300-630 Practice Exam Free – 50 Questions to Simulate the Real Exam
Are you getting ready for the 300-630 certification? Take your preparation to the next level with our 300-630 Practice Exam Free – a carefully designed set of 50 realistic exam-style questions to help you evaluate your knowledge and boost your confidence.
Using a 300-630 practice exam free is one of the best ways to:
- Experience the format and difficulty of the real exam
- Identify your strengths and focus on weak areas
- Improve your test-taking speed and accuracy
Below, you will find 50 realistic 300-630 practice exam free questions covering key exam topics. Each question reflects the structure and challenge of the actual exam.
An engineer must limit local and remote endpoint learning to the bridge domain subnet. Which action should be taken inside the Cisco APIC?
A. Disable Remote EP Learn
B. Enable Enforce Subnet Check
C. Disable Endpoint Dataplane Learning
D. Enable Limit IP Learning to Subnet
Which protocol must be applied between the inter-pod network and spines within each pod to allow broadcast traffic replication between Cisco ACI pods?
A. MSDP Peering
B. Multicast BGP
C. Bidirectional PIM
D. IGMP Registration
An engineer configures Cisco ACI Multi-Site and must specify the control plane TEP IP for spines. Which statement describes control plane TEP IP in this situation?
A. The unique IP address is defined on each spine node that belongs to a fabric and is used to establish MP-BGP EVPN and VPNv4 adjacencies with the spine nodes in remote sites.
B. The unique IP address is defined on each spine node that belongs to a fabric and is used to establish VXLAN adjacencies with the spine nodes in remote sites.
C. The common anycast address is shared by all the spine nodes in the same site and is used to perform headend replication for BUM traffic.
D. The common anycast address is shared by all the spine nodes at the same site and is used to source and receive unicast VXLAN data plane traffic.
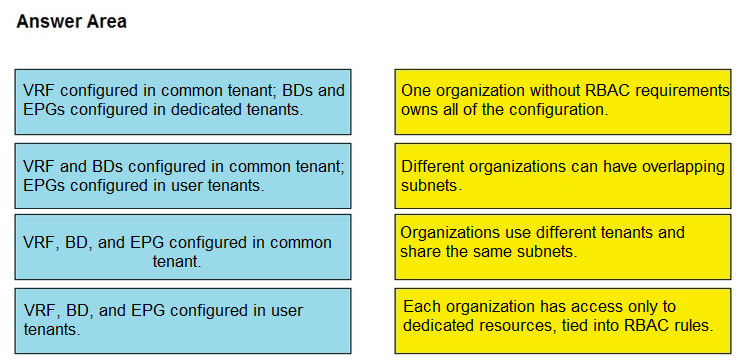
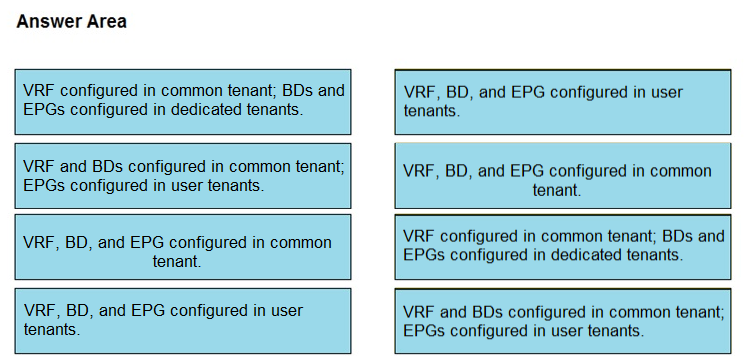
DRAG DROP - Drag and drop the tenant implementation designs from the left onto the outcomes of the design when a greenfield Cisco ACI fabric is deployed on the right. Select and Place:
How is the traffic directed to the firewall pair in a two-site Multi-Pod deployment with an active/standby firewall pair stretched across pods?
A. to the pod with the active service node
B. to a collector in the Inter-Pod Network
C. to the pod designated as the primary pod
D. to the local service node for processing
What is a design implication for Cisco ACI using an application-centric approach?
A. Multiple VLANs and/or multiple EPGs are under one bridge domain
B. VLAN numbers are in the names of the bridge domain and EPG objects
C. One EPG is mapped to multiple bridge domains
D. One VLAN equals one EPG equals one bridge domain
Which mechanism is used by ACI spine switches to maintain a consistent copy of the endpoint address and location information?
A. COOP
B. ISIS
C. BD
D. OSPF
Refer to the exhibit. Which type of design approach is shown?
A. traditional VLAN/subnet model
B. edge-core-edge model
C. application-centric
D. network-centric
Which feature should be disabled on a bridge domain when a default gateway for endpoints is on an external device instead of a Cisco ACI bridge domain SVI?
A. unicast routing
B. ARP flooding
C. unknown unicast flooding
D. proxy ARP
In a Cisco ACI Multi-Site fabric, the Inter-Site BUM Traffic Allow option is enabled in a specific stretched bridge domain. What is used to forward BUM traffic to all endpoints in the same broadcast domain?
A. ingress replication on the spines in the source site
B. egress replication on the source leaf switches
C. egress replication on the destination leaf switches
D. ingress replication on the spines in the destination site
Refer to the exhibit. Which two configuration steps are required in ISN for Cisco ACI Multi-Site setup? (Choose two.)
A. Connect Spine2 to ISN routers.
B. Configure BIDIR-PIM throughout the ISN
C. Increase ISN MTU to support the maximum MTU that is sent by endpoints
D. Configure OSPF between spines and ISN routers
E. Enable IGMPv3 on ISN routers
Refer to the exhibit. An engineer must implement a solution to ensure that ingress and egress traffic flows are symmetric for all stretched bridge domains in the customer multisite architecture. Which configuration accomplishes this goal?
A. Configure host route advertisement on the bridge domains.
B. Enable anycast services to the firewalls in both fabrics.
C. Implement a policy-based redirect using a service graph.
D. Add a new stretched external EPG to the existing L3Outs.
Refer to the exhibit. Which configuration set must be applied to filter 1 to enable SSH communication between Web_EPG to App_EPG?
A. Apply Both Directions: Disabled -Reverse Filter Ports: Enabled
B. Apply Both Directions: Enabled -Reverse Filter Ports: Enabled
C. Apply Both Directions: Disabled -Reverse Filter Ports: Disabled
D. Apply Both Directions: Enabled -Reverse Filter Ports: Disabled
Which device replicates Broadcast, Unicast, and Multicast (BUM) frames to all remote sites in a Cisco ACI Multi-Site with multiple stretched bridge domains?
A. remote spine node that translates the VNID to the locally significant value
B. receiving leaf that learns the location for the sourced BUM traffic
C. source leaf that floods the traffic to the specific multicast group or GIPo
D. local spine that is elected the designated forwarder for each bridge domain
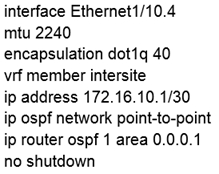
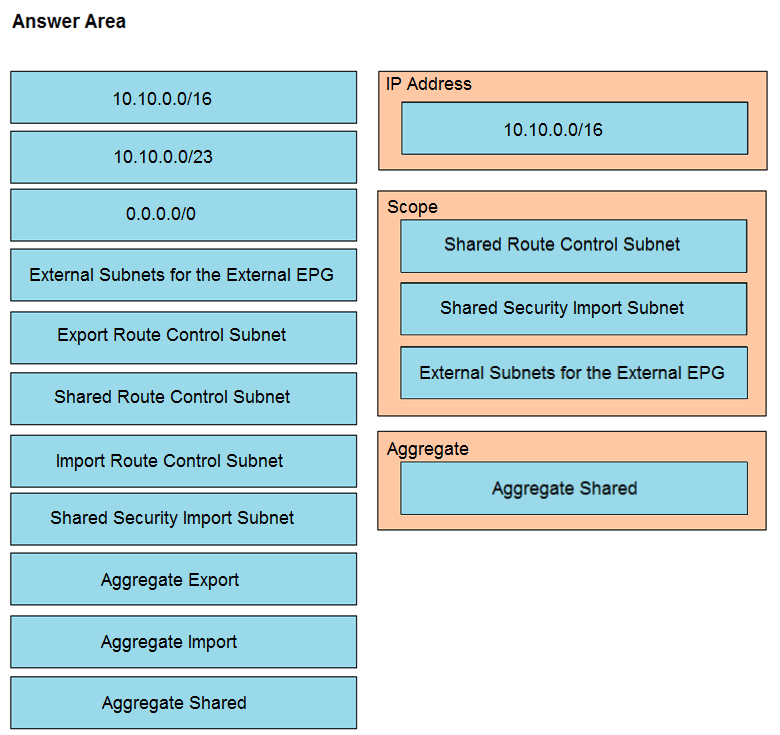
Refer to the exhibit. An engineer must have communication between EPG1 in VRF1 and External EPG in VRF2. Which three actions should be taken for the defined subnets in the L3Out External EPG to accomplish this goal? (Choose three.)
A. Enable Shared Route Control Subnet
B. Enable External Subnets for External EPG
C. Enable Export Route Control Subnet
D. Enable Shared Security Import Subnet
E. Enable Aggregate Shared Routes
F. Enable Import Route Control Subnet
What is a characteristic of application-centric design in Cisco ACI?
A. One-to-one mapping between EPGs and bridge domains is enforced.
B. A bridge domain has only one subnet.
C. EPGs represent different application tiers.
D. It simplifies gradual migration from a traditional network.
Refer to the exhibit. An administrator configures inter-VRF route leaking between Production:vrf-prod and Non-Production:vrf-nonprod. However, the route in the Non-Production:vrf-nonprod VRF to the production tenant is missing. Which action resolves the VRF route leaking issue?
A. Enable the Shared between VRFs option for the BD subnet in the production VRF.
B. Change the contract scope to Global.
C. Enable the Shared between VRFs option for the EPG subnet in the non-production VRF.
D. Export the contract from provider to consumer tenant.
Refer to the exhibit. A company merges three of its departments: CORP, HR, and SERVICES. Currently, the connectivity between departments is achieved by using VRF route leaking. The requirement is to redesign the Cisco ACI networking architecture to communicate between EPGs and BDs from any tenant without configuring contracts or VRF route leaking. Which configuration meets these criteria?
A. Implement an enforced VRF in the common tenant and map all required BDs to it
B. Configure an enforced VRF in the user tenant and map all required EPGs to it.
C. Implement an unenforced VRF in the common tenant and map all required BDs to it.
D. Configure an unenforced VRF in the user tenant and map all required EPGs to it.
A company must connect three Cisco ACI data centers by using Cisco ACI Multi-Site. An engineer must configure the Inter-Site Network (ISN) between the existing sites. Which two configuration steps must be taken to implement the ISN? (Choose two.)
A. Configure encapsulation VLAN-4 between the routers and spine nodes.
B. Configure OSPF on subinterfaces on routers that are directly connected with spine nodes.
C. Configure ISN site extension on Cisco routers in the network.
D. Configure OSPF on all ISN routers.
E. Configure BIDIR-PIM on all ISN routers.
What are two characteristics of network-centric design in Cisco ACI? (Choose two.)
A. There is open communication between EPGs
B. EPGs are used for microsegmentation
C. EPGs are different security zones
D. Applications define the network requirements
E. A bridge domain has one subnet and one EPG
An organization migrates its virtualized servers from a legacy environment to Cisco ACI. VM1 is incorrectly attached to PortGroup IT|3TierApp|Web. Which action limits IP address learning in BD1?
A. Enable Enforce Subnet Check
B. Enable Rouge Endpoint Control
C. Enable GARP-based EP Move Detection Mode
D. Disable Remote EP Learn
Which action should be taken in Cisco ACI to reassign a unique globally scoped pcTag to an EPG that provides a global contract?
A. Configure subnets that are treated as virtual IP
B. Configure subnets that advertise externally
C. Configure subnets that are shared between VRFs
D. Configure subnets that are private to VRF
What is the purpose of the Forwarding Tag (FTAG) in Cisco ACI?
A. FTAG is used in Cisco ACI to add a label to the iVXLAN traffic in the fabric to apply the correct policy.
B. FTAG is used in Cisco ACI to add a label to the VXLAN traffic in the fabric to apply the correct policy.
C. FTAG trees in Cisco ACI are used to load balance unicast traffic.
D. FTAG trees in Cisco ACI are used to load balance mutli-destination traffic.
An engineer configures a Cisco ACI Multi-Pod for disaster recovery. Which action should be taken for the new nodes to be discoverable by the existing Cisco APICs?
A. Enable subinterfaces with dot1q tagging on all links between the IPN routers.
B. Configure IGMPv3 on the interfaces of IPN routers that face the Cisco ACI spine.
C. Enable DHCP relay on all links that are connected to Cisco ACI spines on IPN devices.
D. Configure BGP as the underlay protocol in IPN.
What is a characteristic of a stretched bridge domain solution between Cisco ACI sites with Layer 2 flood enabled?
A. BUM traffic between sites leverages ISN multicast replication.
B. The solution reduces control plane overhead.
C. Spine head-end replication is used to forward BUM traffic between sites.
D. Contracts are local to the provided site.
Refer to the exhibit. Which three actions should be taken to implement the vPC in the Cisco ACI fabric? (Choose three.)
A. Select a common vPC interface policy group
B. Select individual interface profiles
C. Select common interface profiles
D. Select individual switch profiles
E. Select common switch profiles
Refer to the exhibit. The requirement is to prefer the local PBR node and redirect the traffic to the remote pod PBR node in the case of catastrophic node failure. Which configuration meets these requirements?
A. location-based PBRhost route advertisementresilient hashing
B. symmetric PBRlocation-based PBRresilient hashing
C. symmetric PBRunidirectional PBRresilient hashing
D. location-based PBRhost route advertisementnode tracking
The engineer notices frequent MAC and IP address moves between different leaf switch ports. Which action prevents this problem from occurring?
A. Disable enforce subnet check.
B. Disable IP bridge domain enforcement.
C. Enable endpoint loop protection.
D. Enable rogue endpoint control.
Refer to the exhibit. A customer experiences resource overconsumption on one of its border leaf switches. Which action should be taken to reduce the consumption on this switch?
A. Disable VRF Policy Control Enforcement
B. Disable IP Data Plane Learning
C. Migrate L3Outs to another switch
D. Disable Remote EP Learning
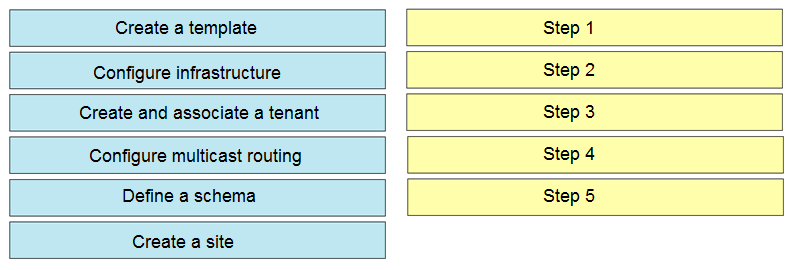
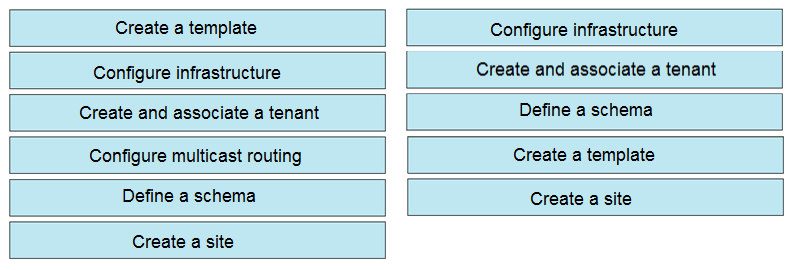
DRAG DROP - An engineer deploys a Cisco ACI Multi-Site Orchestrator for the first time. Drag and drop the actions from the left into the steps on the right to add a site and deploy new Cisco ACI objects to the fabric. Not all actions are used. Select and Place:
An engineer deployed a Cisco ACI fabric and noticed that the fabric learns endpoints from subnets that are not configured on a bridge domain. To meet strict security requirements, the engineer must prevent this behavior. Which action must be taken to prevent this behavior?
A. Activate Enable Data Plane Endpoint Learning
B. Implement Pervasive Gateway
C. Configure Static Binding
D. Enable Enforce Subnet Check
Refer to the exhibit. A customer implements Cisco ACI Multi-Site with default MTU settings between two sites. Which configuration should be applied on the interface Eth1/10 on the ISN-1 device? A.
B.
C.
D.
Refer to the exhibit. Which two configurations enable inter-VRF communication? (Choose two.)
A. Set the subnet scope to Shared Between VRFs
B. Enable Advertise Externally under the subnet scope
C. Change the contract scope to Tenant
D. Change the subject scope to VRF
E. Export the contract and import as a contract interface
A cloud provider must make a pair of firewalls available to all tenants. Each tenant defines its own service graph. Where should the Layer 4 to Layer 7 service be configured to accomplish this goal?
A. management tenant
B. infrastructure tenant
C. user tenant
D. common tenant
Refer to the exhibit. Which method does Cisco ACI fabric use to forward L2 Unknown Unicast packets?
A. The source leaf sends the traffic to all ports in BD.
B. Packets are dropped if dMAC is absent in COOP.
C. The traffic is flooded using VRF Outer Multicast Group ID.
D. Traffic is flooded to all Layer 2 ports of ACI fabric.
Where are STP BPDUs flooded in Cisco ACI fabric?
A. in the bridge domain VLAN
B. in the native VLAN ID
C. in the access encapsulation VLAN part of different VLAN pools
D. in the VNID that is assigned to the FD VLAN
An engineer creates the objects that must be deployed at each site in Cisco ACI Multi-Site Orchestrator. Which action should be taken before the schema can be associated with the newly configured site?
A. Attach the templates to the newly configured site
B. Configure a provider for the Cisco ACI Multi-Site Orchestrator
C. Import existing policies from an existing tenant to Cisco ACI Multi-Site Orchestrator
D. Configure the Infra Site-Specific Settings
Refer to the exhibit. Which configuration mode must be selected for the VMM vSwitch Port Channel policy to avoid MAC flapping on the Cisco UCS Fls and Cisco ACI leaf switches?
A. LACP Passive
B. MAC Pinning
C. LACP Active
D. Static Channel ג€” Mode On
An organization deploys active-active data centers and active-standby firewalls in each data center. Which action should be taken in a Cisco ACI Multi-Pod to maintain traffic symmetry through the firewalls?
A. Enable Endpoint Dataplane Learning
B. Disable service node Health Tracking
C. Enable Pod ID Aware Redirection
D. Disable Resilient Hashing
A host that is connected to a Cisco ACI fabric leaf switch sends an ARP request. Which transmission method does the ingress switch use to send the ARP requests?
A. anycast
B. broadcast
C. multicast
D. unicast
Refer to the exhibit. The client endpoint uses the load-balancer VIP as the destination address to send traffic to the server endpoint. If the load balancer does not do source NAT, which set of configurations must be applied on Cisco ACI to allow only the return traffic to be redirected to the service node? A. ✑ Create a contract with a filter matching `IP` only ✑ Create a L4-L7 device, function type `GoTo` ✑ Create a L4-L7 Policy-Based Redirect Policy with the L3 Destination set to the load-balancer inside IP/MAC ✑ Create a service graph template that references the previously created contract and L4-L7 device ✑ Apply the service graph template. Select `L3 Destination` and reference L4-L7 Policy-Based Redirect Policy on the provider connector only B. ✑ Create a contract linked to the common/default filter ✑ Create a L4-L7 device, function type `GoThrough` ✑ Create a L4-L7 Policy-Based Redirect Policy with the L3 Destination set to the load-balancer inside IP/MAC ✑ Create a service graph template that references the previously created contract and L4-L7 device ✑ Apply the service graph template. Select `L3 Destination` and reference L4-L7 Policy-Based Redirect Policy on the consumer and provider connector C. ✑ Create a contract linked to the common/default filter Create a L4-L7 device, function type `GoTo`
✑ Create a L4-L7 Policy-Based Redirect Policy with `Anycast Endpoint` enabled and the L3 Destination set to the load-balancer inside IP/MAC ✑ Create a service graph template that references the previously created contract and L4-L7 device ✑ Apply the service graph template. Select `L3 Destination` and reference L4-L7 Policy-Based Redirect Policy on the consumer connector only D. ✑ Create a contract with a filter matching `IP` only ✑ Create a L4-L7 device, function type `GoThrough` ✑ Create a L4-L7 Policy-Based Redirect Policy with `Anycast Endpoint` enabled and the L3 Destination set to the load-balancer inside IP/MAC ✑ Create a service graph template that references the previously created contract and L4-L7 device ✑ Apply the service graph template. Select `L3 Destination` and reference L4-L7 Policy-Based Redirect Policy on the consumer and provider
Refer to the exhibit. Which two sets of actions must be taken to permit subnet 192.168.1.0/24 to communicate with subnet 172.18.1.0/24 using Cisco ACI fabric? (Choose two.)
A. Configure 192.168.1.0/24 with scope Export Route Control subnet under L3out_B.Configure 192.168.1.0/24 with scope External subnet for external EPG under L3out_A.
B. Configure 172.18.1.0/24 with scope External subnet for external EPG under L3out_A.Configure 192.168.1.0/24 with scope External subnet for external EPG under L3out_B.
C. Configure 172.18.1.0/24 with scope Export Route Control subnet under L3out_AConfigure 172.18.1.0/24 with scope External subnet for external EPG under L3out_B.
D. Configure 172.18.1.0/24 with scope Export Route Control subnet under L3out_B.Configure 192.168.1.0/24 with scope External subnet for external EPG under L3out_A.
E. Configure 192.168.1.0/24 with scope Export Route Control subnet under L3out_A.Configure 172.18.1.0/24 with scope External subnet for external EPG under L3out_ B.
An engineer is implementing the Cisco ACI fabric but is experiencing loops detected from endpoints. When the issue was investigated, it was discovered that the packets are received with the same source IP address but from different leaf switch ports. The engineer must prevent the issue from happening in the future and make sure that the port is brought back up if it was disabled due to the loop discovered. Which set of actions must be taken to meet these requirements?
A. Enable the enforce endpoint check and set the Rouge EP detection interval
B. Enable the rogue endpoint and set the Error Disabled Recovery Policy
C. Enable the remote endpoint limit and set the Interface override
D. Enable reverse path forwarding and set the Hold Interval
As part of a newly deployed ACI fabric, a pair of border leaf switches have been deployed to provide shared services for all tenants. The configured L3Out runs OSPF as the routing protocol. The requirement is to advertise the routes from the border leaf switches to the compute leaf switches. Which configuration must be implemented to meet these requirements?
A. Configure a BGP route reflector policy for the Cisco ACI pod
B. Define the shared L3Out in the common tenant
C. Enable Import Route Control Enforcement in the L3Out policy
D. Define the consumer subnet under the consumer EPG
How is broadcast forwarded in Cisco ACI Multi-Pod after ARP flooding is enabled?
A. For the specific bridge domain, all spines forward the broadcast frames to IPN routers
B. Broadcast frames are forwarded inside the pod and across the IPN using the multicast address that is associated to the bridge domain
C. Within a pod, the ingress leaf switch floods the broadcast frame on all fabric ports
D. Ingress replication is used on the spines to forward broadcast frames in the IPN infrastructure
Refer to the exhibit. Which combination of flags in the Cisco ACI contract allows a client in WebClient EPG to establish an HTTP connection toward a server in WebServer EPG?
A. Apply Both Direction ENABLED and Reverse Port Filter ENABLED
B. Apply Both Direction DISABLED and Reverse Port Filter DISABLED
C. Apply Both Direction DISABLED and Reverse Port Filter ENABLED
D. Apply Both Direction ENABLED and Reverse Port Filter DISABLED
Refer to the exhibit. A company decided to decrease its routing footprint and remove RT-2 and RT-3 devices from its data center. Because of that, the exit point must be created from all the tenants by using the common tenant. Which two configuration tasks must be completed to meet these requirements? (Choose two.)
A. Move subnets from all the bridge domains to the EPG level and mark them with flag Shared between VRFs.
B. Change contract Ctr-3 scope to Global, consume it by all EPGs, and flag all subnets with flag Shared between VRFs.
C. Update the L3Out ExtEPG subnet in the common tenant with flag Shared Route Control Subnet and Aggregate Shared Routes.
D. Mark all subnets with flag Shared between VRFs and attach contract Ctr-3 as a provider to all the EPGs.
E. Export contract Ctr-2 into the tenant TN-1 and attach it as a consumer to all the EPGs in the tenant TN-1.
Refer to the exhibit. An engineer wants to avoid connectivity problems for the endpoint EP1 when it reaches an external L3Out network through the gateway 10.2.2.254/24. Which two configurations must be implemented in BD-BD2? (Choose two.)
A. Disable unicast routing
B. Enable IP data plane learning for the VRF
C. Disable ARP flooding
D. Enable ARP flooding
E. Enable unicast routing
Refer to the exhibit. A network engineer configures a Layer 4 to Layer 7 device for an outside routed firewall that is connected to POD-1 inside a Cisco ACI fabric that consists of two pods. All traffic from POD-1 or POD-2 that uses the L3Out should pass through the routed firewall. Which Function Type must be implemented in the service graph for POD-2 to use L3Out?
A. GoThrough
B. L1
C. GoTo
D. L2
DRAG DROP -Refer to the exhibit. Drag and drop the subnets and flags from the left into the External Network Instance Profile policies on the right to create a setup that advertises only 10.10.0.0/24 and 10.10.1.0/24 prefixes in VRF1 and establishes connectivity between VRFs. Not all options are used. Select and Place:
Free Access Full 300-630 Practice Exam Free
Looking for additional practice? Click here to access a full set of 300-630 practice exam free questions and continue building your skills across all exam domains.
Our question sets are updated regularly to ensure they stay aligned with the latest exam objectives—so be sure to visit often!
Good luck with your 300-630 certification journey!