200-125 Practice Exam Free – 50 Questions to Simulate the Real Exam
Are you getting ready for the 200-125 certification? Take your preparation to the next level with our 200-125 Practice Exam Free – a carefully designed set of 50 realistic exam-style questions to help you evaluate your knowledge and boost your confidence.
Using a 200-125 practice exam free is one of the best ways to:
- Experience the format and difficulty of the real exam
- Identify your strengths and focus on weak areas
- Improve your test-taking speed and accuracy
Below, you will find 50 realistic 200-125 practice exam free questions covering key exam topics. Each question reflects the structure and challenge of the actual exam.
On which options are standard access lists based?
A. destination address and wildcard mask
B. destination address and subnet mask
C. source address and subnet mask
D. source address and wildcard mask
Which three elements must be used when you configure a router interface for VLAN trunking? (Choose three.)
A. one physical interface for each subinterface.
B. one IP network or subnetwork for each subinterface.
C. a management domain for each subinterface.
D. subinterface encapsulation identifiers that match VLAN tags.
E. one subinterface per VLAN.
F. subinterface numbering that matches VLAN tags. BDE
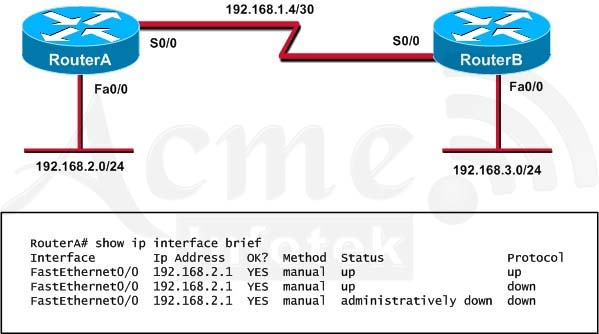
Refer to the exhibit. Hosts in network 192.168.2.0 are unable to reach hosts in network 192.168.3.0. Based on the output from RouterA, what are two possible reasons for the failure?(Choose two)
A. The cable that is connected to S0/0 on RouterA is faulty.
B. Interface S0/0 on RouterB is administratively down.
C. Interface S0/0 on RouterA is configured with an incorrect subnet mask.
D. The IP address that is configured on S0/0 of RouterB is not in the correct subnet.
E. Interface S0/0 on RouterA is not receiving a clock signal from the CSU/DSU.
F. The encapsulation that is configured on S0/0 of RouterB does not match the encapsulation that is configured on S0/0 of RouterA.
What will be the result if the following configuration commands are implemented on a Cisco switch? Switch(config-if)# switchport port-security Switch(config-if)# switchport port-security mac-address sticky
A. A dynamically learned MAC address is saved in the startup-configuration file.
B. A dynamically learned MAC address is saved in the running-configuration file.
C. A dynamically learned MAC address is saved in the VLAN database.
D. Statically configured MAC addresses are saved in the startup-configuration file if frames from that address are received.
E. Statically configured MAC addresses are saved in the running-configuration file if frames from that address are received.
While troubleshooting a connectivity issue from a PC you obtain the following information:You then conduct the following tests from the local PC:

What is the underlying cause of this problem?
A. A remote physical layer problem exists.
B. The host NIC is not functioning.
C. TCP/IP has not been correctly installed on the host.
D. A local physical layer problem exists.
Which three functions are major components of a network virtualization architecture? (Choose three.)
A. virtual network services
B. policy enforcement
C. network access control
D. network resilience
E. authentication services
F. path isolation
Which two options are valid WAN connectivity methods? (Choose two.)
A. PPP
B. WAP
C. DSL
D. L2TPv3
E. Ethernet
Which of these represents an IPv6 link-local address?
A. FE80::380e:611a:e14f:3d69
B. FE81::280f:512b:e14f:3d69
C. FEFE:0345:5f1b::e14d:3d69
D. FE08::280e:611:a:f14f:3d69
A network administrator creates a layer 3 EtherChannel, bundling four interfaces into channel group 1. On what interface is the IP address configured?
A. the port-channel 1 interface
B. the highest number member interface
C. all member interfaces
D. e lowest number member interface
Which two statements about RIPv2 are true? (Choose two.)
A. It does not support clear text authentication, similar to RIPv1
B. It supports CIDR and VLSM
C. It stores RIP neighbor adjacency information in a neighbor table
D. It uses the Bellman-Ford routing algorithm
E. It sends periodic updates via broadcast
Which two statements about switch stacking are true? (Choose two)
A. The stack is powered by a single power cable
B. The switches are connected in a daisy-chain fashion
C. The first and last switch in the stack must be connected to one another
D. The switches are connected by crossover cables
E. The switches must be fully meshed
Which symptom most commonly indicates that two connecting interfaces are configured with a duplex mismatch?
A. an interface with an up/down state
B. an interface with a down/down state
C. late collisions on the interface
D. the spanning tree process shutting down
What is the difference between a CSU/DSU and a modem?
A. A CSU/DSU converts analog signals from a router to a leased line; a modem converts analog signals from a router to a leased line.
B. A CSU/DSU converts analog signals from a router to a phone line; a modem converts digital signals from a router to a leased line.
C. A CSU/DSU converts digital signals from a router to a phone line; a modem converts analog signals from a router to a phone line.
D. A CSU/DSU converts digital signals from a router to a leased line; a modem converts digital signals from a router to a phone line.
Which type of routing protocol operates by using first-hand information from each device’s peers?
A. distance vector protocols
B. link-state protocols
C. path vector protocols
D. exterior gateway protocols
Which component of the Cisco SDN solution serves as the centralized management system?
A. Cisco OpenDaylight
B. Cisco ACI
C. Cisco APIC
D. Cisco IWAN
When a router is unable to find a known route in the routing table, how does it handle the packet?
A. It sends the packet over the route with the best metric.
B. It sends the packet to the gateway of last resort.
C. It sends the packet to the next hop address.
D. It discards the packet.
What does a Layer 2 switch use to decide where to forward a received frame?
A. source MAC address
B. source IP address
C. source switch port
D. destination IP address
E. destination port address
F. destination MAC address
Which three statements accurately describe layer 2 Ethernet switches? (choose three)
A. Microsegmentation decreases the number of collisions on the network.
B. If a switch receives a frame for an unknown destination, it uses ARP to resolve the address.
C. Spanning Tree Protocol allows switches to automatically share vlan information.
D. In a properly functioning network with redundant switched paths, each switched segment will contain one root bridge with all its ports in the forwarding state. All other switches in that broadcast domain will have only one root port.
E. Establishing vlans increases the number of broadcast domains.
F. Switches that are configured with vlans make forwarding decisions based on both layer 2 and layer 3 address information.
In which three ways is an IPv6 header simpler than an IPv4 header? (Choose three.)
A. Unlike IPv4 headers, IPv6 headers have a fixed length.
B. IPv6 uses an extension header instead of the IPv4 Fragmentation field.
C. IPv6 headers eliminate the IPv4 Checksum field.
D. IPv6 headers use the Fragment Offset field in place of the IPv4 Fragmentation field.
E. IPv6 headers use a smaller Option field size than IPv4 headers.
F. IPv6 headers use a 4-bit TTL field, and IPv4 headers use an 8-bit TTL field. ABC
Which two facts must you take into account when you deploy PPPoE? (Choose two.)
A. DDR idle timers must be configured to support VPDN logging
B. DDR is not supported
C. You must manually configure IP addresses on the PPPoE interface
D. PPPoE supports a maximum of 10 clients per customer premises equipment
E. An individual PVC can support one PPPoE client
Which HSRP feature was new in HSRPv2?
A. preemption
B. VLAN group numbers that are greater than 255
C. tracking
D. virtual MAC addresses
Which two statements about northbound and southbound APIs are true? (Choose two.)
A. Only southbound APIs allow program control of the network.
B. Only northbound APIs allow program control of the network.
C. Only southbound API interfaces use a Service Abstraction Layer.
D. Only northbound API interfaces use a Service Abstraction Layer.
E. Both northbound and southbound API interfaces use a Service Abstraction Layer.
F. Both northbound and southbound APIs allow program control of the network.
Which three options are types of Layer 2 network attack? (Choose three)
A. Spoofing attacks
B. Vlan Hopping
C. botnet attacks
D. DDOS attacks
E. ARP Attacks
F. Brute force attacks
You enter the show ipv6 route command on an OSPF device and the device displays a route. Which conclusion can you draw about the environment?
A. OSPF is distributing IPv6 routes to BGP.
B. The router is designated as an ABR.
C. The router is designated as totally stubby.
D. OSPFv3 is in use.
Which three are characteristics of an IPv6 anycast address? (Choose three.)
A. one-to-many communication model
B. one-to-nearest communication model
C. any-to-many communication model
D. a unique IPv6 address for each device in the group
E. the same address for multiple devices in the group
F. delivery of packets to the group interface that is closest to the sending device
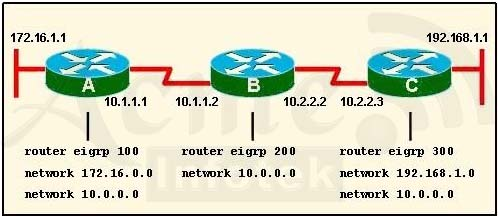
Refer to the exhibit. When running EIGRP, what is required for RouterA to exchange routing updates with RouterC?
A. As numbers must be changed to match on all the routers
B. Loopback interfaces must be configured so a DR is elected
C. The no auto-summary command is needed on Router A and Router C
D. Router B needs to have two network statements, one for each connected network
In which circumstance are multiple copies of the same unicast frame likely to be transmitted in a switched LAN?
A. during high traffic periods
B. after broken links are re-established
C. when upper-layer protocols require high reliability
D. in an improperly implemented redundant topology
E. when a dual ring topology is in use
Why will a switch never learn a broadcast address?
A. Broadcasts only use network layer addressing.
B. A broadcast frame is never forwarded by a switch.
C. A broadcast address will never be the source address of a frame.
D. Broadcast addresses use an incorrect format for the switching table.
E. Broadcast frames are never sent to switches.
In which solution is a router ACL used?
A. protecting a server from unauthorized access
B. controlling path selection, based on the route metric
C. reducing router CPU utilization
D. filtering packets that are passing through a router
Refer to the exhibit, The VLAN configuration of S1 is not being in this VTP enabled environment. The VTP and uplink port configurations for each switch are displayed. Which two command sets, if issued, resolve this failure and allow VTP to operate as expected? (Choose two.)A.
B.
C.
D.
E.
What are three features of the IPv6 protocol? (Choose three.)
A. optional IPsec
B. autoconfiguration
C. no broadcasts
D. complicated header
E. plug-and-play
F. checksums
A BPDU guard is configured on an interface that has PortFast Enable. Which state does the interface enter when it receives a BPDU?
A. Blocking
B. Shutdown
C. Listening
D. Errdisable
Refer to the exhibit. What statement is true of the configuration for this network?Based on the information shown above, Which of the following correctly describe the configuration for this network?
A. The configuration that is shown provides inadequate outside address space for translation of the number of inside addresses that are supported.
B. Because of the addressing on interface FastEthemet0/1, the Serial0/0 interface address will not support the NAT configuration as shown.
C. The number 1 referred to in the ip nat inside source command references access-list number1.
D. External Router must be configured with static routers to networks 172.16.2.0/24.
Which three elements must be used when you configure a router interface for VLAN trunking? (Choose three.)
A. one physical interface for each subinterface
B. one IP network or subnetwork for each subinterface
C. a management domain for each subinterface
D. subinterface encapsulation identifiers that match VLAN tags
E. one subinterface per VLAN
F. subinterface numbering that matches VLAN tags
Refer to the graphic. A static route to the 10.5.6.0/24 network is to be configured on the HFD router. Which commands will accomplish this? (Choose two.)
A. HFD(config)# ip route 10.5.6.0 0.0.0.255 fa0/0
B. HFD(config)# ip route 10.5.6.0 0.0.0.255 10.5.4.6
C. HFD(config)# ip route 10.5.6.0 255.255.255.0 fa0/0
D. HFD(config)# ip route 10.5.6.0 255.255.255.0 10.5.4.6
E. HFD(config)# ip route 10.5.4.6 0.0.0.255 10.5.6.0
F. HFD(config)# ip route 10.5.4.6 255.255.255.0 10.5.6.0
Which statement about the IP SLAs ICMP Echo operation is true?
A. The frequency of the operations specified in milliseconds.
B. It is used to identify the best source interface from which to send traffic.
C. It is used to identify the best source interface from which to send traffic.
D. It is used to determine the frequency of ICMP packets.
If all switches are configured with default values, which switch will take over when the primary root bridge experiences a power loss?
A. switch O0E0.F726 3DC6
B. switch 00E0.F90B 6BE3
C. switch 0004.9A1A C182
D. switch 0040.0BC0 90C5
Refer to the topology below and answer the following question.Why did Branch1 router lose WAN connectivity with R1 router?
A. The IP address is misconfigured on PPP multilink interface on the Branch1 router
B. The PPP multilink group is misconfigured on the Branch1 serial interfaces
C. The PPP multilink group is misconfigured on the R1 serial interfaces
D. The Branch1 serial interfaces are placed in a shutdown condition
CORRECT TEXT -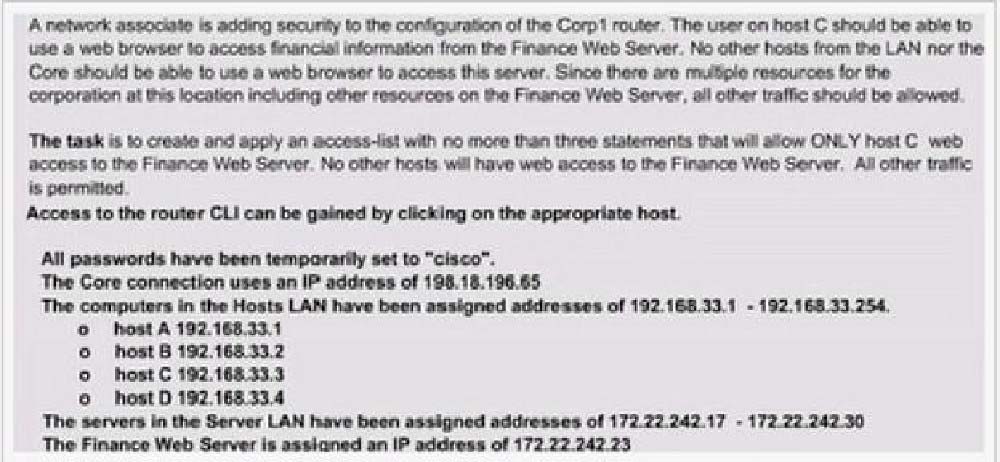
A. B. C. D.
What is the simplest IP SLA operation that can measure end-to-end response time between devices?
A. ICMP path jitter
B. ICMP path echo
C. ICMP echo
D. ICMP jitter
Refer to the exhibit.An attempt to deny web access to a subnet blocks all traffic from the subnet. Which interface command immediately removes the effect of ACL 102?
A. no ip access-class 102 in
B. no ip access-class 102 out
C. no ip access-group 102 in
D. no ip access-group 102 out
E. no ip access-list 102 in
Which command can you use to set the hostname on a switch?
A. switch-mdf-c1(config)#hostname switch-mdf1
B. switch-mdf-c1>hostname switch-mdf1
C. switch-mdf-c1#hostname switch-mdf1
D. switch-mdf-c1(config-if)#hostname switch-mdf1
Which two statements about IPv6 multicast addresses are true? (Choose two.)
A. They use the prefix FC80::/8
B. If the lifetime parameter is set to 1, the route is permanent
C. They identify a group of interfaces on different devices
D. They use the prefix FF00::/8
E. If the scope parameter is set to 5, the route is local to the node
Which IPv6 address is valid?
A. 2031:0:130F::9C0:876A:130B
B. 2001:0db8:0:130H::87C:140B
C. 2001:0db8:0000:130F:0000:0000:08GC:140B
D. 2031::130F::9C0:876A:130B
Which effect of the terminal monitor command is true?
A. It displays the configuration of the syslog server
B. It configures a syslog server
C. It configures the device to log messages to the console
D. It puts the device into global configuration mode
What are three parts of an IPv6 global unicast address? (Choose three.)
A. an interface ID that is used to identify the local host on the network
B. an interface ID that is used to identify the local network for a particular host.
C. a subnet ID that is used to identify networks inside of the local enterprise site
D. a global routing prefix that is used to identify the network portion of the address that has been provided by an ISP
E. a global routing prefix that is used to identify the portion of the network address provided by a local administrator
Which feature facilitates the tagging of a specific VLAN?
A. Routing
B. Hairpinning
C. Encapsulation
D. Switching
Refer to the exhibit.The network administrator cannot connect to Switch 1 over a Telnet session, although the hosts attached to Switch1 can ping the interface Fa0/0 of the router. Given the information in the graphic and assuming that the router and Switch2 are configured properly, which of the following commands should be issued on Switch1 to correct this problem?
A. Switch1(config)# ip default-gateway 192.168.24.1
B. Switch1(config)# interface fa0/1 Switch1(config-if)# switchport mode trunk
C. Switch1(config)# line con0 Switch1(config-line)# password cisco Switch1(config-line)# login
D. Switch1(config)# interface fa0/1 Switch1(config-if)# ip address 192.168.24.3 255.255.255.0
E. Switch1(config)# interface fa0/1 Switch1(config-if)# duplex full Switch1(confiq-if)# speed 100
Which command allows you to verify the encapsulation type (CISCO or IETF) for a frame Relay link?
A. show frame-relay map
B. show frame-relay pvc
C. show frame-relay lmi
D. show interfaces serial
RouterA is unable to reach RouterB. Both routers are running IOS version 12.0.After reviewing the command output and graphic, what is the most likely cause of the problem?
A. incorrect bandwidth configuration
B. incorrect LMI configuration
C. incorrect map statement
D. incorrect IP address
Free Access Full 200-125 Practice Exam Free
Looking for additional practice? Click here to access a full set of 200-125 practice exam free questions and continue building your skills across all exam domains.
Our question sets are updated regularly to ensure they stay aligned with the latest exam objectives—so be sure to visit often!
Good luck with your 200-125 certification journey!