350-701 Practice Exam Free – 50 Questions to Simulate the Real Exam
Are you getting ready for the 350-701 certification? Take your preparation to the next level with our 350-701 Practice Exam Free – a carefully designed set of 50 realistic exam-style questions to help you evaluate your knowledge and boost your confidence.
Using a 350-701 practice exam free is one of the best ways to:
- Experience the format and difficulty of the real exam
- Identify your strengths and focus on weak areas
- Improve your test-taking speed and accuracy
Below, you will find 50 realistic 350-701 practice exam free questions covering key exam topics. Each question reflects the structure and challenge of the actual exam.
Which component performs the resolution between the tunnel address and mGRE address in DMVPN?
A. GDOI
B. NBMA
C. NHRP
D. NHS
Which Cisco solution integrates Encrypted Traffic Analytics to perform enhanced visibility, promote compliance, shorten response times, and provide administrators with the information needed to provide educated and automated decisions to secure the environment?
A. Cisco ISE
B. Cisco SDN
C. Cisco Security Compliance Solution
D. Cisco DNA Center
A network administrator needs to find out what assets currently exist on the network. Third-party systems need to be able to feed host data into Cisco Firepower. What must be configured to accomplish this?
A. a Network Analysis policy to receive NetFlow data from the host
B. a File Analysis policy to send file data into Cisco Firepower
C. a Network Discovery policy to receive data from the host
D. a Threat Intelligence policy to download the data from the host
What is a description of microsegmentation?
A. Environments deploy a container orchestration platform, such as Kubernetes, to manage the application delivery.
B. Environments apply a zero-trust model and specify how applications on different servers or containers can communicate.
C. Environments deploy centrally managed host-based firewall rules on each server or container.
D. Environments implement private VLAN segmentation to group servers with similar applications.
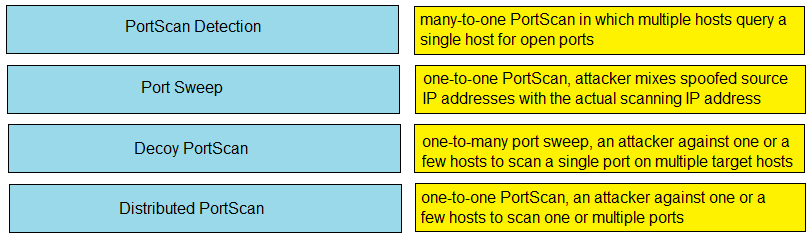
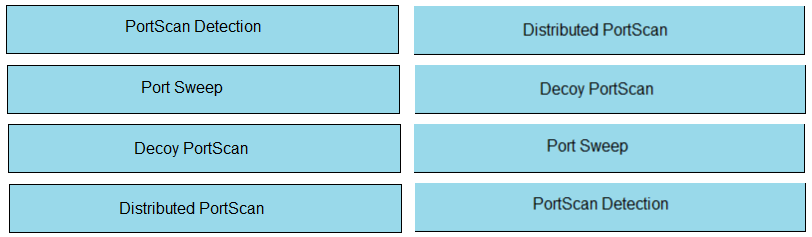
DRAG DROP - Drag and drop the Firepower Next Generation Intrusion Prevention System detectors from the left onto the correct definitions on the right. Select and Place:
An administrator configures a new destination list in Cisco Umbrella so that the organization can block specific domains for its devices. What should be done to ensure that all subdomains of domain.com are blocked?
A. Configure the domain.com address in the block list.
B. Configure the *.domain.com address in the block list.
C. Configure the *.com address in the block list.
D. Configure the *domain.com address in the block list.
Refer to the exhibit. Logins from internal users to a Cisco Adaptive Security Appliance firewall must be performed by using a TACACS server. The firewall is already configured. Which additional configuration must be performed to configure the TACACS+ server group with a key of Cisco4512!?
A.

B.

C.

D.

An engineer is trying to decide whether to use Cisco Umbrella. Cisco CloudLock. Cisco Stealthwatch. or Cisco AppDynamics Cloud Monitoring for visibility into data transfers as well as protection against data exfiltration. Which solution best meets these requirements?
A. Cisco AppDynamics Cloud Monitoring
B. Cisco CloudLock
C. Cisco Stealthwatch
D. Cisco Umbrella
What is an advantage of the Cisco Umbrella roaming client?
A. the ability to see all traffic without requiring TLS decryption
B. visibility into IP-based threats by tunneling suspicious IP connections
C. the ability to dynamically categorize traffic to previously uncategorized sites
D. visibility into traffic that is destined to sites within the office environment
What must be used to share data between multiple security products?
A. Cisco Platform Exchange Grid
B. Cisco Rapid Threat Containment
C. Cisco Stealthwatch Cloud
D. Cisco Advanced Malware Protection
Which type of data exfiltration technique encodes data in outbound DNS requests to specific servers and can be stopped by Cisco Umbrella?
A. DNS hijacking
B. cache poisoning
C. DNS tunneling
D. DNS flood attack
Which Cisco AnyConnect module is integrated with Splunk Enterprise to provide monitoring capabilities to administrators to allow them to view endpoint application usage?
A. AMP Enabler
B. Umbrella Roaming Security
C. ISE Posture
D. Network Visibility
Which attack is commonly associated with C and C++ programming languages?
A. cross-site scripting
B. water holing
C. DDoS
D. buffer overflow
An organization is moving toward the zero-trust model. Which Cisco solution enables administrators to deploy and control microsegmentation of endpoints that are connected to a Cisco Data Center Virtual Edge, Cisco Application Virtual Switch, Microsoft vSwitch, and VMware vSphere Distributed Switch?
A. Cisco Titration
B. Cisco DCNM
C. Cisco Stealthwatch
D. Cisco ACI
In which two ways does the Cisco Advanced Phishing Protection solution protect users? (Choose two.)
A. It prevents use of compromised accounts and social engineering.
B. It automatically removes malicious emails from users’ inbox.
C. It secures all passwords that are shared in video conferences.
D. It prevents trojan horse malware using sensors.
E. It prevents all zero-day attacks coming from the Internet.
What is the purpose of the My Devices Portal in a Cisco ISE environment?
A. to register new laptops and mobile devices
B. to manage and deploy antivirus definitions and patches on systems owned by the end user
C. to provision userless and agentless systems
D. to request a newly provisioned mobile device
Which baseline form of telemetry is recommended for network infrastructure devices?
A. SDNS
B. NetFlow
C. passive taps
D. SNMP
Which Secure Email Gateway implementation method segregates inbound and outbound email?
A. pair of logical listeners on a single physical interface with two unique logical IPv4 addresses and one IPv6 address
B. pair of logical IPv4 listeners and a pair of IPv6 listeners on two physically separate interfaces
C. one listener on one logical IPv4 address on a single logical interface
D. one listener on a single physical interface
A network engineer is tasked with configuring a Cisco ISE server to implement external authentication against Active Directory. What must be considered about the authentication requirements? (Choose two.)
A. RADIUS communication must be permitted between the ISE server and the domain controller.
B. The ISE account must be a domain administrator in Active Directory to perform JOIN operations.
C. Active Directory only supports user authentication by using MSCHAPv2.
D. LDAP communication must be permitted between the ISE server and the domain controller.
E. Active Directory supports user and machine authentication by using MSCHAPv2.
Which method is used on a Cisco IOS router to redirect traffic to the Cisco Secure Web Appliance for URL inspection?
A. WCCP
B. route map
C. PAC file
D. WPAD
Which cryptographic process provides origin confidentiality, integrity, and origin authentication for packets?
A. AH
B. IKEv1
C. IKEv2
D. ESP
DoS attacks are categorized as what?
A. flood attacks
B. virus attacks
C. trojan attacks
D. phishing attacks
Client workstations are experiencing extremely poor response time. An engineer suspects that an attacker is eavesdropping and making independent connections while relaying messages between victims to make them think they are talking to each other over a private connection. Which feature must be enabled and configured to provide relief from this type of attack?
A. Link Aggregation
B. Reverse ARP
C. private VLANs
D. Dynamic ARP Inspection
An engineer must set up 200 new laptops on a network and wants to prevent the users from moving their laptops around to simplify administration. Which switch port MAC address security setting must be used?
A. aging
B. static
C. sticky
D. maximum
Why should organizations migrate to an MFA strategy for authentication?
A. Single methods of authentication can be compromised more easily than MFA.
B. Biometrics authentication leads to the need for MFA due to its ability to be hacked easily.
C. MFA methods of authentication are never compromised.
D. MFA does not require any piece of evidence for an authentication mechanism.
Which technology should be used to help prevent an attacker from stealing usernames and passwords of users within an organization?
A. RADIUS-based REAP
B. fingerprinting
C. Dynamic ARP Inspection
D. multifactor authentication
A network engineer needs to select a VPN type that provides the most stringent security, multiple security associations for the connections, and efficient VPN establishment with the least bandwidth consumption. Why should the engineer select either FlexVPN or DMVPN for this environment?
A. DMVPN because it uses multiple SAs and FlexVPN does not.
B. DMVPN because it supports IKEv2 and FlexVPN does not.
C. FlexVPN because it supports IKEv2 and DMVPN does not.
D. FlexVPN because it uses multiple SAs and DMVPN does not.
What is an advantage of network telemetry over SNMP pulls?
A. security
B. scalability
C. accuracy
D. encapsulation
An engineer recently completed the system setup on a Cisco WSA. Which URL information does the system send to SensorBase Network servers?
A. complete URL, without obfuscating the path segments
B. URL information collected from clients that connect to the Cisco WSA using Cisco AnyConnect
C. none because SensorBase Network Participation is disabled by default
D. summarized server-name information and MD5-hashed path information
In which two ways does Easy Connect help control network access when used with Cisco TrustSec? (Choose two.)
A. It integrates with third-party products to provide better visibility throughout the network.
B. It allows for the assignment of Security Group Tags and does not require 802.1x to be configured on the switch or the endpoint.
C. It creates a dashboard in Cisco ISE that provides full visibility of all connected endpoints.
D. It allows for managed endpoints that authenticate to AD to be mapped to Security Groups (PassiveID).
E. It allows multiple security products to share information and work together to enhance security posture in the network.
Which action adds IOCs to customize detections for a new attack?
A. Use the initiate Endpoint 1OC scan feature to gather the IOC information and push it to clients.
B. Upload the 10Cs into the Installed Endpoint IOC feature within Cisco Secure Endpoint.
C. Add a custom advanced detection to include the 1OCs needed within Cisco Secure Endpoint.
D. Modify the base policy within Cisco Secure Endpoint to include simple custom detections.
Which function is performed by certificate authorities but is a limitation of registration authorities?
A. CRL publishing
B. certificate re-enrollment
C. verifying user identity
D. accepts enrollment requests
Which technology must be used to implement secure VPN connectivity among company branches over a private IP cloud with any-to-any scalable connectivity?
A. DMVPN
B. FlexVPN
C. IPsec DVTI
D. GET VPN
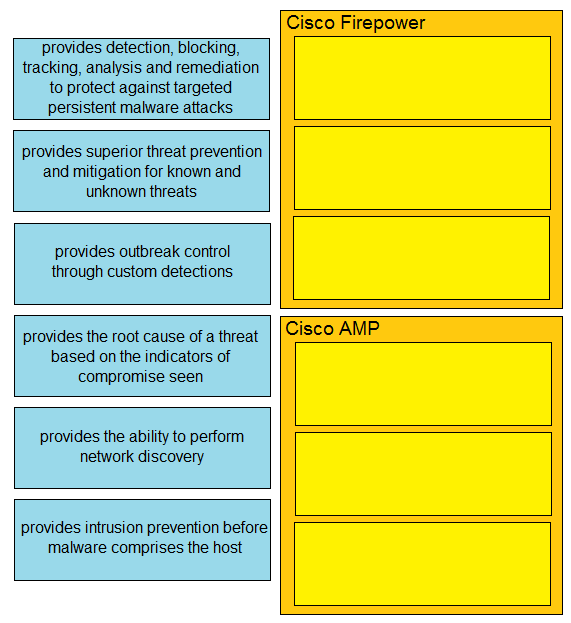
DRAG DROP - Drag and drop the capabilities of Cisco Firepower versus Cisco AMP from the left into the appropriate category on the right. Select and Place:
What is the difference between EPP and EDR?
A. Having an EDR solution gives an engineer the capability to flag offending files at the first sign of malicious behavior.
B. EPP focuses primarily on threats that have evaded front-line defenses that entered the environment.
C. Having an EPP solution allows an engineer to detect, investigate, and remediate modern threats.
D. EDR focuses solely on prevention at the perimeter.
Refer to the exhibit. An engineer must forward all web traffic sent from Client-SiteA to the monitoring server to build a baseline of expected traffic once a new Cisco Secure Web Appliance is deployed. What must be configured on the switch to meet the requirement?
A. ERSPAN
B. RSPAN
C. WCCP
D. SPAN
Which solution provides end-to-end visibility of applications and insights about application performance?
A. Cisco AppDynamics
B. Cisco Tetration
C. Cisco Secure Cloud Analytics
D. Cisco Cloudlock
In an IaaS cloud services model, which security function is the provider responsible for managing?
A. firewalling virtual machines
B. Internet proxy
C. hypervisor OS hardening
D. CASB
An administrator needs to configure the Cisco ASA via ASDM such that the network management system can actively monitor the host using SNMPv3. Which two tasks must be performed for this configuration? (Choose two.)
A. Add an SNMP USM entry.
B. Specify an SNMP user group.
C. Add an SNMP host access entry.
D. Specify the SNMP manager and UDP port.
E. Specify a community string.
An engineer needs a cloud solution that will monitor traffic, create incidents based on events, and integrate with other cloud solutions via an API. Which solution should be used to accomplish this goal?
A. CASB
B. Cisco Cloudlock
C. Adaptive MFA
D. SIEM
Which endpoint solution protects a user from a phishing attack?
A. Cisco AnyConnect with Network Access Manager module
B. Cisco AnyConnect with Umbrella Roaming Security module
C. Cisco Identity Services Engine
D. Cisco AnyConnect with ISE Posture module
A network engineer must create an access control list on a Cisco Adaptive Security Appliance firewall to permit TCP DNS traffic to the internet from the organization’s inside network 192.168.1.0/24. Which IOS command must be used to implement the access control list?
A.

B.

C.

D.

Which type of attack is MFA an effective deterrent for?
A. ping of death
B. phishing
C. teardrop
D. syn flood
What is a language format designed to exchange threat intelligence that can be transported over the TAXII protocol?
A. STIX
B. XMPP
C. pxGrid
D. SMTP
An engineer is configuring a Cisco Secure Email Cloud Gateway instance to send logs to an external server for auditing. For security purposes, a username and SSH key with the fingerprint d0:46:03:8e:d7:f1:bb:9b:33:13:94:60:49:da:9b:e3 has been generated on the remote log server that accepts only the SSHv2 protocol. Which log retrieval method must be configured in the log subscription?
A. syslog push
B. manually download
C. SCP push
D. FTP push
A networking team must harden an organization's network from VLAN hopping attacks. The team disables Dynamic Trunking Protocol and puts any unused ports in an unused VLAN. A trunk port is used as a trunk link. What must the team configure next to harden the network against VLAN hopping attacks?
A. dedicated VLAN ID for all trunk ports
B. disable STP on the network devices
C. DHCP snooping on all the switches
D. enable port-based network access control
An administrator is establishing a new site-to-site VPN connection on a Cisco IOS router. The organization needs to ensure that the ISAKMP key on the hub is used only for terminating traffic from the IP address of 172.19.20.24. Which command on the hub will allow the administrator to accomplish this?
A. crypto isakmp identity address 172.19.20.24
B. crypto ca identity 172.19.20.24
C. crypto enrollment peer address 172.19.20.24
D. crypto isakmp key Cisco0123456789 172.19.20.24
What is a characteristic of traffic storm control behavior?
A. Traffic storm control drops all broadcast and multicast traffic if the combined traffic exceeds the level within the interval.
B. Traffic storm control cannot determine if the packet is unicast or broadcast.
C. Traffic storm control monitors incoming traffic levels over a 10-second traffic storm control interval.
D. Traffic storm control uses the Individual/Group bit in the packet source address to determine if the packet is unicast or broadcast.
An attacker needs to perform reconnaissance on a target system to help gain access to it. The system has weak passwords, no encryption on the VPN links, and software bugs on the system's applications. Which vulnerability allows the attacker to see the passwords being transmitted in clear text?
A. unencrypted links for traffic
B. weak passwords for authentication
C. improper file security
D. software bugs on applications
On which part of the IT environment does DevSecOps focus?
A. application development
B. wireless network
C. data center
D. perimeter network
Free Access Full 350-701 Practice Exam Free
Looking for additional practice? Click here to access a full set of 350-701 practice exam free questions and continue building your skills across all exam domains.
Our question sets are updated regularly to ensure they stay aligned with the latest exam objectives—so be sure to visit often!
Good luck with your 350-701 certification journey!