300-430 Exam Prep Free – 50 Practice Questions to Get You Ready for Exam Day
Getting ready for the 300-430 certification? Our 300-430 Exam Prep Free resource includes 50 exam-style questions designed to help you practice effectively and feel confident on test day
Effective 300-430 exam prep free is the key to success. With our free practice questions, you can:
- Get familiar with exam format and question style
- Identify which topics you’ve mastered—and which need more review
- Boost your confidence and reduce exam anxiety
Below, you will find 50 realistic 300-430 Exam Prep Free questions that cover key exam topics. These questions are designed to reflect the structure and challenge level of the actual exam, making them perfect for your study routine.
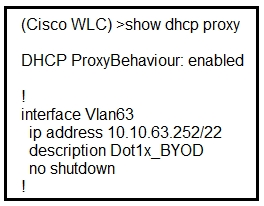
Refer to the exhibit. A network administrator deploys the DHCP profiler service in two ISE servers: 10.3.10.101 and 10.3.10.102. All BYOD devices connecting to WLAN on VLAN63 have been incorrectly profiled and are assigned as unknown profiled endpoints. Which action efficiently rectifies the issue according to Cisco recommendations?
A. Nothing needed to be added on the Cisco WLC or VLAN interface. The ISE configuration must be fixed.
B. Disable DHCP proxy on the Cisco WLC.
C. Disable DHCP proxy on the Cisco WLC and run the ip helper-address command under the VLAN interface to point to DHCP and the two ISE servers.
D. Keep DHCP proxy enabled on the Cisco WLC and define helper-address under the VLAN interface to point to the two ISE servers.
What is the maximum time range that can be viewed on the Cisco DNA Center issues and alarms page?
A. 3 hours
B. 24 hours
C. 3 days
D. 7 days
A network is set up to support wired and wireless clients. Both types must authenticate using 802.1X before connecting to the network. Different types of client authentication must be separated on a Cisco ISE deployment. Which two configuration items achieve this task? (Choose two.)
A. device profiles
B. policy sets
C. separate networks
D. policy groups
E. policy results
An engineer must provide a graphical report with summary grouped data of the total number of wireless clients on the network. Which Cisco Prime Infrastructure report provides the required data?
A. Client Traffic Stream Metrics
B. Client Summary
C. Posture Status Count
D. Mobility Client Summary
A wireless engineer must configure IEEE 802.1X authentication on a WLAN that supports new and legacy wireless devices. Which condition must be met for the legacy clients to be able to associate and authenticate without issues?
A. The authenticator and the authentication server must support the same authentication protocol.
B. The client and the authenticator must support the same authentication protocol.
C. The client and the controller must support the same authentication protocol.
D. The client and the authentication server must support the same authentication protocol.
An IT team is growing quickly and needs a solution for management device access. The solution must authenticate users from an external repository instead of the current local on the WLC, and it must also identify the user and determine what level of access users should have. Which protocol do you recommend to achieve these goals?
A. network policy server
B. RADIUS
C. TACACS+
D. LDAP
A network engineer must segregate all IPads on the guest WLAN to a separate VLAN. How does the engineer accomplish this task without using Cisco ISE?
A. Create a local policy on the WLC.
B. Use 802.1x authentication to profile the devices.
C. Use an mDNS profile for the iPad device.
D. Enable RADIUS DHCP profiling on the WLAN.
On a branch office deployment, it has been noted that if the FlexConnect AP is in standalone mode and loses connection to the WLC, all clients are disconnected, and the SSID is no longer advertised. Considering that FlexConnect local switching is enabled, which setting is causing this behavior?
A. ISE NAC is enabled
B. 802.11r Fast Transition is enabled
C. Client Exclusion is enabled
D. FlexConnect Local Auth is disabled
A healthcare organization notices many rogue APs and is concerned about a honeypot attack. Which configuration must a wireless network engineer perform in Cisco Prime Infrastructure to prevent these attacks most efficiently upon detection?
A. Set the auto containment level to 0 and select the Using Our SSID containment option.
B. Set the manual containment level to 4 and select the Ad Hoc Rogue AP containment option.
C. Set the auto containment level to 0 and select the Ad Hoc Rogue AP containment option.
D. Set the auto containment level to 4 and select the Using Our SSID containment option.
An engineer must collect all Cisco CleanAir alarms in a central location for archival purposes. Which device is configured for collection?
A. wIPS AP
B. Cisco Prime Infrastructure
C. MSE
D. WLC
A hospital wants to offer indoor directions to patient rooms utilizing its existing wireless infrastructure. The wireless network has been using location services specifications. Which two components must be installed to support this requirement? (Choose two.)
A. WIPS
B. Cisco MSE
C. Cisco CMX Visitor Connect
D. Cisco CMX AppEngage
E. Cisco CMX Analytics
Which two events are outcomes of a successful RF jamming attack? (Choose two.)
A. disruption of WLAN services
B. unauthentication association
C. deauthentication broadcast
D. deauthentication multicast
E. physical damage to AP hardware
An engineer is managing a wireless network for a shopping center. The network includes a Cisco WLC, a Cisco MSE, and a Cisco Prime Infrastructure. What is required to use Cisco CMX Location Analytics?
A. Enable tracking parameters in Cisco MSE.
B. Enable Context Aware and CMX Browser Engage.
C. Install Cisco Prime Infrastructure with floor maps.
D. Set history parameters in Cisco MSE.
Refer to the exhibit. An engineer deployed a Cisco WLC using local EAP. Users who are configured for EAP-PEAP cannot connect to the network. Based on the local EAP debug on the controller provided, why is the client unable to connect?
A. The client is failing to accept certificate.
B. The Cisco WLC is configured for the incorrect date.
C. The Cisco WLC local EAP profile is misconfigured.
D. The user is using invalid credentials.
Refer to the exhibit. An engineer must preserve a QoS marking sent by the Cisco Jabber software running on PC1. Which marking value must be trusted on port Fa 0/6?
A. DSCP
B. 802.1p
C. CoS
D. IP precedence
An engineer is configuring multicast for wireless for an all-company video meeting on a network using EIGRP and BGP within a single domain from a single source. Which type of multicast routing should be implemented?
A. Protocol Independent Multicast Dense Mode
B. Source Specific Multicast
C. Multicast Source Discovery Protocol
D. Protocol Independent Multicast Sparse Mode
What are two considerations when deploying a Cisco Hyperlocation? (Choose two.)
A. NTP configuration is available, but not recommended.
B. The Cisco Hyperlocation feature must be enabled only on the wireless LAN controller.
C. After enabling Cisco Hyperlocation on Cisco CMX, the APs and the wireless LAN controller must be restarted.
D. The Cisco Hyperlocation feature must be enabled on the wireless LAN controller and Cisco CMX.
E. If the Cisco CMX server is a VM, a high-end VM is needed for Cisco Hyperlocation deployments.
An engineer is implementing RADIUS to restrict administrative control to the network with the WLC management IP address of 192.168.1.10 and an AP subnet of 192.168.2.0/24. Which entry does the engineer define in the RADIUS server?
A. administrative access defined on the WLC and the network range 192.168.2.0/255.255.254.0
B. NAS entry of the virtual interface and the network range 192.168.2.0/255.255.255.0
C. shared secret defined on the WLC and the network range 192.168.1.0/255.255.254.0
D. WLC roles for commands and the network range 192.168.1.0/255.255.255.0
What must be configured on the Global Configuration page of the WLC for an AP to use 802.1x to authenticate to the wired infrastructure?
A. local access point credentials
B. RADIUS shared secret
C. TACACS server IP address
D. supplicant credentials
A customer is concerned that their wireless network is detecting spurious threats from channels that are not being used by their wireless infrastructure. Which two technologies must they deploy? (Choose two.)
A. FlexConnect mode
B. monitor mode
C. sniffer mode with no submode
D. local mode with WIPS submode
E. rogue detector mode
An engineer needs read/write access to rename access points and add them to the correct AP groups on a wireless controller. Using Cisco ISE TACACS, which custom attributes is the minimum required?
A. role1=WLAN
B. role1=WLAN role2=SECURITY
C. role1=WLANrole2=WIRELESS
D. role1=WIRELESS
Refer to the exhibit. An administrator notices slower location updates from the controller to Cisco CMX. Which command must be configured to get an update every 5 seconds for rogues?
A. config location notification interval rssi rogues 5
B. config nmsp notification interval rssi rogues 5
C. config subscription notification interval rssi rogues 5
D. config cmx notification interval rssi rogues 5
A user is trying to connect to a wireless network that is configured for WPA2-Enterprise security using a corporate laptop. The CA certificate for the authentication server has been installed on the Trusted Root Certification Authorities store on the laptop. The user has been prompted to enter the credentials multiple times, but the authentication has not succeeded. What is causing the issue?
A. There is an IEEE invalid 802.1X authentication policy on the authentication server.
B. The user Active Directory account is locked out after several failed attempts.
C. There is an invalid 802.1X authentication policy on the authenticator.
D. The laptop has not received a valid IP address from the wireless controller.
An engineer must send Cisco OEAPs to the homes of employees. The APs must be able to discover and join the WLC when they connect to each employee home network. Which action accomplishes this task?
A. Use the WLC name and management IP address to configure the OEAPs.
B. Use the OEAP management IP address to listen for discovery broadcasts from the WLC.
C. Use the WLC name and management IP address to configure the DNS server.
D. Use DHCP Option 43 to configure the WLAN name and management IP address.
Which QoS level is recommended for guest services?
A. gold
B. bronze
C. platinum
D. silver
A corporation is spread across different countries and uses MPLS to connect the offices. The senior management wants to utilize the wireless network for all the employees. To ensure strong connectivity and minimize delays, an engineer needs to control the amount of traffic that is traversing between the APs and the central WLC. Which configuration should be used to accomplish this goal?
A. FlexConnect mode with central switching enabled
B. FlexConnect mode with central authentication
C. FlexConnect mode with OfficeExtend enabled
D. FlexConnect mode with local authentication
A company has a Cisco wireless network with Cisco ISE. The company wants to allow employees to use their personal mobile devices on the wireless network. The company wants to allow access to the network only if the devices meet certain criteria. To meet the requirement, the company asked a network engineer to create a native supplicant profile. Which two fields must be configured when the profile is created? (Choose two.)
A. Allowed Protocol (PEAP/TLS)
B. Allowed Protocol (Ms-CHAPv2/ EAP-FAST)
C. SSID Name
D. WLC Name
E. Allowed Protocol (LEAP/ EAP-TTLS)
The IT department creates a video containing instructions for employees who have just joined the company. Newcomers need to join the wireless network named NEW0123456789. The WLAN name will be changed daily by IT support. Only new employees must receive the video over wireless multicast. What allows this feature?
A. WMF
B. WMM
C. TPC
D. DCA
During the EAP process and specifically related to the client authentication session, which encrypted key is sent from the RADIUS server to the access point?
A. WPA key
B. session key
C. encryption key
D. shared-secret key
Where is Cisco Hyperlocation enabled on a Cisco Catalyst 9800 Series Wireless Controller web interface?
A. Policy Profile
B. AP Join Profile
C. Flex Profile
D. RF Profile
An engineer is configuring the maps on the Cisco Prime Infrastructure, but clients fail to show up on the maps. Which two actions are needed to complete this configuration? (Choose two.)
A. Install event group services in Cisco Prime Infrastructure.
B. Synchronize the Cisco WLC with Cisco Prime Infrastructure.
C. Synchronize the network designs with the Cisco MSE.
D. Activate the context-aware service on the Cisco MSE.
E. Install wIPS licenses on the Cisco MSE.
An engineer configures an AireOS WLC v8.2 that has Cisco Aironet 3700 Series APs and Cisco Hyperlocation modules. The engineer deploys and enables a WLAN that has Hyperlocation. During testing, the engineer notices poor location accuracy when the packets arrive. Which action resolves the issue?
A. Open SNMP port 161 and NMSP port 16113 on the WLC.
B. Enable Hyperlocation in the Global Configuration settings of the WLC.
C. Wait 60 to 90 minutes for RRM to settle before recording location measurements.
D. Install the software code for the WLC that supports the Hyperlocation module.
A network administrator just completed the basic implementation of Cisco CMX and tries to implement location tracking. The administrator is having trouble establishing connectivity between one of the WLCs through NMSP. What must be configured to establish this connectivity? (Choose two.)
A. Add permanent licenses on the Cisco CMX server.
B. Allow on the firewall port 16113 between Cisco CMX and the WLC.
C. Enable NMSP on the WLC.
D. Reboot Cisco CMX after adding the WLC for the first time.
E. Add to the WLC the MAC address and SSC key for the Cisco CMX server.
The IT department creates a video containing instructions for employees who have just joined the company. Newcomers need to join the wireless network named NEW4501999110. The WLAN name will be changed daily by IT support. Only new employees must receive the video over wireless multicast. What allows this feature?
A. WMF
B. WMM
C. TPC
D. DCA
Company XYZ recently migrated from AireOS to IOS XE 9800 WLCs. The Internet bandwidth must be limited to 5 Mbps for each guest client as per the global standard. In which configuration on the Cisco Catalyst 9800 WLC must the QoS requirement be added?
A. table map
B. policy map
C. service policy
D. class map
An enterprise has recently deployed a voice and video solution available to all employees using AireOS controllers. The employees must use this service over their laptops, but users report poor service when connected to the wireless network. The programs that consume bandwidth must be identified and restricted. Which configuration on the WLAN aids in recognizing the traffic?
A. NetFlow Monitor
B. AVC Profile
C. QoS Profile
D. Application Visibility
Clients on access points within an AP group are not receiving multicast traffic after roaming to another AP within the AP group. Which action maintains multicast connectivity?
A. Enable a unique NAS-ID for the AP group.
B. Enable NAC out-of-band support.
C. Enable IGMP snooping.
D. Enable an ACL on the router that serves the VLAN or subnet.
An IT department receives a report of a stolen laptop and has information on the MAC address of the laptop. Which two settings must be set on the wireless infrastructure to determine its location? (Choose two.)
A. Location History for Clients must be enabled on the MSE.
B. Client location tracking must be enabled on the MSE.
C. Location History for Visitors must be enabled on the MSE.
D. Location History for Rogue APs & Rogue Clients must be enabled on the MSE.
E. Tracking optimization must be enabled on the WLC.
A new MSE with wIPS service has been installed and no alarm information appears to be reaching the MSE from controllers. Which protocol must be allowed to reach the MSE from the controllers?
A. SOAP/XML
B. NMSP
C. CAPWAP
D. SNMP
An engineer must implement a wireless network to support location services. The network will include an MSE and Cisco WLC. After the deployment, the IT team must be able to locate and track clients. What is the minimum number of APs that a client must hear to accomplish this configuration so that the engineer can position them accordingly?
A. 1
B. 3
C. 4
D. 6
An engineer is planning an image upgrade of the WLC, and hundreds of APs are spread across remote sites with limited WAN bandwidth. The engineer must minimize the WAN utilization for this upgrade. Which approach must be used for the AP image upgrade?
A. Predownload the new code to the APs.
B. Use the Smart AP image upgrade feature.
C. Allow the APs to download their code after WLC reboot.
D. Execute parallel TFTP code upgrade on the APs via SSH.
Which two protocols are used to communicate between the Cisco MSE and the Cisco Prime Infrastructure network management software? (Choose two.)
A. HTTPS
B. Telnet
C. SOAP
D. SSH
E. NMSP
Refer to the exhibit.Which COS to DSCP map must be modified to ensure that voice traffic is tagged correctly as it traverses the network?
A. COS of 6 to DSCP 46
B. COS of 3 to DSCP 26
C. COS of 7 to DSCP 48
D. COS of 5 to DSCP 46
A municipality customer uses a Cisco 5520 Series Wireless Controller for the wireless network. The customer intends to move the depot of its stores from using legacy bespoke voice-over-Wi-Fi handsets to a VoIP software package running on 5 GHz-capable laptops, tablets, and smartphones. Bluetooth headsets will be used for any voice communication on any data device. Assuming that a suitable RF site survey for 5 GHz has already been carried out, which two configuration settings ensure the best possible voice experience? (Choose two.)
A. Configure AVC on the controller to prioritize voice over other applications’ traffic on the same device.
B. Remark all traffic coming from the new voice-capable devices with DSCP 46 (EF) at the AP.
C. Assign the Platinum QoS profile to the SSID carrying the new-style voice traffic.
D. Create mobility groups and include all the APs in the high-density areas.
E. Turn off the 2.4 GHz radios on all APs where the voice application is used.
An engineer has been hired to implement a way for users to stream video content without having issues on the wireless network. To accomplish this goal, the engineer must set up a reliable way for a Media Stream to work between Cisco FlexConnect APs. Which feature must be enabled to guarantee delivery?
A. Unicast Direct
B. IGMP Direct
C. Multicast Direct
D. Multicast-to-Unicast Direct
An engineer has eight WLCs in a mobility group and must reduce the bandwidth consumed. Which two configuration items achieve this result? (Choose two.)
A. global multicast mode
B. mobility group unicast messaging
C. global unicast messaging
D. mobility group multicast messaging
E. global symmetric mobility messaging
An engineer is ensuring that, on the IEEE 802.1X wireless network, clients authenticate using a central repository and local credentials on the Cisco WLC. Which two configuration elements must be completed on the WLAN? (Choose two.)
A. TACACS+
B. MAC authentication
C. local EAP enabled
D. web authentication
E. LDAP server
Which protocol enables multicast traffic only on a specific WLAN named MULTI123456789 instead of the whole network?
A. WMM
B. TPC
C. DCA
D. WMF
Refer to the exhibit. A network architect configured the Cisco Catalyst 9800 Series Controller to find out information on client types in the wireless network. RADIUS profiling is enabled so that the controller forwards the information about clients to a Cisco ISE server through vendor-specific RADIUS attributes. The ISE server is not profiling any data from the controller. Which configuration must be added in the blank in the code to accomplish the profiling on the Cisco 9800 Series controller?
A. aaa accounting identity acct_method start-stop group rad-group
B. aaa accounting network acct_method start-stop group rad-group
C. aaa accounting exec acct_method start-stop group rad-group
D. aaa accounting commands acct_method start-stop group rad-group
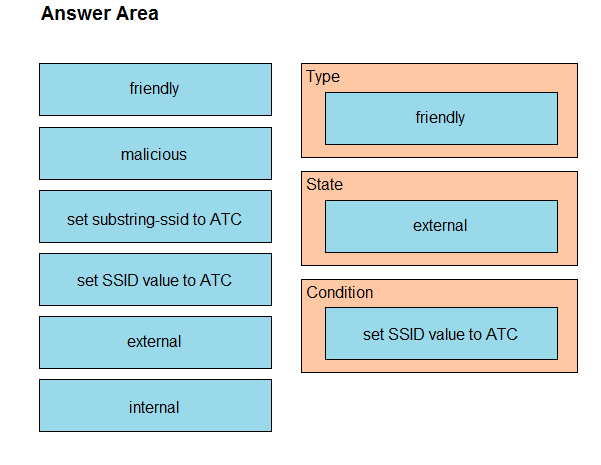
DRAG DROP - The network management team in a large shopping center has detected numerous rogue APs from local coffee shops that are broadcasting SSIDs. All of these SSIDs have names starting with ATC (for example, ATC302, ATC011, and ATC566). A wireless network engineer must appropriately classify these SSIDs using the Rogue Rules feature. Drag and drop the options from the left onto the categories in which they must be used on the right. Not all options are used. Select and Place:
Access Full 300-430 Exam Prep Free
Want to go beyond these 50 questions? Click here to unlock a full set of 300-430 exam prep free questions covering every domain tested on the exam.
We continuously update our content to ensure you have the most current and effective prep materials.
Good luck with your 300-430 certification journey!