PCCET Practice Exam Free – 50 Questions to Simulate the Real Exam
Are you getting ready for the PCCET certification? Take your preparation to the next level with our PCCET Practice Exam Free – a carefully designed set of 50 realistic exam-style questions to help you evaluate your knowledge and boost your confidence.
Using a PCCET practice exam free is one of the best ways to:
- Experience the format and difficulty of the real exam
- Identify your strengths and focus on weak areas
- Improve your test-taking speed and accuracy
Below, you will find 50 realistic PCCET practice exam free questions covering key exam topics. Each question reflects the structure and challenge of the actual exam.
Which core NGFW subscription service defends networks from advanced persistent threats (APTs)?
A. WildFire
B. DNS Security
C. Threat Prevention
D. URL Filtering
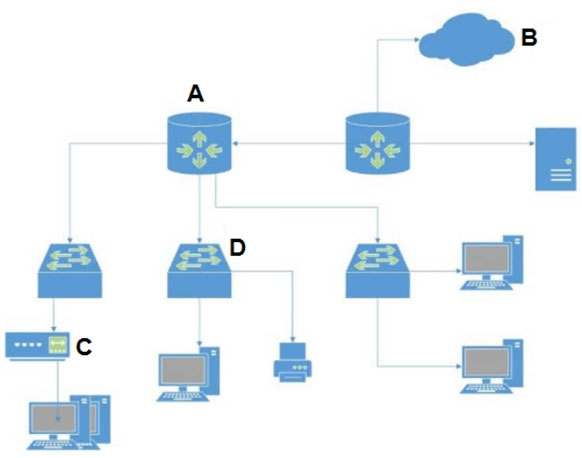
In the attached network diagram, which device is the switch?
A. A
B. B
C. C
D. D
Which three terms are functions of security operations? (Choose three.)
A. Segment
B. Identify
C. Mitigate
D. Investigate
E. Report
Which network device breaks networks into separate broadcast domains?
A. Hub
B. Layer 2 switch
C. Router
D. Wireless access point
Which option is an example of a North-South traffic flow?
A. Lateral movement within a cloud or data center
B. An internal three-tier application
C. Client-server interactions that cross the edge perimeter
D. Traffic between an internal server and internal user
Which pillar of Prisma Cloud application security addresses ensuring that your cloud resources and SaaS applications are correctly configured?
A. visibility, governance, and compliance
B. network protection
C. dynamic computing
D. compute security
Which type of organization benefits most from the features SD-WAN offers?
A. Businesses with one office and many remote employees
B. Small businesses in a single location
C. Large businesses with a single location
D. Businesses with several branches
What is the key to `taking down` a botnet?
A. prevent bots from communicating with the C2
B. install openvas software on endpoints
C. use LDAP as a directory service
D. block Docker engine software on endpoints
During the OSI layer 3 step of the encapsulation process, what is the Protocol Data Unit (PDU) called when the IP stack adds source (sender) and destination (receiver) IP addresses?
A. Frame
B. Segment
C. Packet
D. Data
What is one of the elements of SecOps?
A. Zero Trust model
B. Interfaces
C. Infrastructure
D. Finances
Which type of malware takes advantage of a vulnerability on an endpoint or server?
A. technique
B. patch
C. vulnerability
D. exploit
What is used to orchestrate, coordinate, and control clusters of containers?
A. Kubernetes
B. Prisma Saas
C. Docker
D. CN-Series
In an IDS/IPS, which type of alarm occurs when legitimate traffic is improperly identified as malicious traffic?
A. False-positive
B. True-negative
C. False-negative
D. True-positive
Which TCP/IP sub-protocol operates at the Layer7 of the OSI model?
A. UDP
B. MAC
C. SNMP
D. NFS
DRAG DROP - Match the level of security required in the Shared Security Model by customer with the cloud services used.
Which pillar of Prisma Cloud application security does vulnerability management fall under?
A. dynamic computing
B. identity security
C. compute security
D. network protection
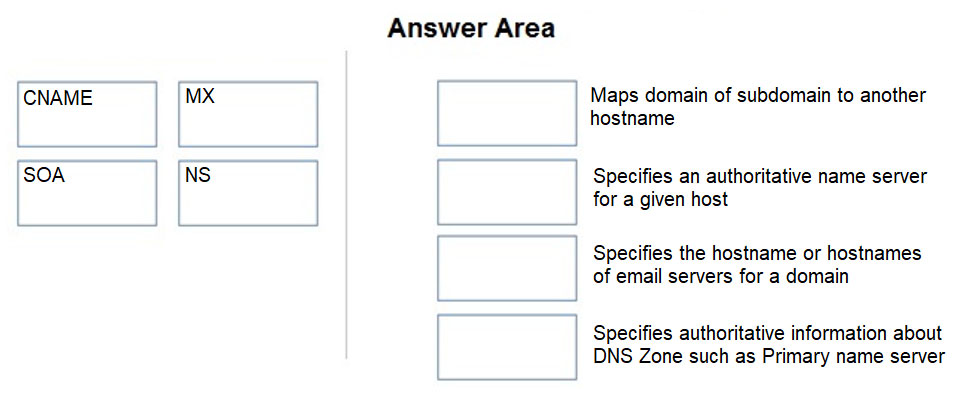
DRAG DROP - Match the DNS record type to its function within DNS. Select and Place:
In which phase of the cyberattack lifecycle do attackers establish encrypted communication channels back to servers across the internet so that they can modify their attack objectives and methods?
A. exploitation
B. actions on the objective
C. command and control
D. installation
Which technique changes protocols at random during a session?
A. use of non-standard ports
B. port hopping
C. hiding within SSL encryption
D. tunneling within commonly used services
Which product from Palo Alto Networks extends the Security Operating Platform with the global threat intelligence and attack context needed to accelerate analysis, forensics, and hunting workflows?
A. Global Protect
B. WildFire
C. AutoFocus
D. STIX
Which endpoint security solution protects against malicious software designed to invade a device and collect user data?
A. Anti-spyware
B. Anti-virus
C. Sandboxing
D. Software-defined wide-area networks (SD-WAN)
Which IoT connectivity technology is provided by satellites?
A. 4G/LTE
B. VLF
C. L-band
D. 2G/2.5G
A doctor receives an email about her upcoming holiday in France. When she clicks the URL website link in the email, the connection is blocked by her office firewall because it's a known malware website. Which type of attack includes a link to a malware website in an email?
A. whaling
B. phishing
C. pharming
D. spam
Which product from Palo Alto Networks enables organizations to prevent successful cyberattacks as well as simplify and strengthen security processes?
A. Expedition
B. AutoFocus
C. MineMeld
D. Cortex XDR
What differentiates Docker from a bare metal hypervisor?
A. Docker lets the user boot up one or more instances of an operating system on the same host whereas hypervisors do not
B. Docker uses more resources than a bare metal hypervisor
C. Docker is more efficient at allocating resources for legacy systems
D. Docker uses OS-level virtualization, whereas a bare metal hypervisor runs independently from the OS
Which Palo Alto Networks subscription dynamically discovers and maintains a real-time inventory of devices on your network?
A. DNS Security
B. Threat Prevention
C. IoT Security
D. Wildfire
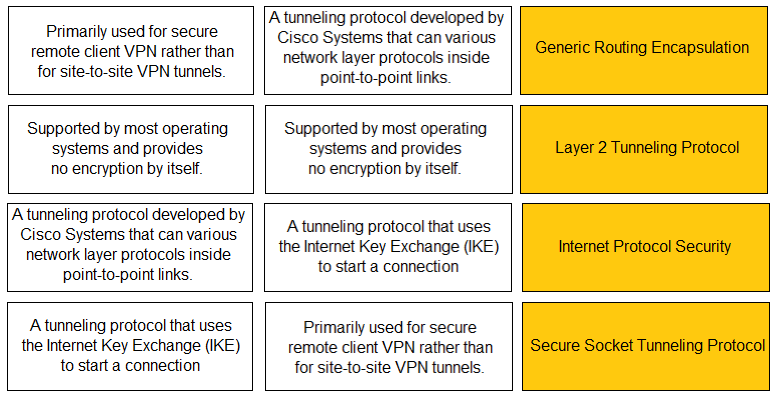
DRAG DROP - Match the description with the VPN technology. Select and Place:
How can local systems eliminate vulnerabilities?
A. Patch systems and software effectively and continuously.
B. Create preventative memory-corruption techniques.
C. Perform an attack on local systems.
D. Test and deploy patches on a focused set of systems.
What is a characteristic of the National Institute Standards and Technology (NIST) defined cloud computing model?
A. requires the use of only one cloud service provider
B. enables on-demand network services
C. requires the use of two or more cloud service providers
D. defines any network service
Which type of SaaS application offers no business benefits and creates risk for an organization?
A. Tolerated
B. Sanctioned
C. Unsanctioned
D. Prohibited
What are two key characteristics of a Type 1 hypervisor? (Choose two.)
A. is hardened against cyber attacks
B. runs without any vulnerability issues
C. runs within an operating system
D. allows multiple, virtual (or guest) operating systems to run concurrently on a single physical host computer
Which subnet does the host 192.168.19.36/27 belong?
A. 192.168.19.0
B. 192.168.19.16
C. 192.168.19.64
D. 192.168.19.32
SecOps consists of interfaces, visibility, technology, and which other three elements? (Choose three.)
A. People
B. Accessibility
C. Processes
D. Understanding
E. Business
Which type of IDS/IPS uses a baseline of normal network activity to identify unusual patterns or levels of network activity that may be indicative of an intrusion attempt?
A. Knowledge-based
B. Signature-based
C. Behavior-based
D. Database-based
Which analysis detonates previously unknown submissions in a custom-built, evasion-resistant virtual environment to determine real-world effects and behavior?
A. Dynamic
B. Pre-exploit protection
C. Bare-metal
D. Static
In which situation would a dynamic routing protocol be the quickest way to configure routes on a router?
A. the network is large
B. the network is small
C. the network has low bandwidth requirements
D. the network needs backup routes
In which step of the cyber-attack lifecycle do hackers embed intruder code within seemingly innocuous files?
A. weaponization
B. reconnaissance
C. exploitation
D. delivery
You have been invited to a public cloud design and architecture session to help deliver secure east west flows and secure Kubernetes workloads. What deployment options do you have available? (Choose two.)
A. PA-Series
B. VM-Series
C. Panorama
D. CN-Series
Anthem server breaches disclosed Personally Identifiable Information (PII) from a number of its servers. The infiltration by hackers was attributed to which type of vulnerability?
A. an intranet-accessed contractor’s system that was compromised
B. exploitation of an unpatched security vulnerability
C. access by using a third-party vendor’s password
D. a phishing scheme that captured a database administrator’s password
Which option describes the `selective network security virtualization` phase of incrementally transforming data centers?
A. during the selective network security virtualization phase, all intra-host communication paths are strictly controlled
B. during the selective network security virtualization phase, all intra-host traffic is forwarded to a Web proxy server
C. during the selective network security virtualization phase, all intra-host traffic is encapsulated and encrypted using the IPSEC protocol
D. during the selective network security virtualization phase, all intra-host traffic is load balanced
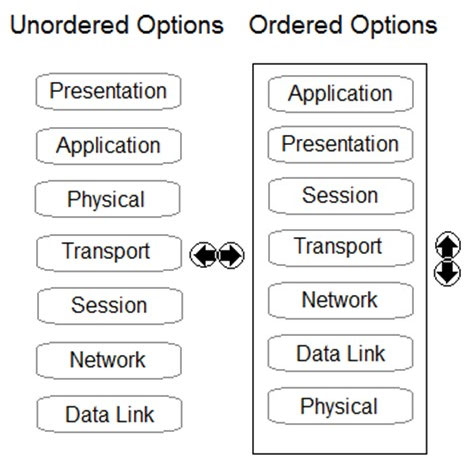
DRAG DROP - Order the OSI model with Layer7 at the top and Layer1 at the bottom. Select and Place:
Which organizational function is responsible for security automation and eventual vetting of the solution to help ensure consistency through machine-driven responses to security issues?
A. NetOps
B. SecOps
C. SecDevOps
D. DevOps
Which statement describes DevOps?
A. DevOps is its own separate team
B. DevOps is a set of tools that assists the Development and Operations teams throughout the software delivery process
C. DevOps is a combination of the Development and Operations teams
D. DevOps is a culture that unites the Development and Operations teams throughout the software delivery process
What is an example of a Web 3.0 application?
A. Github
B. Bitcoin
C. Pinterest
D. Facebook
A native hypervisor runs:
A. with extreme demands on network throughput
B. only on certain platforms
C. within an operating system’s environment
D. directly on the host computer’s hardware
What is the primary security focus after consolidating data center hypervisor hosts within trust levels?
A. control and protect inter-host traffic using routers configured to use the Border Gateway Protocol (BGP) dynamic routing protocol
B. control and protect inter-host traffic by exporting all your traffic logs to a sysvol log server using the User Datagram Protocol (UDP)
C. control and protect inter-host traffic by using IPv4 addressing
D. control and protect inter-host traffic using physical network security appliances
Which characteristic of serverless computing enables developers to quickly deploy application code?
A. Uploading cloud service autoscaling services to deploy more virtual machines to run their application code based on user demand
B. Uploading the application code itself, without having to provision a full container image or any OS virtual machine components
C. Using cloud service spot pricing to reduce the cost of using virtual machines to run their application code
D. Using Container as a Service (CaaS) to deploy application containers to run their code.
Which Palo Alto Networks service is a scalable, cloud-based log repository that stores context-rich logs generated by Palo Alto Networks security products?
A. Cortex XDR
B. Cortex XSOAR
C. Cortex Data Lake
D. Cortex Xpanse
In SecOps, what are two of the components included in the identify stage? (Choose two.)
A. Initial Research
B. Change Control
C. Content Engineering
D. Breach Response
Which term describes data packets that move in and out of the virtualized environment from the host network or a corresponding traditional data center?
A. North-South traffic
B. Intrazone traffic
C. East-West traffic
D. Interzone traffic
Free Access Full PCCET Practice Exam Free
Looking for additional practice? Click here to access a full set of PCCET practice exam free questions and continue building your skills across all exam domains.
Our question sets are updated regularly to ensure they stay aligned with the latest exam objectives—so be sure to visit often!
Good luck with your PCCET certification journey!