350-401 Practice Exam Free – 50 Questions to Simulate the Real Exam
Are you getting ready for the 350-401 certification? Take your preparation to the next level with our 350-401 Practice Exam Free – a carefully designed set of 50 realistic exam-style questions to help you evaluate your knowledge and boost your confidence.
Using a 350-401 practice exam free is one of the best ways to:
- Experience the format and difficulty of the real exam
- Identify your strengths and focus on weak areas
- Improve your test-taking speed and accuracy
Below, you will find 50 realistic 350-401 practice exam free questions covering key exam topics. Each question reflects the structure and challenge of the actual exam.
A client requests a wireless solution for remote branch offices to eliminate the need for a local controller at each branch. The branch users require local termination in a specifc VLAN for local internet breakout. Which solution must be deployed?
A. central switched
B. FlexConnect local switching
C. auto-anchor mobility
D. asymmetric tunneling
An engineer must construct an access list for a Cisco Catalyst 9800 Series WLC that will redirect wireless guest users to a splash page that is hosted on a Cisco ISE server. The Cisco ISE servers are hosted at 10.9.11.144 and 10.1.11.141. Which access list meets the requirements?
A.

B.

C.

D.

Refer to the exhibit.Running the script causes the output in the exhibit. What should be the first line of the script?
A. from ncclient import manager
B. import manager
C. from ncclient import *
D. ncclient manager import
An engineer must protect their company against ransomware attacks. Which solution allows the engineer to block the execution stage and prevent file encryption?
A. Use Cisco Firepower and block traffic to TOR networks.
B. Use Cisco AMP deployment with the Malicious Activity Protection engine enabled.
C. Use Cisco Firepower with Intrusion Policy and snort rules blocking SMB exploitation.
D. Use Cisco AMP deployment with the Exploit Prevention engine enabled.
Which two pieces of information are necessary to compute SNR? (Choose two.)
A. transmit power
B. noise floor
C. EIRP
D. RSSI
E. antenna gain
Refer to the exhibit. Which command set completes the ERSPAN session configuration?
A. monitor session 11 type erspan-destination destination interface GigabitEthemet4 source erspan-id 11 ip address 10.10.10.10
B. monitor session 12 type erspan-destination destination interface GigabitEthernet4 source erspan-id 12 ip address 10.10.10.10
C. monitor session 11 type erspan-destination destination interface GigabitEthernet4 source erspan-id 12 ip address 10.100.10.10
D. monitor session 12 type erspan-destination destination interface GigabitEthernet4 source erspan-id 11 ip address 10.10.10.10 C
What is one role of the VTEP in a VXLAN environment?
A. to maintain VLAN configuration consistency
B. to forward packets to non-LISP sites
C. to provide EID-to-RLOC mapping
D. to encapsulate the tunnel
An engineer is implementing a new SSID on a Cisco Catalyst 9800 Series WLC that must be broadcast on 6 GHz radios. Users will be required to use EAP-TLS to authenticate. Which wireless Layer 2 security method is required?
A. WPA2 Enterprise
B. WPA2 Personal
C. WPA3 Enterprise
D. WPA3 Personal
Refer to the exhibit.What is generated by the script?
A. the router processes
B. the cdp neighbors
C. the routing table
D. the running configuration
What is a benefit of data modeling languages like YANG?
A. They create more secure and efficient SNMP OIDs.
B. They provide a standardized data structure, which results in configuration scalability and consistency.
C. They enable programmers to change or write their own applications within the device operating system.
D. They make the CLI simpler and more efficient.
Refer to the exhibit.Which configuration must be applied to ensure that the preferred path for traffic from AS 65010 toward AS 65020 uses the R2 to R4 path?
A. R4(config)# router bgp 65020 –
R4(config-router)# bgp default local-preference 300
R5(config)# router bgp 65020 –
R5(config-router)# bgp default local-preference 200
B. R2(config)# router bgp 65010 –
R2(config-router)# bgp default local-preference 300
R1(config)# router bgp 65010 –
R1(config-router)# bgp default local-preference 200
C. R2(config)# router bgp 65010 –
R2(config-router)# bgp default local-preference 200
R1(config)# router bgp 65010 –
R1(config-router)# bgp default local-preference 300
D. R4(config)# router bgp 65020 –
R4(config-router)# bgp default local-preference 200
R5(config)# router bgp 65020 –
R5(config-router)# bgp default local-preference 300
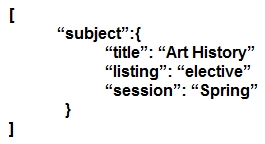
Which JSON script is properly formatted?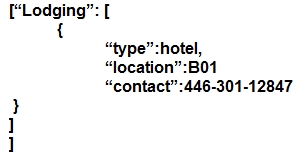
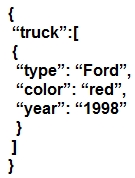
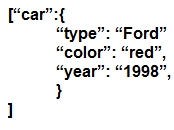
A.
Which protocol infers that a YANG data model is being used?
A. SNMP
B. RESTCONF
C. REST
D. NX-API
Refer to the exhibit.Security policy requires all idle exec sessions to be terminated in 600 seconds. Which configuration achieves this goal?
A. line vty 0 15 absolute-timeout 600
B. line vty 0 15 no exec-timeout
C. line vty 0 15 exec-timeout 10 0
D. line vty 0 4 exec-timeout 600
An engineer measures the Wi-Fi coverage at a customer site The RSSI values are recorded as follows: · Location A: -72 dBm · Location B: -75 dBm · Location C -65 dBm · Location D -80 dBm Which two statements does the engineer use to explain these values to the customer? (Choose two.)
A. The signal strength at location C is too weak to support web sur ng
B. Location D has the strongest RF signal strength
C. The RF signal strength at location B is 50% weaker than location A
D. The RF signal strength at location C is 10 times stronger than location B
E. The signal strength at location B is 10 dB better than location C
Which feature allows clients to perform Layer 2 roaming between wireless controllers?
A. mobility groups
B. N+1 high availability
C. RF grouping
D. SSO
Which of the following are valid statements when configuring Nonstop Forwarding (NSF) with Stateful Switchover (SSO) on a Cisco device? (Choose two.)
A. supports multicast routing protocols
B. Supports IPv4 and IPv6
C. Nonstop Forwarding requires SSO to also be configured
D. HSRP is not supported with NSF/SSO
E. Improper implementation of NSF/SSO can result in routing loops
You need to weigh the pros and cons of deploying a premise-based data center versus using a cloud-based data center deployment. What is an advantage of using a premise-based solution? (Choose two.)
A. Lower application latency for end users
B. Easily scalable
C. Lower capital costs
D. Reduced deployment times
E. Increased control over the environment
Refer to the exhibit. An engineer builds an EEM script to apply an access list. Which statement must be added to complete the script?
A. action 6.0 cli command “ip access-list extended 101”
B. action 3.1 cli command “ip access-list extended 101”
C. event none
D. action 2.1 cli command “ip access-list extended 101”
What is a benefit of deploying an on-premises infrastructure versus a cloud infrastructure deployment?
A. ability to quickly increase compute power without the need to install additional hardware
B. less power and cooling resources needed to run infrastructure on-premises
C. faster deployment times because additional infrastructure does not need to be purchased
D. lower latency between systems that are physically located near each other
Refer to the exhibit.What is output by this code?
A. 0 5
B. 0 1 2 3 4 5
C. 0 1 2 3 4
D. (0,5)
Refer to the exhibit. Which two commands ensure that DSW1 becomes the root bridge for VLAN 10 and 20? (Choose two.)
A. spanning-tree mst 1 priority 4096
B. spanning-tree mst 1 root primary
C. spanning-tree mst vlan 10,20 priority root
D. spanning-tree mst 1 priority 1
E. spanning-tree mstp vlan 10,20 root primary
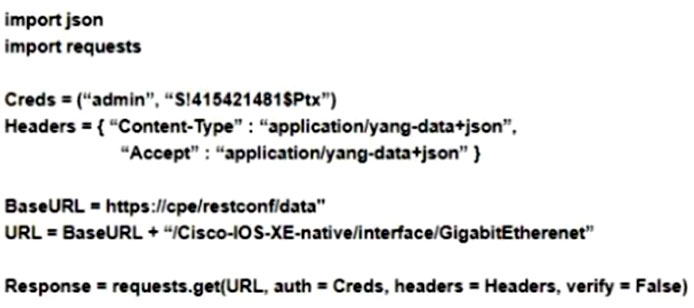
Which Python code snippet must be added to the script to save the returned configuration as a JSON-formatted file?
A. 
B. 
C. 
D. 
An engineer is troubleshooting the AP join process using DNS. Which FQDN must be resolvable on the network for the access points to successfully register to the WLC?
A. wlchostname.domain.com
B. cisco-capwap-controller.domain.com
C. ap-manager.domain.com
D. primary-wlc.domain.com
Refer to the exhibit. After configuring HSRP an engineer enters the show standby command. Which two facts are derived from the output? (Choose two.)
A. R2 becomes the active router after the hold time expires.
B. If Fa0/0 is shut down, the HSRP priority on R2 becomes 80.
C. R2 Fa1/0 regains the primary role when the link comes back up.
D. The router with IP 10.10.1.3 is active because it has a higher IP address.
E. R2 is using the default HSRP hello and hold timers.
Refer to the exhibit. An administrator troubleshoots intermittent connectivity from internal hosts to an external public server. Some internal hosts can connect to the server while others receive an ICMP Host Unreachable message, and these hosts change over time. What is the cause of this issue?
A. The NAT ACL and NAT pool share the same name.
B. The translation does not use address overloading.
C. The NAT ACL does not match all internal hosts.
D. The NAT pool netmask is excessively wide.
Refer to the exhibit. An engineer is configuring WebAuth on a Cisco Catalyst 9800 Series WL
A. The engineer has purchased a third-party certificate using the FQDN of the WLC as the CN and intends to use it on the WebAuth splash page. What must be configured so that the clients do not receive a certificate error?
B. Virtual IPv4 Hostname must match the CN of the certificate
C. Virtual IPv4 Address must be set to a routable address
D. Web Auth Intercept HTTPs must be enabled
E. Trustpoint must be set to the management certificate of the WLC
An engineer is configuring GigabitEthernet1/0/0 for VRRP. When the router has the highest priority in group 5, it must assume the master role. Which command set should the engineer add to the configuration to accomplish this task? interface GigabitEthernet1/0/0 description To IDF A 38- 70-774-10 ip address 172.16.13.2 255.255.255.0
A. standby 5 ip 172.16.13.254 standby 5 priority 100 standby 5 track 1 decrement 10
B. standby 5 ip 172.16.13.254 standby 5 priority 100 standby 5 preempt
C. vrrp 5 ip 172.16.13.254 vrrp 5 priority 100
D. vrrp 5 ip 172.16.13.254 255.255.255.0 vrrp 5 track 1 decrement 10 vrrp 5 preempt C
Refer to the exhibit. The network administrator must be able to perform configuration changes when all the RADIUS servers are unreachable. Which configuration allows all commands to be authorized if the user has successfully authenticated?
A. aaa authentication login default group radius local none
B. aaa authorization exec default group radius
C. aaa authorization exec default group radius if-authenticated
D. aaa authorization exec default group radius none
Refer to the exhibit. Which command must be configured for RESTCONF to operate on port 8888?
A. restconf port 8888
B. ip http restconf port 8888
C. ip http port 8888
D. restconf http port 8888
Which method displays text directly into the active console with a synchronous EEM applet policy?
A. event manager applet boom event syslog pattern ‘UP’ action 1.0 syslog priority direct msg ‘logging directly to console’
B. event manager applet boom event syslog pattern ‘UP’ action 1.0 gets ‘logging directly to console’
C. event manager applet boom event syslog pattern ‘UP’ action 1.0 string ‘logging directly to console’
D. event manager applet boom event syslog pattern ‘UP’ action 1.0 puts ‘logging directly to console’ D
What are two characteristics of vManage APIs? (Choose two.)
A. Northbound API is based on RESTCONF and JSON.
B. Southbound API is based on NETCONF and XML.
C. Southbound API is based on RESTCONF and JSON.
D. Southbound API is based on OMP and DTLS.
E. Northbound API is RESTful using JSON.
Which function does a virtual switch provide?
A. RAID storage for virtual machines
B. connectivity between virtual machines
C. CPU context switching for multitasking between virtual machines
D. emulation of power for virtual machines
What is the result when an active route processor fails in a design that combines NSF with SSO?
A. The standby route processor temporarily forwards packets until route convergence is complete.
B. An NSF-aware device immediately updates the standby route processor RIB without churning the network.
C. An NSF-capable device immediately updates the standby route processor RIB without churning the network.
D. The standby route processor immediately takes control and forwards packets along known routes D
A client with IP address 209.165.201.25 must access a web server on port 80 at 209.165.200.225. To allow this traffic, an engineer must add a statement to an access control list that is applied in the inbound direction on the port connecting to the web server. Which statement allows this traffic?
A. permit tcp host 209.165.200.225 lt 80 host 209.165.201.25
B. permit tcp host 209.165.201.25 host 209.165.200.225 eq 80
C. permit tcp host 209.165.200.225 eq 80 host 209.165.201.25
D. permit tcp host 209.165.200.225 host 209.165.201.25 eq 80
Which resource must the hypervisor make available to the virtual machines?
A. bandwidth
B. IP address
C. processor
D. secure access
Refer to the exhibit. What is the effect of introducing the sampler feature into the Flexible NetFlow configuration on the router?
A. NetFlow updates to the collector are sent 50% less frequently.
B. Every second IPv4 packet is forwarded to the collector for inspection.
C. CPU and memory utilization are reduced when compared with what is required for full NetFlow.
D. The resolution of sampling data increases, but it requires more performance from the router.
What is required for a virtual machine to run?
A. a Type 1 hypervisor and a host operating system
B. a hypervisor and physical server hardware
C. only a Type 1 hypervisor
D. only a Type 2 hypervisor
Refer to the exhibit. An engineer must create a configuration that executes the show run command and then terminates the session when user CCNP logs in. Which configuration change is required?
A. Add the access-class keyword to the username command.
B. Add the autocommand keyword to the aaa authentication command.
C. Add the access-class keyword to the aaa authentication command.
D. Add the autocommand keyword to the username command.
Which feature is offered by the Cisco Advanced Malware Protection for Endpoints solution?
A. File Sandboxing
B. NetFlow
C. TrustSec
D. DNS Protection
Refer to the exhibit. PC-1 must access the web server on port 8080. To allow this traffic, which statement must be added to an access control list that is applied on SW2 port G0/0 in the inbound direction?
A. permit tcp host 172.16.0.2 host 192.168.0.5 eq 8080
B. permit tcp host 192.168.0.5 host 172.16.0.2 eq 8080
C. permit tcp host 192.168.0.5 eq 8080 host 172.16.0.2
D. permit tcp host 192.168.0.5 lt 8080 host 172.16.0.2
Which security actions must be implemented to prevent an API injection attack?
A. Log and monitor failed attempts.
B. Use password hash with biometric authentication.
C. Validate, filter, and sanitize all incoming data.
D. Use short-lived access tokens and authenticate the apps.
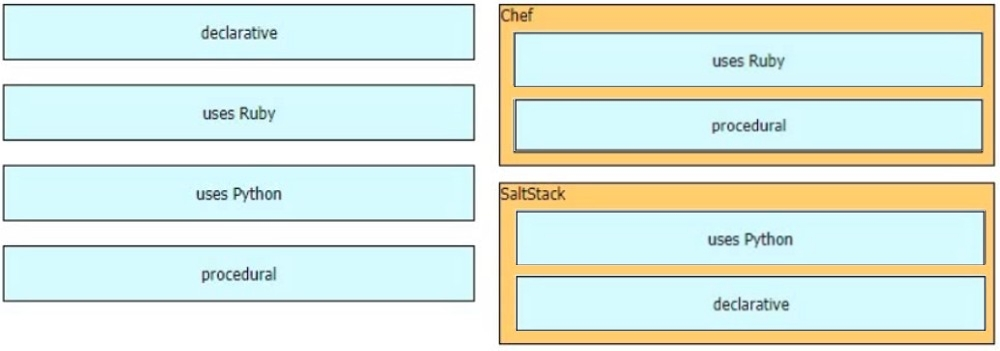
Drag and drop the characteristics from the left onto the orchestration tools that they describe on the right.
Select and Place:
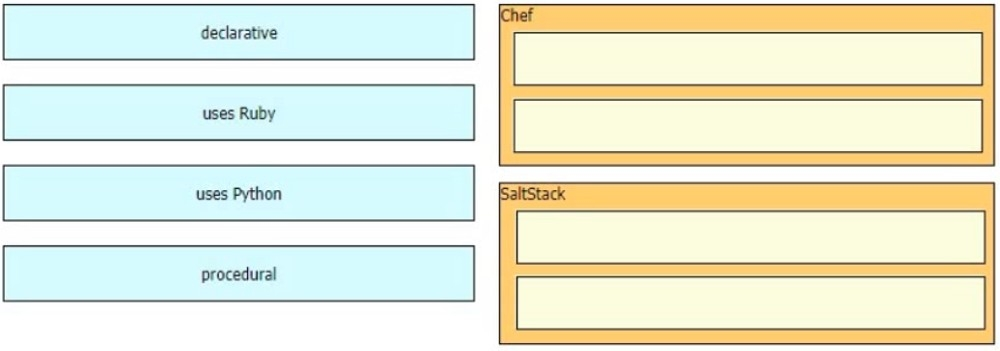
An engineer must create a new SSID on a Cisco 9800 wireless LAN controller. The client has asked to use a pre-shared key for authentication. Which profile must the engineer edit to achieve this requirement?
A. Policy
B. RF
C. Flex
D. WLAN
Which two actions, when applied in the LAN network segment, will facilitate Layer 3 CAPWAP discovery for lightweight AP? (Choose two.)
A. Utilize DHCP option 43.
B. Utilize DHCP option 17.
C. configure an ip helper-address on the router interface.
D. Enable port security on the switch port.
E. configure WLC IP address on LAN switch
Where is radio resource management performed in a Cisco SD-Access wireless solution?
A. DNA Center
B. control plane node
C. wireless controller
D. Cisco CMX
A wireless administrator must create a new web authentication corporate SSID that will be using ISE as the external RADIUS server. The guest VLAN must be speci ed after the authentication completes. Which action must be performed to allow the ISE server to specify the guest VLAN?
A. Enable AAA Override.
B. Enable Network Access Control State.
C. Set AAA Policy name.
D. Set RADIUS Pro ling.
When a DNS host record is configured for a new Cisco AireOS WLC, which hostname must be added to allow APs to successfully discover the WLC?
A. CONTROLLER-CAPWAP-CISCO
B. CISCO-CONTROLLER-CAPWAP
C. CAPWAP-CISCO-CONTROLLER
D. CISCO-CAPWAP-CONTROLLER
A customer requests a design that includes GLBP as the FHRP. The network architect discovers that the members of the GLBP group have different throughput capabilities. Which GLBP load balancing method supports this environment?
A. round robin
B. host dependent
C. weighted
D. least connection
Why does the vBond orchestrator have a public IP?
A. to allow for global reachability from all WAN Edges in the Cisco SD-WAN and to facilitate NAT traversal
B. to provide access to Cisco Smart Licensing servers for license enablement
C. to enable vBond to learn the public IP of WAN Edge devices that are behind NAT gateways or in private address space
D. to facilitate downloading and distribution of operational and security patches
Free Access Full 350-401 Practice Exam Free
Looking for additional practice? Click here to access a full set of 350-401 practice exam free questions and continue building your skills across all exam domains.
Our question sets are updated regularly to ensure they stay aligned with the latest exam objectives—so be sure to visit often!
Good luck with your 350-401 certification journey!