MS-101 Practice Exam Free – 50 Questions to Simulate the Real Exam
Are you getting ready for the MS-101 certification? Take your preparation to the next level with our MS-101 Practice Exam Free – a carefully designed set of 50 realistic exam-style questions to help you evaluate your knowledge and boost your confidence.
Using a MS-101 practice exam free is one of the best ways to:
- Experience the format and difficulty of the real exam
- Identify your strengths and focus on weak areas
- Improve your test-taking speed and accuracy
Below, you will find 50 realistic MS-101 practice exam free questions covering key exam topics. Each question reflects the structure and challenge of the actual exam.
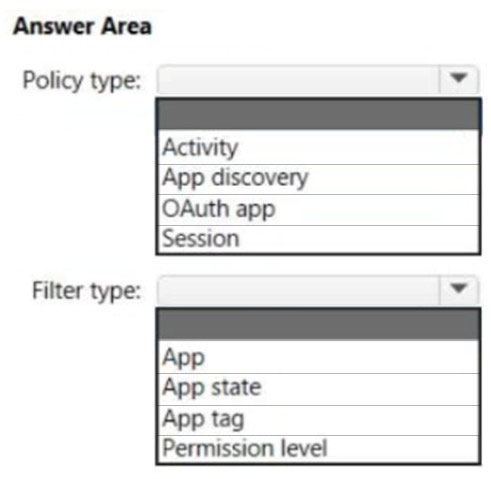
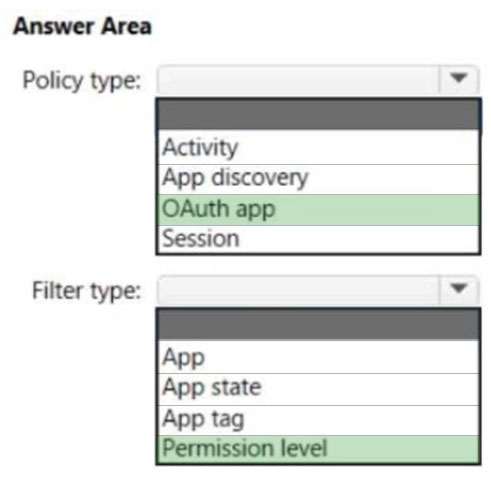
HOTSPOT - You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Cloud Apps. You need to create a policy that will generate an email alert when a banned app is detected requesting permission to access user information or data in the subscription. What should you configure? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You need to meet the technical requirement for large-volume document retrieval. What should you create?
A. an activity policy from Microsoft Defender for Cloud Apps
B. a data loss prevention (DLP) policy from the Microsoft 365 compliance center
C. a file policy from Microsoft Defender for Cloud Apps
D. an alert policy from the Microsoft 365 compliance center
You have a Microsoft 365 subscription. You need to view the IP address from which a user synced a Microsoft SharePoint Online library. What should you do?
A. From the SharePoint Online admin center, view the usage reports.
B. From the Microsoft 365 compliance center, perform an audit log search.
C. From the Microsoft 365 admin center, view the usage reports.
D. From the Microsoft 365 admin center, view the properties of the user’s user account.
Your company has a Microsoft 365 subscription that uses an Azure Active Directory (Azure AD) tenant named contoso.com. The tenant contains computers that run Windows 10 Enterprise and are managed by using Microsoft Endpoint Manager. The computers are configured as shown in the following table.You plan to implement Windows Defender Application Guard for contoso.com. You need to identify on which two Windows 10 computers Windows Defender Application Guard can be installed. Which two computers should you identify? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Computer1
B. Computer3
C. Computer2
D. Computer4
You have a Microsoft 365 subscription. You need to configure a compliance solution that meets the following requirements: • Defines sensitive data based on existing data samples. • Automatically prevents data that matches the samples from being shared externally in Microsoft SharePoint Online or email messages. Which two components should you configure? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. a trainable classifier
B. a sensitive info type
C. an adaptive policy scope
D. a data loss prevention (DLP) policy
E. an insider risk policy
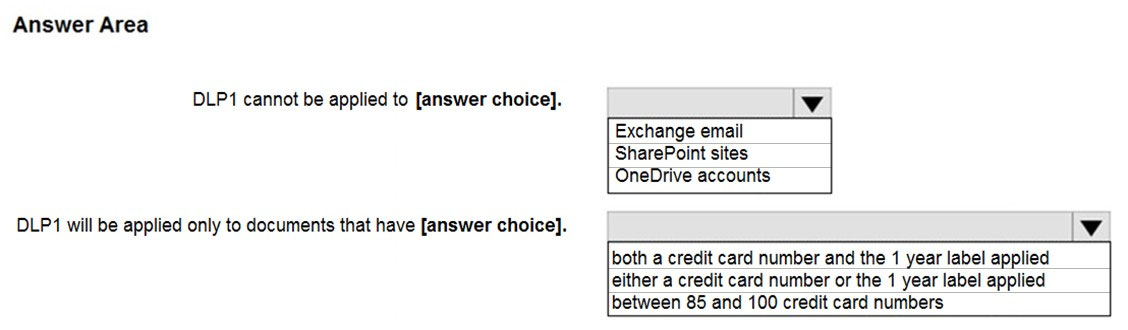
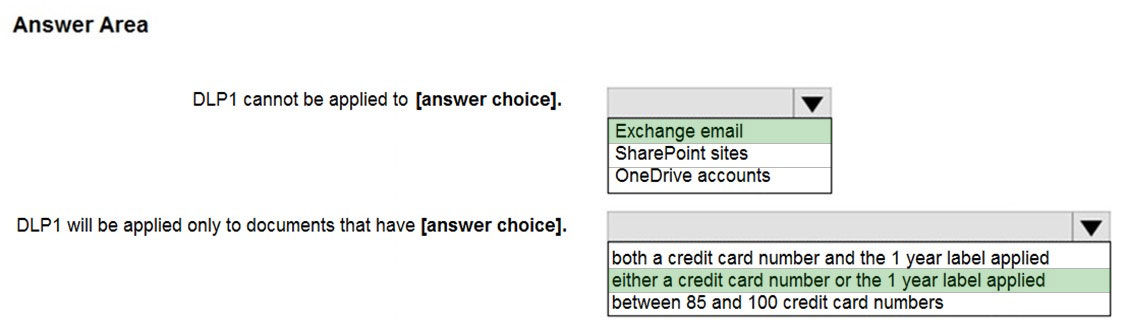
HOTSPOT - You configure a data loss prevention (DLP) policy named DLP1 as shown in the following exhibit.Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point. Hot Area:
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have an Azure Active Directory (Azure AD) tenant that contains a user named User1. Your company purchases a Microsoft 365 subscription. You need to ensure that User1 is assigned the required role to create file policies and manage alerts in the Defender for Cloud Apps admin center. Solution: From the Security & Compliance admin center, you assign the Security Administrator role to User1. Does this meet the goal?
A. Yes
B. No
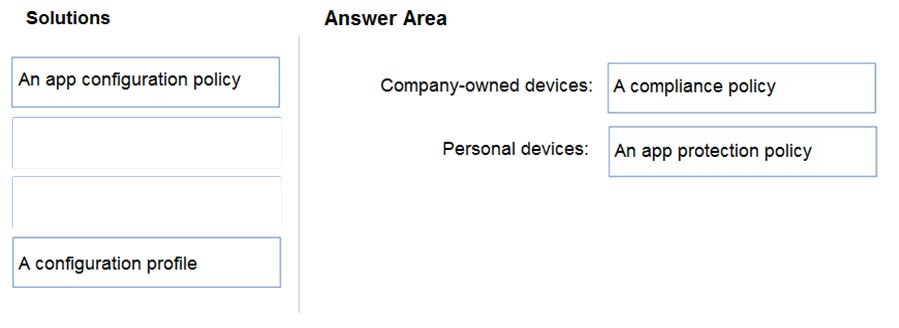
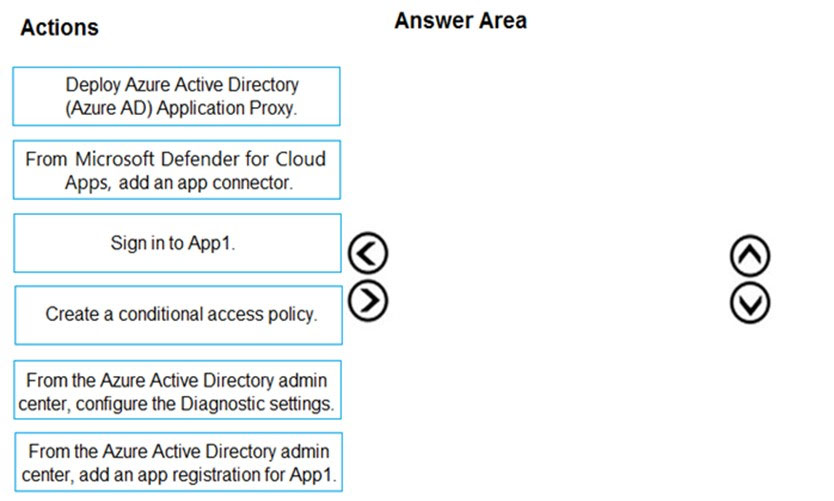
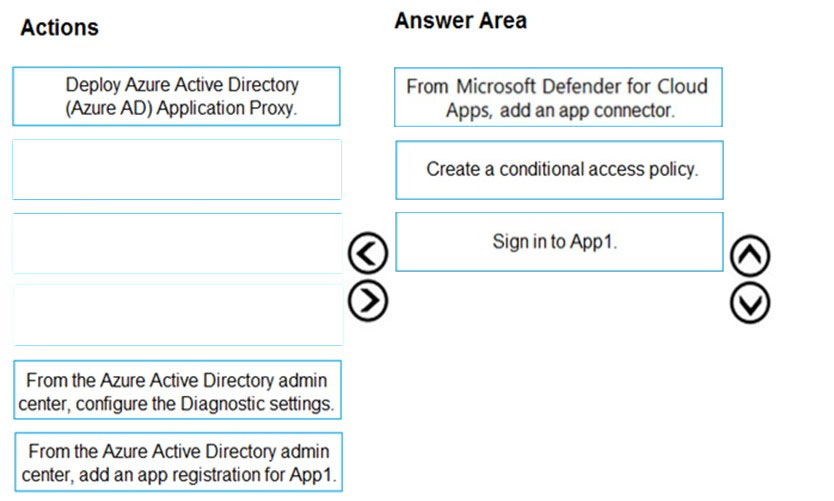
DRAG DROP - Your company has a Microsoft 365 E5 tenant. Users access resources in the tenant by using both personal and company-owned Android devices. Company policies requires that the devices have a threat level of medium or lower to access Microsoft Exchange Online mailboxes. You need to recommend a solution to identify the threat level of the devices and to control access of the devices to the resources. What should you include in the solution for each device type? To answer, drag the appropriate components to the correct devices. Each component may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point. Select and Place:
You have a Microsoft 365 E5 subscription that uses Microsoft SharePoint Online. You need to enable co-authoring for files that are encrypted by using sensitivity labels. What should you use?
A. the Microsoft 365 Defender portal
B. the SharePoint admin center
C. the Microsoft 365 admin center
D. the Microsoft 365 compliance center
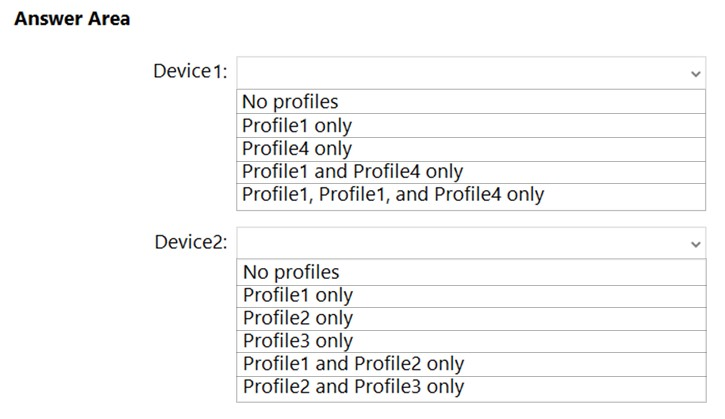
HOTSPOT - You have three devices enrolled in Microsoft Endpoint Manager as shown in the following table.The device compliance policies in Endpoint Manager are configured as shown in the following table.
The device compliance policies have the assignments shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
Your on-premises network contains the device types shown in the following table.You plan to deploy an in-place upgrade to a 64-bit version of Windows 10 Enterprise by using the Microsoft Deployment Toolkit (MDT). Which device types will support an in-place upgrade?
A. Type4 and Type5 only
B. Type3, Type4, and Type5 only
C. Type1, Type4, and Type5 only
D. Type1, Type2, and Type5 only
A user receives the following message when attempting to sign in to https://myapps.microsoft.com: `Your sign-in was blocked. We've detected something unusual about this sign-in. For example, you might be signing in from a new location, device, or app. Before you can continue, we need to verify your identity. Please contact your admin.` Which configuration prevents the users from signing in?
A. Microsoft Azure Active Directory (Azure AD) Identity Protection policies
B. Microsoft Azure Active Directory (Azure AD) conditional access policies
C. Endpoint Manager compliance policies
D. Security & Compliance data loss prevention (DLP) policies
You have a Microsoft 365 tenant. You plan to manage incidents in the tenant by using the Microsoft 365 Defender. Which Microsoft service source will appear on the Incidents page of the Microsoft 365 Defender?
A. Microsoft Defender for Cloud Apps
B. Azure Sentinel
C. Azure Web Application Firewall
D. Azure Information Protection
HOTSPOT - You have a Microsoft 365 E5 subscription that contains a user named User1 and the administrators shown in the following table.User1 reports that after sending 1,000 email messages in the morning, the user is blocked from sending additional emails. You need to identify the following: • Which administrators can unblock User1 • What to configure to allow User1 to send at least 2,000 emails per day without being blocked What should you identify? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription that uses Microsoft Defender for Cloud Apps. You configure a session control policy to block downloads from SharePoint Online sites. Users report that they can still download files from SharePoint Online sites. You need to ensure that file download is blocked while still allowing users to browse SharePoint Online sites. What should you configure?
A. an access policy
B. a data loss prevention (DLP) policy
C. an activity policy
D. a Conditional Access policy
DRAG DROP - You have a Microsoft 365 E5 tenant. You need to implement compliance solutions that meet the following requirements: ✑ Use a file plan to manage retention labels. ✑ Identify, monitor, and automatically protect sensitive information. Capture employee communications for examination by designated reviewers.Which solution should you use for each requirement? To answer, drag the appropriate solutions to the correct requirements. Each solution may be used once, more than once, or not at all. You may need to drag the split bat between panes or scroll to view content. NOTE: Each correct selection is worth one point. Select and Place:
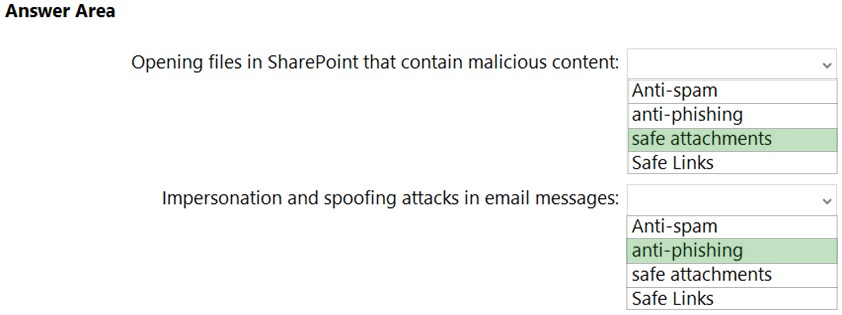
HOTSPOT - You have a Microsoft 365 subscription. You are planning a threat management solution for your organization. You need to minimize the likelihood that users will be affected by the following threats: ✑ Opening files in Microsoft SharePoint that contain malicious content ✑ Impersonation and spoofing attacks in email messages Which policies should you create in the Microsoft 365 Defender? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
Your company has a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com. You sign for Microsoft Store for Business. The tenant contains the users shown in the following table.Microsoft Store for Business has the following Shopping behavior settings: ✑ Allow users to shop is set to On ✑ Make everyone a Basic Purchaser is set to Off You need to identify which users can install apps from the Microsoft for Business private store. Which users should you identify?
A. User3 only
B. User1 only
C. User1 and User2 only
D. User3 and User4 only
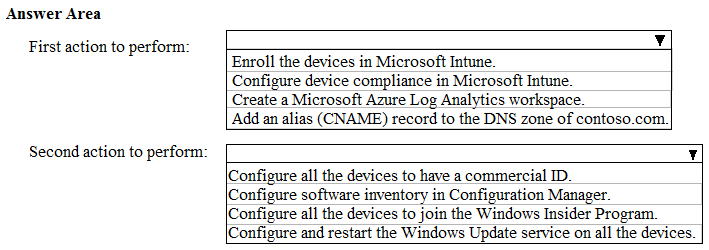
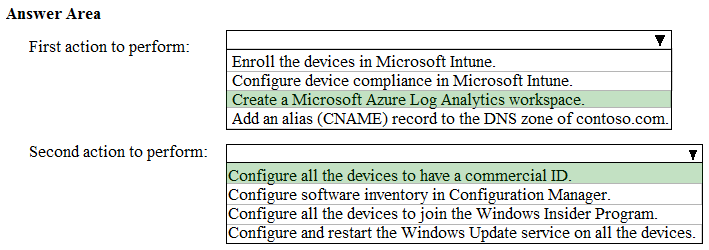
HOTSPOT - You have a Microsoft 365 E5 subscription that uses Microsoft Intune. You have devices enrolled in Intune as shown in the following table.You create the device configuration profiles shown in the following table.
Which profiles will be applied to each device? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
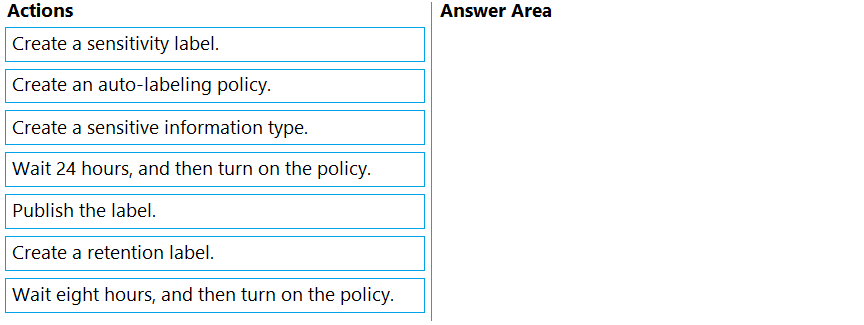
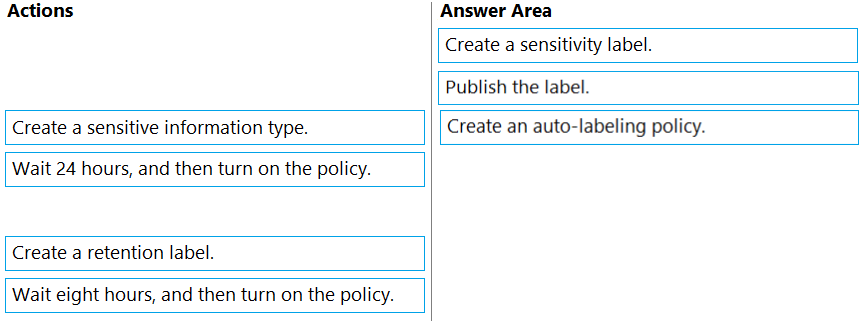
DRAG DROP - You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint Online site named Site1. You need to automatically label the documents on Site1 that contain credit card numbers. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. Select and Place:
HOTSPOT - You have a Microsoft 365 E5 tenant. You create a data loss prevention (DLP) policy to prevent users from using Microsoft Teams to share internal documents with external users. To which two locations should you apply the policy? To answer, select the appropriate locations in the answer area. NOTE: Each correct selection is worth one point.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com. You create a Microsoft Defender for Identity instance named Contoso. The tenant contains the users shown in the following table.You need to modify the configuration of the Defender for Identity sensors. Solution: You instruct User1 to modify the Defender for Identity sensor configuration. Does this meet the goal?
A. Yes
B. No
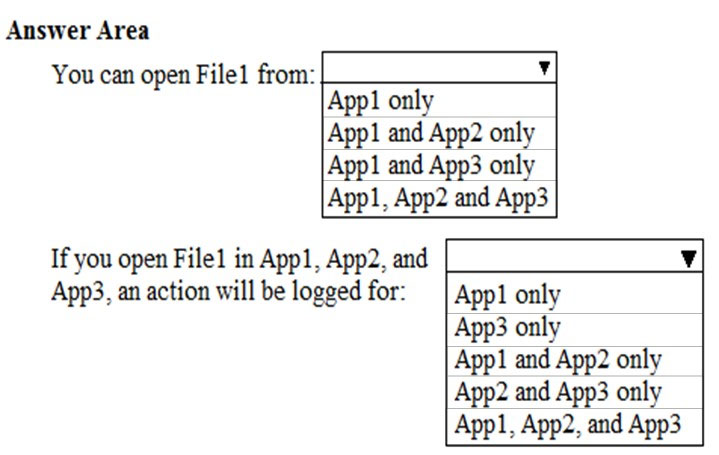
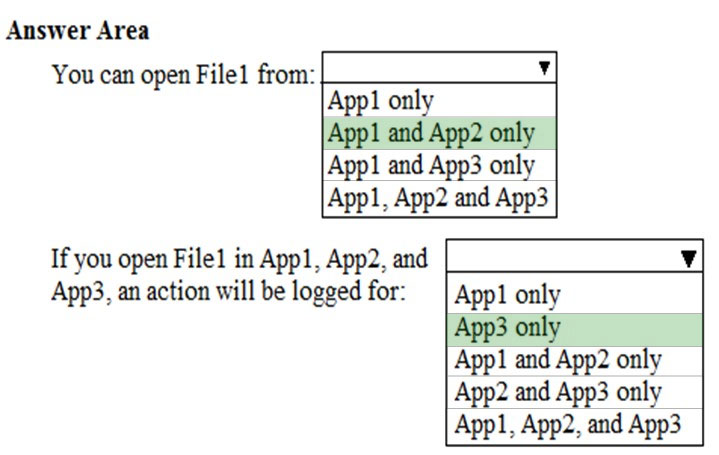
HOTSPOT - Your network contains an Active Directory domain named contoso.com. The domain contains the file servers shown in the following table.A file named File1.abc is stored on Server1. A file named File2.abc is stored on Server2. Three apps named App1, App2 and App3 are installed on a Windows 10 device named Device1. All three apps open files that have the .abc file extension. You implement Windows Information Protection (WIP) by creating a policy named Policy1 that has the following configuration: ✑ Exempt apps: App2 ✑ Protected apps: App1 ✑ Windows Information Protection mode: Block ✑ Network boundary: IPv4 range of: 192.168.1.1-192.168.1.255 You ensure that Policy1 applies to Device1. You need to identify the apps from which you can open File1.abc. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 E5 tenant that contains the devices shown in the following table.You plan to review device startup performance issues by using Endpoint analytics. Which devices can you monitor by using Endpoint analytics?
A. Device1 only
B. Device1 and Device2 only
C. Device1, Device2, and Device3 only
D. Device1, Device2, and Device4 only
E. Device1, Device2, Device3, and Device4
You enable the Azure AD Identity Protection weekly digest email. You create the users shown in the following table.Which users will receive the weekly digest email automatically?
A. Admin2, Admin3, and Admin4 only
B. Admin1, Admin2, Admin3, and Admin4
C. Admin2 and Admin3 only
D. Admin3 only
E. Admin1 and Admin3 only
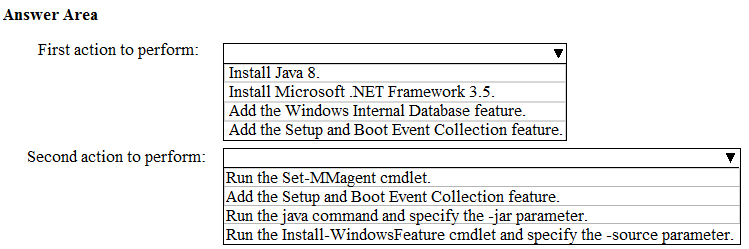
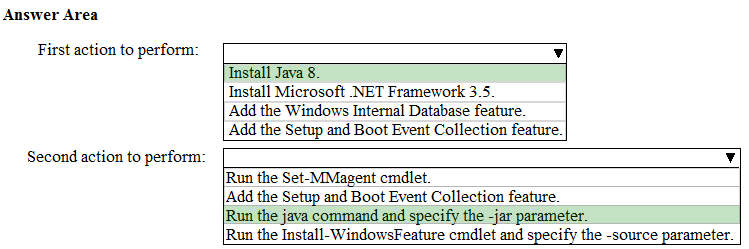
HOTSPOT - Your company uses Microsoft Defender for Cloud Apps. You plan to integrate Defender for Cloud Apps and security information and event management (SIEM). You need to deploy a SIEM agent on a server that runs Windows Server 2016. What should you do? To answer, select the appropriate settings in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 tenant. Company policy requires that all Windows 10 devices meet the following minimum requirements: ✑ Require complex passwords. ✑ Require the encryption of data storage devices. Have Microsoft Defender Antivirus real-time protection enabled.You need to prevent devices that do not meet the requirements from accessing resources in the tenant. Which two components should you create? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. a configuration policy
B. a compliance policy
C. a security baseline profile
D. a conditional access policy
E. a configuration profile
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a computer that runs Windows 10. You need to verify which version of Windows 10 is installed. Solution: From Device Manager, you view the computer properties. Does this meet the goal?
A. Yes
B. No
You have Windows 10 devices that are managed by using Microsoft Endpoint Manager. You need to configure the security settings in Microsoft Edge. What should you create in Microsoft Endpoint Manager?
A. an app configuration policy
B. an app
C. a device configuration profile
D. a device compliance policy
DRAG DROP - Your company purchases a cloud app named App1. You need to ensure that you can use Microsoft Defender for Cloud Apps to block downloads in App1. App1 supports session controls. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. Select and Place:
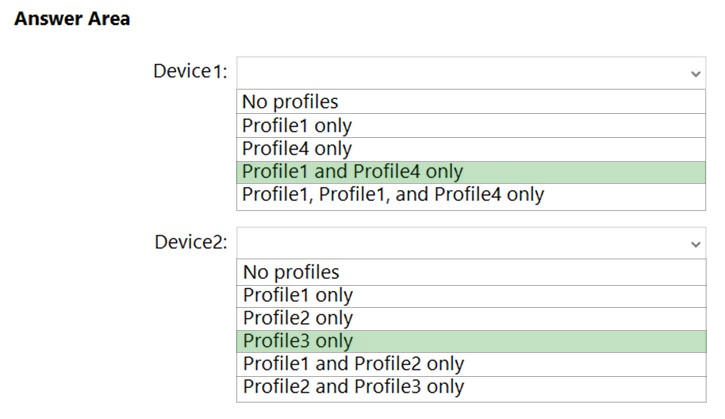
HOTSPOT - You have three devices enrolled in Microsoft Endpoint Manager as shown in the following table.The device compliance policies in Endpoint Manager are configured as shown in the following table.
The device compliance policies have the assignments shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
You need to recommend a solution for the security administrator. The solution must meet the technical requirements. What should you include in the recommendation?
A. Microsoft Azure Active Directory (Azure AD) Privileged Identity Management
B. Microsoft Azure Active Directory (Azure AD) Identity Protection
C. Microsoft Azure Active Directory (Azure AD) conditional access policies
D. Microsoft Azure Active Directory (Azure AD) authentication methods
You have a Microsoft 365 subscription. All users have their email stored in Microsoft Exchange Online. In the mailbox of a user named User1, you need to preserve a copy of all the email messages that contain the word ProjectX. What should you do first?
A. From the Microsoft Purview compliance portal, create a label and a label policy.
B. From the Exchange admin center, create a mail flow rule.
C. From the Microsoft Purview compliance portal, create a data loss prevention (DLP) policy.
D. From Microsoft Defender for Cloud Apps, create an activity policy.
In Microsoft 365, you configure a data loss prevention (DLP) policy named Policy1. Policy1 detects the sharing of United States (US) bank account numbers in email messages and attachments. Policy1 is configured as shown in the exhibit. (Click the Exhibit tab.)You need to ensure that internal users can email documents that contain US bank account numbers to external users who have an email suffix of contoso.com. What should you configure?
A. an exception
B. an action
C. a condition
D. a group
You have a Microsoft 365 E5 subscription. You need to be notified if users receive email containing a file that has a virus. What should you do?
A. From the Exchange admin center, create an in-place eDiscovery & hold.
B. From the Exchange admin center, create a spam filter policy.
C. From the Exchange admin center, create an anti-malware policy.
D. From the Exchange admin center, create a mail flow rule.
HOTSPOT - You have a Microsoft 365 E5 tenant. You need to ensure that administrators are notified when a user receives an email message that contains malware. The solution must use the principle of least privilege. Which type of policy should you create, and which Microsoft Purview solutions role is required to create the policy? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You plan to use the Security & Compliance admin center to import several PST files into Microsoft 365 mailboxes. Which three actions should you perform before you import the data? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. From the Exchange admin center, create a public folder.
B. Copy the PST files by using AzCopy.
C. From the Exchange admin center, assign admin roles.
D. From the Microsoft Azure portal, create a storage account that has a blob container.
E. From the Microsoft 365 admin center, deploy an add-in.
F. Create a mapping file that uses the CSV file format.
You configure a conditional access policy. The locations settings are configured as shown in the Locations exhibit. (Click the Locations tab.)The users and groups settings are configured as shown in the Users and Groups exhibit. (Click Users and Groups tab.)
Members of the Security reader group report that they cannot sign in to Microsoft Active Directory (Azure AD) on their device while they are in the office. You need to ensure that the members of the Security reader group can sign in in to Azure AD on their device while they are in the office. The solution must use the principle of least privilege. What should you do?
A. From the conditional access policy, configure the device state.
B. From the Azure Active Directory admin center, create a custom control.
C. From the Endpoint Manager admin center, create a device compliance policy.
D. From the Azure Active Directory admin center, create a named location.
Your company has five security information and event management (SIEM) appliances. The traffic logs from each appliance are saved to a file share named Logs. You need to analyze the traffic logs. What should you do from Microsoft Defender for Cloud Apps?
A. Click Investigate, and then click Activity log.
B. Click Control, and then click Policies. Create a file policy.
C. Click Discover, and then click Create snapshot report.
D. Click Investigate, and then click Files.
You have an Azure AD tenant that contains a user named User1. User1 has the devices shown in the following table.The Device settings are configured as shown in the following exhibit.
How many of the devices can User1 join to Azure AD?
A. 1
B. 2
C. 3
D. 4
You have a Microsoft 365 tenant that contains 1,000 Windows 10 devices. The devices are enrolled in Microsoft Intune. Company policy requires that the devices have the following configurations: ✑ Require complex passwords. ✑ Require the encryption of removable data storage devices. ✑ Have Microsoft Defender Antivirus real-time protection enabled. You need to configure the devices to meet the requirements. What should you use?
A. an app configuration policy
B. a compliance policy
C. a security baseline profile
D. a conditional access policy
HOTSPOT - Your network contains an Active Directory domain named contoso.com that uses Microsoft System Center Configuration Manager (Current Branch). You have Windows 10 and Windows 8.1 devices. You need to ensure that you can analyze the upgrade readiness of all the Windows 8.1 devices and analyze the update compliance of all the Windows 10 devices. What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 E5 subscription that contains 500 users. Two hundred users have personal devices that run either Android, Windows 10, or macOS. Three hundred users have corporate-owned devices that run either Windows 10 or macOS. You plan to configure device enrollment. You need to ensure that you can apply separate policies to the corporate-owned devices and the personal devices. The solution must minimize administrative effort. What should you create first?
A. a dynamic device group
B. a dynamic user group
C. a deployment package
D. a Microsoft 365 group
Your company has a Microsoft 365 subscription. The subscription contains 500 devices that run Windows 10 and 100 devices that run iOS. You need to create Microsoft Endpoint Manager device configuration profiles to meet the following requirements: ✑ Configure Wi-Fi connectivity to a secured network named ContosoNet. ✑ Require passwords of at least six characters to lock the devices. What is the minimum number of device configuration profiles that you should create?
A. 4
B. 2
C. 1
You need to create the Safe Attachments policy to meet the technical requirements. Which option should you select?
A. Replace
B. Enable redirect
C. Block
D. Dynamic Delivery
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a new Microsoft 365 subscription. You need to prevent users from sending email messages that contain Personally Identifiable Information (PII). Solution: From the Microsoft 365 compliance center, you create a data loss prevention (DLP) policy. Does this meet the goal?
A. Yes
B. No
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a new Microsoft 365 subscription. You need to prevent users from sending email messages that contain Personally Identifiable Information (PII). Solution: From the Azure portal, you create a Microsoft Azure Information Protection label and an Azure Information Protection policy. Does this meet the goal?
A. Yes
B. No
HOTSPOT - You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com. You have three applications named App1, App2, and App3. The apps use files that have the same file extensions. Your company uses Windows Information Protection (WIP). WIP has the following configurations: ✑ Windows Information Protection mode: Silent ✑ Protected apps: App1 ✑ Exempt apps: App2 From App1, you create a file named File1. What is the effect of the configurations? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft 365 subscription. You need to prevent users from accessing your Microsoft SharePoint Online sites unless the users are connected to your on-premises network. Solution: From the Device Management admin center, you create a device configuration profile. Does this meet the goal?
A. Yes
B. No
HOTSPOT - You configure a data loss prevention (DLP) policy named DLP1 with a rule configured as shown in the following exhibit.Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point.
Free Access Full MS-101 Practice Exam Free
Looking for additional practice? Click here to access a full set of MS-101 practice exam free questions and continue building your skills across all exam domains.
Our question sets are updated regularly to ensure they stay aligned with the latest exam objectives—so be sure to visit often!
Good luck with your MS-101 certification journey!