102-500 Practice Exam Free – 50 Questions to Simulate the Real Exam
Are you getting ready for the 102-500 certification? Take your preparation to the next level with our 102-500 Practice Exam Free – a carefully designed set of 50 realistic exam-style questions to help you evaluate your knowledge and boost your confidence.
Using a 102-500 practice exam free is one of the best ways to:
- Experience the format and difficulty of the real exam
- Identify your strengths and focus on weak areas
- Improve your test-taking speed and accuracy
Below, you will find 50 realistic 102-500 practice exam free questions covering key exam topics. Each question reflects the structure and challenge of the actual exam.
Which of the following parameters are used for journalctl to limit the time frame of the output? (Choose two.)A. --since=
B. --from=
C. --until=
D. --upto=
E. --date=
What output is produced by the following command sequence?
echo '1 2 3 4 5 6' | while read a b c; do
echo result $c $b $a;
doneA. result: 6 5 4
B. result: 1 2 3 4 5 6
C. result: 3 4 5 6 2 1
D. result: 6 5 4 3 2 1
E. result: 3 2 1
Which command is used to set restrictions on the size of a core file that is created for a user when a program crashes?A. core
B. edquota
C. quota
D. ulimit
E. ktrace
Which of the following states can NetworkManager show regarding the system's network connectivity? (Choose two.)A. up
B. portal
C. full
D. login-required
E. rewalled
Which of the following commands sets the system's time zone to the Canadian Eastern Time?A. localegen -t -f /usr/share/zoneinfo/Canada/Eastern > /etc/locate.tz
B. tzconf /etc/localtime
C. sysctl -w clock.tz='Canada/Eastern'
D. modprobe tz_ca_est
E. ln -sf /usr/share/zoneinfo/Canada/Eastern /etc/localtime
Which of the following sections exists in a systemd timer unit?A. [Events]
B. [Timer]
C. [cron]
D. [Schedule]
E. [Trigger]
FILL BLANK -
Which command included in NetworkManager is a curses application which provides easy acces to the NetworkManager on the command line? (Specify only the command without any path or parameters.)
nmtui
The X11 configuration file xorg.conf is grouped into section. How is the content of the section SectionName represented?A. It is placed in curly brackets as in Section SectionName { ¶}.
B. It is placed between the tags
and .C. It is placed between a line containing Section SectionName and a line containing EndSection.
D. It is placed after the row [SectionName].
E. It is placed after an initial unindented Section SectionName and must be indented by exactly one tab character.
Which of the following steps prevents a user from obtaining an interactive login session?A. Setting the UID for the user to 0.
B. Running the command chsh "s /bin/false with the user name.
C. Removing the user from the group staff.
D. Adding the user to /etc/noaccess.
E. Creating a .nologin file in the user's home directory.
What output does the command seq 1 5 20 produce?A. 1
B. 1
C. 1
D. 2
E. 5
Which configuration file contains the default options for SSH clients?A. /etc/ssh/sshd_config
B. /etc/ssh/ssh
C. /etc/ssh/ssh_config
D. /etc/ssh/client
E. /etc/ssh/ssh_client
Which of the following commands displays all environment and shell variables?A. getargs
B. lsenv
C. ls
D. env
E. lsshell
Which of the following commands display the number of bytes transmitted and received via the eth0 network interface? (Choose two.)A. route -v via eth0
B. ip stats show dev eth0
C. netstat -s -i eth0
D. ifconfig eth0
E. ip -s link show eth0
Which character in the password field of /etc/passwd is used to indicate that the encrypted password is stored in /etc/shadow?A. *
B. -
C. s
D. #
E. x
Which of the following files assigns a user to its primary group?A. /etc/pgroup
B. /etc/shadow
C. /etc/passwd
D. /etc/group
E. /etc/gshadow
Which of the following changes may occur as a consequence of using the command ip? (Choose three.)A. Network interfaces may become active or inactive.
B. New name servers may be added to the resolver configuration.
C. The system's host name may change.
D. IP addresses may change.
E. The routing table may change.
Which of the following commands can identify the PID od a process which opened a TCP port?A. ptrace
B. strace
C. debug
D. lsof
E. nessus
FILL BLANK -
Which file is processed by newaliases? (Specify the full name of the file, including path.)
FILL BLANK -
What command, depending on its options, can display the open TCP connections, the routing tables, as well as network interface statistics? (Specify only the command without any path or parameters.)
If neither cron.allow nor cron.deny exist in /etc/, which of the following is true?A. Without additional configuration, all users may create user specific crontabs.
B. Without additional configuration, only root may create user specific crontabs.
C. The cron daemon will refuse to start and report missing files in the system's log file.
D. When a user creates a user specific crontab the system administrator must approve it explicitly.
E. The default settings of /etc/crond.conf define whether or not user specific crontabs are generally allowed or not.
How does the ping command work by default?A. Is sends an ICMP Echo Request to a remote host and waits to receive an ICMP Echo Response in return.
B. It sends an ARP request to a remote host and waits to receive an ARP response in return.
C. It sends a TCP SYN packet to a remote host and waits to receive an TCP ACK response in return.
D. Is sends a broadcast packet to all hosts on the net and waits to receive, among others, a response from the target system.
E. It sends a UDP packet to port 0 of the remote host and waits to receive a UDP error response in return.
Which of the following tasks are handled by a display manager like XDM or KMD? (Choose two.)A. configure additional devices like new monitors or projectors when they are attached.
B. Start and prepare the desktop environment for the user.
C. Create an X11 configuration file for the current graphic devices and monitors.
D. Lock the screen when the user was inactive for a configurable amount of time.
E. Handle the login of a user.
Which command makes the shell variable named VARIABLE visible to subshells?A. export $VARIABLE
B. env VARIABLE
C. set $VARIABLE
D. set VARIABLE
E. export VARIABLE
On a machine running several X servers, how do programs identify the different instances of the X11 server?A. By a fixed UUID that is defined in the X11 configuration file.
B. By a display name like: 1.
C. By the name of the user that runs the X server like x11:bob.
D. By a device name like /dev/X11/xservers/1.
E. By a unique IPv6 address from the fe80::/64 subnet.
What is true regarding public and private SSH keys? (Choose two.)A. For each user account, there is exactly one key pair that can be used to log into that account.
B. The private key must never be revealed to anyone.
C. Several different public keys may be generated for the same private key.
D. To maintain the private key's confidentiality, the SSH key pair must be created by its owner.
E. To allow remote logins, the user's private key must be copied to the remote server.
Which of the following options in the chrony configuration file define remote time sources? (Choose two.)A. source
B. clock
C. remote
D. pool
E. server
Which of the following commands configure network interfaces based on the system's existing distribution-specific configuration files? (Choose two.)A. ifconf
B. ifdown
C. ifpause
D. ifstart
E. ifup
Which of the following commands is used to rotate, compress, and mail system logs?A. logrotate
B. striplog
C. syslogd "-rotate
D. rotatelog
E. logger
Which of the following situations is observed and corrected by an NTP client?A. The skew in time between the system clock and the computer's hardware clock.
B. The physical location and the timezone configuration.
C. Changes in the time zone of the current computer's location.
D. Adjustment needed to support Daylight Saving Time.
E. The skew in time between the system clock and the reference clock.
If an alias ls exists, which of the following commands updates the alias to point to the command ls -l instead of the alias's current target?A. set ls='ls -l'
B. alias ls='ls -l'
C. alias --force ls='ls -l'
D. alias --update ls ls='ls -l'
E. realias ls='ls -l'
Which of the following IPv4 networks are reserved by IANA for private address assignment and private routing? (Choose three.)A. 10.0.0.0/8
B. 127.0.0.0/8
C. 169.255.0.0/16
D. 172.16.0.0/12
E. 192.168.0.0/16
FILL BLANK -
Which file, if present, must contain all users that are allowed to use the cron scheduling system? (Specify the full name of the file, including path.)
Which standardized TCP port is used by HTTPS services?A. 25
B. 80
C. 8080
D. 443
E. 636
FILL BLANK -
What command enables a network interface according to distribution-specific configuration, such as /etc/network/interfaces or /etc/sysconfig/ network-scripts/ifcfg-eth0? (Specify only the command without any path or parameters.)
FILL BLANK -
What command is used to add OpenSSH private keys to a running ssh-agent instance? (Specify the command name only without any path.)
ssh-add
Which of the following statements is true if the UID of a regular user is identical to the GID of a group?A. UID have precedence over GIDs, therefore the user is available while the group doesn't.
B. The user as well as the group are not available to avoid ambiguity due to the ID conflict.
C. UIDs and GIDs are independent of each other, therefore the user as well as the group are still available.
D. The user is the only member of the group, even if the group configuration contains other members.
E. GIDs have precedence over UIDs, therefore the group is available while the user isn't.
Which of the following connection types, as seen in nmcli connection show, may exist in NetworkManager? (Choose three.)A. tcp
B. ethernet
C. wi
D. ipv6
E. bridge
What is true regarding the file ~/.forward?A. When configured correctly ~/.forward can be used to forward each incoming mail to one or more other recipients.
B. After editing ~/.forward the user must run newaliases to make the mail server aware of the changes.
C. Using ~/.forward, root may configure any email address whereas all other users may configure only their own addresses.
D. As ~/.forward is owned by the MTA and not writable by the user, it must be edited using the editaliases command.
E. By default, only ~/.forward files of users in the group mailq are processed while all other user's ~/.forward files are ignored.
On a system using systemd-journald, which of the following commands add the message Howdy to the system log? (Choose two.)A. append Howdy
B. logger Howdy
C. systemd-cat echo Howdy
D. echo Howdy > /dev/journal
E. journalctl add Howdy
Which of the following comparison operators for test work on elements in the file system? (Choose two.)A. "z
B. "eq
C. "d
D. "f
E. "lt
Which of the following commands finds all files owned by root that have the SetUID bit set?A. find / -user root -perm -4000
B. find / -user 0 -mode +s
C. find / -owner root -setuid
D. find / -owner 0 -permbits 0x100000000
E. find / -- filter uid=1 -- filter pers=u+s
What is the systemd journal stored?A. /var/jlog/ and /var/jlogd/
B. /proc/log/ and /proc/klog/
C. /run/log/journal/ or /var/log/journal/
D. /var/log/syslog.bin or /var/log/syslog.jrn
E. /etc/systemd/journal/ or /usr/lib/systemd/journal/
Which of the following configuration files should be modified to globally set shell variables for all users?A. /etc/profile
B. /etc/bashrc
C. ~/.bash_profile
D. /etc/.bashrc
E. /etc/shellenv
Which of the commands below might have produced the following output?
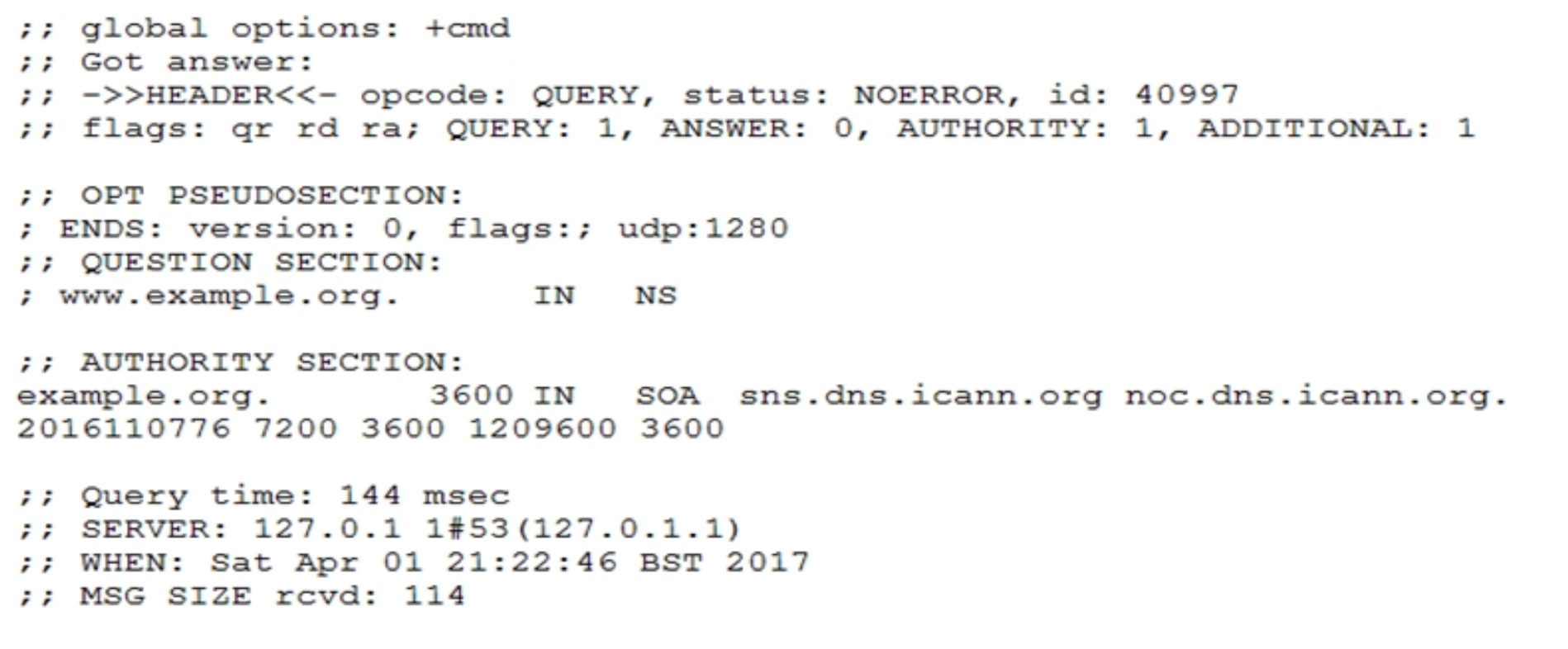
A. dig -t mx www.example.org
B. dig www.example.org
C. dig -t ns www.example.org
D. dig -t a www.example.org
E. dig -t soa www.example.org
Which of the following commands lists all defines variables and functions within Bash?A. env
B. export
C. env -a
D. set
E. echo $ENV
FILL BLANK -
What option to useradd creates a new user's home directory and provisions it with a set of standard files? (Specify only the option name without any values or parameters.)
Which mechanism does ssh use to interact with the SSH agent?A. Connecting to port 2222 which is used by the system-wide SSH agent.
B. Using the fixed socket .ssh-agent/ipc.
C. Creating an alias replacing ssh with calls to ssh-agent.
D. Starting ssh-agent as a child process for each ssh invocation.
E. Evaluating environment variables such as SSH_AUTH_SOCK.
Which option in the chrony configuration file changes the initial interval of polls to a NTP server in order to speed up the initial synchronization?A. iburst
B. quickstart
C. fast
D. fsync
E. ood
Which of the following statements is valid in the file /etc/nsswitch.conf?A. multi on
B. 192.168.168.4 dns-server
C. namespaces: net mount procs
D. include /etc/nsswitch.d/
E. hosts: files dns
FILL BLANK -
The presence of what file will temporarily prevent all users except root from logging into a system? (Specify the full name of the file, including path.)
/sbin/nologin
Free Access Full 102-500 Practice Exam Free
Looking for additional practice? Click here to access a full set of 102-500 practice exam free questions and continue building your skills across all exam domains.
Our question sets are updated regularly to ensure they stay aligned with the latest exam objectives—so be sure to visit often!
Good luck with your 102-500 certification journey!

