101 Practice Exam Free – 50 Questions to Simulate the Real Exam
Are you getting ready for the 101 certification? Take your preparation to the next level with our 101 Practice Exam Free – a carefully designed set of 50 realistic exam-style questions to help you evaluate your knowledge and boost your confidence.
Using a 101 practice exam free is one of the best ways to:
- Experience the format and difficulty of the real exam
- Identify your strengths and focus on weak areas
- Improve your test-taking speed and accuracy
Below, you will find 50 realistic 101 practice exam free questions covering key exam topics. Each question reflects the structure and challenge of the actual exam.
A site is load balancing to a pool of web servers. Which statement is true concerning BIG-IP's ability to verify whether the web servers are functioning properly or not?
A. Web server monitors can test the content of any page on the server.
B. Web server monitors always verify the contents of the index.html page.
C. Web server monitors can test whether the server’s address is reachable, but cannot test a page’s content.
D. Web server monitors can test the content of static web pages, but cannot test pages that would require the web server to dynamically build content.
With standard DNS, assuming no DNS request failures, which process describes the normal resolution process on a "first time" DNS request?
A. Client requests address from root server, root server returns IP address to Authoritative DNS, Authoritative DNS returns requested IP address, LDNS returns requested IP address to client.
B. Client requests address from LDNS, LDNS requests from GTM, GTM requests from Authoritative DNS, Authoritative DNS returns requested IP address, LDNS returns requested IP address to client.
C. Client requests address from LDNS, Authoritative DNS receives request from root server, root server returns LDNS address, LDNS returns client address, Authoritative DNS returns requested IP address, LDNS returns requested IP address to client.
D. Client requests address from LDNS, LDNS requests from root server, root server returns Authoritative DNS address, LDNS requests from Authoritative DNS, Authoritative DNS returns requested IP address, LDNS returns requested IP address to client.
When a business is hacked, they often lose more than money. What are the other consequences to a business as a result of being hacked? Select two.
A. Helpful third party reviews of the security needs of the customer’s web applications.
B. Valuable free press that occurs as companies address hacking incidents.
C. Penalties related to non-compliance with laws and regulations.
D. Final resolution of all security vulnerabilities of the business’ web applications.
E. Loss of customers when slow connections drive customers to competitor’s site.
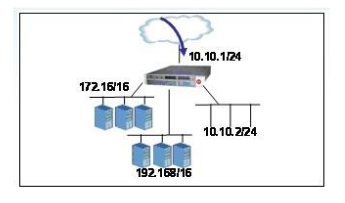
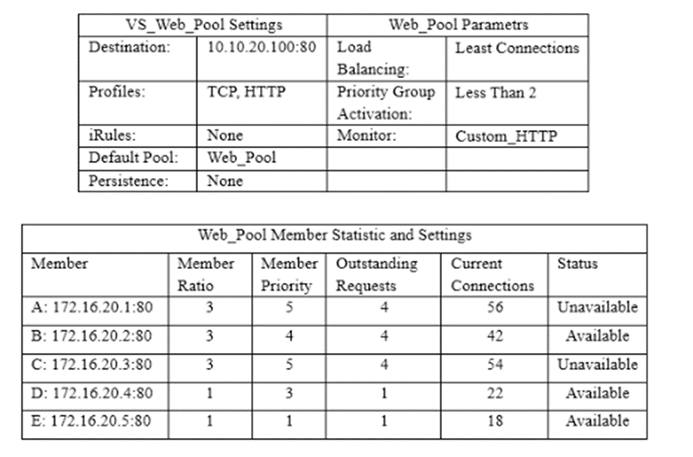
An LTM has the 3 virtual servers, 2 SNATs, four self IP addresses defined, and the networks shown in the exhibit. Selected options for each object are shown below. Settings not shown are at their defaults. Assume port exhaustion has not been reached.A connection attempt is made with a source IP and port of 10.10.100.50:2222 and a destination IP and port of 10.10.2.10:80. When the request is processed, what will be the source and destination IP addresses?
A. The request will be droped.
B. Source IP: 10.10.2.1; Destination IP: 10.10.2.10
C. Source IP: 10.10.2.102; Destination IP 10.10.2.10
D. Source IP: Either 172.16.20.50 or 192.168.10.50; Destination IP: 10.10.2.10
E. Source IP: 10.10.2.1; Destination IP: pool in the 172.16/16 network C
What occurs when a save-config command is issued?
A. The current configuration files are backed up.
B. The current configuration files are verified for syntax, then the running configuration is installed in memory.
C. The current configuration files are loaded into memory.
D. The current configuration files are saved into an archive format.
Which statement is true concerning cookie persistence.
A. Cookie persistence allows persistence independent of IP addresses.
B. Cookie persistence allows persistence even if the data are encrypted from client to pool member.
C. Cookie persistence uses a cookie that stores the virtual server, pool name, and member IP address in clear text.
D. If a client’s browser accepts cookies, cookie persistence will always cause a cookie to be written to the client’s file system.
Which of the following statements are incorrect regarding protection of web services? (Choose two.)
A. The BIG-IP ASM System checks to ensure web services use cookies.
B. The BIG-IP ASM System parses XML requests and XML responses.
C. The BIG-IP ASM System checks to ensure XML documents are well formed.
D. The BIG-IP ASM System uses attack signatures to enforce negative security logic.
E. The BIG-IP ASM System checks for XML syntax, schema validation, and WSDL validation.
Which two methods can be used to determine which BIG-IP is currently active? (Choose two.)
A. The bigtop command displays the status.
B. Only the active system’s configuration screens are active.
C. The status (Active/Standby) is embedded in the command prompt.
D. The ifconfig a command displays the floating addresses on the active system.
The Protected Workspace client-side action provides more client-side security than the Cache and Session Control action.
A. True
B. False
Why does the F5 Application Delivery Firewall solution mitigate SSL attacks more effectively than any other firewalls?
A. Because F5 has unlimited capacity to handle SSL traffic.
B. Because F5 has full visibility and control of SSL traffic.
C. Because F5 has a separate iApp to handle SSL traffic.
D. Because F5 supports large SSL key sizes.
Which two ports must be enabled to establish communication between GTM Systems and other BIG IP Systems? (Choose two.)
A. 22
B. 53
C. 443
D. 4353
E. 4354
Which of the following is not a feature of a standalone BIG-IP ASM System?
A. Attack signatures
B. Multiple pool members
C. Positive security model
D. Real-time traffic policy builder
E. Predefined security policy templates
Which of the following TMOS feature enables BIG-IP to scale performance based to the available CPU cores?
A. Clustered multi-processing
B. OneConnect
C. HTTP class
D. Session persistence
E. Auto Last Hop
Which three are GTM server dynamic load balancing modes? (Choose three.)
A. Packet Rate
B. Virtual Server Score
C. CPU
D. Fallback IP
E. Ratio
What are the best reasons for using the Deployment Wizard? (Choose three.)
A. Flow level parameters checking is required.
B. The application encoding scheme needs to be determined by the BIG-IP ASM System.
C. Sufficient time is available to allow completely automated policy building based on observing live traffic.
D. The application platform must be protected against known attacks for the specific operating system, web server, and database.
Which of the following is a benefit of using iRules?
A. They provide a secure connection between a client and LTM
B. They enable granular control of traffic
C. They can be used as templates for creating new applications
D. They can use Active Directory to authenticate and authorize users
E. They provide an automated way to create LTM objects
Under what condition must an appliance license be reactivated?
A. Licenses only have to be reactivated for RMAs no other situations.
B. Licenses generally have to be reactivated during system software upgrades.
C. Licenses only have to be reactivated when new features are added (IPv6, Routing Modules, etc.) no other situations.
D. Never. Licenses are permanent for the platform regardless the version of software installed.
There are multiple HTTP class profiles assigned to a virtual server. Each profile has Application Security enabled. Which statement is true?
A. Traffic will process through every HTTP class profile every time.
B. Traffic will process through the first HTTP class profile that it matches and then stops.
C. Traffic will process through one HTTP class profile and if the traffic matches another profile, BIG-IP System will send a redirect to the client.
D. Traffic will only process through the HTTP class profile that it matches but always processes through the whole list and will process through each HTTP class profile it matches.
Which is a potential result when a trunk is configured on a BIG-IP?
A. No additional trunks can be configuration since each BIG-IP is limited to one trunk
B. Packets flowing to the VLAN could arrive on any of the interfaces in the trunk
C. Since any VLANs associated with the trunk are necessarily associated with multiple interfaces, the VLAN using the must use tagged packets.
D. VLAN failsafe is not available for any VLAN associated with any trunks.
APM provides access control lists at which two OSI layers? (Choose two.)
A. Layer 5
B. Layer 4
C. Layer 7
D. Layer 6
E. Layer 2
Which of the following statements best describes the ARX architecture?
A. The ARX’s split path architecture has a data path that handles the most common operations, and a control path that handles other operations requiring deeper inspection and updating of the index.
B. The ARX’s architecture has redundancy built in, allowing a single ARX to be deployed in most use cases which provides a huge cost savings to customers.
C. All of the above.
D. It is a software agent that installs on the storage device.
Assuming there are open connections through an active system's NAT and a failover occurs, by default, what happens to those connections?
A. All open connections will be lost.
B. All open connections will be maintained.
C. The “Mirror” option must be chosen on the NAT and the setting synchronized prior to the connection establishment.
D. Long-lived connections such as Telnet and FTP will be maintained while short-lived connections such as HTTP will be lost.
E. All open connections are lost, but new connections are initiated by the newly active BIG-IP, resulting in minimal client downtime.
Which is NOT a function of ASM?
A. Attack signature enforcement
B. HTTP protocol enforcement
C. Network security
D. Parameter value enforcement
Which three of the following are unique differentiators for F5 in the marketplace? (Choose three.)
A. VLANs
B. Load-balancing pools
C. Secure remote access
D. TMOS
E. OneConnect
F. iRules
The SNMP monitor can collect data based on which three metrics? (Choose three.)
A. packet rate
B. memory utilization
C. content verification
D. current connections
E. hops along the network path
When DNS_REV is used as the probe protocol by the GTM System, which information is expected in the response from the probe?
A. a reverse name lookup of the GTM System
B. the list of root servers known by the local DNS
C. the FQDN of the local DNS being probed for metric information
D. the revision number of BIND running on the requesting DNS server
Which two F5 platforms include specialized compression hardware? (Choose two.)
A. 4200
B. 3900
C. 1600
D. 11050
E. 6900
F. 8900
It is common for free storage space to exist somewhere in a business network that is not easy for storage administrators to utilize. What solution can the ARX provide in this situation?
A. The ARX identifies the exact location of the free storage, which allows network administrators to target those locations when provisioning additional storage.
B. The ARX extends the capacity of each server by 10-15, through intelligent file virtualization.
C. The ARX uses the extra storage for transaction logs and index files.
D. The ARX allows the customer to pool storage from anywhere within the enterprise and capacity balance the overflow across devices.
When an administrator creates a new access policy in the Visual Policy Editor, which three options are included by default? (Choose three.)
A. A fallback option
B. An Allow Ad box
C. A Deny End box
D. An empty Resource Assign item
E. A Start box
F. A Block All option
When initially configuring the BIG-IP System using the config tool, which of the following parameters can be configured? (Choose three.)
A. System hostname
B. Netmask of the management port
C. IP address of the management port
D. Default route of the management port
E. Port lockdown of the management port
Which three statements are true about SNATs? (Choose three.)
A. SNAT s provide bidirectional traffic initiation.
B. SNAT s support UDP, TCP, and ICMP traffic.
C. SNAT s provide a many-to-one mapping between IP addresses.
D. SNAT addresses can be identical to virtual server IP addresses.
A BIG-IP has a virtual server at 150.150.10.10:80 with SNAT automap configured. This BIG-IP also has a SNAT at 150.150.10.11 set for a source address range of 200.200.1.0 / 255.255.255.0. All other settings are at their default states. If a client with the IP address 200.200.1.1 sends a request to the virtual server, what is the source IP address when the associated packet is sent to the pool member?
A. 200.200.1.1
B. 150.150.10.11
C. Floating self IP address on VLAN where the packet leaves the system
D. Floating self IP address on VLAN where the packet arrives on the system
GTM solves which three of these standard DNS limitations? (Choose three.)
A. It can verify that a host is available before resolving a host name for a client.
B. It can use HTTPS for the connection between itself and the client.
C. It can ensure that clients remain at the same data center for stateful applications.
D. It can verify that a client does not have any viruses before sending the IP address.
E. It has more complex load balancing methods.
ASM provides antivirus protection by:
A. Extracting files being uploaded and sending them to an AV system via ICAP
B. Running a local antivirus program on the BIG-IP
C. None of the above
D. Using IP Penalty enforcement to block requests from hackers IPs
Which action will take place when a failover trigger is detected by the active system?
A. The active device will take the action specified for the failure.
B. The standby device also detects the failure and assumes the active role.
C. The active device will wait for all connections to terminate and then failover.
D. The standby device will begin processing virtual servers that have failed, but the active device will continue servicing the functional virtual servers.
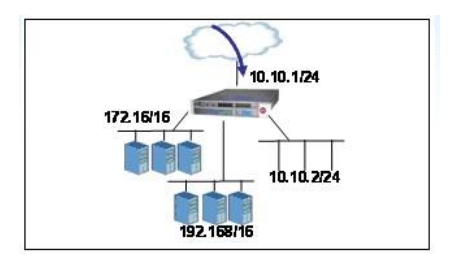
An LTM has the 3 virtual servers, 2 SNATs, four self IP addresses defined and the networks shown in the exhibit. Selected options for each object are shown below. Settings not shown are at their defaults. Assume port exhaustion has not been reached.A connection attempt is made with a source IP and port of 10.20.100.50:2222 and a destination IP and port of 10.10.2.102:443. When the request is processed, what will be the source and destination IP addresses?
A. Source IP: 10.10.2.103; Destination IP: pool member in the 192.168/16 network
B. Source IP: 10.10.201; Destination IP: pool member in the 192.168/16 network G
C. Source IP: 10.10.2.103; Destination IP: 10.10.2.102
D. The request will be dropped.
E. Source IP: 10.20.10.50; Destination IP: pool member in the 192.168/16 network
F. Source IP: 10.10.201; Destination IP: 10.102.102
What is a characteristic of iQuery?
A. It uses SSH.
B. It uses SSL.
C. It uses SCP.
D. It uses HTTPS.
A BIG-IP has two load balancing virtual servers at 150.150.10.10:80 and 150.150.10.10:443. The port 80 virtual server has SNAT automap configured. There is also a SNAT configured at 150.150.10.11 set for a source address range of 200.200.1.0 / 255.255.255.0. All other settings are at their default states. If a client with the IP address 200.200.1.1 sends a request to https://150.150.10.10, what is the source IP address when the associated packet is sent to the pool member?
A. 200.200.1.1
B. 150.150.10.11
C. Floating self IP address on VLAN where the packet leaves the system
D. Floating self IP address on VLAN where the packet arrives on the system
A site has six members in a pool. Three of the servers are new and have more memory and a faster processor than the others. Assuming all other factors are equal and traffic should be sent to all members, which two load balancing methods are most appropriate? (Choose two.)
A. Ratio
B. Priority
C. Observed
D. Round Robin
One reason APM beats the competition is its ability to perform both user authentication and authorization on a single device.
A. True
B. False
Which four of these benefits does APM provide? (Choose four.)
A. Enables remote access by several thousand simultaneous users.
B. Basic Web application firewall capabilities.
C. User authentication based on identity.
D. Acceleration of Web content to the client.
E. Granular authorization to resources.
F. Client workstation security checking.
Which four of these statements regarding object size and WebAccelerator performance are true? (Choose four.)
A. Large objects such as video cache well
B. Large objects allow fewer requests per second
C. Large objects result in higher throughput
D. Small objects result in higher throughput
E. Small objects such as images cache well
F. Small objects allow more requests per second
Network Security personnel are entirely responsible for web application security.
A. True
B. False
Which of the following is NOT a benefit of using SSL offload?
A. It increases the bandwidth between the client and LTM.
B. It enables LTM to decrypt traffic, examine the payload, and then re-encrypt before sending it to a pool member.
C. The organization requires far less SSL certificates.
D. The CPU processing load on backend servers is reduced.
E. It enables iRules to be used on traffic arriving to LTM that is encrypted.
Assuming there are open connections through an active system's virtual servers and a failover occurs, by default, what happens to the connections?
A. All open connections are lost.
B. All open connections are maintained.
C. When persistence mirroring is enabled, open connections are maintained even if a failover occurs.
D. Long-lived connections such as Telnet and FTP are maintained, but short-lived connections such as HTTP are lost.
E. All open connections are lost, but new connections are initiated by the newly active BIG-IP, resulting in minimal client downtime.
How many events can be referenced in a given iRule?
A. iRules are limited to one event, but a virtual server could be associated with multiple rules.
B. iRules can have multiple events.
C. Exactly one.
D. iRules can have up to event if one is client-side and one is server-side.
What is the purpose of provisioning?
A. Provisioning allows modules that are not licensed to be fully tested.
B. Provisioning allows modules that are licensed be granted appropriate resource levels.
C. Provisioning allows the administrator to activate modules in nonstandard combinations.
D. Provisioning allows the administrator to see what modules are licensed, but no user action is ever required.
The administrator must specify APM access control entries as either L4 or L7.
A. True
B. False
An LTM object contains both IP address and port combinations 20.18.9.250:80 and 20.18.9.251:80 and host the same Web application. What is this object?
A. Pool
B. Self-IP
C. Node
D. Pool member
E. Virtual Server
Which facility logs messages concerning GTM System parameters?
A. local0
B. local1
C. local2
D. local3
Free Access Full 101 Practice Exam Free
Looking for additional practice? Click here to access a full set of 101 practice exam free questions and continue building your skills across all exam domains.
Our question sets are updated regularly to ensure they stay aligned with the latest exam objectives—so be sure to visit often!
Good luck with your 101 certification journey!