MS-500 Practice Questions Free – 50 Exam-Style Questions to Sharpen Your Skills
Are you preparing for the MS-500 certification exam? Kickstart your success with our MS-500 Practice Questions Free – a carefully selected set of 50 real exam-style questions to help you test your knowledge and identify areas for improvement.
Practicing with MS-500 practice questions free gives you a powerful edge by allowing you to:
- Understand the exam structure and question formats
- Discover your strong and weak areas
- Build the confidence you need for test day success
Below, you will find 50 free MS-500 practice questions designed to match the real exam in both difficulty and topic coverage. They’re ideal for self-assessment or final review. You can click on each Question to explore the details.
You have a Microsoft 365 E5 subscription. You need to prevent users from uploading data loss prevention (DLP)-protected documents to the following third-party websites: ✑ web1.contoso.com web2.contoso.comThe solution must minimize administrative effort. To what should you set the Service domains setting for Endpoint DLP?
A. web1.contoso.com and web2.contoso.com
B. contoso.com
C. *.contoso.com
D. web*.contoso.com
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft 365 subscription that contains the users shown in the following table.You need to ensure that User1, User2, and User3 can use self-service password reset (SSPR). The solution must not affect User4. Solution: You create a conditional access policy for User1, User2, and User3. Does that meet the goal?
A. Yes
B. No
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft 365 E5 subscription that contains a user named User1. The Azure Active Directory (Azure AD) Identity Protection risky users report identifies User1. For User1, you select Confirm user compromised. User1 can still sign in. You need to prevent User1 from signing in. The solution must minimize the impact on users at a lower risk level. Solution: You configure the sign-in risk policy to block access when the sign-in risk level is high. Does this meet the goal?
A. Yes
B. No
You have a Microsoft 365 subscription. You need to recommend a passwordless authentication solution that uses biometric authentication. What should you include in the recommendation?
A. Windows Hello for Business
B. a smart card
C. the Microsoft Authenticator app
D. a PIN
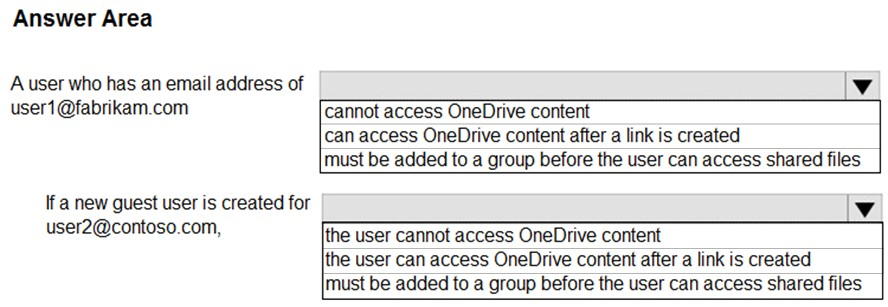
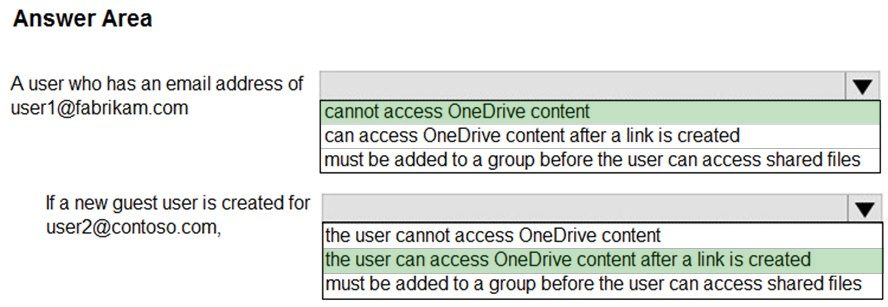
HOTSPOT - You have a Microsoft 365 subscription that uses a default domain name of litwareinc.com. You configure the Sharing settings in Microsoft OneDrive as shown in the following exhibit.Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point. Hot Area:
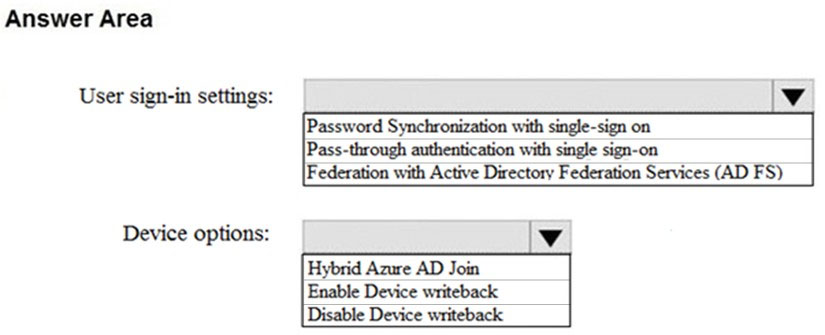
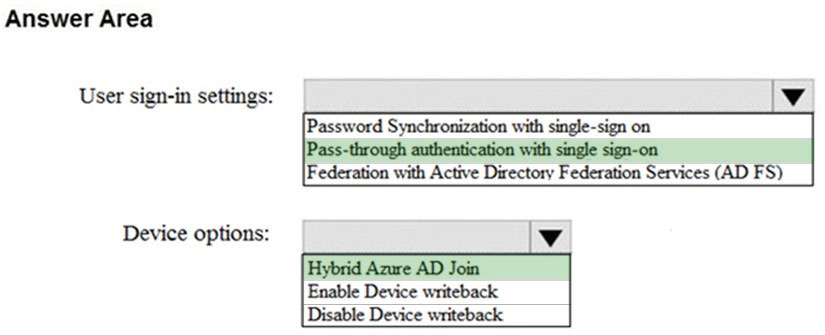
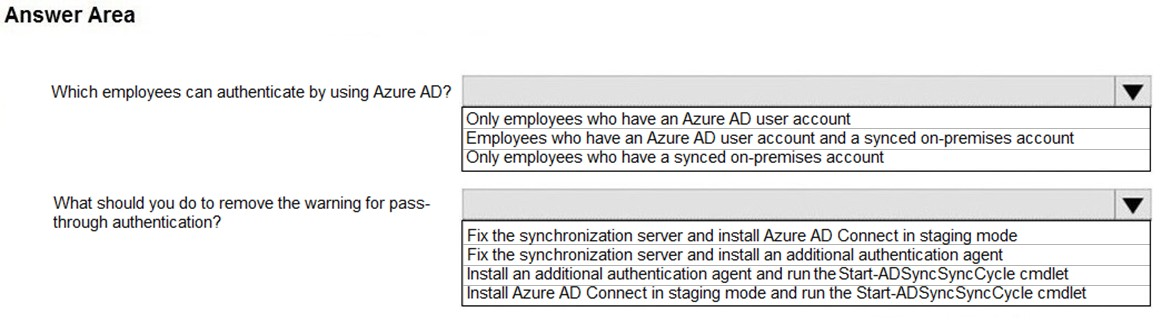
HOTSPOT - How should you configure Azure AD Connect? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
Your company has 500 computers. You plan to protect the computers by using Microsoft Defender for Endpoint. Twenty of the computers belong to company executives. You need to recommend a remediation solution that meets the following requirements: ✑ Microsoft Defender for Endpoint administrators must manually approve all remediation for the executives ✑ Remediation must occur automatically for all other users What should you recommend doing from Microsoft Defender Security Center?
A. Configure 20 system exclusions on automation allowed/block lists
B. Configure two alert notification rules
C. Download an offboarding package for the computers of the 20 executives
D. Create two machine groups
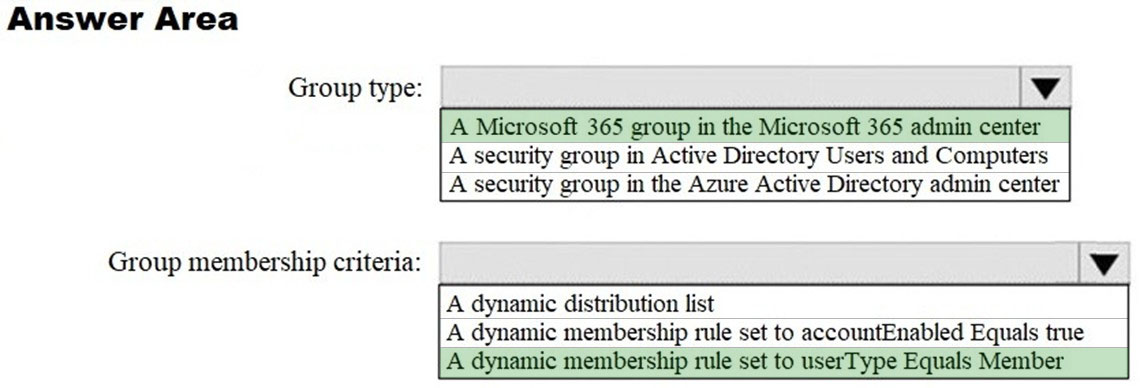
You need to create Group3. What are two possible ways to create the group?
A. a Microsoft 365 group in the Microsoft 365 admin center
B. a mail-enabled security group in the Microsoft 365 admin center
C. a security group in the Microsoft 365 admin center
D. a distribution group in the Microsoft 365 admin center
E. a security group in the Azure AD admin center
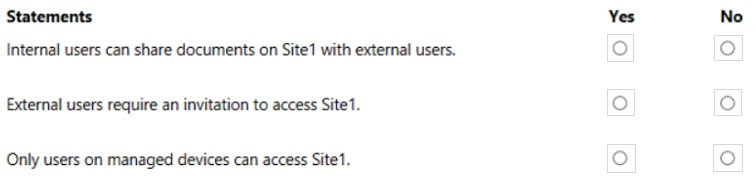
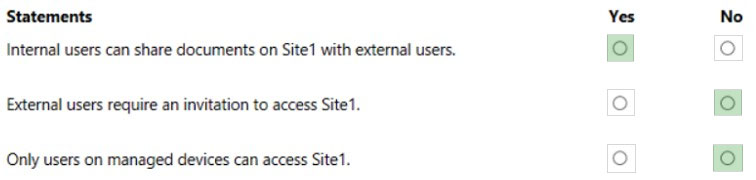
HOTSPOT - You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint Online site named Site1 and a sensitivity label named Label1. The external sharing settings for Site1 are configured as shown in the Site1 exhibit. (Click the Site1 tab.)The external sharing settings for Label1 are configured as shown in the Label1 exhibit. (Click the Label1 tab.)
Label 1 is applied to Site1. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
DRAG DROP - You have a Microsoft 365 E5 subscription. You need to meet the following requirements: • Prevent the sharing of files between the users in a department named department1 and the users in a department named department2. • Generate an alert if a user downloads large quantities of sensitive customer data. Which type of policy should you use for each requirement? To answer, drag the appropriate policy types to the correct requirements. Each policy type may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription. From the Microsoft 365 admin center, you create a new user. You plan to assign the Reports reader role to the user. You need to view the permissions of the Reports reader role. Which admin center should you use?
A. Microsoft 365 Defender
B. Azure Active Directory
C. Microsoft Defender for Identity
D. Microsoft Defender for Cloud Apps
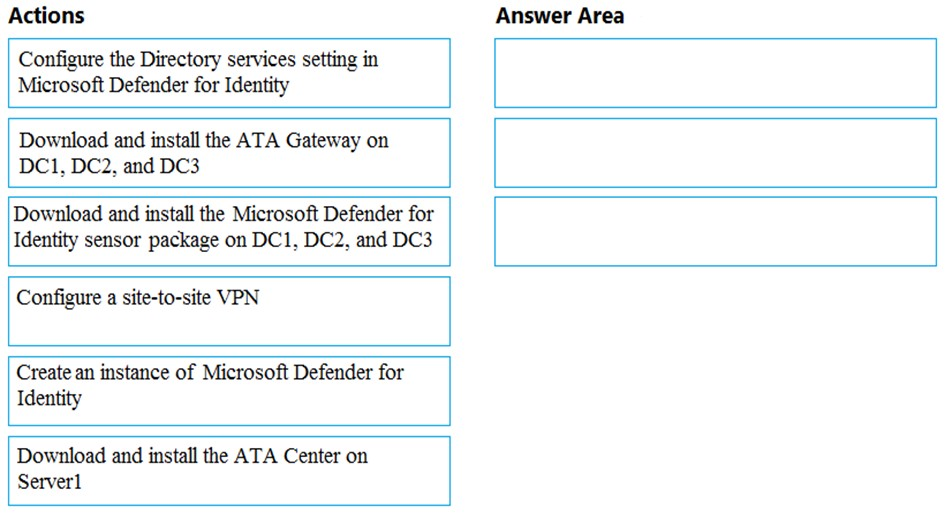
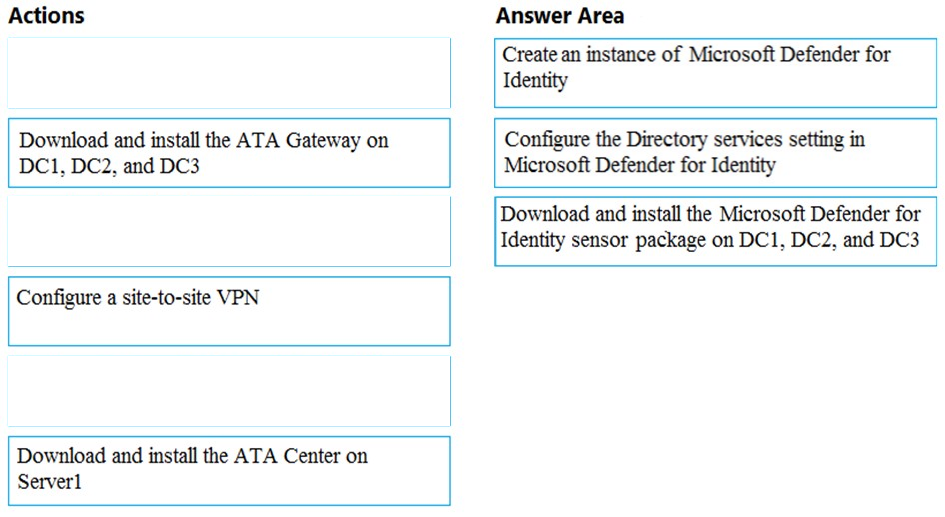
DRAG DROP - You need to configure threat detection for Active Directory. The solution must meet the security requirements. Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. Select and Place:
You have an Azure Sentinel workspace that has an Azure Active Directory (Azure AD) connector and a Microsoft Office 365 connector. You need to use a Fusion rule template to detect multistage attacks in which users sign in by using compromised credentials, and then delete multiple files from Microsoft OneDrive. Based on the Fusion rule template, you create an active rule that has the default settings. What should you do next?
A. Add data connectors.
B. Add a workbook.
C. Add a playbook.
D. Create a custom rule template.
HOTSPOT - How should you configure Group3? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a Microsoft 365 subscription that contains 1,000 user mailboxes. An administrator named Admin1 must be able to search for the name of a competing company in the mailbox of a user named User5. You need to ensure that Admin1 can search the mailbox of User5 successfully. The solution must prevent Admin1 from sending email messages as User5. Solution: You modify the permissions of the mailbox of User5, and then create an eDiscovery case. Does this meet the goal?
A. Yes
B. No
DRAG DROP - Your network contains an on-premises Active Directory domain named contoso.com that syncs to Azure AD by using Azure AD Connect. The domain contains the users shown in the following table.From Active Directory Users and Computers, you add the user shown in the following table.
From Active Directory1 Users and Computers, you update the ProxyAddresses attributes as shown in the following table.
Which status will Azure AD Connect sync return for each user after the next sync? To answer, drag the appropriate statuses to the correct users. Each status may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have an on-premises Active Directory domain named contoso.com. You install and run Azure AD Connect on a server named Server1 that runs Windows Server. You need to view Azure AD Connect events. Solution: You use the Security event log on Server1. Does that meet the goal?
A. Yes
B. No
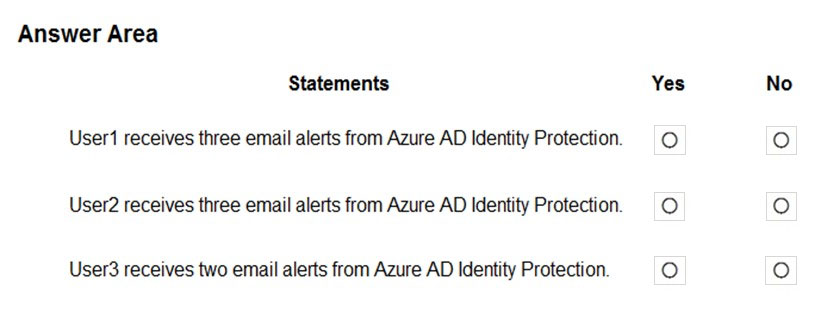
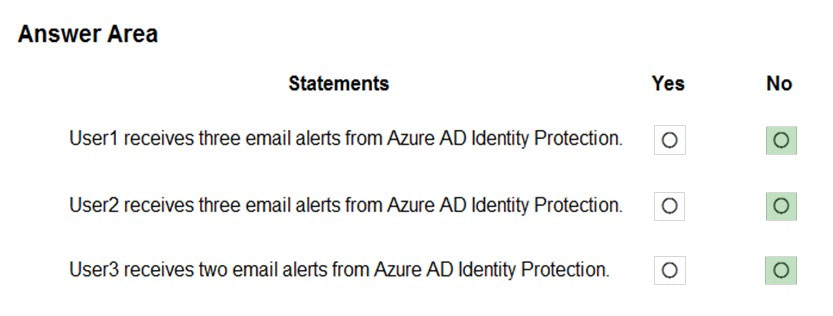
HOTSPOT - You have a Microsoft 365 E5 subscription that contains an Azure Active Directory (Azure AD) tenant named contoso.com. Azure AD Identity Protection alerts for contoso.com are configured as shown in the following exhibit.A user named User1 is configured to receive alerts from Azure AD Identity Protection. You create users in contoso.com as shown in the following table.
The users perform the sign-ins shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table.You discover that several security alerts are visible from the Microsoft Defender for Identity portal. You need to identify which users in contoso.com can close the security alerts. Which users should you identify?
A. User4 only
B. User1 and User2 only
C. User3 and User4 only
D. User1 and User3 only
E. User1 only
You have a Microsoft 365 subscription. You have a Microsoft SharePoint Online site named Site1. The files in Site1 are protected by using Microsoft Azure Information Protection. From the Microsoft 365 Compliance center, you create a label that designates personal data. You need to auto-apply the new label to all the content in Site1. What should you do first?
A. From PowerShell, run Set-ManagedContentSettings.
B. From PowerShell, run Set-ComplianceTag.
C. From the Microsoft 365 Compliance center, create a Data Subject Request (DSR).
D. Remove Azure Information Protection from the Site1 files.
You have a Microsoft 365 E5 subscription that contains the groups shown in the following table.You need to create a Privacy Risk Management policy in Microsoft Priva. To which groups can you apply the policy?
A. Group1, Group2, or Group3 only
B. Group1, Group3, or Group4 only
C. Group1 or Group2 only
D. Group1 only
E. Group1, Group2, Group3, or Group4
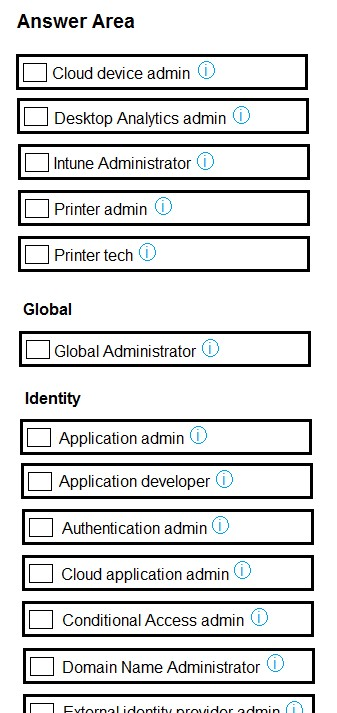
HOTSPOT - You have a Microsoft 365 E5 subscription linked to an Azure Active Directory (Azure AD) tenant. The tenant contains a user named User1 and multiple Windows 10 devices. The devices are Azure AD joined and protected by using BitLocker Drive Encryption (BitLocker). You need to ensure that User1 can perform the following actions: ✑ View BitLocker recovery keys. ✑ Configure the usage location for the users in the tenant. The solution must use the principle of least privilege. Which two roles should you assign to User1 in the Microsoft 365 admin center? To answer, select the appropriate roles in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint Online site named Site1 and the data loss prevention (DLP) policies shown in the following table.The DLP rules are configured as shown in the following table.
All the policies are assigned to Site1. You need to ensure that if a user uploads a document to Site1 that matches all the rules, the user will be shown the Tip 2 policy tip. What should you do?
A. Enable additional processing of the policies if there is a match for Rule1.
B. Prevent additional processing of the policies if there is a match for Rule2.
C. Change the priority of DLP2 to 3.
D. Change the priority of DLP2 to 0.
HOTSPOT - Your network contains an on-premises Active Directory domain that syncs to Azure Active Directory (Azure AD) as shown in the following exhibit.The synchronization schedule is configured as shown in the following exhibit.
Use the drop-down menus to select the answer choice that answers each question based on the information presented in the graphic. NOTE: Each correct selection is worth one point. Hot Area:
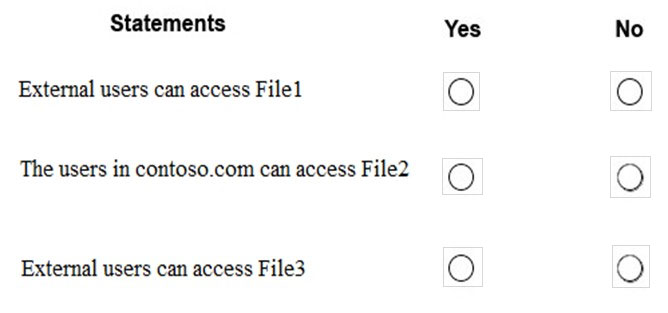
HOTSPOT - You have a Microsoft 365 subscription that uses an Azure Active Directory (Azure AD) tenant named contoso.com. OneDrive stores files that are shared with external users. The files are configured as shown in the following table.You create a data loss prevention (DLP) policy that applies to the content stored in OneDrive accounts. The policy contains the following three rules: Rule1: ✑ Conditions: Label1, Detect content that's shared with people outside my organization ✑ Actions: Restrict access to the content for external users ✑ User notifications: Notify the user who last modified the content ✑ User overrides: On ✑ Priority: 0 Rule2: ✑ Conditions: Label1 or Label2 ✑ Actions: Restrict access to the content ✑ Priority: 1 Rule3: ✑ Conditions: Label2, Detect content that's shared with people outside my organization ✑ Actions: Restrict access to the content for external users ✑ User notifications: Notify the user who last modified the content ✑ User overrides: On ✑ Priority: 2 For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
SIMULATION - You need to ensure that a global administrator is notified when a document that contains U.S. Health Insurance Portability and Accountability Act (HIPAA) data is identified in your Microsoft 365 tenant. To complete this task, sign in to the Microsoft Office 365 admin center.
SIMULATION - You need to ensure that a user named Grady Archie can monitor the service health of your Microsoft 365 tenant. The solution must use the principle of least privilege. To complete this task, sign in to the Microsoft 365 portal.
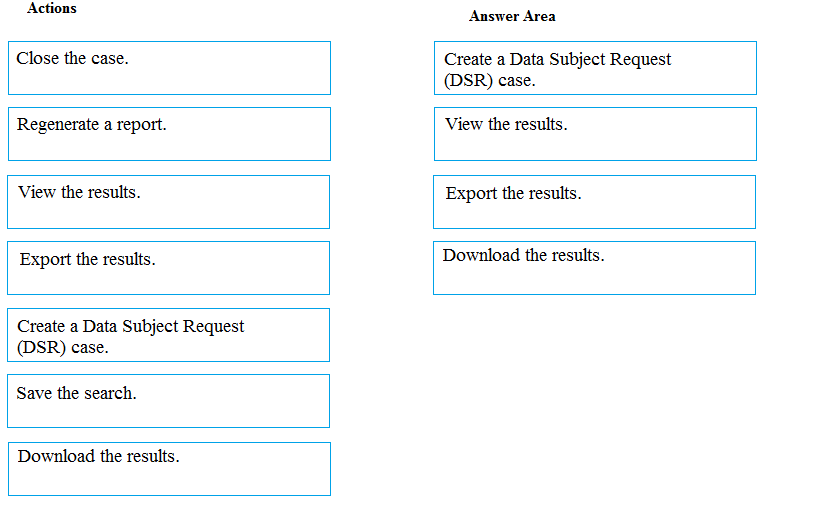
DRAG DROP - You have a Microsoft 365 subscription. A customer requests that you provide her with all documents that reference her by name. You need to provide the customer with a copy of the content. Which four actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order. Select and Place:
You have a Microsoft 365 subscription and a Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP) subscription. You have devices enrolled in Microsoft Endpoint Manager as shown in the following table:You integrate Microsoft Defender ATP and Endpoint Manager. You plan to evaluate the Microsoft Defender ATP risk level for the devices. You need to identify which devices can be evaluated. Which devices should you identify?
A. Device1 and Device2 only
B. Device1 only
C. Device1 and Device3 only
D. Device1, Device2 and Device3
You have a Microsoft 365 tenant. You have 500 computers that run Windows 10. You plan to monitor the computers by using Microsoft Defender for Endpoint after the computers are enrolled in Microsoft Intune. You need to ensure that the computers connect to Microsoft Defender for Endpoint. What should you do in Microsoft Endpoint Manager admin center?
A. Configure an enrollment restriction
B. Create a device configuration profile
C. Create a conditional access policy
D. Create a Windows Autopilot deployment profile
Your company has a Microsoft 365 subscription. The company does not permit users to enroll personal devices in mobile device management (MDM). Users in the sales department have personal iOS devices. You need to ensure that the sales department users can use the Microsoft Power BI app from iOS devices to access the Power BI data in your tenant. The users must be prevented from backing up the app's data to iCloud. What should you create?
A. a conditional access policy in Microsoft Azure Active Directory (Azure AD) that has a device state condition
B. an app protection policy in Microsoft Endpoint Manager
C. a conditional access policy in Microsoft Azure Active Directory (Azure AD) that has a client apps condition
D. a device compliance policy in Microsoft Endpoint Manager
You have a Microsoft 365 E5 subscription. A customer requests access to all his personal data. You need to manage the customer’s request. What should you do first?
A. Create a content search.
B. Enable sharing with external users.
C. Set Require approval for all data access requests to On for Customer Lockbox.
D. Create a Data Subject Request (DSR) case.
You configure several Microsoft Defender for Office 365 policies in a Microsoft 365 subscription. You need to allow a user named User1 to view Microsoft Defender for Office 365 reports in the Threat management dashboard. Which role provides User1 with the required role permissions?
A. Security reader
B. Compliance administrator
C. Information Protection administrator
D. Exchange administrator
You have an Azure Active Directory (Azure AD) tenant that has a Microsoft 365 subscription. You recently configured the tenant to require multi-factor authentication (MFA) for risky sign-ins. You need to review the users who required MFA. What should you do?
A. From the Microsoft 365 admin center, review a Security & Compliance report
B. From the Microsoft 365 Compliance center, run an audit log search and download the results to a CSV file
C. From the Azure Active Directory admin center, review the Authentication methods activities
D. From the Azure Active Directory admin center, download the sign-ins to a CSV file
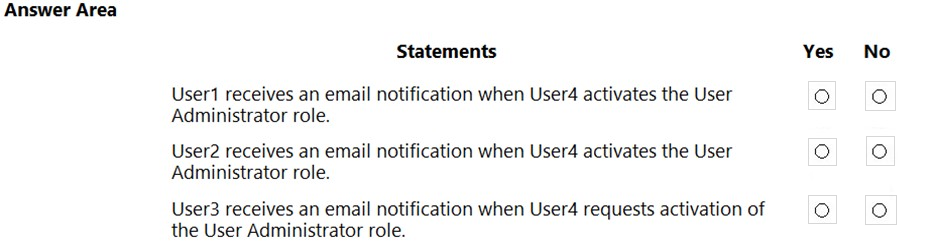
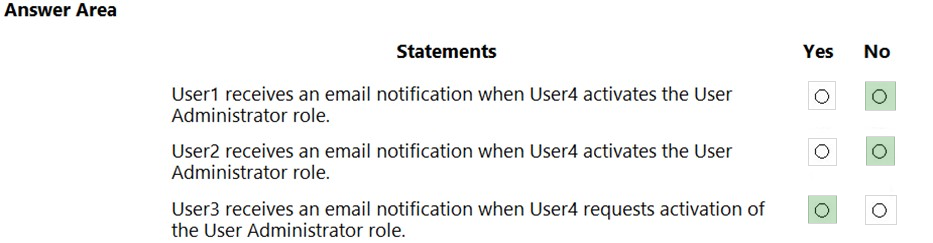
HOTSPOT - You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table.The User Administrator role is configured in Azure AD Privileged Identity Management (PIM) as shown in the following exhibit.
You make User4 eligible for the User Administrator role. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
SIMULATION - You discover that Microsoft SharePoint content is shared with users from multiple domains. You need to allow sharing invitations to be sent only to users in an email domain named contoso.com. To complete this task, sign in to the Microsoft 365 portal.
HOTSPOT - You have a Microsoft 365 E5 subscription that contains two groups named Group1 and Group2 and the users shown in the following table.You have the Privileged Access settings configured as shown in the following exhibit.
You have a privileged access policy that has the following settings: • Policy name: New Transport Rule • Policy type: Task • Policy scope: Exchange • Approval Type: Manual • Approver group: Group1 User1 requests access to the New Transport Rule policy for a duration of two hours. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription. You enable auditing for the subscription. You plan to provide a user named Auditor with the ability to review audit logs. You add Auditor to the Global administrator role group. Several days later, you discover that Auditor disabled auditing. You remove Auditor from the Global administrator role group and enable auditing. You need to modify Auditor to meet the following requirements: ✑ Be prevented from disabling auditing ✑ Use the principle of least privilege ✑ Be able to review the audit log To which role group should you add Auditor?
A. Security reader
B. Compliance administrator
C. Security operator
D. Security administrator
You have a Microsoft 365 subscription. You create a Microsoft Defender for Office 365 safe attachments policy. You need to configure the retention duration for the attachments in quarantine. Which type of threat management policy should you create?
A. Anti-phishing
B. DKIM
C. Anti-spam
D. Anti-malware
HOTSPOT - You have a Microsoft 365 E5 subscription that contains the users shown in the following table.You need to run Attack simulation training. The solution must ensure that the following tasks are performed: • Payloads are created. • The simulation is launched. Which users can perform each task? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Your company has a Microsoft 365 E5 subscription that uses Microsoft Defender for identity. You plan to create a detection exclusion in Microsoft Defender for Identity. What should you use to create the detection exclusion?
A. Microsoft Defender for Identity portal
B. Microsoft 365 Compliance center
C. Microsoft Defender for Cloud Apps portal
D. Microsoft 365 Defender portal
Which IP address space should you include in the Trusted IP MFA configuration?
A. 131.107.83.0/28
B. 192.168.16.0/20
C. 172.16.0.0/24
D. 192.168.0.0/20
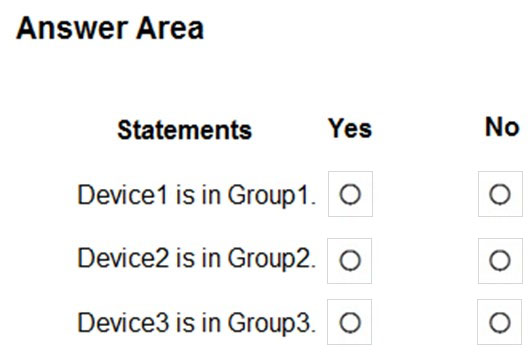
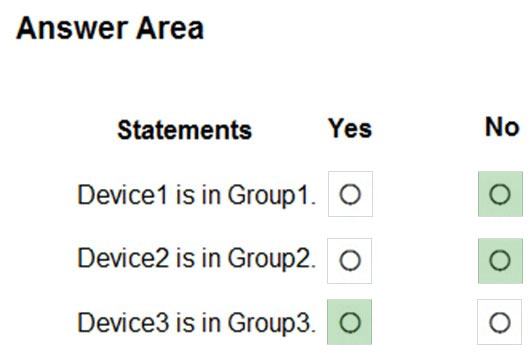
HOTSPOT - You create device groups in Microsoft Defender for Endpoint as shown in the following table.You onboard three devices to Microsoft Defender for Endpoint as shown in the following table.
After the devices are onboarded, you perform the following actions: ✑ Add a tag named Tag1 to Device1. ✑ Rename Computer3 as Device3. For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
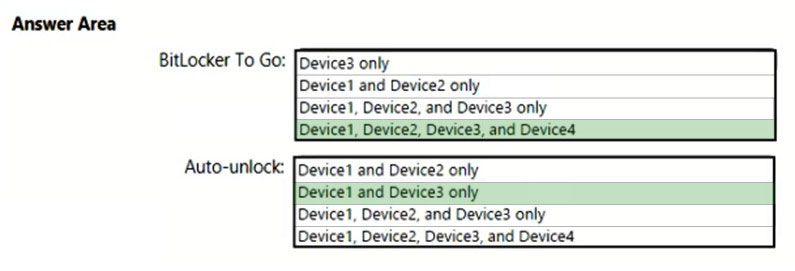
HOTSPOT - You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com. Four Windows 10 devices are joined to the tenant as shown in the following table.On which devices can you use BitLocker To Go and on which devices can you turn on auto-unlock? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
SIMULATION - You need to ensure that a user named Allan Deyoung can perform searches and place holds on mailboxes, SharePoint Online sites, and OneDrive for Business locations. The solution must use the principle of least privilege. To complete this task, sign in to the Microsoft 365 admin center.
SIMULATION - Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time. When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design. Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn't matter how you accomplish the task, if you successfully perform it, you will earn credit for that task. Labs are not timed separately, and this exam may more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided. Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab. Username and password -Use the following login credentials as needed: To enter your username, place your cursor in the Sign in box and click on the username below. To enter your password, place your cursor in the Enter password box and click on the password below. Microsoft 365 Username: admin@LODSe244001.onmicrosoft.com Microsoft 365 Password: &=Q8v@2qGzYz If the Microsoft 365 portal does not load successfully in the browser, press CTRL-K to reload the portal in a new browser tab. The following information is for technical support purposes only: Lab instance: 11032396 - You need to ensure that a user named Alex Wilber can register for multifactor authentication (MFA). To complete this task, sign in to the Microsoft Office 365 admin center.
SIMULATION - Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time. When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design. Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn't matter how you accomplish the task, if you successfully perform it, you will earn credit for that task. Labs are not timed separately, and this exam may more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided. Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab. Username and password -Use the following login credentials as needed: To enter your username, place your cursor in the Sign in box and click on the username below. To enter your password, place your cursor in the Enter password box and click on the password below. Microsoft 365 Username: admin@LODSe244001.onmicrosoft.com Microsoft 365 Password: &=Q8v@2qGzYz If the Microsoft 365 portal does not load successfully in the browser, press CTRL-K to reload the portal in a new browser tab. The following information is for technical support purposes only: Lab instance: 11032396 - You need to ensure that a user named Lee Gu can manage all the settings for Exchange Online. The solution must use the principle of least privilege. To complete this task, sign in to the Microsoft Office 365 admin center.
You have a Microsoft 365 subscription. The Global administrator role is assigned to your user account. You have a user named Admin1. You create an eDiscovery case named Case1. You need to ensure that Admin1 can view the results of Case1. What should you do first?
A. From the Azure Active Directory admin center, assign a role group to Admin1.
B. From the Microsoft 365 admin center, assign a role to Admin1.
C. From the Microsoft 365 Compliance center, assign a role group to Admin1.
You have an Azure Active Directory (Azure AD) tenant that contains the users shown in the following table.You configure the Security Operator role in Azure AD Privileged Identity Management (PIM) as shown in the following exhibit.
You add assignments to the Security Operator role as shown in the following table.
Which users can activate the Security Operator role?
A. User2 only
B. User3 only
C. User1 and User2 only
D. User2 and User3 only
E. User1, User2, and User3
You have a Microsoft 365 tenant. From the Azure Active Directory admin center, you review the Risky sign-ins report as shown in the following exhibit.You need to ensure that you can see additional details including the risk level and the risk detection type. What should you do?
A. Purchase Microsoft 365 Enterprise E5 licenses.
B. Activate an instance of Microsoft Defender for Identity.
C. Configure Diagnostic settings in Azure Active Directory (Azure AD).
D. Deploy Azure Sentinel and add a Microsoft Office 365 connector.
Free Access Full MS-500 Practice Questions Free
Want more hands-on practice? Click here to access the full bank of MS-500 practice questions free and reinforce your understanding of all exam objectives.
We update our question sets regularly, so check back often for new and relevant content.
Good luck with your MS-500 certification journey!