MS-500 Practice Exam Free – 50 Questions to Simulate the Real Exam
Are you getting ready for the MS-500 certification? Take your preparation to the next level with our MS-500 Practice Exam Free – a carefully designed set of 50 realistic exam-style questions to help you evaluate your knowledge and boost your confidence.
Using a MS-500 practice exam free is one of the best ways to:
- Experience the format and difficulty of the real exam
- Identify your strengths and focus on weak areas
- Improve your test-taking speed and accuracy
Below, you will find 50 realistic MS-500 practice exam free questions covering key exam topics. Each question reflects the structure and challenge of the actual exam.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have an on-premises Active Directory domain named contoso.com. You install and run Azure AD Connect on a server named Server1 that runs Windows Server. You need to view Azure AD Connect events. Solution: You use the System event log on Server1. Does that meet the goal?
A. Yes
B. No
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.You enable the authentication methods registration campaign and configure the Microsoft Authenticator method for Group1. Which users will be prompted to configure authentication during sign in?
A. User1 only
B. User2 only
C. User2 and User3 only
D. User1 and User2 only
E. User2 and User3 only
F. User1, User2, and User3 only
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft 365 subscription that contains the users shown in the following table.You need to ensure that User1, User2, and User3 can use self-service password reset (SSPR). The solution must not affect User4. Solution: You enable SSPR for Group2. Does that meet the goal?
A. Yes
B. No
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. Your on-premises network contains a server that runs Windows Server 2019, computers that run Windows 10, macOS, or Linux, and a firewall that utilizes syslog. You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Endpoint. All the computers are onboarded to Microsoft Defender for Endpoint. You are implementing Microsoft Defender for Cloud Apps. You need to discover which cloud apps are accessed from the computers. Solution: You install a Microsoft Defender for Identity sensor on the server. Does this meet the goal?
A. Yes
B. No
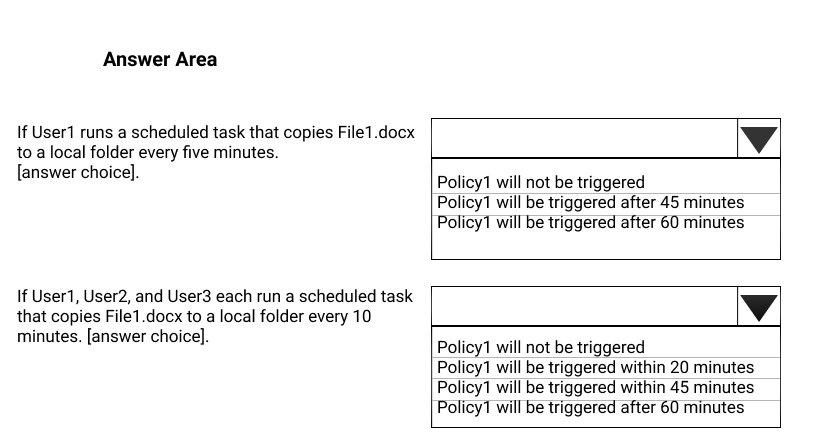
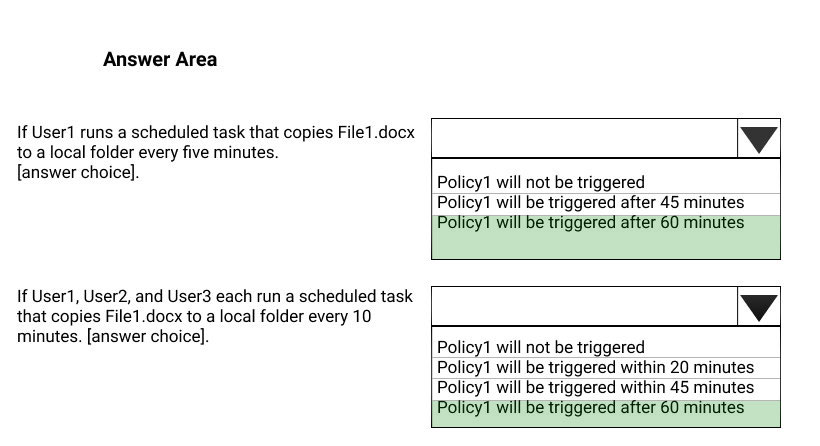
HOTSPOT - You have a Microsoft 365 subscription that includes three users named User1, User2, and User3. A file named File1.docx is stored in Microsoft OneDrive. An automated process updates File1.docx every minute. You create an alert policy named Policy1 as shown in the following exhibit.Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point. Hot Area:
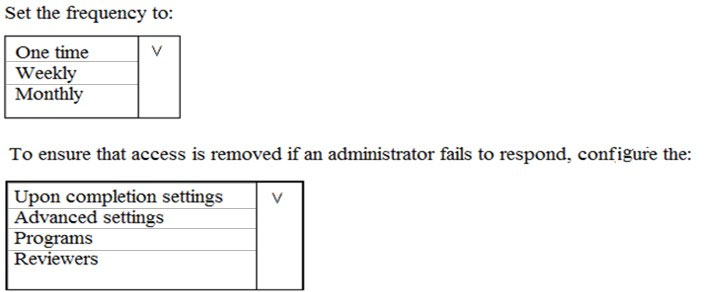
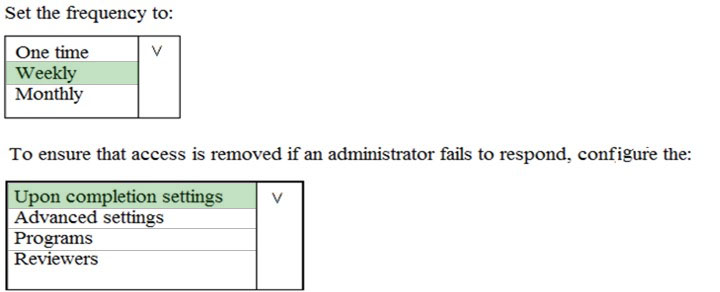
HOTSPOT - You plan to configure an access review to meet the security requirements for the workload administrators. You create an access review policy and specify the scope and a group. Which other settings should you configure? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
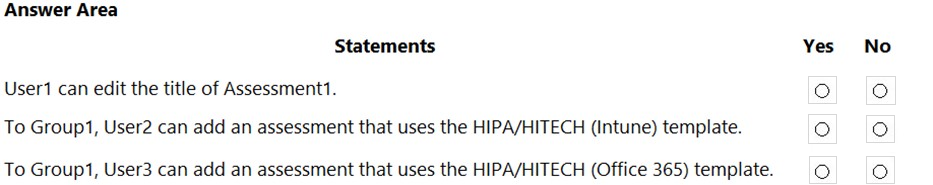
HOTSPOT - You have a Microsoft 365 E5 subscription that contains a security group named Group1 and the users shown in the following table.You assign the Compliance Manager roles to the users as shown in the following table.
You add two assessments to Compliance Manager as shown in the following exhibit.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 E5 subscription. A security manager receives an email message every time a data loss prevention (DLP) policy match occurs. You need to limit alert notifications to actionable DLP events. What should you do?
A. From the Microsoft 365 Compliance center, modify the Policy Tips settings of a DLP policy.
B. From the Cloud App Security portal, apply a filter to the alerts.
C. From the Microsoft 365 Compliance center, modify the User overrides settings of a DLP policy.
D. From the Microsoft 365 Compliance center, modify the matched activities threshold of an alert policy.
You have a Microsoft 365 E5 subscription. You need to use Attack simulation training to launch a credential harvest simulation. For which Microsoft 365 workloads can you create a payload?
A. Microsoft Exchange Online only
B. Microsoft Teams, Exchange Online, SharePoint Online, and OneDrive
C. Microsoft Teams and Exchange Online only
D. Microsoft SharePoint Online and OneDrive only
You have a Microsoft 365 E5 subscription that contains a user named User1. You need to ensure that User1 can use the Microsoft 365 compliance center to search audit logs and identify which users were added to Microsoft 365 role groups. The solution must use the principle of least privilege. To which role group should you add User1?
A. View-Only Organization Management
B. Security Reader
C. Organization Management
D. Compliance Management
You have a Microsoft 365 E5 subscription and a Microsoft Sentinel workspace named Sentinel1. You need to launch the Guided Investigation – Process Alerts notebook in Sentinel1. What should you create first?
A. an Azure logic app
B. a Log Analytics workspace
C. an Azure Machine Learning workspace
D. a Kusto query
You have a Microsoft 365 E5 subscription. You implement Microsoft Defender for Office 365 safe attachments policies for all users. User reports that email messages containing attachments take longer than expected to be received. You need to reduce the amount of time it takes to receive email messages that contain attachments. The solution must ensure that all attachments are scanned for malware. Attachments that have malware must be blocked. What should you do?
A. Set the action to Block
B. Add an exception
C. Add a condition
D. Set the action to Dynamic Delivery
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have an on-premises Active Directory domain named contoso.com. You install and run Azure AD Connect on a server named Server1 that runs Windows Server. You need to view Azure AD Connect events. Solution: You use the Application event log on Server1. Does that meet the goal?
A. Yes
B. No
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft 365 tenant. You create a label named CompanyConfidential in Microsoft Azure Information Protection. You add CompanyConfidential to a global policy. A user protects an email message by using CompanyConfidential and sends the label to several external recipients. The external recipients report that they cannot open the email message. You need to ensure that the external recipients can open protected email messages sent to them. You modify the encryption settings of the label. Does that meet the goal?
A. Yes
B. No
An administrator plans to deploy several Azure Advanced Threat Protection (ATP) sensors. You need to provide the administrator with the Azure information required to deploy the sensors. What information should you provide?
A. an Azure Active Directory Authentication Library (ADAL) token
B. the public key
C. the access key
D. the URL of the Azure ATP admin center
You have a Microsoft 365 subscription that includes a user named User1. You have a conditional access policy that applies to Microsoft Exchange Online. The conditional access policy is configured to use Conditional Access App Control. You need to create a Microsoft Cloud App Security policy that blocks User1 from printing from Exchange Online. Which type of Cloud App Security policy should you create?
A. an app permission policy
B. an activity policy
C. a Cloud Discovery anomaly detection policy
D. a session policy
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.Azure AD Identity Protection detects that the account of User1 is at risk and generates an alert. How many users will receive the alert?
A. 1
B. 2
C. 3
D. 4
E. 5
HOTSPOT - You have a Microsoft 365 E5 subscription that contains four users named User1, User2, User3, and User4. In Azure AD Identity Protection, you configure User4 as the only recipient of Users at risk detected alerts. You set Alert on user risk level at or above to Low. Azure AD Identity Protection detects the risk events shown in the following table.How many alerts will User4 receive that include User1, and how many alerts will User4 receive that include User2 and User3? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table.You discover that several security alerts are visible from the Microsoft Defender for Identity portal. You need to identify which users in contoso.com can close the security alerts. Which users should you identify?
A. User4 only
B. User1 and User2 only
C. User3 and User4 only
D. User1 and User3 only
E. User1 only
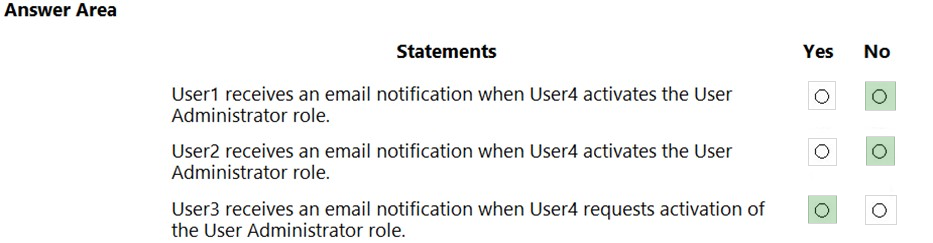
HOTSPOT - You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table.The User Administrator role is configured in Azure AD Privileged Identity Management (PIM) as shown in the following exhibit.
You make User4 eligible for the User Administrator role. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
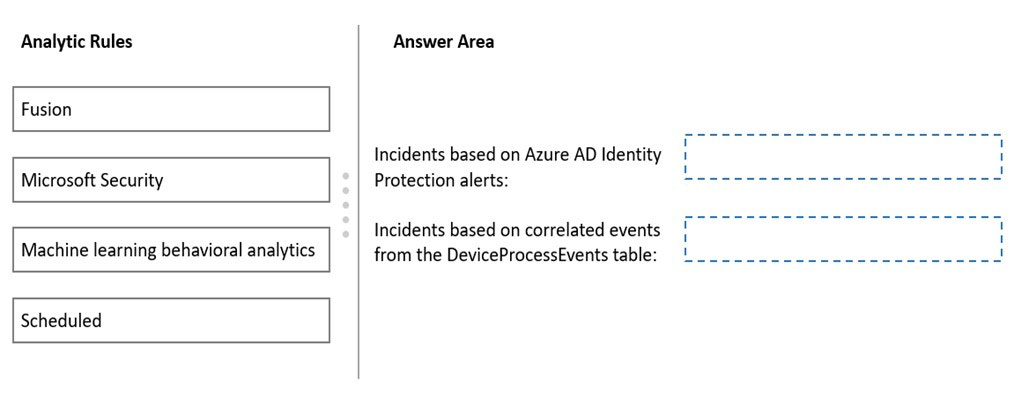
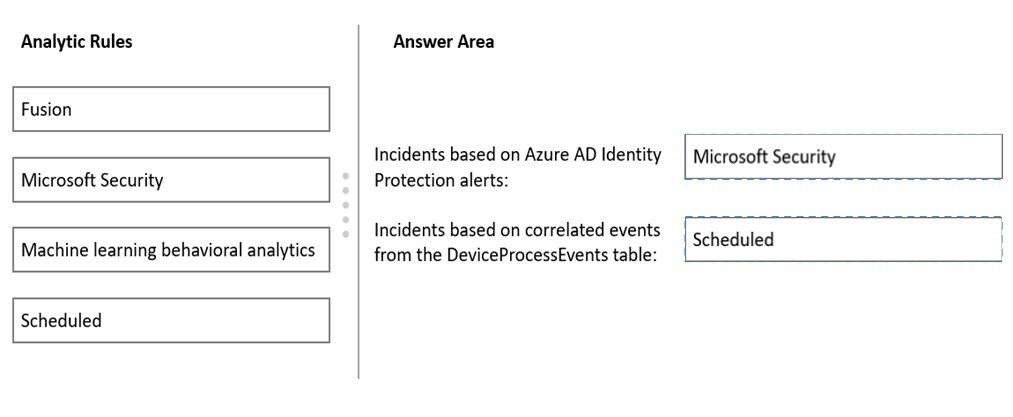
DRAG DROP - You have a Microsoft 365 E5 subscription. You plan to implement Azure Sentinel to create incidents based on: ✑ Azure Active Directory (Azure AD) Identity Protection alerts ✑ Correlated events from the DeviceProcessEvents table Which analytic rule types should you use for each incident type? To answer, drag the appropriate rule types to the correct incident types. Each rule type may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point. Select and Place:
You have a Microsoft 365 subscription that contains the users shown in the following table.You need to prevent users in the finance department from sharing files with users in the research department. Which type of policy should you configure?
A. information barrier
B. insider risk management
C. Conditional Access
D. communication compliance
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft 365 subscription that contains 1,000 user mailboxes. An administrator named Admin1 must be able to search for the name of a competing company in the mailbox of a user named User5. You need to ensure that Admin1 can search the mailbox of User5 successfully. The solution must prevent Admin1 from sending email messages as User5. Solution: You assign the eDiscovery Manager role to Admin1, and then create an eDiscovery case. Does this meet the goal?
A. Yes
B. No
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft 365 subscription that contains the users shown in the following table.You need to ensure that User1, User2, and User3 can use self-service password reset (SSPR). The solution must not affect User4. Solution: You enable SSPR for Group1. Does that meet the goal?
A. Yes
B. No
Your company has a Microsoft 365 subscription. The company does not permit users to enroll personal devices in mobile device management (MDM). Users in the sales department have personal iOS devices. You need to ensure that the sales department users can use the Microsoft Power BI app from iOS devices to access the Power BI data in your tenant. The users must be prevented from backing up the app's data to iCloud. What should you create?
A. a conditional access policy in Microsoft Azure Active Directory (Azure AD) that has a device state condition
B. an app protection policy in Microsoft Endpoint Manager
C. a conditional access policy in Microsoft Azure Active Directory (Azure AD) that has a client apps condition
D. a device compliance policy in Microsoft Endpoint Manager
You need to recommend a solution that meets the technical and security requirements for sharing data with the partners. What should you include in the recommendation? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Create an access review
B. Assign the Global administrator role to User1
C. Assign the Guest inviter role to User1
D. Modify the External collaboration settings in the Azure Active Directory admin center
HOTSPOT - You have a Microsoft SharePoint Online site named Site1 that contains the files shown in the following table.You have a data loss prevention (DLP) policy named DLP1 that has the advanced DLP rules shown in the following table.
You apply DLP1 to Site1. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription that uses a default domain name of fabrikam.com. You create a safe links policy, as shown in the following exhibit.Which URL can a user safely access from Microsoft Word Online?
A. fabrikam.phishing.fabrikam.com
B. malware.fabrikam.com
C. fabrikam.contoso.com
D. www.malware.fabrikam.com
You have a Microsoft 365 E5 subscription. You need to investigate threats to the subscription by using the Campaigns view in Microsoft Defender for Office 365. Which types of threats will appear?
A. phishing only
B. phishing and malware only
C. phishing and password attacks only
D. malware only
E. malware and password attacks only
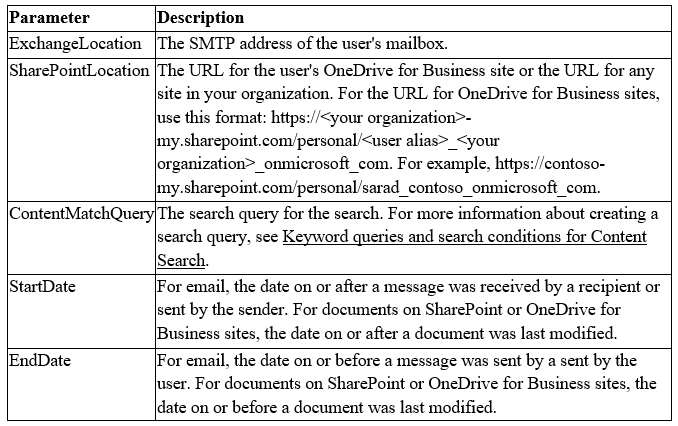
SIMULATION - You plan to create a script to automate user mailbox searches. The script will search the mailbox of a user named Allan Deyoung for messages that contain the word injunction. You need to create the search that will be included in the script. To complete this task, sign in to the Microsoft 365 admin center.
SIMULATION - You need to create an Azure Information Protection label to meet the following requirements: ✑ Content must expire after 21 days. ✑ Offline access must be allowed for 21 days only. ✑ Documents must be protected by using a cloud key. ✑ Authenticated users must be able to view content only. To complete this task, sign in to the Microsoft 365 admin center.
You have a Microsoft 365 subscription. You create a retention policy and apply the policy to Exchange Online mailboxes. You need to ensure that the retention policy tags can be assigned to mailbox items as soon as possible. What should you do?
A. From Exchange Online PowerShell, run Start-RetentionAutoTagLearning
B. From Exchange Online PowerShell, run Start-ManagedFolderAssistant
C. From the Microsoft 365 Compliance admin center, create a data loss prevention (DLP) policy
D. From the Microsoft 365 Compliance admin center, create a label policy
SIMULATION - Your company plans to merge with another company. A user named Debra Berger is an executive at your company. You need to provide Debra Berger with all the email content of a user named Alex Wilber that contains the word merger. To complete this task, sign in to the Microsoft 365 portal.
You have an Azure Active Directory (Azure AD) tenant named contoso.com and a Microsoft 365 subscription. All users in contoso.com use the Microsoft SharePoint Newsfeed. You need to ensure that all the users use the Yammer.com service. What should you do?
A. From the Yammer admin center, modify the Usage Policy settings
B. From the SharePoint admin center, modify the Enterprise Social Collaboration settings
C. From the SharePoint admin center, modify the Connected Services settings
D. From the Yammer admin center, modify the Configuration settings
You have a Microsoft 365 E5 subscription named contoso.com. You create a user named User1. You need to ensure that User1 can change the status of Microsoft Defender for Identity health alerts. The solution must use principle of the least principle. What should you do?
A. From the Microsoft 365 Defender portal, assign User1 the Security Operator role.
B. From the Microsoft 365 admin center, add User1 to the Azure ATP contoso.com Administrators group.
C. From the Microsoft 365 admin center, add User1 to the Azure ATP contoso.com Users group.
D. From the Microsoft 365 admin center, assign User1 the Hybrid Identity Administrator role.
SIMULATION - Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time. When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design. Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn't matter how you accomplish the task, if you successfully perform it, you will earn credit for that task. Labs are not timed separately, and this exam may more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided. Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab. Username and password -Use the following login credentials as needed: To enter your username, place your cursor in the Sign in box and click on the username below. To enter your password, place your cursor in the Enter password box and click on the password below. Microsoft 365 Username: admin@LODSe244001.onmicrosoft.com Microsoft 365 Password: &=Q8v@2qGzYz If the Microsoft 365 portal does not load successfully in the browser, press CTRL-K to reload the portal in a new browser tab. The following information is for technical support purposes only: Lab instance: 11032396 - You need to create a case that prevents the members of a group named Operations from deleting email messages that contain the word IPO. To complete this task, sign in to the Microsoft Office 365 admin center.
Several users in your Microsoft 365 subscription report that they received an email message without the attachment. You need to review the attachments that were removed from the messages. Which two tools can you use? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. the Exchange admin center
B. Azure Defender for Servers
C. Outlook on the web
D. the Microsoft 365 Compliance center.
E. Microsoft Defender for Identity admin center
Your network contains an on-premises Active Directory domain and a Microsoft 365 subscription. You plan to deploy a hybrid Azure Active Directory (Azure AD) tenant that has Azure AD Identity Protection risk policies enabled. You need to configure Azure AD Connect to support the planned deployment. Which Azure AD Connect authentication method should you select?
A. Federation with AD FS
B. Federation with PingFederate
C. Password Hash Synchronization
D. Pass-through authentication
You configure several Microsoft Defender for Office 365 policies in a Microsoft 365 subscription. You need to allow a user named User1 to view Defender for Office 365 reports from the Threat management dashboard. Which role provides User1 with the required role permissions?
A. Security reader
B. Information Protection administrator
C. Reports reader
D. Exchange administrator
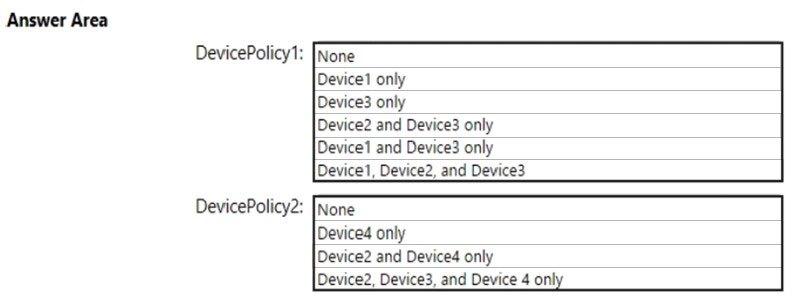
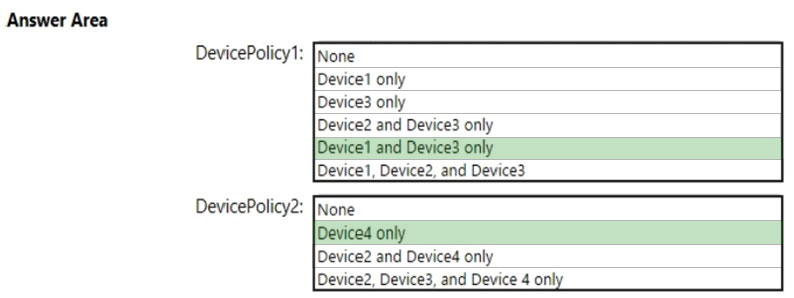
HOTSPOT - Which policies apply to which devices? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 E5 subscription. You need to ensure that users who are assigned the Exchange administrator role have time-limited permissions and must use multi-factor authentication (MFA) to request the permissions. What should you use to achieve the goal?
A. Microsoft 365 Compliance permissions
B. Microsoft Azure Active Directory (Azure AD) Privileged Identity Management
C. Microsoft Azure AD group management
D. Microsoft 365 user management
You have several Conditional Access policies that block noncompliant devices from connecting to services. You need to identify which devices are blocked by which policies. What should you use?
A. the Device compliance report in the Microsoft Endpoint Manager admin center
B. the Device compliance trends report in the Microsoft Endpoint Manager admin center
C. Activity log in the Cloud App Security portal
D. the Conditional Access Insights and Reporting workbook in the Azure Active Directory admin center
You have a Microsoft 365 E5 subscription that contains the resources shown in the following table.You have a retention label configured as shown in the following exhibit.
You apply the label to the resources. Which items can you delete?
A. Mail1 only
B. File1.docx and File2.xlsx only
C. Mail1 and File1.docx only
D. Mail1 and File2.xlsx only
E. Mail1, File1.docx, and File2.xlsx
SIMULATION - Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time. When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design. Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn't matter how you accomplish the task, if you successfully perform it, you will earn credit for that task. Labs are not timed separately, and this exam may more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided. Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab. Username and password -Use the following login credentials as needed: To enter your username, place your cursor in the Sign in box and click on the username below. To enter your password, place your cursor in the Enter password box and click on the password below. Microsoft 365 Username: admin@LODSe244001.onmicrosoft.com Microsoft 365 Password: &=Q8v@2qGzYz If the Microsoft 365 portal does not load successfully in the browser, press CTRL-K to reload the portal in a new browser tab. The following information is for technical support purposes only: Lab instance: 11032396 - You need to ensure that a user named Lee Gu can manage all the settings for Exchange Online. The solution must use the principle of least privilege. To complete this task, sign in to the Microsoft Office 365 admin center.
You have a hybrid deployment of Microsoft 365 that contains the users shown in the following table.You plan to use Microsoft 365 Attack Simulator. You need to identify the users against which you can use Attack Simulator. Which users should you identify?
A. User3 only
B. User1, User2, User3, and User4
C. User3 and User4 only
D. User1 and User3 only
You have an Azure Sentinel workspace that has an Azure Active Directory (Azure AD) connector and an Office 365 connector. From the workspace, you plan to create a scheduled query rule that will use a custom query. The rule will be used to generate alerts when inbound access to Office 365 from specific user accounts is detected. You need to ensure that when multiple alerts are generated by the rule, the alerts are consolidated as a single incident per user account. What should you do?
A. From Set rule logic, map the entities.
B. From Analytic rule details, configure Severity.
C. From Set rule logic, set Suppression to Off.
D. From Analytic rule details, configure Tactics.
SIMULATION - You need to configure your organization to automatically quarantine all phishing email messages. To complete this task, sign in to the Microsoft 365 portal.
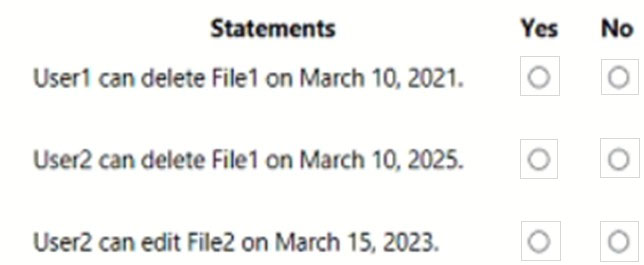
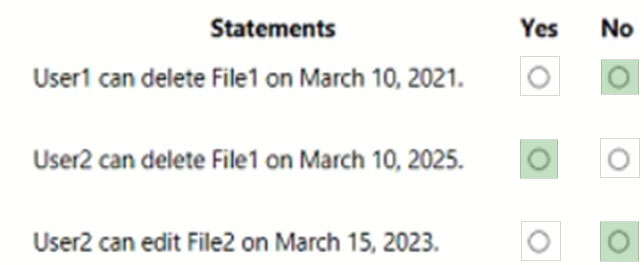
HOTSPOT - You have a Microsoft SharePoint Online site named Site1 that has the users shown in the following table.You create the retention labels shown in the following table.
You publish the retention labels to Site1. On March 1, 2021, you assign the retention labels to the files shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 E5 subscription that has Microsoft Defender for Cloud Apps enabled. You need to create an alert in Defender for Cloud Apps when source code is shared externally. Which type of policy should you create?
A. activity
B. Cloud Discovery anomaly detection
C. access
D. file
SIMULATION - You need to ensure that a user named Allan Deyoung uses multi-factor authentication (MFA) for all authentication requests. To complete this task, sign in to the Microsoft 365 admin center.
Free Access Full MS-500 Practice Exam Free
Looking for additional practice? Click here to access a full set of MS-500 practice exam free questions and continue building your skills across all exam domains.
Our question sets are updated regularly to ensure they stay aligned with the latest exam objectives—so be sure to visit often!
Good luck with your MS-500 certification journey!