350-901 Practice Exam Free – 50 Questions to Simulate the Real Exam
Are you getting ready for the 350-901 certification? Take your preparation to the next level with our 350-901 Practice Exam Free – a carefully designed set of 50 realistic exam-style questions to help you evaluate your knowledge and boost your confidence.
Using a 350-901 practice exam free is one of the best ways to:
- Experience the format and difficulty of the real exam
- Identify your strengths and focus on weak areas
- Improve your test-taking speed and accuracy
Below, you will find 50 realistic 350-901 practice exam free questions covering key exam topics. Each question reflects the structure and challenge of the actual exam.
Which two methods are API security best practices? (Choose two.)
A. Use tokens after the identity of a client has been established.
B. Use the same operating system throughout the infrastructure.
C. Use encryption and signatures to secure data.
D. Use basic auth credentials over all internal API interactions.
E. Use cloud hosting services to manage security configuration.
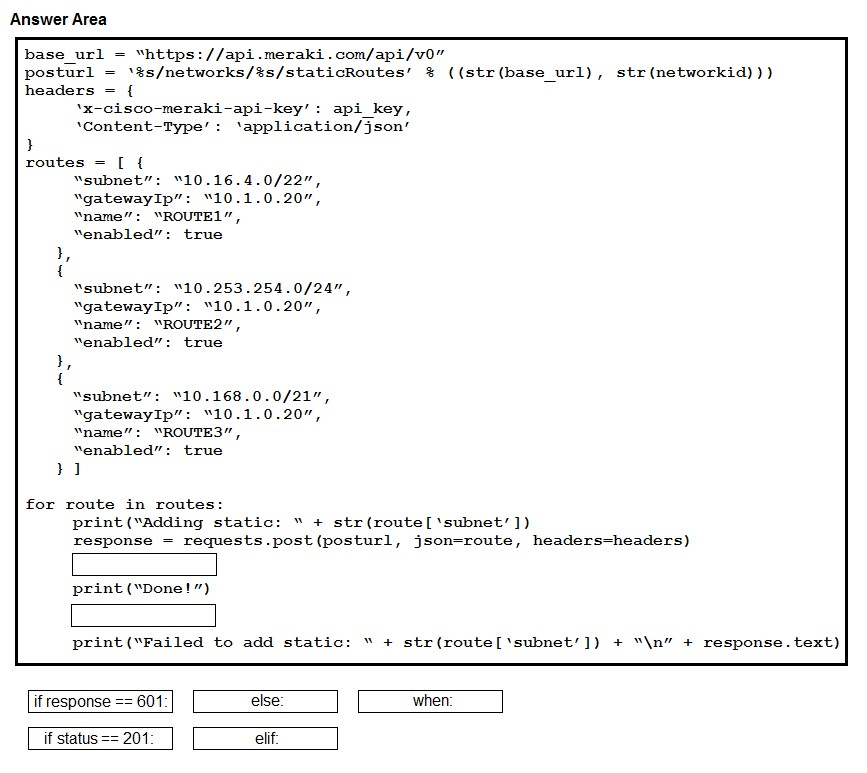
DRAG DROP -Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to query the last 10 Bluetooth clients seen by APs in their network using the Meraki Dashboard API. Not all options are used.
An enterprise refactors its monolithic application into a modern cloud-native application that is based on microservices. A key requirement of the application design is to ensure that the IT team is aware of performance issues or bottlenecks in the new application. Which two approaches must be part of the design considerations? (Choose two.)
A. Adopt a service-oriented architecture to handle communication between the services that make up the application.
B. Implement infrastructure monitoring to ensure that pipeline components interoperate smoothly and reliably.
C. Instrument the application code to gather telemetry data from logs, metrics, or tracing.
D. Periodically scale up the resources of the host machines when the application starts to experience high loads.
E. Deploy infrastructure monitoring agents into the operating system of the host machines.
A developer must apply a new feature on a live project. After the commit, it was discovered that the wrong file was applied. The developer must undo the single commit and apply the file with the name feat-EXP453928854DPS. Which command must the developer use?
A. git clean
B. git checkout
C. git revert
D. git reset
Refer to the exhibit. An engineer needs to configure an interface named GigabitEthernet3 with an IP address on several RESTCONF-enabled Cisco IOS XE devices. Which code snippet must be placed in the blank in the code to meet this requirement?
A. {item[“name”]}’
B. {item[“name”]}/ip/address/primary’
C. {item[“name”]}/ip/address
D. {item[“name”]} /ip
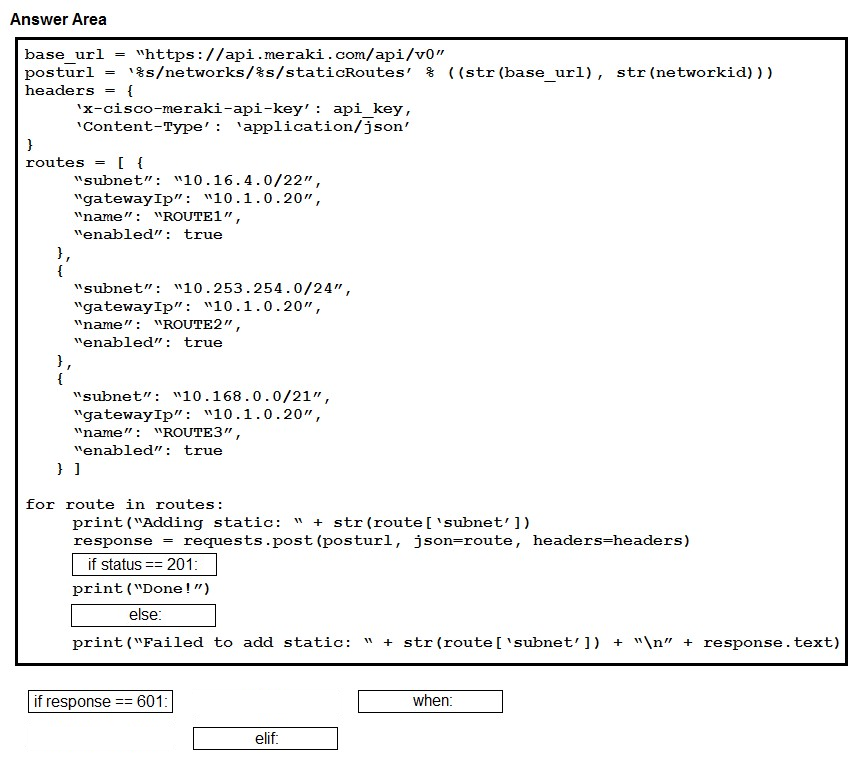
DRAG DROP - Drag and drop the expressions from below onto the code to implement error handling. Not all options are used. Select and Place:
Refer to the exhibit. A network engineer developed an Ansible playbook and committed it to GitLab. A GitLab CI pipeline is started but immediately fails. What is the issue?
A. The runner is running the wrong Docker version.
B. The Ansible playbook has an undefined variable.
C. The runner task uses an incorrect parameter.
D. The Ansible playbook task has a formatting issue.
Which statement about microservices architecture is true?
A. Applications are written in a single unit.
B. It is a complex application composed of multiple independent parts.
C. It is often a challenge to scale individual parts.
D. A single faulty service can bring the whole application down.
A development team is considering options for implementing a new configuration management solution which must: • be agentless • utilize Python as a developing language • leverage YAML based workflows Which solution must be chosen?
A. Terraform
B. Puppet
C. Ansible
D. Nornir
An application has been developed for monitoring rooms in Cisco Webex. An engineer uses the application to retrieve all the messages from a Cisco Webex room, but the results are slowly presented. Which action optimizes calls to retrieve the messages from the /v1/messages endpoint?
A. Define the ma property by using the pagination functionality.
B. Set the beforeMessage property to retrieve the messages sent before a specific message ID.
C. Avoid unnecessary calls by using a prior request to /v1/rooms to retrieve the last activity property.
D. Filter the response results by specifying the created property in the request.
Which HTTP status code indicates that a client application is experiencing intentional rate limiting by the server?
A. 202
B. 401
C. 429
D. 503
A developer releases a new application for network automaton of Cisco devices deployed in a local data center. The application utilizes complex design patterns such as microservices that host multiple third-party libraries and programming languages. The development must be simplified by implementing an observability- driven development lifecycle. Which two considerations must be taken to meet the requirements? (Choose two.)
A. which monitoring tools to use
B. identifying customer priorities
C. relevant metrics to expose
D. description of low-level errors
E. which KPIs to monitor
DRAG DROP -Refer to the exhibit. An engineer needs to connect to the Cisco Services API to retrieve the product alerts for customer ID 1234. However, because there are many results, the API call must be formatted to limit the data that is returned. The engineer has already logged into the Cisco Services API and is now working on the function to retrieve the product alerts. Drag and drop the code snippets from the bottom onto the blanks in the code to retrieve the first 10 items of the product vulnerability alerts. Not all options are used.
Which step is part of a three-legged OAuth2 authorization code grant flow?
A. Use authorization codes to access protected resources when approved.
B. Exchange tokens for authorization codes by using the authentication server.
C. A user initiates a request to the OAuth client by using a predefined token.
D. The OAuth client redirects to the authorization server by using a username and password.
While working with the Webex API, on an application that uses end-to-end encryption, a webhook has been received. What must be considered to read the message?
A. Webhook information cannot be used to read the message because of end-to-end encryption. The API key is needed to decrypt the message.
B. Webhook returns the full unencrypted message. Only the body is needed to query the API.
C. Webhook returns a hashed version of the message that must be unhashed with the API key.
D. Webhook returns message identification. To query, the API is needed for that message to get the decrypted information.
Refer to the exhibit. Which cURL request is included in the presented XML as the body of the response? A.
B.
C.
D.
What is an effective logging strategy according to the 12-factor app tenets?
A. Tag and save logs in a local document database that has querying capabilities.
B. Back up log files in a high-availability remote cluster on the public cloud.
C. Timestamp and save logs in a local time-series database that has querying capabilities.
D. Capture logs by the execution environment and route to a centralized destination.
Refer to the exhibit. The Python code manages a Cisco CSR 1000V router. Which code snippet must be placed in the blank in the code to update the current configuration of the targeted resource?
A.

B.

C.

D.

A custom dashboard of the network health must be created by using Cisco DNA Center APIs. An existing dashboard is a RESTful API that receives data from Cisco DNA Center as a new metric every time the network health information is sent from the script to the dashboard. Which set of requests creates the custom dashboard?
A. POST request to Cisco DNA Center to obtain the network health information, and then a GET request to the dashboard to publish the new metric
B. GET request to Cisco DNA Center to obtain the network health information, and then a PUT request to the dashboard to publish the new metric
C. GET request to Cisco DNA Center to obtain the network health information, and then a POST request to the dashboard to publish the new metric
D. PUT request to Cisco DNA Center to obtain the network health information, and then a POST request to the dashboard to publish the new metric
A developer has created an application based on customer requirements. The customer needs to run the application with the minimum downtime. Which design approach regarding high-availability applications, Recovery Time Objective, and Recovery Point Objective must be taken?
A. Active/passive results in lower RTO and RPO. For RPO, data synchronization between the two data centers must be timely to allow seamless request flow.
B. Active/passive results in lower RTO and RPO. For RPO, data synchronization between the two data centers does not need to be timely to allow seamless request flow.
C. Active/active results in lower RTO and RPO. For RPO, data synchronization between the two data centers does not need to be timely to allow seamless request flow.
D. Active/active results in lower RTO and RPO. For RPO, data synchronization between the two data centers must be timely to allow seamless request flow.
What is submitted when an SSL certificate is requested?
A. PEM
B. CRT
C. DER
D. CSR
Refer to the exhibit. Information was obtained by using RESTCONF and querying URI /restconf/data/ietf-interfaces:interfaces. Which RESTCONF call and which JSON code enables GigabitEthernet2? (Choose two.) A.
B.
C.
D.
E.
F.
DRAG DROP -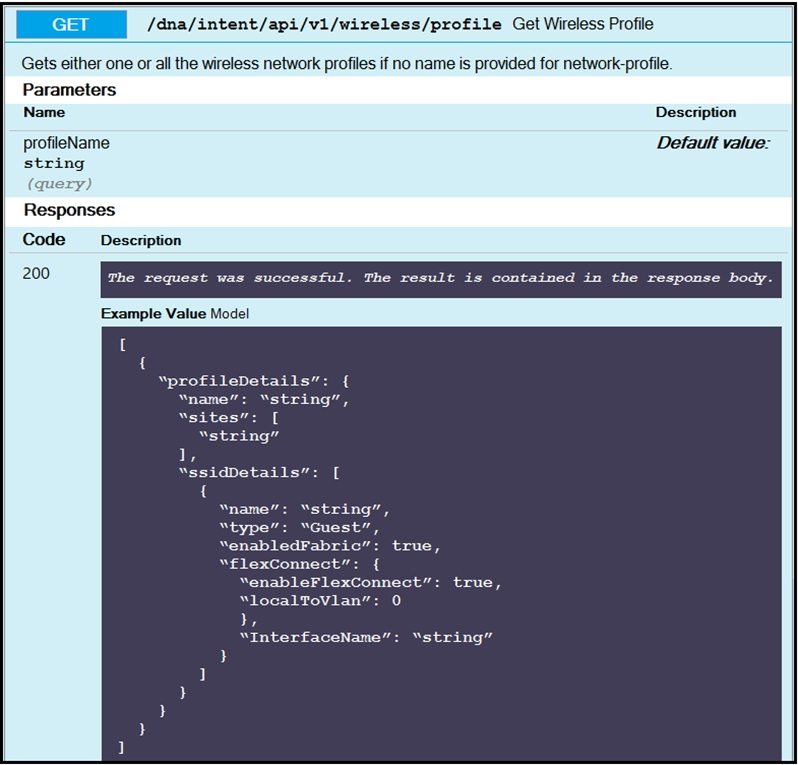
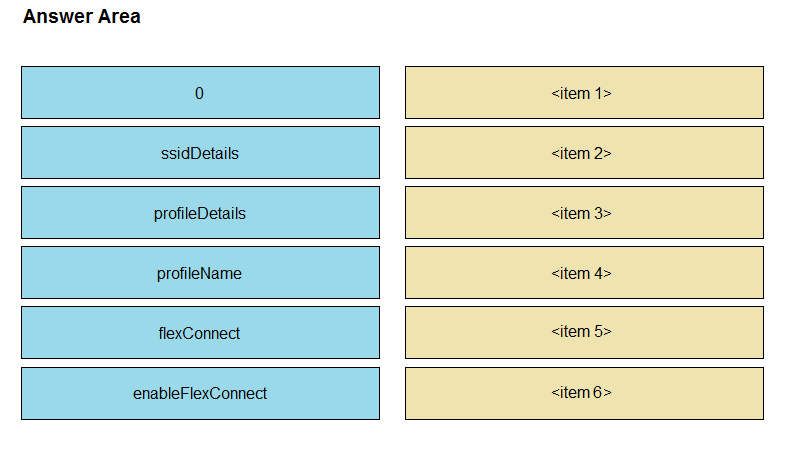
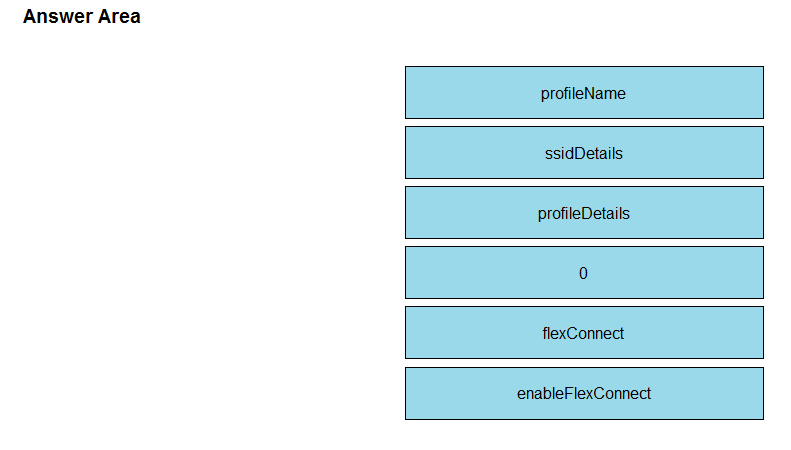
Refer to the exhibit. The Python script is supposed to make an API call to Cisco DNA Center querying a wireless profile for the `ChicagoCampus` and then parsing out its enable FlexConnect value. Drag and drop the parts of the Python code from the left onto the item numbers on the right that match the missing sections in the exhibit. Select and Place:
Refer to the exhibit. An engineer needs to implement REST API error handling when a timeout or rate limit scenario is present. Which code snippet must be placed into the blank in the code to complete the API request?
A.

B.

C.

D.

Refer to the exhibit. An application hosting server in the local data center is experiencing large amounts of traffic from end-users. A developer must optimize this API server to reduce the load on its host. What are two ways to optimize this code through HTTP cache controls? (Choose two.)
A. Include the “Content-Type” header in the API response.
B. Include the “Last-Modified” header in the API response.
C. Include the “ETag” header in the API response.
D. Leverage middleware caching and respond with HTTP code 204 in the API response.
E. Leverage middleware caching and respond with HTTP code 104 in the API response.
An architect must optimize traffic that targets a popular API endpoint. Currently, the application downloads a large file hourly, but often the file is unchanged and the download causes unnecessary load and delays. Which cURL command must be used to determine the last modified date of the file and to optimize the API usage?
A. curl -H ‘Cache-Control: no-cache’ request
B. curl HEAD request
C. curl –silent request
D. curl GET request
Refer to the exhibit. An Intersight API is being used to query RackUnit resources that have a tag keyword set to `Site`. What is the expected output of this command?
A. list of all resources that have a tag with the keyword ג€Siteג€
B. error message because the Value field was not specified
C. error message because the tag filter should be lowercase
D. list of all sites that contain RackUnit tagged compute resources
Refer to the exhibit. Cisco IOS XE switches are used across the entire network and the description that is filed for all interfaces must be configured. Which code snippet must be placed in the blank in the script to leverage RESTCONF to query all the devices in the device list for the interfaces that are present?
A.

B.

C.

D.

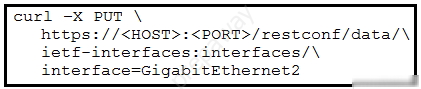
Refer to the exhibit. An engineer needs to change the IP address via RESTCONF on interface GigabitEthemet2. An error message is received when the script is run. Which amendment to the code will result in a successful RESTCONF action?
A. Change POST to PATCH
B. Issue a DELETE before POST
C. Issue a DELETE before PATCH
D. Change POST to GET
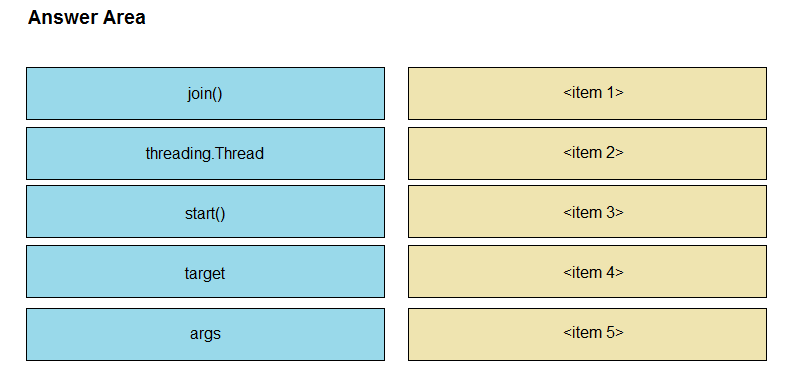
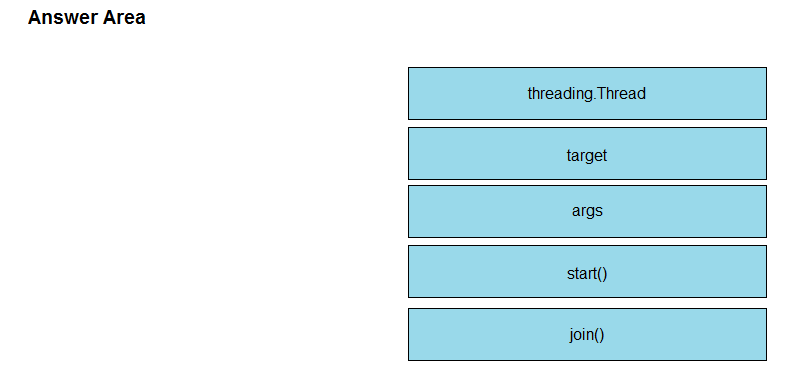
DRAG DROP -Refer to the exhibit. Python threading allows a developer to have different parts of a program run concurrently and simplify a design. Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to create a thread instance. Select and Place:
An engineer must enable an SSID in a Meraki network. Which request accomplishes this task?
A. PUT /networks/{networkId}/ssids/{number}?enabled=true
B. POST /networks/{networkId}/ssids/{number}?enabled=true
C. PUT /networks/{networkId}/ssids/{number} {“enable”: true}
D. POST /networks/{networkId}/ssids/{number} {“enable”: true}
DRAG DROP - Drag and drop the code from the bottom onto the box where the code is missing to delete a host object by using the Cisco Firepower Device Manager API. Not all options are used.
A developer is adding a user experience improvement to an application and is working on a fork. The developer must push a new branch named ‘devcorexpv4g4h1h1y1r5l3w1t4’ to the remote repository named ‘PRODdevcorv01h1t2d1w5i6j4a5b’. The local branch must be updated to include any new changes that were pushed to the remote repository from other developers. Which Git command must be used?
A. git reset -f
B. git fetch -f
C. git merge –all
D. git pull –all
Refer to the exhibit. The Ansible playbook is using the netconf_module to configure an interface using a YANG model. As part of this workflow, which YANG models augment the interface?
A. ietf-interfaces and ietf-ip
B. iana-if-type and ietf-interfaces
C. ietf-ip and openconfig-interface
D. ietf-ip and iana-if-type
DRAG DROP - Drag and drop the code from the bottom onto the box where the code is missing to retrieve location data for network devices. Not all options are used.
What are two steps in the OAuth2 protocol flow? (Choose two.)
A. The user is authenticated by the authorization server and granted an access token.
B. The user’s original credentials are validated by the resource server and authorization is granted.
C. The user indirectly requests authorization through the authorization server.
D. The user requests an access token by authentication and authorization grant presentation.
E. The user requests the protected resource from the resource server using the original credentials.
In the three-legged OAuth2 authorization workflow, which entity grants access to a protected resource?
A. resource owner
B. client
C. resource server
D. authorization server
A developer is developing a microservices code to manage REST API errors. Which two approaches must the developer take to manage the HTTP 429 "Too Many Requests" status code in the microservices code? (Choose two.)
A. Implement subsequent retry with the same interval window.
B. Resend the request immediately without implementing a wait time.
C. Consecutive retries should truncate exponential backup.
D. Throw an exception in the application code.
E. Return errors in the response code.
Refer to the exhibit. Which key value pair from the ios_ntp Ansible module removes the NTP server peer?
A. state: absent
B. state: False
C. config: absent
D. config: False
An engineer is responsible for managing the infrastructure as code in the organization. The engineer must perform these tasks on a set of virtual machines that have already been provisioned: • Install software. • Deploy new configurations. • Maintain the infrastructure. Which configuration management tool must be used to accomplish these tasks?
A. Cisco NSO
B. Python
C. Docker
D. Ansible
Refer to the exhibit. A Python API server has been deployed. Based on metrics and logs, increased load has been noticed. Which two approaches must be taken to optimize API usage on the server? (Choose two.)
A. Include the Content-Type header in the API response.
B. Leverage middleware caching and respond with HTTP code 204 in the API response.
C. Include the ETag header in the API response.
D. Include the Last-Modified header in the API response.
E. Change the query to be more efficient.
What is a well-defined concept for GDPR compliance?
A. Data subjects can require that the data controllers erase their personal data.
B. Personal data that was collected before the compliance standards were set do not need to be protected.
C. Compliance standards apply to organizations that have a physical presence in Europe.
D. Records that are relevant to an existing contract agreement can be retained as long as the contract is in effect.
A Cisco Catalyst 9000 switch has guest shell enabled. Which Linux command installs a third-party application?
A. apt-get install
B. zypper install
C. yum install
D. dnf install
DRAG DROP - A developer is designing an application that uses confidential information for a company and its clients. The developer must implement different secret storage techniques for each handled secret to enforce security policy compliance within a project. Drag and drop the security policy requirements from the left onto the storage solutions on the right.
An engineer needs to improve the responsiveness of an application by implementing client-side HTTP caching. The cached data must be cacheable by everyone and must be validated during each request. Which value must the engineer set in the Cache-Control header to meet these requirements?
A. private
B. no-cache
C. no-store
D. max-age
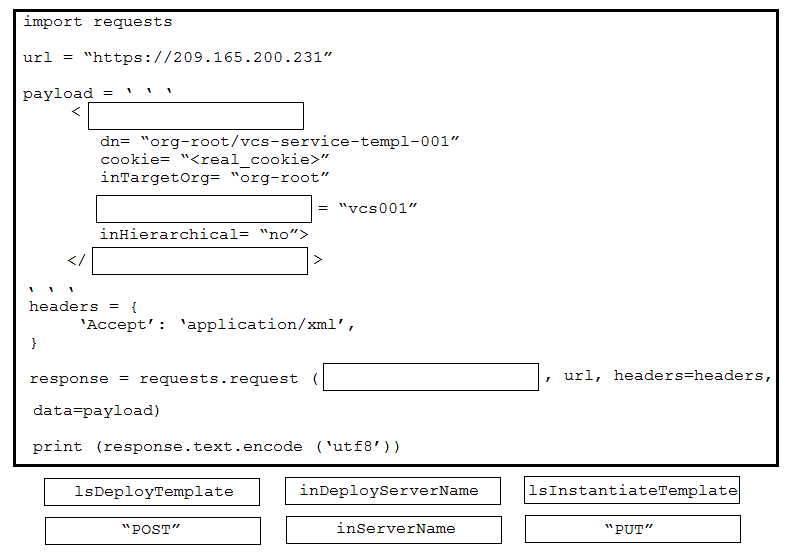
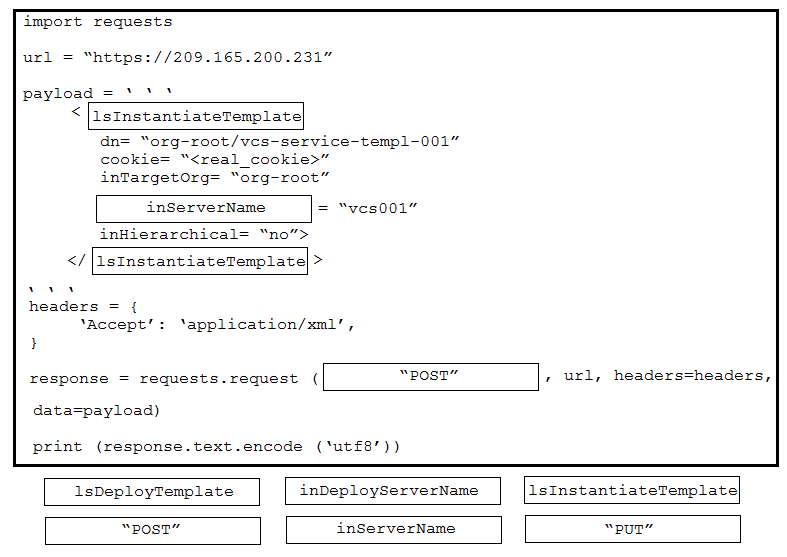
DRAG DROP - Drag and drop the code from the bottom onto the box where the code is missing to provision a new Cisco Unified Computing System server by using the UCS XML API. Options may be used more than once. Not all options are used. Select and Place:
A developer must meet these requirements: • Support the provisioning of up to 500 new virtual machines into private data centers or the public cloud. • Ensure that the configuration of 400 existing virtual machines is kept in sync and can be updated on-demand. • Support specifying a list of instructions or steps that must be performed in a precise order to configure a virtual machine. Which configuration management solution must the developer use?
A. Ansible
B. Docker
C. Puppet
D. Terraform
Refer to the exhibit. An application's REST API GET call is tested to the inventory database. Which missing code must be included to limit the number of values that are returned from the query to 20?
A. ?inventory=20
B. inventory?limit=20
C. limit=?20
D. inventory=limit?20
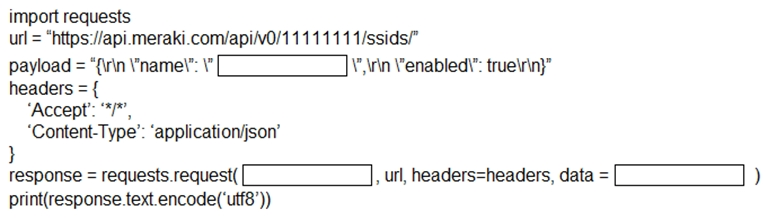
FILL BLANK - Fill in the blanks to complete the Python script to enable the SSID with a name of `371767916` in the network resource `11111111` using the Meraki Dashboard API.
An application is developed in order to communicate with Cisco Webex. For reporting, the application must retrieve all the messages sent to a Cisco Webex room on a monthly basis. Which action calls /v1/messages directly?
A. Set up a webhook that has messages as the resource type and store the results locally.
B. Utilize the pagination functionality by defining the max property.
C. Recursively call the /v1/messages endpoint by using the beforeMessage property.
D. Filter the response results by specifying the created property in the request.
Free Access Full 350-901 Practice Exam Free
Looking for additional practice? Click here to access a full set of 350-901 practice exam free questions and continue building your skills across all exam domains.
Our question sets are updated regularly to ensure they stay aligned with the latest exam objectives—so be sure to visit often!
Good luck with your 350-901 certification journey!