless users into connecting a laptop or mobile phone to a tainted hotspot by posing as a legitimate provider. This type of attack may be used to steal the passwords of unsuspecting users by either snooping the communication link or by phishing, which involves setting up a fraudulent web site and luring people there. Fill in the blank with appropriate choice.
A. Evil Twin Attack
B. Sinkhole Attack
C. Collision Attack
D. Signal Jamming Attack
User A is writing a sensitive email message to user B outside the local network. User A has chosen to use PKI to secure his message and ensure only user B can read the sensitive email. At what layer of the OSI layer does the encryption and decryption of the message take place?
A. Application
B. Transport
C. Session
D. Presentation
In Risk Management, how is the term "likelihood" related to the concept of "threat?"
A. Likelihood is the likely source of a threat that could exploit a vulnerability.
B. Likelihood is the probability that a threat-source will exploit a vulnerability.
C. Likelihood is a possible threat-source that may exploit a vulnerability.
D. Likelihood is the probability that a vulnerability is a threat-source.
Which of the following Secure Hashing Algorithm (SHA) produces a 160-bit digest from a message with a maximum length of (264-1) bits and resembles the MD5 algorithm?
A. SHA-2
B. SHA-3
C. SHA-1
D. SHA-0
Which access control mechanism allows for multiple systems to use a central authentication server (CAS) that permits users to authenticate once and gain access to multiple systems?
A. Single sign-on
B. Windows authentication
C. Role Based Access Control (RBAC)
D. Discretionary Access Control (DAC)
A pen-tester is configuring a Windows laptop for a test. In setting up Wireshark, what river and library are required to allow the NIC to work in promiscuous mode?
A. Winprom
B. Libpcap
C. Winpsw
D. Winpcap
Firewalls are the software or hardware systems that are able to control and monitor the traffic coming in and out the target network based on pre-defined set of rules. Which of the following types of firewalls can protect against SQL injection attacks?
A. Data-driven firewall
B. Stateful firewall
C. Packet firewall
D. Web application firewall
Which of the following is a command line packet analyzer similar to GUI-based Wireshark?
A. Nessus
B. Jack the ripper
C. Tcpdump
D. Ethereal
To reach a bank web site, the traffic from workstations must pass through a firewall. You have been asked to review the firewall configuration to ensure that workstations in network 10.10.10.0/24 can only reach the bank web site 10.20.20.1 using https. Which of the following firewall rules meets this requirement?
A. If (source matches 10.10.10.0/24 and destination matches 10.20.20.1 and port matches 443) then permit
B. If (source matches 10.10.10.0/24 and destination matches 10.20.20.1 and port matches 80 or 443) then permit
C. If (source matches 10.20.20.1 and destination matches 10.10.10.0/24 and port matches 443) then permit
D. If (source matches 10.10.10.0 and destination matches 10.20.20.1 and port matches 443) then permit
Websites and web portals that provide web services commonly use the Simple Object Access Protocol (SOAP). Which of the following is an incorrect definition or characteristics of the protocol?
A. Based on XML
B. Only compatible with the application protocol HTTP
C. Exchanges data between web services
D. Provides a structured model for messaging
Which of the following antennas is commonly used in communications for a frequency band of 10 MHz to VHF and UHF?
A. Omnidirectional antenna
B. Dipole antenna
C. Yagi antenna
D. Parabolic grid antenna
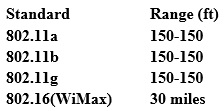
From the following table, identify the wrong answer in terms of Range (ft).
A. 802.11b
B. 802.11g
C. 802.16(WiMax)
D. 802.11a
You have gained physical access to a Windows 2008 R2 server which has an accessible disc drive. When you attempt to boot the server and log in, you are unable to guess the password. In your toolkit, you have an Ubuntu 9.10 Linux LiveCD. Which Linux-based tool can change any user's password or activate disabled Windows accounts?
A. John the Ripper
B. SET
C. CHNTPW
D. Cain & Abel
Which of the following DoS tools is used to attack target web applications by starvation of available sessions on the web server? The tool keeps sessions at halt using never-ending POST transmissions and sending an arbitrarily large content-length header value.
A. Stacheldraht
B. LOIC
C. R-U-Dead-Yet? (RUDY)
D. MyDoom
Steve, a scientist who works in a governmental security agency, developed a technological solution to identify people based on walking patterns and implemented this approach to a physical control access. A camera captures people walking and identifies the individuals using Steve's approach. After that, people must approximate their RFID badges. Both the identifications are required to open the door. In this case, we can say:
A. Although the approach has two phases, it actually implements just one authentication factor
B. The solution implements the two authentication factors: physical object and physical characteristic
C. The solution will have a high level of false positives
D. Biological motion cannot be used to identify people
Which of the following options represents a conceptual characteristic of an anomaly-based IDS over a signature-based IDS?
A. Produces less false positives
B. Can identify unknown attacks
C. Requires vendor updates for a new threat
D. Cannot deal with encrypted network traffic
Why should the security analyst disable/remove unnecessary ISAPI filters?
A. To defend against social engineering attacks
B. To defend against webserver attacks
C. To defend against jailbreaking
D. To defend against wireless attacks
You have several plain-text firewall logs that you must review to evaluate network traffic. You know that in order to do fast, efficient searches of the logs you must use regular expressions. Which command-line utility are you most likely to use?
A. Relational Database
B. MS Excel
C. Notepad
D. Grep
OpenSSL on Linux servers includes a command line tool for testing TLS. What is the name of the tool and the correct syntax to connect to a web server?
A. openssl s_client “”site www.website.com:443
B. openssl_client “”site www.website.com:443
C. openssl_client “”connect www.website.com:443
D. openssl s_client “”connect www.website.com:443
Gavin owns a white-hat firm and is performing a website security audit for one of his clients. He begins by running a scan which looks for common misconfigurations and outdated software versions. Which of the following tools is he most likely using?
A. Armitage
B. Nikto
C. Metasploit
D. Nmap
You are analyzing a traffic on the network with Wireshark. You want to routinely run a cron job which will run the capture against a specific set of IPs. "" 192.168.8.0/24. What command you would use?
A. tshark “”net 192.255.255.255 mask 192.168.8.0
B. wireshark “”capture “”local “”masked 192.168.8.0 “”range 24
C. sudo tshark “”f “net 192.168.8.0/24”
D. wireshark “”fetch “192.168.8/*”
Access Full 312-50V10 Exam Prep Free
Want to go beyond these 50 questions? Click here to unlock a full set of 312-50V10 exam prep free questions covering every domain tested on the exam.
We continuously update our content to ensure you have the most current and effective prep materials.
Good luck with your 312-50V10 certification journey!