PCNSA Practice Exam Free – 50 Questions to Simulate the Real Exam
Are you getting ready for the PCNSA certification? Take your preparation to the next level with our PCNSA Practice Exam Free – a carefully designed set of 50 realistic exam-style questions to help you evaluate your knowledge and boost your confidence.
Using a PCNSA practice exam free is one of the best ways to:
- Experience the format and difficulty of the real exam
- Identify your strengths and focus on weak areas
- Improve your test-taking speed and accuracy
Below, you will find 50 realistic PCNSA practice exam free questions covering key exam topics. Each question reflects the structure and challenge of the actual exam.
Which Security policy action will message a user's browser that their web session has been terminated?
A. Reset client
B. Deny
C. Drop
D. Reset server
Access to which feature requires a URL Filtering license?
A. PAN-DB database
B. External dynamic lists
C. DNS Security
D. Custom URL categories
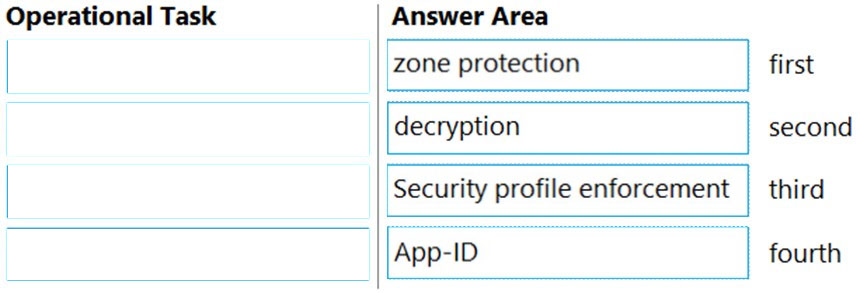
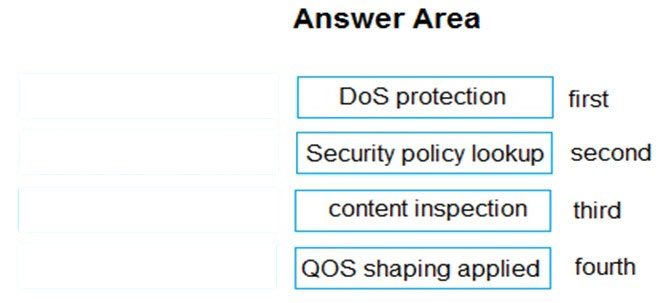
DRAG DROP - Place the steps in the correct packet-processing order of operations. Select and Place:
To use Active Directory to authenticate administrators, which server profile is required in the authentication profile?
A. domain controller
B. TACACS+
C. LDAP
D. RADIUS
An administrator wants to create a NAT policy to allow multiple source IP addresses to be translated to the same public IP address. What is the most appropriate NAT policy to achieve this?
A. Static IP
B. Destination
C. Dynamic IP and Port
D. Dynamic IP
An administrator has configured a Security policy where the matching condition includes a single application, and the action is drop. If the application's default deny action is reset-both, what action does the firewall take?
A. It silently drops the traffic.
B. It silently drops the traffic and sends an ICMP unreachable code.
C. It sends a TCP reset to the server-side device.
D. It sends a TCP reset to the client-side and server-side devices.
Which DNS Query action is recommended for traffic that is allowed by Security policy and matches Palo Alto Networks Content DNS Signatures?
A. block
B. sinkhole
C. allow
D. alert
Which two matching criteria are used when creating a Security policy involving NAT? (Choose two.)
A. Pre-NAT address
B. Post-NAT address
C. Pre-NAT zone
D. Post-NAT zone
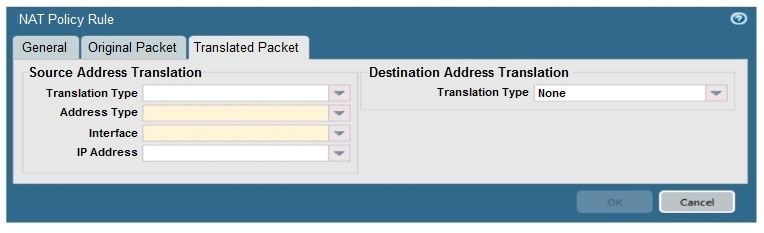
When creating a Source NAT policy, which entry in the Translated Packet tab will display the options Dynamic IP and Port, Dynamic, Static IP, and None?
A. Translation Type
B. Interface
C. Address Type
D. IP Address
The PowerBall Lottery has reached a high payout amount and a company has decided to help employee morale by allowing employees to check the number, but doesn't want to unblock the gambling URL category. Which two methods will allow the employees to get to the PowerBall Lottery site without the company unlocking the gambling URL category? (Choose two.)
A. Add all the URLs from the gambling category except powerball.com to the block list and then set the action for the gambling category to allow.
B. Manually remove powerball.com from the gambling URL category.
C. Add *.powerball.com to the allow list
D. Create a custom URL category called PowerBall and add *.powerball.com to the category and set the action to allow.
Ethernet 2/1 has an IP Address of 10.0 1 2 in Zone ‘trust’ (LAN). If both interfaces are connected to the same virtual router, which IP address information will an administrator need to enter in the Destination field to access the internet?
A. 0.0.0.0
B. 10.0.2.1/32
C. 10.0.1.254/32
D. 0.0.0.0/0
According to best practices, how frequently should WildFire updates he made to perimeter firewalls?
A. every 10 minutes
B. every minute
C. every 5 minutes
D. in real time
What are three Palo Alto Networks best practices when implementing the DNS Security Service? (Choose three.)
A. Configure a URL Filtering profile
B. Train your staff to be security aware.
C. Plan for mobile-employee risk.
D. Rely on a DNS resolver.
E. Implement a threat intel program.
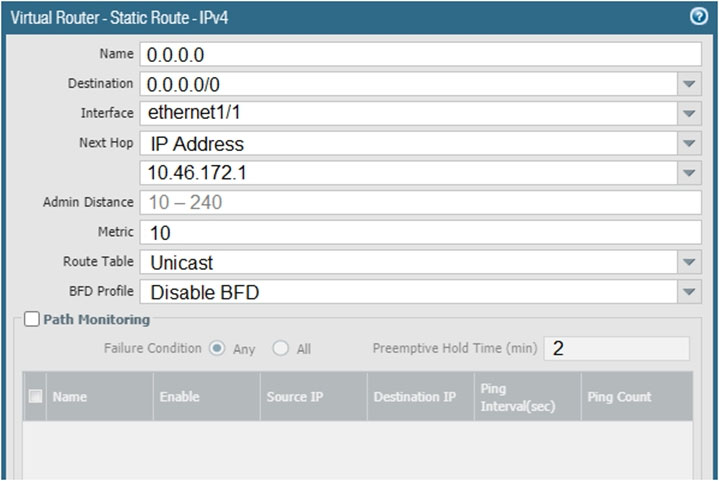
Given the screenshot, what two types of route is the administrator configuring? (Choose two.)
A. BGP
B. static route
C. default route
D. OSPF
What are two valid selections within a Vulnerability Protection profile? (Choose two.)
A. deny
B. drop
C. default
D. sinkhole
In which two Security Profiles can an action equal to the block IP feature be configured? (Choose two.)
A. Antivirus
B. URL Filtering
C. Vulnerability Protection
D. Anti-spyware
A coworker found a USB labeled "confidential in the parking lot. They inserted the drive and it infected their corporate laptop with unknown malware The malware caused the laptop to begin infiltrating corporate data. Which Security Profile feature could have been used to detect the malware on the laptop?
A. DNS Sinkhole
B. WildFire Analysis
C. Antivirus
D. DoS Protection
When is an event displayed under threat logs?
A. When traffic matches a corresponding Security Profile
B. When traffic matches any Security policy
C. Every time a session is blocked
D. Every time the firewall drops a connection
You receive notification about new malware that infects hosts through malicious files transferred by FTP. Which Security profile detects and protects your internal networks from this threat after you update your firewall’s threat signature database?
A. Data Filtering profile applied to outbound Security policy rules.
B. Vulnerability Protection profile applied to outbound Security policy rules.
C. URL Filtering profile applied to inbound Security policy rules.
D. Antivirus profile applied to inbound Security policy rules.
Where can you apply URL Filtering policy in a Security policy rule?
A. Within the applications selection
B. Within a destination address
C. Within a service type
D. Within the actions tab
Which type of address object is `10.5.1.1/0.127.248.2`?
A. IP netmask
B. IP subnet
C. IP wildcard mask
D. IP range
Which tab would an administrator click to create an address object?
A. Objects
B. Monitor
C. Device
D. Policies
Which operations are allowed when working with App-ID application tags?
A. Predefined tags may be deleted.
B. Predefined tags may be augmented by custom tags.
C. Predefined tags may be modified.
D. Predefined tags may be updated by WildFire dynamic updates.
Which built-in IP address EDL would be useful for preventing traffic from IP addresses that are verified as unsafe based on WildFire analysis, Unit 42 research, and data gathered from telemetry?
A. Palo Alto Networks High-Risk IP Addresses
B. Palo Alto Networks Known Malicious IP Addresses
C. Palo Alto Networks C&C IP Addresses
D. Palo Alto Networks Bulletproof IP Addresses
At which point in the App-ID update process can you determine if an existing policy rule is affected by an App-ID update?
A. after clicking Check Now in the Dynamic Update window
B. after committing the firewall configuration
C. after installing the update
D. after downloading the update
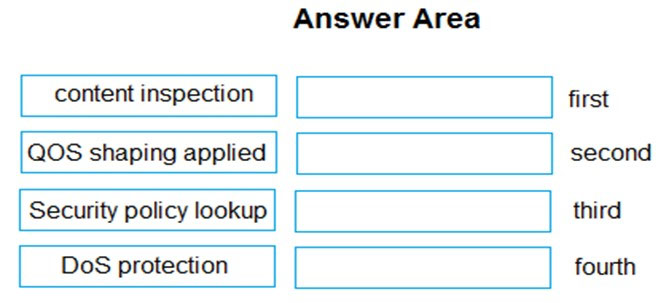
DRAG DROP - Place the following steps in the packet processing order of operations from first to last. Select and Place:
Prior to a maintenance-window activity, the administrator would like to make a backup of only the running configuration to an external location. What command in Device > Setup > Operations would provide the most operationally efficient way to achieve this outcome?
A. export named configuration snapshot
B. save named configuration snapshot
C. export device state
D. save candidate config
Which statement is true regarding NAT rules?
A. Translation of the IP address and port occurs before security processing.
B. Firewall supports NAT on Layer 3 interfaces only.
C. Static NAT rules have precedence over other forms of NAT.
D. NAT rules are processed in order from top to bottom.
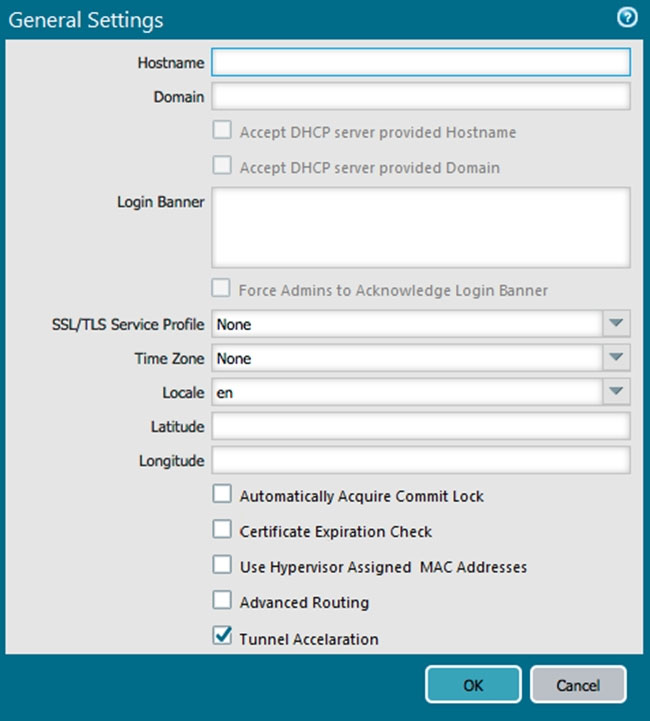
Based on the graphic, what is the purpose of the SSL/TLS Service profile configuration option?
A. It defines the SSL/TLS encryption strength used to protect the management interface.
B. It defines the CA certificate used to verify the client’s browser.
C. It defines the certificate to send to the client’s browser from the management interface.
D. It defines the firewall’s global SSL/TLS timeout values.
All users from the internal zone must be allowed only HTTP access to a server in the DMZ zone. Complete the empty field in the Security policy using an application object to permit only this type of access. Source Zone: Internal - Destination Zone: DMZ Zone - Application: __________ Service: application-default - Action: allow
A. Application = “any”
B. Application = “web-browsing”
C. Application = “ssl”
D. Application = “http”
A Security Profile can block or allow traffic at which point?
A. on either the data plane or the management plane
B. after it is matched to a Security policy rule that allows or blocks traffic
C. after it is matched to a Security policy rule that allows traffic
D. before it is matched to a Security policy rule
Which Security Profile can provide protection against ICMP floods, based on individual combinations of a packet's source and destination IP addresses?
A. DoS protection
B. URL filtering
C. packet buffering
D. anti-spyware
Actions can be set for which two items in a URL filtering security profile? (Choose two.)
A. Block List
B. Custom URL Categories
C. PAN-DB URL Categories
D. Allow List
Selecting the option to revert firewall changes will replace what settings?
A. the candidate configuration with settings from the running configuration
B. dynamic update scheduler settings
C. the running configuration with settings from the candidate configuration
D. the device state with settings from another configuration
An administrator is trying to implement an exception to an external dynamic list manually. Some entries are shown underlined in red. What would cause this error?
A. Entries contain symbols.
B. Entries are wildcards.
C. Entries contain regular expressions.
D. Entries are duplicated.
Which license is required to use the Palo Alto Networks built-in IP address EDLs?
A. DNS Security
B. Threat Prevention
C. WildFire
D. SD-Wan
The CFO found a USB drive in the parking lot and decide to plug it into their corporate laptop. The USB drive had malware on it that loaded onto their computer and then contacted a known command and control (CnC) server, which ordered the infected machine to begin Exfiltrating data from the laptop. Which security profile feature could have been used to prevent the communication with the CnC server?
A. Create an anti-spyware profile and enable DNS Sinkhole
B. Create an antivirus profile and enable DNS Sinkhole
C. Create a URL filtering profile and block the DNS Sinkhole category
D. Create a security policy and enable DNS Sinkhole
Refer to the exhibit. A web server in the DMZ is being mapped to a public address through DNAT.Which Security policy rule will allow traffic to flow to the web server?
A. Untrust (any) to DMZ (10.1.1.100), web browsing – Allow
B. Untrust (any) to Untrust (1.1.1.100), web browsing – Allow
C. Untrust (any) to Untrust (10.1.1.100), web browsing – Allow
D. Untrust (any) to DMZ (1.1.1.100), web browsing – Allow
If a universal security rule was created for source zones A & B and destination zones A & B, to which traffic would the rule apply?
A. Some traffic between A & B
B. Some traffic within A
C. All traffic within zones A & B
D. Some traffic within B
An administrator would like to follow the best-practice approach to log the traffic that traverses the firewall. What action should they take?
A. Enable both Log at Session Start and Log at Session End.
B. Enable Log at Session End.
C. Enable Log at Session Start.
D. Disable all logging options.
Which information is included in device state other than the local configuration?
A. uncommitted changes
B. audit logs to provide information of administrative account changes
C. system logs to provide information of PAN-OS changes
D. device group and template settings pushed from Panorama
Where within the firewall GUI can all existing tags be viewed?
A. Policies > Tags
B. Network > Tags
C. Objects > Tags
D. Monitor > Tags
An administrator is troubleshooting an issue with traffic that matches the interzone-default rule, which is set to default configuration. What should the administrator do?
A. Change the logging action on the rule
B. Tune your Traffic Log filter to include the dates
C. Refresh the Traffic Log
D. Review the System Log
Which order of steps is the correct way to create a static route?
A. 1) Enter the route and netmask2) Specify the outgoing interface for packets to use to go to the next hop3) Enter the IP address for the specific next hop4) Add an IPv4 or IPv6 route by name
B. 1) Enter the IP address for the specific next hop2) Add an IPv4 or IPv6 route by name3) Enter the route and netmask4) Specify the outgoing interface for packets to use to go to the next hop
C. 1) Enter the route and netmask2) Enter the IP address for the specific next hop3) Specify the outgoing interface for packets to use to go to the next hop4) Add an IPv4 or IPv6 route by name
D. 1) Enter the IP address for the specific next hop2) Enter the route and netmask3) Add an IPv4 or IPv6 route by name4) Specify the outgoing interface for packets to use to go to the next hop
Which statement is true regarding a Best Practice Assessment?
A. It runs only on firewalls.
B. It shows how current configuration compares to Palo Alto Networks recommendations.
C. When guided by an authorized sales engineer, it helps determine the areas of greatest risk where you should focus prevention activities.
D. It provides a set of questionnaires that help uncover security risk prevention gaps across all areas of network and security architecture.
An administrator is troubleshooting an issue with traffic that matches the intrazone-default rule, which is set to default configuration. What should the administrator do?
A. change the logging action on the rule
B. review the System Log
C. refresh the Traffic Log
D. tune your Traffic Log filter to include the dates
A server-admin in the USERS-zone requires SSH-access to all possible servers in all current and future Public Cloud environments. All other required connections have already been enabled between the USERS- and the OUTSIDE-zone. What configuration-changes should the Firewall-admin make?
A. Create a custom-service-object called SERVICE-SSH for destination-port-TCP-22. Create a security-rule between zone USERS and OUTSIDE to allow traffic from any source IP-address to any destination IP-address for SERVICE-SSH
B. Create a security-rule that allows traffic from zone USERS to OUTSIDE to allow traffic from any source IP-address to any destination IP-address for application SSH
C. In addition to option a, a custom-service-object called SERVICE-SSH-RETURN that contains source-port-TCP-22 should be created. A second security-rule is required that allows traffic from zone OUTSIDE to USERS for SERVICE-SSH-RETURN for any source-IP-address to any destination-Ip-address
D. In addition to option c, an additional rule from zone OUTSIDE to USERS for application SSH from any source-IP-address to any destination-IP-address is required to allow the return-traffic from the SSH-servers to reach the server-admin
What is the minimum frequency for which you can configure the firewall to check for new WildFire antivirus signatures?
A. every 30 minutes
B. every 5 minutes
C. every 24 hours
D. every 1 minute
What are the requirements for using Palo Alto Networks EDL Hosting Service?
A. an additional paid subscription
B. any supported Palo Alto Networks firewall or Prisma Access firewall
C. a firewall device running with a minimum version of PAN-OS 10.1
D. an additional subscription free of charge
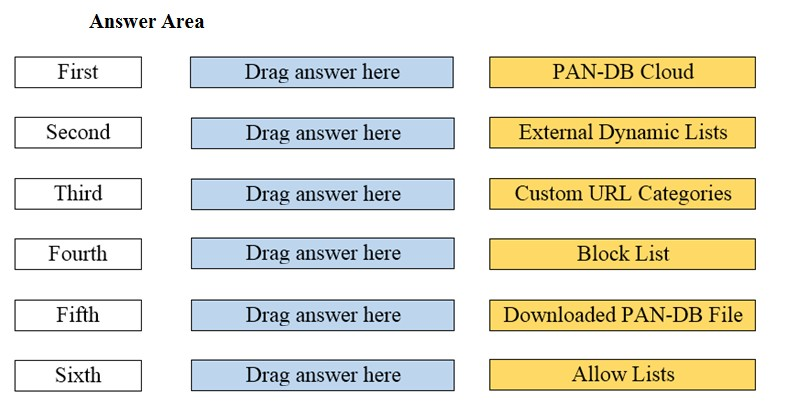
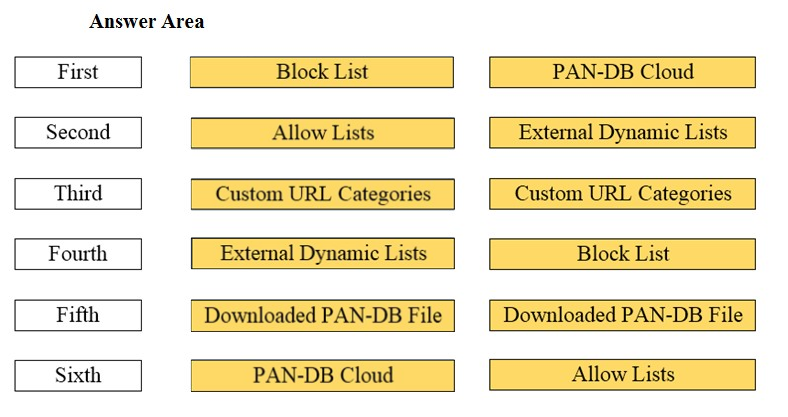
DRAG DROP - Arrange the correct order that the URL classifications are processed within the system. Select and Place:
Free Access Full PCNSA Practice Exam Free
Looking for additional practice? Click here to access a full set of PCNSA practice exam free questions and continue building your skills across all exam domains.
Our question sets are updated regularly to ensure they stay aligned with the latest exam objectives—so be sure to visit often!
Good luck with your PCNSA certification journey!